- Table of Contents
-
- 16-Security Configuration Guide
- 00-Preface
- 01-ACL configuration
- 02-APR configuration
- 03-ARP attack protection configuration
- 04-ASPF configuration
- 05-IP source guard configuration
- 06-IPsec configuration
- 07-ND attack defense configuration
- 08-Password control configuration
- 09-PKI configuration
- 10-SSH configuration
- 11-SSL configuration
- 12-SSL VPN configuration
- 13-URL filtering configuration
- 14-User profile configuration
- 15-Bandwidth management configuration
- 16-Public key management
- 17-Attack detection and prevention configuration
- 18-Session management
- 19-Connection limit configuration
- 20-Crypto engine configuration
- 21-Time range configuration
- 22-Protocol packet rate limit configuration
- 23-DPI engine configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 14-User profile configuration | 371.93 KB |
Prerequisites for user profile
Display and maintenance commands for user profiles
User profile configuration examples
Example: Configuring user profiles with RADIUS and MAC authentication
Configuring user profiles
About user profiles
A user profile defines a set of parameters, such as a QoS policy, for a user or a class of users. A user profile can be reused when a user connected to the network on a different interface.
The user profile application allows flexible traffic policing on a per-user basis. Each time a user passes authentication, the server sends the device the name of the user profile specified for the user. The device applies the parameters in the user profile to the user.
The device works with an authentication server to perform remote user authentication. You must specify the user profile associated with the user on the authentication server.
A user is subject to the associated user profile after it comes online. A user profile limits the access behaviors of online users. The configuration of a user profile is not in effect if the user is not online.
You can use user profiles for the following purposes:
· Allocate system resource per user—The interface-based traffic policing limits the total amount of bandwidth available to a group of users. However, user-profile-based traffic policing can limit the amount of bandwidth available to a single user.
· Flexibly limit access to system resources—For interface-based traffic policing, if the user comes online on a different interface, you must remove the traffic policing configuration and reconfigure traffic policing on the new interface. For user-profile-based traffic policing, the traffic policing configuration is automatically issued to the user when the user comes online. When the user goes offline, the traffic policing configuration is automatically removed.
Prerequisites for user profile
A user profile works with authentication methods. You must configure authentication for a user profile. For information about supported authentication methods, see the configuration guides for the related authentication modules.
Configuring a user profile
1. Enter system view.
system-view
2. Create a user profile and enter user profile view.
user-profile profile-name
Display and maintenance commands for user profiles
|
IMPORTANT: The WX1800H series, WX2500H series, and WX3000H series access controllers do not support parameters or commands that are available only in IRF mode. |
Execute display commands in any view.
|
Task |
Command |
|
Display configuration and online user information for the specified user profile or all user profiles. |
In standalone mode: display user-profile [ name profile-name ] In IRF mode: display user-profile [ name profile-name ] [ slot slot-number ] |
User profile configuration examples
Example: Configuring user profiles with RADIUS and MAC authentication
Network configuration
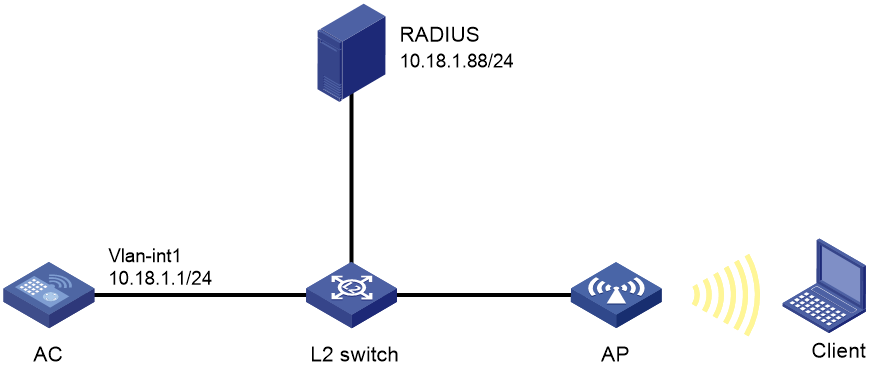
As shown in Figure 1, the AC is connected to the RADIUS server through a Layer 2 switch.
