- Table of Contents
-
- 07-MPLS Configuration Guide
- 00-Preface
- 01-Basic MPLS configuration
- 02-Static LSP configuration
- 03-LDP configuration
- 04-MPLS TE configuration
- 05-Static CRLSP configuration
- 06-RSVP configuration
- 07-Tunnel policy configuration
- 08-MPLS L3VPN configuration
- 09-IPv6 MPLS L3VPN configuration
- 10-MPLS OAM configuration
- 11-MCE configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 09-IPv6 MPLS L3VPN configuration | 762.51 KB |
IPv6 MPLS L3VPN network diagram
IPv6 MPLS L3VPN packet forwarding
IPv6 MPLS L3VPN routing information advertisement
IPv6 MPLS L3VPN network schemes and features
IPv6 MPLS L3VPN tasks at a glance
Prerequisites for IPv6 MPLS L3VPN
Associating a VPN instance with a Layer 3 interface
Configuring route related attributes for a VPN instance
Configuring routing between a PE and a CE
Configuring IPv6 static routing between a PE and a CE
Configuring RIPng between a PE and a CE
Configuring OSPFv3 between a PE and a CE
Configuring IPv6 IS-IS between a PE and a CE
Configuring EBGP between a PE and a CE
Configuring IBGP between a PE and a CE
Configuring routing between PEs
Configuring BGP VPNv6 route control
Specifying a preferred value for BGP VPNv6 routes
Setting the maximum number of received routes
Configuring BGP VPNv6 route reflection
Configuring BGP VPNv6 route attributes
Configuring BGP VPNv6 route filtering
Configuring BGP VPNv6 routes to use private network next hops
Configuring inter-AS IPv6 VPN option A
Configuring inter-AS IPv6 VPN option B
Configuring inter-AS IPv6 VPN option C
Configuring an OSPFv3 sham link
Redistributing the loopback interface address
Configuring BGP AS number substitution and SoO attribute
Configuring the BGP additional path feature
Configuring the public instance
Configuring BGP route replication between different VPN instances
Configuring BGP route replication between public and VPN instances
Configuring route re-origination
Enabling prioritized withdrawal of specific routes
Enabling logging for BGP route flapping
Verifying and maintaining IPv6 MPLS L3VPN
Verifying IPv6 MPLS L3VPN configuration and running status
IPv6 MPLS L3VPN configuration examples
Example: Configuring IPv6 MPLS L3VPNs
Example: Configuring a hub-spoke network
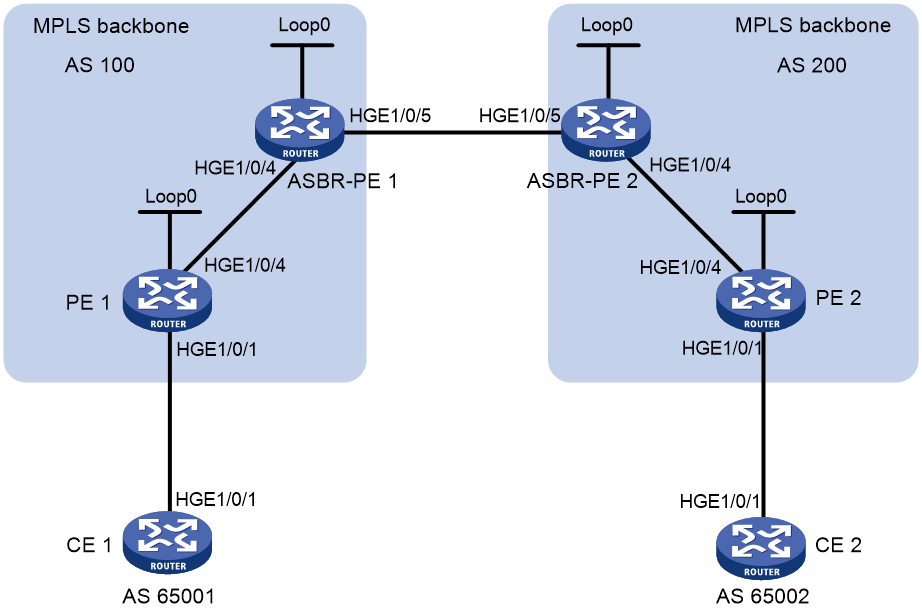
Example: Configuring IPv6 MPLS L3VPN inter-AS option A
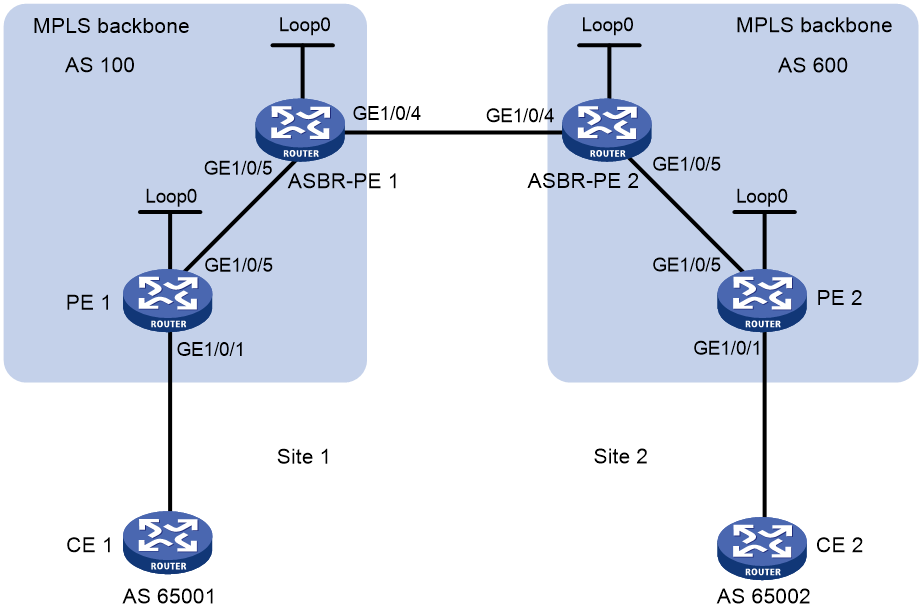
Example: Configuring inter-AS IPv6 VPN option B
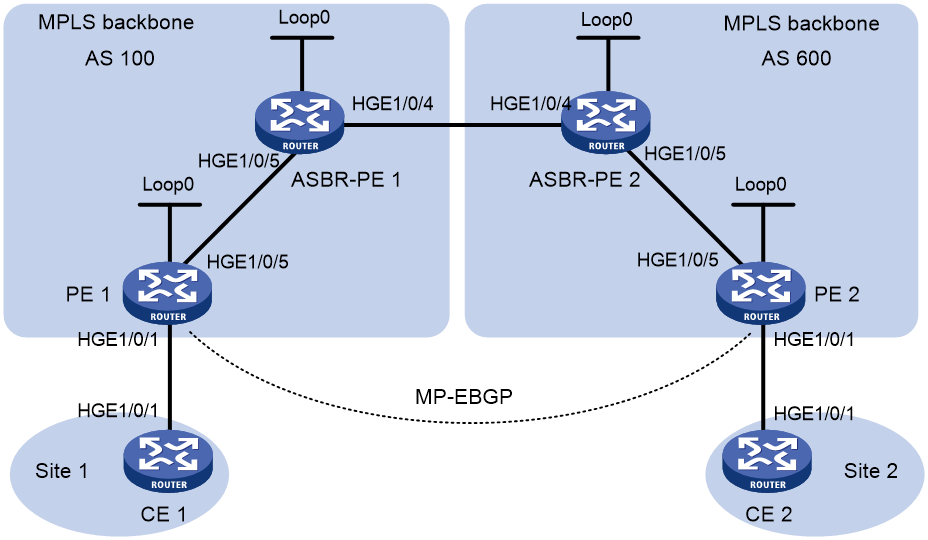
Example: Configuring IPv6 MPLS L3VPN inter-AS option C
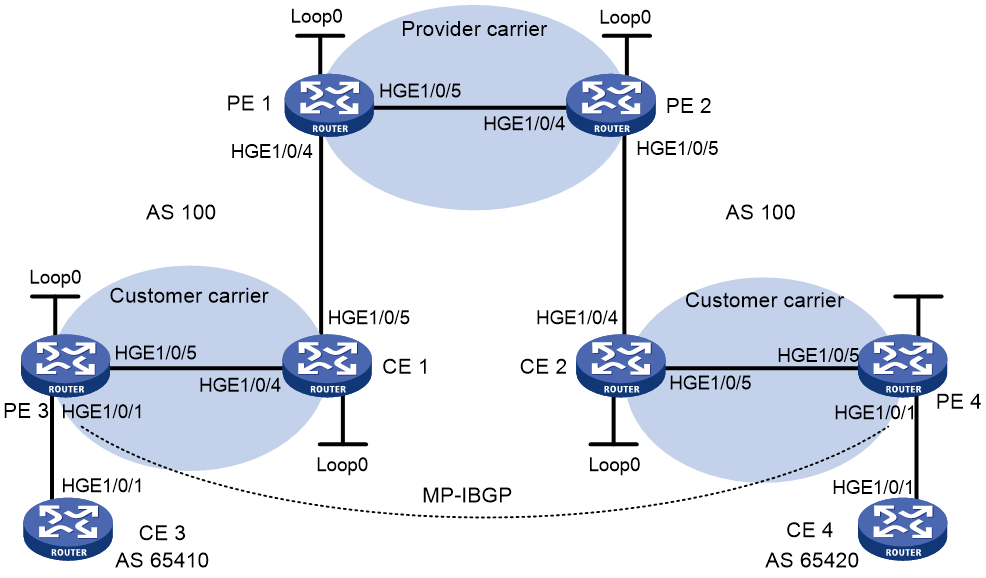
Example: Configuring IPv6 MPLS L3VPN carrier's carrier in the same AS
Example: Configuring an OSPFv3 sham link
Example: Configuring BGP AS number substitution
Example: Configuring BGP AS number substitution and SoO attribute
Configuring IPv6 MPLS L3VPN
About IPv6 MPLS L3VPN
IPv6 MPLS L3VPN uses BGP to advertise IPv6 VPN routes and uses MPLS to forward IPv6 VPN packets on the service provider backbone.
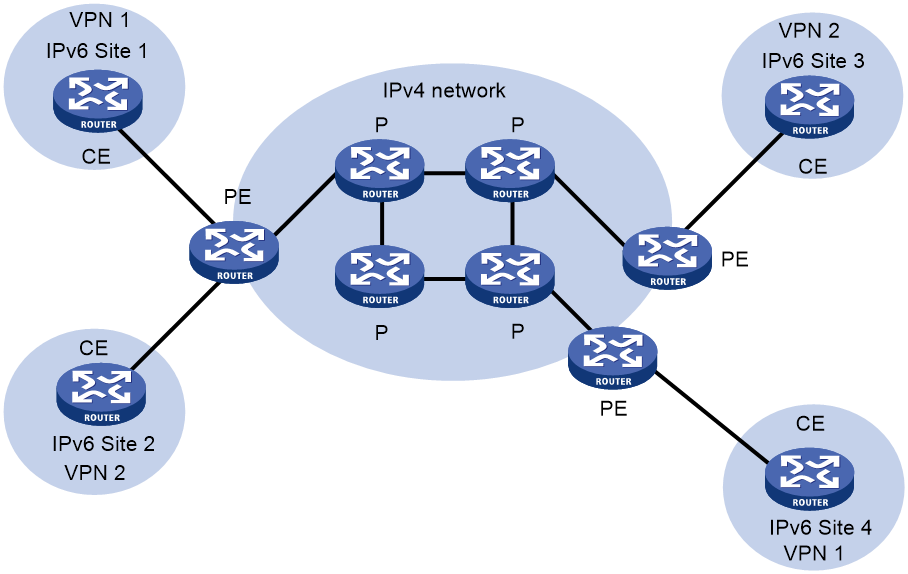
IPv6 MPLS L3VPN network diagram
Figure 1 shows a typical IPv6 MPLS L3VPN model. The service provider backbone in the IPv6 MPLS L3VPN model is an IPv4 network. IPv6 runs inside the VPNs and between CE and PE. Therefore, PEs must support both IPv4 and IPv6. The PE-CE interfaces of a PE run IPv6, and the PE-P interface of a PE runs IPv4.
Figure 1 Network diagram for the IPv6 MPLS L3VPN model
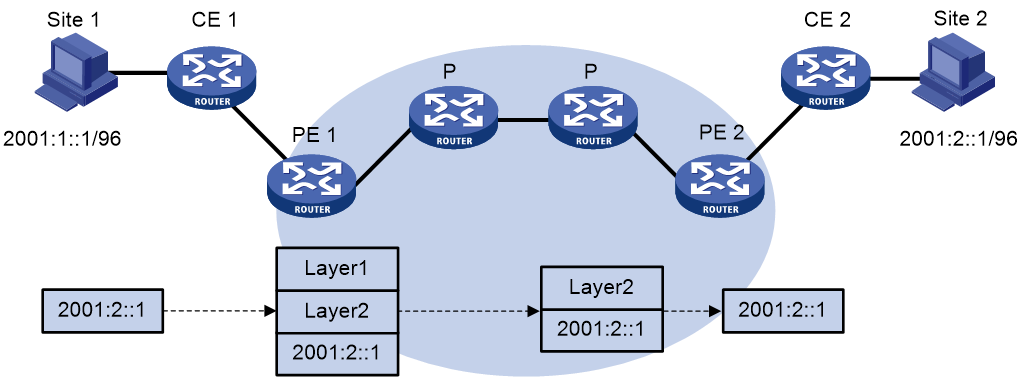
IPv6 MPLS L3VPN packet forwarding
As shown in Figure 2, the IPv6 MPLS L3VPN packet forwarding procedure is as follows:
1. The PC at Site 1 sends an IPv6 packet destined for 2001:2::1, the PC at Site 2. CE 1 transmits the packet to PE 1.
2. Based on the inbound interface and destination address of the packet, PE 1 finds a matching entry from the routing table of the VPN instance, labels the packet with both a private network label (inner label) and a public network label (outer label), and forwards the packet out.
3. The MPLS backbone transmits the packet to PE 2 by outer label. The outer label is removed from the packet at the penultimate hop.
4. According to the inner label and destination address of the packet, PE 2 searches the routing table of the VPN instance to determine the outbound interface, and then forwards the packet out of the interface to CE 2.
5. CE 2 forwards the packet to the destination by IPv6 forwarding.
Figure 2 IPv6 MPLS L3VPN packet forwarding diagram
IPv6 MPLS L3VPN routing information advertisement
The routing information is advertised through the path local CE—ingress PE—egress PE—remote CE.
Routing information advertisement from the local CE to the ingress PE.
The local CE advertises standard IPv6 routing information to the ingress PE over an IPv6 static route, RIPng route, OSPFv3 route, IPv6 IS-IS route, IBGP route, or EBGP route.
Routing information advertisement from the ingress PE to the egress PE.
After receiving the standard IPv6 routes from the CE, the ingress PE performs the following operations:
1. Adds RDs and route targets to create VPN-IPv6 routes.
2. Saves the routes to the routing table of the VPN instance created for the CE.
3. Assigns VPN labels for the routes.
4. Advertises the VPN-IPv6 routes to the egress PE through MP-BGP.
The egress PE performs the following operations:
5. Compares the export target attributes of the VPN-IPv6 routes with the import target attributes that it maintains for the VPN instance.
6. Adds the routes to the routing table of the VPN instance if the export and import target attributes are the same.
The PEs use an IGP to ensure the connectivity between them.
Routing information advertisement from the egress PE to the remote peer CE.
The egress PE restores the original IPv6 routes and advertises them to the remote CE over an IPv6 static route, RIPng route, OSPFv3 route, IPv6 IS-IS route, EBGP, or IBGP route.
IPv6 MPLS L3VPN network schemes and features
IPv6 MPLS L3VPN supports the following network schemes and features:
· Basic VPN.
· Inter-AS VPN option A.
· Inter-AS VPN option B.
· Inter-AS VPN option C.
· Carrier's carrier.
· OSPFv3 VPN extension. (OSPFv3 Type 3, Type 5, and Type 7 LSAs support the DN bit. By default, OSPFv3 VPN extension uses the DN bit to avoid routing loops.)
· BGP AS number substitution and SoO.
Protocols and standards
· RFC 4659, BGP-MPLS IP Virtual Private Network (VPN) Extension for IPv6 VPN
· RFC 6565, OSPFv3 as a Provider Edge to Customer Edge (PE-CE) Routing Protocol
IPv6 MPLS L3VPN tasks at a glance
Unless otherwise indicated, configure IPv6 MPLS L3VPN on PEs.
To configure IPv6 MPLS L3VPN, perform the following tasks:
1. Configuring IPv6 MPLS L3VPN basics:
b. Configuring routing between a PE and a CE
c. Configuring routing between PEs
d. (Optional.) Configuring BGP VPNv6 route control
2. Configuring advanced IPv6 MPLS L3VPN networks
Choose the following tasks as needed:
¡ Configuring inter-AS IPv6 VPN
Perform this task when sites of a VPN are connected to different ASs of an ISP.
3. (Optional.) Controlling route advertisement and reception in MPLS L3VPN
¡ Configuring an OSPFv3 sham link
¡ Configuring BGP AS number substitution and SoO attribute
¡ Configuring the BGP additional path feature
¡ Configuring route replication
Perform this task to enable a VPN instance to communicate with the public network or other VPN instances by replicating routes from the public network or other VPN instances.
¡ Enabling prioritized withdrawal of specific routes
4. (Optional.) Enabling logging for BGP route flapping
Prerequisites for IPv6 MPLS L3VPN
Before configuring IPv6 MPLS L3VPN, perform the following tasks:
1. Configure an IGP on the PEs and P devices to ensure IP connectivity within the MPLS backbone.
2. Configure basic MPLS for the MPLS backbone.
3. Configure MPLS LDP on PEs and P devices to establish LDP LSPs.
Configuring VPN instances
Creating a VPN instance
About this task
A VPN instance is a collection of the VPN membership and routing rules of its associated site. A VPN instance might correspond to more than one VPN.
Procedure
1. Enter system view.
system-view
2. Specify a label range for all VPN instances.
mpls per-vrf-label range minimum maximum
By default, no label range is configured.
3. Create a VPN instance and enter VPN instance view.
ip vpn-instance vpn-instance-name
4. Configure an RD for the VPN instance.
route-distinguisher route-distinguisher
By default, no RD is configured for a VPN instance.
5. (Optional.) Configure a description for the VPN instance.
description text
By default, no description is configured for a VPN instance.
6. (Optional.) Set an ID for the VPN instance.
vpn-id vpn-id
By default, no ID is configured for a VPN instance.
7. (Optional.) Configure an SNMP context for the VPN instance.
snmp context-name context-name
By default, no SNMP context is configured.
8. Specify a label allocation mode.
apply-label { per-instance [ static static-label-value ] | per-route }
By default, BGP allocates labels on a per-next-hop basis.
|
CAUTION: Executing this command will re-advertise all routes in the VPN instance, which will cause temporary interruption of running services in the VPN instance. Please be cautious. |
Associating a VPN instance with a Layer 3 interface
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Associate a VPN instance with the interface.
ip binding vpn-instance vpn-instance-name
By default, an interface is not associated with a VPN instance and belongs to the public network.
|
CAUTION: Associating a VPN instance with an interface or disassociating a VPN instance from an interface will clear the IP address and routing protocol settings of the interface. |
The ip binding vpn-instance command clears the IPv6 address of the interface. Therefore, reconfigure an IPv6 address for the interface after configuring this command.
Configuring route related attributes for a VPN instance
Restrictions and guidelines
Configurations made in VPN instance view apply to both IPv4 VPN and IPv6 VPN.
IPv6 VPN prefers the configurations in VPN instance IPv6 address family view over the configurations in VPN instance view.
Prerequisites
Before you perform this task, create the routing policies to be used by this task. For information about routing policies, see Layer 3—IP Routing Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter VPN instance view or VPN instance IPv6 address family view.
¡ Enter VPN instance view.
ip vpn-instance vpn-instance-name
¡ Execute the following commands in sequence to enter VPN instance IPv6 address family view:
ip vpn-instance vpn-instance-name
address-family ipv6
3. Configure route targets.
vpn-target vpn-target&<1-8> [ both | export-extcommunity | import-extcommunity ]
By default, no route targets are configured.
4. Set the maximum number of active routes.
routing-table limit number { warn-threshold | simply-alert }
By default, the number of active routes in a VPN instance is not limited.
Setting the maximum number of active routes for a VPN instance can prevent the PE from storing too many routes.
5. Apply an import routing policy.
import route-policy route-policy
By default, all routes matching the import target attribute are accepted.
6. Apply an export routing policy.
export route-policy route-policy
By default, routes to be advertised are not filtered.
7. Apply a tunnel policy to the VPN instance.
tnl-policy tunnel-policy-name
By default, only one tunnel is selected (no load balancing) in this order: LSP tunnel, CRLSP tunnel, SRLSP tunnel, and SR TE policy tunnel.
If the specified tunnel policy does not exist, the default tunnel policy is used.
For information about tunnel policies, see "Configuring tunnel policies."
Configuring routing between a PE and a CE
Configuring IPv6 static routing between a PE and a CE
About this task
Perform this configuration on the PE. On the CE, configure a common IPv6 static route.
For more information about IPv6 static routing, see Layer 3—IP Routing Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Configure an IPv6 static route for a VPN instance.
ipv6 route-static vpn-instance s-vpn-instance-name ipv6-address prefix-length { interface-type interface-number [ next-hop-address ] | nexthop-address [ public ] | vpn-instance d-vpn-instance-name nexthop-address } [ permanent ] [ preference preference ] [ tag tag-value ] [ description text ]
Configuring RIPng between a PE and a CE
About this task
Perform this configuration on the PE. On the CE, configure a common RIPng process.
