- Table of Contents
-
- 20-Network Management and Monitoring Configuration Guide
- 00-Preface
- 01-Ping and tracert configuration
- 02-System debugging configuration
- 03-NQA configuration
- 04-iNQA configuration
- 05-iFIT configuration
- 06-NTP configuration
- 07-SNMP configuration
- 08-RMON configuration
- 09-Sampler configuration
- 10-Mirroring configuration
- 11-NetStream configuration
- 12-IPv6 NetStream configuration
- 13-sFlow configuration
- 14-Cloud connection configuration
- 15-Packet capture configuration
- 16-IP traffic statistics collection configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 10-Mirroring configuration | 237.64 KB |
Contents
Configuring local port mirroring (SPAN)
Restrictions and guidelines for local port mirroring configuration
Local port mirroring tasks at a glance
Creating a local mirroring group
Configuring local port mirroring group with multiple monitoring devices
Verifying and maintaining port mirroring
Port mirroring configuration examples
Example: Configuring local port mirroring
Restrictions and guidelines: Flow mirroring configuration
Flow mirroring tasks at a glance
Configuring a traffic behavior
Applying a QoS policy to an interface
Applying a QoS policy globally
Applying a QoS policy to the control plane
Configuring port mirroring
About port mirroring
Port mirroring copies the packets passing through a port to a port that connects to a data monitoring device for packet analysis.
Terminology
The following terms are used in port mirroring configuration.
Mirroring source
The mirroring sources can be one or more monitored ports (called source ports).
Packets passing through mirroring sources are copied to a port connecting to a data monitoring device for packet analysis. The copies are called mirrored packets.
Source device
The device where the mirroring sources reside is called a source device.
Mirroring destination
The mirroring destination connects to a data monitoring device and is the destination port (also known as the monitor port) of mirrored packets. Mirrored packets are sent out of the monitor port to the data monitoring device.
A monitor port might receive multiple copies of a packet when it monitors multiple mirroring sources. For example, two copies of a packet are received on Port A when the following conditions exist:
· Port A is monitoring bidirectional traffic of Port B and Port C on the same device.
· The packet travels from Port B to Port C.
Destination device
The device where the monitor port resides is called the destination device.
Mirroring direction
The mirroring direction specifies the direction of the traffic that is copied on a mirroring source.
· Inbound—Copies packets received.
· Outbound—Copies packets sent.
· Bidirectional—Copies packets received and sent.
Mirroring group
Port mirroring is implemented through mirroring groups.
Local port mirroring (SPAN)
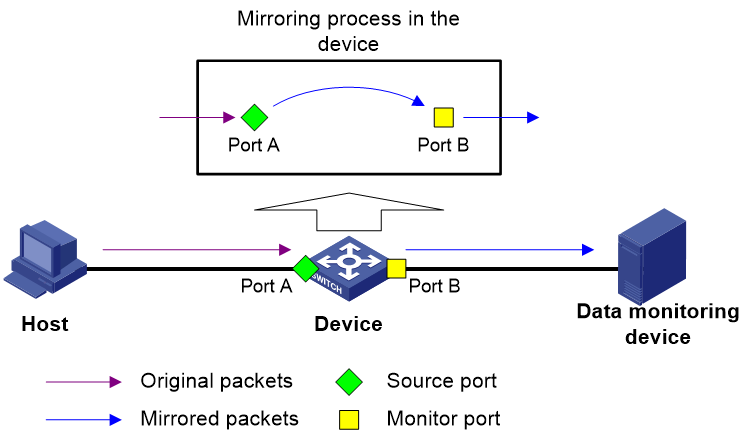
Figure 1 Local port mirroring implementation
As shown in Figure 1, the source port (Port A) and the monitor port (Port B) reside on the same device. Packets received on Port A are copied to Port B. Port B then forwards the packets to the data monitoring device for analysis.
Configuring local port mirroring (SPAN)
Restrictions and guidelines for local port mirroring configuration
A local mirroring group takes effect only after it is configured with the monitor port and mirroring sources.
