- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-WLAN high availability configuration | 184.76 KB |
Restrictions and guidelines: Dual-link backup configuration
Dual-link backup tasks at a glance
Setting AP connection priority and specifying a backup AC
Configuring master CAPWAP tunnel preemption
Dual-link backup configuration examples
Example: Configuring dual-link backup
Restrictions and guidelines: WLAN VSRP
Associating the AC with a VSRP instance
Specifying the TCP port number for establishing a wireless client backup data channel
Verifying and maintaining WLAN VSRP
WLAN VSRP configuration examples
Example: Configuring WLAN VSRP
Configuring dual-link backup
About dual-link backup
Dual-link backup enables two ACs to back up each other to reduce risks of service interruption caused by single-AC failures.
Dual-link backup is applicable to networks that are service continuity insensitive.
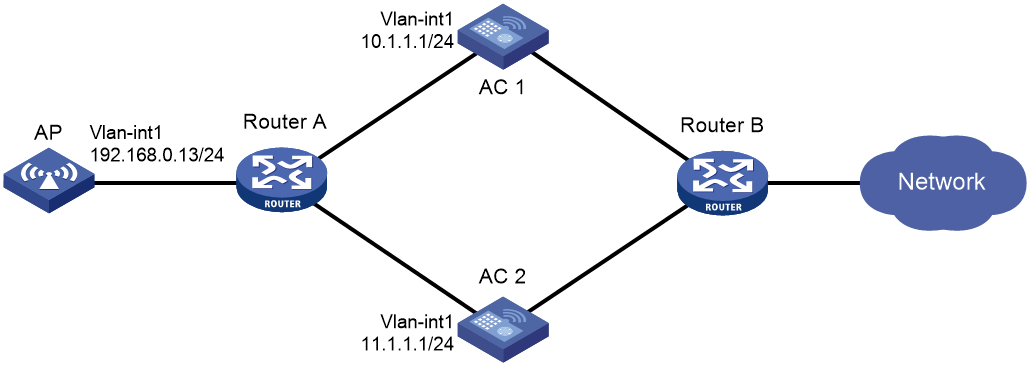
Figure 1 Network diagram for dual-link backup
Restrictions and guidelines: Dual-link backup configuration
For the dual-link backup feature to function correctly, configure auto AP or manual APs on the two ACs. The manual AP configuration must be identical on both ACs. For more information, see managing APs in AP Management Configuration Guide.
You can configure APs by using the following methods:
· Configure APs one by one in AP view.
· Assign APs to an AP group and configure the AP group in AP group view.
· Configure all APs in global configuration view.
For an AP, the settings made in these views for the same parameter take effect in descending order of AP view, AP group view, and global configuration view.
Dual-link backup tasks at a glance
To configure dual-link backup, perform the following tasks:
1. Setting AP connection priority and specifying a backup AC
2. (Optional.) Configuring master CAPWAP tunnel preemption
Setting AP connection priority and specifying a backup AC
About this task
Set a higher AP connection priority for the master AC to ensure that APs can associate with the master AC first.
After an AP establishes a CAPWAP tunnel with the master AC, the AP will establish a backup CAPWAP tunnel with the specified backup AC.
Procedure
1. Enter system view.
system-view
2. Enter AP view or AP group view.
¡ Enter AP view.
wlan ap ap-name
¡ Enter AP group view.
wlan ap-group group-name
3. Set the AP connection priority.
priority priority
By default:
¡ In AP view, an AP uses the configuration in AP group view.
¡ In AP group view, the AP connection priority is 4.
4. Specify a backup AC.
backup-ac { ip ipv4-address | ipv6 ipv6-address }
By default:
¡ In AP view, an AP uses the configuration in AP group view.
¡ In AP group view, no backup AC is specified.
Configuring master CAPWAP tunnel preemption
About this task
This feature enables a backup CAPWAP tunnel to become a master tunnel after 10 minutes if the backup AC has higher AP connection priority than the master AC.
Procedure
1. Enter system view.
system-view
2. Enter AP view, AP group view, or global configuration view.
¡ Enter AP view.
wlan ap ap-name
¡ Enter AP group view.
wlan ap-group group-name
¡ Enter global configuration view.
wlan global-configuration
3. Configure master CAPWAP tunnel preemption.
wlan tunnel-preempt { disable | enable }
By default:
¡ In AP view, an AP uses the configuration in AP group view. If no configuration exists in AP group view, the AP uses the configuration in global configuration view.
