- Table of Contents
-
- 12-Security Configuration Guide
- 00-Preface
- 01-DAE proxy configuration
- 02-Password control configuration
- 03-Keychain configuration
- 04-Public key management
- 05-PKI configuration
- 06-IPsec configuration
- 07-SSH configuration
- 08-SSL configuration
- 09-Session management
- 10-Object group configuration
- 11-Attack detection and prevention configuration
- 12-IP-based attack prevention configuration
- 13-IP source guard configuration
- 14-ARP attack protection configuration
- 15-ND attack defense configuration
- 16-uRPF configuration
- 17-SAVA configuration
- 18-SAVA-P configuration
- 19-Crypto engine configuration
- 20-Trust level configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 06-IPsec configuration | 199.06 KB |
Contents
IPv6 routing protocol-based IPsec
Restrictions and guidelines: IPsec configuration
Configuring IPsec for IPv6 routing protocols
Configuring an IPsec transform set
Configuring and applying a manual IPsec profile
Manual IPsec profile configuration and application tasks at a glance
Configuring a manual IPsec profile
Applying the IPsec profile to an IPv6 routing protocol
Configuring IPsec fragmentation
Setting the maximum number of IPsec tunnels
Configuring the DF bit of IPsec packets
Enabling logging for IPsec packets
Configuring SNMP notifications for IPsec
Display and maintenance commands for IPsec
Example: Configuring IPsec for RIPng
Configuring IPsec
About IPsec
IP Security (IPsec) is defined by the IETF to provide interoperable, high-quality, cryptography-based security for IP communications. It is a Layer 3 VPN technology that transmits data in a secure channel established between two endpoints (such as two security gateways). Such a secure channel is usually called an IPsec tunnel.
IPsec framework
IPsec is a security framework that has the following protocols and algorithms:
· Authentication Header (AH).
· Encapsulating Security Payload (ESP).
· Algorithms for authentication and encryption.
AH and ESP are security protocols that provide security services.
IPsec security services
IPsec provides the following security services for data packets in the IP layer:
· Confidentiality—The sender encrypts packets before transmitting them over the Internet, protecting the packets from being eavesdropped en route.
· Data integrity—The receiver verifies the packets received from the sender to make sure they are not tampered with during transmission.
· Data origin authentication—The receiver verifies the authenticity of the sender.
· Anti-replay—The receiver examines packets and drops outdated and duplicate packets.
Benefits of IPsec
IPsec delivers the following benefits:
· Good compatibility. You can apply IPsec to all IP-based application systems and services without modifying them.
· Encryption on a per-packet rather than per-flow basis. Per-packet encryption allows for flexibility and greatly enhances IP security.
Security protocols
IPsec comes with two security protocols, AH and ESP. They define how to encapsulate IP packets and the security services that they can provide.
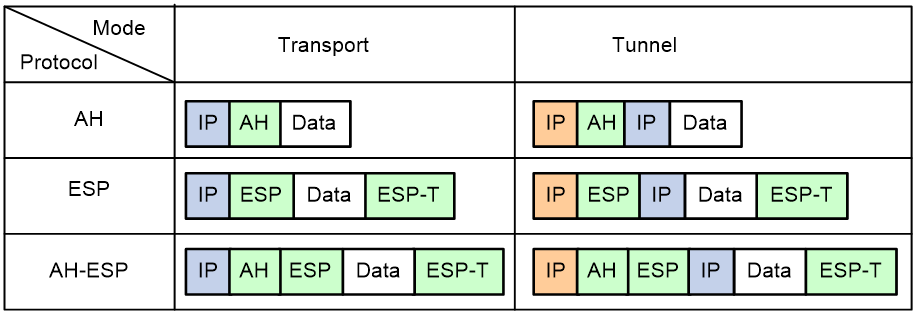
· AH (protocol 51) defines the encapsulation of the AH header in an IP packet, as shown in Figure 3. AH can provide data origin authentication, data integrity, and anti-replay services to prevent data tampering, but it cannot prevent eavesdropping. Therefore, it is suitable for transmitting non-confidential data. AH supports authentication algorithms HMAC-MD5 and HMAC-SHA1.
