- Table of Contents
-
- 12-Security Configuration Guide
- 00-Preface
- 01-MAC authentication configuration
- 02-Password control configuration
- 03-Keychain configuration
- 04-Public key management
- 05-PKI configuration
- 06-IPsec configuration
- 07-SSH configuration
- 08-SSL configuration
- 09-Session management
- 10-Object group configuration
- 11-Attack detection and prevention configuration
- 12-TCP and ICMP attack prevention configuration
- 13-IP source guard configuration
- 14-ARP attack protection configuration
- 15-ND attack defense configuration
- 16-uRPF configuration
- 17-Crypto engine configuration
- 18-DAE proxy configuration
- 19-802.1X configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-MAC authentication configuration | 186.33 KB |
Contents
Configuring MAC authentication
Restrictions: Hardware compatibility with MAC authentication
Restrictions and guidelines: MAC authentication configuration
MAC authentication tasks at a glance
Prerequisites for MAC authentication
Specifying a MAC authentication domain
Configuring the user account format
Configuring MAC authentication timers
Enabling MAC authentication offline detection
Setting the maximum number of concurrent MAC authentication users on a port
Enabling MAC authentication multi-VLAN mode on a port
Configuring the keep-online feature
Display and maintenance commands for MAC authentication
MAC authentication configuration examples
Example: Configuring local MAC authentication
Example: Configuring RADIUS-based MAC authentication
Example: Configuring ACL assignment for MAC authentication
Configuring MAC authentication
About MAC authentication
MAC authentication controls network access by authenticating source MAC addresses on a port. The feature does not require client software, and users do not have to enter a username and password for network access. The device initiates a MAC authentication process when it detects an unknown source MAC address on a MAC authentication-enabled port. If the MAC address passes authentication, the user can access authorized network resources. If the authentication fails, the device marks the MAC address as a silent MAC address, drops the packet, and starts a quiet timer. The device drops all subsequent packets from the MAC address within the quiet time. The quiet mechanism avoids repeated authentication during a short time.
User account policies
MAC authentication supports the following user account policies:
· One MAC-based user account for each user. As shown in Figure 1, the access device uses the source MAC addresses in packets as the usernames and passwords of users for MAC authentication. This policy is suitable for an insecure environment.
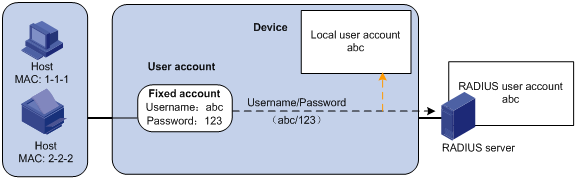
· One shared user account for all users. You specify one username and password, which are not necessarily a MAC address, for all MAC authentication users on the access device. This policy is suitable for a secure environment. See Figure 2.
Figure 1 MAC-based user account policy
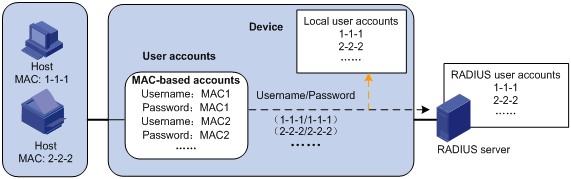
Figure 2 Shared user account policy
Authentication methods
You can perform MAC authentication on the access device (local authentication) or through a RADIUS server.
For more information about configuring local authentication and RADIUS authentication, see AAA in BRAS Services Configuration Guide.
Local authentication
If MAC-based accounts are used, the access device uses the source MAC address of the packet as the username and password to search the local account database for a match.
If a shared account is used, the access device uses the shared account username and password to search the local account database for a match.
RADIUS authentication
If MAC-based accounts are used, the access device sends the source MAC address of the packet as the username and password to the RADIUS server for authentication.
If a shared account is used, the access device sends the shared account username and password to the RADIUS server for authentication.
VLAN assignment
The device uses the authorization VLAN to control the access of a MAC authentication user to authorized network resources.
The device supports the following VLAN authorization methods:
· Remote VLAN authorization—The authorization VLAN information of a MAC authentication user is assigned by a remote server. The device can resolve server-assigned VLANs in the form of VLAN ID or VLAN name.
The port through which the user accesses the device is assigned to the authorization VLAN as a tagged or untagged member.