For more information about RIPng, see Layer 3—IP Routing Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Create a RIPng process for a VPN instance and enter RIPng view.
ripng [ process-id ] vpn-instance vpn-instance-name
A RIPng process can belong to only one VPN instance.
3. Redistribute BGP rotues.
import-route bgp4+ [ as-number ] [ allow-ibgp ] [ cost cost-value | route-policy route-policy-name ] *
By default, RIPng does not redistribute routes from other routing protocols.
4. Return to system view.
quit
5. Enter interface view.
interface interface-type interface-number
6. Enable RIPng on the interface.
ripng process-id enable
By default, RIPng is disabled on an interface.
Configuring OSPFv3 between a PE and a CE
About this task
Perform this configuration on the PE. On the CE, configure a common OSPFv3 process.
For more information about OSPFv3, see Layer 3—IP Routing Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Create an OSPFv3 process for a VPN instance and enter OSPFv3 view.
ospfv3 [ process-id | vpn-instance vpn-instance-name ] *
An OSPFv3 process can belong to only one VPN instance.
Deleting a VPN instance also deletes all related OSPFv3 processes.
3. Set the router ID.
router-id router-id
4. Redistribute BGP routes.
import-route bgp4+ [ as-number ] [ allow-ibgp ] [ cost cost-value | nssa-only | route-policy route-policy-name | tag tag | type type ] *
By default, OSPFv3 does not redistribute routes from other routing protocols.
If the vpn-instance-capability simple command is not configured for the OSPFv3 process, the allow-ibgp keyword is optional to redistribute VPNv6 routes learned from MP-IBGP peers. In any other cases, if you do not specify the allow-ibgp keyword, the OSPFv3 process does not redistribute VPNv6 routes learned from MP-IBGP peers.
5. (Optional.) Configure OSPFv3 route attributes:
a. Set an OSPFv3 domain ID.
domain-id { domain-id [ secondary ] | null }
The default domain ID is 0.
|
Description |
Restrictions and guidelines |
|
When you redistribute OSPFv3 routes into BGP, BGP adds the primary domain ID to the redistributed BGP routes as a BGP extended community attribute. |
You can configure the same domain ID for different OSPFv3 processes. You must configure the same domain ID for all OSPFv3 processes of the same VPN to ensure correct route advertisement. |
b. Configure the type code of an OSPFv3 extended community attribute.
ext-community-type { domain-id type-code1 | route-type type-code2 | router-id type-code3 }
By default, the type codes for domain ID, route type, and router ID are 0x0005, 0x0306, 0x0107, respectively.
c. Configure an external route tag for redistributed VPN routes.
route-tag tag-value
By default, if BGP runs within an MPLS backbone, and the BGP AS number is not greater than 65535, the first two octets of the external route tag are 0xD000. The last two octets are the local BGP AS number. If the AS number is greater than 65535, the external route tag is 0.
d. Disable setting the DN bit in OSPFv3 LSAs.
disable-dn-bit-set
By default, when a PE redistributes BGP routes into OSPFv3 and creates OSPFv3 LSAs, it sets the DN bit for the LSAs.
This command might cause routing loops. Use it with caution.
e. Ignore the DN bit in OSPFv3 LSAs.
disable-dn-bit-check
By default, the PE checks the DN bit in OSPFv3 LSAs.
This command might cause routing loops. Use it with caution.
f. Enable the external route check feature for OSPFv3 LSAs.
route-tag-check enable
By default, the PE does not check the external route tag but checks the DN bit in OSPFv3 LSAs to avoid routing loops.
This command is only for backward compatibility with the old protocol (RFC 4577).
g. Return to system view.
quit
6. Enter interface view.
interface interface-type interface-number
7. Enable OSPFv3 on the interface.
ospfv3 process-id area area-id [ instance instance-id ]
By default, OSPFv3 is disabled on an interface.
For the command to be executed successfully, make sure the VPN instance to which the OSPFv3 process belongs is the VPN instance bound to the interface.
Configuring IPv6 IS-IS between a PE and a CE
About this task
Perform this configuration on the PE. On the CE, configure a common IPv6 IS-IS process.
For more information about IPv6 IS-IS, see Layer 3—IP Routing Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Create an IPv6 IS-IS process for a VPN instance and enter IS-IS view.
isis [ process-id ] vpn-instance vpn-instance-name
An IPv6 IS-IS process can belong to only one VPN instance.
3. Configure a network entity title for the IS-IS process.
network-entity net
By default, no NET is configured.
4. Create the IS-IS IPv6 unicast address family and enter its view.
address-family ipv6 [ unicast ]
5. Redistribute BGP rotues.
import-route bgp4+ [ as-number ] [ allow-ibgp ] [ cost cost-value ] | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] *
By default, IPv6 IS-IS does not redistribute routes from other routing protocols.
6. Return to system view.
quit
quit
7. Enter interface view.
interface interface-type interface-number
8. Enable IPv6 for the IS-IS process on the interface.
isis ipv6 enable [ process-id ]
By default, IPv6 is disabled for the IS-IS process on the interface.
Configuring EBGP between a PE and a CE
Configuring the PE
1. Enter system view.
system-view
2. Enable a BGP instance and enter BGP instance view.
bgp as-number [ instance instance-name ]
By default, BGP is not enabled.
3. Enter BGP-VPN instance view.
ip vpn-instance vpn-instance-name
4. Configure the CE as the VPN EBGP peer.
peer { group-name | ipv6-address [ prefix-length ] } as-number as-number
5. Create the BGP-VPN IPv6 unicast address family and enter its view.
address-family ipv6 [ unicast ]
Configuration commands in BGP-VPN IPv6 unicast address family view are the same as those in BGP IPv6 unicast address family view. For more information, see basic BGP configuration in Layer 3—IP Routing Configuration Guide.
6. Enable IPv6 unicast route exchange with the specified peer.
peer { group-name | ip-address [ prefix-length ] } enable
By default, BGP does not exchange IPv6 unicast routes with a peer.
7. Redistribute the routes of the local CE.
import-route protocol [ { process-id | all-processes } [ allow-direct | med med-value | route-policy route-policy-name ] * ]
A PE must redistribute the routes of the local CE into its VPN routing table so that it can advertise them to the peer PE.
8. (Optional.) Allow the local AS number to appear in the AS_PATH attribute of a received route, and set the maximum number of repetitions.
peer { group-name | ipv6-address [ prefix-length ] } allow-as-loop [ number ]
By default, BGP discards incoming route updates that contain the local AS number.
Execute this command in a hub-spoke network where EBGP is running between a PE and a CE to enable the PE to receive the route updates from the CE.
Configuring the CE
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Configure the PE as an EBGP peer.
peer { group-name | ipv6-address [ prefix-length ] } as-number as-number
4. Create the BGP IPv6 unicast address family and enter its view.
address-family ipv6 [ unicast ]
5. Enable IPv6 unicast route exchange with the specified peer.
peer { group-name | ip-address [ prefix-length ] } enable
By default, BGP does not exchange IPv6 unicast routes with a peer.
6. Configure route redistribution.
import-route protocol [ { process-id | all-processes } [ allow-direct | med med-value | route-policy route-policy-name ] * ]
A CE must advertise its VPN routes to the connected PE so that the PE can advertise them to the peer CE.
Configuring IBGP between a PE and a CE
Restrictions and guidelines
Use IBGP between PE and CE only in a basic IPv6 MPLS L3VPN network. In networks such as inter-AS VPN and carrier's carrier, you cannot configure IBGP between PE and CE.
Configuring the PE
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP-VPN instance view.
ip vpn-instance vpn-instance-name
Configuration commands in BGP-VPN instance view are the same as those in BGP instance view. For more information, see basic BGP configuration in Layer 3—IP Routing Configuration Guide.
4. Configure the CE as the VPN IBGP peer.
peer { group-name | ipv6-address [ prefix-length ] } as-number as-number
5. Create the BGP-VPN IPv6 unicast address family and enter its view.
address-family ipv6 [ unicast ]
6. Enable IPv6 unicast route exchange with the specified peer.
peer { group-name | ipv6-address [ prefix-length ] } enable
By default, BGP does not exchange IPv6 unicast routes with a peer.
7. Configure the CE as a client of the RR to enable the PE to advertise routes learned from the IBGP peer CE to other IBGP peers.
peer { group-name | ipv6-address [ prefix-length ] } reflect-client
By default, no RR or RR client is configured.
Configuring an RR does not change the next hop of a route. To change the next hop of a route, configure an inbound policy on the receiving side.
8. (Optional.) Enable route reflection between clients.
reflect between-clients
By default, route reflection between clients is enabled.
9. (Optional.) Configure the cluster ID for the RR.
reflector cluster-id { cluster-id | ip-address }
By default, the RR uses its own router ID as the cluster ID.
If multiple RRs exist in a cluster, use this command to configure the same cluster ID for all RRs in the cluster to avoid routing loops.
Configuring the CE
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Configure the PE as an IBGP peer.
peer { group-name | ipv6-address [ prefix-length ] } as-number as-number
4. Create the BGP IPv6 unicast family and enter its view.
address-family ipv6 [ unicast ]
5. Enable IPv6 unicast route exchange with the specified peer.
peer { group-name | ipv6-address [ prefix-length ] } enable
By default, BGP does not exchange IPv6 unicast routes with a peer.
6. Configure route redistribution.
import-route protocol [ { process-id | all-processes } [ allow-direct | med med-value | route-policy route-policy-name ] * ]
A CE must redistribute its routes to the PE so the PE can advertise them to the peer CE.
Configuring routing between PEs
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Configure the remote PE as the peer.
peer { group-name | ipv4-address [ mask-length ] } as-number as-number
4. Specify the source interface for TCP connections.
peer { group-name | ipv4-address [ mask-length ] } connect-interface interface-type interface-number
By default, BGP uses the outbound interface of the best route to the BGP peer as the source interface.
5. Create the BGP VPNv6 address family and enter its view.
address-family vpnv6
6. Enable BGP VPNv6 route exchange with the specified peer.
peer { group-name | ipv4-address [ mask-length ] } enable
By default, BGP does not exchange BGP VPNv6 routes with any peer.
Configuring BGP VPNv6 route control
About BGP VPNv6 route control
BGP VPNv6 route control is configured similarly with BGP route control, except that it is configured in BGP VPNv6 address family view. For more information about BGP route control, see basic BGP configuration and advanced BGP configuration in Layer 3—IP Routing Configuration Guide.
Specifying a preferred value for BGP VPNv6 routes
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv6 address family view.
address-family vpnv6
4. Specify a preferred value for routes received from a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } preferred-value value
The default preferred value is 0.
Setting the maximum number of received routes
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv6 address family view.
address-family vpnv6
4. Set the maximum number of routes BGP can receive from a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } route-limit prefix-number [ { alert-only | discard | reconnect reconnect-time } | percentage-value ] *
By default, the number of routes that BGP can receive from a peer or peer group is not limited.
Configuring BGP VPNv6 route reflection
About this task
To ensure the connectivity of IBGP peers, you must establish full-mesh IBGP connections, which costs massive network and CPU resources.
To reduce IBGP connections in the network, you can configure a router as a route reflector (RR) and configure other routers as its clients. You only need to establish IBGP connections between the RR and its clients to enable the RR to forward routes to the clients.
Procedure
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv6 address family view.
address-family vpnv6
4. Configure the local PE as the RR and specify the peer as the client.
peer { group-name | ipv4-address [ mask-length ] } reflect-client
By default, no RR or client is configured.
5. (Optional.) Enable route reflection between clients.
reflect between-clients
By default, route reflection between clients is enabled.
6. (Optional.) Configure a cluster ID for the RR.
reflector cluster-id { cluster-id | ip-address }
By default, an RR uses its own router ID as the cluster ID.
If multiple RRs exist in a cluster, use this command to configure the same cluster ID for all RRs in the cluster to avoid routing loops.
7. (Optional.) Configure a filtering policy for reflected routes.
rr-filter { ext-comm-list-number | ext-comm-list-name }
By default, an RR does not filter reflected routes.
Only IBGP routes whose extended community attribute matches the specified community list are reflected.
By configuring different filtering policies on RRs, you can implement load balancing among the RRs.
8. (Optional.) Allow the RR to change the attributes of routes to be reflected.
reflect change-path-attribute
By default, RR cannot change the attributes of routes to be reflected.
9. (Optional.) Specify a peer or peer group as a client of the nearby cluster.
peer { group-name | ipv4-address [ mask-length ] } reflect-nearby-group
By default, the nearby cluster does not have any clients.
The RR does not change the next hop of routes reflected to clients in the nearby cluster.
Configuring BGP VPNv6 route attributes
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv6 address family view.
address-family vpnv6
4. Configure the AS_PATH attribute.
¡ Allow the local AS number to appear in the AS_PATH attribute of routes received from a peer or peer group and set the maximum number of repetitions.
peer { group-name | ipv4-address [ mask-length ] } allow-as-loop [ number ]
By default, BGP discards route updates that contain the local AS number.
¡ Remove private AS numbers in BGP updates sent to an EBGP peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } public-as-only
By default, BGP updates sent to an EBGP peer or peer group can carry both public and private AS numbers.
5. Advertise the COMMUNITY attribute to a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } advertise-community
By default, BGP does not advertise the COMMUNITY attribute to any peers or peer groups.
6. Configure the SoO attribute for a peer for peer group.
peer { group-name | ipv4-address [ mask-length ] } soo site-of-origin
By default, the SoO attribute is not configured.
Configuring BGP VPNv6 route filtering
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv6 address family view.
address-family vpnv6
4. Filter advertised routes.
filter-policy { ipv6-acl-number | prefix-list ipv6-prefix-name } export [ direct | { isisv6 | ospfv3 | ripng } process-id | static ]
By default, BGP does not filter advertised routes.
5. Filter received routes.
filter-policy { ipv6-acl-number | prefix-list ipv6-prefix-name } import
By default, BGP does not filter received routes.
6. Configure AS_PATH list-based route filtering for a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } as-path-acl as-path-acl-number { export | import }
By default, AS_PATH list-based route filtering is not configured.
7. Configure ACL-based route filtering for a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } filter-policy ipv6-acl-number { export | import }
By default, ACL-based route filtering is not configured.
8. Configure IPv6 prefix list-based route filtering for a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } prefix-list ipv6-prefix-name { export | import }
By default, IPv6 prefix list-based route filtering is not configured.
9. Apply a routing policy to routes advertised to or received from a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } route-policy route-policy-name { export | import }
By default, no routing policy is applied.
10. Enable route target filtering for received BGP VPNv6 routes.
policy vpn-target
By default, route target filtering is enabled for received VPNv6 routes. Only VPNv6 routes whose export route target attribute matches the local import route target attribute are added to the routing table.
11. Enable the first AS number check for EBGP route advertisement to EBGP peers.
peer-as-check enable
By default, BGP does not check the first AS number of a received route and advertises the route to other peers.
After you execute this command, BGP checks the first AS number of a received route. If the AS number of an EBGP peer is the first AS number of the EBGP route to be advertised, BGP will not advertise the route to that EBGP peer.
This command is supported in Release 5111 and later.
Configuring BGP VPNv6 routes to use private network next hops
About this task
By default, the device does not change the next hop attribute of a received BGP VPNv6 route. The next hop address of a BGP VPNv6 route is a public address. This feature changes the next hop of a BGP VPNv6 route received from a peer or peer group to an IP address in the VPN instance. The outgoing label of the VPNv6 route is also changed to an invalid value. For example, the device received a VPNv6 route and its next hop address is 10.1.1.1, which is a public address by default. After this feature is configured, the next hop address changes to private address 10.1.1.1.
Restrictions and guidelines
After you configure this feature, the following applies:
· The device re-establishes the BGP sessions to the specified peer or to all peers in the specified peer group.
· The device receives a BGP VPNv6 route only when its RD is the same as a local RD.
· When advertising a BGP VPNv6 route received from the specified peer or peer group, the device does not change the route target attribute of the route.
· If you delete a VPN instance or its RD, BGP VPNv6 routes received from the specified peer or peer group and in the VPN instance will be deleted.
Procedure
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv6 address family view.
address-family vpnv6
4. Change the next hop of a BGP VPNv6 route received from a peer or peer group to a VPN instance address.
peer { group-name | ipv4-address [ mask-length ] } next-hop-vpn
By default, the device does not change the next hop attribute of a received BGP VPNv6 route, and the next hop belongs to the public network.
Configuring inter-AS IPv6 VPN
Configuring inter-AS IPv6 VPN option A
Inter-AS IPv6 VPN option A applies to scenarios where the number of VPNs and that of VPN routes on the PEs are relatively small.
To configure inter-AS IPv6 option A, perform the following tasks:
· Configure basic IPv6 MPLS L3VPN on each AS.
· Configure VPN instances on both PEs and ASBRs. The VPN instances on PEs allow CEs to access the network, and those on ASBRs are for access of the peer ASBRs.
In the inter-AS IPv6 VPN option A solution, for the same IPv6 VPN, the route targets configured on the PEs must match those configured on the ASBRs in the same AS. This makes sure VPN routes sent by the PEs (or ASBRs) can be received by the ASBRs (or PEs). Route targets configured on the PEs in different ASs do not have such requirements.
Configuring inter-AS IPv6 VPN option B
Restrictions and guidelines
An ASBR always uses its address as the next hop of VPNv6 routes advertised to an MP-IBGP peer regardless of the configuration of the peer next-hop-local command.
Configuring a PE
Configure basic IPv6 MPLS L3VPN, and specify the ASBR in the same AS as an MP-IBGP peer. The route targets for the VPN instances on the PEs in different ASs must match for the same IPv6 VPN.
Configuring an ASBR
1. Enter system view.
system-view
2. Enable MPLS and LDP on the interface connected to an internal router of the AS:
a. Configure an LSR ID for the local LSR.
mpls lsr-id lsr-id
By default, no LSR ID is configured.
b. Enable LDP on the local LSR and enter LDP view.
mpls ldp
By default, LDP is disabled.
c. Return to system view.
quit
d. Enter interface view of the interface connected to an internal router of the AS.
interface interface-type interface-number
e. Enable MPLS on the interface.
mpls enable
By default, MPLS is disabled on the interface.
f. Enable MPLS LDP on the interface.
mpls ldp enable
By default, MPLS LDP is disabled on the interface.
g. Return to system view.
quit
3. Enable MPLS on the interface connected to the remote ASBR:
a. Enter interface view of the interface connected to the remote ASBR.
interface interface-type interface-number
b. Enable MPLS on the interface.
mpls enable
By default, MPLS is disabled on the interface.
c. Return to system view.
quit
4. Enter BGP instance view.
bgp as-number [ instance instance-name ]
5. Configure PEs in the same AS as IBGP peers and ASBRs in different ASs as EBGP peers.
peer { group-name | ipv4-address [ mask-length ] } as-number as-number
6. Enter BGP VPNv6 address family view.
address-family vpnv6
7. Enable BGP to exchange VPNv6 routes with the PE in the same AS and the ASBR in another AS.
peer { group-name | ipv4-address [ mask-length ] } enable
By default, BGP cannot exchange VPNv6 routing information with a peer.
8. Disable route target filtering of received VPNv6 routes.
undo policy vpn-target
By default, route target filtering is enabled for received VPNv6 routes.
Configuring inter-AS IPv6 VPN option C
Prerequisites
Before you configure inter-AS option C, perform the following tasks:
· Configure BGP to advertise routes destined for a PE on PEs or ASBRs. For more information, see basic BGP configuration in Layer 3—IP Routing Configuration Guide.
· Configure a VPN instance on the PE.
· Configure routing between the PE and CE.
Configuring a PE
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Configure the ASBR in the same AS as an IBGP peer and Configure the PE in another AS as an EBGP peer
peer { group-name | ipv4-address [ mask-length ] } as-number as-number
4. Enter BGP IPv4 unicast address family view.
address-family ipv4 [ unicast ]
5. Enable BGP to exchange BGP IPv4 unicast routes with the ASBR in the same AS.
peer { group-name | ipv4-address [ mask-length ] } enable
By default, the PE does not exchange BGP IPv4 unicast routes with any peer.
6. Enable BGP to exchange labeled routes with the ASBR in the same AS.
peer { group-name | ipv4-address [ mask-length ] } label-route-capability
By default, the PE does not advertise labeled routes to any IPv4 peer or peer group.
7. Return to BGP instance view.
quit
8. Enter BGP VPNv6 address family view.
address-family vpnv6
9. Enable BGP to exchange BGP VPNv6 routing information with the EBGP peer.
peer ipv4-address [ mask-length ] enable
By default, the PE does not exchange labeled routes with an IPv4 peer.
10. (Optional.) Configure the PE to not change the next hop of routes advertised to the peer.
peer { group-name | ipv4-address [ mask-length ] } next-hop-invariable
By default, the device uses its address as the next hop of routes advertised to peers.
Configure this command on the RR so the RR does not change the next hop of advertised VPNv6 routes.
Configuring an ASBR-PE
1. Enter system view.
system-view
2. Configure a routing policy:
a. Create a routing policy, and enter routing policy view.
route-policy route-policy-name { deny | permit } node node-number
b. Match IPv4 routes carrying labels.
if-match mpls-label
By default, no MPLS label match criterion is configured.
