- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 04-EVPN L3VPN configuration | 237.82 KB |
Contents
Restrictions and guidelines: EVPN L3VPN configuration
Configuring an EVPN L3VPN network
Enabling MPLS encapsulation for IP prefix advertisement routes
Enabling EVPN to advertise VPN routes
Enabling communication between EVPN L3VPN and MPLS L3VPN
About communication between EVPN L3VPN and MPLS L3VPN
Enabling BGP VPNv4 or VPNv6 route advertisement for the BGP EVPN address family
Enabling BGP EVPN route advertisement for the BGP VPNv4 or VPNv6 address family
Display and maintenance commands for EVPN L3VPN
EVPN L3VPN configuration examples
Example: Configuring IPv4 EVPN L3VPN (SR-MPLS BE public tunnel)
Configuring EVPN L3VPN
About EVPN L3VPN
EVPN supports using MPLS L3VPN for traffic forwarding in the data plane, which is called EVPN L3VPN. EVPN L3VPN provides fast deployment of Layer 2 networks and can convey both Layer 2 and Layer 3 VPN services. In an EVPN L3VPN network, VPN routes are advertised through IP prefix advertisement routes.
Route advertisement
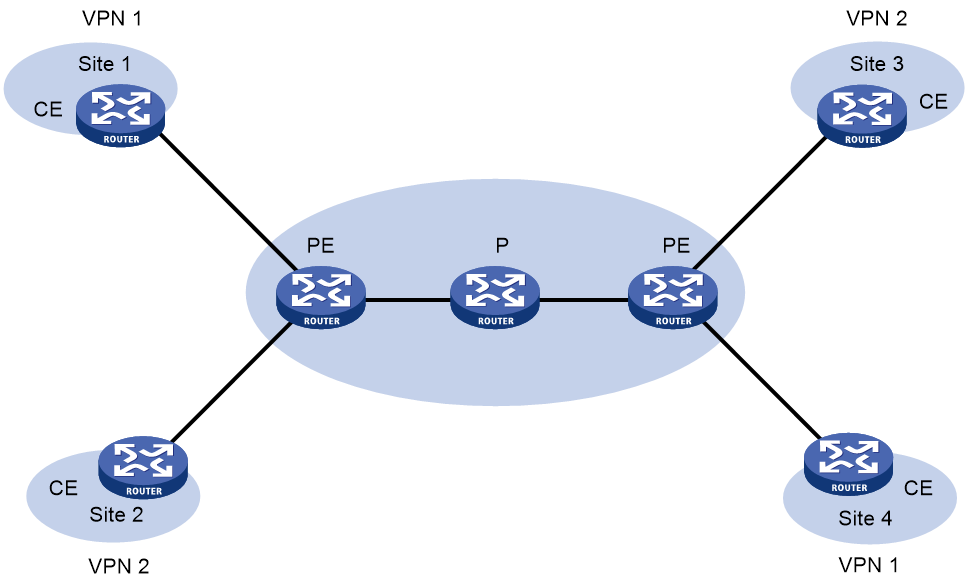
As shown in Figure 1, in an EVPN L3VPN network, CEs and PEs advertises VPN routing information. P routers maintain only the routes within the backbone. A PE maintains only routing information for directly connected VPNs, rather than for all VPNs.
VPN routing information is advertised through the path local CE—ingress PE—egress PE—remote CE.
Figure 1 EVPN L3VPN network model
Route advertisement from the local CE to the ingress PE
The CE advertises standard IPv4 or IPv6 routing information to the ingress PE over a static route, RIP route, OSPF route, IS-IS route, EBGP route, or IBGP route.
Route advertisement from the ingress PE to the egress PE
The ingress PE performs the following operations:
1. Adds RDs and route target attributes to these standard IPv4 or IPv6 routes to create VPN-IPv4 or VPN-IPv6 routes.
2. Assigns MPLS private network labels to the routes to create IP prefix advertisement routes.
3. Advertises the IP prefix advertisement routes to the egress PE.
The egress PE then adds the IP prefix advertisement routes to the routing table of the VPN instance of which an import target matches an export target of the routes.
Route advertisement from the egress PE to the remote CE
The remote CE learns VPN routes from the egress PE through static routes, RIP routes, OSPF routes, IS-IS routes, EBGP routes, or IBGP routes.
Traffic forwarding
In an EVPN L3VPN network, a PE adds the following information into VPN packets:
· Outer tag—Identifies the public tunnel from the local PE to the remote PE. Based on the outer tag, a VPN packet can be forwarded along the public tunnel to the remote PE. The public tunnel can be an LSP, an MPLS TE tunnel, a GRE tunnel, an SR-MPLS BE tunnel, an SR-MPLS TE tunnel, or an SR-MPLS TE policy tunnel. For a GRE public tunnel, the outer tag is the GRE encapsulation. For an LSP, an MPLS TE tunnel, an SR-MPLS BE tunnel, an SR-MPLS TE tunnel, or an SR-MPLS TE policy tunnel, the outer tag is an MPLS label.
