- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-ACL configuration | 202.72 KB |
Contents
Configuring an IPv4 advanced ACL
Configuring an IPv6 advanced ACL
Configuring an Ethernet frame header ACL
Configuring a user-defined ACL
Configuring packet filtering with ACLs
Applying an ACL to filter packets globally
Applying an ACL to an interface for packet filtering
Setting the interval for generating and outputting packet filtering logs
Setting the packet filtering default action
Displaying and maintaining ACLs
Interface-based packet filtering configuration example
Configuration example of filtering TCP packets with ACK or RST flag set
Configuring ACLs
Overview
An access control list (ACL) is a set of rules (or permit or deny statements) for identifying traffic based on criteria such as source IP address, destination IP address, and port number.
ACLs are primarily used for packet filtering. "Configuring packet filtering with ACLs" provides an example. You can use ACLs in QoS, security, routing, and other feature modules for identifying traffic. The packet drop or forwarding decisions depend on the modules that use ACLs.
Applications on the switch
An ACL is implemented in hardware or software, depending on the module that uses it.
· If the module is implemented in hardware (for example, the packet filter or QoS module), the ACL is applied to hardware to process traffic.
· If the module is implemented in software (for example, the routing module or the login management module), the ACL is applied to software to process traffic.
The Telnet and SNMP features in the login management module denies packets that do not match any ACL. Some modules (QoS for example) ignore the permit or deny action in ACL rules and do not base their drop or forwarding decisions on the action set in ACL rules. See the specified module for information about ACL application.
ACL categories
|
Category |
ACL number |
IP version |
Match criteria |
|
Basic ACLs |
2000 to 2999 |
IPv4 |
Source IPv4 address. |
|
IPv6 |
Source IPv6 address. |
||
|
Advanced ACLs |
3000 to 3999 |
IPv4 |
Source IPv4 address, destination IPv4 address, packet priority, protocol number, and other Layer 3 and Layer 4 header fields. |
|
IPv6 |
Source IPv6 address, destination IPv6 address, packet priority, protocol number, and other Layer 3 and Layer 4 header fields. |
||
|
Ethernet frame header ACLs |
4000 to 4999 |
IPv4 and IPv6 |
Layer 2 header fields, such as source and destination MAC addresses, 802.1p priority, and link layer protocol type. |
|
User-defined ACLs |
5000 to 5999 |
IPv4 |
User specified matching patterns in protocol headers. |
Numbering and naming ACLs
Each ACL category has a unique range of ACL numbers. When creating an ACL, you must assign it a number. In addition, you can assign the ACL a name for ease of identification. After creating an ACL with a name, you cannot rename it or delete its name.
For an IPv4 basic or advanced ACLs, its ACL number and name must be unique in IPv4. For an IPv6 basic or advanced ACL, its ACL number and name must be unique in IPv6.
Match order
The rules in an ACL are sorted in a specific order. When a packet matches a rule, the device stops the match process and performs the action defined in the rule. If an ACL contains overlapping or conflicting rules, the matching result and action to take depend on the rule order.
The following ACL match orders are available:
· config—Sorts ACL rules in ascending order of rule ID. A rule with a lower ID is matched before a rule with a higher ID. If you use this method, check the rules and their order carefully.
|
|
NOTE: The match order of user-defined ACLs can only be config. |
· auto—Sorts ACL rules in depth-first order. Depth-first ordering makes sure any subset of a rule is always matched before the rule. Table 1 lists the sequence of tie breakers that depth-first ordering uses to sort rules for each type of ACL.