· ESP (protocol 50) defines the encapsulation of the ESP header and trailer in an IP packet, as shown in Figure 3. ESP can provide data encryption, data origin authentication, data integrity, and anti-replay services. Unlike AH, ESP can guarantee data confidentiality because it can encrypt the data before encapsulating the data to IP packets. ESP supports encryption algorithms such as DES, 3DES, and AES, and authentication algorithms HMAC-MD5 and HMAC-SHA1.
Both AH and ESP provide authentication services, but the authentication service provided by AH is stronger. In practice, you can choose either or both security protocols. When both AH and ESP are used, an IP packet is encapsulated first by ESP and then by AH.
Encapsulation modes
IPsec supports the following encapsulation modes: transport mode and tunnel mode.
Transport mode
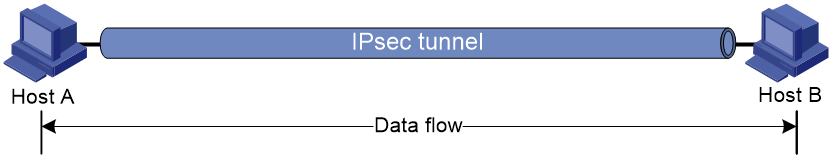
The security protocols protect the upper layer data of an IP packet. Only the transport layer data is used to calculate the security protocol headers. The calculated security protocol headers and the encrypted data (only for ESP encapsulation) are placed after the original IP header. You can use the transport mode when end-to-end security protection is required (the secured transmission start and end points are the actual start and end points of the data). The transport mode is typically used for protecting host-to-host communications, as shown in Figure 1.
Figure 1 IPsec protection in transport mode
Tunnel mode
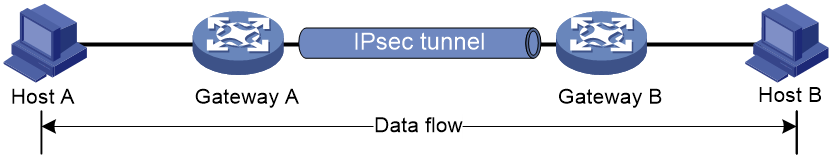
The security protocols protect the entire IP packet. The entire IP packet is used to calculate the security protocol headers. The calculated security protocol headers and the encrypted data (only for ESP encapsulation) are encapsulated in a new IP packet. In this mode, the encapsulated packet has two IP headers. The inner IP header is the original IP header. The outer IP header is added by the network device that provides the IPsec service. You must use the tunnel mode when the secured transmission start and end points are not the actual start and end points of the data packets (for example, when two gateways provide IPsec but the data start and end points are two hosts behind the gateways). The tunnel mode is typically used for protecting gateway-to-gateway communications, as shown in Figure 2.
Figure 2 IPsec protection in tunnel mode
Figure 3 shows how the security protocols encapsulate an IP packet in different encapsulation modes.
Figure 3 Security protocol encapsulations in different modes
Security association
A security association (SA) is an agreement negotiated between two communicating parties called IPsec peers. An SA includes the following parameters for data protection:
· Security protocols (AH, ESP, or both).
· Encapsulation mode (transport mode or tunnel mode).
· Authentication algorithm (HMAC-MD5 or HMAC-SHA1).
· Encryption algorithm (DES, 3DES, or AES).
· Shared keys and their lifetimes.
An SA is unidirectional. At least two SAs are needed to protect data flows in a bidirectional communication. If two peers want to use both AH and ESP to protect data flows between them, they construct an independent SA for each protocol in each direction.
An SA is uniquely identified by a triplet, which consists of the security parameter index (SPI), destination IP address, and security protocol identifier. An SPI is a 32-bit number. It is transmitted in the AH/ESP header.
An SA can be set up manually. You can configure all parameters for the SA through commands. This configuration mode is complex and does not support some advanced features (such as periodic key update). This mode is mainly used in small and static networks or when the number of IPsec peers in the network is small. A manually configured SA never ages out.
Authentication and encryption
Authentication algorithms
IPsec uses hash algorithms to perform authentication. A hash algorithm produces a fixed-length digest for an arbitrary-length message. IPsec peers respectively calculate message digests for each packet. The receiver compares the local digest with that received from the sender. If the digests are identical, the receiver considers the packet intact and the sender's identity valid. IPsec uses the Hash-based Message Authentication Code (HMAC) based authentication algorithms, including HMAC-MD5 and HMAC-SHA1. Compared with HMAC-SHA1, HMAC-MD5 is faster but less secure.