Local port mirroring tasks at a glance
To configure local port mirroring, perform the following tasks:
1. Configuring mirroring sources
2. Configuring the monitor port
Creating a local mirroring group
1. Enter system view.
system-view
2. Create a local mirroring group.
mirroring-group group-id local
Configuring mirroring sources
Restrictions and guidelines for mirroring source configuration
When you configure source ports for a local mirroring group, follow these restrictions and guidelines:
· A mirroring group can contain multiple source ports.
· A source port cannot be configured as a monitor port.
Configuring source ports
· Configure source ports in system view:
a. Enter system view.
system-view
b. Configure source ports for a local mirroring group.
mirroring-group group-id mirroring-port interface-list { both | inbound | outbound }
By default, no source port is configured for a local mirroring group.
· Configure source ports in interface view:
a. Enter system view.
system-view
b. Enter interface view.
interface interface-type interface-number
c. Configure the port as a source port for a local mirroring group.
mirroring-group group-id mirroring-port { both | inbound | outbound }
By default, a port does not act as a source port for any local mirroring groups.
Configuring the monitor port
Restrictions and guidelines
Do not enable the spanning tree feature on the monitor port.
Use a monitor port only for port mirroring, so the data monitoring device receives only the mirrored traffic.
Procedure
· Configure the monitor port in system view:
a. Enter system view.
system-view
b. Configure the monitor port for a local mirroring group.
mirroring-group group-id monitor-port interface-type interface-number
By default, no monitor port is configured for a local mirroring group.
· Configure the monitor port in interface view:
a. Enter system view.
system-view
b. Enter interface view.
interface interface-type interface-number
c. Configure the port as the monitor port for a mirroring group.
mirroring-group group-id monitor-port
By default, a port does not act as the monitor port for any local mirroring groups.
Configuring local port mirroring group with multiple monitoring devices
About this task
To monitor interested traffic passing through a device on multiple directly connected data monitoring devices, configure local port mirroring with a remote probe VLAN as follows:
1. Configure a remote source group on the device.
2. Configure mirroring sources and a reflector port for the remote source group.
3. Specify a VLAN as the remote probe VLAN and assign the ports connecting to the data monitoring devices to the VLAN.
This configuration enables the device to copy packets received on the mirroring sources to the reflector port, which broadcasts the packets in the remote probe VLAN. The packets are then sent out of the member ports of the remote probe VLAN to the data monitoring devices.
Restrictions and guidelines
The reflector port must be a port not in use. Do not connect a network cable to the reflector port.
When a port is configured as a reflector port, all the other settings on the port are cleared. You cannot configure other features on the reflector port.
Do not assign a source port of a mirroring group to the remote probe VLAN of the mirroring group.
A VLAN can act as the remote probe VLAN for only one remote source group. As a best practice, use the VLAN for port mirroring exclusively. Do not create a VLAN interface for the VLAN or configure other features for the VLAN.
The remote probe VLAN must be a static VLAN.
To delete a VLAN that has been configured as the remote probe VLAN for a mirroring group, remove the remote probe VLAN from the mirroring group first.
Procedure
1. Enter system view.
system-view
2. Create a remote source group.
mirroring-group group-id remote-source
3. Configure mirroring sources for the remote source group. Choose one of the following tasks:
¡ Configure mirroring ports in system view:
mirroring-group group-id mirroring-port interface-list { both | inbound | outbound }
¡ Execute the following commands in sequence to enter interface view, and then configure the interface as a source port.
interface interface-type interface-number
mirroring-group group-id mirroring-port { both | inbound | outbound }
quit
4. Configure the reflector port for the remote source group.
mirroring-group group-id reflector-port reflector-port
By default, no reflector port is configured for a remote source group.
5. Create a VLAN and enter VLAN view.
vlan vlan-id
6. Assign the ports that connect to the data monitoring devices to the VLAN.
port interface-list
By default, a VLAN does not contain any ports.