Table 1 Sort ACL rules in depth-first order
|
ACL category |
Sequence of tie breakers |
|
IPv4 basic ACL |
1. VPN instance. 2. More 0s in the source IPv4 address wildcard (more 0s means a narrower IPv4 address range). 3. Rule configured earlier. |
|
IPv4 advanced ACL |
1. VPN instance. 2. Specific protocol number. 3. More 0s in the source IPv4 address wildcard mask. 4. More 0s in the destination IPv4 address wildcard. 5. Narrower TCP/UDP service port number range. 6. Rule configured earlier. |
|
IPv6 basic ACL |
1. VPN instance. 2. Longer prefix for the source IPv6 address (a longer prefix means a narrower IPv6 address range). 3. Rule configured earlier. |
|
IPv6 advanced ACL |
1. VPN instance. 2. Specific protocol number. 3. Longer prefix for the source IPv6 address. 4. Longer prefix for the destination IPv6 address. 5. Narrower TCP/UDP service port number range. 6. Rule configured earlier. |
|
Ethernet frame header ACL |
1. More 1s in the source MAC address mask (more 1s means a smaller MAC address). 2. More 1s in the destination MAC address mask. 3. Rule configured earlier. |
A wildcard mask, also called an inverse mask, is a 32-bit binary number represented in dotted decimal notation. In contrast to a network mask, the 0 bits in a wildcard mask represent "do care" bits, and the 1 bits represent "don't care" bits. If the "do care" bits in an IP address are identical to the "do care" bits in an IP address criterion, the IP address matches the criterion. All "don't care" bits are ignored. The 0s and 1s in a wildcard mask can be noncontiguous. For example, 0.255.0.255 is a valid wildcard mask.
Rule numbering
ACL rules can be manually numbered or automatically numbered. This section describes how automatic ACL rule numbering works.
Rule numbering step
If you do not assign an ID to the rule you are creating, the system automatically assigns it a rule ID. The rule numbering step sets the increment by which the system automatically numbers rules. For example, the default ACL rule numbering step is 5. If you do not assign IDs to rules you are creating, they are automatically numbered 0, 5, 10, 15, and so on. The wider the numbering step, the more rules you can insert between two rules.
By introducing a gap between rules rather than contiguously numbering rules, you have the flexibility of inserting rules in an ACL. This feature is important for a config-order ACL, where ACL rules are matched in ascending order of rule ID.
Automatic rule numbering and renumbering
The ID automatically assigned to an ACL rule takes the nearest higher multiple of the numbering step to the current highest rule ID, starting with 0.
For example, if the numbering step is 5 (the default), and there are five ACL rules numbered 0, 5, 9, 10, and 12, the newly defined rule is numbered 15. If the ACL does not contain any rule, the first rule is numbered 0.
Whenever the step changes, the rules are renumbered, starting from 0. For example, if there are five rules numbered 5, 10, 13, 15, and 20, changing the step from 5 to 2 causes the rules to be renumbered 0, 2, 4, 6, and 8.
Fragment filtering with ACLs
Traditional packet filtering matches only first fragments of packets, and allows all subsequent non-first fragments to pass through. Attackers can fabricate non-first fragments to attack networks.
To avoid the risks, the ACL feature is designed as follows:
· Filters all fragments by default, including non-first fragments.
· Allows for matching criteria modification for efficiency. For example, you can configure the ACL to filter only non-first fragments.
Configuration task list
|
Tasks at a glance |
|
(Required.) Perform at least one of the following tasks: ¡ Configuring an IPv4 basic ACL ¡ Configuring an IPv6 basic ACL ¡ Configuring an IPv4 advanced ACL ¡ Configuring an IPv6 advanced ACL |
|
(Optional.) Copying an ACL |
|
(Optional.) Configuring packet filtering with ACLs |
Configuring a basic ACL
This section describes procedures for configuring IPv4 and IPv6 basic ACLs.
Configuring an IPv4 basic ACL
IPv4 basic ACLs match packets based only on source IP addresses.
To configure an IPv4 basic ACL:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an IPv4 basic ACL and enter its view. |
acl number acl-number [ name acl-name ] [ match-order { auto | config } ] |
By default, no ACL exists. IPv4 basic ACLs are numbered in the range of 2000 to 2999. You can use the acl name acl-name command to enter the view of a named ACL. |
|
3. (Optional.) Configure a description for the IPv4 basic ACL. |
description text |
By default, an IPv4 basic ACL has no ACL description. |
|
4. (Optional.) Set the rule numbering step. |
step step-value |
The default setting is 5. |
|
5. Create or edit a rule. |
rule [ rule-id ] { deny | permit } [ counting | fragment | logging | source { source-address source-wildcard | any } | time-range time-range-name | vpn-instance vpn-instance-name ] * |
By default, an IPv4 basic ACL does not contain any rule. The logging keyword takes effect only when the module (for example, packet filtering) that uses the ACL supports logging. If an IPv4 basic ACL is used for outbound packet filtering, do not specify the vpn-instance keyword. If an IPv4 basic ACL is used for outbound QoS traffic classification or outbound packet filtering: · The rule [ rule-id ] { deny | permit } source { source-address source-wildcard | any } command can match only Layer 3 forwarded packets, but not packets processed by the CPU or Layer 2 forwarded packets. · Any other IPv4 basic ACL rule can match packets processed by the CPU, Layer 2 forwarded packets, and Layer 3 forwarded packets. |
|
6. (Optional.) Add or edit a rule comment. |
rule rule-id comment text |
By default, no rule comment is configured. |
Configuring an IPv6 basic ACL
IPv6 basic ACLs match packets based only on source IP addresses.
