- Table of Contents
-
- 03-Layer 2—LAN Switching Configuration Guide
- 00-Preface
- 01-Ethernet interface configuration
- 02-Loopback, null, and inloopback interface configuration
- 03-Bulk interface configuration
- 04-MAC address table configuration
- 05-Ethernet link aggregation configuration
- 06-Port isolation configuration
- 07-Spanning tree configuration
- 08-Loop detection configuration
- 09-VLAN configuration
- 10-MVRP configuration
- 11-QinQ configuration
- 12-VLAN mapping configuration
- 13-PBB configuration
- 14-LLDP configuration
- 15-L2PT configuration
- 16-Service loopback group configuration
- 17-Cut-through forwarding configuration
- 18-DRNI configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 12-VLAN mapping configuration | 332.78 KB |
Contents
VLAN mapping application scenarios
VLAN mapping configuration task list
Configuring one-to-one VLAN mapping
Configuring many-to-one VLAN mapping
Configuring many-to-one VLAN mapping in a network with dynamic IP address assignment
Configuring many-to-one VLAN mapping in a network with static IP address assignment
Configuring one-to-two VLAN mapping
Configuring two-to-two VLAN mapping
Displaying and maintaining VLAN mapping
VLAN mapping configuration examples
One-to-one and many-to-one VLAN mapping configuration example
One-to-two and two-to-two VLAN mapping configuration example
Configuring VLAN mapping
Overview
VLAN mapping re-marks VLAN tagged traffic with new VLAN IDs. H3C provides the following types of VLAN mapping:
· One-to-one VLAN mapping—Replaces one VLAN tag with another.
· Many-to-one VLAN mapping—Replaces multiple VLAN tags with the same VLAN tag.
· One-to-two VLAN mapping—Tags single-tagged packets with an outer VLAN tag.
· Two-to-two VLAN mapping—Replaces the outer and inner VLAN IDs of double tagged traffic with a new pair of VLAN IDs.