Encryption algorithms
IPsec uses symmetric encryption algorithms, which encrypt and decrypt data by using the same keys. The following encryption algorithms are available for IPsec on the device:
· DES—Encrypts a 64-bit plaintext block with a 56-bit key. DES is the least secure but the fastest algorithm.
· 3DES—Encrypts plaintext data with three 56-bit DES keys. The key length totals up to 168 bits. It provides moderate security strength and is slower than DES.
· AES—Encrypts plaintext data with a 128-bit, 192-bit, or 256-bit key. AES provides the highest security strength and is slower than 3DES.
Crypto engine
The IPsec feature is resource intensive for its complex encryption/decryption and authentication algorithms. To improve processing performance, you can use crypto engine to offload IPsec tasks.
The crypto engine processes all IPsec protected packets and hands the processed packets back to the device for forwarding.
For more information about crypto engines, see "Configuring crypto engines."
IPsec-protected traffic
IPsec tunnels can protect packets of IPv6 routing protocols.
Two peers use security policies (IPsec profiles) to protect packets between them. A security policy defines the range of packets to be protected by IPsec and the security parameters used for the protection. For more information about IPsec policies and IPsec profiles, see "IPsec profile."
The following information describes how IPsec protects packets:
· When an IPsec peer identifies the packets to be protected according to the security policy, it sets up an IPsec tunnel and sends the packet to the remote peer through the tunnel.. The IPsec tunnels are actually the IPsec SAs. The inbound packets are protected by the inbound SA, and the outbound packets are protected by the outbound SA.
· When the remote IPsec peer receives the packet, it drops, de-encapsulates, or directly forwards the packet according to the configured security policy.
IPv6 routing protocol-based IPsec
You can implement IPv6 routing protocol-based IPsec by binding an IPsec profile to an IPv6 routing protocol. All packets of the protocol are encapsulated with IPsec. Supported IPv6 routing protocols include OSPFv3, IPv6 BGP, and RIPng.
All packets of the applications that are not bound to IPsec and the IPsec packets that failed to be de-encapsulated are dropped.
In one-to-many communication scenarios, you must configure the IPsec SAs for an IPv6 routing protocol in manual mode because of the following reasons:
· The automatic key exchange mechanism protects communications between two points. In one-to-many communication scenarios, automatic key exchange cannot be implemented.
· One-to-many communication scenarios require that all the devices use the same SA parameters (SPI and key) to receive and send packets. IKE negotiated SAs cannot meet this requirement.
IPsec profile
IPsec profiles define the parameters used to establish IPsec tunnels between two peers and the range of packets to be protected.
An IPsec profile is uniquely identified by a name and does not support ACL configuration. A manual IPsec profile is used to protect IPv6 routing protocols. It specifies the IPsec transform set used for protecting data flows, and the SPIs and keys used by the SAs.
Protocols and standards
· RFC 2401, Security Architecture for the Internet Protocol
· RFC 2402, IP Authentication Header
· RFC 2406, IP Encapsulating Security Payload
· RFC 4552, Authentication/Confidentiality for OSPFv3
Restrictions and guidelines: IPsec configuration
Typically, AH and ESP use the protocol numbers 51 and 50, respectively. Make sure traffic of these protocols is not denied on the interfaces with IPsec configured.
IPsec tasks at a glance
Configuring IPsec for IPv6 routing protocols
To configure IPsec protection for IPv6 routing protocols, perform the following tasks:
1. Configuring an IPsec transform set
2. Configuring and applying a manual IPsec profile
3. (Optional.) Configuring accessibility features
¡ Configuring IPsec fragmentation
¡ Setting the maximum number of IPsec tunnels
¡ Configuring the DF bit of IPsec packets
4. (Optional.) Configuring logging and SNMP notification for IPsec.
¡ Enabling logging for IPsec packets
¡ Configuring SNMP notifications for IPsec
Configuring an IPsec transform set
About this task
An IPsec transform set defines the security parameters for IPsec SA negotiation, including the security protocol, encryption algorithms, and authentication algorithms.
Restrictions and guidelines
Changes to an IPsec transform set affect only SAs negotiated after the changes. To apply the changes to existing SAs, execute the reset ipsec sa command to clear the SAs so that they can be set up by using the updated parameters.
