- Table of Contents
-
- 01-Fundamentals Configuration Guide
- 00-Preface
- 01-CLI Configuration
- 02-Login Management Configuration
- 03-FTP and TFTP Configuration
- 04-File System Management Configuration
- 05-Configuration File Management Configuration
- 06-Software Upgrade Configuration
- 07-License Management
- 08-Device Management Configuration
- 09-Automatic Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 02-Login Management Configuration | 620.91 KB |
Logging in through the console/AUX port for the first time
Configuring console login control settings
Configuring none authentication for console login
Configuring password authentication for console login
Configuring scheme authentication for console login
Configuring common console user interface settings (optional)
Configuring none authentication for Telnet login
Configuring password authentication for Telnet login
Configuring scheme authentication for Telnet login
Configuring common VTY user interface settings (optional)
Using the device to log in to a Telnet server
Configuring the SSH server on the device
Using the device to log in to an SSH server
Displaying and maintaining CLI login
Logging in to the Web interface
Displaying and maintaining Web login
Web login configuration examples
HTTP login configuration example
HTTPS login configuration example
Configuring SNMPv1 or SNMPv2c settings
Controlling Telnet users by client SSIDs
Configuring source IP-based Telnet login control
Configuring source/destination IP-based Telnet login control
Configuring source MAC-based Telnet login control
Telnet login control configuration example
Configuring source IP-based SNMP login control
SNMP login control configuration example
Configuring source IP-based Web login control
Web login control configuration example
Login overview
This chapter describes the available login methods and their configuration procedures.
Login methods at a glance
The device supports the FIPS mode that complies with NIST FIPS 140-2 requirements. Support for features, commands, and parameters might differ in FIPS mode and non-FIPS mode. For more information about FIPS mode, see Security Configuration Guide.
Telnet, HTTP, and SNMP are not supported in FIPS mode.
|
Login method |
Default setting and configuration requirements |
|
|
|
||
|
· Logging in through the console/AUX port for the first time |
By default, login through the console or AUX port is enabled, no username or password is required, and the user privilege level is 3. |
|
|
By default, Telnet service is enabled. The default login settings are as follows: · IP address—192.168.0.100/24. (The management interface has no IP address by default.) · Username—admin. · Password—admin. |
||
|
By default, SSH service is disabled. To use SSH service, complete the following configuration tasks: · Enable the SSH server function and configure SSH attributes. · Assign an IP address to a Layer 3 interface and make sure the interface and the SSH client can reach each other. · Enable scheme authentication for VTY login users. · Configure the user privilege level of VTY login users (0 by default). |
||
|
By default, Web login is enabled. The default login settings are as follows: · IP address—192.168.0.100/24. (The management interface has no IP address by default.) · Username—admin. · Password—admin. |
||
|
By default, SNMP login is disabled. To use SNMP service, complete the following configuration tasks: · Assign an IP address to a Layer 3 interface, and make sure the interface and the NMS can reach each other. · Configure SNMP basic parameters. |
||
CLI user interfaces
The device uses user interfaces (also called "lines") to control CLI logins and monitor CLI sessions. You can configure access control settings, including authentication, user privilege, and login redirect on user interfaces. After users are logged in, their actions must be compliant with the settings on the user interfaces assigned to them.
Users are assigned different user interfaces, depending on their login methods, as shown in Table 2.
Table 2 CLI login method and user interface matrix
|
User interface |
Login method |
|
Console user interface |
Console port (EIA/TIA-232 DCE) |
|
AUX user interface |
AUX port (EIA/TIA-232 DTE) |
|
Virtual type terminal (VTY) user interface |
Telnet or SSH |
|
|
NOTE: Support for user interfaces depends on the device model. For more information, see About the H3C Access Controllers Configuration Guides. |
User interface assignment
The device automatically assigns user interfaces to CLI login users, depending on their login methods. Each user interface can be assigned to only one user at a time. If no user interface is available, a CLI login attempt will be rejected. The maximum number of user interfaces varies by device.
For a CLI login, the device always picks the lowest numbered user interface from the idle user interfaces available for the type of login. For example, four VTY user interfaces (0 to 3) are configured, of which VTY 0 and VTY 3 are idle. When a user Telnets to the device, the device assigns VTY 0 to the user and uses the settings on VTY 0 to authenticate and manage the user.
User interface identification
A user interface can be identified by an absolute number, or the interface type and a relative number.
An absolute number uniquely identifies a user interface among all user interfaces. The user interfaces are numbered starting from 0 in the sequence of console, AUX, and VTY user interfaces. You can use the display user-interface command without any parameters to view supported user interfaces and their absolute numbers.
A relative number uniquely identifies a user interface among all user interfaces that are the same type. The number format is user interface type + number. All types of user interfaces are numbered starting from 0 and incrementing by 1. For example, the first VTY user interface is VTY 0.
Logging in to the CLI
You can access the CLI through the console port, AUX port, Telnet, or SSH.
Support for the console port and AUX port depends on the device model. For more information, see About the H3C Access Controllers Configuration Guides.
FIPS compliance
The device supports the FIPS mode that complies with NIST FIPS 140-2 requirements. Support for features, commands, and parameters might differ in FIPS mode and non-FIPS mode. For more information about FIPS mode, see Security Configuration Guide.
Telnet is not supported in FIPS mode.
Logging in through the console/AUX port for the first time
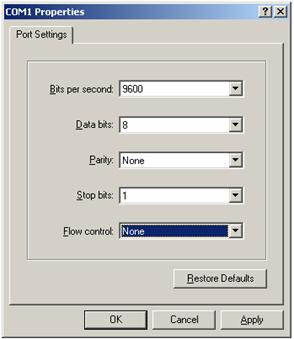
To log in through the console port, make sure the console terminal has a terminal emulation program (for example, HyperTerminal in Windows XP). In addition, the port settings of the terminal emulation program must be the same as the default settings of the console port in Table 3.
Table 3 Default console port properties
|
Parameter |
Default |
|
Bits per second |
9600 bps |
|
Flow control |
None |
|
Parity |
None |
|
Stop bits |
1 |
|
Data bits |
8 |
To log in through the console port from a console terminal (for example, a PC):
1. Connect the DB-9 female connector of the console cable to the serial port of the PC.
2. Connect the RJ-45 connector of the console cable to the console port of the device.
|
|
IMPORTANT: · Identify the mark on the console port and make sure you are connecting to the correct port. · The serial ports on PCs do not support hot swapping. If the switch has been powered on, always connect the console cable to the PC before connecting it to the switch, and when you disconnect the cable, first disconnect it from the switch. |
Figure 1 Connecting a terminal to the console port

3. If the PC is off, turn on the PC.
4. Launch the terminal emulation program and configure the communication properties on the PC.
Figure 2 through Figure 4 show the configuration procedure on Windows XP HyperTerminal. Make sure the port settings are the same as those listed in Table 3.
On Windows Server 2003, add the HyperTerminal program first, and then log in to and manage the device as described in this document. On Windows Server 2008, Windows 7, Windows Vista, or some other operating system, obtain a third-party terminal control program first, and then follow the user guide or online help to log in to the device.