VLAN mapping application scenarios
One-to-one and many-to-one VLAN mapping
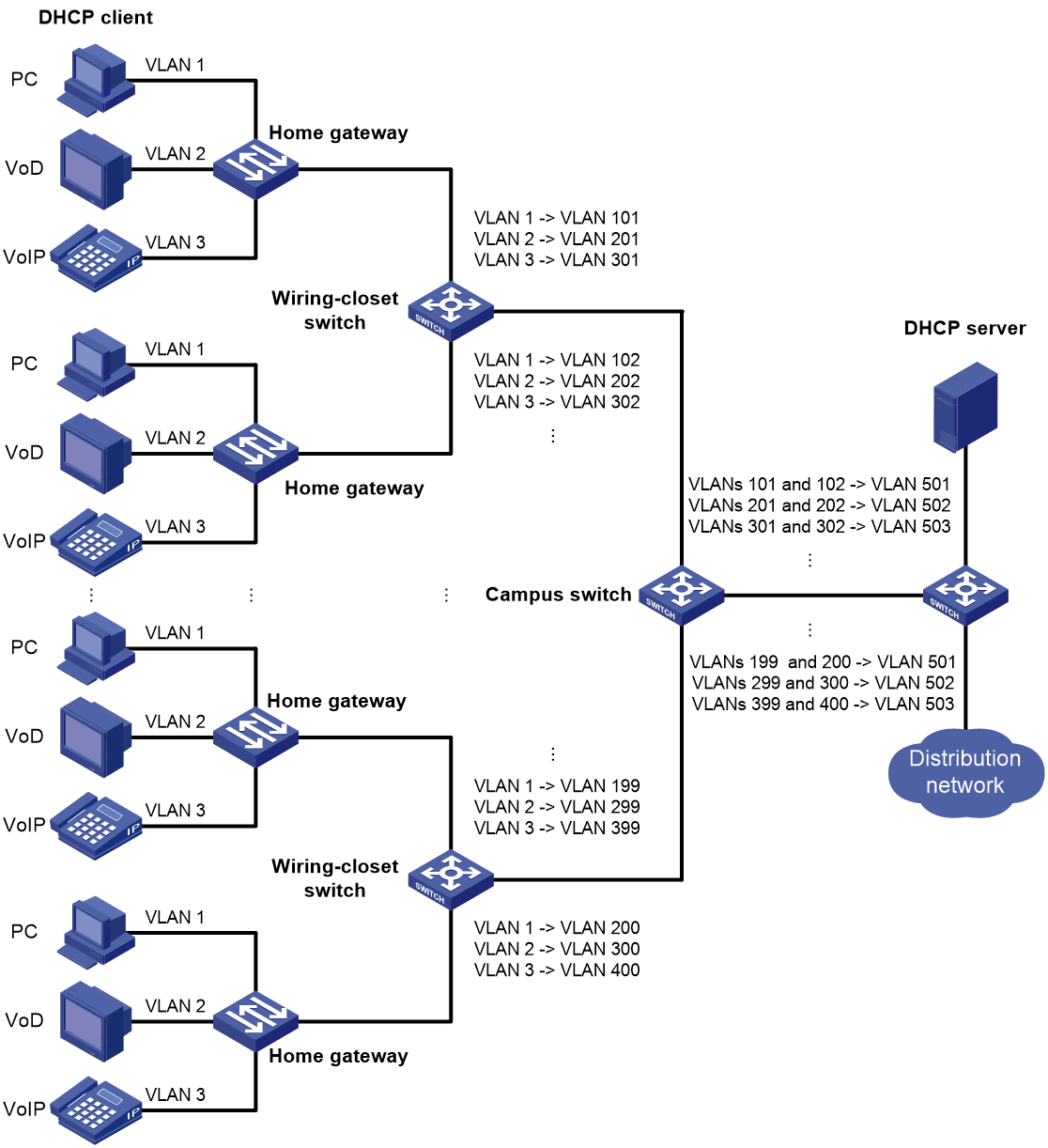
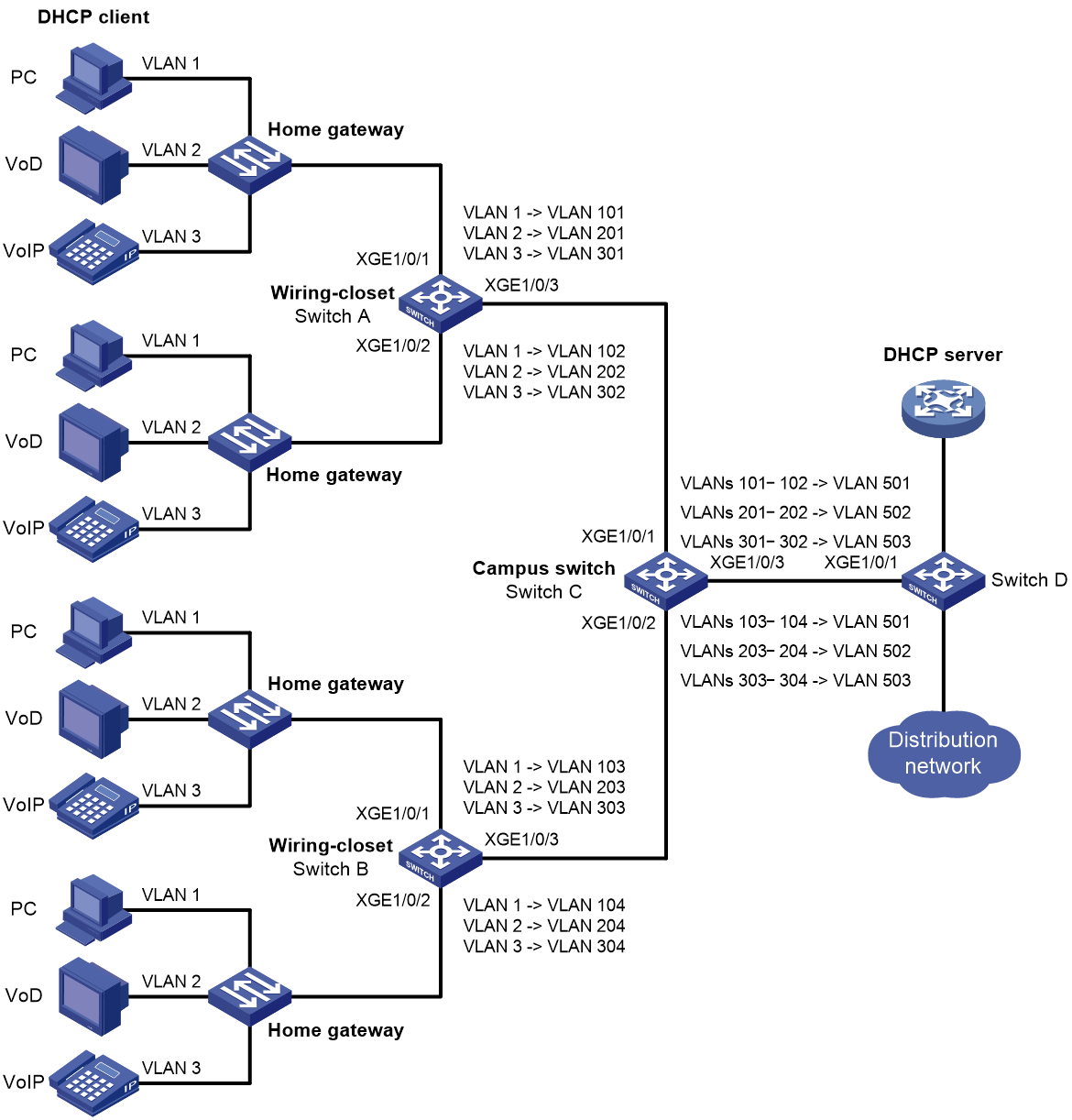
Figure 1 shows a typical application scenario of one-to-one and many-to-one VLAN mapping. The scenario implements broadband Internet access for a community.
Figure 1 Application scenario of one-to-one and many-to-one VLAN mapping
As shown in Figure 1, the network is implemented as follows:
· Each home gateway uses different VLANs to transmit the PC, VoD, and VoIP services.
· To further subclassify each type of traffic by customer, configure one-to-one VLAN mapping on the wiring-closet switches. This feature assigns a separate VLAN to each type of traffic from each customer. The required total number of VLANs in the network can be very large.
One-to-two and two-to-two VLAN mapping
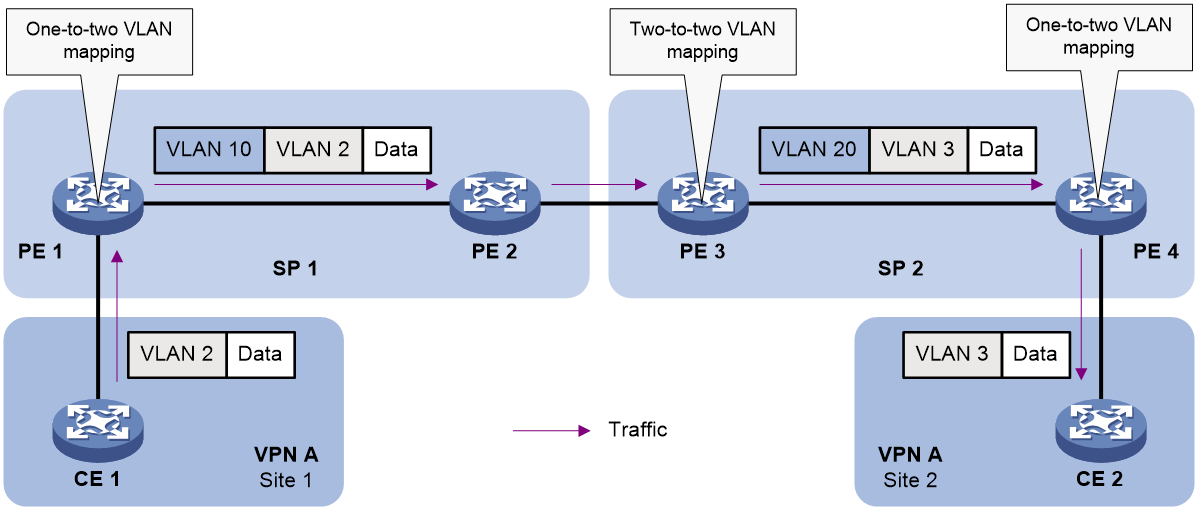
Figure 2 shows a typical application scenario of one-to-two and two-to-two VLAN mapping. In this scenario, the two remote sites of the same VPN must communicate across two SP networks.
Figure 2 Application scenario of one-to-two and two-to-two VLAN mapping
Site 1 and Site 2 are in VLAN 2 and VLAN 3, respectively. The SP 1 network assigns SVLAN 10 to Site 1. The SP 2 network assigns SVLAN 20 to Site 2. When the packet from Site 1 arrives at PE 1, PE 1 tags the packet with SVLAN 10 by using one-to-two VLAN mapping.
When the double-tagged packet from the SP 1 network arrives at the SP 2 network interface, PE 3 processes the packet as follows:
· Replaces SVLAN tag 10 with SVLAN tag 20.
· Replaces CVLAN tag 2 with CVLAN tag 3.
One-to-two VLAN mapping provides the following benefits:
· Enables a customer network to plan its CVLAN assignment without conflicting with SVLANs.