· Local VLAN authorization—The authorization VLAN of a MAC authentication user is specified in local user view or user group view in the form of VLAN ID on the device.
The port through which the user accesses the device is assigned to the VLAN as an untagged member. Tagged VLAN assignment is not supported.
For more information about local authorization VLAN configuration, see AAA in BRAS Services Configuration Guide.
Table 1 describes the way the network access device handles authorization VLANs for MAC authenticated users.
|
Port link type |
VLAN manipulation |
|
· Access port · Trunk port · Hybrid port |
· The device assigns the port to the first authenticated user's authorization VLAN and sets the VLAN as the PVID if that authorization VLAN has the untagged attribute. · If the authorization VLAN has the tagged attribute, the device assigns the port to the authorization VLAN without changing its PVID. NOTE: The tagged attribute is supported only on trunk and hybrid ports. |
|
|
IMPORTANT: · If the users are attached to a port whose link type is access, make sure the authorization VLAN assigned by the server has the untagged attribute. VLAN assignment will fail if the server issues a VLAN that has the tagged attribute. · When you assign VLANs to users attached to a trunk port or a hybrid port, make sure there is only one untagged VLAN. If a different untagged VLAN is assigned to a subsequent user, the user cannot pass authentication. · As a best practice to enhance network security, do not use the port hybrid vlan command to assign a hybrid port to an authorization VLAN as a tagged member. |
ACL assignment
You can specify an authorization ACL in the user account for a MAC authentication user on the authentication server to control the user's access to network resources. After the user passes MAC authentication, the authentication server assigns the authorization ACL to the user access port. Then, the port permits or drops the matching traffic for the user depending on the rules configured in the ACL.
The authentication server can be the local access device or a RADIUS server. In either case, the server only specifies the ACL number. You must create the ACL and configure its rules on the access device.
To change the access control criteria for the user, you can use one of the following methods:
· Modify ACL rules on the access device.
· Specify another authorization ACL on the authentication server.
The supported authorization ACLs include the following types:
· Basic ACLs, which are numbered in the range of 2000 to 2999.
· Advanced ACLs, which are numbered in the range of 3000 to 3999.
· Layer 2 ACLs, which are numbered in the range of 4000 to 4999.
For an authorization ACL to take effect, make sure the ACL exists with rules and none of the rules contains the counting, established, fragment, source-mac, or logging keyword.
For more information about ACLs, see ACL and QoS Configuration Guide.
Periodic MAC reauthentication
Periodic MAC reauthentication tracks the connection status of online users, and updates the authorization attributes assigned by the RADIUS server. The attributes include the ACL and VLAN.
The device reauthenticates an online MAC authentication user periodically only after it receives the termination action Radius-request from the authentication server for this user. The Session-Timeout attribute (session timeout period) assigned by the server is the reauthentication interval. To display the server-assigned Session-Timeout and Termination-Action attributes, use the display mac-authentication connection command. Support for the server configuration and assignment of Session-Timeout and Termination-Action attributes depends on the server model.
Restrictions: Hardware compatibility with MAC authentication
MAC authentication is supported only on CSPC cards (except CSPC-GE16XP4L-E, CSPC-GE24L-E, and CSPC-GP24GE8XP2L-E) and the CMPE-1104 card.
Restrictions and guidelines: MAC authentication configuration
MAC authentication is mutually exclusive with link aggregation groups or service loopback groups.
· You cannot enable MAC authentication on a port already in a link aggregation group or a service loopback group.
· You cannot add a MAC authentication-enabled port to a link aggregation group or a service loopback group.
If the MAC address that has failed authentication is a static MAC address or a MAC address that has passed any security authentication, the device does not mark the MAC address as a silent address.
MAC authentication tasks at a glance
To configure MAC authentication, perform the following tasks:
1. Enabling MAC authentication
2. Configure basic MAC authentication features
¡ Specifying a MAC authentication domain
¡ Configuring the user account format
¡ (Optional.) Configuring MAC authentication timers
3. (Optional.) Configuring other MAC authentication features
¡ Enabling MAC authentication offline detection
¡ Setting the maximum number of concurrent MAC authentication users on a port
¡ Enabling MAC authentication multi-VLAN mode on a port
Perform this task to not reauthenticate online users when VLAN changes occur on a port.
