- Table of Contents
-
- H3C Access Controllers Application Security Web-Based Configuration Examples-6W100
- 00-Preface
- 01-H3C Access Controllers Comware 7 IPS Configuration Example
- 02-H3C Access Controllers Comware 7 URL Filtering Configuration Example
- 03-H3C Access Controllers Comware 7 Anti-Virus Configuration Example
- 04-H3C Access Controllers Comware 7 Application Audit and Management Configuration Example
- 05-H3C Access Controllers Comware 7 Application Rate Limiting Configuration Example
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-H3C Access Controllers Comware 7 IPS Configuration Example | 260.10 KB |
|
|
|
H3C Access Controllers |
|
Comware 7 IPS Configuration Example |
|
|
Copyright © 2024 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Contents
Introduction
The following information provides an example for configuring IPS.
Usage guidelines
Application scenarios
This configuration example is used to protect enterprise information systems and networks from attacks .
Prerequisites
This document is not restricted to specific software or hardware versions. Procedures and information in the examples might be slightly different depending on the software or hardware version of the device.
The configuration examples were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
Restrictions and guidelines
This feature is supported only in E5568P01 and later.
Example: Configuring IPS
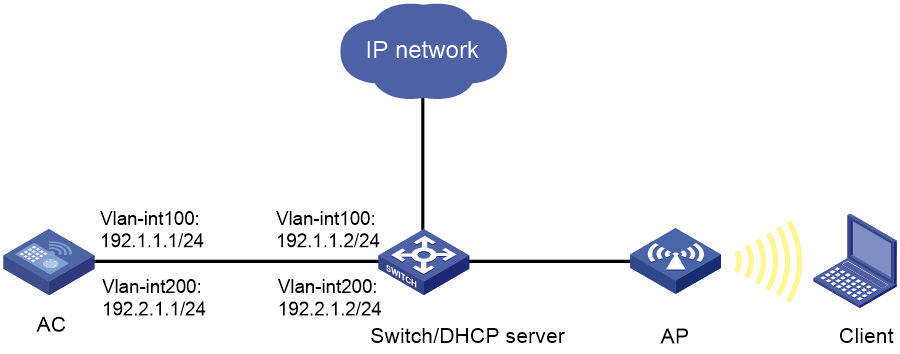
Network configuration
As shown in Figure 1, the switch acts as a DHCP server to assign IP addresses to the AP and the clients. The AP and the AC use VLAN 100 to establish a tunnel, and the clients access the wireless network through VLAN 200. Configure IPS to protect internal users in enterprises from vulnerability attacks from the Internet.
Procedures
Configuring basic AC functions
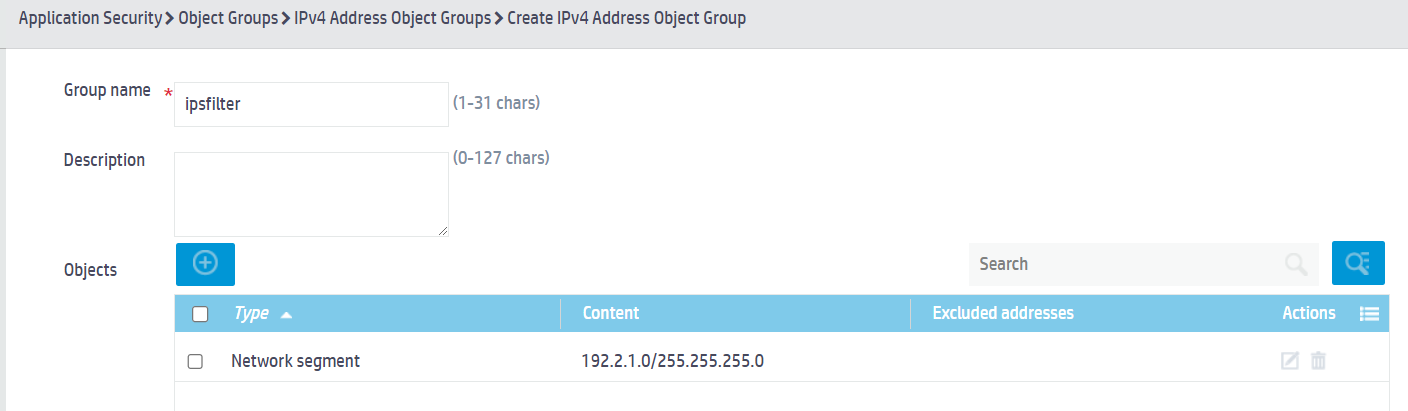
Configuring an address object group
1. From the left navigation pane, select Application Security > Object Groups > IPv4 Address Object Groups.
2. Click ![]() to add an IPv4 address object group:
to add an IPv4 address object group:
a. Enter object group name ipsfilter.
b. Click ![]() to specify the network segment object, specify the content as
192.2.1.0/24, and click Apply.
to specify the network segment object, specify the content as
192.2.1.0/24, and click Apply.
c. Click Apply.