· Inner label—Identifies the remote site. The remote PE uses the inner label to forward packets to the target site of the matching VPN instance. PEs advertise the inner labels assigned to private network routes when advertising BGP EVPN routes.
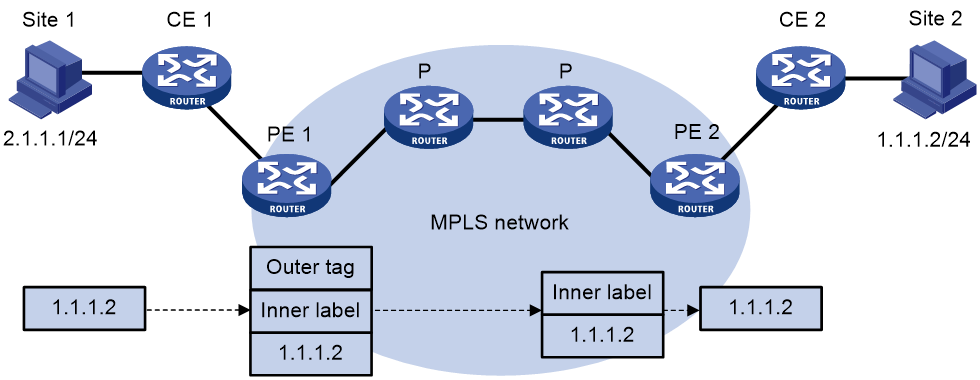
Figure 2 EVPN L3VPN traffic forwarding
As shown in Figure 2, a VPN packet is forwarded from Site 1 to Site 2 by using the following process:
1. Site 1 sends an IP packet with the destination address 1.1.1.2. CE 1 transmits the packet to PE 1.
2. PE 1 performs the following operations:
a. Finds the matching VPN route based on the inbound interface and destination address of the packet.
b. Labels the packet with both the inner label and the outer tag.
c. Forwards the packet to the public tunnel.
3. P devices forward the packet to PE 2 by the outer tag.
¡ If the outer tag is an MPLS label, the label is removed from the packet at the penultimate hop.
¡ If the outer tag is GRE encapsulation, PE 2 removes the GRE encapsulation.
4. PE 2 performs the following operations:
a. Uses the inner label to find the matching VPN instance to which the destination address of the packet belongs.
b. Looks up the routing table of the VPN instance for the outgoing interface.
c. Removes the inner label and forwards the packet out of the interface to CE 2.
5. CE 2 transmits the packet to the destination through IP forwarding.
When two sites of a VPN are connected to the same PE, the PE directly forwards packets between the two sites through the VPN routing table without adding any tag or label.
Restrictions and guidelines: EVPN L3VPN configuration
The device supports only SR-MPLS BE, SR-MPLS TE, SRv6 BE, and SRv6 TE tunnels to carry EVPN L3VPN services. For more information about these tunnels, see Segment Routing Configuration Guide.
EVPN L3VPN tasks at a glance
To configure EVPN L3VPN, perform the following tasks:
1. Configuring basic MPLS L3VPN features
¡ Configuring a VPN instance
¡ Configuring routing between a PE and a CE
For more information about configuration of basic MPLS L3VPN features, see MPLS L3VPN configuration in MPLS Configuration Guide.
2. Configuring an EVPN L3VPN network
¡ Enabling MPLS encapsulation for IP prefix advertisement routes
¡ Enabling EVPN to advertise VPN routes
3. Enabling communication between EVPN L3VPN and MPLS L3VPN
¡ Enabling BGP VPNv4 or VPNv6 route advertisement for the BGP EVPN address family
¡ Enabling BGP EVPN route advertisement for the BGP VPNv4 or VPNv6 address family
4. (Optional.) Configuring BGP EVPN FRR
Configuring an EVPN L3VPN network
Enabling MPLS encapsulation for IP prefix advertisement routes
About this task
By default, a PE advertises IP prefix advertisement routes with VXLAN encapsulation to peers and peer groups. In an EVPN L3VPN network, you must perform this task for PEs to advertise VPN routes through IP prefix advertisement routes.
Restrictions and guidelines
Perform this task on the edge nodes of the EVPN L3VPN network and RRs.
Procedure
1. Enter system view.
system-view
2. Enable a BGP instance and enter BGP instance view.
bgp as-number [ instance instance-name ]
By default, BGP is disabled and no BGP instances exist.