The transport mode applies only when the source and destination IP addresses of data flows match those of the IPsec tunnel. IPsec transform sets used in IPsec profiles for IPv6 routing protocols support only the transport mode.
You can specify multiple authentication or encryption algorithms for the same security protocol. The algorithm specified earlier has a higher priority.
Procedure
1. Enter system view.
system-view
2. Create an IPsec transform set and enter its view.
ipsec transform-set transform-set-name
3. Specify the security protocol for the IPsec transform set.
protocol { ah | ah-esp | esp }
By default, the ESP security protocol is used.
4. Specify the encryption algorithms for ESP. Skip this step if the protocol ah command is configured.
esp encryption-algorithm { 3des-cbc | aes-cbc-128 | aes-cbc-192 | aes-cbc-256 | des-cbc | null | sm4-cbc } *
By default, no encryption algorithm is specified for ESP.
5. Specify the authentication algorithms for ESP. Skip this step if the protocol ah command is configured.
esp authentication-algorithm { md5 | sha1 | sha256 | sha384 | sha512 | sm3 } *
By default, no authentication algorithm is specified for ESP.
6. Specify the authentication algorithms for AH. Skip this step if the protocol esp command is configured.
ah authentication-algorithm { md5 | sha1 | sha256 | sha384 | sha512 | sm3 } *
By default, no authentication algorithm is specified for AH.
7. Specify the packet encapsulation mode.
encapsulation-mode { transport | tunnel }
By default, the security protocol encapsulates IP packets in tunnel mode.
8. (Optional.) Enable the Extended Sequence Number (ESN) feature.
esn enable [ both ]
By default, the ESN feature is disabled.
Configuring and applying a manual IPsec profile
Manual IPsec profile configuration and application tasks at a glance
1. Configuring a manual IPsec profile
2. Applying the IPsec profile to an IPv6 routing protocol
Configuring a manual IPsec profile
About this task
A manual IPsec profile specifies the IPsec transform set used for protecting data flows, and the SPIs and keys used by the SAs.
Restrictions and guidelines
When you configure a manual IPsec profile, make sure the IPsec profile configuration at both tunnel ends meets the following requirements:
· The IPsec transform set specified in the IPsec profile at the two tunnel ends must have the same security protocol, encryption and authentication algorithms, and packet encapsulation mode.
· The local inbound and outbound IPsec SAs must have the same SPI and key.
· The IPsec SAs on the devices in the same scope must have the same key. The scope is defined by protocols. For OSPFv3, the scope consists of OSPFv3 neighbors or an OSPFv3 area. For RIPng, the scope consists of directly-connected neighbors or a RIPng process. For IPv6 BGP, the scope consists of IPv6 BGP peers or an IPv6 BGP peer group.
· The keys for the IPsec SAs at the two tunnel ends must be configured in the same format. For example, if the local end uses a key in hexadecimal format, the remote end must also use a key in hexadecimal format. If you configure a key in both the character and the hexadecimal formats, only the most recent configuration takes effect.
· If you configure a key in character format for ESP, the device automatically generates an authentication key and an encryption key for ESP.
Procedure
1. Enter system view.
system-view
2. Create a manual IPsec profile and enter its view.
ipsec profile profile-name manual
The manual keyword is not needed if you enter the view of an existing IPsec profile.
3. (Optional.) Configure a description for the IPsec profile.
description text
By default, no description is configured.
4. Specify an IPsec transform set.
transform-set transform-set-name
By default, no IPsec transform set is specified in an IPsec profile.
The specified IPsec transform set must use the transport mode.
5. Configure an SPI for an SA.
sa spi { inbound | outbound } { ah | esp } spi-number
By default, no SPI is configured for an SA.
6. Configure keys for the IPsec SA.
¡ Configure an authentication key in hexadecimal format for AH.
sa hex-key authentication { inbound | outbound } ah { cipher | simple } string
¡ Configure an authentication key in character format for AH.
sa string-key { inbound | outbound } ah { cipher | simple } string
¡ Configure a key in character format for ESP.
sa string-key { inbound | outbound } esp { cipher | simple } string
¡ Configure an authentication key in hexadecimal format for ESP.
sa hex-key authentication { inbound | outbound } esp { cipher | simple }
¡ Configure an encryption key in hexadecimal format for ESP.
sa hex-key encryption { inbound | outbound } esp { cipher | simple } string
By default, no keys are configured for the IPsec SA.
