- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Text | 1.13 MB |
Contents
Operating environment configuration
Running the license server on the CentOS or H3Linux operating system
Permitting license server's ports, address, and protocol
Uninstalling the license server
Without changes on the operating system or hardware
With changes on the operating system or hardware
Running the license server on the Ubuntu/Linx operating system
Uploading the license server installation package
Installing the license server on the server
Permitting license server's ports, address, and protocol
Uninstalling the license server
Without changes on the operating system or hardware
With changes on the operating system or hardware
Logging in to the license server
Deploying a license server HA cluster
How to change the hardware after a license is installed?
How can I change the IP of the license server after the license server has been deployed?
Changing the physical IP of the license server in standalone deployment
Changing the physical IP of one or both of the license server nodes in an HA cluster
Changing the virtual IP of a license server HA cluster
Changing the IP during switching from standalone mode to HA mode
Can licenses continue to be used after the license server is uninstalled and reinstalled?
Overview
H3C license server is license management software developed by H3C. It provides centralized management on licensing, licensing for services on the network, and HA. This product simplifies licensing workflow and automates services licensing.
The license server provides the following features:
· Allows you to apply for licenses based on the hardware of the server where the license server resides.
· Allows you to install and store the licenses on the license server.
· Supports licensing service backup, which avoids service interruption.
Preparing for installation
Network requirements
Before you install a license server, plan your network. Make sure the server where the license server resides is accessible in the network.
Server requirements
Hardware requirements
For a license server to function correctly, install the license server on a physical server.
Table 1 shows the recommended and minimum hardware requirements for a server to host the license server.
Table 1 Recommended and minimum hardware requirements
|
Item |
CPU architecture |
CPU |
Memory |
Disk |
NIC |
Remarks |
|
Recommended configuration |
x86-64(Intel64/AMD64) |
16 cores, 2.0 GHz or above |
32 GB or above |
64 GB or above for the system partition where the root directory resides |
1 to 10 Gbps |
Supports a maximum of 2000 clients |
|
Minimum configuration |
x86-64(Intel64/AMD64) |
2 cores or above 2.0 GHz or above |
4 GB or above |
64 GB or above for the system partition where the root directory resides |
1 to 10 Gbps |
Supports a maximum of 20 client |
Software requirements
The server to host a license server must be installed with the following operating systems:
· CentOS 7.3 1611 64-bit (DVD) operating system.
· H3Linux Release 1.1.2 (kernel 3.10/4.14) operating system.
· Linx-6.0.80 64-bit operating system.
· Ubuntu-20.04 64-bit operating system.
Web browser requirements
You can log in to the license server through a Web browser.
The license server supports the following Web browsers:
· Google Chrome 27 and later.
· Internet Explorer 9 and later.
Operating environment configuration
Disabling SELinux
1. Edit the configuration file.
vi /etc/selinux/config
2. Set SELINUX to disabled.
SELINUX=disabled
3. Save the settings. Then exit and restart the system.
Running the license server on the CentOS or H3Linux operating system
Installing the license server
You can install the license server by using the following methods:
· Installing an .rpm file—Install the license server installation package in RPM format. This method installs only the license server, so you need to first install the operating system.
· Installing an .iso file—Install the license server installation package in ISO format. This method installs both the H3Linux operating system and the license server.
Installing an .rpm file
Restrictions and guidelines
Both the root user and non-root users of the operating system can install an .rpm file on the server. As a best practice, log in as the root user and install the .rpm file.
To allow non-root users to install an .rpm file, perform the following tasks:
1. In root user view, execute the visudo command to open the configuration file.
2. Enter <username> ALL=(root) NOPASSWD:/bin/bash at the end of configuration file, where username represents the name of the non-root user.
When you install an .rpm file as the privileged non-root user, add the sudo keyword to the beginning of the command for installing an .rpm file.
Uploading the license server installation package
Copy the license server installation package to the license server installation directory on the server.
If you use FTP or TFTP to upload the installation package to the directory, use the binary mode to avoid damaging the installation package.
Installing the license server on the server
1. Access the directory where the license server installation package (.rpm file) resides and install the installation package.
The license server installation package is named in the format of LICENSE_SERVER-version.rpm, where version represents the version number.
The following example uses the /root directory.
[root@localhost ~] rpm –ivh LICENSE_SERVER-D1101.rpm
Preparing... ################################# [100%]
...
2. If the license server is installed for the first time or configuration is not saved while uninstalling the old version, perform the following tasks:
a. Enter the service port number at the prompt:
Type the license service port (1024-65535, default:5555) :
Make sure the service port number is not used. If you press Enter without entering a port number, the default port number 5555 is used.
b. Enter the HTTPS port number for Web login at the prompt:
Type the HTTPS port for the Web login (1-65535, default:28443) :
Make sure the specified HTTPS port number is not used.
If you press Enter without entering a port number, the default HTTPS port number 28443 is used.
|
IMPORTANT: The HTTPS port for Web login is used for packet exchange between the master and backup license servers. For the HA feature to function, make sure the master and backup license servers are configured with the same HTTPS port number. |
Verifying the installation
1. Identify whether the license server is successfully installed. If the command output displays correct version information for the license server, the installation succeeds.
[root@localhost ~]# rpm -qa | grep license-server
license-server-1101-1.el7.centos.x86_64
2. Identify whether the license server Core, Monitor, Tomcat, and Redis services are running. If these services are running, the license server service is running.
[root@localhost ~] service licscore status
Redirecting to /bin/systemctl status licscore.service
licscore.service - LICS Core
Loaded: loaded (/etc/systemd/system/licscore.service; disabled)
Active: active (running) since Thu 2015-05-28 16:53:40 CST; 2min 51s ago
...
[root@localhost ~]# service licsmonitor status
Redirecting to /bin/systemctl status licsmonitor.service
licsmonitor.service - LICS Monitor
Loaded: loaded (/etc/systemd/system/licsmonitor.service; disabled)
Active: active (running) since Thu 2015-06-11 01:15:36 CST; 49s ago
...
[root@localhost ~]# service licstomcat status
licstomcat is running
[root@localhost ~]# service licsredis status
Redirecting to /bin/systemctl status licsredis.service
licsredis.service – Lics Redis
Loaded: loaded (/etc/systemd/system/licsredis.service; enabled)
Active: active (running) since Mon 2016-01-25 14:05:05 CST; 2min 40s ago
...
|
IMPORTANT: With HA configured, the Core service of the backup license server becomes inactive and other services remain active. |
Installing an .iso file
1. Use the remote console of the server to load the license server installation package in ISO format through a virtual drive.