7. Return to system view.
quit
8. Specify the VLAN as the remote probe VLAN for the remote source group.
mirroring-group group-id remote-probe vlan vlan-id
By default, no remote probe VLAN is configured for a remote source group
Verifying and maintaining port mirroring
To display mirroring group information, execute the following command in any view:
display mirroring-group { group-id | all | local }
Port mirroring configuration examples
Example: Configuring local port mirroring
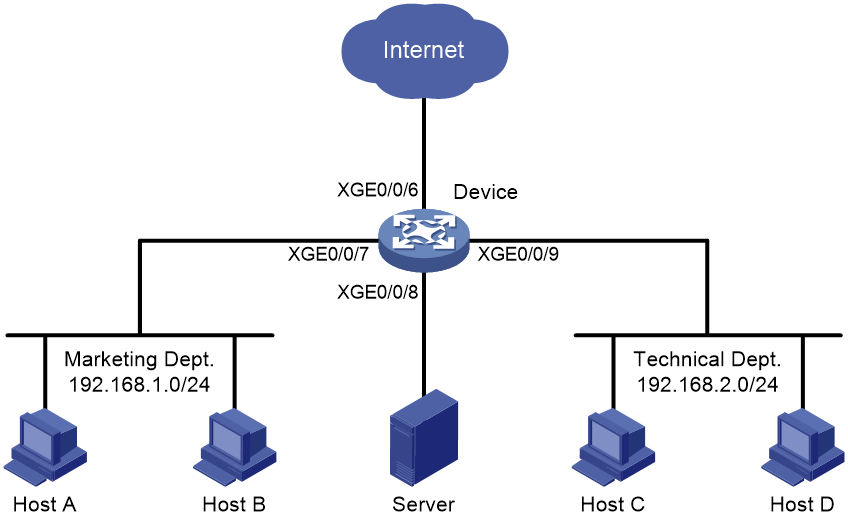
Network configuration
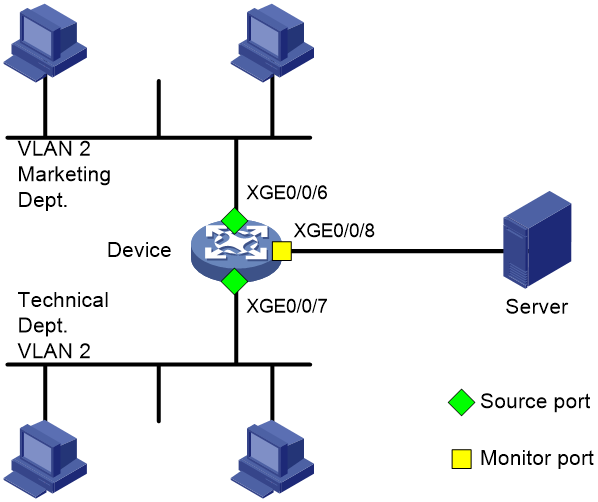
As shown in Figure 2, configure local port mirroring in source port mode to enable the server to monitor the bidirectional traffic of the two departments.
Procedure
# Create local mirroring group 1.
<Device> system-view
[Device] mirroring-group 1 local
# Configure Ten-GigabitEthernet 0/0/6 and Ten-GigabitEthernet 0/0/7 as source ports for local mirroring group 1.
[Device] mirroring-group 1 mirroring-port ten-gigabitethernet 0/0/6 ten-gigabitethernet 0/0/7 both
# Configure Ten-GigabitEthernet 0/0/8 as the monitor port for local mirroring group 1.
[Device] mirroring-group 1 monitor-port ten-gigabitethernet 0/0/8
# Disable the spanning tree feature on the monitor port (Ten-GigabitEthernet 0/0/8).
[Device] interface ten-gigabitethernet 0/0/8
[Device-Ten-GigabitEthernet0/0/8] undo stp enable
[Device-Ten-GigabitEthernet0/0/8] quit
Verifying the configuration
# Verify the mirroring group configuration.
[Device] display mirroring-group all
Mirroring group 1:
Type: Local
Status: Active
Mirroring port: Ten-GigabitEthernet0/0/6 Both
Ten-GigabitEthernet0/0/7 Both
Monitor port: Ten-GigabitEthernet0/0/8
Configuring flow mirroring
About flow mirroring
Flow mirroring copies packets matching a class to a destination for packet analyzing and monitoring. It is implemented through QoS.
To implement flow mirroring through QoS, perform the following tasks:
· Define traffic classes and configure match criteria to classify packets to be mirrored. Flow mirroring allows you to flexibly classify packets to be analyzed by defining match criteria.
