- Table of Contents
-
- 01 Fundamentals Configuration Guide
- 00-Preface
- 01-CLI configuration
- 02-Login management configuration
- 03-RBAC configuration
- 04-FTP and TFTP configuration
- 05-File system management configuration
- 06-Configuration file management configuration
- 07-Software upgrade configuration
- 08-ISSU configuration
- 09-Device management configuration
- 10-Tcl configuration
- 11-Python configuration
- 12-License management
- 13-Automatic configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 09-Device management configuration | 179.78 KB |
Specifying the system time source
Enabling displaying the copyright statement
Setting the system operating mode
Adjusting capacities of the MAC address table, ARP/ND table, and routing table
Rebooting devices immediately at the CLI
Schedule configuration example
Disabling password recovery capability·
Specifying the preferred airflow direction
Setting the port status detection timer
Configuring CPU usage monitoring
Configuring the temperature alarm thresholds
Verifying and diagnosing transceiver modules
Verifying transceiver modules·
Diagnosing transceiver modules·
Restoring the factory-default settings and states
Displaying and maintaining device management configuration
This chapter describes how to configure basic device parameters and manage the device.
You can perform the configuration tasks in this chapter in any order.
Device management task list
|
Tasks at a glance |
|
(Required.) Configuring the device name |
|
(Required.) Configuring the system time |
|
(Optional.) Enabling displaying the copyright statement |
|
(Optional.) Configuring banners |
|
(Required.) Setting the system operating mode |
|
(Optional.) Adjusting capacities of the MAC address table, ARP/ND table, and routing table |
|
(Optional.) Rebooting the device |
|
(Optional.) Scheduling a task |
|
(Optional.) Disabling password recovery capability |
|
(Optional.) Specifying the preferred airflow direction |
|
(Optional.) Setting the port status detection timer |
|
(Optional.) Configuring CPU usage monitoring |
|
(Required.) Setting memory thresholds |
|
(Required.) Configuring the temperature alarm thresholds |
|
(Optional.) Disabling all USB interfaces |
|
(Required.) Verifying and diagnosing transceiver modules |
|
(Optional.) Restoring the factory-default settings and states |
Configuring the device name
A device name (also called hostname) identifies a device in a network and is used as the user view prompt at the CLI. For example, if the device name is Sysname, the user view prompt is <Sysname>.
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the device name. |
sysname sysname |
The default device name is H3C. |
Configuring the system time
Specifying the system time source
The device can use one of the following system time sources:
· None—Local system time, which is manually configured at the CLI.
· PTP—PTP time source. PTP is not supported in the current release.
· NTP—NTP time source. When the device uses the NTP time source, you cannot change the system time manually. For more information about NTP, see Network Management and Monitoring Configuration Guide.
If you configure the clock protocol none command together with the clock protocol ntp or clock protocol ptp command, the device uses the NTP or PTP time source.
Power cycling or using the reboot command to reboot an S7500E-XS restores the default system time settings. Reconfigure the settings after the switch starts up.
To specify the system time source:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify the system time source. |
clock protocol { none | ntp | ptp } |
By default, the device uses the NTP time source. The ptp keyword is not supported in the current release. If you configure this command multiple times, the most recent configuration takes effect. |
Setting the system time
When the system time source is the local system time, the system time is determined by the UTC time, local time zone, and daylight saving time. You can use the display clock command to view the system time.
A correct system time setting is essential to network management and communication. Set the system time correctly or use NTP to synchronize the device with a trusted time source before you run it on the network.
|
Step |
Command |
Remarks |
|
1. Set the UTC time. |
clock datetime time date |
By default, the UTC time is the factory-default time. |
|
2. Enter system view. |
system-view |
N/A |
|
3. Set the local time zone. |
clock timezone zone-name { add | minus } zone-offset |
The default local time zone is the UTC time zone. |
|
4. Set the daylight saving time. |
clock summer-time name start-time start-date end-time end-date add-time |
By default, daylight saving time is disabled. |
Enabling displaying the copyright statement
When displaying the copyright statement is enabled, the device displays the copyright statement in the following situations:
· When a Telnet or SSH user logs in.
· After a console or modem dial-in user quits user view. This is because the device automatically tries to restart the console session.
The following is a sample copyright statement:
******************************************************************************
* Copyright (c) 2004-2014 Hangzhou H3C Tech. Co., Ltd. All rights reserved. *
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
To enable displaying the copyright statement:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable displaying the copyright statement. |
copyright-info enable |
By default, this function is enabled. |
Configuring banners
Banners are messages that the system displays when a user logs in.