2. Restart the server to enter the system loading process.
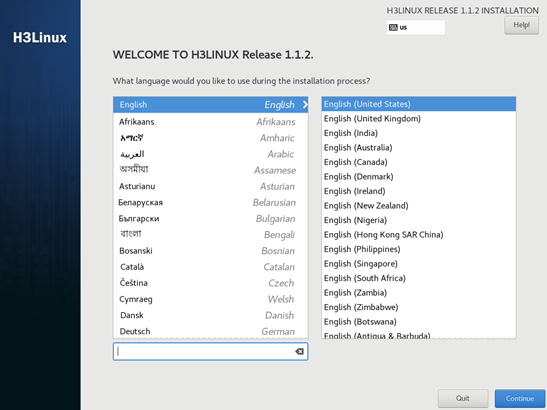
3. After the loading completes, the WELCOME TO H3LINUX page opens. Select a language, and then click Continue. In this example, English is selected.
Figure 1 WELCOME TO H3LINUX page
4. On the INSTALLATION SUMMARY page that opens, click KEYBOARD in the LOCALIZATION area.
Figure 2 INSTALLATION SUMMARY page
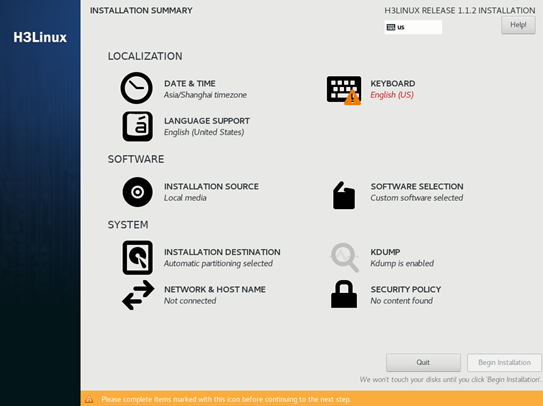
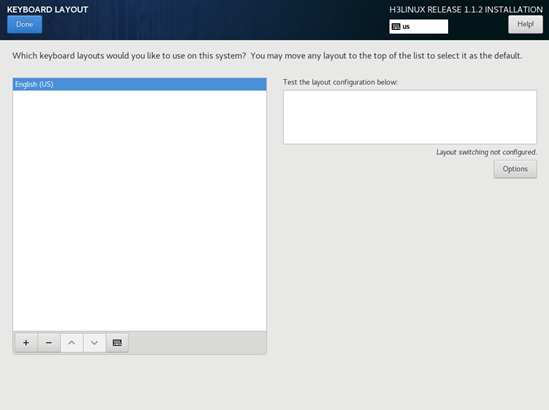
5. On the KEYBOARD LAYOUT page that opens, select English (US) as the keyboard layout, and click Done.
The system returns to the INSTALLATION SUMMARY page.
Figure 3 KEYBOARD LAYOUT page
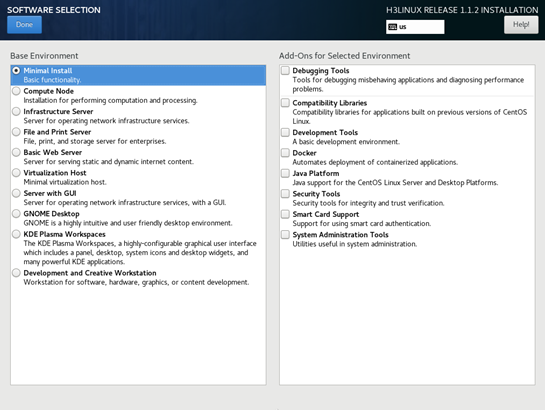
6. Click SOFTWARE SELECTION in the SOFTWARE area.
On the SOFTWARE SELECTION page that opens, select Minimal Install in the Base Environment area, and click Done.
The system returns to the INSTALLATION SUMMARY page.
Figure 4 SOFTWARE SELECTION page
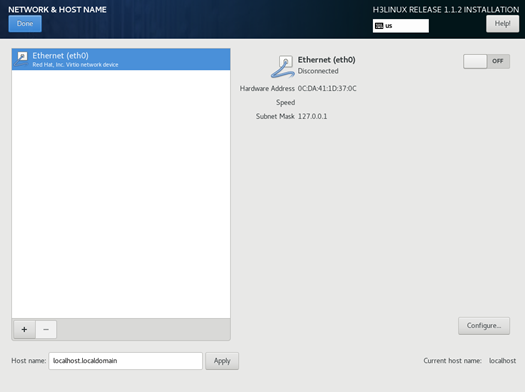
7. Click NETWORK & HOST NAME in the SYSTEM area.
On the NETWORK & HOST NAME page that opens, you can perform the following tasks:
¡ To edit the host name, enter a new host name and click Apply.
Figure 5 NETWORK & HOST NAME page
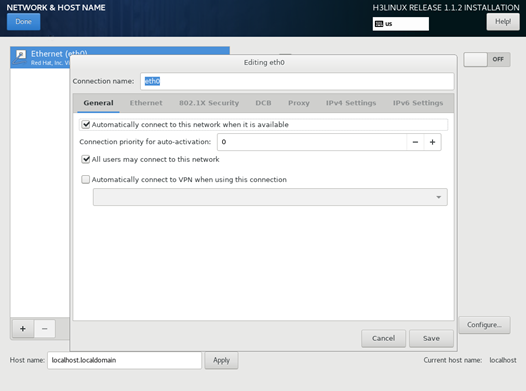
¡ To edit the network settings, click Configure.
On the page that opens, you can perform the following tasks:
- On the General tab, select Automatically connect to this network when it is available.
Figure 6 General settings
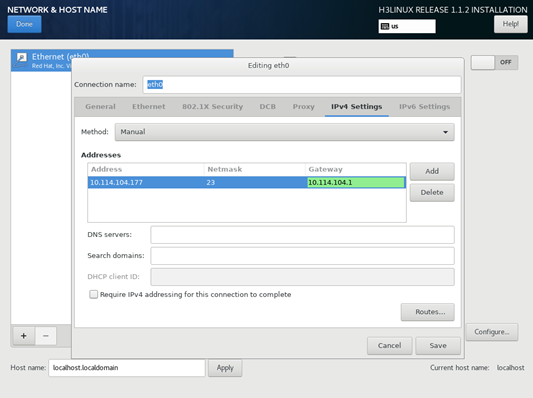
- Click the IPv4 Settings tab and edit IPv4 settings, as shown in Figure 7.
- Click Save after finishing the configuration.
8. After finishing the configuration on the NETWORK & HOST NAME page, click Done.
9. On the INSTALLATION SUMMARY page, click Begin Installation.
During the installation, the Configuration page opens and you can configure the Root password and create users.