Figure 2 Naming the connection
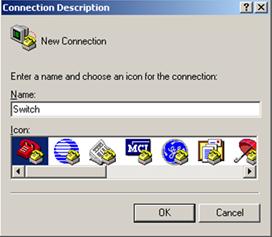
Figure 3 Specifying the serial port used to establish the connection
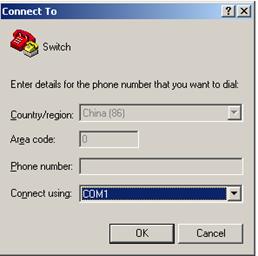
Figure 4 Setting the properties of the serial port
5. Power on the device and press Enter at the prompt.

6. At the default user view prompt <H3C>, enter commands to configure the device or view the running status of the device. To get help, enter ?.
Configuring console login control settings
This section describes how to configure console login control settings. The procedures for configuring AUX login control settings are similar.
The following authentication modes are available for controlling console logins:
· None—Requires no authentication. This mode is insecure, and is not supported in FIPS mode.
· Password—Requires password authentication. This mode is not supported in FIPS mode.
· Scheme—Uses the AAA module to provide local or remote console login authentication. You must provide a username and password for accessing the CLI. If the username or password configured on a remote server was lost, contact the server administrator for help.
By default, console login does not require authentication. Any user can log in through the console port without authentication and have user privilege level 3. To improve device security, configure the password or scheme authentication mode immediately after you log in to the device for the first time.
Table 4 Configuration required for different console login authentication modes
|
Authentication mode |
Configuration tasks |
Reference |
|
None |
Set the authentication mode to none for the console user interface. |
|
|
Password |
Enable password authentication on the console user interface. Set a password. |
|
|
Scheme |
Enable scheme authentication on the console user interface. Configure local or remote authentication settings. To configure local authentication: 1. Configure a local user and specify the password on the device. 2. Configure the device to use local authentication. To configure remote authentication: 1. Configure the RADIUS or HWTACACS scheme on the device. 2. Configure the username and password on the AAA server. 3. Configure the device to use the scheme for user authentication. |
Configuring none authentication for console login
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter console user interface view. |
user-interface console 0 |
N/A |
|
3. Enable none authentication mode. |
authentication-mode none |
By default, you can log in to the device through the console port without authentication and have user privilege level 3. |
|
4. Configure common settings for console login. |
See "Configuring common console user interface settings (optional)." |
Optional. |
The next time you attempt to log in through the console port, you do not need to provide any username or password.
Configuring password authentication for console login
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter console user interface view. |
user-interface console 0 |
N/A |
|
3. Enable password authentication. |
authentication-mode password |
By default, you can log in to the device through the console port without authentication and have user privilege level 3 after login. |
|
4. Set a password. |
set authentication password [ hash ] { cipher | simple } password |
By default, no password is set. |
|
5. Configure common settings for console login. |
See "Configuring common console user interface settings (optional)." |
Optional. |
Configuring scheme authentication for console login
When scheme authentication is used, you can choose to configure the command authorization and command accounting functions.
If command authorization is enabled, a command is available only if the user has the commensurate user privilege level and is authorized to use the command by the AAA scheme.
Command accounting allows the HWTACACS server to record all commands executed by users, regardless of command execution results. This function helps control and monitor user behaviors on the device. If command accounting is enabled and command authorization is not enabled, every executed command is recorded on the HWTACACS server. If both command accounting and command authorization are enabled, only the authorized and executed commands are recorded on the HWTACACS server.
Follow these guidelines when you configure scheme authentication for console login:
· To make the command authorization or command accounting function take effect, apply an HWTACACS scheme to the intended ISP domain. This scheme must specify the IP address of the authorization server and other authorization parameters.
· If the local authentication scheme is used, use the authorization-attribute level level command in local user view to set the user privilege level on the device.
· If a RADIUS or HWTACACS authentication scheme is used, set the user privilege level on the RADIUS or HWTACACS server.
To configure scheme authentication for console login:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter console user interface view. |
user-interface console 0 |
N/A |
|
3. Enable scheme authentication. |
authentication-mode scheme |
Whether local, RADIUS, or HWTACACS authentication is adopted depends on the configured AAA scheme. By default, console login users are not authenticated. |
|
4. Enable command authorization. |
command authorization |
Optional. By default, command authorization is disabled. The commands available for a user only depend on the user privilege level. |
|
5. Enable command accounting. |
command accounting |
Optional. By default, command accounting is disabled. The accounting server does not record the commands executed by users. |
|
6. Exit to system view. |
quit |
N/A |
|
7. Apply an AAA authentication scheme to the intended domain. |
a. Enter ISP domain view: b. Apply an AAA scheme to the domain: c. Exit to system view: |
Optional. By default, local authentication is used. For local authentication, configure local user accounts. For RADIUS or HWTACACS authentication, configure the RADIUS or HWTACACS scheme on the device and configure authentication settings (including the username and password) on the server. For more information about AAA configuration, see Security Configuration Guide. |
|
8. Create a local user and enter local user view. |
local-user user-name |
N/A |
|
9. Set an authentication password for the local user. |
password [ [ hash ] { cipher | simple } password ] |
By default, no password is set. |
|
10. Specifies a command level of the local user. |
authorization-attribute level level |
Optional. By default, the command level is 0. |
|
11. Specify terminal service for the local user. |
service-type terminal |
By default, no service type is specified. |
|
12. Configure common settings for console login. |
See "Configuring common console user interface settings (optional)." |
Optional. |
Configuring common console user interface settings (optional)
Some common settings configured for a console user interface take effect immediately and can interrupt the console login session. To save you the trouble of repeated re-logins, use a login method different from console login to log in to the device before you change console user interface settings.
After the configuration is complete, change the terminal settings on the configuration terminal and make sure they are the same as the settings on the device.
To configure common settings for a console user interface:
|
Step |
Command |
|
|
system-view |
N/A |
|
|
user-interface console 0 |
N/A |
|
|
3. Set the baud rate. |
speed speed-value |
By default, the baud rate is 9600 bps. |
|
4. Specify the parity check mode. |
parity { even | none | odd } |
By default, the parity check mode is none, and no parity check is performed. |
|
5. Specify the number of stop bits. |
stopbits { 1 | 2 } |
The default is 1. Stop bits indicate the end of a character. The more the stop bits, the slower the transmission. |
|
6. Specify the number of data bits in each character. |
databits { 7 | 8 } |
The default is 8. The setting depends on the character coding type. For example, you can set it to 7 if standard ASCII characters are to be sent, and set it to 8 if extended ASCII characters are to be sent. |
|
7. Define the shortcut key for starting a terminal session. |
activation-key character |
|
|
8. Define a shortcut key for terminating tasks. |
escape-key { default | character } |
|
|
9. Specify the terminal display type. |
terminal type { ansi | vt100 } |
By default, the terminal display type is ANSI. The device supports two types of terminal display: ANSI and VT100. H3C recommends setting the display type of both the device and the terminal to VT100. If the device and the client use different display types (for example, HyperTerminal or Telnet terminal) or both are set to ANSI, when the total number of characters of the currently edited command line exceeds 80, an anomaly such as cursor corruption or abnormal display of the terminal display might occur on the client. |
|
10. Configure the user privilege level for login users. |
user privilege level level |
By default, the default command level is 3 for the console user interface. |
|
11. Set the maximum number of lines to be displayed on a screen. |
screen-length screen-length |
By default, a screen displays 24 lines at most. |
|
12. Set the size of command history buffer. |
history-command max-size value |
|
|
13. Set the idle-timeout timer. |
idle-timeout minutes [ seconds ] |
The default idle-timeout is 10 minutes. The system automatically terminates the user's connection if there is no information interaction between the device and the user within the idle-timeout time. Setting idle-timeout to 0 disables the idle-timeout function. |
Logging in through Telnet
You can Telnet to the device for remote management, or use the device as a Telnet client to Telnet to other devices, as shown in Figure 6.
|
|
NOTE: Telnet is not supported in FIPS mode. |

Table 5 shows the Telnet server and client configuration required for a successful Telnet login.