You can configure if-match clauses in the routing policy to filter routes. Routes surviving the filtering are assigned labels, and all others are advertised as common IPv4 routes.
c. Set labels for IPv4 routes.
apply mpls-label
By default, no MPLS label is set for IPv4 routes.
d. Return to system view.
quit
3. Enable MPLS and LDP on the interface connected to an internal router of the AS:
a. Configure an LSR ID for the local LSR.
mpls lsr-id lsr-id
By default, no LSR ID is configured.
By default, no LSR
b. Enable LDP for the local LSR and enter LDP view.
mpls ldp
By default, LDP is disabled.
c. Return to system view.
quit
d. Enter interface view of the interface connected to an internal router of the AS.
interface interface-type interface-number
e. Enable MPLS on the interface.
mpls enable
By default, MPLS is disabled on the interface.
f. Enable MPLS LDP on the interface.
mpls ldp enable
By default, MPLS LDP is disabled on the interface.
g. Return to system view.
quit
4. Enable MPLS on the interface connected to the remote ASBR:
a. Enter interface view of the interface connected to the remote ASBR.
interface interface-type interface-number
b. Enable MPLS on the interface.
mpls enable
By default, MPLS is disabled on the interface.
c. Return to system view.
quit
5. Enter BGP instance view.
bgp as-number [ instance instance-name ]
6. Configure the PE in the same AS as an IBGP peer and the ASBR in another AS as an EBGP peer.
peer { group-name | ipv4-address [ mask-length ] } as-number as-number
7. Create the BGP IPv4 unicast address family and enter its view.
address-family ipv4 [ unicast ]
8. Enable IPv4 unicast route exchange with the PE in the same AS and the ASBR in another AS.
peer { group-name | ipv4-address [ mask-length ] } enable
By default, BGP cannot exchange IPv4 unicast routes with any peer.
9. Enable labeled IPv4 route exchange with the PE in the same AS and the ASBR in another AS.
peer { group-name | ipv4-address [ mask-length ] } label-route-capability
By default, BGP cannot exchange labeled IPv4 routes with any peer.
10. Configure the ASBR to set itself as the next hop of routes advertised to the PE in the local AS.
peer { group-name | ipv4-address [ mask-length ] } next-hop-local
By default, BGP does not use its address as the next hop of routes.
11. Apply a routing policy to routes incoming from or outgoing to a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } route-policy route-policy-name { export | import }
By default, no routing policy is applied.
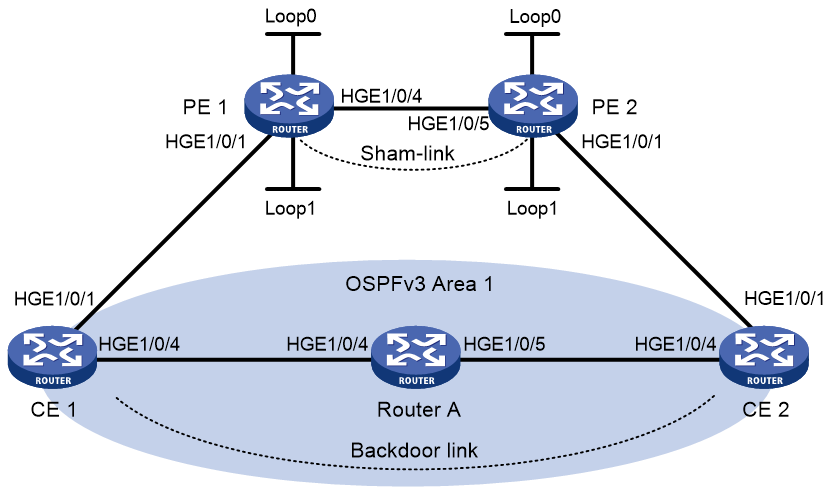
Configuring an OSPFv3 sham link
Prerequisites
Before you configure an OSPFv3 sham link, perform the following tasks:
· Configure basic IPv6 MPLS L3VPN (OSPFv3 is used between PE and CE).
· Configure OSPFv3 in the LAN where customer CEs reside.
Redistributing the loopback interface address
1. Enter system view.
system-view
2. Create a loopback interface and enter loopback interface view.
interface loopback interface-number
3. Associate the loopback interface with a VPN instance.
ip binding vpn-instance vpn-instance-name
By default, the interface is not associated with any VPN instances and belongs to the public network.
4. Configure an IPv6 address for the loopback interface.
See Layer 3—IP Services Configuration Guide.
By default, no IPv6 address is configured for the loopback interface.
5. Enter BGP instance view.
bgp as-number [ instance instance-name ]
6. Enter BGP-VPN instance view.
ip vpn-instance vpn-instance-name
7. Enter BGP-VPN IPv6 unicast address family view.
address-family ipv6 [ unicast ]
8. Redistribute direct routes into BGP (including the loopback interface address).
import-route direct
By default, no direct routes are redistributed into BGP.
Creating a sham link
1. Enter system view.
system-view
2. Enter OSPFv3 view.
ospfv3 [ process-id | vpn-instance vpn-instance-name ] *
3. Enter OSPFv3 area view.
area area-id
4. Configure an OSPFv3 sham link.
sham-link source-ipv6-address destination-ipv6-address [ cost cost-value | dead dead-interval | hello hello-interval | instance instance-id | ipsec-profile profile-name | keychain keychain-name | retransmit retrans-interval | trans-delay delay ] *
Configuring BGP AS number substitution and SoO attribute
About this task
When CEs at different sites have the same AS number, configure the BGP AS number substitution feature to avoid route loss.
When a PE uses different interfaces to connect different CEs in a site, the BGP AS number substitution feature introduces a routing loop. To remove the routing loop, configure the SoO attribute on the PE.
For more information about the BGP AS number substitution feature and the SoO attribute, see "Configuring MPLS L3VPN." For more information about the commands in this feature, see advanced BGP commands in Layer 3—IP Routing Command Reference.
Procedure
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP-VPN instance view.
ip vpn-instance vpn-instance-name
4. Enable the BGP AS number substitution feature.
peer { group-name | ipv6-address [ prefix-length ] } substitute-as
By default, BGP AS number substitution is disabled.
5. Enter BGP-VPN IPv6 unicast address family view.
address-family ipv6 [ unicast ]
6. (Optional.) Configure the SoO attribute for a BGP peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } soo site-of-origin
By default, the SoO attribute is not configured.
Configuring the BGP additional path feature
About this task
By default, BGP advertises only one optimal route. When the optimal route fails, traffic forwarding will be interrupted until route convergence completes.
The BGP additional path (Add-Path) feature enables BGP to advertise multiple routes with the same prefix and different next hops to a peer or peer group. When the optimal route fails, the suboptimal route becomes the optimal route, which shortens the traffic interruption time.
You can enable the BGP additional path sending, receiving, or both sending and receiving capabilities on a BGP peer. For two BGP peers to successfully negotiate the additional path capabilities, make sure one end has the sending capability and the other end has the receiving capability.
For more information about the BGP additional path configuration commands, see advanced BGP commands in Layer 3—IP Routing Command Reference.
Procedure
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv6 address family view.
address-family vpnv6
4. Configure the BGP additional path capabilities.
peer { group-name | ipv4-address [ mask-length ] } additional-paths { receive | send } *
By default, no BGP additional path capabilities are configured.
5. Set the maximum number of Add-Path optimal routes that can be advertised to a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } advertise additional-paths best number
By default, a maximum number of one Add-Path optimal route can be advertised to a peer or peer group.
6. Set the maximum total number of Add-Path optimal routes that can be advertised to all peers.
additional-paths select-best best-number
By default, a maximum total number of one Add-Path optimal route can be advertised to all peers.
Configuring route replication
Configuring the public instance
About this task
Configure the public instance to enable the mutual access between public network and private network users.
Procedure
1. Enter system view.
system-view
2. Enter public instance view.
ip public-instance
3. Configure an RD for the public instance.
route-distinguisher route-distinguisher
By default, no RD is configured for the public instance.
4. Configure a route target for the public instance.
vpn-target vpn-target&<1-8> [ both | export-extcommunity | import-extcommunity ]
By default, no route target is configured for the public instance.
5. Enter public instance IPv6 address family view.
address-family ipv6
6. Configure a route target for the public instance IPv6 address family.
vpn-target vpn-target&<1-8> [ both | export-extcommunity | import-extcommunity ]
By default, no route target is configured.
Configuring BGP route replication between different VPN instances
About this task
In an IPv6 BGP/IPv6 MPLS L3VPN network, only VPN instances that have matching route targets can communicate with each other.
The route replication feature provides the following functions:
· Enables a VPN instance to communicate with the public network or other VPN instances by replicating routes from the public network or other VPN instances.
· Enables the public network to communicate with a VPN instance by replicating routes from the VPN instance.
In an intelligent traffic control network, traffic of different tenants is assigned to different VPNs. To enable the tenants to communicate with the public network, configure this feature to replicate routes from the public network to the VPN instances.
Replicating routes from the public network or VPN instances to a VPN instance
1. Enter system view.
system-view
2. Enter VPN instance view.
ip vpn-instance vpn-instance-name
3. Enter VPN instance IPv6 address family view.
address-family ipv6
4. Replicate routes from the public network or other VPN instances.
route-replicate from { public | vpn-instance vpn-instance-name } protocol bgp4+ as-number [ route-policy route-policy-name ]
route-replicate from { public | vpn-instance vpn-instance-name } protocol { direct | static | { isisv6 | ospfv3 | ripng } process-id } [ advertise ] [ route-policy route-policy-name ]
By default, a VPN instance cannot replicate routes from the public network or other VPN instances.
Replicating routes from a VPN instance to the public network
1. Enter system view.
system-view
2. Enter public instance view.
ip public-instance
3. Enter public instance IPv6 address family view.
address-family ipv6
4. Replicate routes from a VPN instance to the public network.
route-replicate from vpn-instance vpn-instance-name protocol bgp4+ as-number [ route-policy route-policy-name ]
route-replicate from vpn-instance vpn-instance-name protocol { direct | static | { isisv6 | ospfv3 | ripng } process-id } [ advertise ] [ route-policy route-policy-name ]
By default, the public network cannot replicate routes from VPN instances.
Configuring BGP route replication between public and VPN instances
About this task
In traffic cleaning scenarios, traffic between the public and private networks are filtered by firewalls and traffic of different tenants is assigned to different VPNs. To enable the tenants to communicate with the public network under the protection of firewalls, you can configure BGP route replication between public and VPN instances.
After you configure this feature, the public and VPN instances replicate all BGP routes including route attributes from each other.
Software version and feature compatibility
This feature is supported in Release 5111 and later.
Restrictions and guidelines
This feature also enables BGP route replication between VPN instances, so VPNs cannot be isolated. Configure this feature only in specific scenarios, for example, the traffic cleaning scenario.
For more information about the route-replicate enable command, see MPLS L3VPN commands in MPLS Command Reference.
Procedure
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enable BGP route replication between public and VPN instances.
route-replicate enable
By default, BGP route replication between public and VPN instances is disabled.
Configuring route re-origination
About this task
By default, BGP routes in different VPN instances are isolated. In some networks, a device might need to advertise routes across VPN instances or advertise the routes in a VPN instance through other VPN instances to hide the routing information of the VPN instance.
After you configure this feature, the current VPN instance will re-originate the BGP unicast routes from other VPN instances that have the same route target as the current VPN instance. Locally redistributed routes (such as the IGP routes redistributed by using the import-route command) will not be re-originated. The re-originated routes can be advertised to BGP peers.
Software version and feature compatibility
This feature is supported in Release 5111 and later.
Restrictions and guidelines
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP-VPN instance view.
ip vpn-instance vpn-instance-name
4. Enter BGP-VPN IPv6 unicast address family view.
address-family ipv6 [ unicast ]
5. Re-originate BGP unicast routes from other VPN instances.
advertise route-reoriginate [ route-policy route-policy-name ] [ replace-rt ]
By default, a VPN instance cannot re-originate BGP unicast routes from other VPN instances.
This command enables reoriginating BGP routes based on only the BGP routes that match the route targets of the current VPN instance. The VPN instance does not reoriginate BGP routes based on the redistributed local routes.
Enabling prioritized withdrawal of specific routes
About this task
Configure BGP to send withdrawal messages of specific routes prior to other routes to ensure fast route switchover and reduce the traffic interruption time for the specific routes.
For more information about the commands of this feature, see basic BGP commands in Layer 3—IP Routing Command Reference.
Procedure
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv6 address family view.
address-family vpnv6
4. Configure BGP to send withdrawal messages of routes matching the specified routing policy prior to other routes.
update-first route-policy route-policy-name
By default, BGP does not send withdrawal messages of specific routes prior to other routes.
Enabling logging for BGP route flapping
About this task
This feature enables BGP to generate logs for BGP route flappings that trigger log generation. The generated logs are sent to the information center. For the logs to be output correctly, you must also configure information center on the device. For more information about the information center, see Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv6 address family view.
address-family vpnv6
4. Enable logging for BGP route flapping.
log-route-flap monitor-time monitor-count [ log-count-limit | route-policy route-policy-name ] *
By default, logging for BGP route flapping is disabled.
Verifying and maintaining IPv6 MPLS L3VPN
Verifying IPv6 MPLS L3VPN configuration and running status
Verifying BGP route configuration
Perform display tasks in any view.
· Display BGP peer and route summary information.
display bgp [ instance instance-name ] vpnv6 summary
For more information about the commands, see basic BGP commands in Layer 3—IP Routing Command Reference.
· Display BGP VPNv6 routes.
display bgp [ instance instance-name ] routing-table vpnv6 [ [ route-distinguisher route-distinguisher ] [ ipv6-address prefix-length [ advertise-info ] | as-path-acl { as-path-acl-number | as-path-acl-name } | community-list { { basic-community-list-number | comm-list-name } [ whole-match ] | adv-community-list-number } ] | peer ipv4-address { advertised-routes | received-routes } [ ipv6-address prefix-length | statistics ] | statistics ]
Verifying BGP peer and peer group configuration
This section only lists the commands for verifying BGP peer and peer group configuration. For more information about the commands, see basic BGP commands in Layer 3—IP Routing Command Reference.
Perform display tasks in any view.
· Display BGP VPNv6 peer information.
display bgp [ instance instance-name ] peer vpnv6 [ ipv4-address mask-length | { ipv4-address | group-name group-name } log-info | [ ipv4-address ] verbose ]
· Display BGP VPNv6 peer group information.
display bgp [ instance instance-name ] group vpnv6 [ group-name group-name ]
Verifying BGP update group configuration
To display BGP VPNv6 update group configuration, execute the following command in any view:
display bgp [ instance instance-name ] update-group vpnv6 [ ipv4-address ]
For more information about the command, see basic BGP commands in Layer 3—IP Routing Command Reference.
Verifying incoming label and outgoing label configuration
Perform display tasks in any view.
· Display incoming labels for BGP VPNv6 routes.
display bgp [ instance instance-name ] routing-table vpnv6 inlabel
· Display outgoing labels for BGP VPNv6 routes.
display bgp [ instance instance-name ] routing-table vpnv6 outlabel
Verifying VPN instance configuration
Perform display tasks in any view.
· Display information about a VPN instance.
display ip vpn-instance [ instance-name vpn-instance-name ]
· Display the IPv6 routing table for a VPN instance.
display ipv6 routing-table vpn-instance vpn-instance-name [ verbose ]
For more information about the command, see IP routing basics commands in Layer 3—IP Routing Command Reference.
· Display the IPv6 FIB of a VPN instance.
display ipv6 fib vpn-instance vpn-instance-name [ ipv6-address [ prefix-length ] ]
For more information about the command, see IP forwarding basics commands in Layer 3—IP Services Command Reference.
Verifying OSPFv3 sham link configuration
To display OSPFv3 sham link information, execute the following command in any view:
display ospfv3 [ process-id ] [ area area-id ] sham-link [ verbose ]
Resetting BGP sessions
About this task
You can soft-reset or reset BGP sessions to apply new BGP configurations. A soft reset operation updates BGP routing information without tearing down BGP connections. A reset operation updates BGP routing information by tearing down, and then re-establishing BGP connections. Soft reset requires that BGP peers have route refresh capability.
Procedure
The following information only lists the commands for resetting BGP sessions. For more information about the commands, see basic BGP commands in Layer 3—IP Routing Command Reference.
Perform refresh or reset tasks in user view:
· Soft-reset BGP sessions for the BGP VPNv6 address family.
refresh bgp [ instance instance-name ] { ipv4-address [ mask-length ] | all | external | group group-name | internal } { export | import } vpnv6
· Reset BGP sessions for the BGP VPNv6 address family.
reset bgp [ instance instance-name ] { as-number | ipv4-address [ mask-length ] | all | external | internal | group group-name } vpnv6
IPv6 MPLS L3VPN configuration examples
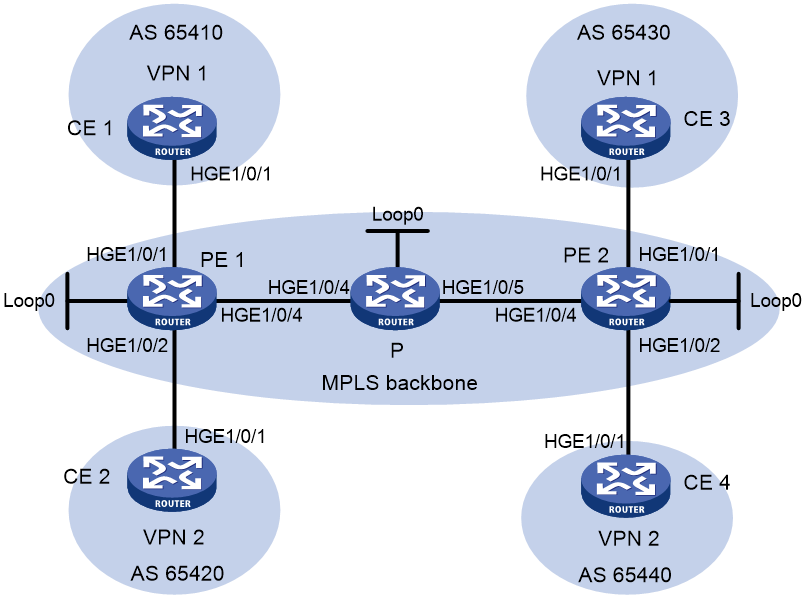
Example: Configuring IPv6 MPLS L3VPNs
Network configuration
CE 1 and CE 3 belong to VPN 1. CE 2 and CE 4 belong to VPN 2.
VPN 1 uses route target attributes 111:1. VPN 2 uses route target attributes 222:2. Users of different VPNs cannot access each other.
Run EBGP between CEs and PEs to exchange VPN routing information.
PEs use OSPF to communicate with each other and use MP-IBGP to exchange VPN routing information.
Figure 3 Network diagram
Table 1 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
||||
|
CE 1 |
HGE1/0/1 |
2001:1::1/96 |
P |
Loop0 |
2.2.2.9/32 |
|
|||
|
PE 1 |
Loop0 |
1.1.1.9/32 |
|
HGE1/0/4 |
172.1.1.2/24 |
|
|||
|
|
HGE1/0/1 |
2001:1::2/96 |
|
HGE1/0/5 |
172.2.1.1/24 |
|
|||
|
|
HGE1/0/2 |
2001:2::2/96 |
PE 2 |
Loop0 |
3.3.3.9/32 |
|
|||
|
|
HGE1/0/4 |
172.1.1.1/24 |
|
HGE1/0/1 |
2001:3::2/96 |
|
|||
|
CE 2 |
HGE1/0/1 |
2001:2::1/96 |
|
HGE1/0/2 |
2001:4::2/96 |
|
|||
|
CE 3 |
HGE1/0/1 |
2001:3::1/96 |
|
HGE1/0/4 |
172.2.1.2/24 |
|
|||
|
CE 4 |
HGE1/0/1 |
2001:4::1/96 |
|
|
|
|
|||
Prerequisite
By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface.
Procedure
1. Configure OSPF on the MPLS backbone to ensure IP connectivity among the PEs and the P router:
# Configure PE 1.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 1.1.1.9 32
[PE1-LoopBack0] quit
[PE1] interface hundredgige 1/0/4
[PE1-HundredGigE1/0/4] ip address 172.1.1.1 24
[PE1-HundredGigE1/0/4] quit
[PE1] ospf
[PE1-ospf-1] area 0
[PE1-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255
[PE1-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0
[PE1-ospf-1-area-0.0.0.0] quit
[PE1-ospf-1] quit
# Configure the P router.
<P> system-view
[P] interface loopback 0
[P-LoopBack0] ip address 2.2.2.9 32
[P-LoopBack0] quit
[P] interface hundredgige 1/0/4
[P-HundredGigE1/0/4] ip address 172.1.1.2 24
[P-HundredGigE1/0/4] quit
[P] interface hundredgige 1/0/5
[P-HundredGigE1/0/5] ip address 172.2.1.1 24
[P-HundredGigE1/0/5] quit
[P] ospf
[P-ospf-1] area 0
[P-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255
[P-ospf-1-area-0.0.0.0] network 172.2.1.0 0.0.0.255
[P-ospf-1-area-0.0.0.0] network 2.2.2.9 0.0.0.0
[P-ospf-1-area-0.0.0.0] quit
[P-ospf-1] quit
# Configure PE 2.
<PE2> system-view
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 3.3.3.9 32
[PE2-LoopBack0] quit
[PE2] interface hundredgige 1/0/4
[PE2-HundredGigE1/0/4] ip address 172.2.1.2 24
[PE2-HundredGigE1/0/4] quit
[PE2] ospf
[PE2-ospf-1] area 0
[PE2-ospf-1-area-0.0.0.0] network 172.2.1.0 0.0.0.255
[PE2-ospf-1-area-0.0.0.0] network 3.3.3.9 0.0.0.0
[PE2-ospf-1-area-0.0.0.0] quit
[PE2-ospf-1] quit
# Execute the display ospf peer command to verify that OSPF adjacencies in Full state have been established between PE 1, P, and PE 2. Execute the display ip routing-table command to verify that the PEs have learned the routes to the loopback interfaces of each other. (Details not shown.)
