- Table of Contents
-
- 12-Security Configuration Guide
- 00-Preface
- 01-MAC authentication configuration
- 02-Password control configuration
- 03-Keychain configuration
- 04-Public key management
- 05-PKI configuration
- 06-IPsec configuration
- 07-SSH configuration
- 08-SSL configuration
- 09-Session management
- 10-Object group configuration
- 11-Attack detection and prevention configuration
- 12-TCP and ICMP attack prevention configuration
- 13-IP source guard configuration
- 14-ARP attack protection configuration
- 15-ND attack defense configuration
- 16-uRPF configuration
- 17-Crypto engine configuration
- 18-DAE proxy configuration
- 19-802.1X configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 15-ND attack defense configuration | 68.61 KB |
ND attack defense tasks at a glance
Configuring source MAC-based ND attack detection
About source MAC-based ND attack detection
Hardware and feature compatibility
Display and maintenance commands for source MAC-based ND attack detection
Configuring interface-based ND attack suppression
About interface-based ND attack suppression
Hardware and feature compatibility
Display and maintenance commands for interface-based ND attack suppression
Enabling source MAC consistency check for ND messages
Configuring ND attack defense
About ND attack defense
IPv6 Neighbor Discovery (ND) attack defense is able to identify forged ND messages to prevent ND attacks.
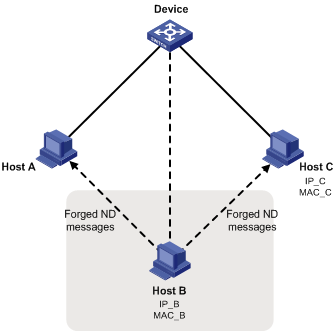
The IPv6 ND protocol does not provide any security mechanisms and is vulnerable to network attacks. As shown in Figure 1, an attacker can send the following forged ICMPv6 messages to perform ND attacks:
· Forged NS/NA/RS messages with an IPv6 address of a victim host. The gateway and other hosts update the ND entry for the victim with incorrect address information. As a result, all packets intended for the victim are sent to the attacking terminal.
· Forged RA messages with the IPv6 address of a victim gateway. As a result, all hosts attached to the victim gateway maintain incorrect IPv6 configuration parameters and ND entries.
ND attack defense tasks at a glance
All ND attack defense tasks are optional.
· Configuring source MAC-based ND attack detection
· Configuring interface-based ND attack suppression
· Enabling source MAC consistency check for ND messages
Configuring source MAC-based ND attack detection
About source MAC-based ND attack detection
Source MAC-based ND attack detection checks the number of ND messages delivered to the CPU. If the number of messages from the same MAC address within the check interval exceeds the threshold, the device generates an ND attack entry for the MAC address. The processing of the ND messages sent from the MAC address in this entry depends on the detection mode. With ND logging enabled (by using the ipv6 nd check log enable command), source MAC-based ND attack detection processes the messages as follows:
· Filter mode—Filters out subsequent ND messages sent from the MAC address, and generates log messages.
· Monitor mode—Only generates log messages.
During the ND attack defense period, the device monitors the number of dropped packets in an entry within the aging time:
· If the number of dropped packets is higher than or equal to a calculated value, the device resets the aging time for the entry when the entry ages out.
The calculated value = (aging time/check interval) × source MAC-based ND attack detection threshold
If the number of dropped packets is lower than calculated value, the system deletes the entry when the entry ages out and marks MAC address in the entry as a common MAC address.
Hardware and feature compatibility
The feature is available only on the CSPC-GE16XP4L-E, CSPC-GE24L-E, and CSPC-GP24GE8XP2L-E cards, CSPEX cards, and CEPC cards.
Restrictions and guidelines
When you change the detection mode from monitor to filter, the filter mode takes effect immediately. When you change the detection mode from filter to monitor, the device continues filtering messages that match existing attack entries.
You can exclude certain MAC addresses from source MAC-based ND attack detection on gateways and servers that might receive large numbers of ND messages. Source MAC-based ND attack detection does not drop ND messages sent from the excluded MAC addresses even if it detects attacks launched from these MAC addresses.
If attacks occur frequently in your network, set a short check interval so that source MAC-based ND attacks can be detected in a timely manner. If attacks seldom occur, you can set a long check interval.
Procedure
1. Enter system view.
system-view
2. Enable source MAC-based ND attack detection and set the detection mode.
ipv6 nd source-mac { filter | monitor }
By default, source MAC-based ND attack detection is disabled.
3. Set the check interval for source MAC-based ND attack detection.
ipv6 nd source-mac check-interval interval
By default, the check interval is 5 seconds for source MAC-based ND attack detection.
4. (Optional.) Set the threshold for source MAC-based ND attack detection.
ipv6 nd source-mac threshold threshold-value
The default setting is 30.
5. (Optional.) Set the aging time for source MAC-based ND attack detection entries .
ipv6 nd source-mac aging-time time
The default setting is 300 seconds (5 minutes).
6. (Optional.) Exclude MAC addresses from source MAC-based ND attack detection.
ipv6 nd source-mac exclude-mac mac-address&<1-10>
By default, no MAC addresses are excluded from source MAC-based ND attack detection.
7. (Optional.) Enable the ND logging feature.
ipv6 nd check log enable
By default, the ND logging feature is disabled.