Configure a key for the security protocol (AH, ESP, or both) you have specified.
Applying the IPsec profile to an IPv6 routing protocol
For information about the configuration procedure, see IPv6 BGP, OSPFv3, and RIPng configuration in Layer 3—IP Routing Configuration Guide.
Configuring IPsec fragmentation
About this task
If you configure the device to fragment packets before IPsec encapsulation (prefragmentation), the device predetermines the encapsulated packet size before the actual encapsulation. If the encapsulated packet size exceeds the MTU of the output interface, the device fragments the packets before encapsulation. If a packet's DF bit is set, the device drops the packet and sends an ICMP error message.
Restrictions and guidelines
This feature takes effect on IPsec protected IPv4 packets.
Procedure
1. Enter system view.
system-view
2. Configure IPsec fragmentation.
ipsec fragmentation before-encryption
By default, the device fragments packets before IPsec encapsulation.
Setting the maximum number of IPsec tunnels
Restrictions and guidelines
To maximize concurrent performance of IPsec when memory is sufficient, increase the maximum number of IPsec tunnels. To ensure service availability when memory is insufficient, decrease the maximum number of IPsec tunnels.
Procedure
1. Enter system view.
system-view
2. Set the maximum number of IPsec tunnels.
ipsec limit max-tunnel tunnel-limit
The number of IPsec tunnels is not limited.
Configuring the DF bit of IPsec packets
About this task
Perform this task to configure the Don't Fragment (DF) bit in the new IP header of IPsec packets in one of the following ways:
· clear—Clears the DF bit in the new header.
· set—Sets the DF bit in the new header.
· copy—Copies the DF bit in the original IP header to the new IP header.
You can configure the DF bit in system view and interface view. The interface-view DF bit setting takes precedence over the system-view DF bit setting. If the interface-view DF bit setting is not configured, the interface uses the system-view DF bit setting.
Restrictions and guidelines for DF bit configuration for IPsec packets
The DF bit setting takes effect only in tunnel mode, and it changes the DF bit in the new IP header rather than the original IP header.
Configure the same DF bit setting on the interfaces where the same IPsec policy bound to a source interface is applied.
If the DF bit is set, the devices on the path cannot fragment the IPsec packets. To prevent IPsec packets from being discarded, make sure the path MTU is larger than the IPsec packet size. As a best practice, clear the DF bit if you cannot make sure the path MTU is larger than the IPsec packet size.
Configuring the DF bit of IPsec packets on an interface
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure the DF bit of IPsec packets on the interface.
ipsec df-bit { clear | copy | set }
By default, the interface uses the global DF bit setting.
Configuring the DF bit of IPsec packets globally
1. Enter system view.
system-view
2. Configure the DF bit of IPsec packets globally.
ipsec global-df-bit { clear | copy | set }
By default, IPsec copies the DF bit in the original IP header to the new IP header.
Enabling logging for IPsec packets
About this task
Perform this task to enable logging for IPsec packets that are discarded for reasons such as IPsec SA lookup failure, AH-ESP authentication failure, and ESP encryption failure. The log information includes the source and destination IP addresses, SPI value, and sequence number of a discarded IPsec packet, and the reason for the discard.
Procedure
1. Enter system view.
system-view
2. Enable logging for IPsec packets.
ipsec logging packet enable
By default, logging for IPsec packets is disabled.
Configuring SNMP notifications for IPsec
About this task
After you enable SNMP notifications for IPsec, the IPsec module notifies the NMS of important module events. The notifications are sent to the device's SNMP module. For the notifications to be sent correctly, you must also configure SNMP on the device. For more information about SNMP notifications, see Network Management and Monitoring Configuration Guide.
To generate and output SNMP notifications for a specific IPsec failure or event type, perform the following tasks:
1. Enable SNMP notifications for IPsec globally.
2. Enable SNMP notifications for the failure or event type.
Procedure
1. Enter system view.
system-view
2. Enable SNMP notifications for IPsec globally.
snmp-agent trap enable ipsec global
By default, SNMP notifications for IPsec are disabled.