Configure the AC to meet the following requirements:
· MAC authentication is used.
· MAC-authenticated users access the wireless network through the specified AP.
Procedure
Before configuring the AC, make sure:
· The AC and the RADIUS server can reach each other.
· An account with username 123 and password aaa_maca has been added on the RADIUS server.
1. Configure a RADIUS scheme:
# Create a RADIUS scheme named imcc.
<AC> system-view
[AC] radius scheme imcc
# Specify the primary authentication server.
[AC-radius-imcc] primary authentication 10.18.1.88 1812
# Specify the primary accounting server.
[AC-radius-imcc] primary accounting 10.18.1.88 1813
# Set the authentication key to 12345678 in plaintext form.
[AC-radius-imcc] key authentication simple 12345678
# Set the accounting key to 12345678 in plaintext form.
# Exclude domain names from the usernames sent to the RADIUS server.
[AC-radius-imcc] user-name-format without-domain
[AC-radius-imcc] quit
2. Configure AAA methods for an ISP domain:
# Create an ISP domain named imc.
[AC] domain imc
# Apply RADIUS scheme imcc to ISP domain imc for authentication, authorization, and accounting.
[AC-isp-imc] authentication lan-access radius-scheme imcc
[AC-isp-imc] authorization lan-access radius-scheme imcc
[AC-isp-imc] accounting lan-access radius-scheme imcc
[AC-isp-imc] quit
3. Configure MAC authentication:
# Specify username 123 and password aaa_maca in plain text for the account shared by MAC authentication users.
[AC] mac-authentication user-name-format fixed account 123 password simple aaa_maca