Figure 2 Adding an IPv4 address object group
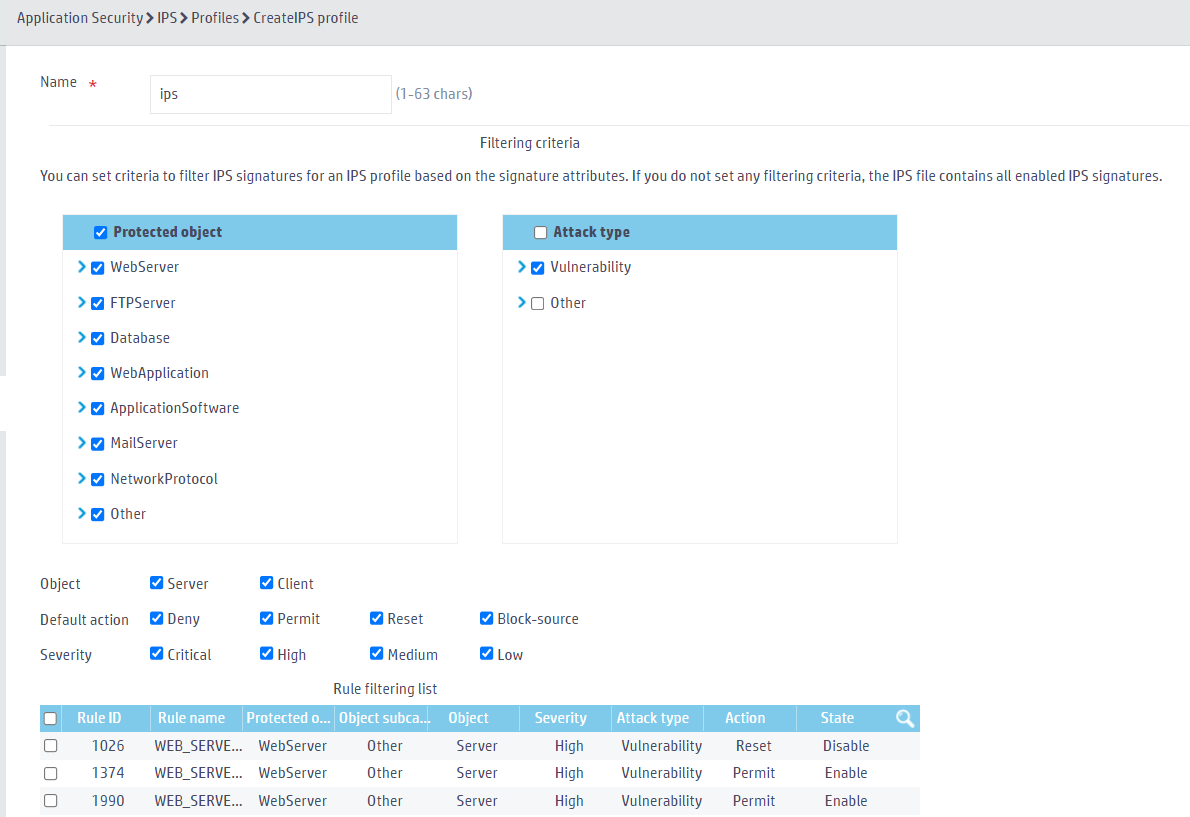
Configuring an IPS profile
1. From the left navigation pane, select Application Security > IPS > Profiles.
2. Click ![]() to add an IPS profile, and configure the following parameters:
to add an IPS profile, and configure the following parameters:
¡ Enter IPS profile name ips.
¡ Select all protected objects.
¡ Select Vulnerability as the attack type.
¡ Select Server and Client as objects.
¡ Select Deny, Permit, Reset, and Block-source as default actions.
¡ Select all severity levels, including Critical, High, Medium, and Low.
Figure 3 Configuring filtering criteria
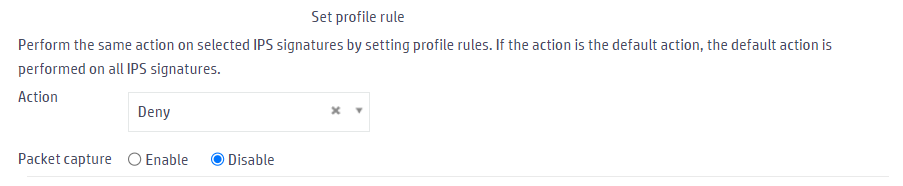
3. In the Set profile rule area, configure the following parameters:
¡ Select the Deny action.