Banner types
The system supports the following banners:
· Legal banner—Appears after the copyright or license statement. To continue login, the user must enter Y or press Enter. To quit the process, the user must enter N. Y and N are case insensitive.
· Message of the Day (MOTD) banner—Appears after the legal banner and before the login banner.
· Login banner—Appears only when password or scheme authentication is configured.
· Incoming banner—Appears for Modem users.
· Shell banner—Appears before a non-modem dial-in user accesses user view.
Banner input modes
You can configure a single-line banner or a multiline banner.
· Single-line banner.
A single-line banner must be input in the same line as the command. The start and end delimiters for the banner can be any printable character. However, they must be the same and must not be included in the banner. The input text, including the command keywords and the delimiters, cannot exceed 510 characters. Do not press Enter before you input the end delimiter.
For example, you can configure the shell banner "Have a nice day." as follows:
<System> system-view
[System] header shell %Have a nice day.%
· Multiline banner.
A multiline banner can be up to 2000 characters. To input a multiline banner, use one of the following methods:
¡ Method 1—Press Enter after the last command keyword. At the system prompt, enter the banner and end the last line with the delimiter character %. For example, you can configure the banner "Have a nice day. Please input the password." as follows:
<System> system-view
[System] header shell
Please input banner content, and quit with the character '%'.
Have a nice day.
Please input the password.%
¡ Method 2—After you type the last command keyword, type any single printable character as the start delimiter for the banner and press Enter. At the system prompt, type the banner and end the last line with the same delimiter. For example, you can configure the banner "Have a nice day. Please input the password." as follows:
<System> system-view
[System] header shell A
Please input banner content, and quit with the character 'A'.
Have a nice day.
Please input the password.A
¡ Method 3—After you type the last command keyword, type the start delimiter and part of the banner and press Enter. At the system prompt, enter the rest of the banner and end the last line with the same delimiter. For example, you can configure the banner "Have a nice day. Please input the password." as follows:
<System> system-view
[System] header shell AHave a nice day.
Please input banner content, and quit with the character 'A'.
Please input the password.
A
Configuration procedure
To configure banners:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the legal banner. |
header legal text |
By default, the device does not have a banner. |
|
3. Configure the MOTD banner. |
header motd text |
By default, the device does not have a banner. |
|
4. Configure the login banner. |
header login text |
By default, the device does not have a banner. |
|
5. Configure the incoming banner. |
header incoming text |
By default, the device does not have a banner. |
|
6. Configure the shell banner. |
header shell text |
By default, the device does not have a banner. |
Setting the system operating mode
The device can operate in the following modes:
· advance—Advanced mode.
· standard—Standard mode.
· expert—Expert mode.
In different operating modes, the device supports different features, and might have different specifications for the supported features.
If the prompt "Not enough hardware resources available." appears after you set the system operating mode, perform the following tasks:
· Use the display qos-acl resource command to display ACL resource usage.
· Use the undo acl command to release ACL resources as required.
· Set the system operating mode again.
For more information about the display qos-acl resource and undo acl commands, see ACL and QoS Command Reference.
To set the system operating mode:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the system operating mode. |
system-working-mode { advance | standard | expert } |
By default, the device operates in standard mode. Change to the operating mode takes effect after a reboot. |
Adjusting capacities of the MAC address table, ARP/ND table, and routing table
The switch supports multiple table capacity modes. The capacities of the MAC address table, ARP/ND table, and routing table depend on the following conditions:
· Table capacity mode.
· Whether the switch-routing-mode ipv6-128 command is configured. For more information about the switch-routing-mode ipv6-128 command, see Layer 3—IP Routing Command Reference.
Mode 4 and the switch-routing-mode ipv6-128 command are mutually exclusive.
Mode 5 and the switch-routing-mode ipv6-128 command are mutually exclusive.
The term IPv6-64 means that the prefix length is equal to or less than 64 bits. The term IPv6-128 means that the prefix length is greater than 64 bits. The value 1K is 1024 entries.