# Configure SSID maca_imc for wireless service template maca_imc.
[AC] wlan service-template maca_imc
[AC-wlan-st-maca_imc] ssid maca_imc
# Set the authentication mode to MAC authentication.
[AC-wlan-st-maca_imc] client-security authentication-mode mac
# Specify the ISP domain imc for the service template.
[AC-wlan-st-maca_imc] mac-authentication domain imc
# Enable the service template.
[AC-wlan-st-maca_imc] service-template enable
[AC-wlan-st-maca_imc] quit
4. Configure the manual AP ap1, and bind the service template to an AP radio:
# Create a manual AP named ap1, and specify the AP model and serial ID.
[AC] wlan ap ap1 model WA4320i-ACN
[AC-wlan-ap-ap1] serial-id 210235A1BSC123000050
# Configure channel 149 as the working channel for radio 1 of the AP, and enable radio 1.
[AC-wlan-ap-ap1-radio-1] channel 149
[AC-wlan-ap-ap1-radio-1] radio enable
# Bind the service template maca_imc to radio 1.
[AC-wlan-ap-ap1-radio-1] service-template maca_imc
[AC-wlan-ap-ap1-radio-1] quit
[AC-wlan-ap-ap1] quit
5. Configure a user profile:
# Create an AP group named macauth1, and add AP ap1 to the AP group.
[AC] wlan ap-group macauth1
[AC-wlan-ap-group-macauth1] ap ap1
[AC-wlan-ap-group-macauth1] quit
# Create a user profile named mac1, and specify AP group macauth1 as the permitted AP group for client access.
[AC] user-profile mac1
[AC-user-profile-mac1] wlan permit-ap-group macauth1
[AC-user-profile-mac1] quit
6. Configure the RADIUS server on IMC 7.0:
|
|
NOTE: In this example, the RADIUS server runs on IMC PLAT 7.2 and IMC EIA 7.2. |
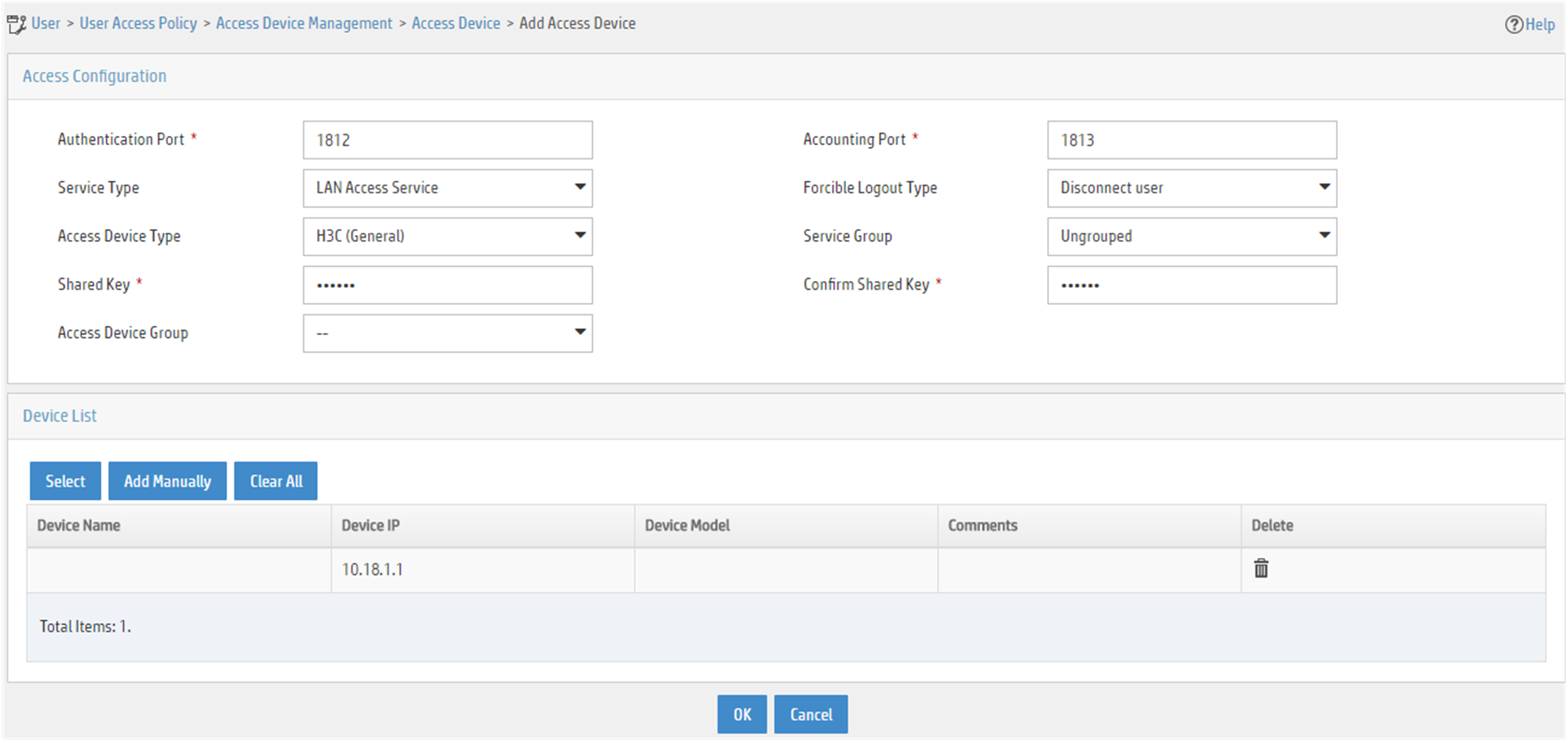
# Add the AC to IMC EIA as an access device.
a. Log in to IMC, click the User tab, and select User Access Policy > Access Device Management > Access Device from the navigation tree.
b. Click Add. Configure an access device as follows:
- Set the shared key for secure RADIUS communication to 12345678.