2. Configure basic MPLS and enable MPLS LDP on the MPLS backbone to establish LDP LSPs:
# Configure PE 1.
[PE1] mpls lsr-id 1.1.1.9
[PE1] mpls ldp
[PE1-ldp] quit
[PE1] interface hundredgige 1/0/4
[PE1-HundredGigE1/0/4] mpls enable
[PE1-HundredGigE1/0/4] mpls ldp enable
[PE1-HundredGigE1/0/4] quit
# Configure the P router.
[P] mpls lsr-id 2.2.2.9
[P] mpls ldp
[P-ldp] quit
[P] interface hundredgige 1/0/4
[P-HundredGigE1/0/4] mpls enable
[P-HundredGigE1/0/4] mpls ldp enable
[P-HundredGigE1/0/4] quit
[P] interface hundredgige 1/0/5
[P-HundredGigE1/0/5] mpls enable
[P-HundredGigE1/0/5] mpls ldp enable
[P-HundredGigE1/0/5] quit
# Configure PE 2.
[PE2] mpls lsr-id 3.3.3.9
[PE2] mpls ldp
[PE2-ldp] quit
[PE2] interface hundredgige 1/0/4
[PE2-HundredGigE1/0/4] mpls enable
[PE2-HundredGigE1/0/4] mpls ldp enable
[PE2-HundredGigE1/0/4] quit
# Execute the display mpls ldp peer command to verify that LDP sessions in Operational state have been established between PE 1, P, and PE 2. Execute the display mpls ldp lsp command to verify that the LSPs have been established by LDP. (Details not shown.)
3. Configure IPv6 VPN instances on the PEs to allow CE access:
# Configure PE 1.
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 100:1
[PE1-vpn-instance-vpn1] vpn-target 111:1
[PE1-vpn-instance-vpn1] quit
[PE1] ip vpn-instance vpn2
[PE1-vpn-instance-vpn2] route-distinguisher 100:2
[PE1-vpn-instance-vpn2] vpn-target 222:2
[PE1-vpn-instance-vpn2] quit
[PE1] interface hundredgige 1/0/1
[PE1-HundredGigE1/0/1] ip binding vpn-instance vpn1
[PE1-HundredGigE1/0/1] ipv6 address 2001:1::2 96
[PE1-HundredGigE1/0/1] quit
[PE1] interface hundredgige 1/0/2
[PE1-HundredGigE1/0/2] ip binding vpn-instance vpn2
[PE1-HundredGigE1/0/2] ipv6 address 2001:2::2 96
[PE1-HundredGigE1/0/2] quit
# Configure PE 2.
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] route-distinguisher 200:1
[PE2-vpn-instance-vpn1] vpn-target 111:1
[PE2-vpn-instance-vpn1] quit
[PE2] ip vpn-instance vpn2
[PE2-vpn-instance-vpn2] route-distinguisher 200:2
[PE2-vpn-instance-vpn2] vpn-target 222:2
[PE2-vpn-instance-vpn2] quit
[PE2] interface hundredgige 1/0/1
[PE2-HundredGigE1/0/1] ip binding vpn-instance vpn1
[PE2-HundredGigE1/0/1] ipv6 address 2001:3::2 96
[PE2-HundredGigE1/0/1] quit
[PE2] interface hundredgige 1/0/2
[PE2-HundredGigE1/0/2] ip binding vpn-instance vpn2
[PE2-HundredGigE1/0/2] ipv6 address 2001:4::2 96
[PE2-HundredGigE1/0/2] quit
# Configure IP addresses for the CEs according to Table 1. (Details not shown.)
# Execute the display ip vpn-instance command on the PEs to display information about the VPN instances, for example, on PE 1.
[PE1] display ip vpn-instance
Total VPN-Instances configured : 2
Total IPv4 VPN-Instances configured : 0
Total IPv6 VPN-Instances configured : 2
VPN-Instance Name RD Address family Create time
vpn1 100:1 IPv6 2012/02/13 12:49:08
vpn2 100:2 IPv6 2012/02/13 12:49:20
# Use the ping command on the PEs to verify that the PEs can ping their attached CEs, for example, on PE 1.
[PE1] ping ipv6 -vpn-instance vpn1 2001:1::1
Ping6(56 bytes) 2001:1::2 --> 2001:1::1, press CTRL_C to break
56 bytes from 2001:1::1, icmp_seq=0 hlim=64 time=9.000 ms
56 bytes from 2001:1::1, icmp_seq=1 hlim=64 time=1.000 ms
56 bytes from 2001:1::1, icmp_seq=2 hlim=64 time=0.000 ms
56 bytes from 2001:1::1, icmp_seq=3 hlim=64 time=0.000 ms
56 bytes from 2001:1::1, icmp_seq=4 hlim=64 time=0.000 ms
--- Ping6 statistics for 2001:1::1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/2.000/9.000/3.521 ms
4. Establish EBGP peer relationships between the PEs and CEs to allow them to exchange VPN routes:
# Configure CE 1.
<CE1> system-view
[CE1] bgp 65410
[CE1-bgp-default] peer 2001:1::2 as-number 100
[CE1-bgp-default] address-family ipv6 unicast
[CE1-bgp-default-ipv6] peer 2001:1::2 enable
[CE1-bgp-default-ipv6] import-route direct
[CE1-bgp-default-ipv6] quit
[CE1-bgp-default] quit
# Configure the other CEs (CE 2 through CE 4) in the same way that CE 1 is configured. (Details not shown.)
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp-default] ip vpn-instance vpn1
[PE1-bgp-default-vpn1] peer 2001:1::1 as-number 65410
[PE1-bgp-default-vpn1] address-family ipv6 unicast
[PE1-bgp-default-ipv6-vpn1] peer 2001:1::1 enable
[PE1-bgp-default-ipv6-vpn1] quit
[PE1-bgp-default-vpn1] quit
[PE1-bgp-default] ip vpn-instance vpn2
[PE1-bgp-default-vpn2] peer 2001:2::1 as-number 65420
[PE1-bgp-default-vpn2] address-family ipv6 unicast
[PE1-bgp-default-ipv6-vpn2] peer 2001:2::1 enable
[PE1-bgp-default-ipv6-vpn2] quit
[PE1-bgp-default-vpn2] quit
[PE1-bgp-default] quit
# Configure PE 2 in the same way that PE 1 is configured. (Details not shown.)
# Execute the display bgp peer ipv6 vpn-instance command on the PEs to verify that a BGP peer relationship in Established state has been established between a PE and a CE. (Details not shown.)
5. Configure an MP-IBGP peer relationship between the PEs:
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp-default] peer 3.3.3.9 as-number 100
[PE1-bgp-default] peer 3.3.3.9 connect-interface loopback 0
[PE1-bgp-default] address-family vpnv6
[PE1-bgp-default-vpnv6] peer 3.3.3.9 enable
[PE1-bgp-default-vpnv6] quit
[PE1-bgp-default] quit
# Configure PE 2.
[PE2] bgp 100
[PE2-bgp-default] peer 1.1.1.9 as-number 100
[PE2-bgp-default] peer 1.1.1.9 connect-interface loopback 0
[PE2-bgp-default] address-family vpnv6
[PE2-bgp-default-vpnv6] peer 1.1.1.9 enable
[PE2-bgp-default-vpnv6] quit
[PE2-bgp-default] quit
# Execute the display bgp peer vpnv6 command on the PEs to verify that a BGP peer relationship in Established state has been established between the PEs. (Details not shown.)
Verifying the configuration
# Execute the display ipv6 routing-table vpn-instance command on the PEs.
[PE1] display ipv6 routing-table vpn-instance vpn1
Destinations : 6 Routes : 6
Destination: ::1/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 2001:1::/96 Protocol : Direct
NextHop : :: Preference: 0
Interface : HGE1/0/1 Cost : 0
Destination: 2001:1::2/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 2001:3::/96 Protocol : BGP4+
NextHop : ::FFFF:3.3.3.9 Preference: 255
Interface : HGE1/0/4 Cost : 0
Destination: FE80::/10 Protocol : Direct
NextHop : :: Preference: 0
Interface : NULL0 Cost : 0
Destination: FF00::/8 Protocol : Direct
NextHop : :: Preference: 0
Interface : NULL0 Cost : 0
[PE1] display ipv6 routing-table vpn-instance vpn2
Destinations : 6 Routes : 6
Destination: ::1/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 2001:2::/96 Protocol : Direct
NextHop : :: Preference: 0
Interface : HGE1/0/2 Cost : 0
Destination: 2001:2::2/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 2001:4::/96 Protocol : BGP4+
NextHop : ::FFFF:3.3.3.9 Preference: 255
Interface : HGE1/0/4 Cost : 0
Destination: FE80::/10 Protocol : Direct
NextHop : :: Preference: 0
Interface : NULL0 Cost : 0
Destination: FF00::/8 Protocol : Direct
NextHop : :: Preference: 0
Interface : NULL0 Cost : 0
The output shows that PE 1 has routes to the remote CEs. Output on PE 2 is similar.
# Verify that CEs of the same VPN can ping each other, whereas those of different VPNs cannot. For example, CE 1 can ping CE 3 (2001:3::1), but cannot ping CE 4 (2001:4::1). (Details not shown.)
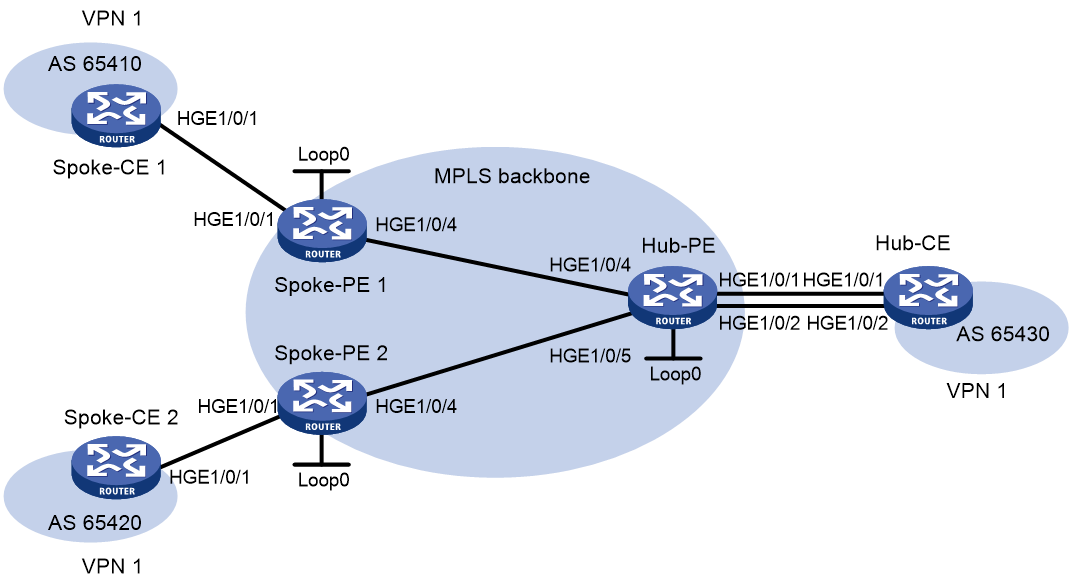
Example: Configuring a hub-spoke network
Network configuration
The Spoke-CEs cannot communicate directly. They can communicate only through the Hub-CE.
Configure EBGP between the Spoke-CEs and Spoke-PEs and between the Hub-CE and Hub-PE to exchange VPN routing information.
Configure OSPF between the Spoke-PEs and Hub-PE to implement communication between the PEs. Configure MP-IBGP between the Spoke-PEs and Hub-PE to exchange VPN routing information.
Figure 4 Network diagram
Table 2 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Spoke-CE 1 |
HGE1/0/1 |
11::1/64 |
Hub-CE |
HGE1/0/1 |
13::1/64 |
|
Spoke-PE 1 |
Loop0 |
1.1.1.9/32 |
|
HGE1/0/2 |
14::1/64 |
|
|
HGE1/0/1 |
11::2/64 |
Hub-PE |
Loop0 |
2.2.2.9/32 |
|
|
HGE1/0/4 |
172.1.1.1/24 |
|
HGE1/0/4 |
172.1.1.2/24 |
|
Spoke-CE 2 |
HGE1/0/1 |
12::1/64 |
|
HGE1/0/5 |
172.2.1.2/24 |
|
Spoke-PE 2 |
Loop0 |
3.3.3.9/32 |
|
HGE1/0/1 |
13::2/64 |
|
|
HGE1/0/1 |
12::2/64 |
|
HGE1/0/2 |
14::2/64 |
|
|
HGE1/0/4 |
172.2.1.1/24 |
|
|
|
Prerequisite
By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface.
Procedure
1. Configure an IGP on the MPLS backbone to ensure IP connectivity within the backbone:
# Configure Spoke-PE 1.
<Spoke-PE1> system-view
[Spoke-PE1] interface loopback 0
[Spoke-PE1-LoopBack0] ip address 1.1.1.9 32
[Spoke-PE1-LoopBack0] quit
[Spoke-PE1] interface hundredgige 1/0/4
[Spoke-PE1-HundredGigE1/0/4] ip address 172.1.1.1 24
[Spoke-PE1-HundredGigE1/0/4] quit
[Spoke-PE1] ospf
[Spoke-PE1-ospf-1] area 0
[Spoke-PE1-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255
[Spoke-PE1-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0
[Spoke-PE1-ospf-1-area-0.0.0.0] quit
[Spoke-PE1-ospf-1] quit
# Configure Spoke-PE 2.
<Spoke-PE2> system-view
[Spoke-PE2] interface loopback 0
[Spoke-PE2-LoopBack0] ip address 3.3.3.9 32
[Spoke-PE2-LoopBack0] quit
[Spoke-PE2] interface hundredgige 1/0/4
[Spoke-PE2-HundredGigE1/0/4] ip address 172.1.1.1 24
[Spoke-PE2-HundredGigE1/0/4] quit
[Spoke-PE2] ospf
[Spoke-PE2-ospf-1] area 0
[Spoke-PE2-ospf-1-area-0.0.0.0] network 172.2.1.0 0.0.0.255
[Spoke-PE2-ospf-1-area-0.0.0.0] network 3.3.3.9 0.0.0.0
[Spoke-PE2-ospf-1-area-0.0.0.0] quit
[Spoke-PE2-ospf-1] quit
# Configure Hub-PE.
<Hub-PE> system-view
[Hub-PE] interface loopback 0
[Hub-PE-LoopBack0] ip address 2.2.2.9 32
[Hub-PE-LoopBack0] quit
[Hub-PE] interface hundredgige 1/0/4
[Hub-PE-HundredGigE1/0/4] ip address 172.1.1.2 24
[Hub-PE-HundredGigE1/0/4] quit
[Hub-PE] interface hundredgige 1/0/5
[Hub-PE-HundredGigE1/0/5] ip address 172.2.1.2 24
[Hub-PE-HundredGigE1/0/5] quit
[Hub-PE] ospf
[Hub-PE-ospf-1] area 0
[Hub-PE-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255
[Hub-PE-ospf-1-area-0.0.0.0] network 172.2.1.0 0.0.0.255
[Hub-PE-ospf-1-area-0.0.0.0] network 2.2.2.9 0.0.0.0
[Hub-PE-ospf-1-area-0.0.0.0] quit
[Hub-PE-ospf-1] quit
# Execute the display ospf peer command on the PEs to verify that OSPF adjacencies in Full state have been established between the PEs. Execute the display ip routing-table command on the PEs to verify that the PEs have learned the routes to the loopback interfaces of each other. (Details not shown.)
2. Configure basic MPLS and MPLS LDP on the MPLS backbone to establish LDP LSPs:
# Configure Spoke-PE 1.
[Spoke-PE1] mpls lsr-id 1.1.1.9
[Spoke-PE1] mpls ldp
[Spoke-PE1-ldp] quit
[Spoke-PE1] interface hundredgige 1/0/4
[Spoke-PE1-HundredGigE1/0/4] mpls enable
[Spoke-PE1-HundredGigE1/0/4] mpls ldp enable
[Spoke-PE1-HundredGigE1/0/4] quit
# Configure Spoke-PE 2.
[Spoke-PE2] mpls lsr-id 3.3.3.9
[Spoke-PE2] mpls ldp
[Spoke-PE2-ldp] quit
[Spoke-PE2] interface hundredgige 1/0/4
[Spoke-PE2-HundredGigE1/0/4] mpls enable
[Spoke-PE2-HundredGigE1/0/4] mpls ldp enable
[Spoke-PE2-HundredGigE1/0/4] quit
# Configure Hub-PE.
[Hub-PE] mpls lsr-id 2.2.2.9
[Hub-PE] mpls ldp
[Hub-PE-ldp] quit
[Hub-PE] interface hundredgige 1/0/4
[Hub-PE-HundredGigE1/0/4] mpls enable
[Hub-PE-HundredGigE1/0/4] mpls ldp enable
[Hub-PE-HundredGigE1/0/4] quit
[Hub-PE] interface hundredgige 1/0/5
[Hub-PE-HundredGigE1/0/5] mpls enable
[Hub-PE-HundredGigE1/0/5] mpls ldp enable
[Hub-PE-HundredGigE1/0/5] quit
# Execute the display mpls ldp peer command on the PEs to verify that LDP sessions in Operational state have been established between the PEs. Execute the display mpls ldp lsp command on the PEs to verify that the LSPs have been established by LDP. (Details not shown.)
3. Configure VPN instances on the Spoke-PEs and Hub-PE:
# Configure Spoke-PE 1.
[Spoke-PE1] ip vpn-instance vpn1
[Spoke-PE1-vpn-instance-vpn1] route-distinguisher 100:1
[Spoke-PE1-vpn-instance-vpn1] vpn-target 111:1 import-extcommunity
[Spoke-PE1-vpn-instance-vpn1] vpn-target 222:2 export-extcommunity
[Spoke-PE1-vpn-instance-vpn1] quit
[Spoke-PE1] interface hundredgige 1/0/1
[Spoke-PE1-HundredGigE1/0/1] ip binding vpn-instance vpn1
[Spoke-PE1-HundredGigE1/0/1] ip address 11::2 24
[Spoke-PE1-HundredGigE1/0/1] quit
# Configure Spoke-PE 2.
[Spoke-PE2] ip vpn-instance vpn1
[Spoke-PE2-vpn-instance-vpn1] route-distinguisher 100:2
[Spoke-PE2-vpn-instance-vpn1] vpn-target 111:1 import-extcommunity
[Spoke-PE2-vpn-instance-vpn1] vpn-target 222:2 export-extcommunity
[Spoke-PE2-vpn-instance-vpn1] quit
[Spoke-PE2] interface hundredgige 1/0/1
[Spoke-PE2-HundredGigE1/0/1] ip binding vpn-instance vpn1
[Spoke-PE2-HundredGigE1/0/1] ip address 12::2 24
[Spoke-PE2-HundredGigE1/0/1] quit
# Configure Hub-PE.
[Hub-PE] ip vpn-instance vpn1-in
[Hub-PE-vpn-instance-vpn1-in] route-distinguisher 100:3
[Hub-PE-vpn-instance-vpn1-in] vpn-target 222:2 import-extcommunity
[Hub-PE-vpn-instance-vpn1-in] quit
[Hub-PE] ip vpn-instance vpn1-out
[Hub-PE-vpn-instance-vpn1-out] route-distinguisher 100:4
[Hub-PE-vpn-instance-vpn1-out] vpn-target 111:1 export-extcommunity
[Hub-PE-vpn-instance-vpn1-out] quit
[Hub-PE] interface hundredgige 1/0/1
[Hub-PE-HundredGigE1/0/1] ip binding vpn-instance vpn1-in
[Hub-PE-HundredGigE1/0/1] ip address 13::2 24
[Hub-PE-HundredGigE1/0/1] quit
[Hub-PE] interface hundredgige 1/0/2
[Hub-PE-HundredGigE1/0/2] ip binding vpn-instance vpn1-out
[Hub-PE-HundredGigE1/0/2] ip address 14::2 24
[Hub-PE-HundredGigE1/0/2] quit
# Configure IP addresses for the CEs according to Table 2. (Details not shown.)
# Execute the display ip vpn-instance command on the PEs to display the VPN instance configuration. This example uses Spoke-PE 1.
