- Table of Contents
-
- 05-Layer 3—IP Routing Configuration Guide
- 00-Preface
- 01-Basic IP routing configuration
- 02-Static routing configuration
- 03-RIP configuration
- 04-OSPF configuration
- 05-IS-IS configuration
- 06-BGP configuration
- 07-Policy-based routing configuration
- 08-IPv6 static routing configuration
- 09-RIPng configuration
- 10-OSPFv3 configuration
- 11-IPv6 IS-IS configuration
- 12-IPv6 policy-based routing configuration
- 13-Routing policy configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 07-Policy-based routing configuration | 126.99 KB |
Restrictions and guidelines: PBR configuration
Setting match criteria for a node
Configuring actions for a node
Specifying a policy for local PBR
Specifying a policy for interface PBR
Displaying and maintaining PBR
Configuring PBR
Overview
Policy-based routing (PBR) uses user-defined policies to route packets. A policy can specify the next hop for packets that match specific criteria such as ACLs.
The device forwards received packets using the following process:
1. The device uses PBR to forward matching packets.
2. If the packets do not match the PBR policy or the PBR-based forwarding fails, the device uses the routing table, excluding the default route, to forward the packets.
3. If the routing table-based forwarding fails, the device uses the default route to forward packets.
PBR includes the following types:
· Local PBR—Guides the forwarding of locally generated packets, such as ICMP packets generated by using the ping command.
· Interface PBR—Guides the forwarding of packets received on an interface.
Policy
A policy includes match criteria and actions to be taken on the matching packets. A policy can have one or multiple nodes as follows:
· Each node is identified by a node number. A smaller node number has a higher priority.
· A node contains if-match and apply clauses. An if-match clause specifies a match criterion, and an apply clause specifies an action.
· A node has a match mode of permit or deny.
A policy compares packets with nodes in priority order. If a packet matches the criteria on a node, it is processed by the action on the node. Otherwise, it goes to the next node for a match. If the packet does not match the criteria on any node, it is forwarded according to the routing table.
if-match clause
PBR supports the if-match acl clause to set an ACL match criterion. On a node, you can configure only one if-match clause.
apply clause
PBR supports the apply next-hop clause to set next hops.
Relationship between the match mode and clauses on the node
|
Does a packet match all the if-match clauses on the node? |
Match mode |
|
|
Permit |
Deny |
|
|
Yes. |
· If the node is configured with apply clauses, PBR executes the apply clauses on the node. If the PBR-based forwarding succeeds, PBR does not compare the packet with the next node. · If the node is configured with no apply clauses, the packet is forwarded according to the routing table. |
The packet is forwarded according to the routing table. |
|
No. |
PBR compares the packet with the next node. |
PBR compares the packet with the next node. |
A node that has no if-match clauses matches any packet.
PBR and Track
PBR can work with the Track feature to dynamically adapt the availability status of an apply clause to the link status of a tracked object. The tracked object can be a next hop.
· When the track entry associated with an object changes to Negative, the apply clause is invalid.
· When the track entry changes to Positive or NotReady, the apply clause is valid.
For more information about Track-PBR collaboration, see High Availability Configuration Guide.
Restrictions and guidelines: PBR configuration
PBR configuration task list
|
Tasks at a glance |
|
(Required.) Configuring a policy: |
|
(Required.) Specifying a policy for PBR |
Configuring a policy
Creating a node
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a node for a policy, and enter its view. |
policy-based-route policy-name [ deny | permit ] node node-number |
By default, no policy nodes exist. |
Setting match criteria for a node
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter policy node view. |
policy-based-route policy-name [ deny | permit ] node node-number |
N/A |
|
3. Set an ACL match criterion. |
if-match acl { acl-number | name acl-name } |
By default, no ACL match criterion is set. The ACL match criterion cannot match Layer 2 information. |
|
|
NOTE: If an ACL match criterion is defined, packets are compared with the ACL rule. The permit or deny action and the time range of the specified ACL are ignored. If the specified ACL does not exist, no packet is matched. |
Configuring actions for a node
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter policy node view. |
policy-based-route policy-name [ deny | permit ] node node-number |
N/A |
|
3. Set next hops. |
apply next-hop { ip-address [ direct ] [ track track-entry-number ] }&<1-2> |
By default, no next hop is specified. You can specify multiple next hops for backup in one command line or by executing this command multiple times. |
|
|
NOTE: PBR periodically looks up the FIB table to determine the availability of a next hop specified in a PBR policy. If a next hop route change occurs, PBR might not update the route immediately. This results in a temporarily communication interruption. |
Specifying a policy for PBR
Specifying a policy for local PBR
Local PBR might affect local services such as ping and Telnet. When you use local PBR, make sure you fully understand its impact on local services of the device.
You can specify only one policy for local PBR and must make sure the specified policy already exists.
Before you apply a new policy, you must first remove the current policy.
To specify a policy for local PBR:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify a policy for local PBR. |
ip local policy-based-route policy-name |
By default, local PBR is not enabled. |
Specifying a policy for interface PBR
You can specify only one policy for interface PBR and must make sure the specified policy already exists.
Before you can apply a new policy to an interface, you must first remove the current policy from the interface.
You can apply a policy to multiple interfaces.
To specify a policy for interface PBR on an interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Specify a policy for interface PBR. |
ip policy-based-route policy-name |
By default, no interface policy is applied to an interface. |
Displaying and maintaining PBR
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display PBR policy information. |
display ip policy-based-route [ policy policy-name ] |
|
Display PBR configuration. |
display ip policy-based-route setup |
|
Display local PBR configuration and statistics. |
display ip policy-based-route local [ slot slot-number ] |
|
Display interface PBR configuration and statistics. |
display ip policy-based-route interface interface-type interface-number [ slot slot-number ] |
|
Clear PBR statistics. |
reset ip policy-based-route statistics [ policy policy-name ] |
PBR configuration examples
Packet type-based local PBR configuration example
Network requirements
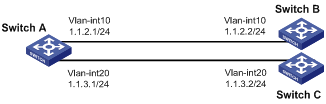
As shown in Figure 1, Switch B and Switch C cannot reach each other.