¡ Configuring the keep-online feature
Prerequisites for MAC authentication
Before you configure MAC authentication, configure an ISP domain and specify an AAA method. For more information, see AAA in BRAS Services Configuration Guide.
· For local authentication, you must also create local user accounts (including usernames and passwords) and specify the lan-access service for local users.
· For RADIUS authentication, make sure the device and the RADIUS server can reach each other and create user accounts on the RADIUS server. If you are using MAC-based accounts, make sure the username and password for each account are the same as the MAC address of each MAC authentication user.
Enabling MAC authentication
Restrictions and guidelines
For MAC authentication to take effect on a port, you must enable this feature globally and on the port.
Procedure
1. Enter system view.
system-view
2. Enable MAC authentication globally.
mac-authentication
By default, MAC authentication is disabled globally.
3. Enter interface view.
interface interface-type interface-number
4. Enable MAC authentication on the port.
mac-authentication
By default, MAC authentication is disabled on a port.
Specifying a MAC authentication domain
About authentication domains for MAC authentication
By default, MAC authentication users are in the system default authentication domain. To implement different access policies for users, you can use one of the following methods to specify authentication domains for MAC authentication users:
· Specify a global authentication domain in system view. This domain setting applies to all ports enabled with MAC authentication.
· Specify an authentication domain for an individual port in interface view.
MAC authentication chooses an authentication domain for users on a port in this order: the port-specific domain, the global domain, and the default domain. For more information about authentication domains, see AAA in BRAS Services Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Specify an authentication domain for MAC authentication users.
¡ In system view:
mac-authentication domain domain-name
¡ In interface view:
interface interface-type interface-number
mac-authentication domain domain-name
By default, the system default authentication domain is used for MAC authentication users.
Configuring the user account format
1. Enter system view.
system-view
2. Configure the MAC authentication user account format.
¡ Use one MAC-based user account for each user.
mac-authentication user-name-format mac-address [ { with-hyphen | without-hyphen } [ lowercase | uppercase ] ]
¡ Use one shared user account for all users.
mac-authentication user-name-format fixed [ account name ] [ password { cipher | simple } string ]
By default, the device uses the MAC address of a user as the username and password for MAC authentication. The MAC address is in hexadecimal notation without hyphens, and letters are in lower case.
Configuring MAC authentication timers
About MAC authentication timers
MAC authentication uses the following timers:
· Offline detect timer—Sets the interval that the device must wait for traffic from a user before the device determines that the user is idle. If the device has not received traffic from a user before the timer expires, the device logs off that user and requests the accounting server to stop accounting for the user. This timer takes effect only when the MAC authentication offline detection feature is enabled.
· Quiet timer—Sets the interval that the device must wait before the device can perform MAC authentication for a user that has failed MAC authentication. All packets from the MAC address are dropped during the quiet time. This quiet mechanism prevents repeated authentication from affecting system performance.
· Server timeout timer—Sets the interval that the device waits for a response from a RADIUS server before the device determines that the RADIUS server is unavailable. If the timer expires during MAC authentication, the user cannot access the network.
Procedure
1. Enter system view.
system-view
2. Configure MAC authentication timers.
mac-authentication timer { offline-detect offline-detect-value | quiet quiet-value | server-timeout server-timeout-value }
By default, the offline detect timer is 300 seconds, the quiet timer is 60 seconds, and the server timeout timer is 100 seconds.
Enabling MAC authentication offline detection
About MAC authentication offline detection
This feature logs a user out of the device if the device does not receive any packets from that user within an offline detect interval. In addition, the device requests the accounting server to stop accounting for that user. For more information about the offline detect timer, see "Configuring MAC authentication timers."
Disabling this feature disables the device from inspecting the online user status.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable MAC authentication offline detection.
mac-authentication offline-detect enable
By default, MAC authentication offline detection is enabled on a port.
Setting the maximum number of concurrent MAC authentication users on a port
About limiting the number of concurrent MAC authentication users on a port
Perform this task to prevent the system resources from being overused.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Set the maximum number of concurrent MAC authentication users on the port.
mac-authentication max-user max-number
The default setting is 4294967295.