· Configure traffic behaviors to mirror the matching packets to the specified destination.
For more information about QoS policies, traffic classes, and traffic behaviors, see ACL and QoS Configuration Guide.
Flow mirroring ERSPAN
About flow mirroring ERSPAN
You can implement ERSPAN through flow-mirroring traffic to interfaces.
ERSPAN encapsulation formats include ERSPANv2 and ERSPANv3.
· ERSPANv2—Encapsulates mirrored packets in GRE packets with protocol number 0x88BE.
· ERSPANv3—Encapsulates mirrored packets in GRE packets with protocol number 0x22EB.
Compared with ERSPANv2, ERSPANv3 introduces a bigger, more flexible composite header to meet the requirements in the network monitoring scenarios (for example, network management, intrusion protection, and performance & latency analysis), which are becoming more complicated and diversified. In these scenarios, all parameters of the original mirrored packets must be known, including those parameters that do not exist in the original mirrored packets.
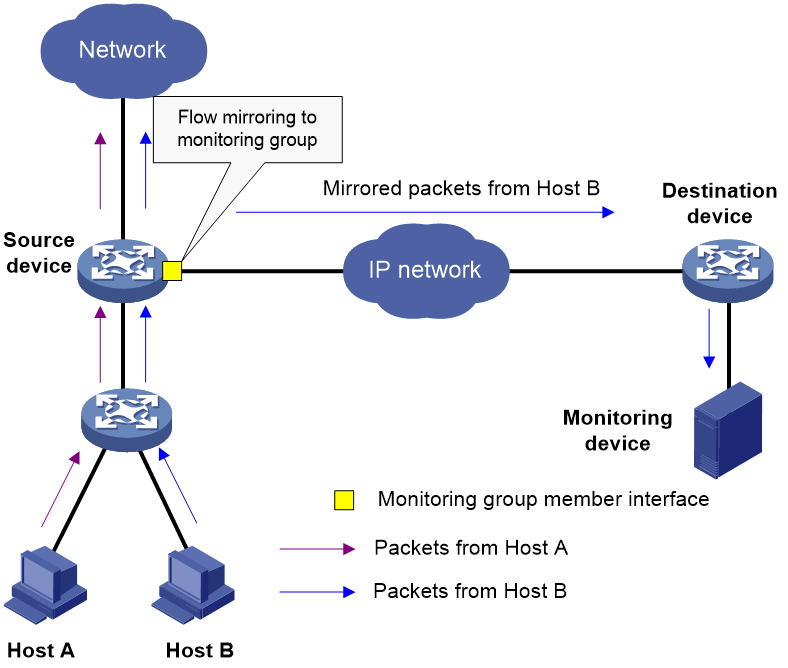
Flow mirroring ERSPAN can be implemented in loopback mode, encapsulation parameter mode, or monitoring group mode.
Operating mechanisms
Flow mirroring ERSPAN can be implemented in the following modes:
· Loopback mode.
· Encapsulation parameter mode.
· Monitoring group mode.
Loopback mode
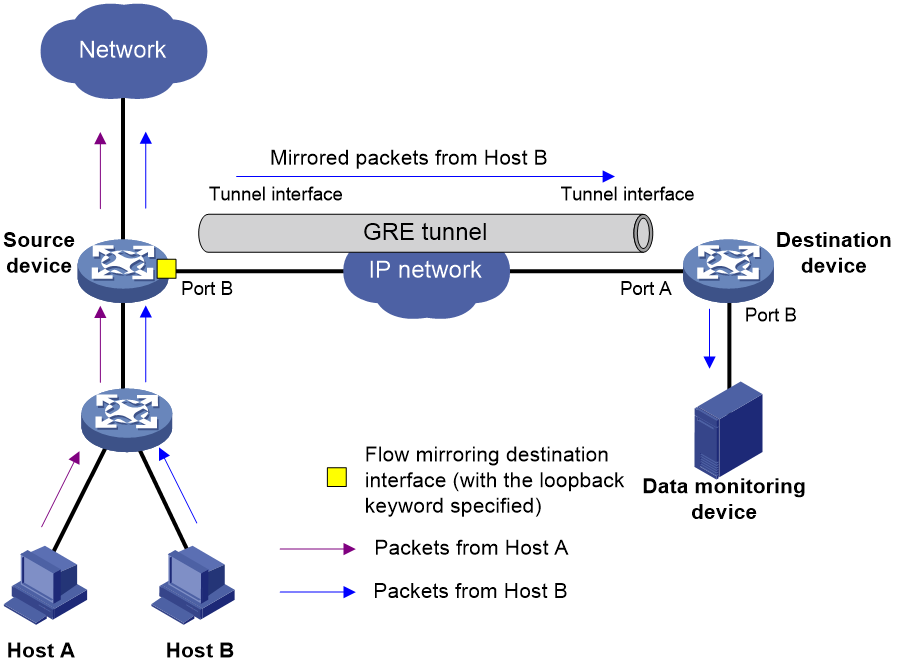
As shown in Figure 3, configure flow mirroring ERSPAN in loopback mode as follows:
1. On the source device, apply a QoS policy to the source interface as follows:
a. Configure a traffic class to match packets.