Table 5 Telnet server and Telnet client configuration requirements
|
Device role |
Requirements |
|
Telnet server |
Enable Telnet server. (Enabled by default.) Configure the IP address of a Layer 3 interface, and make sure the Telnet server and client can reach each other. Configure the authentication mode and other settings. |
|
Telnet client |
Run the Telnet client program. Obtain the IP address of the Layer 3 interface on the server. |
To control Telnet access to the device operating as a Telnet server, configure login authentication and user privilege levels for Telnet users.
By default, scheme authentication applies to Telnet login.
The following are authentication modes available for controlling Telnet logins:
· None—Requires no authentication. This mode is insecure.
· Password—Requires a password for accessing the CLI. If your password was lost, log in to the device through the console port to re-set the password.
· Scheme—Uses the AAA module to provide local or remote authentication. You must provide a username and password for accessing the CLI. If the password configured in the local user database was lost, log in to the device through the console port and re-set the password. If the username or password configured on a remote server was lost, contact the server administrator for help.
Table 6 Configuration required for different Telnet login authentication modes
|
Authentication mode |
Configuration tasks |
Reference |
|
None |
Set the authentication mode to none for the VTY user interface. |
|
|
Password |
Enable password authentication on the VTY user interface. Set a password. |
|
|
Scheme |
Enable scheme authentication on the VTY user interface. Configure local or remote authentication settings. To configure local authentication: 1. Configure a local user and specify the password. 2. Configure the device to use local authentication. To configure remote authentication: 1. Configure the RADIUS or HWTACACS scheme on the device. 2. Configure the username and password on the AAA server. 3. Configure the device to use the scheme for user authentication. |
Configuring none authentication for Telnet login
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable Telnet server. |
telnet server enable |
Optional. By default, the Telnet server function is enabled. |
|
3. Enter one or multiple VTY user interface views. |
user-interface vty first-number [ last-number ] |
N/A |
|
4. Enable none authentication mode. |
authentication-mode none |
By default, password authentication is enabled for VTY user interfaces. |
|
5. Configure the command level for login users on the current user interfaces. |
user privilege level level |
By default, the default command level is 0 for VTY user interfaces. |
|
6. Configure common settings for the VTY user interfaces. |
See "Configuring common VTY user interface settings (optional)." |
Optional. |
The next time you attempt to Telnet to the device, you do not need to provide any username or password, as shown in the following example:
******************************************************************************
* Copyright (c) 2004-2017 New H3C Technologies Co., Ltd. All rights reserved.*
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
<H3C>
If the maximum number of login users has been reached, your login attempt fails and the device displays the "All user lines are used, please try later!" message.
Configuring password authentication for Telnet login
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable Telnet server. |
telnet server enable |
Optional. By default, the Telnet server function is enabled. |
|
3. Enter one or multiple VTY user interface views. |
user-interface vty first-number [ last-number ] |
N/A |
|
4. Enable password authentication. |
authentication-mode password |
By default, password authentication is enabled for VTY user interfaces. |
|
5. Set a password. |
set authentication password [ hash ] { cipher | simple } password |
By default, no password is set. |
|
6. Configure the user privilege level for login users. |
user privilege level level |
The default level is 0. |
|
7. Configure common settings for VTY user interfaces. |
See "Configuring common VTY user interface settings (optional)." |
Optional. |
The next time you attempt to Telnet to the device, you must provide the configured login password, as shown in the following example:
******************************************************************************
* Copyright (c) 2004-2017 New H3C Technologies Co., Ltd. All rights reserved.*
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
Login authentication
Password:
<H3C>
If the maximum number of login users has been reached, your login attempt fails and the device displays the "All user lines are used, please try later!" message.
Configuring scheme authentication for Telnet login
When scheme authentication is used, you can choose to configure the command authorization and command accounting functions.
If command authorization is enabled, a command is available only if the user has the commensurate user privilege level and is authorized to use the command by the AAA scheme.
Command accounting allows the HWTACACS server to record all commands executed by users, regardless of command execution results. This function helps control and monitor user behaviors on the device. If command accounting is enabled and command authorization is not enabled, every executed command is recorded on the HWTACACS server. If both command accounting and command authorization are enabled, only the authorized and executed commands are recorded on the HWTACACS server.
Follow these guidelines when you configure scheme authentication for Telnet login:
· To make the command authorization or command accounting function take effect, apply an HWTACACS scheme to the intended ISP domain. This scheme must specify the IP address of the authorization server and other authorization parameters.
· If the local authentication scheme is used, use the authorization-attribute level level command in local user view to set the user privilege level on the device.
· If a RADIUS or HWTACACS authentication scheme is used, set the user privilege level on the RADIUS or HWTACACS server.
To configure scheme authentication for Telnet login:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable Telnet server. |
telnet server enable |
Optional. By default, the Telnet server function is enabled. |
|
3. Enter one or multiple VTY user interface views. |
user-interface vty first-number [ last-number ] |
N/A |
|
4. Enable scheme authentication. |
authentication-mode scheme |
Whether local, RADIUS, or HWTACACS authentication is adopted depends on the configured AAA scheme. By default, local authentication is adopted. |
|
5. Enable command authorization. |
command authorization |
Optional. By default, command authorization is disabled. The commands available for a user only depend on the user privilege level. |
|
6. Enable command accounting. |
command accounting |
Optional. By default, command accounting is disabled. The accounting server does not record the commands executed by users. |
|
7. Exit to system view. |
quit |
N/A |
|
8. Apply an AAA authentication scheme to the intended domain. |
a. Enter ISP domain view: b. Apply an AAA scheme to the domain: c. Exit to system view: |
Optional. By default, local authentication is used. For local authentication, configure local user accounts. For RADIUS or HWTACACS authentication, configure the RADIUS or HWTACACS scheme on the device and configure authentication settings (including the username and password) on the server. For more information about AAA configuration, see Security Configuration Guide. |
|
9. Create a local user and enter local user view. |
local-user user-name |
N/A |
|
10. Set a password. |
password [ [ hash ] { cipher | simple } password ] |
By default, no password is set. |
|
11. Specify the command level of the local user. |
authorization-attribute level level |
Optional. By default, the command level is 0. |
|
12. Specify Telnet service for the local user. |
service-type telnet |
By default, no service type is specified. |
|
13. Exit to system view. |
quit |
N/A |
|
14. Configure common settings for VTY user interfaces. |
See "Configuring common VTY user interface settings (optional)." |
Optional. |
The next time you attempt to Telnet to the CLI, you must provide the configured login username and password, as shown in the following example:
******************************************************************************
* Copyright (c) 2004-2017 New H3C Technologies Co., Ltd. All rights reserved.*
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
Login authentication
Username:admin
Password:
<H3C>
If you are required to pass a second authentication, you must also provide the correct password to access the CLI. If the maximum number of login users has been reached, your login attempt fails and the device displays the "All user lines are used, please try later!" message.