[Spoke-PE1] display ip vpn-instance
Total VPN-Instances configured : 1
Total IPv4 VPN-Instances configured : 0
Total IPv6 VPN-Instances configured : 1
VPN-Instance Name RD Address family Create time
vpn1 100:1 IPv6 2009/04/08 10:55:07
# Use the ping command on the PEs to verify that the PEs can ping their attached CEs. This example uses Spoke-PE 1.
[Spoke-PE1] ping ipv6 -vpn-instance vpn1 11::1
Ping6(56 bytes) 11::2 --> 11::1, press CTRL_C to break
56 bytes from 11::1, icmp_seq=0 hlim=64 time=0.000 ms
56 bytes from 11::1, icmp_seq=1 hlim=64 time=1.000 ms
56 bytes from 11::1, icmp_seq=2 hlim=64 time=0.000 ms
56 bytes from 11::1, icmp_seq=3 hlim=64 time=1.000 ms
56 bytes from 11::1, icmp_seq=4 hlim=64 time=0.000 ms
--- Ping6 statistics for 11::1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/0.400/1.000/0.490 ms
4. Establish EBGP peer relationships between the PEs and CEs, and redistribute VPN routes into BGP:
# Configure Spoke-CE 1.
<Spoke-CE1> system-view
[Spoke-CE1] bgp 65410
[Spoke-CE1-bgp-default] peer 11::2 as-number 100
[Spoke-CE1-bgp-default] address-family ipv6
[Spoke-CE1-bgp-default-ipv6] peer 11::2 enable
[Spoke-CE1-bgp-default-ipv6] import-route direct
[Spoke-CE1-bgp-default-ipv6] quit
[Spoke-CE1-bgp-default] quit
# Configure Spoke-CE 2.
<Spoke-CE2> system-view
[Spoke-CE2] bgp 65420
[Spoke-CE2-bgp-default] peer 12::2 as-number 100
[Spoke-CE2-bgp-default] address-family ipv6
[Spoke-CE2-bgp-default-ipv6] peer 12::2 enable
[Spoke-CE2-bgp-default-ipv6] import-route direct
[Spoke-CE2-bgp-default-ipv6] quit
[Spoke-CE2-bgp-default] quit
# Configure Hub-CE.
<Hub-CE> system-view
[Hub-CE] bgp 65430
[Hub-CE-bgp-default] peer 13::2 as-number 100
[Hub-CE-bgp-default] peer 14::2 as-number 100
[Hub-CE-bgp-default] address-family ipv6
[Hub-CE-bgp-default-ipv6] peer 13::2 enable
[Hub-CE-bgp-default-ipv6] peer 14::2 enable
[Hub-CE-bgp-default-ipv6] import-route direct
[Hub-CE-bgp-default-ipv6] quit
[Hub-CE-bgp-default] quit
# Configure Spoke-PE 1.
[Spoke-PE1] bgp 100
[Spoke-PE1-bgp-default] ip vpn-instance vpn1
[Spoke-PE1-bgp-default-vpn1] peer 11::1 as-number 65410
[Spoke-PE1-bgp-default-vpn1] address-family ipv6
[Spoke-PE1-bgp-default-ipv6-vpn1] peer 11::1 enable
[Spoke-PE1-bgp-default-ipv6-vpn1] quit
[Spoke-PE1-bgp-default-vpn1] quit
[Spoke-PE1-bgp-default] quit
# Configure Spoke-PE 2.
[Spoke-PE2] bgp 100
[Spoke-PE2-bgp-default] ip vpn-instance vpn1
[Spoke-PE2-bgp-default-vpn1] peer 12::1 as-number 65420
[Spoke-PE2-bgp-default-vpn1] address-family ipv6
[Spoke-PE2-bgp-default-ipv6-vpn1] peer 12::1 enable
[Spoke-PE2-bgp-default-ipv6-vpn1] quit
[Spoke-PE2-bgp-default-vpn1] quit
[Spoke-PE2-bgp-default] quit
# Configure Hub-PE.
[Hub-PE] bgp 100
[Hub-PE-bgp-default] ip vpn-instance vpn1-in
[Hub-PE-bgp-default-vpn1-in] peer 13::1 as-number 65430
[Hub-PE-bgp-default-vpn1-in] address-family ipv6
[Hub-PE-bgp-default-ipv6-vpn1-in] peer 13::1 enable
[Hub-PE-bgp-default-ipv6-vpn1-in] quit
[Hub-PE-bgp-default-vpn1-in] quit
[Hub-PE-bgp-default] ip vpn-instance vpn1-out
[Hub-PE-bgp-default-vpn1-out] peer 14::1 as-number 65430
[Hub-PE-bgp-default-vpn1-out] address-family ipv6
[Hub-PE-bgp-default-ipv6-vpn1-out] peer 14::1 enable
[Hub-PE-bgp-default-ipv6-vpn1-out] peer 14::1 allow-as-loop 2
[Hub-PE-bgp-default-ipv6-vpn1-out] quit
[Hub-PE-bgp-default-vpn1-out] quit
[Hub-PE-bgp-default] quit
# Execute the display bgp peer ipv6 vpn-instance command on the PEs to verify that a BGP peer relationship in Established state has been established between a PE and a CE. (Details not shown.)
5. Establish an MP-IBGP peer relationship between the Spoke-PEs and Hub-PE:
# Configure Spoke-PE 1.
[Spoke-PE1] bgp 100
[Spoke-PE1-bgp-default] peer 2.2.2.9 as-number 100
[Spoke-PE1-bgp-default] peer 2.2.2.9 connect-interface loopback 0
[Spoke-PE1-bgp-default] address-family vpnv6
[Spoke-PE1-bgp-default-vpnv6] peer 2.2.2.9 enable
[Spoke-PE1-bgp-default-vpnv6] quit
[Spoke-PE1-bgp-default] quit
# Configure Spoke-PE 2.
[Spoke-PE2] bgp 100
[Spoke-PE2-bgp-default] peer 2.2.2.9 as-number 100
[Spoke-PE2-bgp-default] peer 2.2.2.9 connect-interface loopback 0
[Spoke-PE2-bgp-default] address-family vpnv6
[Spoke-PE2-bgp-default-vpnv6] peer 2.2.2.9 enable
[Spoke-PE2-bgp-default-vpnv6] quit
[Spoke-PE2-bgp-default] quit
# Configure Hub-PE.
[Hub-PE] bgp 100
[Hub-PE-bgp-default] peer 1.1.1.9 as-number 100
[Hub-PE-bgp-default] peer 1.1.1.9 connect-interface loopback 0
[Hub-PE-bgp-default] peer 3.3.3.9 as-number 100
[Hub-PE-bgp-default] peer 3.3.3.9 connect-interface loopback 0
[Hub-PE-bgp-default] address-family vpnv6
[Hub-PE-bgp-default-vpnv6] peer 1.1.1.9 enable
[Hub-PE-bgp-default-vpnv6] peer 3.3.3.9 enable
[Hub-PE-bgp-default-vpnv6] quit
[Hub-PE-bgp-default] quit
# Execute the display bgp peer vpnv6 command on the PEs to verify that a BGP peer relationship in Established state has been established between the PEs. (Details not shown.)
Verifying the configuration
# Verify that Spoke-CE 1 and Spoke-CE 2 can ping each other. The TTL value indicates that traffic from Spoke-CE 1 to Spoke-CE 2 passes six hops (64-59+1) and is forwarded through Hub-CE. This example uses Spoke-CE 1.
[Spoke-CE1] ping ipv6 12::1
Ping6(56 bytes) 11::1 --> 12::1, press CTRL_C to break
56 bytes from 12::1, icmp_seq=0 hlim=59 time=0.000 ms
56 bytes from 12::1, icmp_seq=1 hlim=59 time=1.000 ms
56 bytes from 12::1, icmp_seq=2 hlim=59 time=0.000 ms
56 bytes from 12::1, icmp_seq=3 hlim=59 time=1.000 ms
56 bytes from 12::1, icmp_seq=4 hlim=59 time=0.000 ms
--- Ping6 statistics for 12::1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/0.400/1.000/0.490 ms
Example: Configuring IPv6 MPLS L3VPN inter-AS option A
Network configuration
CE 1 and CE 2 belong to the same VPN. CE 1 accesses the network through PE 1 in AS 100 and CE 2 accesses the network through PE 2 in AS 200.
Configure IPv6 MPLS L3VPN inter-AS option A, and use VRF-to-VRF method to manage VPN routes.
Run OSPF on the MPLS backbone of each AS.
Figure 5 Network diagram
Table 3 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
HGE1/0/1 |
2001:1::1/96 |
CE 2 |
HGE1/0/1 |
2001:2::1/96 |
|
PE 1 |
Loop0 |
1.1.1.9/32 |
PE 2 |
Loop0 |
4.4.4.9/32 |
|
|
HGE1/0/1 |
2001:1::2/96 |
|
HGE1/0/1 |
2001:2::2/96 |
|
|
HGE1/0/4 |
172.1.1.2/24 |
|
HGE1/0/4 |
162.1.1.2/24 |
|
ASBR-PE1 |
Loop0 |
2.2.2.9/32 |
ASBR-PE2 |
Loop0 |
3.3.3.9/32 |
|
|
HGE1/0/4 |
172.1.1.1/24 |
|
HGE1/0/4 |
162.1.1.1/24 |
|
|
HGE1/0/5 |
2002:1::1/96 |
|
HGE1/0/5 |
2002:1::2/96 |
Prerequisite
By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface.
Restrictions and guidelines
For the same VPN, the route targets for the VPN instance on the PE must match those for the VPN instance on the ASBR-PE in the same AS. This is not required for PEs in different ASs.
Procedure
1. Configure an IGP on each MPLS backbone to ensure IP connectivity within the backbone.
This example uses OSPF. Be sure to advertise the route to the 32-bit loopback interface address of each router through OSPF. Use the loopback interface address of a router as the router's LSR ID. (Details not shown.)
# Execute the display ospf peer command to verify that each ASBR-PE has established an OSPF adjacency in Full state with the PE in the same AS, and that the PEs and ASBR-PEs in the same AS have learned the routes to the loopback interfaces of each other. Execute the ping command to verify that the PEs and ASBR-PEs in the same AS can ping each other. (Details not shown.)
2. Configure basic MPLS and enable MPLS LDP on each MPLS backbone to establish LDP LSPs:
# Configure basic MPLS on PE 1, and enable MPLS LDP for both PE 1 and the interface connected to ASBR-PE 1.
<PE1> system-view
[PE1] mpls lsr-id 1.1.1.9
[PE1] mpls ldp
[PE1-ldp] quit
[PE1] interface hundredgige 1/0/4
[PE1-HundredGigE1/0/4] mpls enable
[PE1-HundredGigE1/0/4] mpls ldp enable
[PE1-HundredGigE1/0/4] quit
# Configure basic MPLS on ASBR-PE 1, and enable MPLS LDP for both ASBR-PE 1 and the interface connected to PE 1.
<ASBR-PE1> system-view
[ASBR-PE1] mpls lsr-id 2.2.2.9
[ASBR-PE1] mpls ldp
[ASBR-PE1-ldp] quit
[ASBR-PE1] interface hundredgige 1/0/4
[ASBR-PE1-HundredGigE1/0/4] mpls enable
[ASBR-PE1-HundredGigE1/0/4] mpls ldp enable
[ASBR-PE1-HundredGigE1/0/4] quit
# Configure basic MPLS on ASBR-PE 2, and enable MPLS LDP for both ASBR-PE 2 and the interface connected to PE 2.
<ASBR-PE2> system-view
[ASBR-PE2] mpls lsr-id 3.3.3.9
[ASBR-PE2] mpls ldp
[ASBR-PE2-ldp] quit
[ASBR-PE2] interface hundredgige 1/0/4
[ASBR-PE2-HundredGigE1/0/4] mpls enable
[ASBR-PE2-HundredGigE1/0/4] mpls ldp enable
[ASBR-PE2-HundredGigE1/0/4] quit
# Configure basic MPLS on PE 2, and enable MPLS LDP for both PE 2 and the interface connected to ASBR-PE 2.
<PE2> system-view
[PE2] mpls lsr-id 4.4.4.9
[PE2] mpls ldp
[PE2-ldp] quit
[PE2] interface hundredgige 1/0/4
[PE2-HundredGigE1/0/4] mpls enable
[PE2-HundredGigE1/0/4] mpls ldp enable
[PE2-HundredGigE1/0/4] quit
# Execute the display mpls ldp session command on the routers to verify that the session status is Operational, and that each PE and the ASBR-PE in the same AS have established an LDP neighbor relationship. (Details not shown.)
3. Configure a VPN instance on the PEs:
# Configure CE 1.
<CE1> system-view
[CE1] interface hundredgige 1/0/1
[CE1-HundredGigE1/0/1] ipv6 address 2001:1::1 96
[CE1-HundredGigE1/0/1] quit
# Configure PE 1.
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 100:2
[PE1-vpn-instance-vpn1] vpn-target 100:1 both
[PE1-vpn-instance-vpn1] quit
[PE1] interface hundredgige 1/0/1
[PE1-HundredGigE1/0/1] ip binding vpn-instance vpn1
[PE1-HundredGigE1/0/1] ipv6 address 2001:1::2 96
[PE1-HundredGigE1/0/1] quit
# Configure CE 2.
<CE2> system-view
[CE2] interface hundredgige 1/0/1
[CE2-HundredGigE1/0/1] ipv6 address 2001:2::1 96
[CE2-HundredGigE1/0/1] quit
# Configure PE 2.
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] route-distinguisher 200:1
[PE2-vpn-instance-vpn1] vpn-target 200:1 both
[PE2-vpn-instance-vpn1] quit
[PE2] interface hundredgige 1/0/1
[PE2-HundredGigE1/0/1] ip binding vpn-instance vpn1
[PE2-HundredGigE1/0/1] ipv6 address 2001:2::2 96
[PE2-HundredGigE1/0/1] quit
# On ASBR-PE 1, create a VPN instance, and bind the VPN instance to the interface connected to ASBR-PE 2. ASBR-PE 1 considers ASBR-PE 2 to be its attached CE.
[ASBR-PE1] ip vpn-instance vpn1
[ASBR-PE1-vpn-instance-vpn1] route-distinguisher 100:1
[ASBR-PE1-vpn-instance-vpn1] vpn-target 100:1 both
[ASBR-PE1-vpn-instance-vpn1] quit
[ASBR-PE1] interface hundredgige 1/0/5
[ASBR-PE1-HundredGigE1/0/5] ip binding vpn-instance vpn1
[ASBR-PE1-HundredGigE1/0/5] ipv6 address 2002:1::1 96
[ASBR-PE1-HundredGigE1/0/5] quit
# On ASBR-PE 2, create a VPN instance, and bind the VPN instance to the interface connected to ASBR-PE 1. ASBR-PE 2 considers ASBR-PE 1 to be its attached CE.
[ASBR-PE2] ip vpn-instance vpn1
[ASBR-PE2-vpn-instance-vpn1] route-distinguisher 200:1
[ASBR-PE2-vpn-instance-vpn1] vpn-target 200:1 both
[ASBR-PE2-vpn-instance-vpn1] quit
[ASBR-PE2] interface hundredgige 1/0/5
[ASBR-PE2-HundredGigE1/0/5] ip binding vpn-instance vpn1
[ASBR-PE2-HundredGigE1/0/5] ipv6 address 2002:1::2 96
[ASBR-PE2-HundredGigE1/0/5] quit
# Execute the display ip vpn-instance command to display VPN instance information. Verify that each PE can ping its attached CE, and that ASBR-PE 1 and ASBR-PE 2 can ping each other. (Details not shown.)
4. Establish EBGP peer relationships between PEs and CEs to allow them to exchange VPN routes:
# Configure CE 1.
[CE1] bgp 65001
[CE1-bgp-default] peer 2001:1::2 as-number 100
[CE1-bgp-default] address-family ipv6 unicast
[CE1-bgp-default-ipv6] peer 2001:1::2 enable
[CE1-bgp-default-ipv6] import-route direct
[CE1-bgp-default-ipv6] quit
[CE1-bgp-default] quit
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp-default] ip vpn-instance vpn1
[PE1-bgp-default-vpn1] peer 2001:1::1 as-number 65001
[PE1-bgp-default-vpn1] address-family ipv6 unicast
[PE1-bgp-default-ipv6-vpn1] peer 2001:1::1 enable
[PE1-bgp-default-ipv6-vpn1] quit
[PE1-bgp-default-vpn1] quit
[PE1-bgp-default] quit
# Configure CE 2.
[CE2] bgp 65002
[CE2-bgp-default] peer 2001:2::2 as-number 200
[CE2-bgp-default] address-family ipv6
[CE2-bgp-default-ipv6] peer 2001:2::2 enable
[CE2-bgp-default-ipv6] import-route direct
[CE2-bgp-default-ipv6] quit
[CE2-bgp-default] quit
# Configure PE 2.
[PE2] bgp 200
[PE2-bgp-default] ip vpn-instance vpn1
[PE2-bgp-default-vpn1] peer 2001:2::1 as-number 65002
[PE2-bgp-default-vpn1] address-family ipv6 unicast
[PE2-bgp-default-ipv6-vpn1] peer 2001:2::1 enable
[PE2-bgp-default-ipv6-vpn1] quit
[PE2-bgp-default-vpn1] quit
[PE2-bgp-default] quit
5. Establish an IBGP peer relationship between each PE and the ASBR-PE in the same AS and an EBGP peer relationship between the ASBR-PEs:
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp-default] peer 2.2.2.9 as-number 100
[PE1-bgp-default] peer 2.2.2.9 connect-interface loopback 0
[PE1-bgp-default] address-family vpnv6
[PE1-bgp-default-vpnv6] peer 2.2.2.9 enable
[PE1-bgp-default-vpnv6] quit
[PE1-bgp-default] quit
# Configure ASBR-PE 1.
[ASBR-PE1] bgp 100
[ASBR-PE1-bgp-default] ip vpn-instance vpn1
[ASBR-PE1-bgp-default-vpn1] peer 2002:1::2 as-number 200
[ASBR-PE1-bgp-default-vpn1] address-family ipv6 unicast
[ASBR-PE1-bgp-default-ipv6-vpn1] peer 2002:1::2 enable
[ASBR-PE1-bgp-default-ipv6-vpn1] quit
[ASBR-PE1-bgp-default-vpn1] quit
[ASBR-PE1-bgp-default] peer 1.1.1.9 as-number 100
[ASBR-PE1-bgp-default] peer 1.1.1.9 connect-interface loopback 0
[ASBR-PE1-bgp-default] address-family vpnv6
[ASBR-PE1-bgp-default-vpnv6] peer 1.1.1.9 enable
[ASBR-PE1-bgp-default-vpnv6] quit
[ASBR-PE1-bgp-default] quit
# Configure ASBR-PE 2.
[ASBR-PE2] bgp 200
[ASBR-PE2-bgp-default] ip vpn-instance vpn1
[ASBR-PE2-bgp-default-vpn1] peer 2002:1::1 as-number 100
[ASBR-PE2-bgp-default-vpn1] address-family ipv6 unicast
[ASBR-PE2-bgp-default-ipv6-vpn1] peer 2002:1::1 enable
[ASBR-PE2-bgp-default-ipv6-vpn1] quit
[ASBR-PE2-bgp-default-vpn1] quit
[ASBR-PE2-bgp-default] peer 4.4.4.9 as-number 200
[ASBR-PE2-bgp-default] peer 4.4.4.9 connect-interface loopback 0
[ASBR-PE2-bgp-default] address-family vpnv6
[ASBR-PE2-bgp-default-vpnv6] peer 4.4.4.9 enable
[ASBR-PE2-bgp-default-vpnv6] quit
[ASBR-PE2-bgp-default] quit
# Configure PE 2.
[PE2] bgp 200
[PE2-bgp-default] peer 3.3.3.9 as-number 200
[PE2-bgp-default] peer 3.3.3.9 connect-interface loopback 0
[PE2-bgp-default] address-family vpnv6
[PE2-bgp-default-vpnv6] peer 3.3.3.9 enable
[PE2-bgp-default-vpnv6] quit
[PE2-bgp-default] quit
Verifying the configuration
# Verify that the CEs can learn the route to each other and can ping each other. (Details not shown.)
Example: Configuring inter-AS IPv6 VPN option B
Network configuration
Site 1 and Site 2 belong to the same VPN. CE 1 of Site 1 accesses the network through PE 1 in AS 100, and CE 2 of Site 2 accesses the network through PE 2 in AS 600.
PEs in the same AS run IS-IS.
PE 1 and ASBR-PE 1 exchange VPNv6 routes through MP-IBGP. PE 2 and ASBR-PE 2 exchange VPNv6 routes through MP-IBGP. ASBR-PE 1 and ASBR-PE 2 exchange VPNv6 routes through MP-EBGP.
ASBRs do not perform route target filtering of received VPNv6 routes.
Figure 6 Network diagram
Table 4 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
PE 1 |
Loop0 |
2.2.2.9/32 |
PE 2 |
Loop0 |
5.5.5.9/32 |
|
|
HGE1/0/1 |
30::1/64 |
|
HGE1/0/1 |
20::1/64 |
|
|
HGE1/0/5 |
1.1.1.2/8 |
|
HGE1/0/5 |
9.1.1.2/8 |
|
ASBR-PE 1 |
Loop0 |
3.3.3.9/32 |
ASBR-PE 2 |
Loop0 |
4.4.4.9/32 |
|
|
HGE1/0/5 |
1.1.1.1/8 |
|
HGE1/0/5 |
9.1.1.1/8 |
|
|
HGE1/0/4 |
11.0.0.2/8 |
|
HGE1/0/4 |
11.0.0.1/8 |
Prerequisite
By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface.