b. Configure a traffic behavior to mirror packets to Port B and specify the loopback keyword.
c. Create a QoS policy, and associate the traffic class with the traffic behavior.
d. Apply the QoS policy to the source interface.
2. On the source device, apply a QoS policy to Port B as follows:
a. Configure a traffic class to match packets.
b. Configure a traffic behavior to redirect packets to a tunnel interface.
c. Create a QoS policy, and associate the traffic class with the traffic behavior.
d. Apply the QoS policy to Port B.
3. The destination device receives mirrored packets on the tunnel interface and decapsulates the packets. Then, the destination device forwards the packets based on the destination IP address of the original packets.
Make sure the destination device has the route and ARP entry to the destination IP address.
Figure 3 Flow mirroring ERSPAN in loopback mode
Encapsulation parameter mode
In this mode, configure a QoS policy on the source device. Configure the QoS policy as follows:
1. Configure a traffic class to match packets.
2. Configure a traffic behavior to flow-mirror traffic to an interface.
3. Associate the traffic class with the traffic behavior.
You can configure flow-mirroring traffic to an interface in one of the following modes:
· Directly specifying an outgoing interface—In this mode, specify both the outgoing interface and encapsulation parameters. The device encapsulates packets with the specified parameters and then forwards packets out of the specified interface.
· Specifying an outgoing interface through route lookup—In this mode, specify only encapsulation parameters without specifying an outgoing interface. The device looks up a route for the encapsulated mirrored packets based on the source IP address and destination IP address of the encapsulated packets. The outgoing interface of the route is a destination interface of the mirrored packets.
In this mode, you can use the load sharing function of a routing protocol to forward mirrored packets to multiple destination interfaces.
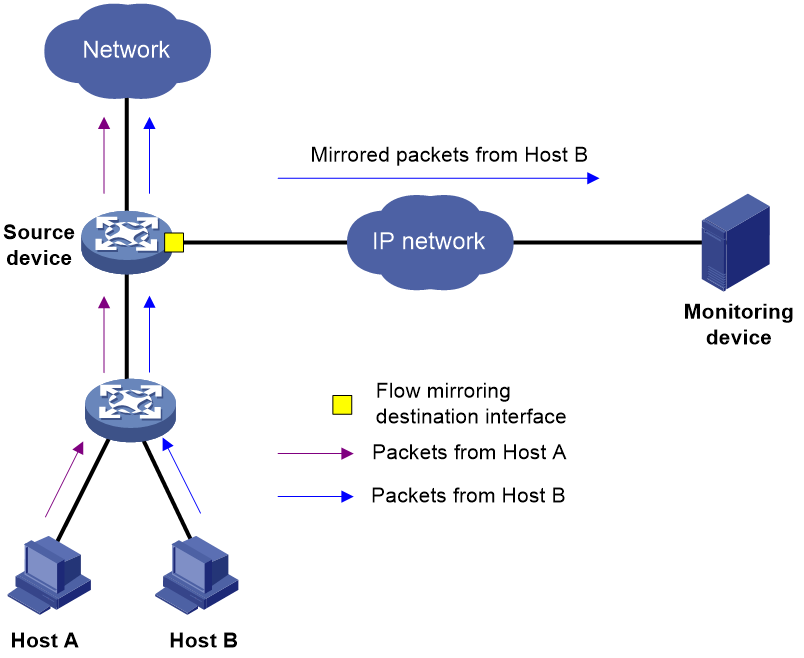
As shown in Figure 4, flow mirroring ERSPAN in encapsulation parameter mode works as follows:
4. The source device copies a matching packet.
5. The source device encapsulates the packet with the specified ERSPAN encapsulation parameters.
6. The source device forwards the packet in either of the following methods:
¡ Forwards the mirrored packets out of the specified outgoing interface.