Display and maintenance commands for source MAC-based ND attack detection
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display the configuration of source MAC-based ND attack detection. |
display ipv6 nd source-mac configuration |
|
(In IRF mode.) Display source MAC-based ND attack detection entries. |
display ipv6 nd source-mac interface interface-type interface-number [ chassis chassis-number slot slot-number ] [ verbose ] display ipv6 nd source-mac { mac mac-address | vlan vlan-id } chassis chassis-number slot slot-number [ verbose ] display ipv6 nd source-mac chassis chassis-number slot slot-number [ count | verbose ] |
|
(In standalone mode.) Display source MAC-based ND attack detection entries. |
display ipv6 nd source-mac interface interface-type interface-number [ slot slot-number ] [ verbose ] display ipv6 nd source-mac { mac mac-address | vlan vlan-id } slot slot-number [ verbose ] display ipv6 nd source-mac slot slot-number [ count | verbose ] |
|
(In IRF mode.) Display statistics for ND messages dropped by source MAC-based ND attack detection. |
display ipv6 nd source-mac statistics chassis chassis-number slot slot-number |
|
(In standalone mode.) Display statistics for ND messages dropped by source MAC-based ND attack detection. |
display ipv6 nd source-mac statistics slot slot-number |
|
(In IRF mode.) Delete source MAC-based ND attack detection entries. |
reset ipv6 nd source-mac [ interface interface-type interface-number | mac mac-address | vlan vlan-id ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Delete source MAC-based ND attack detection entries. |
reset ipv6 nd source-mac [ interface interface-type interface-number | mac mac-address | vlan vlan-id ] [ slot slot-number ] |
|
(In IRF mode.) Clear statistics for ND messages dropped by source MAC-based ND attack detection. |
reset ipv6 nd source-mac statistics [ interface interface-type interface-number | mac mac-address | vlan vlan-id ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Clear statistics for ND messages dropped by source MAC-based ND attack detection. |
reset ipv6 nd source-mac statistics [ interface interface-type interface-number | mac mac-address | vlan vlan-id ] [ slot slot-number ] |
Configuring interface-based ND attack suppression
About interface-based ND attack suppression
Use this feature to rate limit ND request on each Layer 3 interface to prevent ND spoofing attacks. This feature monitors the number of ND requests that each Layer 3 interface received within the check interval. If the number on an interface exceeds the threshold, the device creates an ND attack suppression entry for the interface.
During the suppression period, the maximum receiving rate for ND requests is 12800 bytes per second on the interface.
When the suppression time expires, the system examines the number of received ND messages on the interface within the suppression time:
· If the number of the received ND messages is higher than or equal to a calculated value, the device resets the suppression time for the entry and continues the ND suppression on the interface.
The calculated value = (suppression time/check interval) × suppression threshold
· If the number of the received ND messages is lower than the calculated value, the device deletes the suppression entry.
Hardware and feature compatibility
The interface-based ND attack suppression feature is available only on Layer 3 Ethernet interfaces and Layer 3 Ethernet subinterfaces of the CSPEX cards (except CSPEX-1204 and CSPEX-1104-E) and CEPC cards.
Restrictions and guidelines
As a best practice, enable this feature on the gateway.
Procedure
1. Enter system view.
system-view
2. Enable interface-based ND attack suppression.
ipv6 nd attack-suppression enable per-interface
By default, interface-based ND attack suppression is disabled.
3. Set the check interval for interface-based ND attack suppression.
ipv6 nd attack-suppression check-interval interval
By default, the check interval is 5 seconds for interface-based ND attack suppression.
4. Set the threshold for triggering ND attack suppression.
ipv6 nd attack-suppression threshold threshold-value
By default, the threshold for triggering ND attack suppression is 1000.
5. Set the interface-based ND attack suppression time.
ipv6 nd attack-suppression suppression-time time
By default, the interface-based ND attack suppression time is 300 seconds.
Display and maintenance commands for interface-based ND attack suppression
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display the configuration of interface-based ND attack suppression. |
display ipv6 nd attack-suppression configuration |
|
(In IRF mode.) Display interface-based ND attack suppression entries. |
display ipv6 nd attack-suppression per-interface chassis chassis-number slot slot-number [ count | verbose ] |
|
(In standalone mode.) Display interface-based ND attack suppression entries. |
display ipv6 nd attack-suppression per-interface slot slot-number [ count | verbose ] |
|
Display interface-based ND attack suppression entries on an interface. |
display ipv6 nd attack-suppression per-interface interface interface-type interface-number [ verbose ] |
|
(In IRF mode.) Delete interface-based ND attack suppression entries. |
reset ipv6 nd attack-suppression per-interface [ interface interface-type interface-number ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Delete interface-based ND attack suppression entries. |
reset ipv6 nd attack-suppression per-interface [ interface interface-type interface-number ] [ slot slot-number ] |
|
(In IRF mode.) Clear statistics for ND messages dropped by interface-based ND attack suppression. |
reset ipv6 nd attack-suppression per-interface statistics [ interface interface-type interface-number ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Clear statistics for ND messages dropped by interface-based ND attack suppression. |
reset ipv6 nd attack-suppression per-interface statistics [ interface interface-type interface-number ] [ slot slot-number ] |
Enabling source MAC consistency check for ND messages
About source MAC consistency check
The source MAC consistency check feature is typically configured on gateways to prevent ND attacks.
This feature checks the source MAC address and the source link-layer address for consistency for each arriving ND message.
· If the source MAC address and the source link-layer address are not the same, the device drops the packet.
· If the addresses are the same, the device continues learning ND entries.
The ND logging feature logs source MAC inconsistency events, and it sends the log messages to the information center. The information center can then output log messages from different source modules to different destinations. For more information about the information center, see Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enable source MAC consistency check for ND messages.
ipv6 nd mac-check enable
By default, source MAC consistency check is disabled for ND messages.
3. (Optional.) Enable the ND logging feature.
ipv6 nd check log enable
By default, the ND logging feature is disabled.
As a best practice, disable the ND logging feature to avoid excessive ND logs.