¡ In AP group view, an AP uses the configuration in global configuration view.
¡ In global configuration view, master CAPWAP tunnel preemption is disabled.
Dual-link backup configuration examples
Example: Configuring dual-link backup
Network configuration
As shown in Figure 2, configure AC 1 to act as the master AC and AC 2 as the backup AC. When AC 1 fails and AC 2 takes over, the AP can communicate through AC 2. Configure the master CAPWAP tunnel preemption feature on the two ACs so that the AP reconnects to AC 1 when AC 1 recovers.
Procedure
1. Configure AC 1:
# Create VLAN-interface 1 and assign an IP address to it.
<AC1> system-view
[AC1] interface vlan-interface 1
[AC1-Vlan-interface1] ip address 10.1.1.1 24
[AC1-Vlan-interface1] quit
# Create an AP named ap1, and specify the AP model and serial ID. Set the AP connection priority to 7.
[AC1] wlan ap ap1 model WA6320
[AC1-wlan-ap-ap1] serial-id 219801A28N819CE0002T
[AC1-wlan-ap-ap1] priority 7
[AC1-wlan-ap-ap1] backup-ac ip 11.1.1.1
# Enable master CAPWAP tunnel preemption.
[AC1-wlan-ap-ap1] wlan tunnel-preempt enable
[AC1-wlan-ap-ap1] quit
2. Configure AC 2:
# Create VLAN-interface 1 and assign an IP address to it.
<AC2> system-view
[AC2] interface Vlan-interface 1
[AC2-Vlan-interface1] ip address 11.1.1.1 24
[AC2-Vlan-interface1] quit
# Create an AP named ap1, and specify the AP model and serial ID. Set the AP connection priority to 5.
[AC2] wlan ap ap1 model WA6320
[AC2-wlan-ap-ap1] serial-id 219801A28N819CE0002T
[AC2-wlan-ap-ap1] priority 5
# Specify a backup AC.
[AC2-wlan-ap-ap1] backup-ac ip 10.1.1.1
# Enable master CAPWAP tunnel preemption.
[AC2-wlan-ap-ap1] wlan tunnel-preempt enable
[AC2-wlan-ap-ap1] quit
Verifying the configuration
# Get the AP online on AC 1. (Details not shown.)
# Shut down VLAN-interface 1 on AC 1 and wait no longer than 3 minutes, during which service interruption occurs. (Details not shown.)
# Verify that the AP comes online on AC 2 and the AP state is R/M on AC 2. (Details not shown.)
# Bring up VLAN-interface 1 on AC 1. (Details not shown.)
# Verify that the AP comes online on AC 1 again and the AP state is R/M on AC 1 and R/B in AC 2. (Details not shown.)
Configuring WLAN VSRP
About WLAN VSRP
WLAN Virtual Service Redundancy Protocol (VSRP) establishes a data backup tunnel between the master AC and backup AC for real-time synchronization of WLAN service data. If the master AC or the link to the master AC fails, the backup AC takes over services to ensure service continuity.
For more information about VSRP, see High Availability Configuration Guide.
Restrictions and guidelines: WLAN VSRP
· Make sure the master AC and backup AC are associated with the same VSRP instance.
· Data backup is not supported if the master and backup ACs use different versions.
· WLAN VSRP is available only in AC hair-pin deployment. Make sure the ACs do not act as a gateway or DHCP server.
· If you enable accounting-on, WLAN VSRP does not take effect.
· With WLAN VSRP configured, do not enable STP on the switch interfaces that connect the switch to the ACs in the VRRP group. If STP is configured globally, specify the switch interfaces as edge interfaces.
· To avoid data backup failure, make sure the master and backup ACs meet the following requirements:
¡ The two ACs have the same software version, and use consistent authentication, VSRP, and service template settings.
¡ Service templates are bound to APs or AP groups in the same order on both ACs.
· To use remote 802.1X or MAC authentication, configure the NAS-IP as the virtual IP address of VRRP on the master and backup ACs.
· Make sure VSRP, VRRP, and AP association use the same VLAN.
· Do not bind the VRRP service VLAN to multiple physical interfaces.