· Adds a VLAN tag to a tagged packet and expands the number of available VLANs to 4094 × 4094.
· Reduces the stress on the SVLAN resources, which were 4094 VLANs in the SP network before the mapping process was initiated.
VLAN mapping implementations
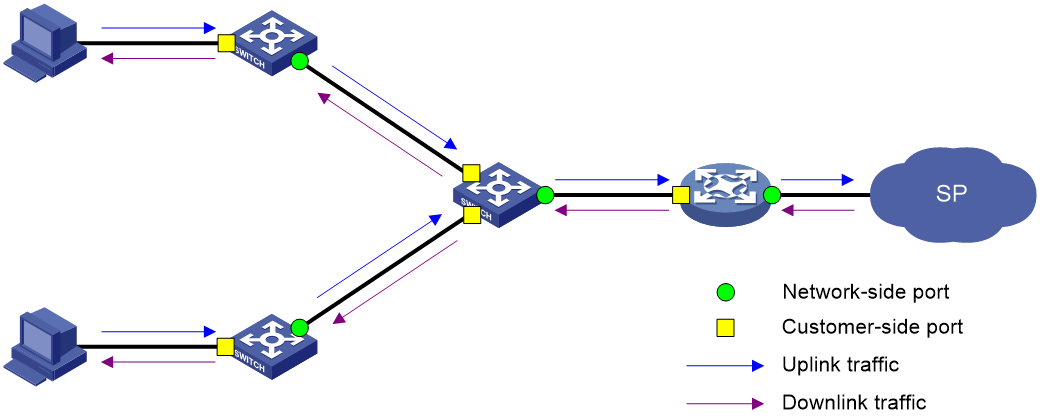
Figure 3 shows a simplified network that illustrates basic VLAN mapping terms.
Basic VLAN mapping terms include the following:
· Uplink traffic—Traffic transmitted from the customer network to the service provider network.
· Downlink traffic—Traffic transmitted from the service provider network to the customer network.
· Network-side port—A port connected to or closer to the service provider network.
· Customer-side port—A port connected to or closer to the customer network.
Figure 3 Basic VLAN mapping terms
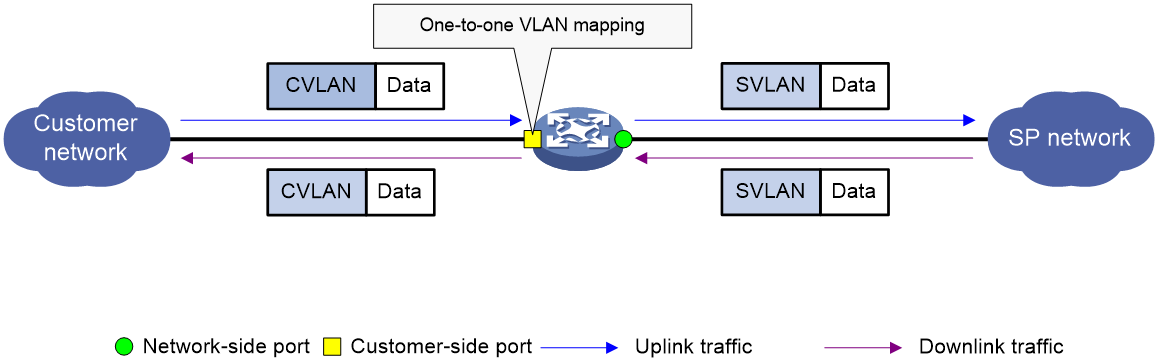
One-to-one VLAN mapping
As shown in Figure 4, one-to-one VLAN mapping is implemented on the customer-side port and replaces VLAN tags as follows:
· Replaces the CVLAN with the SVLAN for the uplink traffic.
· Replaces the SVLAN with the CVLAN for the downlink traffic.
Figure 4 One-to-one VLAN mapping implementation
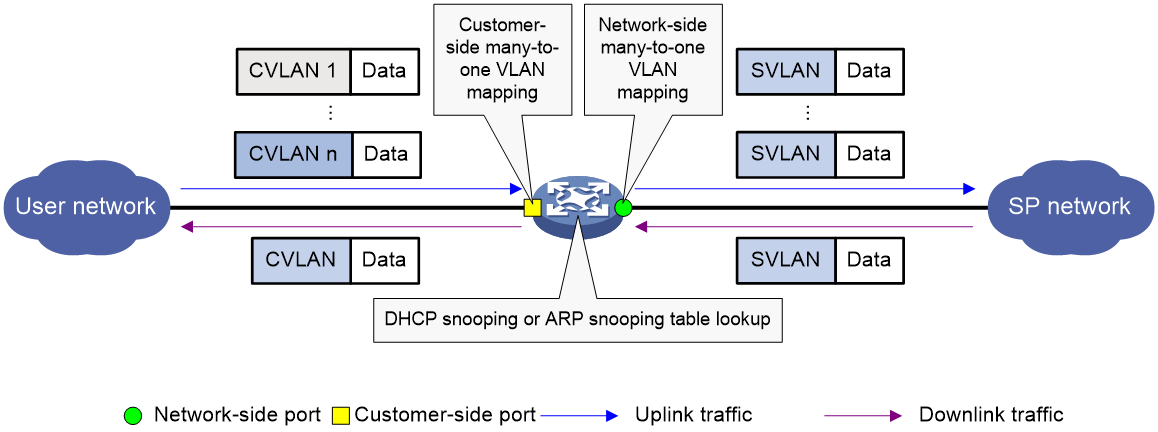
Many-to-one VLAN mapping
As shown in Figure 5, many-to-one VLAN mapping is implemented on both the customer-side and network-side ports as follows:
· For the uplink traffic, the customer-side many-to-one VLAN mapping replaces multiple CVLANs with the same SVLAN.
· For the downlink traffic, the network-side many-to-one VLAN mapping replaces the SVLAN with the CVLAN found in the DHCP or ARP snooping table. For more information about DHCP and ARP snooping, see Layer 3—IP Services Configuration Guide.
