- Table of Contents
-
- 01-Fundamentals Configuration Guide
- 00-Preface
- 01-CLI Configuration
- 02-Login Management Configuration
- 03-FTP and TFTP Configuration
- 04-File System Management Configuration
- 05-Configuration File Management Configuration
- 06-Software Upgrade Configuration
- 07-License Management
- 08-Device Management Configuration
- 09-Automatic Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 06-Software Upgrade Configuration | 241.10 KB |
Installing and running a patch in one step·
Installing a patch step by step
Uninstalling a patch step by step
Displaying and maintaining software upgrade
Disabling password recovery capability·
Examining the state of password recovery capability
Dealing with console login password loss when password recovery capability is enabled
Dealing with user privilege level password loss when password recovery capability is enabled
Dealing with password loss when password recovery capability is disabled
Upgrading software
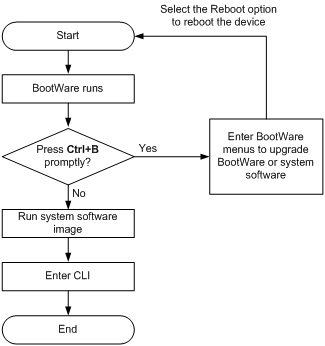
Upgrading software includes upgrading the BootWare (called "bootrom" in CLI) and system software. Each time the device is powered on, it runs the BootWare image to initialize hardware and display hardware information, and then runs the system software image (called the "boot file" in software code) so you can access the software features, as shown in Figure 1.
Figure 1 System startup process
FIPS compliance
The device supports the FIPS mode that complies with NIST FIPS 140-2 requirements. Support for features, commands, and parameters might differ in FIPS mode and non-FIPS mode. For more information about FIPS mode, see Security Configuration Guide.
Software upgrade methods
You can use one of the following methods to upgrade system software:
|
Upgrading method |
Software types |
Remarks |
|
Upgrading from the CLI: |
|
|
|
Upgrading the software |
· BootWare image · System software image (excluding patches) |
This method is disruptive. You must reboot the entire device to complete the upgrade. |
|
Installing hotfixes |
System software image |
Hotfixes repair software defects without requiring a reboot or service interruption. Hotfixes do not add new features to system software images. |
|
Upgrading from the BootWare menus |
· BootWare image · System software image |
Use this method when the device cannot correctly start up. For information about this upgrading method, see the release notes for your device. |
This chapter covers only upgrading the software and installing hotfixes from the CLI.
Upgrading BootWare
|
Step |
Command |
Remarks |
|
1. Use FTP or TFTP to transfer the BootWare image to the root directory of the storage medium on the device. |
See "Configuring FTP" or "Configuring TFTP." |
Make sure the image file is saved in the root directory of the storage medium. |
|
2. Read, restore, back up, or upgrade BootWare on the device in user view. |
bootrom { backup | read | restore | update file file-url } [ all | part ] |
If neither the all keyword nor the part keyword is specified, the operation applies to the entire BootWare image. In FIPS mode, the BootWare image file must pass authenticity verification before the bootrom update file file-url command can be executed. |
|
3. Reboot the device. |
reboot |
N/A |
Upgrading system software
|
Step |
Command |
Remarks |
|
1. Use FTP or TFTP to transfer the system software image to the root directory of the storage medium on the device. |
See "Configuring FTP" or "Configuring TFTP." |
The image file must be saved in the root directory for a successful upgrade. |
|
2. Specify the file as the startup system software image in user view. |
boot-loader file file-url { main | backup } |
In FIPS mode, the file must pass authenticity verification before it can be set as a startup system software image file. |
|
3. Reboot the device. |
reboot |
N/A |
Installing hotfixes
Hotfixes (called "patches" in this document) repair software defects without requiring a system reboot.
Basic concepts
This section describes the basic patch concepts.
Patch, patch file, and patch package file
A patch fixes certain software defects.
A patch file contains one or more patches. After being loaded from the storage medium to the patch memory area, each patch is assigned a unique number, which starts from 1. For example, if a patch file has three patches, they are numbered 1, 2, and 3.