Figure 8 Configuration page
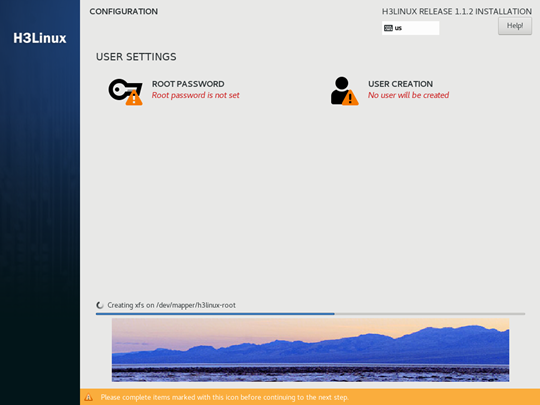
10. After the installation completes, the server will restart automatically to finish the installation of the operating system and license server.
Permitting license server's ports, address, and protocol
The firewalld and iptables services are available to fulfill the firewall function. Select a service according to your server configuration and permit license server's ports, address, and protocol by the firewall.
After the installation, verify the firewalld or iptables service status on the physical server.
· If the service is disabled permanently, you can skip this task. If the service is disabled temporarily, it will become enabled after device reboot. In this case, the license server cannot run correctly. As a best practice, enable the service for security purposes if the license server has risks of exposures to public networks.
· If the service is enabled, for the license server to operate correctly, make sure related license server's ports are opened, and addresses and protocols are permitted by the firewall.
The following ports, address, and protocol must be permitted:
· HTTPS port for the Web login.
· License service port.
· Redis service port 6387.
· Multicast IPv4 address 244.0.0.18 and multicast IPv6 address ff02::12 for HA Keepalived packets and the VRRP protocol.
Configuring the firewalld service
1. Verify that the firewalld service is active. The field value active (running) indicates that the service is active.
[root@localhost ~]# service firewalld status
Redirecting to /bin/systemctl status firewalld.service
firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; disabled)
Active: active (running) since Thu 2015-07-30 12:33:26 CST; 20s ago
...
2. Open the license service port and HTTPS port:
a. Examine whether the license service port and HTTPS port are blocked. In this example, the license service port is 5555 and the HTTPS port is 28443. The field value no indicates that the port is blocked.
[root@localhost ~]# firewall-cmd --query-port=5555/tcp
no
[root@localhost ~]# firewall-cmd --query-port=28443/tcp
no
b. Open the related ports. The field value success indicates that the operation succeeds.
[root@localhost ~]# firewall-cmd --permanent --add-port=5555/tcp
success
[root@localhost ~]# firewall-cmd --permanent --add-port=28443/tcp
success
c. Reload the configuration to make the configuration take effect.
[root@localhost ~]# firewall-cmd –reload
success
d. Verify that the ports are successfully opened. The field value yes indicates that the ports are opened.
[root@localhost ~]# firewall-cmd --query-port=5555/tcp
yes
[root@localhost ~]# firewall-cmd --query-port=28443/tcp
yes
3. Open the Redis service port for HA.
If HA is required, make sure port 6387 used by the Redis service for HA is opened. To ensure database security, open this port only between the master license server and the backup license server. On the physical server hosting the master license server, open the Redis service port only for the backup license server. On the physical server hosting the backup license server, open the Redis service port only for the master license server.
a. Examine whether the Redis service port (port 6387) is blocked. The field value no indicates that the port is blocked.
[root@localhost ~]# firewall-cmd --permanent --query-port=6387/tcp
no
b. If the field value is yes, remove port 6387 from the blocked port list.
[root@localhost ~]# firewall-cmd --permanent --remove-port=6387/tcp
success
c. Open port 6387 only for the master or backup license server.
In this example, the IPv4 address of the master license server or backup license server uses 192.168.109.15.
[root@localhost ~]# firewall-cmd --permanent --add-rich-rule="rule family="ipv4" source address="192.168.109.15" port protocol="tcp" port="6387" accept"
success
In this example, the IPv6 address of the master license server or backup license server uses 2001::142.
[root@localhost ~]# firewall-cmd --permanent --add-rich-rule="rule family="ipv6" source address="2001::142" port protocol="tcp" port="6387" accept"
success
d. Reload the configuration to make the configuration take effect.
[root@localhost ~]# firewall-cmd –reload
success
e. Verify that port 6387 is successfully opened.
In an IPv4 network:
[root@localhost ~]# firewall-cmd --list-all
...
rule family="ipv4" source address="192.168.109.15" port port="6387" protocol="tcp" accept
In an IPv6 network:
[root@localhost ~]# firewall-cmd --list-all
...
rule family="ipv6" source address="2001::142" port port="6387" protocol="tcp" accept
4. Permit the multicast address for the HA Keepalived packets and the VRRP protocol.
You must permit multicast address for Keepalived packets and the VRRP protocol if the license server is to be configured with the HA feature.
a. Examine whether permit rules are configured for the Keepalived multicast address and the VRRP protocol. If the output shows that no permit rules are configured for the Keepalived multicast address and the VRRP protocol, the multicast address and the VRRP protocol are not permitted.
IPv4:
[root@localhost ~]# firewall-cmd --query-rich-rule="rule family="ipv4" destination address="224.0.0.18" protocol value="vrrp" accept"
no
IPv6:
[root@localhost ~]# firewall-cmd --query-rich-rule="rule family="ipv6" destination address="ff02::12" protocol value="vrrp" accept"
no
b. Configure permit rules for the Keepalived multicast address and the VRRP protocol.
IPv4:
[root@localhost ~]# firewall-cmd --permanent --add-rich-rule="rule family="ipv4" destination address="224.0.0.18" protocol value="vrrp" accept"
success
IPv6:
[root@localhost ~]# firewall-cmd --permanent --add-rich-rule="rule family="ipv6" destination address="ff02::12" protocol value="vrrp" accept"
success
c. Reload the configuration to make the configuration take effect.
[root@localhost ~]# firewall-cmd --reload
Success
Configuring the iptables service in an IPv4 network
1. Verify that the iptables service is enabled. The field value active (exited) indicates that the service is enabled.
[root@localhost ~]# service iptables status
Redirecting to /bin/systemctl status iptables.service
iptables.service - IPv4 firewall with iptables
Loaded: loaded (/usr/lib/systemd/system/iptables.service; disabled; vendor preset: disabled)
Active: active (exited) since Thu 2020-01-16 10:11:01 EST; 11s ago
...
2. Open the license service port and HTTPS port:
a. Examine whether the license service port and HTTPS port are blocked. In this example, the license service port is 5555 and the HTTPS port is 28443. If the field value shows that no rule is configured or a rule in other state than ACCEPT exists for the port, the port is blocked.
[root@localhost ~]# iptables -nvL | grep 5555
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:5555
[root@localhost ~]# iptables -nvL | grep 28443
b. If no rule is specified, first specify a rule to open the port. If a rule for other actions than ACCEPT is specified for the port, first delete the rule and then add a rule to open the port.