Enabling MAC authentication multi-VLAN mode on a port
About the MAC authentication multi-VLAN mode
The MAC authentication multi-VLAN mode prevents an authenticated online user from service interruption caused by VLAN changes on a port. When the port receives a packet sourced from the user in a VLAN not matching the existing MAC-VLAN mapping, the device neither logs off the user nor reauthenticates the user. The device creates a new MAC-VLAN mapping for the user, and traffic transmission is not interrupted. The original MAC-VLAN mapping for the user remains on the device until it dynamically ages out. As a best practice, configure this feature on hybrid or trunk ports.
This feature improves transmission of data that is vulnerable to delay and interference. It is typically applicable to IP phone users.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable MAC authentication multi-VLAN mode.
mac-authentication host-mode multi-vlan
By default, this feature is disabled on a port. When the port receives a packet sourced from an authenticated user in a VLAN not matching the existing MAC-VLAN mapping, the device logs off and reauthenticates the user.
Configuring the keep-online feature
About the keep-online feature
By default, the device logs off online MAC authentication users if no server is reachable for MAC reauthentication. The keep-online feature keeps authenticated MAC authentication users online when no server is reachable for MAC reauthentication.
In a fast-recovery network, you can use the keep-online feature to prevent MAC authentication users from coming online and going offline frequently.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable the keep-online feature for authenticated MAC authentication users on the port.
mac-authentication re-authenticate server-unreachable keep-online
By default, the keep-online feature is disabled.
This command takes effect only when the authentication server assigns reauthentication attributes to the device.
Display and maintenance commands for MAC authentication
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display MAC authentication information. |
display mac-authentication [ interface interface-type interface-number ] |
|
(In standalone mode.) Display MAC authentication connections. |
display mac-authentication connection [ interface interface-type interface-number | slot slot-number | user-mac mac-address | user-name user-name ] |
|
(In IRF mode.) Display MAC authentication connections. |
display mac-authentication connection [ chassis chassis-number slot slot-number | interface interface-type interface-number | user-mac mac-address | user-name user-name ] |
|
Clear MAC authentication statistics. |
reset mac-authentication statistics [ interface interface-type interface-number ] |
MAC authentication configuration examples
Example: Configuring local MAC authentication
Network configuration
As shown in Figure 3, the device performs local MAC authentication on GigabitEthernet 3/1/1 to control Internet access of users.
Configure the device to meet the following requirements:
· Detect whether a user has gone offline every 180 seconds.
· Deny a user for 180 seconds if the user fails MAC authentication.
· Authenticate all users in ISP domain bbb.
· Use the MAC address of each user as the username and password for authentication. The MAC addresses are in hexadecimal notation with hyphens, and letters are in lower case.
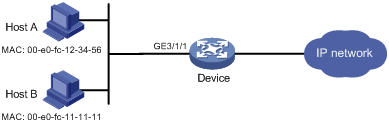
Procedure
# Add a network access local user. In this example, configure both the username and password as Host A's MAC address 00-e0-fc-12-34-56.
<Device> system-view
[Device] local-user 00-e0-fc-12-34-56 class network
[Device-luser-network-00-e0-fc-12-34-56] password simple 00-e0-fc-12-34-56
# Specify the LAN access service for the user.
[Device-luser-network-00-e0-fc-12-34-56] service-type lan-access
[Device-luser-network-00-e0-fc-12-34-56] quit
# Configure ISP domain bbb to perform local authentication for LAN users.
[Device] domain name bbb
[Device-isp-bbb] authentication lan-access local
[Device-isp-bbb] quit
# Enable MAC authentication on GigabitEthernet 3/1/1.
[Device] interface gigabitethernet 3/1/1
[Device-GigabitEthernet3/1/1] mac-authentication
[Device-GigabitEthernet3/1/1] quit
# Specify ISP domain bbb as the MAC authentication domain.
[Device] mac-authentication domain bbb
# Configure MAC authentication timers.
[Device] mac-authentication timer offline-detect 180
[Device] mac-authentication timer quiet 180
# Configure MAC authentication to use MAC-based accounts. Each MAC address is in hexadecimal notation with hyphens, and letters are in lower case.