A patch package file contains patch files for multiple modules. It enables you to use one command to bulk-fix bugs for multiple modules.
Incremental patch
Incremental patches are dependent on previous patches and cannot separately run. For example, if a patch file has three patches, patch 3 can be running only after patch 1 and 2 take effect. You cannot run patch 3 separately.
Patches that have been released are all incremental patches.
Common patch and temporary patch
Common patches are formally released to users.
A common patch always includes the functions of its previous temporary patches. The system deletes all the temporary patches before loading the common patch.
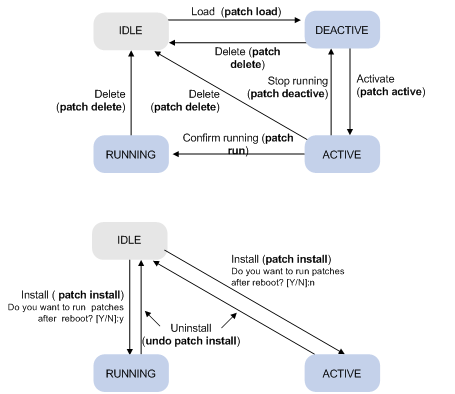
Patch states
A patch is in IDLE, DEACTIVE, ACTIVE, or RUNNING state, depending on the patch manipulation command.
Patch manipulation commands include patch load (load), patch active (run temporarily), patch run (confirm running), patch deactive (stop running), patch delete (delete), patch install (install), and undo patch install (uninstall).
For example, if you execute the patch active command, patches in DEACTIVE state change to the ACTIVE state.
Figure 2 shows the patch manipulation commands and how they affect the patch state.
|
|
IMPORTANT: Patch state information is saved in the patchstate file on the storage medium. To make sure the device can correctly find the patches, do not edit, delete, move the file, or change the file name. |
Figure 2 Impact of patch manipulation commands on patch state
IDLE state
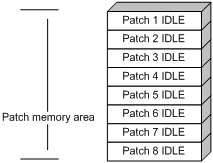
Patches that have not been loaded are in IDLE state. You cannot install or run these patches. As shown in Figure 3, the patch memory area can load up to eight patches.
The patch memory area supports up to 200 patches.
Figure 3 Patches that are not loaded to the patch memory area
DEACTIVE state
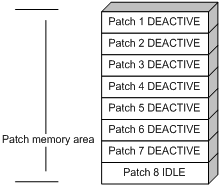
Patches in DEACTIVE state have been loaded to the patch memory area but have not yet run in the system. For example, suppose that the patch file you are loading has seven patches. After the seven patches successfully pass the version check and CRC check, they are loaded to the patch memory area and are in DEACTIVE state. In the patch area, patch states are as shown in Figure 4.
Figure 4 Patch states in the patch memory area after a patch file is loaded
ACTIVE state
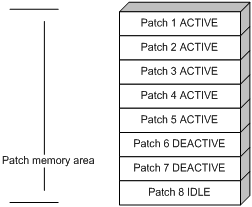
Patches in ACTIVE state run temporarily in the system and become DEACTIVE at a reboot. For example, for the seven patches in Figure 4, if you activate the first five patches, their states change from DEACTIVE to ACTIVE. Figure 5 shows the patch states in the system.
The patches that are in ACTIVE state change to the DEACTIVE state at a reboot.
Figure 5 Patches are activated
RUNNING state
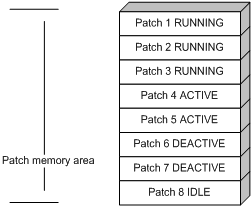
After you confirm ACTIVE patches, their states change to RUNNING and persist after a reboot. In contrast to ACTIVE patches, RUNNING patches continue to take effect after a reboot. For example, if you confirm the first three patches in Figure 5, their state changes from ACTIVE to RUNNING, and the RUNNING state persists after a reboot. Figure 6 shows the patch states in the system.
Figure 6 Patches in RUNNING state
Patch installation task list
|
Task |
Remarks |
|
|
Installing patches: |
Use either method. Step-by-step patch installation allows you to control the patch status. |
|
|
Optional. |
Installation prerequisites
To ensure a successful patch operation and normal device operation after the patch installation:
· Make sure each patch file you are installing matches the device model and software version.