- Select the access device from the device list or manually add the access device (with the IP address 10.18.1.1).
- Leave the default settings for other parameters and click OK.
Figure 2 Adding the AC as an access device
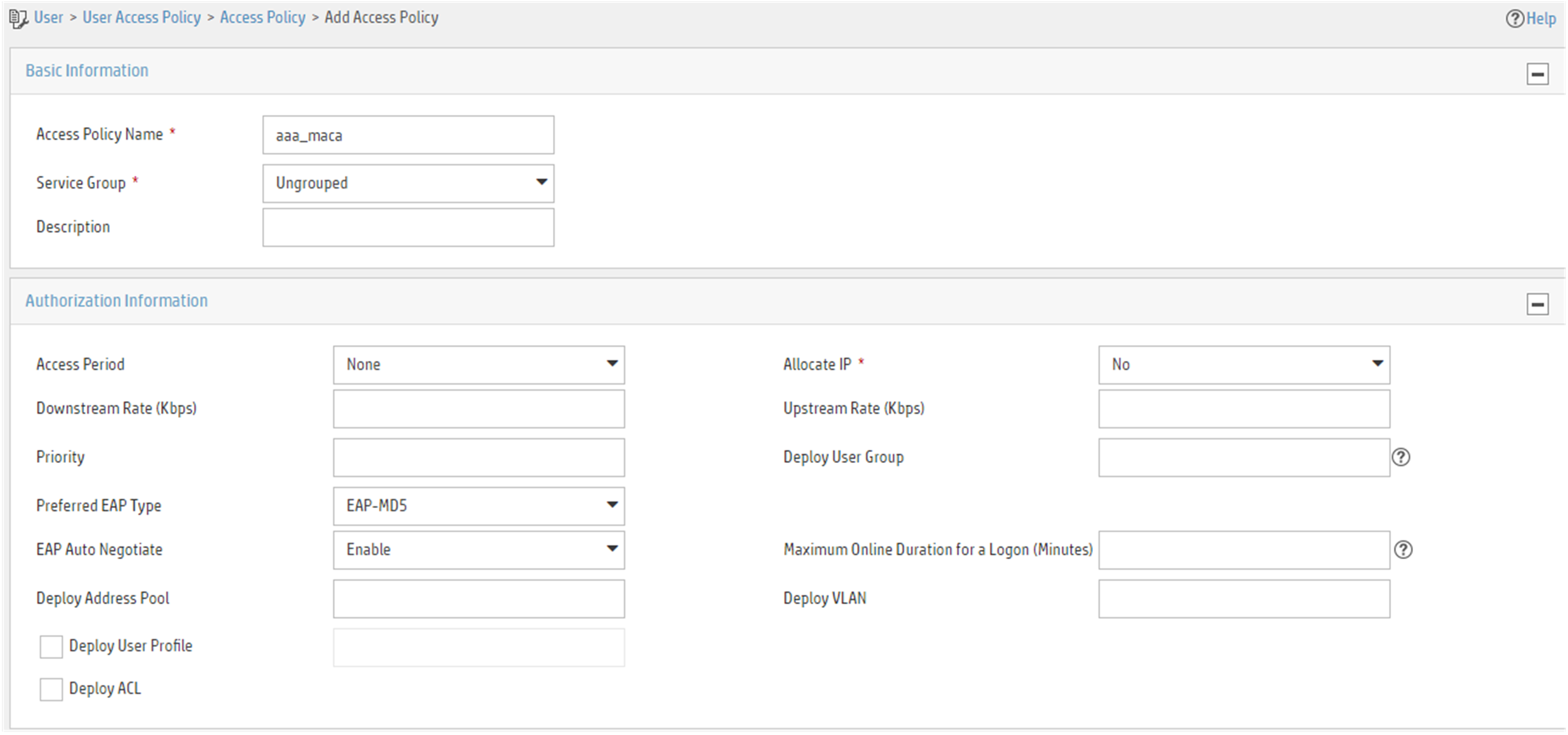
# Add an access policy.
a. Click the User tab, and select User Access Policy > Access Policy from the navigation tree. Then, click Add to configure an access policy.
b. Set the policy name to aaa_maca, and use default settings for other parameters.