· As a best practice to ensure system stability, set the VRRP advertisement interval for notification packets to a value larger than 300 centiseconds.
· In VRRP preemptive mode, retain the default preemption delay (60 minutes) as a best practice. To change the preemption delay, set the delay to a value longer than 10 minutes as a best practice.
· To support hot backup-incapable APs, configure AP connection priorities on the ACs for APs to establish master tunnels with the master AC and backup tunnels with the backup AC.
· For APs to use static configuration to obtain AC addresses, you must specify the AC IP addresses for APs manually.
· If auto AP is configured, convert auto APs to manual APs before configuring VSRP.
· WLAN VSRP does not support using a virtual IP address as the access IP address for APs.
· During the use of WLAN VSRP, after adding service template configurations on the master and backup ACs, execute the save and reboot commands in sequence to save the configuration and then reboot the ACs.
Associating the AC with a VSRP instance
1. Enter system view.
system-view
2. Enter global configuration view.
wlan global-configuration
3. Associate the AC with a VSRP instance.
vsrp-instance vsrp-instance-name
By default, the AC is not associated with a VSRP instance.
Specifying the TCP port number for establishing a wireless client backup data channel
About this task
To back up wireless client data in real time, the master and the backup must establish a backup TCP data channel. You can change the TCP port number as needed.
Restrictions and guidelines
Changing the port number disconnects the current TCP backup tunnel. The ACs will use the new port to establish a new tunnel.
Procedure
1. Enter system view.
system-view
2. Enter global configuration view.
wlan global-configuration
3. Specify a TCP port number for VSRP to establish a data channel for wireless client data backup.
client vsrp-port port-number
By default, the TCP port number is 60048.
Verifying and maintaining WLAN VSRP
To display WLAN VSRP instance information, execute the following command in any view:
display wlan client vsrp instance [ instance-name ]
WLAN VSRP configuration examples
Example: Configuring WLAN VSRP
Network configuration
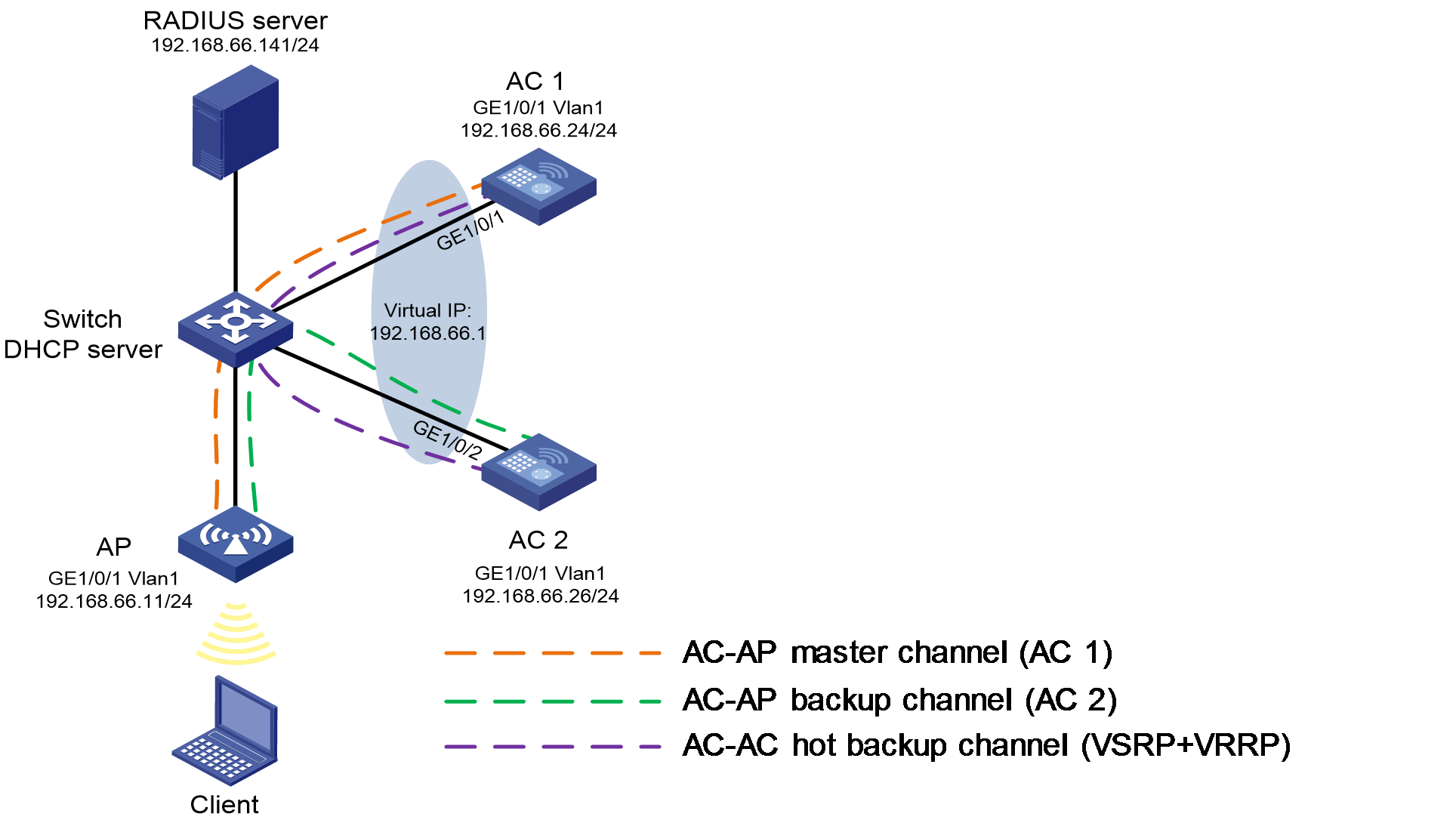
