Country / Region
Active Management Platform for Campus Network Security

1. Challenges of network security construction in colleges and universities
Various challenges impede the construction of the campus network security, including unclear responsibilities of network security, chaotic management of campus information assets, unawareness of network security risks, and other issues.
1.1 Insufficient management synergy of campus network security: The security management system fails to integrate with the campus’s organizational structure. The responsibilities of network security are difficult to implement, and the system vulnerabilities and risks fail to be supervised during the whole life cycle.
1.2 Lagging management of information assets: Campus information assets fail to be effectively sorted and managed because there is no campus-level management system and process, resulting in insufficient control of domain names and IP addresses.
1.3 Insufficient technical capabilities in network security: The campus faces challenges in network security management and O&M as it has no professional network security team for technical support.
1.4 Passive network security protection system: No emergency response methods are available to handle system vulnerabilities and security incidents. The warning and regulation capabilities, as well as the security status detection and round-the-clock risk monitoring before websites and information systems are launched need to be enhanced.
H3C is committed to handling the pain points in campus network security construction and creating an active management platform for campus network security. (1) Take the information system as the main management platform, designate an administrator based on the campus organizational structure, clearly define rights and responsibilities, and implement the security responsibility system. (2) Achieve the unified management of information assets of the campus through the platform to make the asset risks and responsible personnel clear, and enable vulnerabilities and risks to be rectified in a closed-loop manner with the work order system. (3) Associate the platform and security devices to issue policies with one click to perform automatic vulnerability scanning, risk monitoring, and attack blocking of information assets.
2. Core idea of constructing the campus network security system
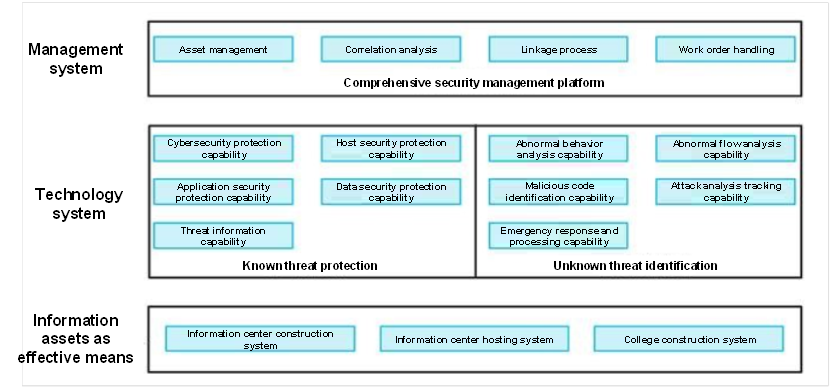
Figure 1 Solution structure
The core idea of constructing the campus network security system is to enhance the management of information assets and regulate the platform with network-wide linkage. Four stages are set up for managing the whole process of network security with information assets as clues as follows:
Stage 1: sort and check information assets of the campus
(1) Asset baseline: Establish an asset information database and make information assets clear based on the campus service system.
(2) Compliant operation: Optimize the filing and approval process and security inspection of the information system, ensuring comprehensive information and safe operation for the information system.
Stage 2: unify the security protection
Conduct all-around monitoring of system vulnerabilities, website risks, and Internet attack risks, connect the platform to the security devices in the entire network for automatic protection, and provide the function of one-click network disconnection as an emergency response.
Stage 3: handle the security incidents in a closed-loop manner
(1) Administrators of the information center issue a rectification work order concerning network risks to the related personnel responsible for the information system and ensure that the risks are handled in a closed-loop manner through processing, reporting, and verification of the work order.
(2) For high-risk information systems, administrators of the network center block access from the whole network or access from the campus network, preventing the spread of risks.
Figure 2 Overview of work order disposal
Stage 4: unify the O&M and management of network security
(1) Match the security management system with the organizational structure of the campus, clearly define rights and responsibilities, and the presidents, deans, and administrators of the network center have their own security dashboards that present the system risks in their respective management areas.
(2) Trace the sources of various security risks and rectification results and provide data for leaders to make decisions based on security O&M reports. The reports are automatically generated on a daily, weekly, and monthly basis.