Figure 3 Adding an access policy
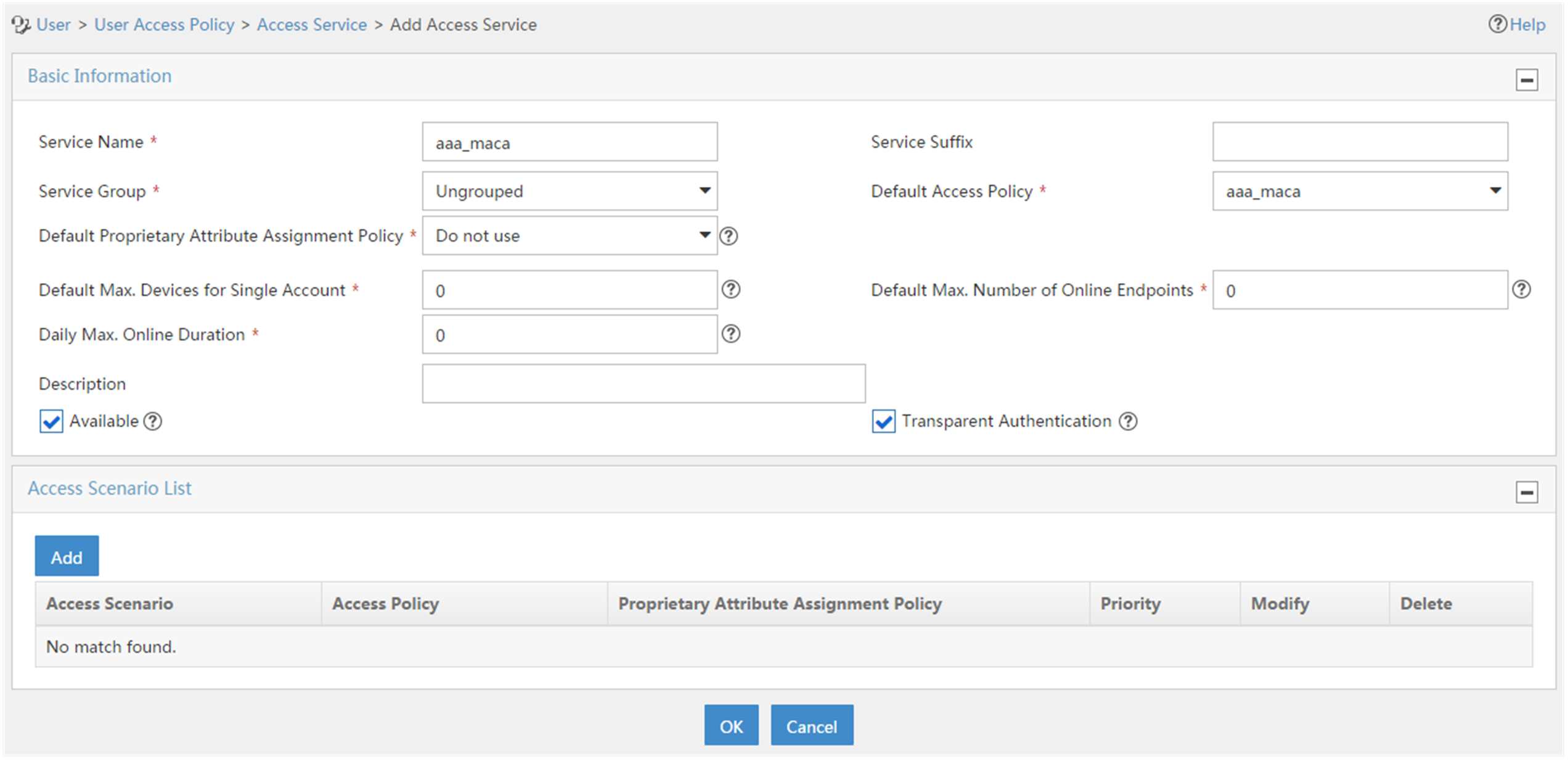
# Add an access service.
a. Click the User tab, and select User Access Policy > Access Service from the navigation tree.