As shown in Figure 3, AC 1, AC 2, and the AP connect to each other through the switch to form a dual-link network. Configure WLAN VSRP to establish a VRRP+VSRP hot backup tunnel between the ACs and configure 802.1X EAP-PEAP authentication. The switch acts as the DHCP server to assign IP addresses to clients. AC 1, AC 2, and the AP use IP addresses 192.168.66.24, 192.168.66.26, and 192.168.66.11, respectively.
Procedure
1. Configure interface IP addresses and global route settings. (Details not shown.)
2. Configure the RADIUS server:
|
|
NOTE: In this example, the RADIUS server runs IMC V7. |
# Add an access device.
a. Log in to IMC and click the User tab.
b. From the navigation pane, select User Access Policy > Access Device Management > Access Device.
c. Click Add.
- Specify the shared key for authentication and accounting to 12345678, and retain the default settings in the other fields.
- Select or manually add device at 192.168.66.1 (VRRP virtual IP address) as an access device.
# Add an access policy.
a. Click the User tab.
b. From the navigation pane, select User Access Policy > Access Policy.
c. Click Add.
- Specify the policy name as dot1x.
- Select EAP for the Certificate Authentication field.
- Select EAP-PEAP as the certificate type and MS-CHAPV2 as the sub-type. Make sure the subtype is consistent with the client authentication method.
# Add an access service.
a. Click the User tab.
b. From the navigation pane, select User Access Policy > Access Service.
c. Click Add.
- Enter dot1x as the service name.
- Select dot1x as the default access policy.
# Add an access user.
a. Click the User tab.
b. From the navigation pane, select Access User > All Access Users.
c. Click Add.
- Set the username to user.
- Set the account name and password to user and dot1x, respectively.
- Select service dot1x for the user.
3. Configure AC 1:
¡ Configure VRRP:
# Create VRRP group 1, set its virtual IP address to 192.168.66.1, and set the AC priority to 250 on VLAN-interface 1. The priority is higher than the priority configured on AC 2.
<AC1> system-view
[AC1] interface vlan-interface 1
[AC1-Vlan-interface1] vrrp vrid 1 virtual-ip 192.168.66.1
[AC1-Vlan-interface1] vrrp vrid 1 priority 250
# Configure AC 1 to operate in preemptive mode, and set the preemption delay to 120000 centiseconds (20 minutes).
[AC1-Vlan-interface1] vrrp vrid 1 preempt-mode delay 120000
[AC1-Vlan-interface1] quit
¡ Configure VSRP-track collaboration:
# Configure track entry 1, and associate it with interface GigabitEthernet 1/0/1. If the state of the track entry is Negative, it indicates that the VRRP, VSRP, or CAPWAP link is faulty.