3. Specify remote PEs as BGP peers.
peer { group-name | ipv4-address [ mask-length ] | ipv6-address [ prefix-length ] } as-number as-number
4. Enter BGP EVPN address family view.
address-family l2vpn evpn
5. Enable MPLS encapsulation for the IP prefix advertisement routes advertised to a peer or peer group.
peer { group name | ipv4-address [ mask-length ] | ipv6-address [ prefix-length ] } advertise encap-type mpls
By default, IP prefix advertisement routes use VXLAN encapsulation.
Enabling EVPN to advertise VPN routes
About this task
This feature enables devices to exchange the routes of a VPN instance by using IP prefix advertisement routes with MPLS encapsulation. After you enable this feature for a VPN instance, the device advertises the routes of the VPN instance through IP prefix advertisement routes. When receiving IP prefix advertisement routes with MPLS encapsulation, the device adds the routes that belong to the VPN instance to the routing table.
Procedure
1. Enter system view.
system-view
2. Enter VPN instance view.
ip vpn-instance vpn-instance-name
3. Enter VPN instance IPv4 or IPv6 unicast address family view.
¡ Enter VPN instance IPv4 unicast address family view.
address-family ipv4 unicast
¡ Enter VPN instance IPv6 unicast address family view.
address-family ipv6 unicast
4. Enable EVPN to advertise the routes of the VPN instance.
evpn mpls routing-enable
By default, EVPN does not advertise the routes of VPN instances.
Enabling communication between EVPN L3VPN and MPLS L3VPN
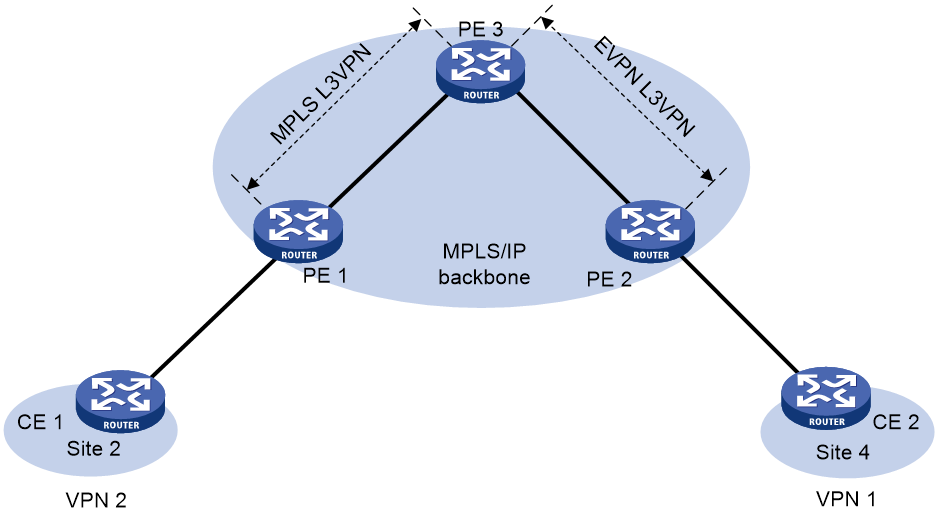
About communication between EVPN L3VPN and MPLS L3VPN
As shown in Figure 3, when you configure an L3VPN network to convey EVPN service, perform the following tasks on PE 3 to enable communication between EVPN L3VPN and MPLS L3VPN:
· Enable BGP VPNv4 or VPNv6 route advertisement for the BGP EVPN address family.
· Enable BGP EVPN route advertisement for the BGP VPNv4 or VPNv6 address family.
Figure 3 Communication between MPLS L3VPN and EVPN L3VPN
Enabling BGP VPNv4 or VPNv6 route advertisement for the BGP EVPN address family
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP EVPN address family view.
address-family l2vpn evpn
4. Enable BGP VPNv4 or VPNv6 route advertisement for the BGP EVPN address family.
advertise l3vpn route [ replace-rt ][ advertise-policy policy-name ]
By default, BGP VPNv4 or VPNv6 routes are not advertised through the BGP EVPN address family.
Enabling BGP EVPN route advertisement for the BGP VPNv4 or VPNv6 address family
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv4 address family view or BGP VPNv6 address family view.
address-family { vpnv4 | vpnv6 }
4. Enable BGP EVPN route advertisement for the BGP VPNv4 or VPNv6 address family.
advertise evpn route [ replace-rt ][ advertise-policy policy-name ]
By default, BGP EVPN routes are not advertised through the BGP VPNv4 or VPNv6 address family.
After you execute this command, the device advertises IP prefix advertisement routes and MAC/IP advertisement routes that contain host route information through the BGP VPNv4 or VPNv6 address family.
Configuring BGP EVPN FRR
About this task
BGP EVPN FRR enables the device to calculate backup routes for all routes of the BGP EVPN address family to reduce the traffic interruption caused by link or device failures on the MPLS or IP backbone. If the device learns two unequal-cost routes destined for the same network from different peers, the optimal route is backed up by the other route. When the optimal route becomes unavailable, the device uses the backup route to forward traffic. At the same time, the device calculates a new optimal route and then uses it to direct traffic forwarding.