Procedure
1. Configure PE 1:
# Configure IS-IS on PE 1.
<PE1> system-view
[PE1] isis 1
[PE1-isis-1] network-entity 10.111.111.111.111.00
[PE1-isis-1] quit
# Configure LSR ID, and enable MPLS and LDP.
[PE1] mpls lsr-id 2.2.2.9
[PE1] mpls ldp
[PE1-ldp] quit
# Configure interface HundredGigE 1/0/5, and enable IS-IS, MPLS, and LDP on the interface.
[PE1] interface hundredgige 1/0/5
[PE1-HundredGigE1/0/5] ip address 1.1.1.2 255.0.0.0
[PE1-HundredGigE1/0/5] isis enable 1
[PE1-HundredGigE1/0/5] mpls enable
[PE1-HundredGigE1/0/5] mpls ldp enable
[PE1-HundredGigE1/0/5] quit
# Configure interface Loopback 0, and enable IS-IS on it.
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 2.2.2.9 32
[PE1-LoopBack0] isis enable 1
[PE1-LoopBack0] quit
# Create VPN instance vpn1, and configure the RD and route target attributes.
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 11:11
[PE1-vpn-instance-vpn1] vpn-target 1:1 2:2 3:3 import-extcommunity
[PE1-vpn-instance-vpn1] vpn-target 3:3 export-extcommunity
[PE1-vpn-instance-vpn1] quit
# Bind the interface connected to CE 1 to the created VPN instance.
[PE1] interface hundredgige 1/0/1
[PE1-HundredGigE1/0/1] ip binding vpn-instance vpn1
[PE1-HundredGigE1/0/1] ip address 30::1 64
[PE1-HundredGigE1/0/1] quit
# Enable BGP on PE 1.
[PE1] bgp 100
# Configure IBGP peer 3.3.3.9 as a VPNv6 peer.
[PE1-bgp-default] peer 3.3.3.9 as-number 100
[PE1-bgp-default] peer 3.3.3.9 connect-interface loopback 0
[PE1-bgp-default] address-family vpnv6
[PE1-bgp-default-vpnv6] peer 3.3.3.9 enable
[PE1-bgp-default-vpnv6] quit
# Redistribute direct routes to the VPN routing table of vpn1.
[PE1-bgp-default] ip vpn-instance vpn1
[PE1-bgp-default-vpn1] address-family ipv6 unicast
[PE1-bgp-default-ipv6-vpn1] import-route direct
[PE1-bgp-default-ipv6-vpn1] quit
[PE1-bgp-default-vpn1] quit
[PE1-bgp-default] quit
2. Configure ASBR-PE 1:
# Enable IS-IS on ASBR-PE 1.
<ASBR-PE1> system-view
[ASBR-PE1] isis 1
[ASBR-PE1-isis-1] network-entity 10.222.222.222.222.00
[ASBR-PE1-isis-1] quit
# Configure LSR ID, and enable MPLS and LDP.
[ASBR-PE1] mpls lsr-id 3.3.3.9
[ASBR-PE1] mpls ldp
[ASBR-PE1-ldp] quit
# Configure interface HundredGigE 1/0/5, and enable IS-IS, MPLS, and LDP on the interface.
[ASBR-PE1] interface hundredgige 1/0/5
[ASBR-PE1-HundredGigE1/0/5] ip address 1.1.1.1 255.0.0.0
[ASBR-PE1-HundredGigE1/0/5] isis enable 1
[ASBR-PE1-HundredGigE1/0/5] mpls enable
[ASBR-PE1-HundredGigE1/0/5] mpls ldp enable
[ASBR-PE1-HundredGigE1/0/5] quit
# Configure interface HundredGigE 1/0/4, and enable MPLS.
[ASBR-PE1] interface hundredgige 1/0/4
[ASBR-PE1-HundredGigE1/0/4] ip address 11.0.0.2 255.0.0.0
[ASBR-PE1-HundredGigE1/0/4] mpls enable
[ASBR-PE1-HundredGigE1/0/4] quit
# Configure interface Loopback 0, and enable IS-IS on it.
[ASBR-PE1] interface loopback 0
[ASBR-PE1-LoopBack0] ip address 3.3.3.9 32
[ASBR-PE1-LoopBack0] isis enable 1
[ASBR-PE1-LoopBack0] quit
# Enable BGP on ASBR-PE 1.
[ASBR-PE1] bgp 100
[ASBR-PE1-bgp-default] peer 2.2.2.9 as-number 100
[ASBR-PE1-bgp-default] peer 2.2.2.9 connect-interface loopback 0
[ASBR-PE1-bgp-default] peer 11.0.0.1 as-number 600
[ASBR-PE1-bgp-default] peer 11.0.0.1 connect-interface hundredgige 1/0/4
# Disable route target based filtering of received VPNv6 routes.
[ASBR-PE1-bgp-default] address-family vpnv6
[ASBR-PE1-bgp-default-vpnv6] undo policy vpn-target
# Configure IBGP peer 2.2.2.9 and EBGP peer 11.0.0.1 as VPNv6 peers.
[ASBR-PE1-bgp-default-vpnv6] peer 11.0.0.1 enable
[ASBR-PE1-bgp-default-vpnv6] peer 2.2.2.9 enable
[ASBR-PE1-bgp-default-vpnv6] quit
3. Configure ASBR-PE 2:
# Enable IS-IS on ASBR-PE 2.
<ASBR-PE2> system-view
[ASBR-PE2] isis 1
[ASBR-PE2-isis-1] network-entity 10.222.222.222.222.00
[ASBR-PE2-isis-1] quit
# Configure LSR ID, and enable MPLS and LDP.
[ASBR-PE2] mpls lsr-id 4.4.4.9
[ASBR-PE2] mpls ldp
[ASBR-PE2-ldp] quit
# Configure interface HundredGigE 1/0/5, and enable IS-IS, MPLS, and LDP on the interface.
[ASBR-PE2] interface hundredgige 1/0/5
[ASBR-PE2-HundredGigE1/0/5] ip address 9.1.1.1 255.0.0.0
[ASBR-PE2-HundredGigE1/0/5] isis enable 1
[ASBR-PE2-HundredGigE1/0/5] mpls enable
[ASBR-PE2-HundredGigE1/0/5] mpls ldp enable
[ASBR-PE2-HundredGigE1/0/5] quit
# Configure interface HundredGigE 1/0/4, and enable MPLS.
[ASBR-PE2] interface hundredgige 1/0/4
[ASBR-PE2-HundredGigE1/0/4] ip address 11.0.0.1 255.0.0.0
[ASBR-PE2-HundredGigE1/0/4] mpls enable
[ASBR-PE2-HundredGigE1/0/4] quit
# Configure interface Loopback 0, and enable IS-IS on it.
[ASBR-PE2] interface loopback 0
[ASBR-PE2-LoopBack0] ip address 4.4.4.9 32
[ASBR-PE2-LoopBack0] isis enable 1
[ASBR-PE2-LoopBack0] quit
# Enable BGP on ASBR-PE 2.
[ASBR-PE2] bgp 600
[ASBR-PE2-bgp-default] peer 11.0.0.2 as-number 100
[ASBR-PE2-bgp-default] peer 11.0.0.2 connect-interface hundredgige 1/0/4
[ASBR-PE2-bgp-default] peer 5.5.5.9 as-number 600
[ASBR-PE2-bgp-default] peer 5.5.5.9 connect-interface loopback 0
# Disable route target based filtering of received VPNv6 routes.
[ASBR-PE2-bgp-default] address-family vpnv6
[ASBR-PE2-bgp-default-vpnv6] undo policy vpn-target
# Configure IBGP peer 5.5.5.9 and EBGP peer 11.0.0.2 as VPNv6 peers.
[ASBR-PE2-bgp-default-vpnv6] peer 11.0.0.2 enable
[ASBR-PE2-bgp-default-vpnv6] peer 5.5.5.9 enable
[ASBR-PE2-bgp-default-vpnv6] quit
[ASBR-PE2-bgp-default] quit
4. Configure PE 2:
# Enable IS-IS on PE 2.
<PE2> system-view
[PE2] isis 1
[PE2-isis-1] network-entity 10.111.111.111.111.00
[PE2-isis-1] quit
# Configure the LSR ID, and enable MPLS and LDP.
[PE2] mpls lsr-id 5.5.5.9
[PE2] mpls ldp
[PE2-ldp] quit
# Configure interface HundredGigE 1/0/5, and enable IS-IS, MPLS, and LDP on the interface.
[PE2] interface hundredgige 1/0/5
[PE2-HundredGigE1/0/5] ip address 9.1.1.2 255.0.0.0
[PE2-HundredGigE1/0/5] isis enable 1
[PE2-HundredGigE1/0/5] mpls enable
[PE2-HundredGigE1/0/5] mpls ldp enable
[PE2-HundredGigE1/0/5] quit
# Configure interface Loopback 0, and enable IS-IS on it.
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 5.5.5.9 32
[PE2-LoopBack0] isis enable 1
[PE2-LoopBack0] quit
# Create VPN instance vpn1, and configure the RD and route target attributes.
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] route-distinguisher 12:12
[PE2-vpn-instance-vpn1] vpn-target 1:1 2:2 3:3 import-extcommunity
[PE2-vpn-instance-vpn1] vpn-target 3:3 export-extcommunity
[PE2-vpn-instance-vpn1] quit
# Bind the interface connected to CE 1 to the created VPN instance.
[PE2] interface hundredgige 1/0/1
[PE2-HundredGigE1/0/1] ip binding vpn-instance vpn1
[PE2-HundredGigE1/0/1] ip address 20::1 64
[PE2-HundredGigE1/0/1] quit
# Enable BGP on PE 2.
[PE2] bgp 600
# Configure IBGP peer 4.4.4.9 as a VPNv6 peer.
[PE2-bgp-default] peer 4.4.4.9 as-number 600
[PE2-bgp-default] peer 4.4.4.9 connect-interface loopback 0
[PE2-bgp-default] address-family vpnv6
[PE2-bgp-default-vpnv6] peer 4.4.4.9 enable
[PE2-bgp-default-vpnv6] quit
# Redistribute direct routes to the VPN routing table of vpn1.
[PE2-bgp-default] ip vpn-instance vpn1
[PE2-bgp-default-vpn1] address-family ipv6 unicast
[PE2-bgp-default-ipv6-vpn1] import-route direct
[PE2-bgp-default-ipv6-vpn1] quit
[PE2-bgp-default-vpn1] quit
[PE2-bgp-default] quit
Verifying the configuration
# Use the following command on PE 1 to verify its connectivity to PE 2.
[PE1] ping ipv6 -a 30::1 -vpn-instance vpn1 20::1
Ping6(56 data bytes) 30::1-->20::1, press CTRL_C to break
56 bytes from 20::1: icmp_seq=0 hlim=64 time=1.208 ms
56 bytes from 20::1: icmp_seq=1 hlim=64 time=0.867 ms
56 bytes from 20::1: icmp_seq=2 hlim=64 time=0.551 ms
56 bytes from 20::1: icmp_seq=3 hlim=64 time=0.566 ms
56 bytes from 20::1: icmp_seq=4 hlim=64 time=0.570 ms
--- Ping6 statistics for 20::1 in VPN instance vpn1---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.551/0.752/1.208/0.257 ms
Example: Configuring IPv6 MPLS L3VPN inter-AS option C
Network configuration
Site 1 and Site 2 belong to the same VPN. Site 1 accesses the network through PE 1 in AS 100. Site 2 accesses the network through PE 2 in AS 600. PEs in the same AS run IS-IS.
PE 1 and ASBR-PE 1 exchange labeled IPv4 routes by IBGP. PE 2 and ASBR-PE 2 exchange labeled IPv4 routes by IBGP. PE 1 and PE 2 are MP-EBGP peers to exchange VPNv6 routes.
ASBR-PE 1 and ASBR-PE 2 use their respective routing policies and label the routes received from each other.
ASBR-PE 1 and ASBR-PE 2 use EBGP to exchange labeled IPv4 routes.
Figure 7 Network diagram
Table 5 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
PE 1 |
Loop0 |
2.2.2.9/32 |
PE 2 |
Loop0 |
5.5.5.9/32 |
|
|
HGE1/0/1 |
2001::1/64 |
|
HGE1/0/1 |
2002::1/64 |
|
|
HGE1/0/5 |
1.1.1.2/8 |
|
HGE1/0/5 |
9.1.1.2/8 |
|
ASBR-PE 1 |
Loop0 |
3.3.3.9/32 |
ASBR-PE 2 |
Loop0 |
4.4.4.9/32 |
|
|
HGE1/0/5 |
1.1.1.1/8 |
|
HGE1/0/5 |
9.1.1.1/8 |
|
|
HGE1/0/4 |
11.0.0.2/8 |
|
HGE1/0/4 |
11.0.0.1/8 |
|
CE 1 |
HGE1/0/1 |
2001::2/64 |
CE 1 |
HGE1/0/1 |
2002::2/64 |
Prerequisite
By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface.
Procedure
1. Configure CE 1:
# Configure an IPv6 address for HundredGigE 1/0/1.
<CE1> system-view
[CE1] interface hundredgige 1/0/1
[CE1-HundredGigE1/0/1] ipv6 address 2001::2 64
[CE1-HundredGigE1/0/1] quit
# Establish an EBGP peer relationship with PE 1, and redistribute VPN routes.
[CE1] bgp 65001
[CE1-bgp-default] peer 2001::1 as-number 100
[CE1-bgp-default] address-family ipv6 unicast
[CE1-bgp-default-ipv6] peer 2001::1 enable
[CE1-bgp-default-ipv6] import-route direct
[CE1-bgp-default-ipv6] quit
[CE1-bgp-default] quit
2. Configure PE 1:
# Configure IS-IS on PE 1.
<PE1> system-view
[PE1] isis 1
[PE1-isis-1] network-entity 10.111.111.111.111.00
[PE1-isis-1] quit
# Configure an LSR ID, and enable MPLS and LDP.
[PE1] mpls lsr-id 2.2.2.9
[PE1] mpls ldp
[PE1-ldp] quit
# Configure HundredGigE 1/0/5, and enable IS-IS, MPLS, and LDP on the interface.
[PE1] interface hundredgige 1/0/5
[PE1-HundredGigE1/0/5] ip address 1.1.1.2 255.0.0.0
[PE1-HundredGigE1/0/5] isis enable 1
[PE1-HundredGigE1/0/5] mpls enable
[PE1-HundredGigE1/0/5] mpls ldp enable
[PE1-HundredGigE1/0/5] quit
# Configure Loopback 0 and start IS-IS on it.
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 2.2.2.9 32
[PE1-LoopBack0] isis enable 1
[PE1-LoopBack0] quit
# Create VPN instance vpn1, and configure the RD and route target attributes for it.
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 11:11
[PE1-vpn-instance-vpn1] vpn-target 3:3 import-extcommunity
[PE1-vpn-instance-vpn1] vpn-target 3:3 export-extcommunity
[PE1-vpn-instance-vpn1] quit
# Associate HundredGigE 1/0/1 with VPN instance vpn1, and specify the IPv6 address for the interface.
[PE1] interface hundredgige 1/0/1
[PE1-HundredGigE1/0/1] ip binding vpn-instance vpn1
[PE1-HundredGigE1/0/1] ipv6 address 2001::1 64
[PE1-HundredGigE1/0/1] quit
# Start BGP on PE 1.
[PE1] bgp 100
# Enable the capability to advertise labeled routes to and receive labeled routes from IBGP peer 3.3.3.9.
[PE1-bgp-default] peer 3.3.3.9 as-number 100
[PE1-bgp-default] peer 3.3.3.9 connect-interface loopback 0
[PE1-bgp-default] address-family ipv4 unicast
[PE1-bgp-default-ipv4] peer 3.3.3.9 enable
[PE1-bgp-default-ipv4] peer 3.3.3.9 label-route-capability
[PE1-bgp-default-ipv4] quit
# Configure the maximum hop count from PE 1 to EBGP peer 5.5.5.9 as 10.
[PE1-bgp-default] peer 5.5.5.9 as-number 600
[PE1-bgp-default] peer 5.5.5.9 connect-interface loopback 0
[PE1-bgp-default] peer 5.5.5.9 ebgp-max-hop 10
# Configure peer 5.5.5.9 as a VPNv6 peer.
[PE1-bgp-default] address-family vpnv6
[PE1-bgp-default-af-vpnv6] peer 5.5.5.9 enable
[PE1-bgp-default-af-vpnv6] quit
# Establish an EBGP peer relationship with CE 1, and add the learned BGP routes to the routing table of VPN instance vpn1.
[PE1-bgp-default] ip vpn-instance vpn1
[PE1-bgp-default-vpn1] peer 2001::2 as-number 65001
[PE1-bgp-default-vpn1] address-family ipv6 unicast
[PE1-bgp-default-ipv6-vpn1] peer 2001::2 enable
[PE1-bgp-default-ipv6-vpn1] quit
[PE1-bgp-default-vpn1] quit
[PE1-bgp-default] quit
3. Configure ASBR-PE 1:
# Start IS-IS on ASBR-PE 1.
<ASBR-PE1> system-view
[ASBR-PE1] isis 1
[ASBR-PE1-isis-1] network-entity 10.222.222.222.222.00
[ASBR-PE1-isis-1] quit
# Configure an LSR ID, and enable MPLS and LDP.
[ASBR-PE1] mpls lsr-id 3.3.3.9
[ASBR-PE1] mpls ldp
[ASBR-PE1-ldp] quit
# Configure HundredGigE 1/0/5, and enable IS-IS, MPLS, and LDP on the interface.
[ASBR-PE1] interface hundredgige 1/0/5
[ASBR-PE1-HundredGigE1/0/5] ip address 1.1.1.1 255.0.0.0
[ASBR-PE1-HundredGigE1/0/5] isis enable 1
[ASBR-PE1-HundredGigE1/0/5] mpls enable
[ASBR-PE1-HundredGigE1/0/5] mpls ldp enable
[ASBR-PE1-HundredGigE1/0/5] quit
# Configure HundredGigE 1/0/4, and enable MPLS on it.
[ASBR-PE1] interface hundredgige 1/0/4
[ASBR-PE1-HundredGigE1/0/4] ip address 11.0.0.2 255.0.0.0
[ASBR-PE1-HundredGigE1/0/4] mpls enable
[ASBR-PE1-HundredGigE1/0/4] quit
# Configure Loopback 0, and start IS-IS on it.
[ASBR-PE1] interface loopback 0
[ASBR-PE1-LoopBack0] ip address 3.3.3.9 32
[ASBR-PE1-LoopBack0] isis enable 1
[ASBR-PE1-LoopBack0] quit
# Create routing policies.
[ASBR-PE1] route-policy policy1 permit node 1
[ASBR-PE1-route-policy-policy1-1] apply mpls-label
[ASBR-PE1-route-policy-policy1-1] quit
[ASBR-PE1] route-policy policy2 permit node 1
[ASBR-PE1-route-policy-policy2-1] if-match mpls-label
[ASBR-PE1-route-policy-policy2-1] apply mpls-label
[ASBR-PE1-route-policy-policy2-1] quit
# Start BGP on ASBR-PE 1, and apply routing policy policy2 to routes advertised to IBGP peer 2.2.2.9.
[ASBR-PE1] bgp 100
[ASBR-PE1-bgp-default] peer 2.2.2.9 as-number 100
[ASBR-PE1-bgp-default] peer 2.2.2.9 connect-interface loopback 0
[ASBR-PE1-bgp-default] address-family ipv4 unicast
[ASBR-PE1-bgp-default-ipv4] peer 2.2.2.9 enable
[ASBR-PE1-bgp-default-ipv4] peer 2.2.2.9 route-policy policy2 export
# Enable the capability to advertise labeled routes to and receive labeled routes from IBGP peer 2.2.2.9.
[ASBR-PE1-bgp-default-ipv4] peer 2.2.2.9 label-route-capability
# Redistribute routes from IS-IS process 1
[ASBR-PE1-bgp-default-ipv4] import-route isis 1
[ASBR-PE1-bgp-default-ipv4] quit
# Apply routing policy policy1 to routes advertised to EBGP peer 11.0.0.1.
[ASBR-PE1-bgp-default] peer 11.0.0.1 as-number 600
[ASBR-PE1-bgp-default] address-family ipv4 unicast
[ASBR-PE1-bgp-default-ipv4] peer 11.0.0.1 enable
[ASBR-PE1-bgp-default-ipv4] peer 11.0.0.1 route-policy policy1 export
# Enable the capability to advertise labeled routes to and receive labeled routes from EBGP peer 11.0.0.1.
[ASBR-PE1-bgp-default-ipv4] peer 11.0.0.1 label-route-capability
[ASBR-PE1-bgp-default-ipv4] quit
[ASBR-PE1-bgp-default] quit
4. Configure ASBR-PE 2:
# Start IS-IS on ASBR-PE 2.
<ASBR-PE2> system-view
[ASBR-PE2] isis 1
[ASBR-PE2-isis-1] network-entity 10.333.333.333.333.00
[ASBR-PE2-isis-1] quit
# Configure an LSR ID, and enable MPLS and LDP.
[ASBR-PE2] mpls lsr-id 4.4.4.9
[ASBR-PE2] mpls ldp
[ASBR-PE2-ldp] quit
# Configure HundredGigE 1/0/5, and enable IS-IS, MPLS, and LDP on the interface.
[ASBR-PE2] interface hundredgige 1/0/5
[ASBR-PE2-HundredGigE1/0/5] ip address 9.1.1.1 255.0.0.0
[ASBR-PE2-HundredGigE1/0/5] isis enable 1
[ASBR-PE2-HundredGigE1/0/5] mpls enable
[ASBR-PE2-HundredGigE1/0/5] mpls ldp enable
[ASBR-PE2-HundredGigE1/0/5] quit
# Configure Loopback 0, and start IS-IS on it.
[ASBR-PE2] interface loopback 0
[ASBR-PE2-LoopBack0] ip address 4.4.4.9 32
[ASBR-PE2-LoopBack0] isis enable 1
[ASBR-PE2-LoopBack0] quit
# Configure HundredGigE 1/0/4, and enable MPLS on it.
[ASBR-PE2] interface hundredgige 1/0/4
[ASBR-PE2-HundredGigE1/0/4] ip address 11.0.0.1 255.0.0.0
[ASBR-PE2-HundredGigE1/0/4] mpls enable
[ASBR-PE2-HundredGigE1/0/4] quit
# Create routing policies.
[ASBR-PE2] route-policy policy1 permit node 1
[ASBR-PE2-route-policy-policy1-1] apply mpls-label
[ASBR-PE2-route-policy-policy1-1] quit
[ASBR-PE2] route-policy policy2 permit node 1
[ASBR-PE2-route-policy-policy2-1] if-match mpls-label
[ASBR-PE2-route-policy-policy2-1] apply mpls-label
[ASBR-PE2-route-policy-policy2-1] quit
# Start BGP on ASBR-PE 2, and enable the capability to advertise labeled routes to and receive labeled routes from IBGP peer 5.5.5.9.