[root@localhost ~]# iptables -I INPUT -p tcp --dport 5555 -j ACCEPT
[root@localhost ~]# iptables -I INPUT -p tcp --dport 28443 -j ACCEPT
c. Save rules.
[root@localhost ~]# service iptables save
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]
d. Restart the iptables service to make the configuration take effect.
[root@localhost ~]# service iptables restart
Redirecting to /bin/systemctl restart iptables.service
e. Verify that the ports are successfully opened. The field value ACCEPT indicates that the ports are opened.
[root@localhost ~]# iptables -nvL | grep 5555
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:5555
[root@localhost ~]# iptables -nvL | grep 28443
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:28443
3. Open the Redis service port for HA.
If HA is required, make sure port 6387 used by the Redis service for HA is opened. To ensure database security, open this port only between the master license server and the backup license server. On the physical server hosting the master license server, open the Redis service port only for the backup license server. On the physical server hosting the backup license server, open the Redis service port only for the master license server.
a. Examine whether the Redis service port (port 6387) is blocked. If the output shows that no rule is configured or a rule in other state than ACCEPT exists for the port, the port is blocked.
[root@localhost ~]# iptables -nvL | grep 6387
b. If no rule is specified, first specify a rule to open the port. If a rule for other actions than ACCEPT is specified for the port, first delete the rule and then add a rule to open the port.
[root@localhost ~]# iptables -I INPUT -s 192.168.109.15 -p tcp --dport 6387 -j ACCEPT
c. Save the rule.
[root@localhost ~]# service iptables save
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]
d. Restart the iptables service to make the configuration take effect.
[root@localhost ~]# service iptables restart
Redirecting to /bin/systemctl restart iptables.service
e. Verify that port 6387 is successfully opened.
[root@localhost ~]# iptables -nvL | grep 6387
0 0 ACCEPT tcp -- * * 192.168.109.15 0.0.0.0/0 tcp dpt:6387
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:6387
4. Permit the multicast address for the HA Keepalived packets and the VRRP protocol.
You must permit multicast address 244.0.0.18 for Keepalived packets and the VRRP protocol if the license server is to be configured with the HA feature.
a. Examine whether the Keepalived multicast address and the VRRP protocol are permitted. If the output shows that no rule is configured or a rule in other state than ACCEPT exists for the Keepalived multicast address and the VRRP protocol, the multicast address and the VRRP protocol are not permitted.
[root@localhost ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
348 25382 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
32 2336 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
...
b. If no rule is specified, first specify a rule to permit the Keepalived multicast address. If a rule for other actions than ACCEPT is specified for the Keepalived multicast address, first delete the rule and then add a rule to permit the Keepalived multicast address.
[root@localhost ~]# iptables -I INPUT -d 244.0.0.18/8 -j ACCEPT
[root@localhost ~]# iptables -I INPUT -p vrrp -j ACCEPT
c. Save rules.
[root@localhost ~]# service iptables save
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]
d. Restart the iptables service to make the configuration take effect.
[root@localhost ~]# service iptables restart
Redirecting to /bin/systemctl restart iptables.service
Configuring the iptables service in an IPv6 network
1. Verify that the iptables service is enabled. The field value active (exited) indicates that the service is enabled.
[root@localhost ~]# service ip6tables status
Redirecting to /bin/systemctl status ip6tables.service
ip6tables.service - IPv6 firewall with ip6tables
Loaded: loaded (/usr/lib/systemd/system/ip6tables.service; disabled; vendor preset: disabled)
Active: active (exited) since Fri 2020-07-03 06:22:04 EDT; 31min ago
...
2. Open the license service port and HTTPS port:
a. Examine whether the license service port and HTTPS port are blocked. In this example, the license service port is 5555 and the HTTPS port is 28443. If the field value shows that no rule is configured or a rule in other state than ACCEPT exists for the port, the port is blocked.
[root@localhost ~]# ip6tables -nvL | grep 5555
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:5555
[root@localhost ~]# ip6tables -nvL | grep 28443
b. If no rule is specified, first specify a rule to open the port. If a rule for other actions than ACCEPT is specified for the port, first delete the rule and then add a rule to open the port.
[root@localhost ~]# ip6tables -I INPUT -p tcp --dport 5555 -j ACCEPT
[root@localhost ~]# ip6tables -I INPUT -p tcp --dport 28443 -j ACCEPT
c. Save rules.
[root@localhost ~]# service ip6tables save
ip6tables: Saving firewall rules to /etc/sysconfig/ip6table[ OK ]
d. Restart the iptables service to make the configuration take effect.
[root@localhost ~]# service ip6tables restart
Redirecting to /bin/systemctl restart ip6tables.service
e. Verify that the ports are successfully opened. The field value ACCEPT indicates that the ports are opened.
[root@localhost ~]# ip6tables -nvL | grep 5555
0 0 ACCEPT tcp * * ::/0 ::/0 tcp dpt:5555
[root@localhost ~]# ip6tables -nvL | grep 28443
0 0 ACCEPT tcp * * ::/0 ::/0 tcp dpt:28443
3. Open the Redis service port for HA.
If HA is required, make sure port 6387 used by the Redis service for HA is opened. To ensure database security, open this port only between the master license server and the backup license server. On the physical server hosting the master license server, open the Redis service port only for the backup license server. On the physical server hosting the backup license server, open the Redis service port only for the master license server.
a. Examine whether the Redis service port (port 6387) is blocked. If the output shows that no rule is configured or a rule in other state than ACCEPT exists for the port, the port is blocked.
[root@localhost ~]# ip6tables -nvL | grep 6387
b. If no rule is specified, first specify a rule to open the port. If a rule for other actions than ACCEPT is specified for the port, first delete the rule and then add a rule to open the port.
[root@localhost ~]# ip6tables -I INPUT -s 2001::142 -p tcp --dport 6387 -j ACCEPT
c. Save the rule.
[root@localhost ~]# service ip6tables save
ip6tables: Saving firewall rules to /etc/sysconfig/ip6table[ OK ]
d. Restart the iptables service to make the configuration take effect.
[root@localhost ~]# service ip6tables restart
Redirecting to /bin/systemctl restart ip6tables.service
e. Verify that port 6387 is successfully opened.
[root@localhost ~]# ip6tables -nvL | grep 6387
0 0 ACCEPT tcp * * 2001::142 ::/0 tcp dpt:6387
0 0 ACCEPT tcp * * 2001::186 ::/0 tcp dpt:6387
4. Permit the multicast address for the HA Keepalived packets and the VRRP protocol.
You must permit multicast address ff02::12 for Keepalived packets and the VRRP protocol if the license server is to be configured with the HA feature.
a. Examine whether the Keepalived multicast address and the VRRP protocol are permitted. If the output shows that no rule is configured or a rule in other state than ACCEPT exists for the Keepalived multicast address and the VRRP protocol, the multicast address and the VRRP protocol are not permitted.