[AC1] track 1 interface gigabitethernet1/0/1
¡ Configure VSRP:
# Create VSRP peer pname, specify the peer IP address as 192.168.66.26, and specify the local IP address as 192.168.66.24. This configuration enables AC 1 to use VLAN-interface 1 to establish the backup data tunnel for VSRP.
[AC1] vsrp peer pname
[AC1-vsrp-peer-pname] peer 192.168.66.26 local 192.168.66.24
# Associate VSRP peer pname with track entry 1.
[AC1-vsrp-peer-pname] track 1
[AC1-vsrp-peer-pname] quit
# Create VSRP instance inst, associate the instance with VSRP group pname, and set the backup ID of the instance to 1.
[AC1] vsrp instance inst
[AC1-vsrp-instance-inst] backup id 1 peer pname
# Bind the VSRP instance to VRRP group 1 on interface VLAN-interface 1.
[AC1-vsrp-instance-inst] bind vrrp vrid 1 interface vlan-interface1
[AC1-vsrp-instance-inst] quit
# Associate VSRP instance inst to AC 1.
[AC1] wlan global-configuration
[AC1-wlan-global-configuration] vsrp-instance inst
[AC1-wlan-global-configuration] quit
¡ Configure AAA:
# Configure EAP relay.
[AC1] dot1x authentication-method eap
# Create RADIUS scheme imc. Specify the primary authentication server and primary account server, and set the shared key for authentication and accounting to 12345678 in plaintext.
[AC1] radius scheme imc
[AC1-radius-imc] primary authentication 192.168.66.141 key simple 12345678
[AC1-radius-imc] primary accounting 192.168.66.14 key simple 12345678
# Exclude domain names from the usernames sent to the RADIUS server, and specify the source IP address for outgoing RADIUS packets as 192.168.66.1.
[AC1-radius-imc] user-name-format without-domain
[AC1-radius-imc] nas-ip 192.168.66.1
[AC1-radius-imc] quit
# Create ISP domain dot1x, and apply RADIUS scheme imc to the ISP domain for authentication, authorization, and accounting.
[AC1] domain dot1x
[AC1-isp-dot1x] authentication lan-access radius-scheme imc
[AC1-isp-dot1x] authorization lan-access radius-scheme imc
[AC1-isp-dot1x] accounting lan-access radius-scheme imc
[AC1-isp-dot1x] quit
¡ Configure the service template:
# Create service template wlas_imc_dot1x, and configure the 802.1X authentication mode. Specify the ISP domain, SSID, AKM mode, cipher suite, and security IE as domain dot1x, wlas_imc_dot1x, 802.1X, CCMP, and RSN, respectively.
[AC1] wlan service-template wlas_imc_dot1x
[AC1-wlan-st-wlas_imc_dot1x] client-security authentication-mode dot1x
[AC1-wlan-st-wlas_imc_dot1x] dot1x domain dot1x
[AC1-wlan-st-wlas_imc_dot1x] ssid wlas_imc_dot1x
[AC1-wlan-st-wlas_imc_dot1x] akm mode dot1x
[AC1-wlan-st-wlas_imc_dot1x] cipher-suite ccmp
[AC1-wlan-st-wlas_imc_dot1x] security-ie rsn
# Enable the service template.
[AC1-wlan-st-wlas_imc_dot1x] service-template enable
[AC1-wlan-st-wlas_imc_dot1x] quit
¡ Configure the AP:
# Create AP ap1.
[AC1] wlan ap ap1 model WA6320
[AC1-wlan-ap-ap1] serial-id 219801A28N819CE0002T
# Specify the working channel of radio 1 as channel 149, and enable the radio.
[AC1-wlan-ap-ap1] radio 1
[AC1-wlan-ap-ap1-radio-1] channel 149
[AC1-wlan-ap-ap1-radio-1] radio enable
# Bind service template wlas_imc_dot1x to radio 1.
[AC1-wlan-ap-ap1-radio-1] service-template wlas_imc_dot1x
[AC1-wlan-ap-ap1-radio-1] quit
[AC1-wlan-ap-ap1] quit
¡ Save the configuration and then restart the AC.
[AC1] save
The current configuration will be written to the device. Are you sure? [Y/N]:y
Please input the file name(*.cfg)[flash:/startup.cfg]
(To leave the existing filename unchanged, press the enter key):
flash:/startup.cfg exists, overwrite? [Y/N]:y
Validating file. Please wait...