[ASBR-PE2] bgp 600
[ASBR-PE2-bgp-default] peer 5.5.5.9 as-number 600
[ASBR-PE2-bgp-default] peer 5.5.5.9 connect-interface loopback 0
[ASBR-PE2-bgp-default] address-family ipv4 unicast
[ASBR-PE2-bgp-default-ipv4] peer 5.5.5.9 enable
[ASBR-PE2-bgp-default-ipv4] peer 5.5.5.9 label-route-capability
# Apply routing policy policy2 to routes advertised to IBGP peer 5.5.5.9.
[ASBR-PE2-bgp-default-ipv4] peer 5.5.5.9 route-policy policy2 export
# Redistribute routes from IS-IS process 1.
[ASBR-PE2-bgp-default-ipv4] import-route isis 1
[ASBR-PE2-bgp-default-ipv4] quit
# Apply routing policy policy1 to routes advertised to EBGP peer 11.0.0.2.
[ASBR-PE2-bgp-default] peer 11.0.0.2 as-number 100
[ASBR-PE2-bgp-default] address-family ipv4 unicast
[ASBR-PE2-bgp-default-ipv4] peer 11.0.0.2 enable
[ASBR-PE2-bgp-default-ipv4] peer 11.0.0.2 route-policy policy1 export
# Enable the capability to advertise labeled routes to and receive labeled routes from EBGP peer 11.0.0.2.
[ASBR-PE2-bgp-default-ipv4] peer 11.0.0.2 label-route-capability
[ASBR-PE2-bgp-default-ipv4] quit
[ASBR-PE2-bgp-default] quit
5. Configure PE 2:
# Start IS-IS on PE 2.
<PE2> system-view
[PE2] isis 1
[PE2-isis-1] network-entity 10.444.444.444.444.00
[PE2-isis-1] quit
# Configure an LSR ID, and enable MPLS and LDP.
[PE2] mpls lsr-id 5.5.5.9
[PE2] mpls ldp
[PE2-ldp] quit
# Configure HundredGigE 1/0/5, and enable IS-IS, MPLS, and LDP on the interface.
[PE2] interface hundredgige 1/0/5
[PE2-HundredGigE1/0/5] ip address 9.1.1.2 255.0.0.0
[PE2-HundredGigE1/0/5] isis enable 1
[PE2-HundredGigE1/0/5] mpls enable
[PE2-HundredGigE1/0/5] mpls ldp enable
[PE2-HundredGigE1/0/5] quit
# Configure Loopback 0, and start IS-IS on it.
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 5.5.5.9 32
[PE2-LoopBack0] isis enable 1
[PE2-LoopBack0] quit
# Create VPN instance vpn1, and configure the RD and route target attributes for it.
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] route-distinguisher 11:11
[PE2-vpn-instance-vpn1] vpn-target 3:3 import-extcommunity
[PE2-vpn-instance-vpn1] vpn-target 3:3 export-extcommunity
[PE2-vpn-instance-vpn1] quit
# Associate HundredGigE 1/0/1 with VPN instance vpn1, and specify the IPv6 address for the interface.
[PE2] interface hundredgige 1/0/1
[PE2-HundredGigE1/0/1] ip binding vpn-instance vpn1
[PE2-HundredGigE1/0/1] ipv6 address 2002::1 64
[PE2-HundredGigE1/0/1] quit
# Start BGP.
[PE2] bgp 600
# Enable the capability to advertise labeled routes to and receive labeled routes from IBGP peer 4.4.4.9.
[PE2-bgp-default] peer 4.4.4.9 as-number 600
[PE2-bgp-default] peer 4.4.4.9 connect-interface loopback 0
[PE2-bgp-default] address-family ipv4 unicast
[PE2-bgp-default-ipv4] peer 4.4.4.9 enable
[PE2-bgp-default-ipv4] peer 4.4.4.9 label-route-capability
[PE2-bgp-default-ipv4] quit
# Configure the maximum hop count from PE 2 to EBGP peer 2.2.2.9 as 10.
[PE2-bgp-default] peer 2.2.2.9 as-number 100
[PE2-bgp-default] peer 2.2.2.9 connect-interface loopback 0
[PE2-bgp-default] peer 2.2.2.9 ebgp-max-hop 10
# Configure peer 2.2.2.9 as a VPNv6 peer.
[PE2-bgp-default] address-family vpnv6
[PE2-bgp-default-af-vpnv6] peer 2.2.2.9 enable
[PE2-bgp-default-af-vpnv6] quit
# Establish an EBGP peer relationship with CE 2, and add the learned BGP routes to the routing table of VPN instance vpn1.
[PE2-bgp-default] ip vpn-instance vpn1
[PE2-bgp-default-vpn1] peer 2002::2 as-number 65002
[PE2-bgp-default-vpn1] address-family ipv6 unicast
[PE2-bgp-default-ipv6-vpn1] peer 2002::2 enable
[PE2-bgp-default-ipv6-vpn1] quit
[PE2-bgp-default-vpn1] quit
[PE2-bgp-default] quit
6. Configure CE 2:
# Configure an IPv6 address for HundredGigE 1/0/1.
<CE2> system-view
[CE2] interface hundredgige 1/0/1
[CE2-HundredGigE1/0/1] ipv6 address 2002::2 64
[CE2-HundredGigE1/0/1] quit
# Establish an EBGP peer relationship with PE 2, and redistribute VPN routes.
[CE2] bgp 65002
[CE2-bgp-default] peer 2002::1 as-number 600
[CE2-bgp-default] address-family ipv6 unicast
[CE2-bgp-default-ipv6] peer 2002::1 enable
[CE2-bgp-default-ipv6] import-route direct
[CE2-bgp-default-ipv6] quit
[CE2-bgp-default] quit
Verifying the configuration
# Execute the display ipv6 routing table command on CE 1 and CE 2 to verify that CE 1 and CE 2 have a route to each other. Verify that CE 1 and CE 2 can ping each other. (Details not shown.)
Example: Configuring IPv6 MPLS L3VPN carrier's carrier in the same AS
Network configuration
Configure carrier's carrier for the scenario shown in Figure 8. In this scenario:
· PE 1 and PE 2 are the provider carrier's PE routers. They provide VPN services to the customer carrier.
· CE 1 and CE 2 are the customer carrier's routers. They are connected to the provider carrier's backbone as CE routers.
· PE 3 and PE 4 are the customer carrier's PE routers. They provide IPv6 MPLS L3VPN services to end customers.
· CE 3 and CE 4 are customers of the customer carrier.
· The customer carrier and the provider carrier reside in the same AS.
The key to the carrier's carrier deployment is to configure exchange of two kinds of routes:
· Exchange of the customer carrier's internal routes on the provider carrier's backbone.
· Exchange of the end customers' internal routes between PE 3 and PE 4, the PEs of the customer carrier. In this process, an MP-IBGP peer relationship must be established between PE 3 and PE 4.
Table 6 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 3 |
HGE1/0/1 |
2001:1::1/96 |
CE 4 |
HGE1/0/1 |
2001:2::1/96 |
|
PE 3 |
Loop0 |
1.1.1.9/32 |
PE 4 |
Loop0 |
6.6.6.9/32 |
|
|
HGE1/0/1 |
2001:1::2/96 |
|
HGE1/0/1 |
2001:2::2/96 |
|
|
HGE1/0/5 |
10.1.1.1/24 |
|
HGE1/0/5 |
20.1.1.2/24 |
|
CE 1 |
Loop0 |
2.2.2.9/32 |
CE 2 |
Loop0 |
5.5.5.9/32 |
|
|
HGE1/0/4 |
10.1.1.2/24 |
|
HGE1/0/4 |
21.1.1.2/24 |
|
|
HGE1/0/5 |
11.1.1.1/24 |
|
HGE1/0/5 |
20.1.1.1/24 |
|
PE 1 |
Loop0 |
3.3.3.9/32 |
PE 2 |
Loop0 |
4.4.4.9/32 |
|
|
HGE1/0/4 |
11.1.1.2/24 |
|
HGE1/0/4 |
30.1.1.2/24 |
|
|
HGE1/0/5 |
30.1.1.1/24 |
|
HGE1/0/5 |
21.1.1.1/24 |
Prerequisite
By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface.
Procedure
1. Configure MPLS L3VPN on the provider carrier backbone. Start IS-IS as the IGP, enable LDP on PE 1 and PE 2, and establish an MP-IBGP peer relationship between the PEs:
# Configure PE 1.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 3.3.3.9 32
[PE1-LoopBack0] quit
[PE1] mpls lsr-id 3.3.3.9
[PE1] mpls ldp
[PE1-ldp] quit
[PE1] isis 1
[PE1-isis-1] network-entity 10.0000.0000.0000.0004.00
[PE1-isis-1] quit
[PE1] interface loopback 0
[PE1-LoopBack0] isis enable 1
[PE1-LoopBack0] quit
[PE1] interface hundredgige 1/0/5
[PE1-HundredGigE1/0/5] ip address 30.1.1.1 24
[PE1-HundredGigE1/0/5] isis enable 1
[PE1-HundredGigE1/0/5] mpls enable
[PE1-HundredGigE1/0/5] mpls ldp enable
[PE1-HundredGigE1/0/5] mpls ldp transport-address interface
[PE1-HundredGigE1/0/5] quit
[PE1] bgp 100
[PE1-bgp-default] peer 4.4.4.9 as-number 100
[PE1-bgp-default] peer 4.4.4.9 connect-interface loopback 0
[PE1-bgp-default] address-family vpnv4
[PE1-bgp-default-vpnv4] peer 4.4.4.9 enable
[PE1-bgp-default-vpnv4] quit
[PE1-bgp-default] quit
# Configure PE 2 in the same way that PE 1 is configured. (Details not shown.)
# On PE 1 or PE 2, execute the following commands:
¡ Execute the display mpls ldp peer command to verify that an LDP session in Operational state has been established between PE 1 and PE 2. (Details not shown.)
¡ Execute the display bgp peer vpnv4 command to verify that a BGP peer relationship in Established state has been established between PE 1 and PE 2. (Details not shown.)
¡ Execute the display isis peer command to verify that the IS-IS neighbor relationship has been established between PE 1 and PE 2. (Details not shown.)
2. Configure the customer carrier network. Start IS-IS as the IGP, and enable LDP between PE 3 and CE 1, and between PE 4 and CE 2:
# Configure PE 3.
<PE3> system-view
[PE3] interface loopback 0
[PE3-LoopBack0] ip address 1.1.1.9 32
[PE3-LoopBack0] quit
[PE3] mpls lsr-id 1.1.1.9
[PE3] mpls ldp
[PE3-ldp] quit
[PE3] isis 2
[PE3-isis-2] network-entity 10.0000.0000.0000.0001.00
[PE3-isis-2] quit
[PE3] interface loopback 0
[PE3-LoopBack0] isis enable 2
[PE3-LoopBack0] quit
[PE3] interface hundredgige 1/0/5
[PE3-HundredGigE1/0/5] ip address 10.1.1.1 24
[PE3-HundredGigE1/0/5] isis enable 2
[PE3-HundredGigE1/0/5] mpls enable
[PE3-HundredGigE1/0/5] mpls ldp enable
[PE3-HundredGigE1/0/5] mpls ldp transport-address interface
[PE3-HundredGigE1/0/5] quit
# Configure CE 1.
<CE1> system-view
[CE1] interface loopback 0
[CE1-LoopBack0] ip address 2.2.2.9 32
[CE1-LoopBack0] quit
[CE1] mpls lsr-id 2.2.2.9
[CE1] mpls ldp
[CE1-ldp] quit
[CE1] isis 2
[CE1-isis-2] network-entity 10.0000.0000.0000.0002.00
[CE1-isis-2] quit
[CE1] interface loopback 0
[CE1-LoopBack0] isis enable 2
[CE1-LoopBack0] quit
[CE1] interface hundredgige 1/0/4
[CE1-HundredGigE1/0/4] ip address 10.1.1.2 24
[CE1-HundredGigE1/0/4] isis enable 2
[CE1-HundredGigE1/0/4] mpls enable
[CE1-HundredGigE1/0/4] mpls ldp enable
[CE1-HundredGigE1/0/4] mpls ldp transport-address interface
[CE1-HundredGigE1/0/4] quit
PE 3 and CE 1 can establish an LDP session and IS-IS neighbor relationship between them.
# Configure PE 4 and CE 2 in the same way that PE 3 and CE 1 are configured. (Details not shown.)
3. Connect the customer carrier and the provider carrier:
# Configure PE 1.
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 200:1
[PE1-vpn-instance-vpn1] vpn-target 1:1
[PE1-vpn-instance-vpn1] quit
[PE1] mpls ldp
[PE1-ldp] vpn-instance vpn1
[PE1-ldp-vpn-instance-vpn1] quit
[PE1-ldp] quit
[PE1] isis 2 vpn-instance vpn1
[PE1-isis-2] network-entity 10.0000.0000.0000.0003.00
[PE1-isis-2] address-family ipv4
[PE1-isis-2-ipv4] import-route bgp allow-ibgp
[PE1-isis-2-ipv4] quit
[PE1-isis-2] quit
[PE1] interface hundredgige 1/0/4
[PE1-HundredGigE1/0/4] ip binding vpn-instance vpn1
[PE1-HundredGigE1/0/4] ip address 11.1.1.2 24
[PE1-HundredGigE1/0/4] isis enable 2
[PE1-HundredGigE1/0/4] mpls enable
[PE1-HundredGigE1/0/4] mpls ldp enable
[PE1-HundredGigE1/0/4] mpls ldp transport-address interface
[PE1-HundredGigE1/0/4] quit
[PE1] bgp 100
[PE1-bgp-default] ip vpn-instance vpn1
[PE1-bgp-default-vpn1] address-family ipv4 unicast
[PE1-bgp-default-ipv4-vpn1] import isis 2
[PE1-bgp-default-ipv4-vpn1] quit
[PE1-bgp-default-vpn1] quit
[PE1-bgp-default] quit
# Configure CE 1.
[CE1] interface hundredgige 1/0/5
[CE1-HundredGigE1/0/5] ip address 11.1.1.1 24
[CE1-HundredGigE1/0/5] isis enable 2
[CE1-HundredGigE1/0/5] mpls enable
[CE1-HundredGigE1/0/5] mpls ldp enable
[CE1-HundredGigE1/0/5] mpls ldp transport-address interface
[CE1-HundredGigE1/0/5] quit
PE 1 and CE 1 can establish an LDP session and IS-IS neighbor relationship between them.
# Configure PE 2 and CE 2 in the same way that PE 1 and CE 1 are configured. (Details not shown.)
4. Connect end customers and the customer carrier:
# Configure CE 3.
<CE3> system-view
[CE3] interface hundredgige 1/0/1
[CE3-HundredGigE1/0/1] ipv6 address 2001:1::1 96
[CE3-HundredGigE1/0/1] quit
[CE3] bgp 65410
[CE3-bgp-default] peer 2001:1::2 as-number 100
[CE3-bgp-default] address-family ipv6
[CE3-bgp-default-ipv6] peer 2001:1::2 enable
[CE3-bgp-default-ipv6] import-route direct
[CE3-bgp-default-ipv6] quit
[CE3-bgp-default] quit
# Configure PE 3.
[PE3] ip vpn-instance vpn1
[PE3-vpn-instance-vpn1] route-distinguisher 100:1
[PE3-vpn-instance-vpn1] vpn-target 1:1
[PE3-vpn-instance-vpn1] quit
[PE3] interface hundredgige 1/0/1
[PE3-HundredGigE1/0/1] ip binding vpn-instance vpn1
[PE3-HundredGigE1/0/1] ipv6 address 2001:1::2 96
[PE3-HundredGigE1/0/1] quit
[PE3] bgp 100
[PE3-bgp-default] ip vpn-instance vpn1
[PE3-bgp-default-vpn1] peer 2001:1::1 as-number 65410
[PE3-bgp-default-vpn1] address-family ipv6 unicast
[PE3-bgp-default-ipv6-vpn1] peer 2001:1::1 enable
[PE3-bgp-default-ipv6-vpn1] quit
[PE3-bgp-default-vpn1] quit
[PE3-bgp-default] quit
# Configure PE 4 and CE 4 in the same way that PE 3 and CE 3 are configured. (Details not shown.)
5. Configure an MP-IBGP peer relationship between the PEs of the customer carrier to exchange the VPN routes of the end customers:
# Configure PE 3.
[PE3] bgp 100
[PE3-bgp-default] peer 6.6.6.9 as-number 100
[PE3-bgp-default] peer 6.6.6.9 connect-interface loopback 0
[PE3-bgp-default] address-family vpnv6
[PE3-bgp-default-af-vpnv6] peer 6.6.6.9 enable
[PE3-bgp-default-af-vpnv6] quit
[PE3-bgp-default] quit
# Configure PE 4 in the same way that PE 3 is configured. (Details not shown.)
Verifying the configuration
1. Display the public network routing table and VPN routing table on the provider carrier PEs, for example, on PE 1:
# Verify that the public network routing table contains only routes of the provider carrier network.
[PE1] display ip routing-table
Destinations : 14 Routes : 14
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
3.3.3.9/32 Direct 0 0 127.0.0.1 InLoop0
4.4.4.9/32 IS_L1 15 10 30.1.1.2 HGE1/0/5
30.1.1.0/24 Direct 0 0 30.1.1.1 HGE1/0/5
30.1.1.0/32 Direct 0 0 30.1.1.1 HGE1/0/5
30.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
30.1.1.255/32 Direct 0 0 30.1.1.1 HGE1/0/5
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Verify that the VPN routing table contains the internal routes of the customer carrier network.
[PE1] display ip routing-table vpn-instance vpn1
Destinations : 18 Routes : 18
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
1.1.1.9/32 IS_L1 15 20 11.1.1.1 HGE1/0/4
2.2.2.9/32 IS_L1 15 10 11.1.1.1 HGE1/0/4
5.5.5.9/32 BGP 255 10 4.4.4.9 HGE1/0/5
6.6.6.9/32 BGP 255 20 4.4.4.9 HGE1/0/5
10.1.1.0/24 IS_L1 15 20 11.1.1.1 HGE1/0/4
11.1.1.0/24 Direct 0 0 11.1.1.2 HGE1/0/4
11.1.1.0/32 Direct 0 0 11.1.1.2 HGE1/0/4
11.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
11.1.1.255/32 Direct 0 0 11.1.1.2 HGE1/0/4
20.1.1.0/24 BGP 255 20 4.4.4.9 HGE1/0/5
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
2. Display the routing table on the customer carrier CEs, for example, on CE 1:
# Verify that the routing table contains the internal routes of the customer carrier network.
[CE1] display ip routing-table
Destinations : 21 Routes : 21
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
1.1.1.9/32 IS_L1 15 10 10.1.1.1 HGE1/0/4
2.2.2.9/32 Direct 0 0 127.0.0.1 InLoop0
5.5.5.9/32 IS_L2 15 74 11.1.1.2 HGE1/0/5
6.6.6.9/32 IS_L2 15 74 11.1.1.2 HGE1/0/5
10.1.1.0/24 Direct 0 0 10.1.1.2 HGE1/0/4
10.1.1.0/32 Direct 0 0 10.1.1.2 HGE1/0/4
10.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.255/32 Direct 0 0 10.1.1.2 HGE1/0/4
11.1.1.0/24 Direct 0 0 11.1.1.1 HGE1/0/5
11.1.1.0/32 Direct 0 0 11.1.1.1 HGE1/0/5
11.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
11.1.1.255/32 Direct 0 0 11.1.1.1 HGE1/0/5
20.1.1.0/24 IS_L2 15 74 11.1.1.2 HGE1/0/5
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
3. Display the public network routing table and VPN routing table on the customer carrier PEs, for example, on PE 3:
# Verify that the public network routing table contains the internal routes of the customer carrier network.
[PE3] display ip routing-table
Destinations : 18 Routes : 18
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
1.1.1.9/32 Direct 0 0 127.0.0.1 InLoop0
2.2.2.9/32 IS_L1 15 10 10.1.1.2 HGE1/0/5
5.5.5.9/32 IS_L2 15 84 10.1.1.2 HGE1/0/5
6.6.6.9/32 IS_L2 15 84 10.1.1.2 HGE1/0/5
10.1.1.0/24 Direct 0 0 10.1.1.1 HGE1/0/5
10.1.1.0/32 Direct 0 0 10.1.1.1 HGE1/0/5
10.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.255/32 Direct 0 0 10.1.1.1 HGE1/0/5
11.1.1.0/24 IS_L1 15 20 10.1.1.2 HGE1/0/5
20.1.1.0/24 IS_L2 15 84 10.1.1.2 HGE1/0/5
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Verify that the VPN routing table has the remote VPN route.