[root@localhost ~]# ip6tables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp * * ::/0 ::/0 tcp dpt:28443
0 0 ACCEPT tcp * * ::/0 ::/0 tcp dpt:5555
0 0 ACCEPT all * * ::/0 ::/0 state RELATED,ESTABLISHED
4 272 ACCEPT icmpv6 * * ::/0 ::/0
0 0 ACCEPT all lo * ::/0 ::/0
...
b. If no rule is specified, first specify a rule to permit the Keepalived multicast address. If a rule for other actions than ACCEPT is specified for the Keepalived multicast address, first delete the rule and then add a rule to permit the Keepalived multicast address.
[root@localhost ~]# ip6tables -I INPUT -d ff02::12/64 -j ACCEPT
[root@localhost ~]# ip6tables -I INPUT -p vrrp -j ACCEPT
c. Save rules.
[root@localhost ~]# service ip6tables save
ip6tables: Saving firewall rules to /etc/sysconfig/ip6table[ OK ]
d. Restart the iptables service to make the configuration take effect.
[root@localhost ~]# service ip6tables restart
Redirecting to /bin/systemctl restart ip6tables.service
Uninstalling the license server
Restrictions and guidelines
Both the root user and non-root users of the CentOS or H3Linux operating system can remove the installed .rpm file from the server. As a best practice, log in as the root user and remove the .rpm file.
To allow non-root users to remove an .rpm file, perform the following tasks:
1. In root user view, execute the visudo command to open the configuration file.
2. Enter <username> ALL=(root) NOPASSWD:/bin/bash at the end of configuration file, where username represents the name of the non-root user.
When you remove an .rpm file as the privileged non-root user, add the sudo keyword to the beginning of the command for uninstalling an .rpm file.
When you uninstall the license server, you can choose to back up the configuration file and log messages. Later, when you reinstall the license server, the system automatically uses the backup files to restore the configuration and log messages.
To prevent data loss of the master license server configured with HA, back up the configuration file and log messages during uninstallation. To uninstall the master license server without backing up the configuration file or log messages, please first execute the master/backup switchover, and then uninstall the license server.
The license file remains after you uninstall the license server. It is automatically uploaded when you reinstall the license server.
Procedure
1. Remove the license server installation package.
[root@localhost ~] rpm -e license-server
2. Enter Y when you are prompted whether to remove the installation package. Then press Enter.
If you want to abort the uninstallation, enter N.
Do you really want to uninstall license-server? (y/n, default:y) :Y
3. At the prompt of the backup of the configuration file and log messages:
¡ Enter Y to confirm the backup operation.
Do you want to backup the configuration? (y/n, default:y) : y
The backup path is '/opt/LicServer/uninstallbackup/'.
Uninstalling license-server...
...
¡ Enter N to uninstall the server without backup.
Do you want to backup the configuration? (y/n, default:y) : n
Uninstalling license-server...
...
Upgrading the license server
Without changes on the operating system or hardware
License server upgrade includes the following tasks:
1. Remove the old version of the license server (see "Uninstalling the license server").
2. Install the new version of the license server (see "Installing the license server").
To avoid licensing service interruption, back up the configuration file and log messages when you remove the old version of the license server.
As a best practice, use the following procedure for license server upgrade if HA is configured:
1. Upgrade the backup license server.
2. Wait for 2 minutes after the state of the backup license server turns active. In the 2 minutes, the master and backup license servers will synchronize data with each other.
3. Upgrade the master license server.
The license server configured with HA does not support non-service interruption upgrade from E1140 or earlier to E1141 or later. To reduce the service interruption duration, use the following procedure:
1. Remove the old version of the backup license server and save configuration.
2. Remove the old version of the master license server and save configuration.
3. Install the new versions of the master and backup license servers in sequence.
The license server will automatically reconnect to the clients after the upgrade. The license services obtained by the clients during the upgrade will not be interrupted. As a best practice, do not disconnect the clients from the license server during license server upgrade. The manual disconnection will cause the license server to reclaim all licenses from the clients, which causes license-based services to malfunction on the clients.
With changes on the operating system or hardware
If the license server upgrade requires the changes on the operating system (for example, system reinstallation or upgrade) or hardware, you might be unable to use the licenses after the upgrade. To use the licenses normally after the upgrade, use the following upgrading procedures:
1. Select License Management > License Files, uninstall all formal licenses, and export the Uninstall files to the local server.
2. Change the operating system or hardware:
¡ Change the operating system, and then install the license server. For more information, see "Installing the license server."
¡ Change the hardware, remove the old version of the license server (see "Uninstalling the license server"), and then install the new version of the license server (see "Installing the license server").
3. Log in to the licenser server after the upgrade. Select License Management > License Files, click Export DID to obtain the DID file.
4. Contact the technical engineers and provide them the new DID file and Uninstall files to obtain new activation files.
5. Install new activation files on the license server after upgrade.
Running the license server on the Ubuntu/Linx operating system
Restrictions and guidelines
Both the root user and non-root users of the operating system can install the license server installation package on the server or remove the license server installation package from the server. As a best practice, log in as the root user and then install or remove the license server installation package.
To allow non-root users to install or remove a license server installation package, perform the following tasks:
1. In root user view, execute the visudo command to open the configuration file.
2. Enter <username> ALL=(root) NOPASSWD:/bin/bash at the end of configuration file, where username represents the name of the non-root user.
When you install or remove a license server installation package as the privileged non-root user, add the sudo keyword to the beginning of the command for installing or removing a license server installation package.
Installing the license server
Uploading the license server installation package
Copy the license server installation package to the license server installation directory on the server.
If you use FTP or TFTP to upload the installation package to the directory, use the binary mode to avoid damaging the installation package.
Installing the license server on the server
1. Access the directory where the license server installation package (.deb file) resides and install the installation package.
The license server installation package is named in the format of LICENSE_SERVER-version.deb, where version represents the version number.
The following example uses the /root directory.
root@wsy-Standard-PC-i440FX-PIIX-1996:~# dpkg -i LICENSE_SERVER-E1144.deb
Selecting previously unselected package license-server.
(Reading database ... 206437 files and directories currently installed.)
Preparing to unpack LICENSE_SERVER-E1144.deb ...
Unpacking license-server (1144) ...
Setting up license-server (1144) ...
......
2. If the license server is installed for the first time or configuration is not saved while uninstalling the old version, perform the following tasks:
a. Enter the service port number at the prompt:
Type the license service port (1024-65535, default:5555) :
Make sure the service port number is not used. If you press Enter without entering a port number, the default port number 5555 is used.
b. Enter the HTTPS port number for Web login at the prompt:
Type the HTTPS port for the Web login (1-65535, default:28443) :
Make sure the specified HTTPS port number is not used.