¡ Looks up a route for the encapsulated mirrored packet based on the source IP address and destination IP address of the encapsulated packet.
7. The encapsulated packet is routed to the monitoring device.
8. The monitoring device decapsulates the packet and analyzes the packet contents.
The packet sent to the monitoring device through flow mirroring in this mode is encapsulated. In this mode, make sure the monitoring device supports decapsulating packets.
Figure 4 Flow mirroring ERSPAN in encapsulation parameter mode
Monitoring group mode
As shown in Figure 5, flow mirroring ERSPAN in monitoring group mode works as follows:
1. On the source device, configure a monitoring group, add member interfaces to the monitoring group, and configure the encapsulation parameters for the member interfaces.
2. On the source device, apply a QoS policy as follows:
a. Configure a traffic class to match packets.
b. Configure a traffic behavior to mirror traffic to the monitoring group.
c. Create a QoS policy, and associate the traffic class with the traffic behavior in the QoS policy.
d. Apply the QoS policy.
3. The source device copies a matching packet and mirrors the packet to the monitoring group. The member interfaces of the monitoring group encapsulate the packet with the specified encapsulation parameters.
4. The source device forwards the packet in either of the following methods:
¡ Forwards the mirrored packet out of the specified outgoing interface.
¡ Looks up a route for the encapsulated mirrored packet based on the source IP address and destination IP address of the encapsulated packet.
5. The encapsulated packet is routed to the monitoring device.
6. The monitoring device decapsulates the packet and analyzes the packet contents.
The packet sent to the monitoring device through flow mirroring in this mode is encapsulated. In this mode, make sure the monitoring device supports decapsulating packets.
Figure 5 Flow mirroring ERSPAN in monitoring group mode
Restrictions and guidelines: Flow mirroring configuration
For information about the configuration commands except the mirror-to command, see ACL and QoS Command Reference.
Flow mirroring tasks at a glance
To configure flow mirroring, perform the following tasks:
1. Configuring a traffic class
A traffic class defines the criteria that filters the traffic to be mirrored.
2. Configuring a traffic behavior
A traffic behavior specifies mirroring destinations.
Choose one of the following tasks:
¡ Applying a QoS policy to an interface
¡ Applying a QoS policy globally
¡ Applying a QoS policy to the control plane
Configuring a traffic class
1. Enter system view.
system-view
2. Create a class and enter class view.
traffic classifier classifier-name [ operator { and | or } ]
3. Configure match criteria.
if-match [ not ] match-criteria
By default, no match criterion is configured in a traffic class.
4. (Optional.) Display traffic class information.
display traffic classifier { system-defined | user-defined } [ classifier-name ] [ slot slot-number ]
For more information about this command, see ACL and QoS Command Reference.
Configuring a traffic behavior
1. Enter system view.
system-view
2. Create a traffic behavior and enter traffic behavior view.
traffic behavior behavior-name
3. Configure mirroring destinations for the traffic behavior.
¡ Mirror traffic to interfaces.
Syntax I:
mirror-to interface interface-type interface-number [ { destination-ip destination-ip-address source-ip source-ip-address | destination-ipv6 destination-ipv6-address source-ipv6 source-ipv6-address } [ dscp dscp-value | erspan-id erspan-id-value | vlan vlan-id | vrf-instance vrf-instance-name ] * ] [ destination-mac mac-address ]
Syntax II:
mirror-to interface { destination-ip destination-ip-address source-ip source-ip-address | destination-ipv6 destination-ipv6-address source-ipv6 source-ipv6-address } [ dscp dscp-value | erspan-id erspan-id-value | vlan vlan-id | vrf-instance vrf-name ] * [ destination-mac mac-address ]
By default, no mirroring actions exist to mirror traffic to interfaces.