· Save patch files or patch package files to the root directory of the storage medium on the device.
· Correctly name a patch file in the patch_PATCH-FlAG suffix.bin format. The PATCH-FLAG suffix is predefined and must be the same as the letters (digits are excluded) displayed for the Version field in the output from the display patch information command. If a patch file is not correctly named, the system cannot identify the file.
The default system patch file name is patch_mpu.bin for all WLAN-supported cards except for the WX3000E/WX5540E switching engine and the WX6103 switch interface board.
Installing and running a patch in one step
To install and run patches in one step, use the patch install command. This command changes the state of installed patches from IDLE to ACTIVE or RUNNING, depending on your choice.
When executing the patch install command, you must choose to run installed patches or disable running them after a reboot. If you choose to have installed patches continue to run after a reboot, the installed patches are set in RUNNING state and remain in this state after a reboot. If not, the installed patches are set in ACTIVE state and change to the DEACTIVE state at a reboot.
To install and run patches in one step:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Install patches in one step. |
patch install { patch-location | file patch-package } |
· patch-location: Specifies the directory where the patch file is located. · file patch-package: Specifies a patch package file name. In FIPS mode, the patch file or patch package file must pass authenticity verification before this command can be executed. |
If you execute the patch install patch-location command, the directory specified for the patch-location argument replaces the directory specified with the patch location command after the upgrade is complete.
If you execute the patch install file patch-package command, the directory specified with the patch location command does not change.
To uninstall all ACTIVE and RUNNING patches in one step, use the undo patch install command. For information about the step-by-step patch uninstall method, see "Uninstalling a patch step by step."
Installing a patch step by step
In contrast to the one-step patch installation method, step-by-step patch installation enables you to control patch status during the patch installation process.
Step-by-step patch installation task list
|
Task |
Remarks |
|
Optional. To install a patch package, skip this step. |
|
|
Required. |
|
|
Required. |
|
|
Optional. |
Configuring the patch file location
The patch file location must be the root directory of the storage medium.
To configure the patch file location:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the patch file location. |
patch location patch-location |
By default, the system loads patch files from the root directory of the storage medium. |
|
|
NOTE: If you execute the patch install patch-location command, the directory specified for the patch-location argument replaces the directory specified with the patch location command after the upgrade is complete. |
Loading a patch file
You must load the correct patch file before performing any patch installation operations.
If you install a patch from a patch file, the system loads the patch file from the patch file location, which is the root directory of the storage medium.
If you install a patch from a patch package, the system finds the correct patch file in the patch package file and loads the patch file.
|
|
IMPORTANT: Set the file transfer mode to binary mode before using FTP or TFTP to upload or download patch files. Otherwise, patch files cannot be parsed properly. |
To load a patch file:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Load the patch file from the storage medium to the patch memory area. |
patch load [ file patch-package ] |
In FIPS mode, the patch file or patch package file must pass authenticity verification before this command can be executed. |
Activating patches
Activating a patch changes its state to ACTIVE. An ACTIVE patch runs in memory until a reboot occurs. To have a patch continue to run after a reboot, you must change its state to RUNNING.
To activate patches:
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Activate patches. |
patch active [ patch-number ] |
Confirming ACTIVE patches
To have an ACTIVE patch continue to run after a reboot, perform the task in this section.
After you confirm an ACTIVE patch, its state changes to RUNNING and persists after a reboot.
To confirm ACTIVE patches:
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Confirm ACTIVE patches. |
patch run [ patch-number ] |
Uninstalling a patch step by step
To uninstall a patch step by step, you must first stop running the patch and then remove it from the patch memory area.
Stopping running patches
When you stop running a patch, the patch state becomes DEACTIVE, and the system runs the way it did before the patch was installed.
To stop running patches:
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Stop running patches. |
patch deactive [ patch-number ] |
Removing patches from the patch memory area
After being removed from the patch memory area, a patch is still retained in IDLE state in the storage medium. The system runs the way it did before the patch was installed.