Restrictions and guidelines
This feature might cause routing loops in certain conditions. Make sure you are fully aware of this feature when you use it on a live network.
Procedure
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP EVPN address family view.
address-family l2vpn evpn
4. Enable BGP EVPN FRR.
pic
By default, BGP EVPN FRR is disabled.
For more information about this command, see BGP commands in Layer 3—IP Routing Command Reference.
Display and maintenance commands for EVPN L3VPN
Execute display commands in any view.
|
Task |
Command |
|
Display incoming labels for IP prefix advertisement routes. |
display bgp [ instance instance-name ] l2vpn evpn inlabel |
|
Display BGP VPNv4 peer group information. |
display bgp [ instance instance-name ] group vpnv4 [ vpn-instance vpn-instance-name ] [ group-name group-name ] |
|
Display BGP VPNv6 peer group information. |
display bgp [ instance instance-name ] group vpnv6 [ group-name group-name ] |
|
Display BGP VPNv4 peer information. |
display bgp [ instance instance-name ] peer vpnv4 [ vpn-instance vpn-instance-name ] [ ipv4-address mask-length | { ipv4-address | group-name group-name } log-info | [ ipv4-address ] verbose ] |
|
Display BGP VPNv6 peer information. |
display bgp [ instance instance-name ] peer vpnv6 [ ipv4-address mask-length | { ipv4-address | group-name group-name } log-info | [ ipv4-address ] verbose ] |
|
Display BGP VPNv4 routes. |
display bgp [ instance instance-name ] routing-table vpnv4 [ [ route-distinguisher route-distinguisher ] [ ipv4-address [ { mask-length | mask } [ longest-match ] ] | ipv4-address [ mask-length | mask ] advertise-info | as-path-acl as-path-acl-number | community-list { { basic-community-list-number | comm-list-name } [ whole-match ] | adv-community-list-number } ] | [ vpn-instance vpn-instance-name ] peer ipv4-address { advertised-routes | received-routes } [ ipv4-address [ mask-length | mask ] | statistics ] | statistics ] |
|
Display BGP VPNv6 routes. |
display bgp [ instance instance-name ] routing-table vpnv6 [ [ route-distinguisher route-distinguisher ] [ ipv6-address prefix-length [ advertise-info ] | as-path-acl as-path-acl-number | community-list { { basic-community-list-number | comm-list-name } [ whole-match ] | adv-community-list-number } ] | peer ipv4-address { advertised-routes | received-routes } [ ipv6-address prefix-length | statistics ] | statistics ] |
|
Display routing table information for a VPN instance. |
display ip routing-table vpn-instance vpn-instance-name [ statistics | verbose ] |
|
Display information about VPN instances. |
display ip vpn-instance [ instance-name vpn-instance-name ] |
|
|
NOTE: For more information about the display ip routing-table vpn-instance command, see IP routing basics commands in Layer 3—IP Routing Command Reference. |
|
|
NOTE: For more information about the following commands, see MPLS L3VPN commands in MPLS Command Reference: · display bgp group vpnv4. · display bgp peer vpnv4. · display bgp routing-table vpnv4. · display ip vpn-instance |
EVPN L3VPN configuration examples
Example: Configuring IPv4 EVPN L3VPN (SR-MPLS BE public tunnel)
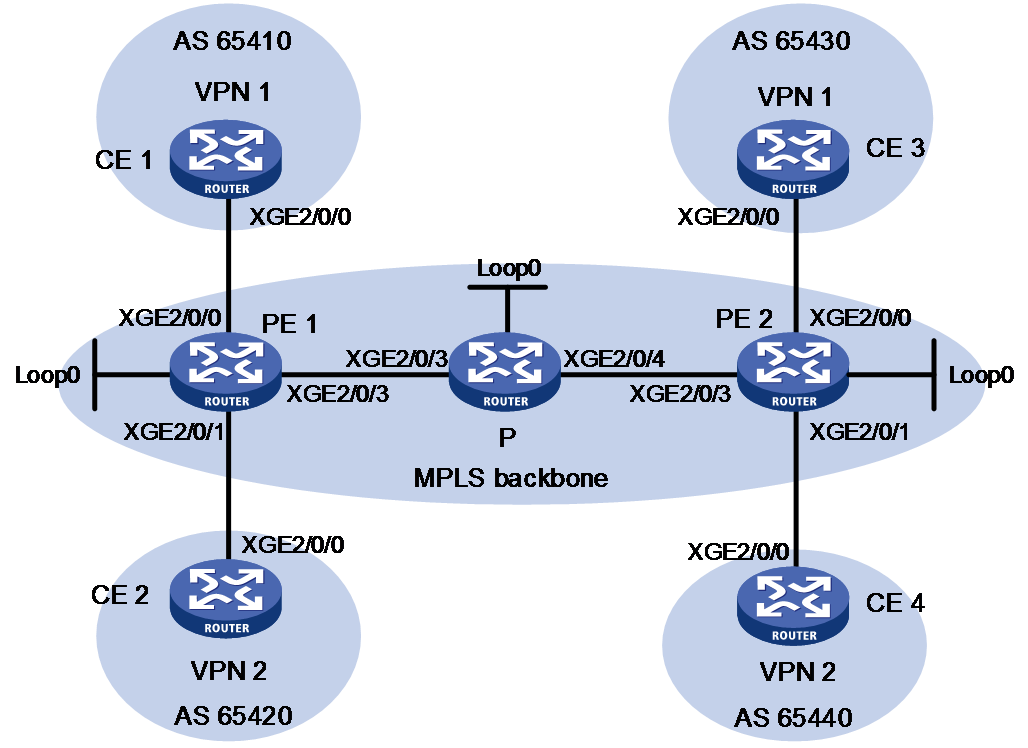
Network configuration
As shown in Figure 4:
· Configure IPv4 EVPN L3VPN for different sites of a VPN instance to communicate with each other.