3. Enable SNMP notifications for the specified failure or event types.
snmp-agent trap enable ipsec [ auth-failure | decrypt-failure | encrypt-failure | invalid-sa-failure | no-sa-failure | policy-add | policy-attach | policy-delete | policy-detach | tunnel-start | tunnel-stop ] *
By default, SNMP notifications for all failure and event types are disabled.
Display and maintenance commands for IPsec
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display IPsec history error information. |
display ipsec history-error |
|
Display IPsec profile information. |
display ipsec profile [ profile-name ] |
|
Display IPsec transform set information. |
display ipsec transform-set [ transform-set-name ] |
|
Display IPsec SA information. |
display ipsec sa [ brief | count | profile profile-name [ brief | count ] | remote [ ipv6 ] ip-address [ brief | count ] ] |
|
Display IPsec statistics. |
display ipsec statistics [ tunnel-id tunnel-id ] |
|
Display IPsec tunnel information. |
display ipsec tunnel [ brief | count | tunnel-id tunnel-id ] |
|
Clear IPsec history error information. |
reset ipsec history-error |
|
Clear IPsec SAs. |
reset ipsec sa [ profile profile-name | remote { ipv4-address | ipv6 ipv6-address } | spi { ipv4-address | ipv6 ipv6-address } { ah | esp } spi-num ] |
|
Clear IPsec statistics. |
reset ipsec statistics [ tunnel-id tunnel-id ] |
IPsec configuration examples
Example: Configuring IPsec for RIPng
Network configuration
As shown in Figure 4, Router A, Router B, and Router C learn IPv6 routes through RIPng.
Establish an IPsec tunnel between the routers to protect the RIPng packets transmitted in between. Specify the security protocol as ESP, the encryption algorithm as 128-bit AES, and the authentication algorithm as HMAC-SHA1 for the IPsec tunnel.
Analysis
To meet the network configuration requirements, perform the following tasks:
1. Configure basic RIPng.
For more information about RIPng configuration, see Layer 3—IP Routing Configuration Guide.
2. Configure an IPsec profile.
¡ The IPsec profiles on all the routers must have IPsec transform sets that use the same security protocol, authentication and encryption algorithms, and encapsulation mode.
¡ The SPI and key configured for the inbound SA and those for the outbound SA must be the same on each router.
¡ The SPI and key configured for the SAs on all the routers must be the same.
3. Apply the IPsec profile to a RIPng process or to an interface.
Procedure
1. Configure Router A:
# Configure IPv6 addresses for interfaces. (Details not shown.)
# Configure basic RIPng.
<RouterA> system-view
[RouterA] ripng 1
[RouterA-ripng-1] quit
[RouterA] interface ten-gigabitethernet 3/0/1
[RouterA-Ten-GigabitEthernet3/0/1] ripng 1 enable
[RouterA-Ten-GigabitEthernet3/0/1] quit
# Create and configure the IPsec transform set named tran1.
[RouterA] ipsec transform-set tran1
[RouterA-ipsec-transform-set-tran1] encapsulation-mode transport
[RouterA-ipsec-transform-set-tran1] protocol esp
[RouterA-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-128
[RouterA-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[RouterA-ipsec-transform-set-tran1] quit
# Create and configure the IPsec profile named profile001.
[RouterA] ipsec profile profile001 manual
[RouterA-ipsec-profile-manual-profile001] transform-set tran1
[RouterA-ipsec-profile-manual-profile001] sa spi outbound esp 123456
[RouterA-ipsec-profile-manual-profile001] sa spi inbound esp 123456
[RouterA-ipsec-profile-manual-profile001] sa string-key outbound esp simple abcdefg
[RouterA-ipsec-profile-manual-profile001] sa string-key inbound esp simple abcdefg