Figure 5 Many-to-one VLAN mapping implementation
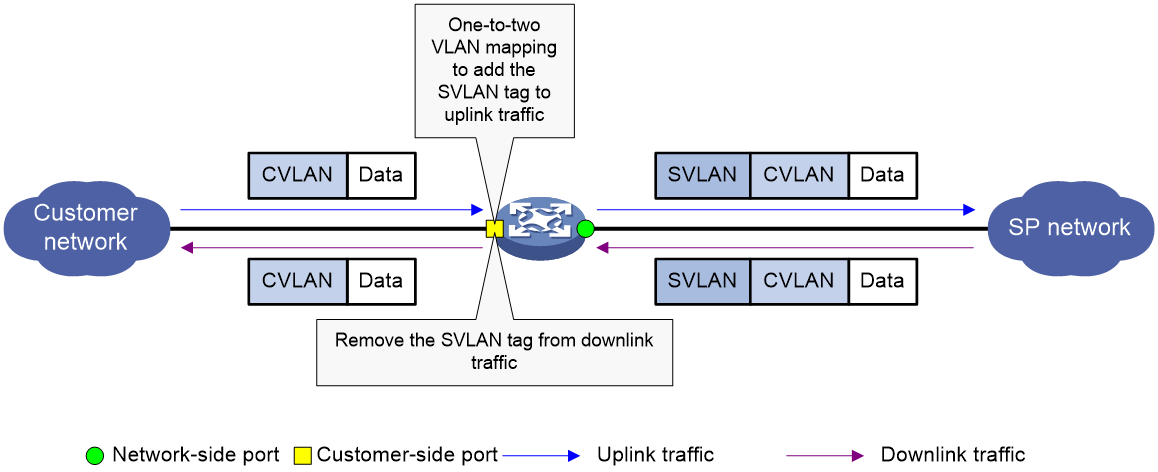
One-to-two VLAN mapping
As shown in Figure 6, one-to-two VLAN mapping is implemented on the customer-side port to add the SVLAN tag for the uplink traffic.
For the downlink traffic to be correctly sent to the customer network, make sure the SVLAN tag is removed on the customer-side port before transmission. Use one of the following methods to remove the SVLAN tag from the downlink traffic:
· Configure the customer-side port as a hybrid port and assign the port to the SVLAN as an untagged member.
· Configure the customer-side port as a trunk port and set the port PVID to the SVLAN.
Figure 6 One-to-two VLAN mapping implementation
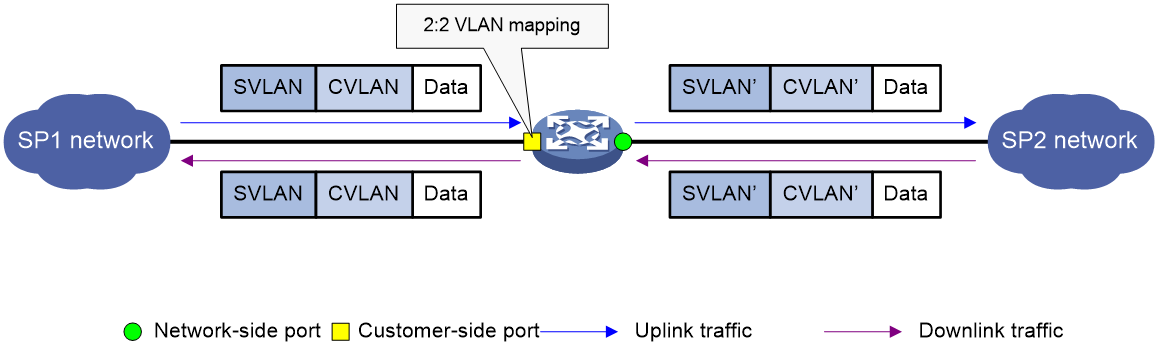
Two-to-two VLAN mapping
As shown in Figure 7, two-to-two VLAN mapping is implemented on the customer-side port and replaces VLAN tags as follows:
· Replaces the CVLAN and the SVLAN with the CVLAN' and the SVLAN' for the uplink traffic.
· Replaces the SVLAN' and CVLAN' with the SVLAN and the CVLAN for the downlink traffic.
Figure 7 Two-to-two VLAN mapping implementation
VLAN mapping configuration task list
When you configure VLAN mapping, follow these guidelines:
· To add VLAN tags to packets, you can configure both VLAN mapping and QinQ. VLAN mapping takes effect if a configuration conflict occurs. For more information about QinQ, see "Configuring QinQ."
· To add or replace VLAN tags for packets, you can configure both VLAN mapping and a QoS policy. The QoS policy takes effect if a configuration conflict occurs. For information about QoS policies, see ACL and QoS Configuration Guide.
· The following features are mutually exclusive with one another on a Layer 2 Ethernet interface or Layer 2 aggregate interface:
¡ EVB.
¡ VLAN mapping.
¡ Binding an Ethernet service instance to a VSI or to an MPLS L2VPN cross-connect.
Do not configure these features simultaneously on the same interface. Otherwise, the features cannot take effect.
|
IMPORTANT: Use the appropriate VLAN mapping methods for the devices in the network. |
To configure VLAN mapping:
|
Tasks at a glance |
Remarks |
|
Configure one-to-one VLAN mapping on the wiring-closet switch, as shown in Figure 1. |
|
|
Configuring many-to-one VLAN mapping · Configuring many-to-one VLAN mapping in a network with dynamic IP address assignment · Configuring many-to-one VLAN mapping in a network with static IP address assignment |
Configure many-to-one VLAN mapping on the campus switch, as shown in Figure 1. |
|
Configure one-to-two VLAN mapping on PE 1 and PE 4, as shown in Figure 2, through which traffic from customer networks enters the service provider networks. |
|
|
Configure two-to-two VLAN mapping on PE 3, as shown in Figure 2, which is an edge device of the SP 2 network. |
Configuring one-to-one VLAN mapping
Configure one-to-one VLAN mapping on the customer-side ports of wiring-closet switches (see Figure 1) to isolate traffic of the same service type from different homes.
Before you configure one-to-one VLAN mapping, create the original VLAN and the translated VLAN.
To configure one-to-one VLAN mapping:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
· Enter Layer 2 Ethernet interface view: · Enter Layer 2 aggregate interface view: |
N/A |
|
3. Set the link type of the port. |
· Set the port link type to trunk: · Set the port link type to hybrid: |
By default, the link type of a port is access. |
|
4. Assign the port to the original VLANs and the translated VLANs. |
· For the trunk port: · For the hybrid port: |
N/A |
|
5. Configure a one-to-one VLAN mapping. |
vlan mapping vlan-id translated-vlan vlan-id |
By default, no VLAN mapping is configured on an interface. |
Configuring many-to-one VLAN mapping
Configure many-to-one VLAN mapping on campus switches (see Figure 1) to transmit the same type of traffic from different users in one VLAN.
Configuring many-to-one VLAN mapping in a network with dynamic IP address assignment
In a network that uses dynamic address assignment, configure many-to-one VLAN mapping with DHCP snooping.
The switch replaces the SVLAN tag of the downlink traffic with the associated CVLAN tag based on the DHCP snooping entry lookup.