· Configure route target 111:1 for VPN 1 and route target 222:2 for VPN 2 to isolate these VPN instances.
· Configure the CE and the PE of each site to use EBGP to exchange VPN routes.
· Configure the PEs to communicate through IS-IS and to exchange BGP EVPN routes through MP-IBGP.
· Configure SR MPLS on PE 1, P, and PE 2 and use an SR-MPLS BE tunnel as the public tunnel.
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
XGE2/0/0 |
10.1.1.1/24 |
P |
Loop0 |
2.2.2.9/32 |
|
PE 1 |
Loop0 |
1.1.1.9/32 |
|
XGE2/0/3 |
172.1.1.2/24 |
|
|
XGE2/0/0 |
10.1.1.2/24 |
|
XGE2/0/4 |
172.2.1.1/24 |
|
|
XGE2/0/1 |
10.2.1.2/24 |
PE 2 |
Loop0 |
3.3.3.9/32 |
|
|
XGE2/0/3 |
172.1.1.1/24 |
|
XGE2/0/0 |
10.3.1.2/24 |
|
CE 2 |
XGE2/0/0 |
10.2.1.1/24 |
|
XGE2/0/1 |
10.4.1.2/24 |
|
CE 3 |
XGE2/0/0 |
10.3.1.1/24 |
|
XGE2/0/3 |
172.2.1.2/24 |
|
CE 4 |
XGE2/0/0 |
10.4.1.1/24 |
|
|
|
Procedure
1. Configure an IGP on the MPLS backbone for the PEs and P device to reach one another:
# Configure PE 1.
<PE1> system-view
[PE1] isis 1
[PE1-isis-1] network-entity 00.0000.0000.0001.00
[PE1-isis-1] cost-style wide
[PE1-isis-1] quit
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 1.1.1.9 32
[PE1-LoopBack0] isis enable 1
[PE1-LoopBack0] quit
[PE1] interface ten-gigabitethernet 2/0/3
[PE1-Ten-GigabitEthernet2/0/3] ip address 172.1.1.1 24
[PE1-Ten-GigabitEthernet2/0/3] isis enable 1
[PE1-Ten-GigabitEthernet2/0/3] quit
# Configure P.
<P> system-view
[P] isis 1
[P-isis-1] network-entity 00.0000.0000.0002.00
[P-isis-1] cost-style wide
[P-isis-1] quit
[P] interface loopback 0
[P-LoopBack0] ip address 2.2.2.9 32
[P-LoopBack0] isis enable 1
[P-LoopBack0] quit
[P] interface ten-gigabitethernet 2/0/3
[P-Ten-GigabitEthernet2/0/3] ip address 172.1.1.2 24
[P-Ten-GigabitEthernet2/0/3] isis enable 1
[P-Ten-GigabitEthernet2/0/3] quit
[P] interface ten-gigabitethernet 2/0/4
[P-Ten-GigabitEthernet2/0/4] ip address 172.2.1.1 24
[P-Ten-GigabitEthernet2/0/4] isis enable 1
[P-Ten-GigabitEthernet2/0/4] quit
# Configure PE 2.
<PE2> system-view
[PE2] isis 1
[PE2-isis-1] network-entity 00.0000.0000.0003.00
[PE2-isis-1] cost-style wide
[PE2-isis-1] quit
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 3.3.3.9 32
[PE2-LoopBack0] isis enable 1
[PE2-LoopBack0] quit
[PE2] interface ten-gigabitethernet 2/0/3
[PE2-Ten-GigabitEthernet2/0/3] ip address 172.2.1.2 24
[PE2-Ten-GigabitEthernet2/0/3] isis enable 1
[PE2-Ten-GigabitEthernet2/0/3] quit
# Execute the display isis peer command to verify that IS-IS neighbor relationships have been established between PE 1, P, and PE 2. Execute the display ip routing-table command to verify that the PEs have learned the routes to the loopback interfaces of each other. (Details not shown.)