If you press Enter without entering a port number, the default HTTPS port number 28443 is used.
|
IMPORTANT: The HTTPS port for Web login is used for packet exchange between the master and backup license servers. For the HA feature to function, make sure the master and backup license servers are configured with the same HTTPS port number. |
Verifying the installation
1. Identify whether the license server is successfully installed. If the command output displays correct version information for the license server, the installation succeeds.
root@Linx:~# dpkg -l |grep license-server
ii license-server 1144 amd64 License Server
2. Identify whether the license server Core, Monitor, Tomcat, and Redis services are running. If these services are running, the license server service is running.
root@Linx:~# service licscore status
licscore.service - LICS Core
Loaded: loaded (/etc/systemd/system/licscore.service; enabled)
Active: active (running) since Sat 2019-07-27 17:06:50 CST; 8min ago
...
root@Linx:~# service licsmonitor status
licsmonitor.service - LICS Monitor
Loaded: loaded (/etc/systemd/system/licsmonitor.service; enabled)
Active: active (running) since Sat 2019-07-27 17:06:50 CST; 9min ago
...
root@Linx:~# service licstomcat status
licstomcat.service - LSB: start|stop|restart|status
Loaded: loaded (/etc/init.d/licstomcat)
Active: active (running) since Sat 2019-07-27 17:06:50 CST; 16min ago
...
root@Linx:~# service licsredis status
licsredis.service - Lics Redis
Loaded: loaded (/etc/systemd/system/licsredis.service; enabled)
Active: active (running) since Sat 2019-07-27 17:06:46 CST; 18min ago
...
|
IMPORTANT: With HA configured, the Core service of the backup license server becomes inactive and other services remain active. |
Permitting license server's ports, address, and protocol
After the installation, verify the ufw service status on the physical server.
· If the service is disabled permanently, you can skip this task. If the service is disabled temporarily, it will become enabled after device reboot. In this case, the license server cannot run correctly. As a best practice, enable the service for security purposes if the license server has risks of exposures to, public networks.
· If the service is enabled, for the license server to operate correctly, make sure related license server's ports are opened, and addresses and protocols are permitted by the firewall.
The following ports, address, and protocol must be permitted:
· HTTPS port for the Web login.
· License service port.
· Redis service port 6387.
· Multicast IPv4 address 244.0.0.18 and multicast IPv6 address ff02::12 for HA Keepalived packets and the VRRP protocol.
To permit license server's ports and address:
1. Verify that the ufw service is active. The output active indicates that the service is active.
root@Linx:~# ufw status
Status: active
2. Open the license service port and HTTPS port:
a. Add rules to open the license service port and HTTPS port. In this example, the license service port is 5555 and the HTTPS port is 28443.
root@Linx:~# ufw allow 28443
Rule added
Rule added (v6)
root@Linx:~# ufw allow 5555
Rule added
Rule added (v6)
b. Examine whether the license service port and HTTPS port are opened. The field value ALLOW IN indicates that the ports are opened.
root@Linx:~# ufw status verbose
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing)
New profiles: skip
To Action From
-- ------ ----
28443 ALLOW IN Anywhere
5555 ALLOW IN Anywhere
28443 ALLOW IN Anywhere (v6)
5555 ALLOW IN Anywhere (v6)
3. Open the Redis service port for HA.
If HA is required, make sure port 6387 used by the Redis service for HA is opened. To ensure database security, open this port only between the master license server and the backup license server. On the physical server hosting the master license server, open the Redis service port only for the backup license server. On the physical server hosting the backup license server, open the Redis service port only for the master license server.
a. Examine whether the Redis service port (port 6387) is opened. The field value ALLOW IN indicates that the port is opened and the value Anywhere indicates that the port is opened for all devices.
root@Linx:~# ufw status verbose
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing)
New profiles: skip
To Action From
-- ------ ----
28443 ALLOW IN Anywhere
5555 ALLOW IN Anywhere
6387 ALLOW IN Anywhere
28443 ALLOW IN Anywhere (v6)
5555 ALLOW IN Anywhere (v6)
6387 ALLOW IN Anywhere (v6)
b. If ALLOW IN and Anywhere are displayed for port 6387, delete the rules that opens port 6387 for all devices.
Obtain the serial numbers of the configured rules.
root@Linx:~# ufw status numbered
Status: active
To Action From
-- ------ ----
[ 1] 28443 ALLOW IN Anywhere
[ 2] 5555 ALLOW IN Anywhere
[ 3] 6387 ALLOW IN Anywhere
[ 4] 28443 ALLOW IN Anywhere (v6)
[ 5] 5555 ALLOW IN Anywhere (v6)
[ 6] 6387 ALLOW IN Anywhere (v6)
Delete the rules in a declining order of the serial number.
root@Linx:~# ufw delete 8
Deleting:
allow 6387
Proceed with operation (y|n)? y
Rule deleted (v6)
root@Linx:~# ufw delete 4
Deleting:
allow 6387
Proceed with operation (y|n)? y
Rule deleted
c. Verify that port 6387 is blocked for all devices.
root@Linx:~# ufw status numbered
Status: active
To Action From
-- ------ ----
[ 1] 28443 ALLOW IN Anywhere
[ 2] 5555 ALLOW IN Anywhere
[ 3] 28443 ALLOW IN Anywhere (v6)
[ 4] 5555 ALLOW IN Anywhere (v6)
d. Add a rule to open port 6387 only for the master or backup license server.
In this example, the IPv4 address of the master license server or backup license server uses 10.114.104.120 and the local IPv4 address uses 10.114.104.121.
root@Linx:~# ufw allow proto tcp from 10.114.104.120 to 10.114.104.121 port 6387
Rule added
In this example, the IPv6 address of the master license server or backup license server uses 2001::142 and the local IPv6 address uses 2001::65.
root@Linx:~# ufw allow proto tcp from 2001::142 to 2001::65 port 6387
Rule added (v6)
e. Verify that port 6387 is successfully opened for the master or backup license server.
root@Linx:~# ufw status numbered
Status: active
To Action From
-- ------ ----
[ 1] 28443 ALLOW IN Anywhere
[ 2] 5555 ALLOW IN Anywhere
[ 3] 10.114.104.121 6387/tcp ALLOW IN 10.114.104.120
[ 4] 28443 ALLOW IN Anywhere (v6)
[ 5] 5555 ALLOW IN Anywhere (v6)
[ 6] 2001::65 6387/tcp ALLOW IN 2001::142
4. Permit the multicast address for the HA Keepalived packets.
You must permit multicast IPv4 address 244.0.0.18 and multicast IPv6 address ff02::12 for Keepalived packets if the license server is to be configured with the HA feature.