Configuration is saved to device successfully.
[AC1] quit
<AC1> reboot
Start to check configuration with next startup configuration file, please wait..
.......DONE!
Current configuration may be lost after the reboot, save current configuration?
[Y/N]:y
This command will reboot the device. Continue? [Y/N]:y
4. Configure AC 2:
¡ Configure VRRP:
# Create VRRP group 1, set its virtual IP address to 192.168.66.1, and set the AC priority to 200 on VLAN-interface 1. The priority is lower than the priority configured on AC 1.
<AC2> system-view
[AC2] interface vlan-interface 1
[AC2-Vlan-interface1] vrrp vrid 1 virtual-ip 192.168.66.1
[AC2-Vlan-interface1] vrrp vrid 1 priority 200
# Configure AC 2 to operate in preemptive mode, and set the preemption delay to 120000 centiseconds (20 minutes).
[AC2-Vlan-interface1] vrrp vrid 1 preempt-mode delay 120000
[AC2-Vlan-interface1] quit
¡ Configure VSRP-track collaboration:
# Configure track entry 1, and associate it with interface GigabitEthernet 1/0/2. If the state of the track entry is Negative, it indicates that the VRRP, VSRP, or CAPWAP link is faulty.
[AC2] track 1 interface gigabitethernet1/0/2
¡ Configure VSRP:
# Create VSRP peer pname, specify the peer IP address as 192.168.66.24, and specify the local IP address as 192.168.66.26. This configuration enables AC 2 to use VLAN-interface 1 to establish the backup data tunnel for VSRP.
[AC2] vsrp peer pname
[AC2-vsrp-peer-pname] peer 192.168.66.24 local 192.168.66.26
# Associate VSRP peer pname with track 1.
[AC2-vsrp-peer-pname] track 1
[AC2-vsrp-peer-pname] quit
# Create VSRP instance inst, associate the instance with VSRP group pname, and set the backup ID of the instance to 1.
[AC2] vsrp instance inst
[AC2-vsrp-instance-inst] backup id 1 peer pname
# Bind the VSRP instance to VRRP group 1 on interface VLAN-interface 1.
[AC2-vsrp-instance-inst] bind vrrp vrid 1 interface vlan-interface1
[AC2-vsrp-instance-inst] quit
# Associate VSRP instance inst to AC 1.
[AC2] wlan global-configuration
[AC2-wlan-global-configuration] vsrp-instance inst
[AC2-wlan-global-configuration] quit
¡ Configure AAA:
# Configure EAP relay.
[AC2] dot1x authentication-method eap
# Create RADIUS scheme imc. Specify the primary authentication server and primary account server, and set the shared key for authentication and accounting to 12345678 in plaintext.
[AC2] radius scheme imc
[AC2-radius-imc] primary authentication 192.168.66.141 key simple 12345678
[AC2-radius-imc] primary accounting 192.168.66.141 key simple 12345678
# Exclude domain names from the usernames sent to the RADIUS server, and specify the source IP address for outgoing RADIUS packets as 192.168.66.1.
[AC2-radius-imc] user-name-format without-domain
[AC2-radius-imc] nas-ip 192.168.66.1
[AC2-radius-imc] quit
# Create ISP domain dot1x, and apply RADIUS scheme imc to the ISP domain for authentication, authorization, and accounting.
[AC2] domain dot1x
[AC2-isp-dot1x] authentication lan-access radius-scheme imc
[AC2-isp-dot1x] authorization lan-access radius-scheme imc
[AC2-isp-dot1x] accounting lan-access radius-scheme imc
[AC2-isp-dot1x] quit
¡ Configure the service template:
# Create service template wlas_imc_dot1x, and configure the 802.1X authentication mode. Specify the ISP domain, SSID, AKM mode, cipher suite, and security IE as domain dot1x, wlas_imc_dot1x, 802.1X, CCMP, and RSN, respectively.