2. Configure basic MPLS and MPLS TE capabilities on the MPLS backbone:
# Configure PE 1.
[PE1] mpls lsr-id 1.1.1.9
[PE1] mpls te
[PE1-te] quit
[PE1] interface ten-gigabitethernet 2/0/3
[PE1-Ten-GigabitEthernet2/0/3] mpls enable
[PE1-Ten-GigabitEthernet2/0/3] mpls te enable
[PE1-Ten-GigabitEthernet2/0/3] quit
# Configure P.
[P] mpls lsr-id 2.2.2.9
[P] mpls te
[P-te] quit
[P] interface ten-gigabitethernet 2/0/3
[P-Ten-GigabitEthernet2/0/3] mpls enable
[P-Ten-GigabitEthernet2/0/3] mpls te enable
[P-Ten-GigabitEthernet2/0/3] quit
[P] interface ten-gigabitethernet 2/0/4
[P-Ten-GigabitEthernet2/0/4] mpls enable
[P-Ten-GigabitEthernet2/0/4] mpls te enable
[P-Ten-GigabitEthernet2/0/4] quit
# Configure PE 2.
[PE2] mpls lsr-id 3.3.3.9
[PE2] mpls te
[PE2-te] quit
[PE2] interface ten-gigabitethernet 2/0/3
[PE2-Ten-GigabitEthernet2/0/3] mpls enable
[PE2-Ten-GigabitEthernet2/0/3] mpls te enable
[PE2-Ten-GigabitEthernet2/0/3] quit
3. Configure VPN instances on PEs to allow CE access:
# Configure PE 1.
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 100:1
[PE1-vpn-instance-vpn1] vpn-target 111:1
[PE1-vpn-instance-vpn1] quit
[PE1] ip vpn-instance vpn2
[PE1-vpn-instance-vpn2] route-distinguisher 100:2
[PE1-vpn-instance-vpn2] vpn-target 222:2
[PE1-vpn-instance-vpn2] quit
[PE1] interface ten-gigabitethernet 2/0/0
[PE1-Ten-GigabitEthernet2/0/0] ip binding vpn-instance vpn1
[PE1-Ten-GigabitEthernet2/0/0] ip address 10.1.1.2 24
[PE1-Ten-GigabitEthernet2/0/0] quit
[PE1] interface ten-gigabitethernet 2/0/1
[PE1-Ten-GigabitEthernet2/0/1] ip binding vpn-instance vpn2
[PE1-Ten-GigabitEthernet2/0/1] ip address 10.2.1.2 24
[PE1-Ten-GigabitEthernet2/0/1] quit
# Configure PE 2.
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] route-distinguisher 200:1
[PE2-vpn-instance-vpn1] vpn-target 111:1
[PE2-vpn-instance-vpn1] quit
[PE2] ip vpn-instance vpn2
[PE2-vpn-instance-vpn2] route-distinguisher 200:2
[PE2-vpn-instance-vpn2] vpn-target 222:2
[PE2-vpn-instance-vpn2] quit
[PE2] interface ten-gigabitethernet 2/0/0
[PE2-Ten-GigabitEthernet2/0/0] ip binding vpn-instance vpn1
[PE2-Ten-GigabitEthernet2/0/0] ip address 10.3.1.2 24
[PE2-Ten-GigabitEthernet2/0/0] quit
[PE2] interface ten-gigabitethernet 2/0/1
[PE2-Ten-GigabitEthernet2/0/1] ip binding vpn-instance vpn2
[PE2-Ten-GigabitEthernet2/0/1] ip address 10.4.1.2 24
[PE2-Ten-GigabitEthernet2/0/1] quit
# Configure IP addresses for the CEs according to Figure 4. (Details not shown.)
# Execute the display ip vpn-instance command on the PEs to display the configuration of the VPN instance, for example, on PE 1.