To configure an IPv6 basic ACL:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an IPv6 basic ACL view and enter its view. |
acl ipv6 number acl-number [ name acl-name ] [ match-order { auto | config } ] |
By default, no ACL exists. IPv6 basic ACLs are numbered in the range of 2000 to 2999. You can use the acl ipv6 name acl-name command to enter the view of a named ACL. |
|
3. (Optional.) Configure a description for the IPv6 basic ACL. |
description text |
By default, an IPv6 basic ACL has no ACL description. |
|
4. (Optional.) Set the rule numbering step. |
step step-value |
The default setting is 5. |
|
5. Create or edit a rule. |
rule [ rule-id ] { deny | permit } [ counting | fragment | logging | routing [ type routing-type ] | source { source-address source-prefix | source-address/source-prefix | any } | time-range time-range-name | vpn-instance vpn-instance-name ] * |
By default, an IPv6 basic ACL does not contain any rule. The logging keyword takes effect only when the module (for example, packet filtering) that uses the ACL supports logging. If an IPv6 basic ACL is used for outbound packet filtering, do not specify the vpn-instance or routing keyword. If an IPv6 basic ACL is used for QoS traffic classification or packet filtering, do not specify the fragment keyword. If an IPv6 basic ACL is used for outbound QoS traffic classification or outbound packet filtering: · The rule [ rule-id ] { deny | permit } source { source-address source-prefix | source-address/source-prefix | any } command can match only Layer 3 forwarded packets, but not packets processed by the CPU or Layer 2 forwarded packets. · Any other IPv6 basic ACL rule can match packets processed by the CPU, Layer 2 forwarded packets, and Layer 3 forwarded packets. |
|
6. (Optional.) Add or edit a rule comment. |
rule rule-id comment text |
By default, no rule comment is configured. |
Configuring an advanced ACL
This section describes procedures for configuring IPv4 and IPv6 advanced ACLs.
Configuring an IPv4 advanced ACL
IPv4 advanced ACLs match packets based on the following criteria:
· Source IP addresses.
· Destination IP addresses.
· Packet priorities.
· Protocol types.
· Other protocol header information, such as TCP/UDP source and destination port numbers, TCP flags, ICMP message types, and ICMP message codes.
· Encapsulation types.
· Inner source IP addresses.
· Inner destination addresses.
· Inner protocol types.
· Other inner protocol header information, such as inner TCP/UDP source and destination port numbers.
Compared to IPv4 basic ACLs, IPv4 advanced ACLs allow more flexible and accurate filtering.
To configure an IPv4 advanced ACL:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an IPv4 advanced ACL and enter its view. |
acl number acl-number [ name acl-name ] [ match-order { auto | config } ] |
By default, no ACL exists. IPv4 advanced ACLs are numbered in the range of 3000 to 3999. You can use the acl name acl-name command to enter the view of a named ACL. |
|
3. (Optional.) Configure a description for the IPv4 advanced ACL. |
description text |
By default, an IPv4 advanced ACL has no ACL description. |
|
4. (Optional.) Set the rule numbering step. |
step step-value |
The default setting is 5. |
|
5. Create or edit a rule. |
·
To match ordinary packets: ·
To match VXLAN packets: |
By default, an IPv4 advanced ACL does not contain any rule. The logging keyword takes effect only when the module (for example, packet filtering) that uses the ACL supports logging. The rule { deny | permit } vxlan command can match VXLAN packets by both outer and inner packet information. To match GRE-encapsulated or IPinIP-encapsulated packets, you must specify the protocol as GRE or IPinIP. If an IPv4 advanced ACL is used for outbound packet filtering, do not specify the vpn-instance keyword. If an IPv4 advanced ACL is used for QoS traffic classification or packet filtering, do not specify the neq for the operator argument. If an IPv4 advanced ACL is used for outbound QoS traffic classification or outbound packet filtering: · The rule [ rule-id ] { deny | permit } ip command can match only Layer 3 forwarded packets, but not packets processed by the CPU or Layer 2 forwarded packets. · Any other IPv4 advanced ACL rule can match packets processed by the CPU, Layer 2 forwarded packets, and Layer 3 forwarded packets. |
|
6. (Optional.) Add or edit a rule comment. |
rule rule-id comment text |
By default, no rule comment is configured. |
Configuring an IPv6 advanced ACL
IPv6 advanced ACLs match packets based on the following criteria:
· Source IPv6 addresses.