Figure 4 Access Service page
a. Click Add to configure an access service. Set the policy name to aaa_maca, and use default settings for other parameters.
Figure 5 Adding an access service
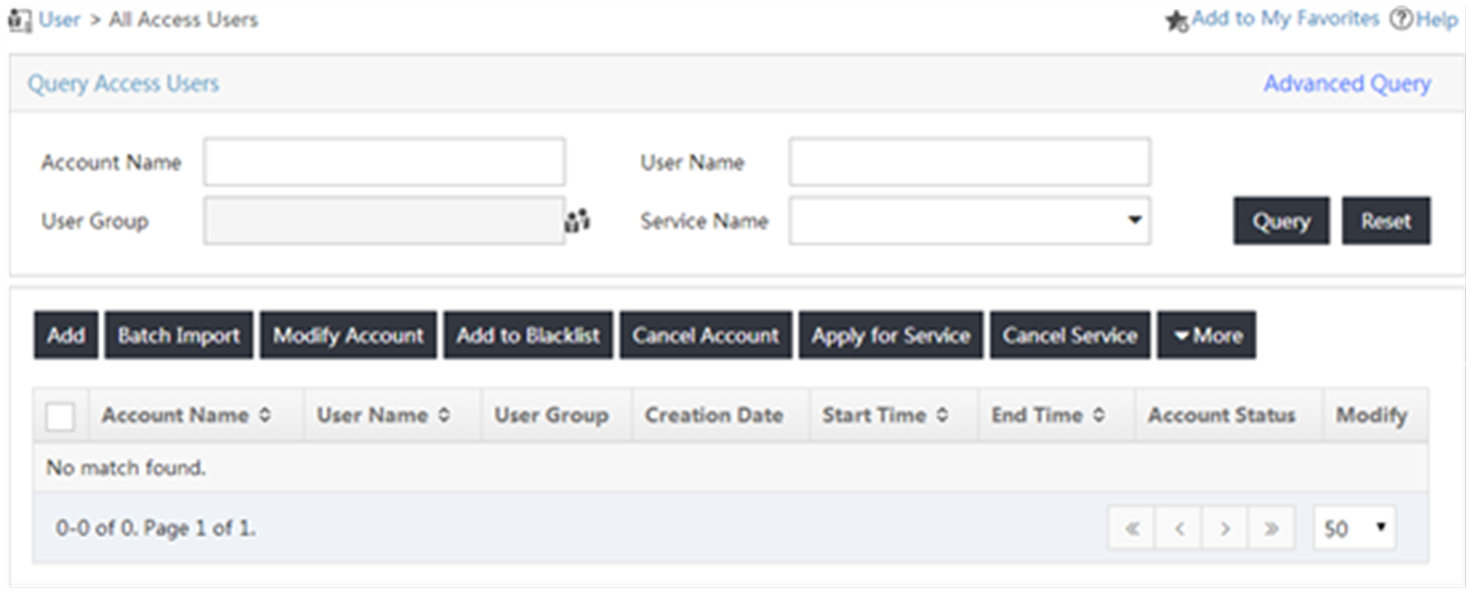
# Add an access user.
a. Click the User tab, and select Access User from the navigation tree.