[Device] mac-authentication user-name-format mac-address with-hyphen lowercase
# Enable MAC authentication globally.
[Device] mac-authentication
Verifying the configuration
# Display MAC authentication settings and statistics to verify your configuration.
[Device] display mac-authentication
Global MAC authentication parameters:
MAC authentication : Enabled
User name format : MAC address in lowercase(xx-xx-xx-xx-xx-xx)
Username : mac
Password : Not configured
Offline detect period : 180 s
Quiet period : 180 s
Server timeout : 100 s
Authentication domain : bbb
Online MAC-auth wired users : 1
Silent MAC users:
MAC address VLAN ID From port Port index
00e0-fc11-1111 8 GE3/1/1 1
GigabitEthernet3/1/1 is link-up
MAC authentication : Enabled
Authentication domain : Not configured
Re-auth server-unreachable : Logoff
Guest VLAN : Not configured
Guest VLAN auth-period : 30 s
Critical VLAN : Not configured
Critical voice VLAN : Disabled
Host mode : Single VLAN
Offline detection : Enabled
Max online users : 4294967295
Authentication attempts : successful 1, failed 0
Current online users : 1
MAC address Auth state
00e0-fc12-3456 Authenticated
The output shows that Host A has passed MAC authentication and has come online. Host B failed MAC authentication and its MAC address is marked as a silent MAC address.
Example: Configuring RADIUS-based MAC authentication
Network configuration
As shown in Figure 4, the device uses RADIUS servers to perform authentication, authorization, and accounting for users.
To control user access to the Internet by MAC authentication, perform the following tasks:
· Enable MAC authentication globally and on GigabitEthernet 3/1/1.
· Configure the device to detect whether a user has gone offline every 180 seconds.
· Configure the device to deny a user for 180 seconds if the user fails MAC authentication.
· Configure all users to belong to ISP domain bbb.
· Use a shared user account for all users, with username aaa and password 123456.
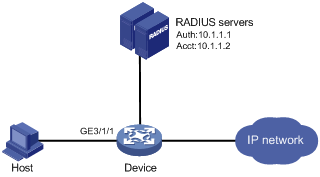
Procedure
Make sure the RADIUS servers and the access device can reach each other.
1. Configure the RADIUS servers to provide authentication, authorization, and accounting services. Create a shared account with username aaa and password 123456 for MAC authentication users. (Details not shown.)
2. Configure RADIUS-based MAC authentication on the device:
# Configure a RADIUS scheme.
<Device> system-view
[Device] radius scheme 2000
[Device-radius-2000] primary authentication 10.1.1.1 1812
[Device-radius-2000] primary accounting 10.1.1.2 1813
[Device-radius-2000] key authentication simple abc
[Device-radius-2000] key accounting simple abc
[Device-radius-2000] user-name-format without-domain
[Device-radius-2000] quit
# Apply the RADIUS scheme to ISP domain bbb for authentication, authorization, and accounting.
[Device] domain name bbb
[Device-isp-bbb] authentication default radius-scheme 2000
[Device-isp-bbb] authorization default radius-scheme 2000
[Device-isp-bbb] accounting default radius-scheme 2000
[Device-isp-bbb] quit
# Enable MAC authentication on GigabitEthernet 3/1/1.
[Device] interface gigabitethernet 3/1/1
[Device-GigabitEthernet3/1/1] mac-authentication
[Device-GigabitEthernet3/1/1] quit
# Specify the MAC authentication domain as ISP domain bbb.
[Device] mac-authentication domain bbb
# Set MAC authentication timers.
[Device] mac-authentication timer offline-detect 180
[Device] mac-authentication timer quiet 180
# Specify username aaa and password 123456 in plain text for the account shared by MAC authentication users.
[Device] mac-authentication user-name-format fixed account aaa password simple 123456
# Enable MAC authentication globally.
[Device] mac-authentication
Verifying the configuration
# Verify the MAC authentication configuration.
[Device] display mac-authentication
Global MAC authentication parameters:
MAC authentication : Enabled
Username format : Fixed account
Username : aaa
Password : ******
Offline detect period : 180 s
Quiet period : 180 s
Server timeout : 100 s
Authentication domain : bbb
Online MAC-auth wired users : 1
Silent MAC users:
MAC address VLAN ID From port Port index
GigabitEthernet3/1/1 is link-up
MAC authentication : Enabled
Authentication domain : Not configured
Re-auth server-unreachable : Logoff
Guest VLAN : Not configured
Guest VLAN auth-period : 30 s
Critical VLAN : Not configured
Critical voice VLAN : Disabled
Host mode : Single VLAN
Offline detection : Enabled
Max online users : 4294967295
Authentication attempts : successful 1, failed 0
Current online users : 1
MAC address Auth state
00e0-fc12-3456 Authenticated
Example: Configuring ACL assignment for MAC authentication
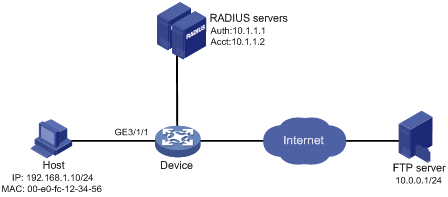
Network configuration
As shown in Figure 5, configure the device to meet the following requirements:
· Use RADIUS servers to perform authentication, authorization, and accounting for users.