· Destination IPv6 addresses.
· Packet priorities.
· Protocol numbers.
· Other protocol header fields such as the TCP/UDP source port number, TCP/UDP destination port number, ICMPv6 message type, and ICMPv6 message code.
Compared to IPv6 basic ACLs, IPv6 advanced ACLs allow more flexible and accurate filtering.
To configure an IPv6 advanced ACL:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an IPv6 advanced ACL and enter its view. |
acl ipv6 number acl-number [ name acl-name ] [ match-order { auto | config } ] |
By default, no ACL exists. IPv6 advanced ACLs are numbered in the range of 3000 to 3999. You can use the acl ipv6 name acl-name command to enter the view of a named ACL. |
|
3. (Optional.) Configure a description for the IPv6 advanced ACL. |
description text |
By default, an IPv6 advanced ACL has no ACL description. |
|
4. (Optional.) Set the rule numbering step. |
step step-value |
The default setting is 5. |
|
5. Create or edit a rule. |
rule [ rule-id ] { deny | permit } protocol [ { { ack ack-value | fin fin-value | psh psh-value | rst rst-value | syn syn-value | urg urg-value } * | established } | counting | destination { dest-address dest-prefix | dest-address/dest-prefix | any } | destination-port operator port1 [ port2 ] | dscp dscp | flow-label flow-label-value | fragment | icmp6-type { icmp6-type icmp6-code | icmp6-message } | logging | qos-local-id local-id-value | routing [ type routing-type ] | hop-by-hop [ type hop-type ] | source { source-address source-prefix | source-address/source-prefix | any } | source-port operator port1 [ port2 ] | time-range time-range-name | vpn-instance vpn-instance-name ] * |
By default, IPv6 advanced ACL does not contain any rule. The logging keyword takes effect only when the module (for example, packet filtering) that uses the ACL supports logging. If an IPv6 advanced ACL is used for outbound packet filtering, do not specify the vpn-instance, routing, hop-by-hop, or flow-label keyword. If an IPv6 advanced ACL is used for QoS traffic classification or packet filtering, do not specify the fragment keyword or neq for the operator argument. If an IPv6 advanced ACL is used for outbound QoS traffic classification or outbound packet filtering: · The rule [ rule-id ] { deny | permit } ipv6 command can match only Layer 3 forwarded packets, but not packets processed by the CPU or Layer 2 forwarded packets. · Any other IPv6 advanced ACL rule can match packets processed by the CPU, Layer 2 forwarded packets, and Layer 3 forwarded packets. |
|
6. (Optional.) Add or edit a rule comment. |
rule rule-id comment text |
By default, no rule comment is configured. |
|
|
NOTE: If an ACL is to match information in the IPv6 packet payload, it can only match packets with one extension header. It cannot match packets with two or more extension headers or with the Encapsulating Security Payload Header. |
Configuring an Ethernet frame header ACL
Ethernet frame header ACLs, also called "Layer 2 ACLs," match packets based on Layer 2 protocol header fields, such as:
· Source MAC address.
· Destination MAC address.
· 802.1p priority (VLAN priority).
· Link layer protocol type.
· Encapsulation type.
· Inner source MAC address.
· Inner destination MAC address.
· Inner link layer protocol type.