[AC2] wlan service-template wlas_imc_dot1x
[AC2-wlan-st-wlas_imc_dot1x] client-security authentication-mode dot1x
[AC2-wlan-st-wlas_imc_dot1x] dot1x domain dot1x
[AC2-wlan-st-wlas_imc_dot1x] ssid wlas_imc_dot1x
[AC2-wlan-st-wlas_imc_dot1x] akm mode dot1x
[AC2-wlan-st-wlas_imc_dot1x] cipher-suite ccmp
[AC2-wlan-st-wlas_imc_dot1x] security-ie rsn
# Enable the service template.
[AC2-wlan-st-wlas_imc_dot1x] service-template enable
[AC2-wlan-st-wlas_imc_dot1x] quit
¡ Configure the AP:
# Create AP ap1.
[AC2] wlan ap ap1 model WA6320
[AC2-wlan-ap-ap1] serial-id 219801A28N819CE0002T
# Specify the working channel of radio 1 as channel 149, and enable the radio.
[AC2-wlan-ap-ap1] radio 1
[AC2-wlan-ap-ap1-radio-1] channel 149
[AC2-wlan-ap-ap1-radio-1] radio enable
# Bind service template wlas_imc_dot1x to radio 1.
[AC2-wlan-ap-ap1-radio-1] service-template wlas_imc_dot1x
[AC2-wlan-ap-ap1-radio-1] quit
[AC2-wlan-ap-ap1] quit
¡ Save the configuration and then restart the AC.
[AC2] save
The current configuration will be written to the device. Are you sure? [Y/N]:y
Please input the file name(*.cfg)[flash:/startup.cfg]
(To leave the existing filename unchanged, press the enter key):
flash:/startup.cfg exists, overwrite? [Y/N]:y
Validating file. Please wait...
Configuration is saved to device successfully.
[AC2] quit
<AC2> reboot
Start to check configuration with next startup configuration file, please wait..
.......DONE!
Current configuration may be lost after the reboot, save current configuration?
[Y/N]:y
This command will reboot the device. Continue? [Y/N]:y
Verifying the configuration
# Verify that AC 1 is the master device, AC 2 is the backup device, and both channels are in up state.
[AC1] display wlan client vsrp instance inst
VSRP instance name : inst
Instance peer address : 192.168.66.26
Instance status : Master
Channel status : Up
Created at : 2021-11-30 15:51:26
[AC2] display wlan client vsrp instance inst
VSRP instance name : inst
Instance peer address : 192.168.66.24
Instance status : Backup
Channel status : Up
Created at : 2021-11-30 10:55:30
# Connect the client to wireless service wlas_imc_dot1x, and enter username user and password dot1x. For an Android terminal, if you select MSCHAPV2, you can skip CA certificate verification. To verify CA certificate, you must install the certificate on the terminal.
# Display 802.1X user connections on AC 1 and AC 2.
[AC1] display dot1x connection
Total connections: 1
User MAC address : aa22-40a8-aa85
AP name : ap1
Radio ID : 1
SSID : wlas_imc_dot1x
BSSID : 0868-8dfd-1650
Username : user
Authentication domain : imc
IPv4 address : 192.168.66.172
Authentication method : EAP
Initial VLAN : 1
Authorization VLAN : 1
Authorization ACL number : N/A
Authorization user profile : N/A
Authorization CAR : N/A
Termination action : Default
Session timeout last from : 2021/11/30 21:08:27
Session timeout period : 86400 s
Online from : 2021/11/30 21:08:27
Online duration : 0h 0m 3s
[AC2] display dot1x connection-backup
Total backup connections: 1
User MAC address : aa22-40a8-aa85
AP name : ap1
Radio ID : 1
SSID : wlas_imc_dot1x
BSSID : 0868-8dfd-1650
Username : dot1x
Authentication domain : imc
IPv4 address : 192.168.66.172
Authentication method : EAP
Initial VLAN : 1
Authorization VLAN : 1
Authorization ACL number : N/A
Authorization user profile : N/A
Authorization CAR : N/A
Termination action : Default
Session timeout period : 86400 s
Online from : 2021/11/30 21:08:27
Online duration : 0h 1m 35s
# View user information on AC 1 and AC 2.
[AC1] display wlan client
Total number of clients: 1
MAC address User name AP name R IP address VLAN
aa22-40a8-aa85 user ap1 1 192.168.66.172 1
[AC2] display wlan client-backup
Total number of clients: 1
MAC address User name AP name R IP address VLAN
aa22-40a8-aa85 user ap1 1 192.168.66.172 1