· Perform MAC authentication on GigabitEthernet 3/1/1 to control Internet access.
· Use MAC-based user accounts for MAC authentication users. Each MAC address is in hexadecimal notation with hyphens, and letters are in lower case.
· Use an ACL to deny authenticated users to access the FTP server at 10.0.0.1.
Procedure
Make sure the RADIUS servers and the access device can reach each other.
1. Configure the RADIUS servers:
# Configure the RADIUS servers to provide authentication, authorization, and accounting services. (Details not shown.)
# Add a user account with 00-e0-fc-12-34-56 as both the username and password on each RADIUS server. (Details not shown.)
# Specify ACL 3000 as the authorization ACL for the user account. (Details not shown.)
2. Configure ACL 3000 to deny packets destined for 10.0.0.1 on the device.
<Device> system-view
[Device] acl advanced 3000
[Device-acl-ipv4-adv-3000] rule 0 deny ip destination 10.0.0.1 0
[Device-acl-ipv4-adv-3000] quit
3. Configure RADIUS-based MAC authentication on the device:
# Configure a RADIUS scheme.
[Device] radius scheme 2000
[Device-radius-2000] primary authentication 10.1.1.1 1812
[Device-radius-2000] primary accounting 10.1.1.2 1813
[Device-radius-2000] key authentication simple abc
[Device-radius-2000] key accounting simple abc
[Device-radius-2000] user-name-format without-domain
[Device-radius-2000] quit
# Apply the RADIUS scheme to an ISP domain for authentication, authorization, and accounting.
[Device] domain name bbb
[Device-isp-bbb] authentication default radius-scheme 2000
[Device-isp-bbb] authorization default radius-scheme 2000
[Device-isp-bbb] accounting default radius-scheme 2000
[Device-isp-bbb] quit
# Specify the ISP domain for MAC authentication.
[Device] mac-authentication domain bbb
# Configure the device to use MAC-based user accounts. Each MAC address is in hexadecimal notation with hyphens, and letters are in lower case.
[Device] mac-authentication user-name-format mac-address with-hyphen lowercase
# Enable MAC authentication on GigabitEthernet 3/1/1.
[Device] interface gigabitethernet 3/1/1
[Device-GigabitEthernet3/1/1] mac-authentication
[Device-GigabitEthernet3/1/1] quit
# Enable MAC authentication globally.
[Device] mac-authentication
Verifying the configuration
# Verify the MAC authentication configuration.
[Device] display mac-authentication
Global MAC authentication parameters:
MAC authentication : Enabled
Username format : MAC address in lowercase(xx-xx-xx-xx-xx-xx)
Username : mac
Password : Not configured
Offline detect period : 300 s
Quiet period : 60 s
Server timeout : 100 s
Authentication domain : bbb
Online MAC-auth wired users : 1
Silent MAC users:
MAC address VLAN ID From port Port index
GigabitEthernet3/1/1 is link-up
MAC authentication : Enabled
Authentication domain : Not configured
Re-auth server-unreachable : Logoff
Guest VLAN : Not configured
Guest VLAN auth-period : 30 s
Critical VLAN : Not configured
Critical voice VLAN : Disabled
Host mode : Single VLAN
Offline detection : Enabled
Max online users : 4294967295
Authentication attempts : successful 1, failed 0
Current online users : 1
MAC address Auth state
00e0-fc12-3456 Authenticated
# Verify that you cannot ping the FTP server from the host.
C:\>ping 10.0.0.1
Pinging 10.0.0.1 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 10.0.0.1:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
The output shows that ACL 3000 has been assigned to GigabitEthernet 3/1/1 to deny access to the FTP server.