[PE1] display ip vpn-instance
Total VPN-Instances configured : 2
Total IPv4 VPN-Instances configured : 0
Total IPv6 VPN-Instances configured : 0
Total IPv4 VPN-Instances EVPN configured : 0
Total IPv6 VPN-Instances EVPN configured : 0
VPN-Instance Name RD Address family Create time
vpn1 100:1 N/A 2018/12/13 12:49:08
vpn2 100:2 N/A 2018/12/13 12:49:20
# Use the ping command on the PEs to verify that the PEs can ping their attached CEs, for example, on PE 1.
[PE1] ping -vpn-instance vpn1 10.1.1.1
Ping 10.1.1.1 (10.1.1.1): 56 data bytes, press CTRL_C to break
56 bytes from 10.1.1.1: icmp_seq=0 ttl=255 time=1.000 ms
56 bytes from 10.1.1.1: icmp_seq=1 ttl=255 time=2.000 ms
56 bytes from 10.1.1.1: icmp_seq=2 ttl=255 time=0.000 ms
56 bytes from 10.1.1.1: icmp_seq=3 ttl=255 time=1.000 ms
56 bytes from 10.1.1.1: icmp_seq=4 ttl=255 time=0.000 ms
--- Ping statistics for 10.1.1.1 in VPN instance vpn1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/0.800/2.000/0.748 ms
4. Establish EBGP peer relationships between PEs and CEs, and redistribute VPN routes into BGP:
# Configure CE 1.
<CE1> system-view
[CE1] bgp 65410
[CE1-bgp-default] peer 10.1.1.2 as-number 100
[CE1-bgp-default] address-family ipv4 unicast
[CE1-bgp-default-ipv4] peer 10.1.1.2 enable
[CE1-bgp-default-ipv4] import-route direct
[CE1-bgp-default-ipv4] quit
[CE1-bgp-default] quit
# Configure the other three CEs in the same way CE 1 is configured. (Details not shown.)
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp-default] ip vpn-instance vpn1
[PE1-bgp-default-vpn1] peer 10.1.1.1 as-number 65410
[PE1-bgp-default-vpn1] address-family ipv4 unicast
[PE1-bgp-default-ipv4-vpn1] peer 10.1.1.1 enable
[PE1-bgp-default-ipv4-vpn1] quit
[PE1-bgp-default-vpn1] quit
[PE1-bgp-default] ip vpn-instance vpn2
[PE1-bgp-default-vpn2] peer 10.2.1.1 as-number 65420
[PE1-bgp-default-vpn2] address-family ipv4 unicast
[PE1-bgp-default-ipv4-vpn2] peer 10.2.1.1 enable
[PE1-bgp-default-ipv4-vpn2] quit
[PE1-bgp-default-vpn1] quit
[PE1-bgp-default] quit
# Configure PE 2 in the same way PE 1 is configured. (Details not shown.)
# Execute the display bgp peer ipv4 vpn-instance command on the PEs to verify that a BGP peer relationship in Established state has been established between a PE and a CE. (Details not shown.)
5. Create an MP-IBGP peer relationship between PEs:
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp-default] peer 3.3.3.9 as-number 100
[PE1-bgp-default] peer 3.3.3.9 connect-interface loopback 0
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 3.3.3.9 enable
[PE1-bgp-default-evpn] quit
[PE1-bgp-default] quit
# Configure PE 2.
[PE2] bgp 100
[PE2-bgp-default] peer 1.1.1.9 as-number 100
[PE2-bgp-default] peer 1.1.1.9 connect-interface loopback 0
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 1.1.1.9 enable
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] quit
# Execute the display bgp peer l2vpn evpn command on the PEs to verify that a BGP peer relationship in Established state has been established between the PEs. (Details not shown.)
6. Enable EVPN to advertise VPN routes on the PEs:
# Configure PE 1.
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] address-family ipv4
[PE1-vpn-ipv4-vpn1] evpn mpls routing-enable
[PE1-vpn-ipv4-vpn1] quit
[PE1-vpn-instance-vpn1] quit
[PE1] ip vpn-instance vpn2
[PE1-vpn-instance-vpn2] address-family ipv4
[PE1-vpn-ipv4-vpn2] evpn mpls routing-enable
[PE1-vpn-ipv4-vpn2] quit
[PE1-vpn-instance-vpn2] quit
# Configure PE 2.
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] address-family ipv4
[PE2-vpn-ipv4-vpn1] evpn mpls routing-enable
[PE2-vpn-ipv4-vpn1] quit
[PE2-vpn-instance-vpn1] quit
[PE2] ip vpn-instance vpn2
[PE2-vpn-instance-vpn2] address-family ipv4
[PE2-vpn-ipv4-vpn2] evpn mpls routing-enable
[PE2-vpn-ipv4-vpn2] quit
[PE2-vpn-instance-vpn2] quit
# Execute the display bgp l2vpn evpn command on the PEs to verify that the VPN routes received from CEs have been added to the EVPN routing table. (Details not shown.)
7. Enable MPLS encapsulation for the IP prefix advertisement routes on the PEs:
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 3.3.3.9 advertise encap-type mpls
[PE1-bgp-default-evpn] peer 3.3.3.9 next-hop-local
[PE1-bgp-default-evpn] quit
[PE1-bgp-default] quit
# Configure PE 2.
[PE2] bgp 100
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 1.1.1.9 advertise encap-type mpls
[PE2-bgp-default-evpn] peer 1.1.1.9 next-hop-local
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] quit
# Execute the display bgp l2vpn evpn command to verify that the PEs have received IP prefix advertisement routes from one another.