To configure an Ethernet frame header ACL:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an Ethernet frame header ACL and enter its view. |
acl number acl-number [ name acl-name ] [ match-order { auto | config } ] |
By default, no ACL exists. Ethernet frame header ACLs are numbered in the range of 4000 to 4999. You can use the acl name acl-name command to enter the view of a named ACL. |
|
3. (Optional.) Configure a description for the Ethernet frame header ACL. |
description text |
By default, an Ethernet frame header ACL has no ACL description. |
|
4. (Optional.) Set the rule numbering step. |
step step-value |
The default setting is 5. |
|
5. Create or edit a rule. |
·
To match ordinary packets: ·
To match VXLAN packets: |
By default, an Ethernet frame header ACL does not contain any rule. The rule { deny | permit } vxlan command can match VXLAN packets by both outer and inner packet information. If an Ethernet frame header ACL is used for packet filtering or QoS traffic classification: · If the lsap keyword is used, the lsap-type argument must be AAAA, and the lsap-type-mask argument must be FFFF. Otherwise, the ACL does not take effect. · If the ACL is for outbound application, do not specify the lsap, type, and counting keywords. |
|
6. (Optional.) Add or edit a rule comment. |
rule rule-id comment text |
By default, no rule comment is configured. |
Configuring a user-defined ACL
User-defined ACLs allow you to customize rules based on information in protocol headers. You can define a user-defined ACL to match packets. A specific number of bytes after an offset (relative to the specified header) are compared against a match pattern after being ANDed with a match pattern mask.
To configure a user-defined ACL:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a user-defined ACL and enter its view. |
acl number acl-number [ name acl-name ] |
By default, no ACL exists. User-defined ACLs are numbered in the range of 5000 to 5999. You can use the acl name acl-name command to enter the view of a named ACL. |
|
3. (Optional.) Configure a description for the user-defined ACL. |
description text |
By default, a user-defined ACL does not have a description. |
|
4. Create or edit a rule. |
rule [ rule-id ] { deny | permit } [ { l2 rule-string rule-mask offset }&<1-8> ] [ counting | time-range time-range-name ] * |
By default, a user-defined ACL does not contain any rule. A user-defined ACL cannot be used for outbound QoS traffic classification or outbound packet filtering. |
|
5. (Optional.) Add or edit a rule comment. |
rule rule-id comment text |
By default, no rule comment is configured. |
|
|
NOTE: If a user-defined ACL is to match packets with VLAN tags, the offset must include the length of the VLAN tags. Each VLAN tag is 4 bytes long. |
Copying an ACL
You can create an ACL by copying an existing ACL (source ACL). The new ACL (destination ACL) has the same properties and content as the source ACL, but not the same ACL number and name.
To successfully copy an ACL, make sure:
· The destination ACL number is from the same category as the source ACL number.
· The source ACL already exists, but the destination ACL does not.
To copy an ACL:
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Copy an existing ACL to create a new ACL. |
acl [ ipv6 ] copy { source-acl-number | name source-acl-name } to { dest-acl-number | name dest-acl-name } |
Configuring packet filtering with ACLs
This section describes procedures for using an ACL to filter packets. For example, you can apply an ACL to an interface to filter incoming or outgoing packets.
|
|
NOTE: If packet filtering is configured on Ethernet interfaces, on VLAN interfaces, on VSI interfaces, and globally on the device, the packet filtering priority is as follows: · Packet filtering in extended mode takes priority over packet filtering in non-extended mode. · For packet filtering in extended mode, packet filtering on Ethernet interfaces takes priority over packet filtering on VLAN interfaces. · For packet filtering in non-extended mode, interface-based packet filtering takes priority over global packet filtering. The priority of interface-based packet filtering descends in the order of Ethernet interface, VSI interface, and VLAN interface. |
Applying an ACL to filter packets globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Apply an ACL to filter packets globally. |
packet-filter [ ipv6 ] { acl-number | name acl-name } global { inbound | outbound } [ hardware-count ] |
By default, no ACL is applied to filter packets globally. |
Applying an ACL to an interface for packet filtering
The interface-based packet filtering feature is available on Layer 2 and Layer 3 Ethernet interfaces, VLAN interfaces, and VSI interfaces. The term "interface" in this section collectively refers to these types of interfaces. You can use the port link-mode command to configure an Ethernet port as a Layer 2 or Layer 3 interface (see Layer 2—LAN Switching Configuration Guide). For more information about the VSI interface, see VXLAN Configuration Guide.