Configuration restrictions and guidelines
When you configure many-to-one VLAN mapping in a network that uses dynamic address assignment, follow these restrictions and guidelines:
· Before you configure many-to-one VLAN mapping, create the original VLANs and the translated VLANs.
· To ensure correct traffic forwarding from the service provider network to the customer network, do not configure many-to-one VLAN mapping together with uRPF. For more information about uRPF, see Security Configuration Guide.
· To modify many-to-one VLAN mappings, first use the reset dhcp snooping binding command to clear the DHCP snooping entries.
Many-to-one VLAN mapping configuration task list
|
Tasks at a glance |
Enabling DHCP snooping
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable DHCP snooping. |
dhcp snooping enable |
By default, DHCP snooping is disabled. For more information about DHCP snooping configuration commands, see Layer 3—IP Services Command Reference. |
Enabling ARP detection
Enable ARP detection for the original VLANs and the translated VLANs.
To enable ARP detection:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Enable ARP detection. |
arp detection enable |
By default, ARP detection is disabled. For more information about ARP detection configuration commands, see Security Command Reference. |
Configuring the customer-side port
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
· Enter Layer 2 Ethernet interface view: · Enter Layer 2 aggregate interface view: |
N/A |
|
3. Set the link type of the port. |
· Set the port link type to trunk: · Set the port link type to hybrid: |
By default, the link type of a port is access. |
|
4. Assign the port to the original VLANs and the translated VLANs. |
· For the trunk port: · For the hybrid port: |
N/A |
|
5. Configure a many-to-one VLAN mapping. |
vlan mapping uni { range vlan-range-list | single vlan-id-list } translated-vlan vlan-id |
By default, no VLAN mapping is configured on an interface. |
|
6. Enable DHCP snooping entry recording. |
dhcp snooping binding record |
By default, DHCP snooping entry recording is disabled on an interface. |
Configuring the network-side port
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
· Enter Layer 2 Ethernet interface view: · Enter Layer 2 aggregate interface view: |
N/A |
|
3. Set the link type of the port. |
· Set the port link type to trunk: · Set the port link type to hybrid: |
By default, the link type of a port is access. |
|
4. Assign the port to the translated VLANs. |
· For the trunk port: · For
the hybrid port: |
N/A |
|
5. Configure the port as a DHCP snooping trusted port. |
dhcp snooping trust |
By default, all ports that support DHCP snooping are untrusted ports when DHCP snooping is enabled. |
|
6. Configure the port as an ARP trusted port. |
arp detection trust |
By default, all ports are ARP untrusted ports. |
|
7. Configure the port to use the original VLAN tags of the many-to-one mapping to replace the VLAN tags of the packets destined for the user network. |
vlan mapping nni |
By default, the port does not replace the VLAN tags of the packets destined for the user network. |
Configuring many-to-one VLAN mapping in a network with static IP address assignment
In a network that uses static IP addresses, configure many-to-one VLAN mapping with ARP snooping.
The switch replaces the SVLAN tag of the downlink traffic with the associated CVLAN tag based on the ARP snooping entry lookup.
Configuration restrictions and guidelines
When you configure many-to-one VLAN mapping in a network that uses static address assignment, follow these restrictions and guidelines:
· Before you configure many-to-one VLAN mapping, create the original VLANs and the translated VLANs.
· Make sure hosts in different CVLANs do not use the same IP address.
· When an IP address is no longer associated with the MAC address and VLAN in an ARP snooping entry, wait for this entry to be aged out. You can also use the reset arp snooping ip ip-address command to clear the entry.
· Before you modify many-to-one VLAN mapping, use the reset arp snooping vlan vlan-id command to clear the ARP snooping entries in each CVLAN.
· To ensure correct traffic forwarding from the service provider network to the customer network, do not configure many-to-one VLAN mapping together with uRPF. For more information about uRPF, see Security Configuration Guide.
Configuration task list
|
Tasks at a glance |
Enabling ARP snooping
Enable ARP snooping for the original VLANs and the translated VLANs.
To enable ARP snooping:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Enable ARP snooping. |
arp snooping enable |
By default, ARP snooping is disabled. For more information about ARP snooping commands, see Layer 3—IP Services Command Reference. |
Configuring the customer-side port
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
· Enter Layer 2 Ethernet interface view: · Enter Layer 2 aggregate interface view: |
N/A |
|
3. Set the link type of the port. |
· Set the port link type to trunk: · Set the port link type to hybrid: |
By default, the link type of a port is access. |
|
4. Assign the port to the original VLANs and the translated VLANs. |
· For the trunk port: · For
the hybrid port: |
N/A |
|
5. Configure a many-to-one VLAN mapping. |
vlan mapping uni { range vlan-range-list | single vlan-id-list } translated-vlan vlan-id |
By default, no VLAN mapping is configured on an interface. |
Configuring the network-side port
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
· Enter Layer 2 Ethernet interface view: · Enter Layer 2 aggregate interface view: |
N/A |
|
3. Set the link type of the port. |
· Set the port link type to trunk: · Set the port link type to hybrid: |
By default, the link type of a port is access. |
|
4. Assign the port to the translated VLANs. |
· For
the trunk port: · For
the hybrid port: |
N/A |
|
5. Configure the port to use the original VLAN tags of the many-to-one mapping to replace the VLAN tags of the packets destined for the user network. |
vlan mapping nni |
By default, the port does not replace the VLAN tags of the packets destined for the user network. |
Configuring one-to-two VLAN mapping
Configure one-to-two VLAN mapping on the customer-side ports of edge devices from which customer traffic enters SP networks, for example, on PEs 1 and 4 in Figure 2. One-to-two VLAN mapping enables the edge devices to add an SVLAN tag to each incoming packet.
Before you configure one-to-two VLAN mapping, create the SVLAN first.
The MTU of an interface is 1500 bytes by default. After a VLAN tag is added to a packet, the packet length is added by 4 bytes. As a best practice, set the MTU to a minimum of 1504 bytes for ports on the forwarding path of the packet in the service provider network.
To configure one-to-two VLAN mapping:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
· Enter Layer 2 Ethernet interface view: · Enter Layer 2 aggregate interface view: |
N/A |
|
3. Set the link type of the port. |
· Set the port link type to trunk: · Set the port link type to hybrid: |
By default, the link type of a port is access. |
|
4. Configure the port to allow packets from the SVLAN to pass through untagged. |
· For the trunk port: a. Configure the SVLAN as the PVID of
the trunk port: b. Assign the trunk
port to the SVLAN: · For the hybrid port: |
N/A |
|
5. Configure a one-to-two VLAN mapping. |
vlan mapping nest { range vlan-range-list | single vlan-id-list } nested-vlan vlan-id |
By default, no VLAN mapping is configured on an interface. Only one SVLAN tag can be added to packets from the same CVLAN. To add different SVLAN tags to different CVLAN packets, set the port link type to hybrid and repeat this command. |
Configuring two-to-two VLAN mapping
Configure two-to-two VLAN mapping on the customer-side port of an edge device that connects two SP networks, for example, on PE 3 in Figure 2. Two-to-two VLAN mapping enables two sites in different VLANs to communicate at Layer 2 across two service provider networks that use different VLAN assignment schemes.