To remove patches from the patch memory area:
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Remove patches from the patch memory area. |
patch delete [ patch-number ] |
Displaying and maintaining software upgrade
|
Task |
Command |
Remarks |
|
Display information about the system software image. |
display boot-loader [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display information about the patch package. |
display patch [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display patch information. |
display patch information [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
Software upgrade examples
Upgrading the system software
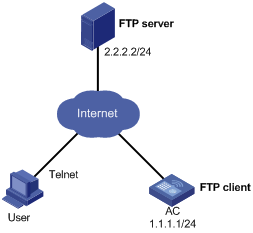
Network requirement
As shown in Figure 7, the current system software version of the AC is soft-version1. The latest system software image soft-version2.bin and the latest configuration file new-config.cfg are both saved in the aaa directory of the FTP server. The AC and the FTP server can reach each other. You can log in to the AC through Telnet.
Upgrade the software version of the AC to soft-version2 and configuration file to new-config during an off-peak period.
Configuration procedure
1. Configure the FTP server (configuration varies with different types of servers):
# Set access parameters for the FTP client (including enabling the FTP server function, setting the FTP username to aaa and password to hello, and assigning the FTP user the right to access the cfa0:/aaa directory).
<FTP-server> system-view
[FTP-server] ftp server enable
[FTP-server] local-user aaa
[FTP-server-luser-aaa] password cipher hello
[FTP-server-luser-aaa] service-type ftp
[FTP-server-luser-aaa] authorization-attribute work-directory cfa0:/aaa
# Create a .txt batch command file on the FTP server for automatic software upgrade. In this example, the file name is auto-update.txt. The following is the file content:
return
startup saved-configuration new-config.cfg
boot-loader file soft-version2.bin main
reboot
2. Configure the AC:
# Log in to the FTP server. (The prompt may vary with servers.)
<AC> ftp 2.2.2.2
Trying 2.2.2.2 ...
Press CTRL+K to abort
Connected to 2.2.2.2.
220 WFTPD 2.0 service (by Texas Imperial Software) ready for new user
User(2.2.2.2:(none)):aaa
331 Give me your password, please
Password:
230 Logged in successfully
[ftp]
# Download auto-update.txt from the FTP server.
[ftp] ascii
[ftp] get auto-update.txt
# Download new-config.cfg from the FTP server.
[ftp]get new-config.cfg
# Download soft-version2.bin from the FTP server.
[ftp] binary
[ftp] get soft-version2.bin
[ftp] bye
<AC>
# Change the file extension of auto-update.txt to .bat.
<AC> rename auto-update.txt auto-update.bat
# Use the more command to verify that the file content is correct. (Details not shown.)
# Schedule an automatic software upgrade job for 3 a.m.
<AC> system-view
[AC] job autoupdate
[AC-job-autoupdate] view system
[AC-job-autoupdate] time 1 one-off at 03:00 command execute auto-update.bat
3. After the scheduled job is completed, use the display version command to verify the upgrade. (Details not shown.)
Installing patches
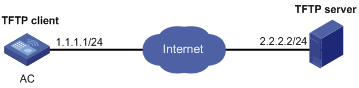
Network requirements
Download a patch file from a TFTP server to fix bugs on the AC in Figure 8. The patch file patch_mpu.bin is saved on the TFTP server. The AC and the TFTP server can reach each other.
Configuration procedure
1. Configure the TFTP server:
# Enable the TFTP server function. (Details not shown.)
# Save the patch file patch_mpu.bin to the working directory on the TFTP server. (Details not shown.)
2. Configure the AC:
# Use the save command to save the running configuration. (Details not shown.)
# Examine the storage medium on the AC for space insufficiency. If the free space is not sufficient for the patches, delete unused files. (Details not shown.)
# Load the patch file patch_mpu.bin from the TFTP server to the root directory of the device's storage medium.
<AC> tftp 2.2.2.2 get patch_mpu.bin
# Install the patches.
<AC> system-view
[AC] patch install cfa0:
Patches will be installed. Continue? [Y/N]:y
Do you want to continue running patches after reboot? [Y/N]:y
Installing patches........
Installation completed, and patches will continue to run after reboot.