Table 1 Table capacities when the switch-routing-mode ipv6-128 command is not configured
|
Capacity of the MAC address table |
Capacity of the ARP /ND table |
Capacity of the routing table |
|
|
16K ARP table or 8K ND table |
|||
|
56K ARP table or 28K ND table |
|||
|
88K ARP table or 44K ND table |
|||
|
120K ARP table or 60K ND table |
|||
|
16K ARP table or 8K ND table |
|||
|
5 |
32K |
16K ARP table or 8K ND table |
64K (IPv4) or 16K (IPv6-64) |
Table 2 Table capacities when the switch-routing-mode ipv6-128 command is configured
|
Table capacity mode |
Capacity of the MAC address table |
Capacity of the ARP /ND table |
Capacity of the routing table |
|
0 |
288K |
16K ARP table or 8K ND table |
8K (IPv4) or 4K (IPv6-64) 2K (IPv6-128) |
|
1 |
224K |
56K ARP table or 28K ND table |
8K (IPv4) or 4K (IPv6-64) 2K (IPv6-128) |
|
2 |
160K |
88K ARP table or 44K ND table |
8K (IPv4) or 4K (IPv6-64) 2K (IPv6-128) |
|
3 |
96K |
120K ARP table or 60K ND table |
8K (IPv4) or 4K (IPv6-64) 2K (IPv6-128) |
To set the table capacity mode:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the table capacity mode. |
switch-mode { 0 | 1 | 2 | 3 | 4 | 5 } |
The default table capacity mode is 0. This setting takes effect after a reboot. Before rebooting the switch, make sure you know the possible impact on the network. |
Rebooting the device
|
|
CAUTION: · A device reboot might interrupt network services. · To avoid configuration loss, use the save command to save the running configuration before a reboot. For more information about the save command, see Fundamentals Command Reference. · Before a reboot, use the display startup and display boot-loader commands to verify that the startup configuration file and startup software images are correctly specified. If a startup configuration file or software image problem exists, the device cannot start up correctly. For more information about the two display commands, see Fundamentals Command Reference. |
The following device reboot methods are available:
· Immediately reboot the device at the CLI.
· Schedule a reboot at the CLI, so the device automatically reboots at the specified time or after the specified period of time.
· Power off and then power on the device. This method might cause data loss, and is the least-preferred method.
Using the CLI, you can reboot the device from a remote host.
Configuration guidelines
When you schedule a reboot, follow these guidelines:
· The automatic reboot configuration takes effect on all member devices. It will be canceled if a master/subordinate switchover occurs.
· For data security purposes, the device does not reboot while it is performing file operations.
Rebooting devices immediately at the CLI
Execute the following command in user view:
|
Task |
Command |
Remarks |
|
Reboot an IRF member device or all IRF member devices. |
reboot [ slot slot-number ] [ force ] |
Use this command in user view |
Scheduling a device reboot
The device supports only one device reboot schedule. If you configure the scheduler reboot at or scheduler reboot delay command multiple times or configure both commands, the most recent configuration takes effect.
To schedule a reboot, execute either of the following commands in user view:
|
Task |
Command |
Remarks |
|
Specify the reboot date and time. |
scheduler reboot at time [ date ] |
By default, no reboot date or time is specified. |
|
Specify the reboot delay time. |
scheduler reboot delay time |
By default, no reboot delay time is specified. |
Scheduling a task
You can schedule the device to automatically execute a command or a set of commands without administrative interference.
You can configure a one-time schedule or a periodic schedule. A one-time schedule is not saved to the configuration file and is lost when the device reboots. A periodic schedule is saved to the startup configuration file and is automatically executed periodically.
Configuration guidelines
Follow these guidelines when you schedule a task:
· Make sure all commands in a schedule are compliant to the command syntax. The system does not check the syntax when you assign a command to a job.
· A schedule cannot contain any of these commands: telnet, ftp, ssh2, and monitor process.
· A schedule does not support user interaction. If a command requires a yes or no answer, the system always assumes that a Y or Yes is entered. If a command requires a character string input, the system assumes that either the default character string (if any) is entered, or a null string is entered.
· A schedule is executed in the background, and no output (except for logs, traps, and debug information) is displayed for the schedule.