[PE3] display ipv6 routing-table vpn-instance vpn1
Destinations : 6 Routes : 6
Destination: ::1/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 2001:1::/96 Protocol : Direct
NextHop : :: Preference: 0
Interface : HGE1/0/1 Cost : 0
Destination: 2001:1::2/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 2001:2::/96 Protocol : BGP4+
NextHop : ::FFFF:6.6.6.9 Preference: 255
Interface : HGE1/0/5 Cost : 0
Destination: FE80::/10 Protocol : Direct
NextHop : :: Preference: 0
Interface : InLoop0 Cost : 0
Destination: FF00::/8 Protocol : Direct
NextHop : :: Preference: 0
Interface : NULL0 Cost : 0
4. Verify that PE 3 and PE 4 can ping each other. (Details not shown.)
5. Verify that CE 3 and CE 4 can ping each other. (Details not shown.)
Example: Configuring an OSPFv3 sham link
Network configuration
As shown in Figure 9, CE 1 and CE 2 belong to VPN 1. Configure an OSPFv3 sham link between PE 1 and PE 2 so traffic between the CEs is forwarded through the MPLS backbone instead of the backdoor link.
Table 7 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
HGE1/0/1 |
100::1/64 |
CE 2 |
HGE1/0/1 |
120::1/64 |
|
|
HGE1/0/4 |
20::1/64 |
|
HGE1/0/4 |
30::2/64 |
|
PE 1 |
Loop0 |
1.1.1.9/32 |
PE 2 |
Loop0 |
2.2.2.9/32 |
|
|
Loop1 |
3::3/128 |
|
Loop1 |
5::5/128 |
|
|
HGE1/0/1 |
100::2/64 |
|
HGE1/0/1 |
120::2/64 |
|
|
HGE1/0/4 |
10.1.1.1/24 |
|
HGE1/0/5 |
10.1.1.2/24 |
|
Router A |
HGE1/0/5 |
30::1/64 |
|
|
|
|
|
HGE1/0/4 |
20::2/64 |
|
|
|
Prerequisite
By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface.
Procedure
1. Configure OSPFv3 on the customer networks:
# Configure conventional OSPFv3 on CE 1, Router A, and CE 2 to advertise addresses of the interfaces (see Figure 9). (Details not shown.)
# Set the cost value to 2 for both the link between CE 1 and Router A, and the link between CE 2 and Router A. (Details not shown.)
# Execute the display ipv6 routing-table command to verify that CE 1 and CE 2 have learned the route to each other. (Details not shown.)
2. Configure IPv6 MPLS L3VPN on the backbone:
# Configure basic MPLS and MPLS LDP on PE 1 to establish LDP LSPs.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 1.1.1.9 32
[PE1-LoopBack0] quit
[PE1] mpls lsr-id 1.1.1.9
[PE1] mpls ldp
[PE1-ldp] quit
[PE1] interface hundredgige 1/0/4
[PE1-HundredGigE1/0/4] ip address 10.1.1.1 24
[PE1-HundredGigE1/0/4] mpls enable
[PE1-HundredGigE1/0/4] mpls ldp enable
[PE1-HundredGigE1/0/4] quit
# Configure PE 1 to take PE 2 as an MP-IBGP peer.
[PE1] bgp 100
[PE1-bgp-default] peer 2.2.2.9 as-number 100
[PE1-bgp-default] peer 2.2.2.9 connect-interface loopback 0
[PE1-bgp-default] address-family vpnv6
[PE1-bgp-default-vpnv6] peer 2.2.2.9 enable
[PE1-bgp-default-vpnv6] quit
[PE1-bgp-default] quit
# Configure OSPF on PE 1.
[PE1] ospf 1
[PE1-ospf-1] area 0
[PE1-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0
[PE1-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[PE1-ospf-1-area-0.0.0.0] quit
[PE1-ospf-1] quit
# Configure basic MPLS and MPLS LDP on PE 2 to establish LDP LSPs.
<PE2> system-view
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 2.2.2.9 32
[PE2-LoopBack0] quit
[PE2] mpls lsr-id 2.2.2.9
[PE2] mpls ldp
[PE2-ldp] quit
[PE2] interface hundredgige 1/0/4
[PE2-HundredGigE1/0/4] ip address 10.1.1.2 24
[PE2-HundredGigE1/0/4] mpls enable
[PE2-HundredGigE1/0/4] mpls ldp enable
[PE2-HundredGigE1/0/4] quit
# Configure PE 2 to take PE 1 as an MP-IBGP peer.
[PE2] bgp 100
[PE2-bgp-default] peer 1.1.1.9 as-number 100
[PE2-bgp-default] peer 1.1.1.9 connect-interface loopback 0
[PE2-bgp-default] address-family vpnv6
[PE2-bgp-default-vpnv6] peer 1.1.1.9 enable
[PE2-bgp-default-vpnv6] quit
[PE2-bgp-default] quit
# Configure OSPF on PE 2.
[PE2] ospf 1
[PE2-ospf-1] area 0
[PE2-ospf-1-area-0.0.0.0] network 2.2.2.9 0.0.0.0
[PE2-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[PE2-ospf-1-area-0.0.0.0] quit
[PE2-ospf-1] quit
3. Configure PEs to allow CE access:
# Configure PE 1.
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 100:1
[PE1-vpn-instance-vpn1] vpn-target 1:1
[PE1-vpn-instance-vpn1] quit
[PE1] interface hundredgige 1/0/1
[PE1-HundredGigE1/0/1] ip binding vpn-instance vpn1
[PE1-HundredGigE1/0/1] ipv6 address 100::2 64
[PE1-HundredGigE1/0/1] ospfv3 100 area 1
[PE1-HundredGigE1/0/1] quit
[PE1] ospfv3 100
[PE1-ospfv3-100] router-id 100.1.1.1
[PE1-ospfv3-100] domain-id 10
[PE1-ospfv3-100] quit
[PE1] bgp 100
[PE1-bgp-default] ip vpn-instance vpn1
[PE1-bgp-default-vpn1] address-family ipv6 unicast
[PE1-bgp-default-ipv6-vpn1] import-route ospfv3 100
[PE1-bgp-default-ipv6-vpn1] import-route direct
[PE1-bgp-default-ipv6-vpn1] quit
[PE1-bgp-default-vpn1] quit
[PE1-bgp-default] quit
# Configure PE 2.
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] route-distinguisher 100:2
[PE2-vpn-instance-vpn1] vpn-target 1:1
[PE2-vpn-instance-vpn1] quit
[PE2] interface hundredgige 1/0/1
[PE2-HundredGigE1/0/1] ip binding vpn-instance vpn1
[PE2-HundredGigE1/0/1] ipv6 address 120::2 64
[PE2-HundredGigE1/0/1] ospfv3 100 area 1
[PE2-HundredGigE1/0/1] quit
[PE2] ospfv3 100
[PE2-ospfv3-100] router-id 120.1.1.1
[PE2-ospfv3-100] domain-id 10
[PE2-ospfv3-100] quit
[PE2] bgp 100
[PE2-bgp-default] ip vpn-instance vpn1
[PE2-bgp-default-vpn1] address-family ipv6 unicast
[PE2-bgp-default-ipv6-vpn1] import-route ospfv3 100
[PE2-bgp-default-ipv6-vpn1] import-route direct
[PE2-bgp-default-ipv6-vpn1] quit
[PE2-bgp-default-vpn1] quit
[PE2-bgp-default] quit
# Execute the display ipv6 routing-table vpn-instance command on the PEs. Verify that the path to the peer CE is along the OSPFv3 route across the customer networks, instead of the IPv6 BGP route across the backbone. (Details not shown.)
4. Configure a sham link:
# Configure PE 1.
[PE1] interface loopback 1
[PE1-LoopBack1] ip binding vpn-instance vpn1
[PE1-LoopBack1] ipv6 address 3::3 128
[PE1-LoopBack1] quit
[PE1] ospfv3 100
[PE1-ospfv3-100] area 1
[PE1-ospfv3-100-area-0.0.0.1] sham-link 3::3 5::5
[PE1-ospfv3-100-area-0.0.0.1] quit
[PE1-ospfv3-100] quit
# Configure PE 2.
[PE2] interface loopback 1
[PE2-LoopBack1] ip binding vpn-instance vpn1
[PE2-LoopBack1] ipv6 address 5::5 128
[PE2-LoopBack1] quit
[PE2] ospfv3 100
[PE2-ospfv3-100] area 1
[PE2-ospfv3-100-area-0.0.0.1] sham-link 5::5 3::3
[PE2-ospfv3-100-area-0.0.0.1] quit
[PE2-ospfv3-100] quit
Verifying the configuration
# Execute the display ipv6 routing-table vpn-instance command on the PEs to verify the following results (details not shown):
· The path to the peer CE is now along the IPv6 BGP route across the backbone.
· A route to the sham link destination address exists.
# Execute the display ipv6 routing-table command on the CEs. Verify that the next hop of the OSPFv3 route to the peer CE is the interface connected to the PE (HundredGigE 1/0/1). This means that the VPN traffic to the peer CE is forwarded over the backbone. (Details not shown.)
# Verify that a sham link has been established on PEs, for example, on PE 1.
[PE1] display ospfv3 sham-link
OSPFv3 Process 100 with Router ID 100.1.1.1
Sham-link (Area: 0.0.0.1)
Neighbor ID State Instance ID Destination address
120.1.1.1 P-2-P 0 5::5
# Verify that the peer state is Full on PE 1.
[PE1] display ospfv3 sham-link verbose
OSPFv3 Process 100 with Router ID 100.1.1.1
Sham-link (Area: 0.0.0.1)
Source : 3::3
Destination : 5::5
Interface ID: 2147483649
Neighbor ID : 120.1.1.1, Neighbor state: Full
Cost: 1 State: P-2-P Type: Sham Instance ID: 0
Timers: Hello 10, Dead 40, Retransmit 5, Transmit delay 1
Request list: 0 Retransmit list: 0
Example: Configuring BGP AS number substitution
Network configuration
As shown in Figure 10, CE 1 and CE 2 belong to VPN 1, and are connected to PE 1 and PE 2. The two CEs have the same AS number, 600. Configure BGP AS number substitution on the PEs to avoid route loss.
Table 8 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
HGE1/0/1 |
10:1::2/96 |
P |
Loop0 |
2.2.2.9/32 |
|
|
HGE1/0/2 |
100::1/96 |
|
HGE1/0/1 |
20.1.1.2/24 |
|
PE 1 |
Loop0 |
10.1.1.1/32 |
|
HGE1/0/2 |
30.1.1.1/24 |
|
|
HGE1/0/1 |
10:1::1/96 |
PE 2 |
Loop0 |
10.1.1.2/32 |
|
|
HGE1/0/2 |
20.1.1.1/24 |
|
HGE1/0/1 |
10:2::1/96 |
|
CE 2 |
HGE1/0/1 |
10:2::2/96 |
|
HGE1/0/2 |
30.1.1.2/24 |
|
|
HGE1/0/2 |
200::1/96 |
|
|
|
Prerequisite
By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface.
Procedure
1. Configure basic IPv6 MPLS L3VPN:
¡ Configure OSPF on the MPLS backbone to allow the PEs and P device to learn the routes of the loopback interfaces from each other.
¡ Configure basic MPLS and MPLS LDP on the MPLS backbone to establish LDP LSPs.
¡ Establish an MP-IBGP peer relationship between the PEs to advertise VPN IPv6 routes.
¡ Configure the VPN instance of VPN 1 on PE 1 to allow CE 1 to access the network.
¡ Configure the VPN instance of VPN 1 on PE 2 to allow CE 2 to access the network.
¡ Configure BGP as the PE-CE routing protocol, and redistribute routes of the CEs into the PEs.
For more information about basic IPv6 MPLS L3VPN configurations, see "Example: Configuring IPv6 MPLS L3VPNs."
# Execute the display ipv6 routing-table command on CE 2 to verify that CE 2 has not learned the route to the VPN (100::/96) behind CE 1.
<CE2> display ipv6 routing-table
Destinations : 6 Routes : 6
Destination: ::1/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 10:2::/96 Protocol : Direct
NextHop : :: Preference: 0
Interface : HGE1/0/1 Cost : 0
Destination: 10:2::2/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 200::/96 Protocol : Static
NextHop : :: Preference: 60
Interface : NULL0 Cost : 0
Destination: FE80::/10 Protocol : Direct
NextHop : :: Preference: 0
Interface : NULL0 Cost : 0
Destination: FF00::/8 Protocol : Direct
NextHop : :: Preference: 0
Interface : NULL0 Cost : 0
# Execute the display ipv6 routing-table command on CE 1 to verify that CE 1 has not learned the route to the VPN behind CE 2. (Details not shown.)
# Execute the display ipv6 routing-table vpn-instance command on the PEs. The output shows the route to the VPN behind the peer CE. This example uses PE 2.
<PE2> display ipv6 routing-table vpn-instance vpn1
Destinations : 7 Routes : 7
Destination: ::1/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 10:2::/96 Protocol : Direct
NextHop : :: Preference: 0
Interface : HGE1/0/1 Cost : 0
Destination: 10:2::1/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 100::/96 Protocol : BGP4+
NextHop : ::FFFF:10.1.1.1 Preference: 255
Interface : HGE1/0/2 Cost : 0
Destination: 200::/96 Protocol : BGP4+
NextHop : 10:2::2 Preference: 255
Interface : HGE1/0/1 Cost : 0
Destination: FE80::/10 Protocol : Direct
NextHop : :: Preference: 0
Interface : NULL0 Cost : 0
Destination: FF00::/8 Protocol : Direct
NextHop : :: Preference: 0
Interface : NULL0 Cost : 0
# Enable BGP update packet debugging on PE 2. The output shows that PE 2 has advertised the route for 100::/96, and the AS_PATH is 100 600.
<PE2> terminal monitor
<PE2> terminal logging level 7
<PE2> debugging bgp update vpn-instance vpn1 10:2::2 ipv6
<PE2> refresh bgp all export ipv6 vpn-instance vpn1
*Jun 13 16:12:52:096 2012 PE2 BGP/7/DEBUG:
BGP_IPV6.vpn1: Send UPDATE to update-group 0 for following destinations:
Origin : Incomplete
AS path : 100 600
Next hop : ::FFFF:10.1.1.1
100::/96,
*Jun 13 16:12:53:024 2012 PE2 BGP/7/DEBUG:
BGP.vpn1: Send UPDATE MSG to peer 10:2::2(IPv6-UNC) NextHop: 10:2::1.
# Execute the display bgp routing-table ipv6 peer received-routes command on CE 2 to verify that CE 2 has not received the route to 100::/96.
<CE2> display bgp routing-table ipv6 peer 10:2::1 received-routes
Total number of routes: 0
2. Configure BGP AS number substitution:
# Configure BGP AS number substitution on PE 1.
<PE1> system-view
[PE1] bgp 100
[PE1-bgp-default] ip vpn-instance vpn1
[PE1-bgp-default-vpn1] peer 10:1::2 substitute-as
[PE1-bgp-default-vpn1] quit
[PE1-bgp-default] quit
# Configure BGP AS number substitution on PE 2.
<PE2> system-view
[PE2] bgp 100
[PE2-bgp-default] ip vpn-instance vpn1
[PE2-bgp-default-vpn1] peer 10:2::2 substitute-as
[PE2-bgp-default-vpn1] quit
[PE2-bgp-default] quit
Verifying the configuration
# The output shows that among the routes advertised by PE 2 to CE 2, the AS_PATH of 100::/96 has changed from 100 600 to 100 100.
*Jun 27 18:07:34:420 2013 PE2 BGP/7/DEBUG:
BGP_IPV6.vpn1: Send UPDATE to peer 10:2::2 for following destinations:
Origin : Incomplete
AS path : 100 100
Next hop : 10:2::1
100::/96,
# Display again the routing information that CE 2 has received, and the routing table. The output shows that CE 2 has learned the route 100::/96.
<CE2> display bgp routing-table ipv6 peer 10:2::1 received-routes
Total number of routes: 1
BGP local router ID is 12.1.1.3
Status codes: * - valid, > - best, d - dampened, h - history,
s - suppressed, S - stale, i - internal, e - external
Origin: i - IGP, e - EGP, ? - incomplete
* >e Network : 100:: PrefixLen : 96
NextHop : 10:2::1 LocPrf :
PrefVal : 0 OutLabel : NULL
MED :
Path/Ogn: 100 100?
<CE2> display ipv6 routing-table
Destinations : 7 Routes : 7
Destination: ::1/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 10:2::/96 Protocol : Direct
NextHop : :: Preference: 0
Interface : HGE1/0/1 Cost : 0
Destination: 10:2::2/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 100::/96 Protocol : BGP4+
NextHop : 10:2::1 Preference: 255
Interface : HGE1/0/1 Cost : 0
Destination: 200::/96 Protocol : Static
NextHop : :: Preference: 60
Interface : NULL0 Cost : 0
Destination: FE80::/10 Protocol : Direct
NextHop : :: Preference: 0
Interface : NULL0 Cost : 0
Destination: FF00::/8 Protocol : Direct
NextHop : :: Preference: 0
Interface : NULL0 Cost : 0
# Verify that HundredGigE 1/0/2 of CE 1 and HundredGigE 1/0/2 of CE 2 can ping each other. (Details not shown.)
Example: Configuring BGP AS number substitution and SoO attribute
Network configuration
CE 1, CE 2, and CE 3 belong to VPN 1, and are connected to PE1, PE 2, and PE 3. CE 1 and CE 2 reside in the same site. CE1, CE2, and CE 3 all use AS number 600.
To avoid route loss, configure BGP AS number substitution on PEs.
To avoid routing loops, configure the same SoO attribute on PE 1 and PE 2 for CE 1 and CE 2.
Figure 11 Network diagram
Table 9 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
Loop0 |
100::1/96 |
CE 3 |
Loop0 |
200::1/96 |
|
|
HGE1/0/1 |
10:1::1/96 |
|
HGE1/0/1 |
10:3::1/96 |
|
CE 2 |
HGE1/0/1 |
10:2::1/96 |
PE 2 |
Loop0 |
2.2.2.9/32 |
|
PE 1 |
Loop0 |
1.1.1.9/32 |
|
HGE1/0/1 |
10:2::2/96 |
|
|
HGE1/0/1 |
10:1::2/96 |
|
HGE1/0/2 |
40.1.1.1/24 |
|
|
HGE1/0/2 |
20.1.1.1/24 |
|
HGE1/0/3 |
20.1.1.2/24 |
|
|
HGE1/0/3 |
30.1.1.1/24 |
P |
Loop0 |
3.3.3.9/32 |
|
PE 3 |
Loop0 |
4.4.4.9/32 |
|
HGE1/0/1 |
30.1.1.2/24 |
|
|
HGE1/0/1 |
10:3::2/96 |
|
HGE1/0/2 |
40.1.1.2/24 |
|
|
HGE1/0/2 |
50.1.1.2/24 |
|
HGE1/0/3 |
50.1.1.1/24 |
Prerequisite
By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface.
Procedure
1. Configure basic IPv6 MPLS L3VPN:
¡ Configure OSPF on the MPLS backbone to allow the PEs and P device to learn the routes of the loopback interfaces from each other.
¡ Configure basic MPLS and MPLS LDP on the MPLS backbone to establish LDP LSPs.
¡ Establish an MP-IBGP peer relationship between the PEs to advertise VPN IPv6 routes.
¡ Configure the VPN instance of VPN 1 on PE 1 to allow CE 1 to access the network.
¡ Configure the VPN instance of VPN 1 on PE 2 to allow CE 2 to access the network.
¡ Configure the VPN instance of VPN 1 on PE 3 to allow CE 3 to access the network.
¡ Configure BGP as the PE-CE routing protocol, and redistribute routes of the CEs into the PEs.
For more information about basic MPLS L3VPN configurations, see "Example: Configuring IPv6 MPLS L3VPNs."
2. Configure BGP AS number substitution:
# Configure BGP AS number substitution on PE 1, PE 2, and PE 3. For more information about the configuration, see "Configuring MPLS L3VPN."
# Display routing information on CE 2. The output shows that CE 2 has learned the route 100::/96 from CE 1. A routing loop has occurred because CE 1 and CE 2 reside in the same site.
<CE2> display bgp routing-table ipv6 peer 10:2::2 received-routes
Total number of routes: 2
BGP local router ID is 12.1.1.3
Status codes: * - valid, > - best, d - dampened, h - history,
s - suppressed, S - stale, i - internal, e - external
Origin: i - IGP, e - EGP, ? - incomplete
* >e Network : 100:: PrefixLen : 96
NextHop : 10:2::2 LocPrf :
PrefVal : 0 OutLabel : NULL
MED :
Path/Ogn: 100 100?
* >e Network : 200:: PrefixLen : 96
NextHop : 10:2::2 LocPrf :
PrefVal : 0 OutLabel : NULL
MED :
Path/Ogn: 100 100?
3. Configure BGP SoO attribute:
# On PE 1, configure the SoO attribute as 1:100 for CE 1.
<PE1> system-view
[PE1] bgp 100
[PE1-bgp-default] ip vpn-instance vpn1
[PE1-bgp-default-vpn1] address-family ipv6
[PE1-bgp-default-ipv6-vpn1] peer 10:1::1 soo 1:100
# On PE 2, configure the SoO attribute as 1:100 for CE 2.
[PE2] bgp 100
[PE2-bgp-default] ip vpn-instance vpn1
[PE2-bgp-default-vpn1] address-family ipv6
[PE2-bgp-default-ipv6-vpn1] peer 10:2::1 soo 1:100
Verifying the configuration
# PE 2 does not advertise routes received from CE 1 to CE 2 because the same SoO attribute has been configured. Display the routing table of CE 2. The output shows that the route 100::/96 has been removed.
<CE2> display ipv6 routing-table
Destinations : 4 Routes : 4
Destination: ::1/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 10:2::/96 Protocol : Direct
NextHop : :: Preference: 0
Interface : HGE1/0/1 Cost : 0
Destination: 10:2::1/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 200::/96 Protocol : Static
NextHop : :: Preference: 60
Interface : NULL0 Cost : 0