To apply an ACL to an interface for packet filtering:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Apply an ACL to the interface to filter packets. |
packet-filter [ ipv6 ] { acl-number | name acl-name } { inbound [ extension ] | outbound } [ hardware-count ] |
By default, an interface does not filter packets. You can apply only one ACL to the same direction of an interface. Only Ethernet interfaces and VLAN interfaces on an FE card support the extension keyword. |
Setting the interval for generating and outputting packet filtering logs
After you set the interval, the device periodically generates and outputs the packet filtering logs to the information center, including the number of matching packets and the matched ACL rules. For more information about information center, see Network Management and Monitoring Configuration Guide.
To set the interval for generating and outputting packet filtering logs:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the interval for generating and outputting packet filtering logs. |
acl [ ipv6 ] logging interval interval |
The default setting is 0 minutes, which mean that no packet filtering logs are generated. |
Setting the packet filtering default action
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the packet filtering default action to deny. |
packet-filter default deny |
By default, the packet filter permits packets that do not match any ACL rule to pass. |
Displaying and maintaining ACLs
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display ACL configuration and match statistics. |
display acl [ ipv6 ] { acl-number | all | name acl-name } |
|
Display whether an ACL has been successfully applied to an interface for packet filtering (in standalone mode). |
display packet-filter { global [ inbound | outbound ] [ slot slot-number ] | interface [ interface-type interface-number ] [ inbound | outbound ] | interface vlan-interface vlan-interface-number [ inbound | outbound ] [ slot slot-number ] } |
|
Display whether an ACL has been successfully applied to an interface for packet filtering (in IRF mode). |
display packet-filter { global [ inbound | outbound ] [ chassis chassis-number slot slot-number ] | interface [ interface-type interface-number ] [ inbound | outbound ] | interface vlan-interface vlan-interface-number [ inbound | outbound ] [ chassis chassis-number slot slot-number ] } |
|
Display match statistics for packet filtering ACLs. |
display packet-filter statistics { global | interface interface-type interface-number } { inbound | outbound } [ [ ipv6 ] { acl-number | name acl-name } ] [ brief ] |
|
Display the accumulated statistics for packet filtering ACLs. |
display packet-filter statistics sum { inbound | outbound } [ ipv6 ] { acl-number | name acl-name } [ brief ] |
|
Display detailed ACL packet filtering information (in standalone mode). |
display packet-filter verbose { global | interface interface-type interface-number } { inbound | outbound } [ [ ipv6 ] acl-number | name acl-name ] [ slot slot-number ] |
|
Display detailed ACL packet filtering information (in IRF mode). |
display packet-filter verbose { global | interface interface-type interface-number } { inbound | outbound } [ [ ipv6 ] acl-number | name acl-name ] [ chassis chassis-number slot slot-number ] |
|
Display QoS and ACL resource usage (in standalone mode). |
display qos-acl resource [ slot slot-number ] |
|
Display QoS and ACL resource usage (in IRF mode). |
display qos-acl resource [ chassis chassis-number slot slot-number ] |
|
Clear ACL statistics. |
reset acl [ ipv6 ] counter { acl-number | all | name acl-name } |
|
Clear match statistics (including the accumulated statistics) for packet filtering ACLs. |
reset packet-filter statistics { global | interface [ interface-type interface-number ] } { inbound | outbound } [ [ ipv6 ] { acl-number | name acl-name } ] |
ACL configuration examples
Interface-based packet filtering configuration example
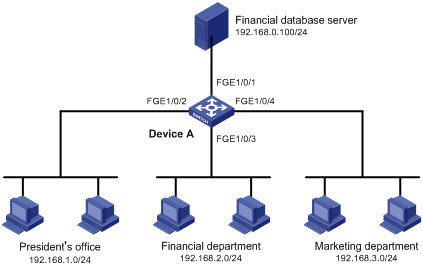
Network requirements
A company interconnects its departments through Device A. Configure an ACL to:
· Permit access from the President's office at any time to the financial database server.
· Permit access from the Financial department to the database server only during working hours (from 8:00 to 18:00) on working days.
· Deny access from any other department to the database server.
Figure 1 Network diagram
Configuration procedure
# Create a periodic time range from 8:00 to 18:00 on working days.
<DeviceA> system-view
[DeviceA] time-range work 08:0 to 18:00 working-day
# Create an IPv4 advanced ACL numbered 3000 and configure three rules in the ACL. One rule permits access from the President's office to the financial database server, one rule permits access from the Financial department to the database server during working hours, and one rule denies access from any other department to the database server.