a. Permit the Keepalived multicast address.
root@Linx:~# ufw allow to 224.0.0.18
Rule added
root@Linx:~# ufw allow to ff02::12
Rule added (v6)
b. Verify that multicast address 244.0.0.18 is permitted.
root@Linx:~# ufw status numbered
Status: active
To Action From
-- ------ ----
[ 1] 28443 ALLOW IN Anywhere
[ 2] 5555 ALLOW IN Anywhere
[ 3] 10.114.104.121 6387/tcp ALLOW IN 10.114.104.120
[ 4] 224.0.0.18 ALLOW IN Anywhere
[ 5] 28443 ALLOW IN Anywhere (v6)
[ 6] 5555 ALLOW IN Anywhere (v6)
[ 7] 2001::65 6387/tcp ALLOW IN 2001::142
[ 8] ff02::12 ALLOW IN Anywhere (v6)
Uninstalling the license server
Restrictions and guidelines
When you uninstall the license server, you can choose to back up the configuration file and log messages. Later, when you reinstall the license server, the system automatically uses the backup files to restore the configuration and log messages.
To prevent data loss of the master license server configured with HA, back up the configuration file and log messages during uninstallation. To uninstall the master license server without backing up the configuration file or log messages, please first execute the master/backup switchover, and then uninstall the license server.
The license file remains after you uninstall the license server. It is automatically uploaded when you reinstall the license server.
Procedure
1. Remove the license server installation package.
[root@localhost ~] rpm -e license-server
2. Enter Y when you are prompted whether to remove the installation package. Then press Enter.
If you want to abort the uninstallation, enter N.
Do you really want to uninstall license-server? (y/n, default:y) :Y
3. At the prompt of the backup of the configuration file and log messages:
¡ Enter Y to confirm the backup operation.
Do you want to backup the configuration? (y/n, default:y) : y
The backup path is '/opt/LicServer/uninstallbackup/'.
Uninstalling license-server...
...
¡ Enter N to uninstall the server without backup.
Do you want to backup the configuration? (y/n, default:y) : n
Uninstalling license-server...
...
Upgrading the license server
Without changes on the operating system or hardware
License server upgrade includes the following tasks:
1. Remove the old version of the license server (see "Uninstalling the license server").
2. Install the new version of the license server (see "Installing the license server").
To avoid licensing service interruption, back up the configuration file and log messages when you remove the old version of the license server.
As a best practice, use the following procedure for license server upgrade if HA is configured:
1. Upgrade the backup license server.
2. Wait for 2 minutes after the state of the backup license server turns active. In the 2 minutes, the master and backup license servers will synchronize data with each other.
3. Upgrade the master license server.
The license server will automatically reconnect to the clients after the upgrade. The license services obtained by the clients during the upgrade will not be interrupted. As a best practice, do not disconnect the clients from the license server during license server upgrade. The manual disconnection will cause the license server to reclaim all licenses from the clients, which causes license-based services to malfunction on the clients.
With changes on the operating system or hardware
If the license server upgrade requires the changes on the operating system (for example, system reinstallation or upgrade) or hardware, you might be unable to use the licenses after the upgrade. To use the licenses normally after the upgrade, use the following upgrading procedures:
1. Select License Management > License Files, uninstall all formal licenses, and export the Uninstall files to the local server.
2. Change the operating system or hardware:
¡ Change the operating system, and then install the license server. For more information, see "Installing the license server."
¡ Change the hardware, remove the old version of the license server (see "Uninstalling the license server"), and then install the new version of the license server (see "Installing the license server").
3. Log in to the licenser server after the upgrade. Select License Management > License Files. On the page that opens, click Export DID to obtain the DID file.
4. Contact the technical engineers and provide them the new DID file and Uninstall files to obtain new activation files.
5. Install new activation files on the license server after upgrade.
Logging in to the license server
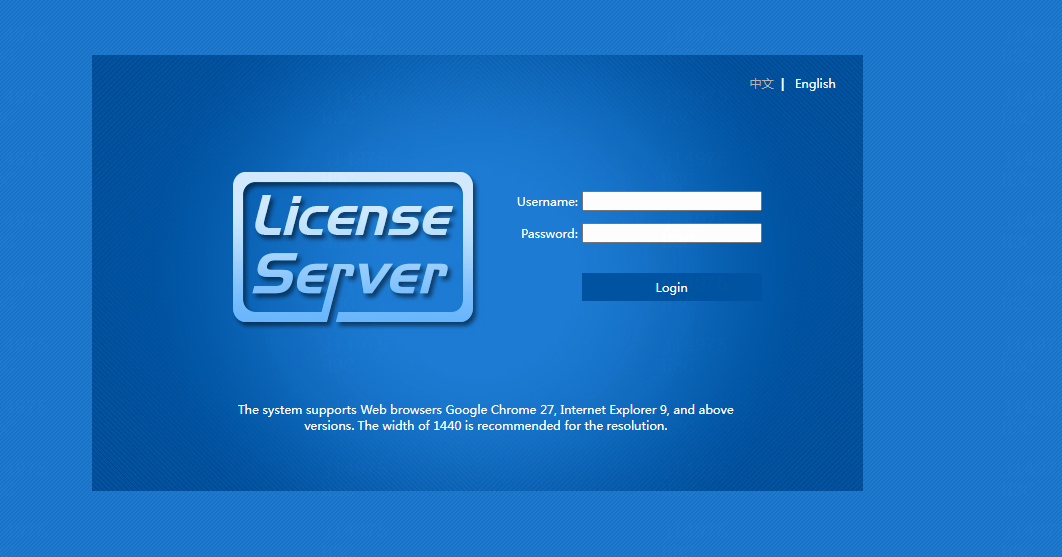
1. Enter the Web login address of the license server in the browser and then press Enter.
The Web login address of the license server varies by version.
Table 2 Web login address in versions earlier than E1144
|
IP protocol type |
Web login address format |
Default port number |
|
IPv4 |
http://lics_ipv4_address:port/licsmanager |
8090 |
Table 3 Web login address from E1144 to versions earlier than E1146
|
IP protocol type |
Web login address format |
Default port number |
|
IPv4 |
http://lics_ipv4_address:port/licsmanager |
8090 |
|
https://lics_ipv4_address:port/licsmanager |
28443 |
Table 4 Web login address from E1146
|
IP protocol type |
Web login address format |
Default port number |
|
IPv4 |
https://lics_ipv4_address:port/ https://lics_ipv4_address:port/licsmanager |
28443 |
|
IPv6 |
https://[lics_ipv6_address]:port/ https://[lics_ipv6_address]:port/licsmanager |
28443 |
The lics_ip4_address or lics_ipv6_address argument represents the IPv4 or IPv6 address of the server that hosts the license server. If HA is configured, the IP address represents the virtual IP address or the IP address of the master license server.