Before you configure two-to-two VLAN mapping, create the original VLANs and the translated VLANs.
To configure two-to-two VLAN mapping:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
· Enter Layer 2 Ethernet interface view: · Enter Layer 2 aggregate interface view: |
N/A |
|
3. Set the link type of the port. |
· Set the port link type to trunk: · Set the port link type to hybrid: |
By default, the link type of a port is access. |
|
4. Assign the port to the original VLANs and the translated VLANs. |
· For the trunk port: · For the hybrid port: |
N/A |
|
5. Configure a two-to-two VLAN mapping. |
vlan mapping tunnel outer-vlan-id inner-vlan-id translated-vlan outer-vlan-id inner-vlan-id |
By default, no VLAN mapping is configured on an interface. |
Displaying and maintaining VLAN mapping
Execute display commands in any view.
|
Task |
Command |
|
Display VLAN mapping information. |
display vlan mapping [ interface interface-type interface-number ] |
VLAN mapping configuration examples
One-to-one and many-to-one VLAN mapping configuration example
Network requirements
As shown in Figure 8:
· Each household subscribes to PC, VoD, and VoIP services, and obtains the IP address through DHCP.
· On the home gateways, VLANs 1, 2, and 3 are assigned to PC, VoD, and VoIP traffic, respectively.
To isolate traffic of the same service type from different households, configure one-to-one VLAN mappings on the wiring-closet switches. This feature assigns one VLAN to each type of traffic from each household.
To save VLAN resources, configure many-to-one VLAN mappings on the campus switch (Switch C). This feature transmits the same type of traffic from different households in one VLAN. Use VLANs 501, 502, and 503 for PC, VoD, and VoIP traffic, respectively.
Table 1 VLAN mappings for each service
|
Service |
VLANs on home gateways |
VLANs on wiring-closet switches (Switch A and Switch B) |
VLANs on campus switch (Switch C) |
|
PC |
VLAN 1 |
VLANs 101, 102, 103, 104 |
VLAN 501 |
|
VoD |
VLAN 2 |
VLANs 201, 202, 203, 204 |
VLAN 502 |
|
VoIP |
VLAN 3 |
VLANs 301, 302, 303, 304 |
VLAN 503 |
Configuration procedure
1. Configure Switch A:
# Create the original VLANs.
<SwitchA> system-view
[SwitchA] vlan 2 to 3
# Create the translated VLANs.
[SwitchA] vlan 101 to 102
[SwitchA] vlan 201 to 202
[SwitchA] vlan 301 to 302
# Configure customer-side port Ten-GigabitEthernet 1/0/1 as a trunk port.
<SwitchA> system-view
[SwitchA] interface ten-gigabitethernet 1/0/1
[SwitchA-Ten-GigabitEthernet1/0/1] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/1 to all original VLANs and translated VLANs.
[SwitchA-Ten-GigabitEthernet1/0/1] port trunk permit vlan 1 2 3 101 201 301
# Configure one-to-one VLAN mappings on Ten-GigabitEthernet 1/0/1 to map VLANs 1, 2, and 3 to VLANs 101, 201, and 301, respectively.
[SwitchA-Ten-GigabitEthernet1/0/1] vlan mapping 1 translated-vlan 101
[SwitchA-Ten-GigabitEthernet1/0/1] vlan mapping 2 translated-vlan 201
[SwitchA-Ten-GigabitEthernet1/0/1] vlan mapping 3 translated-vlan 301
[SwitchA-Ten-GigabitEthernet1/0/1] quit
# Configure customer-side port Ten-GigabitEthernet 1/0/2 as a trunk port.
[SwitchA] interface ten-gigabitethernet 1/0/2
[SwitchA-Ten-GigabitEthernet1/0/2] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/2 to all original VLANs and translated VLANs.
[SwitchA-Ten-GigabitEthernet1/0/2] port trunk permit vlan 1 2 3 102 202 302
# Configure one-to-one VLAN mappings on Ten-GigabitEthernet 1/0/2 to map VLANs 1, 2, and 3 to VLANs 102, 202, and 302, respectively.
[SwitchA-Ten-GigabitEthernet1/0/2] vlan mapping 1 translated-vlan 102
[SwitchA-Ten-GigabitEthernet1/0/2] vlan mapping 2 translated-vlan 202
[SwitchA-Ten-GigabitEthernet1/0/2] vlan mapping 3 translated-vlan 302
[SwitchA-Ten-GigabitEthernet1/0/2] quit
# Configure the network-side port (Ten-GigabitEthernet 1/0/3) as a trunk port.
[SwitchA] interface ten-gigabitethernet 1/0/3
[SwitchA-Ten-GigabitEthernet1/0/3] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/3 to the translated VLANs.
[SwitchA-Ten-GigabitEthernet1/0/3] port trunk permit vlan 101 201 301 102 202 302
[SwitchA-Ten-GigabitEthernet1/0/3] quit
2. Configure Switch B in the same way Switch A is configured. (Details not shown.)
3. Configure Switch C:
# Enable DHCP snooping.
<SwitchC> system-view
[SwitchC] dhcp snooping enable
# Create the original VLANs and translated VLANs, and enable ARP detection for these VLANs.
[SwitchC] vlan 101
[SwitchC-vlan101] arp detection enable
[SwitchC-vlan101] vlan 201
[SwitchC-vlan201] arp detection enable
[SwitchC-vlan201] vlan 301
[SwitchC-vlan301] arp detection enable
[SwitchC-vlan301] vlan 102
[SwitchC-vlan102] arp detection enable
[SwitchC-vlan102] vlan 202
[SwitchC-vlan202] arp detection enable
[SwitchC-vlan202] vlan 302
[SwitchC-vlan302] arp detection enable
[SwitchC-vlan302] vlan 103
[SwitchC-vlan103] arp detection enable
[SwitchC-vlan103] vlan 203
[SwitchC-vlan203] arp detection enable
[SwitchC-vlan203] vlan 303
[SwitchC-vlan303] arp detection enable
[SwitchC-vlan303] vlan 104
[SwitchC-vlan104] arp detection enable
[SwitchC-vlan104] vlan 204
[SwitchC-vlan204] arp detection enable
[SwitchC-vlan204] vlan 304
[SwitchC-vlan304] arp detection enable
[SwitchC-vlan304] vlan 501
[SwitchC-vlan501] arp detection enable
[SwitchC-vlan501] vlan 502
[SwitchC-vlan502] arp detection enable
[SwitchC-vlan502] vlan 503
[SwitchC-vlan503] arp detection enable
[SwitchC-vlan503] quit
# Configure customer-side port Ten-GigabitEthernet 1/0/1 as a trunk port.
[SwitchC] interface ten-gigabitethernet 1/0/1
[SwitchC-Ten-GigabitEthernet1/0/1] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/1 to all original VLANs and translated VLANs.