[DeviceA] acl number 3000
[DeviceA-acl-adv-3000] rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.0.100 0
[DeviceA-acl-adv-3000] rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.0.100 0 time-range work
[DeviceA-acl-adv-3000] rule deny ip source any destination 192.168.0.100 0
[DeviceA-acl-adv-3000] quit
# Apply IPv4 advanced ACL 3000 to filter outgoing packets on interface FortyGigE 1/0/1.
[DeviceA] interface fortygige 1/0/1
[DeviceA-FortyGigE1/0/1] packet-filter 3000 outbound
[DeviceA-FortyGigE1/0/1] quit
Verifying the configuration
# Ping the database server from a PC in the Financial department during the working hours. (All PCs in this example use Windows XP).
C:\> ping 192.168.0.100
Pinging 192.168.0.100 with 32 bytes of data:
Reply from 192.168.0.100: bytes=32 time=1ms TTL=255
Reply from 192.168.0.100: bytes=32 time<1ms TTL=255
Reply from 192.168.0.100: bytes=32 time<1ms TTL=255
Reply from 192.168.0.100: bytes=32 time<1ms TTL=255
Ping statistics for 192.168.0.100:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 1ms, Average = 0ms
The output shows that the database server can be pinged.
# Ping the database server from a PC in the Marketing department during the working hours.
C:\> ping 192.168.0.100
Pinging 192.168.0.100 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 192.168.0.100:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
The output shows the database server cannot be pinged.
# Display configuration and match statistics for IPv4 advanced ACL 3000 on Device A during the working hours.
[DeviceA] display acl 3000
Advanced ACL 3000, named -none-, 3 rules,
ACL's step is 5
rule 0 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.0.100 0
rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.0.100 0 time-range work (Active)
rule 10 deny ip destination 192.168.0.100 0
The output shows that rule 5 is active.
Configuration example of filtering TCP packets with ACK or RST flag set
Network requirements
As shown in Figure 2, the hosts on subnet 192.168.1.0/24 access the server through the switch. Configure packet filtering on FortyGigE 1/0/1 of the switch to prevent TCP packets with the ACK or RST flag bit set from being forwarded to the server.
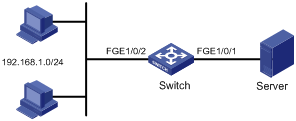
Configuration procedure
# Create advanced ACL 3000 and configure a rule to match TCP packets whose ACK or RST flag bit is set.
<Switch> system-view
[Switch] acl number 3000
[Switch-acl-adv-3000] rule permit tcp established
[Switch-acl-adv-3000] quit
# Create a traffic class named tcp and use ACL 3000 as the match criterion in the traffic class.
[Switch] traffic classifier tcp
[Switch-classifier-tcp] if-match acl 3000
[Switch-classifier-tcp] quit
# Create a traffic behavior named remark_qos_local to mark traffic with local QoS ID 1.
[Switch] traffic behavior remark_qos_local
[Switch-behavior-remark_qos_local] remark qos-local-id 1
[Switch-behavior-remark_qos_local] quit
# Create QoS policy tcp_remark_qos_local. Associate traffic class tcp with traffic behavior remark_qos_local.
[Switch] qos policy tcp_remark_qos_local
[Switch-qospolicy-tcp_remark_qos_local] classifier tcp behavior remark_qos_local
[Switch-qospolicy-tcp_remark_qos_local] quit
# Apply QoS policy tcp_remark_qos_local to incoming traffic globally.
[Switch] qos apply policy tcp_remark_qos_local global inbound
# Create advanced ACL 3001 and configure a rule to deny packets whose local QoS ID is 1.
[Switch] acl number 3001
[Switch-acl-adv-3001] rule deny ip qos-local-id 1
[Switch-acl-adv-3001] quit
# Apply ACL 3001 to FortyGigE 1/0/1 to filtering outgoing packets.
[Switch] interface fortygige 1/0/1
[Switch-FortyGigE1/0/1] packet-filter 3001 outbound
|
|
NOTE: For more information about QoS configuration, see "Configuring a QoS policy." For more information about QoS commands, see ACL and QoS Command Reference. |