Configuring common VTY user interface settings (optional)
You might be unable to access the CLI through a VTY user interface after configuring the auto-execute command command on it. Before you configure the command and save the configuration, make sure you can access the CLI through a different user interface.
To configure common settings for VTY user interfaces:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter one or multiple VTY user interface views. |
user-interface vty first-number [ last-number ] |
N/A |
|
3. Enable the terminal service. |
shell |
Optional. By default, terminal service is enabled. |
|
4. Enable the user interfaces to support Telnet, SSH, or both of them. |
protocol inbound { all | ssh | telnet } |
Optional. By default, both Telnet and SSH are supported. The configuration takes effect the next time you log in. |
|
5. Define a shortcut key for terminating tasks. |
escape-key { default | character } |
Optional. By default, pressing Ctrl+C terminates a task. |
|
6. Configure the type of terminal display. |
terminal type { ansi | vt100 } |
Optional. By default, the terminal display type is ANSI. |
|
7. Set the maximum number of lines to be displayed on a screen. |
screen-length screen-length |
Optional. By default, up to 24 lines is displayed on a screen. A value of 0 disables the function. |
|
8. Set the size of command history buffer. |
history-command max-size value |
Optional. By default, the buffer saves 10 history commands. |
|
9. Set the idle-timeout timer. |
idle-timeout minutes [ seconds ] |
Optional. The default idle-timeout is 10 minutes for all user interfaces. The system automatically terminates the user's connection if there is no information interaction between the device and the user within the timeout time. Setting idle-timeout to 0 disables the timer. |
|
10. Specify a command to be automatically executed when a user logs in to the user interfaces. |
auto-execute command command |
Optional. By default, no automatically executed command is specified. The command auto-execute function is typically used for redirecting a Telnet user to a specific host. After executing the specified command and performing the incurred task, the system automatically disconnects the Telnet session. |
Using the device to log in to a Telnet server
You can use the device as a Telnet client to log in to a Telnet server. If the server is located in a different subnet than the device, make sure the two devices have routes to reach each other.
Figure 7 Telnetting from the device to a Telnet server
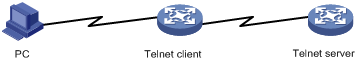
To use the device to log in to a Telnet server:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify the source IPv4 address or source interface for outgoing Telnet packets. |
telnet client source { interface interface-type interface-number | ip ip-address } |
Optional. By default, no source IPv4 address or source interface is specified. The device automatically selects a source IPv4 address. |
|
3. Exit to user view. |
quit |
N/A |
|
4. Use the device to log in to a Telnet server. |
· Log in to an IPv4 Telnet server: · Log in to an IPv6 Telnet server: |
Use either command. |
Logging in through SSH
SSH offers a secure approach to remote login. By providing encryption and strong authentication, it protects devices against attacks such as IP spoofing and plain text password interception. You can use an SSH client to log in to the device operating as an SSH server for remote management, as shown in Figure 8. You can also use the device as an SSH client to log in to an SSH server.

Table 7 shows the SSH server and client configuration required for a successful SSH login.
Table 7 SSH server and client requirements
|
Device role |
Requirements |
|
SSH server |
Assign an IP address to a Layer 3 interface, and make sure the interface and the client can reach each other. Configure the authentication mode and other settings. |
|
SSH client |
If a host operates as an SSH client, run the SSH client program on the host. Obtain the IP address of the Layer 3 interface on the server. |
To control SSH access to the device operating as an SSH server, configure authentication and user privilege level for SSH users. By default, password authentication is adopted for SSH login, but no login password is configured. To allow SSH access to the device after you enable the SSH server, you must configure a password.
Configuring the SSH server on the device
When scheme authentication is used, you can choose to configure the command authorization and command accounting functions.
If command authorization is enabled, a command is available only if the user has the commensurate user privilege level and is authorized by the AAA scheme to use the command.
Command accounting allows the HWTACACS server to record all commands executed by users, regardless of command execution results. This function helps control and monitor user behaviors on the device. If command accounting is enabled and command authorization is not enabled, every executed command is recorded on the HWTACACS server. If both command accounting and command authorization are enabled, only the authorized and executed commands are recorded on the HWTACACS server.
Follow these guidelines when you configure the SSH server:
· To make the command authorization or command accounting function take effect, apply an HWTACACS scheme to the intended ISP domain. This scheme must specify the IP address of the authorization server and other authorization parameters.
· If the local authentication scheme is used, use the authorization-attribute level level command in local user view to set the user privilege level on the device.
· If a RADIUS or HWTACACS authentication scheme is used, set the user privilege level on the RADIUS or HWTACACS server.
The SSH client authentication method is password in this configuration procedure. For more information about SSH and publickey authentication, see Security Configuration Guide.
To configure the SSH server on the device:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create local key pairs. |
public-key local create { dsa | ecdsa | rsa } |
By default, no local key pairs are created. |
|
3. Enable SSH server. |
ssh server enable |
By default, SSH server is disabled. |
|
4. Enter one or multiple VTY user interface views. |
user-interface vty first-number [ last-number ] |
N/A |
|
5. Enable scheme authentication. |
authentication-mode scheme |
By default, password authentication is enabled on VTY user interfaces. |
|
6. Enable the user interfaces to support Telnet, SSH, or both. |
protocol inbound { all | ssh | telnet } |
Optional. In non-FIPS mode, Telnet and SSH are supported by default. In FIPS mode, SSH is supported by default, and the telnet keyword is not supported. |
|
7. Enable command authorization. |
command authorization |
Optional. By default, command authorization is disabled. The commands available for a user only depend on the user privilege level. |
|
8. Enable command accounting. |
command accounting |
Optional. By default, command accounting is disabled. The accounting server does not record the commands executed by users. |
|
9. Exit to system view. |
quit |
N/A |
|
10. Apply an AAA authentication scheme to the intended domain. |
a. Enter the ISP domain view: b. Apply the specified AAA scheme to the domain: c. Exit to system view: |
Optional. For local authentication, configure local user accounts. For RADIUS or HWTACACS authentication, configure the RADIUS or HWTACACS scheme on the device and configure authentication settings (including the username and password) on the server. For more information about AAA configuration, see Security Configuration Guide. |
|
11. Create a local user and enter local user view. |
local-user user-name |
N/A |
|
12. Set a password for the local user. |
password [ [ hash ] { cipher | simple } password ] |
By default, no password is set. |
|
13. Specify the command level of the user. |
authorization-attribute level level |
Optional. By default, the command level is 0. |
|
14. Specify SSH service for the user. |
service-type ssh |
By default, no service type is specified. |
|
15. Exit to system view. |
quit |
N/A |
|
16. Create an SSH user, and specify the authentication mode for the SSH user. |
ssh user username service-type stelnet authentication-type { password | { any | password-publickey | publickey } assign publickey keyname } |
N/A |
|
17. Configure common settings for VTY user interfaces. |
See "Configuring common VTY user interface settings (optional)." |
Optional. |
Using the device to log in to an SSH server
You can use the device as an SSH client to log in to an SSH server. If the server is located in a different subnet than the device, make sure the two devices have routes to reach each other.