Dealing with password loss
|
|
CAUTION: Dealing with console login password loss and user privilege level password loss from BootWare menus is disruptive. |
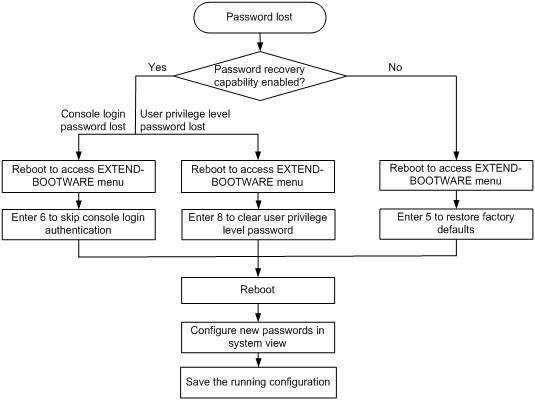
How to deal with console login password loss and user privilege level password loss depends on the state of password recovery capability (see Figure 9). You can use one of the following methods to deal with password loss:
· Dealing with console login password loss when password recovery capability is enabled
· Dealing with user privilege level password loss when password recovery capability is enabled
· Dealing with password loss when password recovery capability is disabled
If password recovery capability is enabled, dealing with password loss does not delete the next-startup configuration file.
If password recovery capability is disabled, dealing with password loss deletes the next-startup configuration file and the device starts up with the factory-default configuration.
Figure 9 shows the process for dealing with password loss events.
Figure 9 Dealing with password loss
Disabling password recovery capability
Password recovery capability controls console user access to the device configuration and SDRAM from BootWare menus.
If password recovery capability is enabled, a console user can access the device configuration without authentication to reconfigure new passwords.
If password recovery capability is disabled, a console user must restore the factory-default configuration before configuring new passwords. Restoring the factory-default configuration deletes the next-startup configuration file.
To enhance system security, disable password recovery capability.
To disable password recovery capability:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Disable password recovery capability. |
undo password-recovery enable |
By default, password recovery capability is enabled. |
Examining the state of password recovery capability
1. Reboot the device. The following information appears:
System is starting...
Press Ctrl+D to access BASIC-BOOTWARE MENU
Booting Normal Extend BootWare.
The Extend BootWare is self-decompressing.......................Done!
****************************************************************************
* *
* H3C WX3010E BootWare, Version 2.01 *
* *
****************************************************************************
Copyright (c) 2004-2017 New H3C Technologies Co., Ltd.
Compiled Date : Jan 28 2013
CPU Type : XLS208
CPU L1 Cache : 32KB
CPU Clock Speed : 750MHz
Memory Type : DDR2 SDRAM
Memory Size : 512MB
Memory Speed : 533MHz
BootWare Size : 512KB
Flash Size : 16MB
cfa0 Size : 999MB
CPLD Version : 002
PCB Version : Ver.A
BootWare Validating...
Press Ctrl+B to enter extended boot menu..
2. Press Enter to access the EXTEND-BOOTWARE menu.
The output displays the EXTEND-BOOTWARE menu, including the state of password recovery capability.
Password recovery capability is enabled.
Note: The current operating device is cfa0
Enter < Storage Device Operation > to select device.
===========================<EXTEND-BOOTWARE MENU>===========================
|<1> Boot System |
|<2> Enter Serial SubMenu |
|<3> Enter Ethernet SubMenu |
|<4> File Control |
|<5> Restore to Factory Default Configuration |
|<6> Skip Current System Configuration |
|<7> BootWare Operation Menu |
|<8> Clear Super Password |
|<9> Storage Device Operation |
|<0> Reboot |
============================================================================
Ctrl+Z: Access EXTEND-ASSISTANT MENU
Ctrl+F: Format File System
Enter your choice(0-9):
Dealing with console login password loss when password recovery capability is enabled
1. Reboot the device to access the EXTEND-BOOTWARE menu, and then enter 6.
Password recovery capability is enabled.
Note: The current operating device is cfa0
Enter < Storage Device Operation > to select device.