4. (Optional.) Display traffic behavior configuration.
display traffic behavior
This command is available in any view.
Configuring a QoS policy
1. Enter system view.
system-view
2. Create a QoS policy and enter QoS policy view.
qos policy policy-name
3. Associate a class with a traffic behavior in the QoS policy.
classifier classifier-name behavior behavior-name
By default, no traffic behavior is associated with a class.
4. (Optional.) Display QoS policy configuration.
display qos policy
This command is available in any view.
Applying a QoS policy
Applying a QoS policy to an interface
Restrictions and guidelines
You can apply a QoS policy to an interface to mirror the traffic of the interface.
A policy can be applied to multiple interfaces.
In one traffic direction of an interface, only one QoS policy can be applied.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Apply a policy to the interface.
qos apply policy policy-name { inbound | outbound }
4. (Optional.) Display the QoS policy applied to the interface.
display qos policy interface
This command is available in any view.
Applying a QoS policy globally
Restrictions and guidelines
You can apply a QoS policy globally to mirror the traffic on all ports.
Procedure
1. Enter system view.
system-view
2. Apply a QoS policy globally.
qos apply policy policy-name global { inbound | outbound }
3. (Optional.) Display global QoS policies.
display qos policy global
This command is available in any view.
Applying a QoS policy to the control plane
Restrictions and guidelines
You can apply a QoS policy to the control plane to mirror the traffic of all ports on the control plane.
Procedure
1. Enter system view.
system-view
2. Enter control plane view.
control-plane slot slot-number
3. Apply a QoS policy to the control plane.
qos apply policy policy-name inbound
4. (Optional.) Display QoS policies applied to the control plane
display qos policy control-plane
This command is available in any view.
Flow mirroring configuration examples
Example: Configuring flow mirroring
Network configuration
As shown in Figure 6, configure flow mirroring so that the server can monitor the following traffic:
· All traffic that the Technical Department sends to access the Internet.
· IP traffic that the Technical Department sends to the Marketing Department during working hours (8:00 to 18:00) on weekdays.
Procedure
# Create working hour range work, in which working hours are from 8:00 to 18:00 on weekdays.
<DeviceA> system-view
[DeviceA] time-range work 8:00 to 18:00 working-day
# Create IPv4 advanced ACL 3000 to allow packets from the Technical Department to access the Internet and the Marketing Department during working hours.
[DeviceA] acl advanced 3000
[DeviceA-acl-ipv4-adv-3000] rule permit tcp source 192.168.2.0 0.0.0.255 destination-port eq www
[DeviceA-acl-ipv4-adv-3000] rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 time-range work
[DeviceA-acl-ipv4-adv-3000] quit
# Create traffic class tech_c, and configure the match criterion as ACL 3000.
[DeviceA] traffic classifier tech_c
[DeviceA-classifier-tech_c] if-match acl 3000
[DeviceA-classifier-tech_c] quit
# Create traffic behavior tech_b, configure the action of mirroring traffic to Ten-GigabitEthernet 0/0/8.
[DeviceA] traffic behavior tech_b
[DeviceA-behavior-tech_b] mirror-to interface ten-gigabitethernet 0/0/8
[DeviceA-behavior-tech_b] quit
# Create QoS policy tech_p, and associate traffic class tech_c with traffic behavior tech_b in the QoS policy.
[DeviceA] qos policy tech_p
[DeviceA-qospolicy-tech_p] classifier tech_c behavior tech_b
[DeviceA-qospolicy-tech_p] quit
# Apply QoS policy tech_p to the incoming packets of Ten-GigabitEthernet 0/0/9.
[DeviceA] interface ten-gigabitethernet 0/0/9
[DeviceA-Ten-GigabitEthernet0/0/9] qos apply policy tech_p inbound
[DeviceA-Ten-GigabitEthernet0/0/9] quit
Verifying the configuration
# Verify that the server can monitor the following traffic:
· All traffic sent by the Technical Department to access the Internet.
· IP traffic that the Technical Department sends to the Marketing Department during working hours on weekdays.
(Details not shown.)