Figure 9 Logging in to an SSH client from the device
Perform the following tasks in user view:
|
Task |
Command |
Remarks |
|
Log in to an IPv4 SSH server. |
ssh2 server |
The server argument represents the IPv4 address or host name of the server. |
|
Log in to an IPv6 SSH server. |
ssh2 ipv6 server |
The server argument represents the IPv6 address or host name of the server. |
To work with the SSH server, you might need to configure the SSH client. For information about configuring the SSH client, see Security Configuration Guide.
Displaying and maintaining CLI login
|
Task |
Command |
Remarks |
|
Display information about the user interfaces that are being used. |
display users [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display information about all user interfaces the device supports. |
display users all [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display user interface information. |
display user-interface [ num1 | { aux | console | vty } num2 ] [ summary ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. Support for the console and aux keywords depends on the device model. For more information, see About the H3C Access Controllers Command References. |
|
Display the configuration of the device when it serves as a Telnet client. |
display telnet client configuration [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Release a user interface. |
free user-interface { num1 | { aux | console | vty } num2 } |
Available in user view. Multiple users can log in to the device to simultaneously configure the device. When necessary, you can execute this command to release some connections. You cannot use this command to release the connection you are using. Support for the console and aux keywords depends on the device model. For more information, see About the H3C Access Controllers Command References. |
|
Lock the current user interface. |
lock |
Available in user view. By default, the system does not automatically lock a user interface. |
|
Send messages to user interfaces. |
send { all | num1 | { aux | console | vty } num2 } |
Available in user view. Support for the console and aux keywords depends on the device model. For more information, see About the H3C Access Controllers Command References. |
Logging in to the Web interface
The device provides one or more built-in Web servers for you to configure the device and its cards through a Web browser. See Table 8.
|
Hardware |
Web interfaces |
|
AC modules (installed in a switch) |
|
|
LSQM1WCMD0 LSRM1WCM3A1 LSUM3WCMD0 EWPXM1WCME0 LSUM1WCME0 |
Provides only one Web server. Using the login parameters provided or configured in this chapter, you log in to the Web interface of the AC module. |
|
Wireless switches |
|
|
WX3024E WX3010E |
Provides two Web servers: one by the access controller engine and one by the switching engine. Using the login parameters provided or configured in this chapter, you log in to the Web interface of the access controller engine. For information about how to log in to the Web interface of the switching engine, see H3C WX3000E Unified Switches Switching Engine Configuration Guide. |
|
ACs |
|
|
WX6103 |
Provides two Web servers: one by the MPU and one by the switching engine. Using the login parameters provided or configured in this chapter, you log in to the Web interface of the MPU. For information about how to log in to the Web interface of the switching engine, see H3C WX6103 Access Controller Switch Interface Board Configuration Guide. |
|
WX5002V2 WX5004 WX3510E WX3540E WX5510E |
You log in to the Web interfaces of the AC. |
|
WX5540E |
You log in to the Web interfaces of the AC. For information about how to log in to the Web interface of the switching engine, see H3C WX5540E Access Controller Switching Engine Configuration Guide. |
Web login is enabled by default. The default login settings are as follows:
· IP address—192.168.0.100/24. (The management interface has no IP address by default.)
· Username—admin.
· Password—admin.
The device supports HTTP 1.0 and HTTPS for transferring webpage data across the Internet.
HTTPS uses SSL to encrypt data between the client and the server for data integrity and security, and is more secure than HTTP. You can define a certificate attribute-based access control policy to allow only legal clients to access the device.
HTTP login and HTTPS login are separate login methods. To use HTTPS login, you do not need to configure HTTP login.
Table 9 shows the basic Web login configuration requirements.
Table 9 Basic Web login configuration requirements
|
Object |
Requirements |
|
Device |
Assign an IP address to a Layer 3 interface. Configure routes to make sure the interface and the PC can reach each other. Perform either or both of the following tasks: |
|
PC |
Install a Web browser. Obtain the IP address of the device's Layer 3 interface. |
FIPS compliance
The device supports the FIPS mode that complies with NIST FIPS 140-2 requirements. Support for features, commands, and parameters might differ in FIPS mode and non-FIPS mode. For more information about FIPS mode, see Security Configuration Guide.
HTTP is not supported in FIPS mode.
Configuring HTTP login
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the HTTP service. |
ip http enable |
By default, HTTP service is enabled. |
|
3. Configure the HTTP service port number. |
ip http port port-number |
Optional. The default HTTP service port is 80. If you execute the command multiple times, the most recent configuration takes effect. |
|
4. Associate the HTTP service with an ACL. |
ip http acl acl-number |
Optional. By default, the HTTP service is not associated with any ACL. Associating the HTTP service with an ACL enables the device to allow only clients permitted by the ACL to access the device. |
|
5. Set the Web connection timeout time. |
web idle-timeout minutes |
Optional. |
|
6. Set the size of the buffer for Web login logging. |
web logbuffer size pieces |
Optional. |
|
7. Create a local user and enter local user view. |
local-user user-name |
N/A |
|
8. Configure a password for the local user. |
password [ [ hash ] { cipher | simple } password ] |
By default, no password is configured for the local user. |
|
9. Specify the command level of the local user. |
authorization-attribute level level |
No command level is configured for the local user. |
|
10. Specify the Telnet service type for the local user. |
service-type web |
By default, no service type is configured for the local user. |
|
11. Exit to system view. |
quit |
N/A |
|
12. Create a VLAN interface and enter its view. |
interface vlan-interface vlan-interface-id |
If the VLAN interface already exists, the command enters its view. You could replace this VLAN interface with any other Layer 3 interface as appropriate. |
|
13. Assign an IP address and subnet mask to the interface. |
ip address ip-address { mask | mask-length } |
By default, the IP address of VLAN-interface 1 is 192.168.0.100. |
Configuring HTTPS login
The device supports the following HTTPS login modes:
· Simplified mode—To make the device operate in this mode, you only need to enable HTTPS service on the device. The device will use a self-signed certificate (a certificate that is generated and signed by the device itself, rather than a CA) and the default SSL settings. This mode is simple to configure but has potential security risks.
· Secure mode—To make the device operate in this mode, you must enable HTTPS service on the device, specify an SSL server policy for the service, and configure PKI domain-related parameters. This mode is more complicated to configure but provides higher security.
For more information about SSL and PKI, see Security Configuration Guide.