Figure 6 Access User page
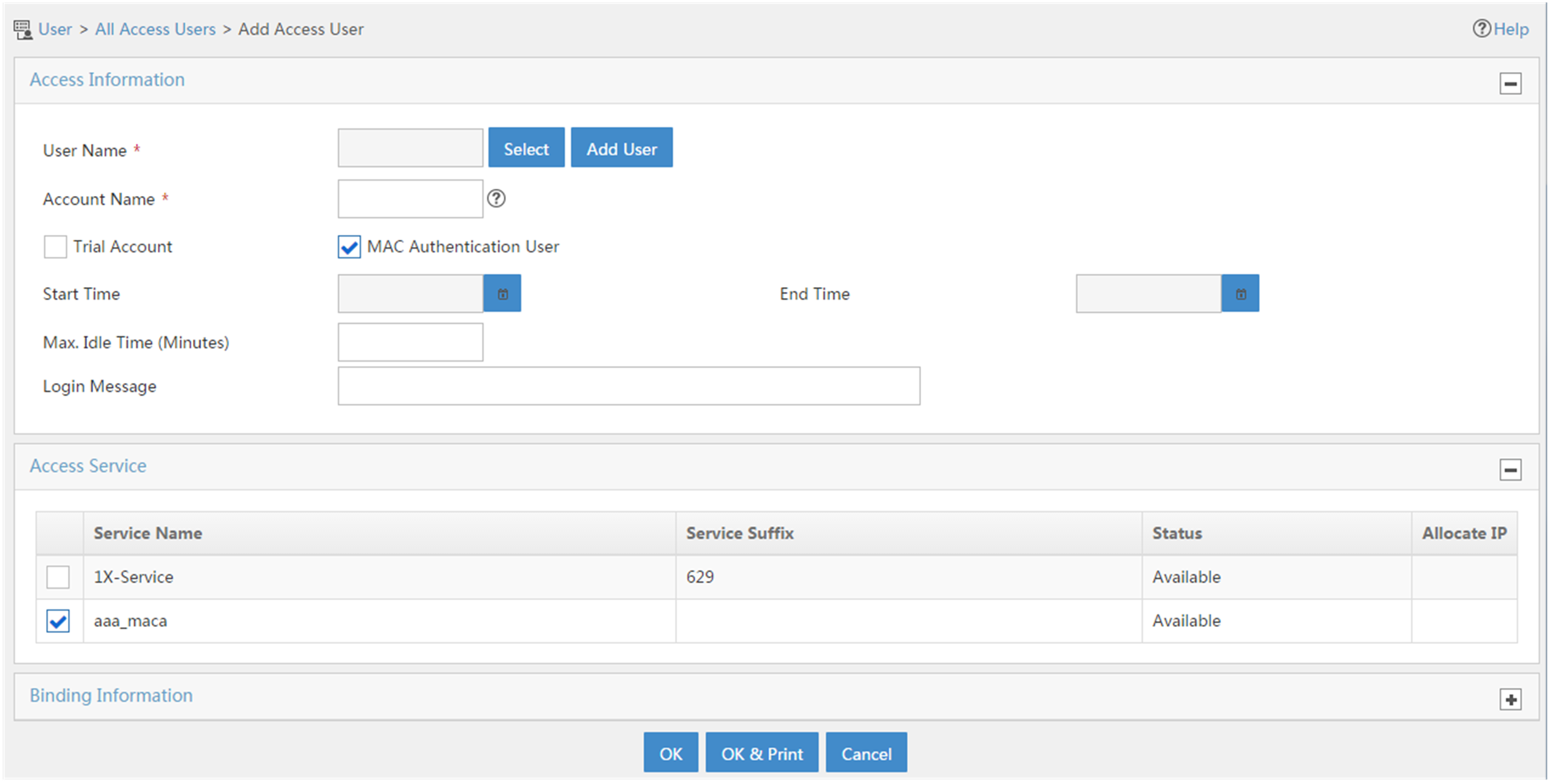
a. Click Add to configure an access user. Set the username and account name, and select MAC Authentication User.
Figure 7 Adding an access user