[RouterA-ipsec-profile-manual-profile001] quit
# Apply the IPsec profile to RIPng process 1.
[RouterA] ripng 1
[RouterA-ripng-1] enable ipsec-profile profile001
[RouterA-ripng-1] quit
2. Configure Router B:
# Configure IPv6 addresses for interfaces. (Details not shown.)
# Configure basic RIPng.
<RouterB> system-view
[RouterB] ripng 1
[RouterB-ripng-1] quit
[RouterB] interface ten-gigabitethernet 3/0/1
[RouterB-Ten-GigabitEthernet3/0/1] ripng 1 enable
[RouterB-Ten-GigabitEthernet3/0/1] quit
[RouterB] interface ten-gigabitethernet 3/0/2
[RouterB-Ten-GigabitEthernet3/0/2] ripng 1 enable
[RouterB-Ten-GigabitEthernet3/0/2] quit
# Create and configure the IPsec transform set named tran1.
[RouterB] ipsec transform-set tran1
[RouterB-ipsec-transform-set-tran1] encapsulation-mode transport
[RouterB-ipsec-transform-set-tran1] protocol esp
[RouterB-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-128
[RouterB-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[RouterB-ipsec-transform-set-tran1] quit
# Create and configure the IPsec profile named profile001.
[RouterB] ipsec profile profile001 manual
[RouterB-ipsec-profile-manual-profile001] transform-set tran1
[RouterB-ipsec-profile-manual-profile001] sa spi outbound esp 123456
[RouterB-ipsec-profile-manual-profile001] sa spi inbound esp 123456
[RouterB-ipsec-profile-manual-profile001] sa string-key outbound esp simple abcdefg
[RouterB-ipsec-profile-manual-profile001] sa string-key inbound esp simple abcdefg
[RouterB-ipsec-profile-manual-profile001] quit
# Apply the IPsec profile to RIPng process 1.
[RouterB] ripng 1
[RouterB-ripng-1] enable ipsec-profile profile001
[RouterB-ripng-1] quit
3. Configure Router C:
# Configure IPv6 addresses for interfaces. (Details not shown.)
# Configure basic RIPng.
<RouterC> system-view
[RouterC] ripng 1
[RouterC-ripng-1] quit
[RouterC] interface ten-gigabitethernet 3/0/1
[RouterC-Ten-GigabitEthernet3/0/1] ripng 1 enable
[RouterC-Ten-GigabitEthernet3/0/1] quit
# Create and configure the IPsec transform set named tran1.
[RouterC] ipsec transform-set tran1
[RouterC-ipsec-transform-set-tran1] encapsulation-mode transport
[RouterC-ipsec-transform-set-tran1] protocol esp
[RouterC-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-128
[RouterC-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[RouterC-ipsec-transform-set-tran1] quit
# Create and configure the IPsec profile named profile001.
[RouterC] ipsec profile profile001 manual
[RouterC-ipsec-profile-manual-profile001] transform-set tran1
[RouterC-ipsec-profile-manual-profile001] sa spi outbound esp 123456
[RouterC-ipsec-profile-manual-profile001] sa spi inbound esp 123456
[RouterC-ipsec-profile-manual-profile001] sa string-key outbound esp simple abcdefg
[RouterC-ipsec-profile-manual-profile001] sa string-key inbound esp simple abcdefg
[RouterC-ipsec-profile-manual-profile001] quit
# Apply the IPsec profile to RIPng process 1.
[RouterC] ripng 1
[RouterC-ripng-1] enable ipsec-profile profile001
[RouterC-ripng-1] quit
Verifying the configuration
After the configuration is completed, Router A, Router B, and Router C learn IPv6 routing information through RIPng. IPsec SAs are set up successfully on the routers to protect RIPng packets. This example uses Router A to verify the configuration.
# Display the RIPng configuration. The output shows that IPsec profile profile001 has been applied to RIPng process 1.
[RouterA] display ripng 1
RIPng process : 1
Preference : 100
Checkzero : Enabled
Default Cost : 0
Maximum number of load balanced routes : 8
Update time : 30 secs Timeout time : 180 secs
Suppress time : 120 secs Garbage-Collect time : 120 secs
Update output delay: 20(ms) Output count: 3
Graceful-restart interval: 60 secs
Triggered Interval : 5 50 200
Number of periodic updates sent : 186
Number of triggered updates sent : 1
IPsec profile name: profile001
# Display the established IPsec SAs.
[RouterA] display ipsec sa
-------------------------------
Global IPsec SA
-------------------------------
-----------------------------
IPsec profile: profile001
Mode: Manual
-----------------------------
Encapsulation mode: transport
[Inbound ESP SA]
SPI: 123456 (0x3039)
Connection ID: 90194313219
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
No duration limit for this SA
[Outbound ESP SA]
SPI: 123456 (0x3039)
Connection ID: 64424509441
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
No duration limit for this SA