8. Configure the MPLS SRGB and enable MPLS TE for IS-IS process 1, enable SR-MPLS in IS-IS IPv4 unicast address family view, and configure an IS-IS prefix SID on Loopback 0:
# Configure PE 1.
[PE1] isis 1
[PE1-isis-1] mpls te enable
[PE1-isis-1] segment-routing global-block 16000 16999
[PE1-isis-1] address-family ipv4
[PE1-isis-1-ipv4] segment-routing mpls
[PE1-isis-1-ipv4] quit
[PE1-isis-1] quit
[PE1] interface loopback 0
[PE1-LoopBack0] isis prefix-sid index 10
[PE1-LoopBack0] quit
# Configure P.
[P] isis 1
[P-isis-1] mpls te enable
[P-isis-1] segment-routing global-block 17000 17999
[P-isis-1] address-family ipv4
[P-isis-1-ipv4] segment-routing mpls
[P-isis-1-ipv4] quit
[P-isis-1] quit
[P] interface loopback 0
[P-LoopBack1] isis prefix-sid index 20
[P-LoopBack1] quit
# Configure PE 2.
[PE2] isis 1
[PE2-isis-1] mpls te enable
[PE2-isis-1] segment-routing global-block 18000 18999
[PE2-isis-1] address-family ipv4
[PE2-isis-1-ipv4] segment-routing mpls
[PE2-isis-1-ipv4] quit
[PE2-isis-1] quit
[PE2] interface loopback 0
[PE2-LoopBack0] isis prefix-sid index 30
[PE2-LoopBack0] quit
9. Configure a tunnel policy on the PEs to enable EVPN L3VPN to preferentially select an SR-MPLS BE tunnel as the public tunnel:
# Configure PE 1.
[PE1] tunnel-policy srbe
[PE1-tunnel-policy-srbe] select-seq sr-lsp load-balance-number 1
[PE1-tunnel-policy-srbe] quit
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] tnl-policy srbe
[PE1-vpn-instance-vpn1] quit
[PE1] ip vpn-instance vpn2
[PE1-vpn-instance-vpn2] tnl-policy srbe
[PE1-vpn-instance-vpn2] quit
# Configure PE 2.
[PE2] tunnel-policy srbe
[PE2-tunnel-policy-srbe] select-seq sr-lsp load-balance-number 1
[PE2-tunnel-policy-srbe] quit
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] tnl-policy srbe
[PE2-vpn-instance-vpn1] quit
[PE2] ip vpn-instance vpn2
[PE2-vpn-instance-vpn2] tnl-policy srbe
[PE2-vpn-instance-vpn2] quit
Verifying the configuration
# Verify that a PE has the route to the remote CE in the same VPN instance, for example, PE 1.
[PE1] display ip routing-table vpn-instance vpn1
Destinations : 11 Routes : 11
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.0/24 Direct 0 0 10.1.1.2 XGE2/0/0
10.1.1.0/32 Direct 0 0 10.1.1.2 XGE2/0/0
10.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.255/32 Direct 0 0 10.1.1.2 XGE2/0/0
10.3.1.0/24 BGP 255 0 3.3.3.9 XGE2/0/3
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Verify that a PE has the FIB entry to the remote CE in the same VPN instance, for example, PE 1. In the entry, the private label is 1150 and the public tunnel is the tunnel with NHLFE ID 1.
[PE1] display fib vpn-instance vpn1 10.3.1.0
FIB entry count: 1
Flag:
U:Usable G:Gateway H:Host B:Blackhole D:Dynamic S:Static
R:Relay F:FRR
Destination/Mask Nexthop Flag OutInterface/Token Label
10.3.1.0/24 3.3.3.9 UGR 1 1150
# Display NHLFE entry information on a PE, for example, PE 1. Verify that the tunnel with NHLFE ID 1 is an SRLSP, which indicates that the public tunnel is an SR-MPLS BE tunnel.
[PE1] display mpls forwarding nhlfe 1
Flags: T - Forwarded through a tunnel
N - Forwarded through the outgoing interface to the nexthop IP address
B - Backup forwarding information
A - Active forwarding information
M - P2MP forwarding information
NID Tnl-Type Flag OutLabel Forwarding Info
--------------------------------------------------------------------------------
1 SRLSP NA 17030 XGE2/0/3 172.1.1.2
# Verify that CEs of the same VPN can ping each other, and CEs of different VPNs cannot. For example, CE 1 can ping CE 3 (10.3.1.1), but it cannot ping CE 4 (10.4.1.1). (Details not shown.)