To configure HTTPS login:
|
Step |
Command |
Remarks |
|
1. Specify a fixed verification code for Web login. |
web captcha verification-code |
Optional. By default, a Web user must enter the verification code indicated on the login page to log in. This command is available in user view. |
|
2. Enter system view. |
system-view |
N/A |
|
3. Associate the HTTPS service with an SSL server policy. |
ip https ssl-server-policy policy-name |
Optional. By default, the HTTPS service is not associated with any SSL server policy, and the device uses a self-signed certificate for authentication. If you disable the HTTPS service, the system automatically de-associates the HTTPS service from the SSL service policy. Before re-enabling the HTTPS service, associate the HTTPS service with an SSL server policy first. If the HTTPS service has been enabled, any changes to the SSL server policy associated with it do not take effect. |
|
4. Enable the HTTPS service. |
ip https enable |
By default, HTTPS is disabled. Enabling the HTTPS service triggers an SSL handshake negotiation process. During the process, if the local certificate of the device exists, the SSL negotiation succeeds, and the HTTPS service can be started properly. If no local certificate exists, a certificate application process will be triggered by the SSL negotiation. Because the application process takes much time, the SSL negotiation often fails, and the HTTPS service cannot be started normally. In that case, execute the ip https enable command multiple times to start the HTTPS service. |
|
5. Associate the HTTPS service with a certificate attribute-based access control policy. |
ip https certificate access-control-policy policy-name |
Optional. By default, the HTTPS service is not associated with any certificate-based attribute access control policy. Associating the HTTPS service with a certificate-based attribute access control policy enables the device to control the access rights of clients. You must configure the client-verify enable command in the associated SSL server policy. Otherwise, no clients can log in to the device. The associated SSL server policy must contain at least one permit rule. Otherwise, no clients can log in to the device. For more information about certificate attribute-based access control policies, see Security Configuration Guide. |
|
6. Specify the HTTPS service port number. |
ip https port port-number |
Optional. The default HTTPS service port is 443. |
|
7. Associate the HTTPS service with an ACL. |
ip https acl acl-number |
By default, the HTTPS service is not associated with any ACL. Associating the HTTPS service with an ACL enables the device to allow only clients permitted by the ACL to access the device. |
|
8. Specify the authentication mode for users trying to log in to the device through HTTPS. |
web https-authorization mode { auto | manual } |
Optional. By default, a user must enter the correct username and password to log in through HTTPS. When the auto mode is enabled: · If the user's PKI certificate is correct and not expired, the CN field in the certificate is used as the username to perform AAA authentication. If the authentication succeeds, the user automatically enters the Web interface of the device. · If the user's PKI certificate is correct and not expired, but the AAA authentication fails, the device shows the Web login page. The user can log in to the device after entering correct username and password. |
|
9. Set the Web user connection timeout time. |
web idle-timeout minutes |
Optional. |
|
10. Set the size of the buffer for Web login logging. |
web logbuffer size pieces |
Optional. |
|
11. Create a local user and enter local user view. |
local-user user-name |
N/A |
|
12. Configure a password for the local user. |
password [ [ hash ] { cipher | simple } password ] |
By default, no password is configured for the local user. |
|
13. Specify the command level of the local user. |
authorization-attribute level level |
By default, no command level is configured for the local user. |
|
14. Specify the Web service type for the local user. |
service-type web |
By default, no service type is configured for the local user. |
|
15. Exit to system view. |
quit |
N/A |
|
16. Create a VLAN interface and enter its view. |
interface vlan-interface vlan-interface-id |
If the VLAN interface already exists, the command enters its view. You could replace this VLAN interface with any other Layer 3 interface as appropriate. |
|
17. Assign an IP address and subnet mask to the interface. |
ip address ip-address { mask | mask-length } |
By default, the IP address of VLAN-interface 1 is 192.168.0.100. |
Displaying and maintaining Web login
|
Task |
Command |
Remarks |
|
Display information about Web users. |
display web users [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display HTTP state information. |
display ip http [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display HTTPS state information. |
display ip https [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
Web login configuration examples
HTTP login configuration example
Network requirements
As shown in Figure 10, configure the AC so the PC can log in to the AC's Web interface through HTTP.
Configuration procedure
1. Configure the AC:
# Create VLAN 999, and add the interface connected to the PC to VLAN 999.
<AC> system-view
[AC] vlan 999
[AC-vlan999] port gigabitethernet 1/0/1
[AC-vlan999] quit
# Assign IP address 192.168.1.58/24 to VLAN-interface 999.
[AC] interface vlan-interface 999
[AC-VLAN-interface999] ip address 192.168.1.58 255.255.255.0
[AC-VLAN-interface999] quit
# Create a local user named admin, and set the password to admin for the user. Specify the Web service type for the local user, and set the command level to 3 for this user.
[AC] local-user admin
[AC-luser-admin] service-type web
[AC-luser-admin] authorization-attribute level 3
[AC-luser-admin] password simple admin
2. Log in from the PC:
# On the PC, open the Web browser. Enter the IP address of the device in the address bar. The Web login page appears, as shown in Figure 11.
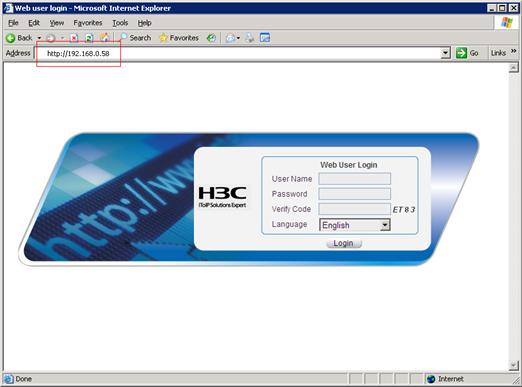
# Type the user name, password, and verify code. Then, select English, and click Login. The homepage appears. After login, you can configure the AC settings through the Web interface.
HTTPS login configuration example
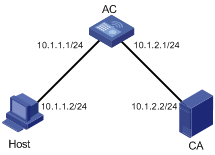
Network requirements
As shown in Figure 12, to prevent unauthorized users from accessing the AC's Web interface, configure the AC as the HTTPS server and the host as the HTTPS client, and request a certificate for each of them.
Configuration procedure
In this example, the CA is named new-ca, runs Windows Server, and is installed with the SCEP add-on.
Before performing the following configuration, make sure that the AC, host, and CA can reach each other.
1. Configure the AC (the HTTPS server):
# Configure a PKI entity, and set the common name to http-server1 and the FQDN to ssl.security.com.
<AC> system-view
[AC] pki entity en
[AC-pki-entity-en] common-name http-server1
[AC-pki-entity-en] fqdn ssl.security.com
[AC-pki-entity-en] quit
# Create a PKI domain, specify the trusted CA as new-ca, the URL of the server for certificate request as http://10.1.2.2/certsrv/mscep/mscep.dll, authority for certificate request as RA, and the entity for certificate request as en.
[AC] pki domain 1
[AC-pki-domain-1] ca identifier new-ca
[AC-pki-domain-1] certificate request url http://10.1.2.2/certsrv/mscep/mscep.dll
[AC-pki-domain-1] certificate request from ra
[AC-pki-domain-1] certificate request entity en
[AC-pki-domain-1] quit
# Create RSA local key pairs.
[AC] public-key local create rsa
# Retrieve the CA certificate from the certificate issuing server.
[AC] pki retrieval-certificate ca domain 1
# Request a local certificate from a CA through SCEP for the AC.
[AC] pki request-certificate domain 1
# Create an SSL server policy myssl, specify PKI domain 1 for the SSL server policy, and enable certificate-based SSL client authentication.