===========================<EXTEND-BOOTWARE MENU>===========================
|<1> Boot System |
|<2> Enter Serial SubMenu |
|<3> Enter Ethernet SubMenu |
|<4> File Control |
|<5> Restore to Factory Default Configuration |
|<6> Skip Current System Configuration |
|<7> BootWare Operation Menu |
|<8> Clear Super Password |
|<9> Storage Device Operation |
|<0> Reboot |
============================================================================
Ctrl+Z: Access EXTEND-ASSISTANT MENU
Ctrl+F: Format File System
Enter your choice(0-9): 6
After the configuration skipping flag is set successfully, the following message appears:
Flag Set Success.
2. When the EXTEND-BOOTWARE menu appears again, enter 0 to reboot the device.
The device starts up with empty configuration.
<Sysname> system-view
[Sysname] configuration replace file startup.cfg
Current configuration will be lost, save current configuration? [Y/N]:n
Info: Now replacing the current configuration. Please wait...
Info: Succeeded in replacing current configuration with the file startup.cfg.
4. Configure a new console login password.
For security purposes, the password is always saved in ciphertext to the configuration file, regardless of whether you enter the password in ciphertext or plain text.
<Sysname> system-view
[Sysname] user-interface console 0
[Sysname-ui-console0] authentication-mode password
[Sysname-ui-console0] set authentication password cipher 123456
[Sysname-ui-console0] quit
5. For the settings to take effect at reboot, save the configuration.
[Sysname] save
Dealing with user privilege level password loss when password recovery capability is enabled
1. Reboot the device to access the EXTEND-BOOTWARE menu, and then enter 8.
Password recovery capability is enabled.
Note: The current operating device is cfa0
Enter < Storage Device Operation > to select device.
===========================<EXTEND-BOOTWARE MENU>===========================
|<1> Boot System |
|<2> Enter Serial SubMenu |
|<3> Enter Ethernet SubMenu |
|<4> File Control |
|<5> Restore to Factory Default Configuration |
|<6> Skip Current System Configuration |
|<7> BootWare Operation Menu |
|<8> Clear Super Password |
|<9> Storage Device Operation |
|<0> Reboot |
============================================================================
Ctrl+Z: Access EXTEND-ASSISTANT MENU
Ctrl+F: Format File System
Enter your choice(0-9): 8
The device deletes the user privilege level password configuration commands from the next-startup configuration file. After the operation is completed, the following message appears:
Clear Super Password Success!
2. When the EXTEND-BOOTWARE menu appears again, enter 0 to reboot the device.
The device starts up with the next-startup configuration file.
3. Configure new passwords for user privilege levels.
For security purposes, the password is always saved in ciphertext to the configuration file, regardless of whether you enter the password in ciphertext or plain text.
<Sysname> system-view
[Sysname] super password cipher 123456
4. For the settings to take effect at reboot, save the configuration.
[Sysname] save
Dealing with password loss when password recovery capability is disabled
1. Reboot the device to access the EXTEND-BOOTWARE menu, and then enter 5.
Password recovery capability is disabled.
Note: The current operating device is cfa0
Enter < Storage Device Operation > to select device.
===========================<EXTEND-BOOTWARE MENU>===========================
|<1> Boot System |
|<2> Enter Serial SubMenu |
|<3> Enter Ethernet SubMenu |
|<4> File Control |
|<5> Restore to Factory Default Configuration |
|<6> Skip Current System Configuration |
|<7> BootWare Operation Menu |
|<8> Clear Super Password |
|<9> Storage Device Operation |
|<0> Reboot |
============================================================================
Ctrl+Z: Access EXTEND-ASSISTANT MENU
Ctrl+F: Format File System
Enter your choice(0-9): 5
2. At the prompt for confirmation, enter Y.
The device deletes its next-startup configuration file and restores the factory-default configuration.
The current mode is no password recovery. The configuration files will be
deleted, and the system will start up with factory defaults, Are you sure to
continue?[Y/N]Y
Setting...Done.
3. When the EXTEND-BOOTWARE menu appears again, enter 0 to reboot the device.
The device starts up with the factory-default configuration.
4. Configure a new console login password (see "Configure a new console login password.") or new user privilege level passwords (see "Configure new passwords for user privilege levels.").
5. For the settings to take effect at reboot, save the configuration.
[Sysname] save