The port argument represents the port number.
2. On the Web login page, perform the following tasks:
a. At the upper right of the login page, click English as the interface language.
b. Enter the administrator's username and password.
The default username is admin and password is admin@h3c.
c. Click Login.
Figure 9 License server Web login page
3. On the configuration wizard that appears for the first login, perform the following tasks:
¡ Add license clients.
¡ Modify system configuration such as the license service port.
Deploying a license server HA cluster
A license server HA cluster contains two member nodes. The master license server processes services and backs up data to the backup license server. The cluster uses a virtual IP address to provide services. When the master license server fails, the backup license server takes over to ensure service continuity. As a best practice, deploy an HA cluster to avoid licensing service interruption caused by single point of failure.
Restrictions and guidelines
Make sure the master and backup license servers have the same port number configuration.
Before configuring HA, make sure the system time is the same on the master and backup license servers.
With HA configured, the Core service of the backup license server becomes inactive and other services remain active. For correct operation of the HA feature, do not edit the configuration file for the NIC on the server.
When HA is configured, increase the following priority values of the ports on the switch that connects the two physical servers where the license servers are installed:
· Local precedence.
· 802.1p priority.
· DSCP priority.
Larger port priority values ensure the performance of information exchange between member license servers.
As a best practice, configure a license server to receive system logs from the license server cluster for monitoring the HA status and licensing status.
Deploying the HA cluster
1. Install two license servers on two separate servers.
2. Specify one license server as the master license server:
¡ If both license servers are newly installed, you can specify either of them as the master license server.
¡ If you enable HA for the license server in standalone mode, specify the license server as the master license server.
¡ If none of the license servers is newly installed, check the data on each license server carefully. Specify the license server on which data will be retained as the master license server.
3. Log in to the master license server, and then select HA.
4. On the Configure HA page, select the IP version and enter the HA ID, virtual IP, master IP address, and backup IP address.
¡ The HA ID cannot be the same as the virtual router IDs of VRRP groups in the same broadcast domain.
¡ The virtual IP cannot be the same as the virtual IPs of other clusters or services.
¡ Use the static IP addresses of the master and backup license servers as the master and backup IP addresses, respectively.
5. Click OK.
6. Verify the HA configuration and license server status. The HA cluster is created successfully if the backup license server is in active status.
After HA is configured, clients must use the virtual IP to access the license server HA cluster.
FAQ
What should I do if I cannot install a license file because hardware has changed after I obtained the license file?
You need to contact Technical Support to apply for license change.
If hardware change as follows occurs on the server after you obtain the license file, the license file will become invalid and you cannot install the license file on the license server:
· NIC change (NIC forbidden, new NIC enabled, NIC replaced, or NIC damaged).
· MPU replacement.
· CPU replacement.
· BIOS upgrade.
How to change the hardware after a license is installed?
After a license is installed on the license server, a hardware change such as system board replacement, CPU replacement, or BIOS upgrade might cause the license file to be invalid.
To change the hardware after a license is installed on the license server, use the following procedures:
|
CAUTION: If a license transfer operation affect services, take preventive measures before the operation, such as apply for and install a trail license for use during the operation. |
1. Log in to the license server, select License Management > License Files.
2. In the Operation
column, click the Uninstall icon ![]() to set the status of a license file to Uninstalled, and then click the Export Uninstall file icon
to set the status of a license file to Uninstalled, and then click the Export Uninstall file icon ![]() to export the Uninstall file to the local server.
to export the Uninstall file to the local server.
3. Change the hardware and log in to the license server. Select License Management > License Files. On the page that opens, click Export DID to obtain the DID file.
4. Contact the technical engineers and provide them the new DID file and Uninstall file to obtain a new activation file.
5. Log in to the license server after the hardware changes, select License Management > License Files. On the page that opens, click Install license file. On the dialog box that opens, click Browse. Select the locally saved license file and click OK.
How can I change the IP of the license server after the license server has been deployed?
|
CAUTION: After you change the IP of the license server, the client is disconnected from the license server, and you might need to reconnect the client to the license server. Before performing this operation, contact the client technical support to assess the impact. |
Changing the physical IP of the license server in standalone deployment
Change the physical IP of the license server directly. After the change, reconfigure the new IP of the license server on the client and connect the client to the license server.
Changing the physical IP of one or both of the license server nodes in an HA cluster
1. Verify that the HA configuration and status are normal.
Access the license server HA cluster from the virtual IP address. View the HA configuration and status on the HA page. Make sure the backup license server is in active status.
2. Delete HA on the HA page. Then, access each node by using the physical IP of that node and verify that the HA configuration has been deleted.
3. Change the physical IP of the specified nodes and then make the change take effect.
4. Use the original master license server as the master license server to re-create an HA cluster.
Log in to the original master license server from its physical IP. On the HA page, enter the original HA ID, original virtual IP, (new, if changed) master IP address, and (new, if changed) backup IP address to create a new HA cluster. Then, verify that the HA cluster status is normal.
5. Verify that the connection status and licensing status are normal on the client.
Changing the virtual IP of a license server HA cluster
1. Verify that the HA configuration and status are normal.
Access the license server HA cluster from the virtual IP address. View the HA configuration and status on the HA page. Make sure the backup license server is in active status.
2. Delete HA on the HA page. Then, access each node by using the physical IP of that node and verify that the HA configuration has been deleted.
3. Use the original master license server as the master license server to re-create an HA cluster.
Log in to the original master license server from its physical IP. On the HA page, enter the original HA ID, new virtual IP, master IP address, and backup IP address to create a new HA cluster. Then, verify that the HA status is normal.
4. Reconfigure the new license server IP on the client and connect the client to the license server. Verify that the connection status and licensing status are normal on the client.
Changing the IP during switching from standalone mode to HA mode
During a switching from standalone mode to HA mode, you can use the following procedure so that you do not need to change the license server IP on the client:
1. Change the physical IP of the license server in standalone mode and make the new IP take effect.
2. Use the license server as the master license server to create an HA cluster.
Log in to the master license server from the new IP and create the HA cluster from the HA page. Use the original IP of the server as the virtual IP.
3. Verify that the HA configuration and status are normal.
Access the license server HA cluster from the virtual IP address. View the HA configuration and status on the HA page. Make sure the backup license server is in active status.
4. Verify that the connection status and licensing status are normal on the client.
Can licenses continue to be used after the license server is uninstalled and reinstalled?
Yes. License information is not deleted after the license server is uninstalled.
Can license information be restored after a backup file is used for restoring the configuration of the license server?
No. Only client settings, system settings, and log settings are restored.