[AC] ssl server-policy myssl
[AC-ssl-server-policy-myssl] pki-domain 1
[AC-ssl-server-policy-myssl] client-verify enable
[AC-ssl-server-policy-myssl] quit
# Create a certificate attribute group mygroup1, and configure a certificate attribute rule, specifying that the distinguished name in the subject name includes the string new-ca.
[AC] pki certificate attribute-group mygroup1
[AC-pki-cert-attribute-group-mygroup1] attribute 1 issuer-name dn ctn new-ca
[AC-pki-cert-attribute-group-mygroup1] quit
# Create a certificate attribute-based access control policy myacp. Configure a certificate attribute-based access control rule, specifying that a certificate is considered valid when it matches an attribute rule in certificate attribute group myacp.
[AC] pki certificate access-control-policy myacp
[AC-pki-cert-acp-myacp] rule 1 permit mygroup1
[AC-pki-cert-acp-myacp] quit
# Associate the HTTPS service with SSL server policy myssl.
[AC] ip https ssl-server-policy myssl
# Associate the HTTPS service with certificate attribute-based access control policy myacp.
[AC] ip https certificate access-control-policy myacp
# Enable the HTTPS service.
[AC] ip https enable
# Create a local user named usera, set the password to 123 for the user, and specify the Web service type for the local user.
[AC] local-user usera
[AC-luser-usera] password simple 123
[AC-luser-usera] service-type Web
[AC-luser-usera] authorization-attribute level 3
2. Configure the host (the HTTPS client):
On the host, run the IE browser. In the address bar, enter http://10.1.2.2/certsrv and request a certificate for the host as prompted.
3. Verify the configuration:
Enter https://10.1.1.1 in the address bar, and select the certificate issued by new-ca. Then the Web login page of the AC appears. On the login page, type the username usera and password 123 to enter the Web management page.
For more information about PKI configuration commands, SSL configuration commands, and the public-key local create rsa command, see Security Command Reference.
Logging in through SNMP
You can run SNMP on an NMS to access the device MIB and perform GET and SET operations to manage and monitor the device. The device supports SNMPv1, SNMPv2c, and SNMPv3, and can work with various network management software products, including IMC. For more information about SNMP, see Network Management and Monitoring Configuration Guide.
By default, SNMP access is disabled. To enable SNMP access, log in to the device through any other method, and configure SNMP login.
FIPS compliance
The device supports the FIPS mode that complies with NIST FIPS 140-2 requirements. Support for features, commands, and parameters might differ in FIPS mode and non-FIPS mode. For more information about FIPS mode, see Security Configuration Guide.
SNMP is not supported in FIPS mode.
Configuring SNMP login
Connect the PC (the NMS) and the device to the network, making sure they can reach each other, as shown in Figure 13. This document describes only the basic SNMP configuration procedures on the device.

|
|
IMPORTANT: To make SNMP operate correctly, make sure the SNMP settings (including the SNMP version) on the NMS are consistent with those on the device. |
Prerequisites
· Assign an IP address to a Layer 3 interface on the device.
· Configure routes to make sure the NMS and the Layer 3 interface can reach each other.
Configuring SNMPv3 settings
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the SNMP agent. |
snmp-agent |
Optional. By default, the SNMP agent is disabled. You can enable SNMP agent with any command that begins with snmp-agent, except for the snmp-agent calculate-password command. |
|
3. Configure an SNMP group and specify its access right. |
snmp-agent group v3 group-name [ authentication | privacy ] [ read-view read-view ] [ write-view write-view ] [ notify-view notify-view ] [ acl acl-number | acl ipv6 ipv6-acl-number ] * |
By default, no SNMP group is configured. |
|
4. Add a user to the SNMP group. |
snmp-agent usm-user v3 user-name group-name [ [ cipher ] authentication-mode { md5 | sha } auth-password [ privacy-mode { 3des | aes128 | des56 } priv-password ] ] [ acl acl-number | acl ipv6 ipv6-acl-number ] * |
N/A |
Configuring SNMPv1 or SNMPv2c settings
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the SNMP agent. |
snmp-agent |
Optional. By default, the SNMP agent is disabled. You can enable SNMP agent with any command that begins with snmp-agent, except for the snmp-agent calculate-password command. |
|
3. Create or update MIB view information. |
snmp-agent mib-view { excluded | included } view-name oid-tree [ mask mask-value ] |
Optional. By default, the MIB view name is ViewDefault and OID is 1. |
|
4. Configure the SNMP access right. |
· (Approach 1) Specify the SNMP NMS access right
directly by configuring an SNMP community: · (Approach 2) Configure an SNMP group and add a user to the SNMP group: a. snmp-agent group { v1 | v2c } group-name [ read-view read-view ] [ write-view write-view ] [ notify-view notify-view ] [ acl acl-number | acl ipv6 ipv6-acl-number ] * b. snmp-agent usm-user { v1 | v2c } user-name group-name [ acl acl-number | acl ipv6 ipv6-acl-number ] * |
Use either approach. The username in approach 2 is equivalent to the community name used in approach 1, and must be the same as the community name configured on the NMS. |
NMS login example
Network requirements
Configure the AC and NMS so you can remotely manage the AC through SNMPv3.
Figure 14 Network diagram

Configuration procedure
1. Configure the AC:
# Assign an IP address to the AC. Make sure the AC and the NMS can reach each other. (Details not shown.)
# Enter system view.
<AC> system-view
# Enable the SNMP agent.
[AC] snmp-agent
# Configure an SNMP group.
[AC] snmp-agent group v3 managev3group
# Add a user to the SNMP group.
[AC] snmp-agent usm-user v3 managev3user managev3group
2. Configure the NMS:
Make sure the NMS has the same SNMP settings, including the username, as the device. If not, the device cannot be discovered or managed by the NMS.
3. Use the network management station to discover, query, and configure the device. For more information, see the NMS manual.
Controlling user logins
Use ACLs to prevent unauthorized logins. For more information about ACLs, see ACL and QoS Configuration Guide.
FIPS compliance
The device supports the FIPS mode that complies with NIST FIPS 140-2 requirements. Support for features, commands, and parameters might differ in FIPS mode and non-FIPS mode. For more information about FIPS mode, see Security Configuration Guide.
Telnet and HTTP are not supported in FIPS mode.
Controlling Telnet logins
Use a basic ACL (2000 to 2999) to filter Telnet traffic by source IP address. Use an advanced ACL (3000 to 3999) to filter Telnet traffic by source and/or destination IP address. Use an Ethernet frame header ACL (4000 to 4999) to filter Telnet traffic by source MAC address.
To access the device, a Telnet user must match a permit statement in the ACL applied to the user interface.
Controlling Telnet users by client SSIDs
Controlling Telnet users by service set identifiers (SSIDs) is achieved by matching WLAN ACLs with packets based on SSIDs of clients. WLAN ACLs are numbered from 100 to 199. For information about defining an ACL, see ACL and QoS Configuration Guide.