Configure PBR on Switch A to forward all TCP packets to the next hop 1.1.2.2 (Switch B).
Configuration procedure
1. Configure Switch A:
# Create VLAN 10 and VLAN 20.
<SwitchA> system-view
[SwitchA] vlan 10
[SwitchA-vlan10] quit
[SwitchA] vlan 20
[SwitchA-vlan20] quit
# Configure the IP addresses of VLAN-interface 10 and VLAN-interface 20.
[SwitchA] interface vlan-interface 10
[SwitchA-Vlan-interface10] ip address 1.1.2.1 24
[SwitchA-Vlan-interface10] quit
[SwitchA] interface vlan-interface 20
[SwitchA-Vlan-interface20] ip address 1.1.3.1 24
[SwitchA-Vlan-interface20] quit
# Configure ACL 3101 to match TCP packets.
[SwitchA] acl advanced 3101
[SwitchA-acl-ipv4-adv-3101] rule permit tcp
[SwitchA-acl-ipv4-adv-3101] quit
# Configure Node 5 for the policy aaa to forward TCP packets to next hop 1.1.2.2.
[SwitchA] policy-based-route aaa permit node 5
[SwitchA-pbr-aaa-5] if-match acl 3101
[SwitchA-pbr-aaa-5] apply next-hop 1.1.2.2
[SwitchA-pbr-aaa-5] quit
# Configure local PBR by applying the policy aaa to Switch A.
[SwitchA] ip local policy-based-route aaa
2. Configure Switch B:
# Create VLAN 10.
<SwitchB> system-view
[SwitchB] vlan 10
[SwitchB-vlan10] quit
# Configure the IP address of VLAN-interface 10.
[SwitchB] interface vlan-interface 10
[SwitchB-Vlan-interface10] ip address 1.1.2.2 24
3. Configure Switch C:
# Create VLAN 20.
<SwitchC> system-view
[SwitchC] vlan 20
[SwitchC-vlan20] quit
# Configure the IP address of VLAN-interface 20.
[SwitchC] interface vlan-interface 20
[SwitchC-Vlan-interface20] ip address 1.1.3.2 24
Verifying the configuration
# Telnet to Switch B on Switch A. The operation succeeds. (Details not shown.)
# Telnet to Switch C on Switch A. The operation fails. (Details not shown.)
# Ping Switch C from Switch A. The operation succeeds. (Details not shown.)
Telnet uses TCP, and ping uses ICMP. The results show the following:
· All TCP packets sent from Switch A are forwarded to the next hop 1.1.2.2.
· Other packets are forwarded through VLAN-interface 20.
· The local PBR configuration is effective.
Packet type-based interface PBR configuration example
Network requirements
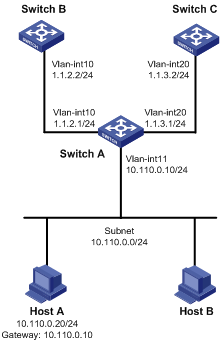
As shown in Figure 2, Switch B and Switch C cannot reach each other.
Configure PBR on Switch A to forward all TCP packets received on VLAN-interface 11 to the next hop 1.1.2.2 (Switch B).
Configuration procedure
1. Make sure Switch B and Switch C can reach Host A. (Details not shown.)
2. Configure Switch A:
# Create VLAN 10 and VLAN 20.
<SwitchA> system-view
[SwitchA] vlan 10
[SwitchA-vlan10] quit
[SwitchA] vlan 20
[SwitchA-vlan20] quit
# Configure the IP addresses of VLAN-interface 10 and VLAN-interface 20.
[SwitchA] interface vlan-interface 10
[SwitchA-Vlan-interface10] ip address 1.1.2.1 24
[SwitchA-Vlan-interface10] quit
[SwitchA] interface vlan-interface 20
[SwitchA-Vlan-interface20] ip address 1.1.3.1 24
[SwitchA-Vlan-interface20] quit
# Configure ACL 3101 to match TCP packets.
[SwitchA] acl advanced 3101
[SwitchA-acl-ipv4-adv-3101] rule permit tcp
[SwitchA-acl-ipv4-adv-3101] quit
# Configure Node 5 for the policy aaa to forward TCP packets to next hop 1.1.2.2.
[SwitchA] policy-based-route aaa permit node 5
[SwitchA-pbr-aaa-5] if-match acl 3101
[SwitchA-pbr-aaa-5] apply next-hop 1.1.2.2
[SwitchA-pbr-aaa-5] quit
# Configure interface PBR by applying the policy aaa to VLAN-interface 11.
[SwitchA] interface vlan-interface 11
[SwitchA-Vlan-interface11] ip address 10.110.0.10 24
[SwitchA-Vlan-interface11] ip policy-based-route aaa
[SwitchA-Vlan-interface11] quit
Verifying the configuration
# On Host A, Telnet to Switch B that is directly connected to Switch A. The operation succeeds. (Details not shown.)
# On Host A, Telnet to Switch C that is directly connected to Switch A. The operation fails. (Details not shown.)
# Ping Switch C from Host A. The operation succeeds. (Details not shown.)
Telnet uses TCP, and ping uses ICMP. The results show the following:
· All TCP packets arriving on VLAN-interface 11 of Switch A are forwarded to next hop 1.1.2.2.
· Other packets are forwarded through VLAN-interface 20.
· The interface PBR configuration is effective.