[SwitchC-Ten-GigabitEthernet1/0/1] port trunk permit vlan 101 102 201 202 301 302 501 to 503
# Configure many-to-one VLAN mappings on Ten-GigabitEthernet 1/0/1 to map VLANs for PC, VoD, and VoIP traffic to VLANs 501, 502, and 503, respectively.
[SwitchC-Ten-GigabitEthernet1/0/1] vlan mapping uni range 101 to 102 translated-vlan 501
[SwitchC-Ten-GigabitEthernet1/0/1] vlan mapping uni range 201 to 202 translated-vlan 502
[SwitchC-Ten-GigabitEthernet1/0/1] vlan mapping uni range 301 to 302 translated-vlan 503
# Enable DHCP snooping entry recording on Ten-GigabitEthernet 1/0/1.
[SwitchC-Ten-GigabitEthernet1/0/1] dhcp snooping binding record
[SwitchC-Ten-GigabitEthernet1/0/1] quit
# Configure customer-side port Ten-GigabitEthernet 1/0/2 as a trunk port.
[SwitchC] interface ten-gigabitethernet 1/0/2
[SwitchC-Ten-GigabitEthernet1/0/2] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/2 to all original VLANs and translated VLANs.
[SwitchC-Ten-GigabitEthernet1/0/2] port trunk permit vlan 103 104 203 204 303 304 501 to 503
# Configure many-to-one VLAN mappings on Ten-GigabitEthernet 1/0/2 to map VLANs for PC, VoD, and VoIP traffic to VLANs 501, 502, and 503, respectively.
[SwitchC-Ten-GigabitEthernet1/0/2] vlan mapping uni range 103 to 104 translated-vlan 501
[SwitchC-Ten-GigabitEthernet1/0/2] vlan mapping uni range 203 to 204 translated-vlan 502
[SwitchC-Ten-GigabitEthernet1/0/2] vlan mapping uni range 303 to 304 translated-vlan 503
# Enable recording of client information in DHCP snooping entries on Ten-GigabitEthernet 1/0/2.
[SwitchC-Ten-GigabitEthernet1/0/2] dhcp snooping binding record
[SwitchC-Ten-GigabitEthernet1/0/2] quit
# Configure the network-side port (Ten-GigabitEthernet 1/0/3) to use the original VLAN tags of the many-to-one mappings to replace the VLAN tags of the packets destined for the user network.
[SwitchC] interface ten-gigabitethernet 1/0/3
[SwitchC-Ten-GigabitEthernet1/0/3] vlan mapping nni
# Configure the network-side port Ten-GigabitEthernet 1/0/3 as a trunk port.
[SwitchC-Ten-GigabitEthernet1/0/3] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/3 to the translated VLANs.
[SwitchC-Ten-GigabitEthernet1/0/3] port trunk permit vlan 501 to 503
# Configure Ten-GigabitEthernet 1/0/3 as a DHCP snooping trusted and ARP trusted port.
[SwitchC-Ten-GigabitEthernet1/0/3] dhcp snooping trust
[SwitchC-Ten-GigabitEthernet1/0/3] arp detection trust
[SwitchC-Ten-GigabitEthernet1/0/3] quit
4. Configure Switch D:
# Create the translated VLANs.
<SwitchD> system-view
[SwitchD] vlan 501 to 503
# Configure Ten-GigabitEthernet 1/0/1 as a trunk port.
<SwitchD> system-view
[SwitchD] interface ten-gigabitethernet 1/0/1
[SwitchD-Ten-GigabitEthernet1/0/1] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/1 to the translated VLANs.
[SwitchD-Ten-GigabitEthernet1/0/1] port trunk permit vlan 501 to 503
[SwitchD-Ten-GigabitEthernet1/0/1] quit
Verifying the configuration
# Verify VLAN mapping information on the wiring-closet switches, for example, Switch A.
[SwitchA] display vlan mapping
Interface Ten-GigabitEthernet1/0/1:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
1 N/A 101 N/A
2 N/A 201 N/A
3 N/A 301 N/A
Interface Ten-GigabitEthernet1/0/2:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
1 N/A 102 N/A
2 N/A 202 N/A
3 N/A 302 N/A
# Verify VLAN mapping information on Switch C.
[SwitchC] display vlan mapping
Interface Ten-GigabitEthernet1/0/1:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
101-102 N/A 501 N/A
201-202 N/A 502 N/A
301-302 N/A 503 N/A
Interface Ten-GigabitEthernet1/0/2:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
103-104 N/A 501 N/A
203-204 N/A 502 N/A
303-304 N/A 503 N/A
One-to-two and two-to-two VLAN mapping configuration example
Network requirements
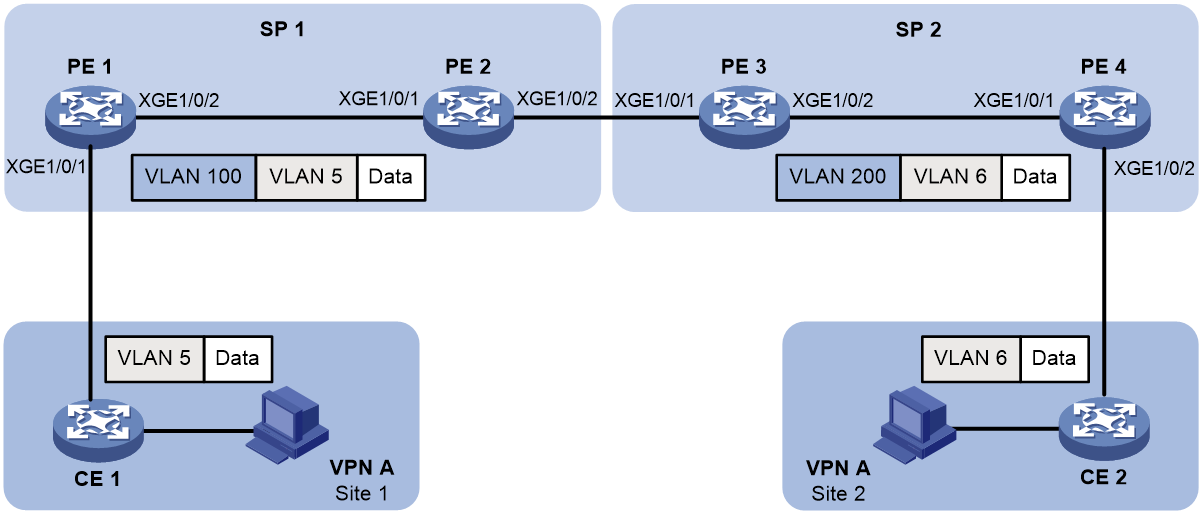
As shown in Figure 9:
· Two VPN A branches, Site 1 and Site 2, are in VLAN 5 and VLAN 6, respectively.