To control Telnet users by client SSIDs:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a WLAN ACL and enter WLAN ACL view. |
acl number acl-number |
N/A |
|
3. Define a rule for the WLAN ACL. |
rule [ rule-id ] { permit | deny } [ ssid ssid-name ] |
N/A |
|
4. Exit to system view. |
quit |
N/A |
|
5. Enter user interface view. |
user-interface { first-num1 [ last-num1 ] | { aux | console | vty } first-num2 [ last-num2 ] } |
N/A |
|
6. Apply the WLAN ACL to control Telnet users by SSIDs of WLAN clients. |
acl acl-number inbound |
Use the inbound keyword to filter users trying to Telnet to the current AC. |
Configuring source IP-based Telnet login control
|
Command |
Remarks |
|
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a basic ACL and enter its view, or enter the view of an existing basic ACL. |
acl [ ipv6 ] number acl-number [ name name ] [ match-order { config | auto } ] |
By default, no basic ACL exists. |
|
3. Configure an ACL rule. |
· For IPv4 networks: · For IPv6 networks: |
By default, a basic ACL does not contain any rule. |
|
Exit the basic ACL view. |
quit |
N/A |
|
5. Enter user interface view. |
user-interface { first-num1 [ last-num1 ] | { aux | console | vty } first-num2 [ last-num2 ] } |
N/A |
|
6. Use the ACL to control user logins by source IP address. |
acl [ ipv6 ] acl-number { inbound | outbound } |
· inbound: Filters incoming packets. · outbound: Filters outgoing packets. |
Configuring source/destination IP-based Telnet login control
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
Create an advanced ACL and enter its view, or enter the view of an existing advanced ACL. |
acl [ ipv6 ] number acl-number [ name name ] [ match-order { config | auto } ] |
By default, no advanced ACL exists. |
|
3. Configure an ACL rule. |
rule [ rule-id ] { permit | deny } rule-string |
N/A |
|
4. Exit advanced ACL view. |
quit |
N/A |
|
5. Enter user interface view. |
user-interface { first-num1 [ last-num1 ] | { aux | console | vty } first-num2 [ last-num2 ] } |
N/A |
|
6. Apply the ACL to the user interfaces. |
acl [ ipv6 ] acl-number { inbound | outbound } |
· inbound: Filters incoming Telnet packets. outbound: Filters outgoing Telnet packets. |
Configuring source MAC-based Telnet login control
Ethernet frame header ACLs apply to Telnet traffic only if the Telnet client and server are located in the same subnet.
To configure source MAC-based Telnet login control:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an Ethernet frame header ACL and enter its view. |
acl number acl-number [ name name ] [ match-order { config | auto } ] |
By default, no Ethernet frame header ACL exists. |
|
3. Configure an ACL rule. |
rule [ rule-id ] { permit | deny } rule-string |
N/A |
|
4. Exit Ethernet frame header ACL view. |
quit |
N/A |
|
5. Enter user interface view. |
user-interface { first-num1 [ last-num1 ] | { aux | console | vty } first-num2 [ last-num2 ] } |
N/A |
|
6. Use the ACL to control user logins by source MAC address. |
acl acl-number inbound |
inbound: Filters incoming packets. |
Telnet login control configuration example
Network requirements
Configure the AC in Figure 15 to permit only incoming Telnet packets sourced from Host A and Host B.
Configuration procedure
# Configure basic ACL 2000, and configure rule 1 to permit packets sourced from Host B and rule 2 to permit packets sourced from Host A.
<AC> system-view
[AC] acl number 2000 match-order config
[AC-acl-basic-2000] rule 1 permit source 10.110.100.52 0
[AC-acl-basic-2000] rule 2 permit source 10.110.100.46 0
[AC-acl-basic-2000] quit
# Reference ACL 2000 on user interfaces VTY 0 through VTY 4 so only Host A and Host B can Telnet to the Device.
[AC] user-interface vty 0 4
[AC-ui-vty0-4] acl 2000 inbound
Configuring source IP-based SNMP login control
Use a basic ACL (2000 to 2999) to control SNMP logins by source IP address. To access the requested MIB view, an NMS must use a source IP address permitted by the ACL.
Configuration procedure
To configure source IP-based SNMP login control:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a basic ACL and enter its view, or enter the view of an existing basic ACL. |
acl [ ipv6 ] number acl-number [ name name ] [ match-order { config | auto } ] |
By default, no basic ACL exists. |
|
3. Configure an ACL rule. |
rule [ rule-id ] { deny | permit } [ counting | source { sour-addr sour-wildcard | any } | time-range time-range-name ] * |
N/A |
|
4. Exit the basic ACL view. |
quit |
N/A |
|
5. Apply the ACL to an SNMP community, group, or user. |
· SNMPv1/v2c community: · SNMPv1/v2c group: · SNMPv3 group: · SNMPv1/v2c
user: · SNMPv3 user: |
For more information about SNMP, see Network Management and Monitoring Configuration Guide. |
SNMP login control configuration example
Network requirements
Configure the AC in Figure 16 to allow only Host A and Host B to access the AC through SNMP.
Configuration procedure
# Create ACL 2000, and configure rule 1 to permit packets sourced from Host B and rule 2 to permit packets sourced from Host A.
<AC> system-view
[AC] acl number 2000 match-order config
[AC-acl-basic-2000] rule 1 permit source 10.110.100.52 0
[AC-acl-basic-2000] rule 2 permit source 10.110.100.46 0
[AC-acl-basic-2000] quit
# Associate the ACL with the SNMP community and the SNMP group.
[AC] snmp-agent community read aaa acl 2000
[AC] snmp-agent group v2c groupa acl 2000
[AC] snmp-agent usm-user v2c usera groupa acl 2000
Configuring Web login control
Use a basic ACL (2000 to 2999) to filter HTTP/HTTPS traffic by source IP address for Web login control. To access the device, a Web user must use an IP address permitted by the ACL.
You can also log off suspicious Web users that have been logged in.
Configuring source IP-based Web login control
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a basic ACL and enter its view, or enter the view of an existing basic ACL. |
acl [ ipv6 ] number acl-number [ name name ] [ match-order { config | auto } ] |
By default, no basic ACL exists. |
|
3. Create rules for this ACL. |
rule [ rule-id ] { deny | permit } [ counting | source { sour-addr sour-wildcard | any } | time-range time-range-name ] * |
N/A |
|
Exit the basic ACL view. |
quit |
N/A |
|
5. Associate the HTTP service with the ACL. |
ip http acl acl-number |
Configure either or both of the commands. HTTP login and HTTPS login are separate login methods. To use HTTPS login, you do not need to configure HTTP login. |
|
6. Associate the HTTPS service with the ACL. |
ip https acl acl-number |
Logging off online Web users
|
Task |
Command |
Remarks |
|
Log off online Web users. |
free web-users { all | user-id user-id | user-name user-name } |
Available in user interface view. |
Web login control configuration example
Network requirements
Configure the AC in Figure 17 to provide Web access service only to Host B.

Configuration procedure
# Create ACL 2000, and configure rule 1 to permit packets sourced from Host B.
<AC> system-view
[AC] acl number 2030 match-order config
[AC-acl-basic-2030] rule 1 permit source 10.110.100.52 0
[AC-acl-basic-2030] quit
# Associate the ACL with the HTTP service so only the Web users on Host B can access the device.
[AC] ip http acl 2030