¡ Use the default settings for other parameters.
Figure 4 Configuration profile rules
4. Click Apply.
5. Activate the IPS profile settings.
<AC> system-view
[AC] inspect activate
Configuring a security policy
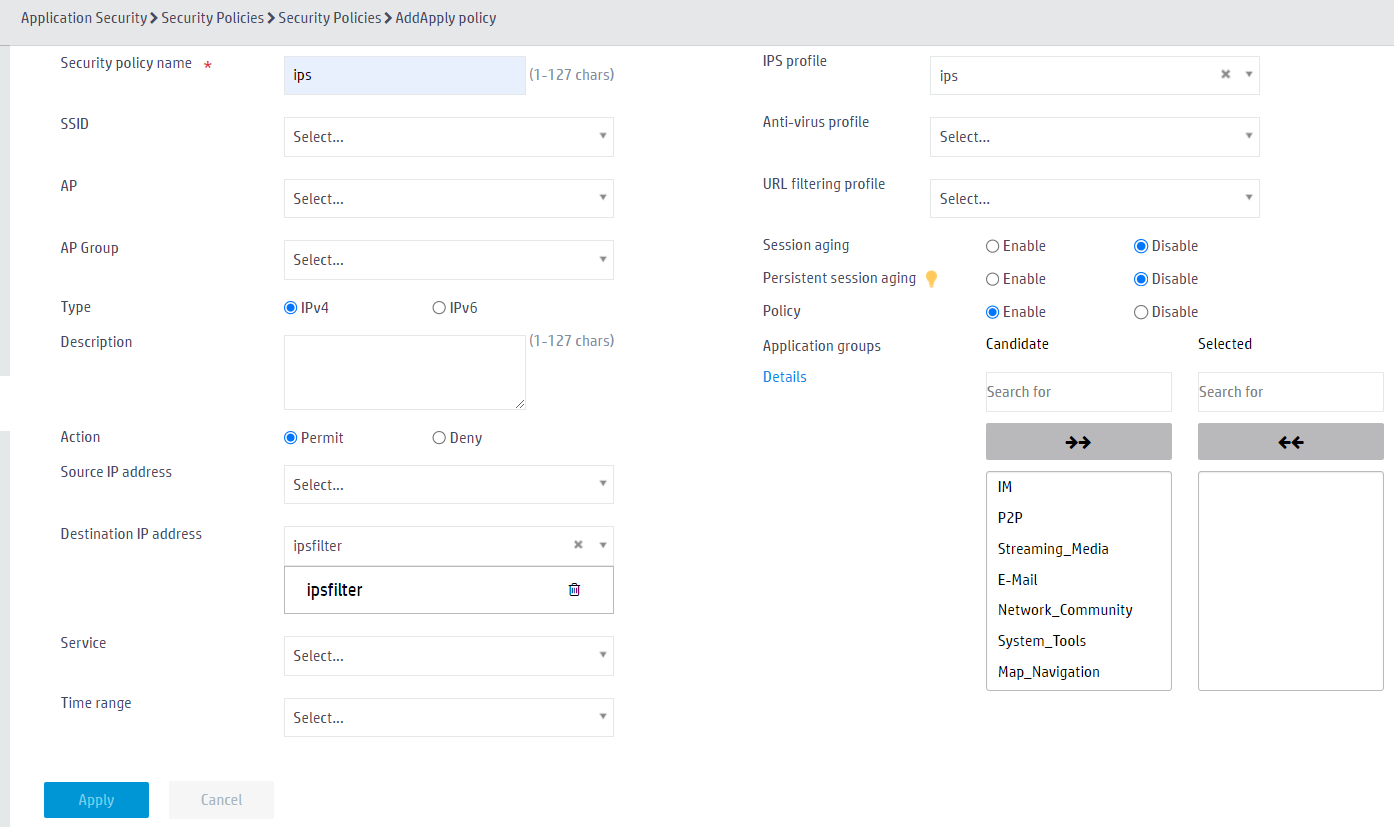
1. From the left navigation pane, select Application Security > Security Policies > Security Policies.
2. Click ![]() to add a security policy:
to add a security policy:
¡ Enter security policy name name.
¡ Select Permit as the action.
¡ Enter ipsfilter in the Destination IP address field.
¡ Select IPS profile ips.
¡ Use the default settings for other parameters.
3. Click OK.
Figure 5 Adding a security policy
Verifying the configuration
Verify that the AC can use the IPS profile to protect internal users from vulnerability attacks.
Related documentation
H3C Access Controllers Web-Based Configuration Guide