· The two sites use different VPN access services from different service providers, SP 1 and SP 2.
· SP 1 assigns VLAN 100 to Site 1 and Site 2. SP 2 assigns VLAN 200 to Site 1 and Site 2.
Configure one-to-two VLAN mappings and two-to-two VLAN mappings to enable the two branches to communicate across networks SP 1 and SP 2.
Configuration procedure
1. Configure PE 1:
# Create VLANs 5 and 100.
<PE1> system-view
[PE1] vlan 5
[PE1-vlan5] quit
[PE1] vlan 100
[PE1-vlan100] quit
# Configure a one-to-two VLAN mapping on the customer-side port (Ten-GigabitEthernet 1/0/1) to add SVLAN tag 100 to packets from VLAN 5.
[PE1] interface ten-gigabitethernet 1/0/1
[PE1-Ten-GigabitEthernet1/0/1] vlan mapping nest single 5 nested-vlan 100
# Configure Ten-GigabitEthernet 1/0/1 as a hybrid port.
[PE1-Ten-GigabitEthernet1/0/1] port link-type hybrid
# Assign Ten-GigabitEthernet 1/0/1 to VLAN 100 as an untagged member.
[PE1-Ten-GigabitEthernet1/0/1] port hybrid vlan 100 untagged
[PE1-Ten-GigabitEthernet1/0/1] quit
# Configure the network-side port (Ten-GigabitEthernet 1/0/2) as a trunk port.
[PE1] interface ten-gigabitethernet 1/0/2
[PE1-Ten-GigabitEthernet1/0/2] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/2 to VLAN 100.
[PE1-Ten-GigabitEthernet1/0/2] port trunk permit vlan 100
[PE1-Ten-GigabitEthernet1/0/2] quit
2. Configure PE 2:
# Create VLAN 100.
<PE2> system-view
[PE2] vlan 100
[PE2-vlan100] quit
# Configure Ten-GigabitEthernet 1/0/1 as a trunk port.
[PE2] interface ten-gigabitethernet 1/0/1
[PE2-Ten-GigabitEthernet1/0/1] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/1 to VLAN 100.
[PE2-Ten-GigabitEthernet1/0/1] port trunk permit vlan 100
[PE2-Ten-GigabitEthernet1/0/1] quit
# Configure Ten-GigabitEthernet 1/0/2 as a trunk port.
[PE2] interface ten-gigabitethernet 1/0/2
[PE2-Ten-GigabitEthernet1/0/2] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/2 to VLAN 100.
[PE2-Ten-GigabitEthernet1/0/2] port trunk permit vlan 100
[PE2-Ten-GigabitEthernet1/0/2] quit
3. Configure PE 3:
# Create VLANs 5, 6, 100, and 200.
<PE3> system-view
[PE3] vlan 5 to 6
[PE3] vlan 100
[PE3-vlan100] quit
[PE3] vlan 200
[PE3-vlan200] quit
# Configure Ten-GigabitEthernet 1/0/1 as a trunk port.
[PE3] interface ten-gigabitethernet 1/0/1
[PE3-Ten-GigabitEthernet1/0/1] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/1 to VLANs 100 and 200.
[PE3-Ten-GigabitEthernet1/0/1] port trunk permit vlan 100 200
# Configure a two-to-two VLAN mapping on Ten-GigabitEthernet 1/0/1 to map SVLAN 100 and CVLAN 5 to SVLAN 200 and CVLAN 6.
[PE3-Ten-GigabitEthernet1/0/1] vlan mapping tunnel 100 5 translated-vlan 200 6
[PE3-Ten-GigabitEthernet1/0/1] quit
# Configure Ten-GigabitEthernet 1/0/2 as a trunk port.
[PE3] interface ten-gigabitethernet 1/0/2
[PE3-Ten-GigabitEthernet1/0/2] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/2 to VLAN 200.
[PE3-Ten-GigabitEthernet1/0/2] port trunk permit vlan 200
[PE3-Ten-GigabitEthernet1/0/2] quit
4. Configure PE 4:
# Create VLANs 6 and 200.
<PE4> system-view
[PE4] vlan 6
[PE4-vlan6] quit
[PE4] vlan 200
[PE4-vlan200] quit
# Configure the network-side port (Ten-GigabitEthernet 1/0/1) as a trunk port.
[PE4] interface ten-gigabitethernet 1/0/1
[PE4-Ten-GigabitEthernet1/0/1] port link-type trunk
# Assign Ten-GigabitEthernet 1/0/1 to VLAN 200.
[PE4-Ten-GigabitEthernet1/0/1] port trunk permit vlan 200
[PE4-Ten-GigabitEthernet1/0/1] quit
# Configure the customer-side port (Ten-GigabitEthernet 1/0/2) as a hybrid port.
[PE4] interface ten-gigabitethernet 1/0/2
[PE4-Ten-GigabitEthernet1/0/2] port link-type hybrid
# Assign Ten-GigabitEthernet 1/0/2 to VLAN 200 as an untagged member.
[PE4-Ten-GigabitEthernet1/0/2] port hybrid vlan 200 untagged
# Configure a one-to-two VLAN mapping on Ten-GigabitEthernet 1/0/2 to add SVLAN tag 200 to packets from VLAN 6.
[PE4-Ten-GigabitEthernet1/0/2] vlan mapping nest single 6 nested-vlan 200
[PE4-Ten-GigabitEthernet1/0/2] quit
Verifying the configuration
# Verify VLAN mapping information on PE 1.
[PE1] display vlan mapping
Interface Ten-GigabitEthernet1/0/1:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
5 N/A 100 5
# Verify VLAN mapping information on PE 3.
[PE3] display vlan mapping
Interface Ten-GigabitEthernet1/0/1:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
100 5 200 6
# Verify VLAN mapping information on PE 4.
[PE4] display vlan mapping
Interface Ten-GigabitEthernet1/0/2:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
6 N/A 200 6