Configuration procedure
To configure a one-time schedule for the device:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a job. |
scheduler job job-name |
By default, no job exists. |
|
3. Assign a command to the job. |
command id command |
By default, no command is assigned to a job. You can assign multiple commands to a job. A command with a smaller ID will be executed first. |
|
4. Exit system view. |
quit |
N/A |
|
5. Create a schedule. |
scheduler schedule schedule-name |
By default, no schedule exists. |
|
6. Assign a job to a schedule. |
job job-name |
By default, no job is assigned to a schedule. You can assign multiple jobs to a schedule. The jobs will be executed concurrently. |
|
7. Assign user roles to the schedule. |
user-role role-name |
By default, a schedule has the user role of the schedule creator. A command in a schedule can be executed if it is permitted by one or more user roles of the schedule. The security-audit user role is mutually exclusive with any other user roles. Assigning the security-audit user role to a schedule removes all the other user role assignments for the schedule. Assigning any other user roles to a schedule removes the security-audit user role assignment for the schedule. |
|
8. Specify an execution time table for the one-time schedule. |
· Specify the
execution date and time: · Specify the
execution days and time: · Specify the
execution delay time: |
Configure one command as required. By default, no execution time is specified for a schedule. Executing commands clock datetime, clock summer-time, and clock timezone does not change the execution time table that is already configured for a schedule. |
To configure a periodic schedule for the device:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a job. |
scheduler job job-name |
By default, no job exists. |
|
3. Assign a command to the job. |
command id command |
By default, no command is assigned to a job. You can assign multiple commands to a job. A job with a smaller ID will be executed first. |
|
4. Exit system view. |
quit |
N/A |
|
5. Create a schedule. |
scheduler schedule schedule-name |
By default, no schedule exists. |
|
6. Assign user roles to the schedule. |
user-role role-name |
By default, a schedule has the user role of the schedule creator. A command in a schedule can be executed if it is permitted by one or more user roles of the schedule. |
|
7. Assign a job to a schedule. |
job job-name |
By default, no job is assigned to a schedule. You can assign multiple jobs to a schedule. The jobs will be executed concurrently. |
|
8. Specify an execution time table for the periodic schedule. |
·
Execute the schedule at an interval from the specified time on: · Execute the schedule at the specified time on every specified day in a month
or week: |
Configure either command. By default, no execution time is specified for a schedule. Executing commands clock datetime, clock summer-time, and clock timezone does not change the execution time table that is already configured for a schedule. |
Schedule configuration example
Network requirements
As shown in Figure 1, two interfaces of the device are connected to users.
To save energy, configure the device to perform the following operations:
· Enable interfaces FortyGigE 1/1/1 and FortyGigE 1/1/2 at 8:00 a.m. every Monday through Friday.
· Disable the interfaces at 18:00 every Monday through Friday.
Scheduling procedure
# Enter system view.
<Sysname> system-view
# Configure a job for disabling interface FortyGigE 1/1/1.
[Sysname] scheduler job shutdown-FortyGigE1/1/1
[Sysname-job-shutdown-FortyGigE1/1/1] command 1 system-view
[Sysname-job-shutdown-FortyGigE1/1/1] command 2 interface fortygige 1/1/1
[Sysname-job-shutdown-FortyGigE1/1/1] command 3 shutdown
[Sysname-job-shutdown-FortyGigE1/1/1] quit
# Configure a job for enabling interface FortyGigE 1/1/1.
[Sysname] scheduler job start-FortyGigE1/1/1
[Sysname-job-start-FortyGigE1/1/1] command 1 system-view
[Sysname-job-start-FortyGigE1/1/1] command 2 interface fortygige 1/1/1
[Sysname-job-start-FortyGigE1/1/1] command 3 undo shutdown
[Sysname-job-start-FortyGigE1/1/1] quit
# Configure a job for disabling interface FortyGigE 1/1/2.
[Sysname] scheduler job shutdown-FortyGigE1/1/2
[Sysname-job-shutdown-FortyGigE1/1/2] command 1 system-view
[Sysname-job-shutdown-FortyGigE1/1/2] command 2 interface fortygige 1/1/2
[Sysname-job-shutdown-FortyGigE1/1/2] command 3 shutdown
[Sysname-job-shutdown-FortyGigE1/1/2] quit
# Configure a job for enabling interface FortyGigE 1/1/2.
[Sysname] scheduler job start-FortyGigE1/1/2
[Sysname-job-start-FortyGigE1/1/2] command 1 system-view
[Sysname-job-start-FortyGigE1/1/2] command 2 interface fortygige 1/1/2
[Sysname-job-start-FortyGigE1/1/2] command 3 undo shutdown
[Sysname-job-start-FortyGigE1/1/2] quit
# Configure a periodic schedule for enabling the interfaces at 8:00 a.m. every Monday through Friday.
[Sysname] scheduler schedule START-pc1/pc2
[Sysname-schedule-START-pc1/pc2] job start-FortyGigE1/1/1
[Sysname-schedule-START-pc1/pc2] job start-FortyGigE1/1/2
[Sysname-schedule-START-pc1/pc2] time repeating at 8:00 week-day mon tue wed thu fri
[Sysname-schedule-START-pc1/pc2] quit
# Configure a periodic schedule for disabling the interfaces at 18:00 every Monday through Friday.
[Sysname] scheduler schedule STOP-pc1/pc2
[Sysname-schedule-STOP-pc1/pc2] job shutdown-FortyGigE1/1/1
[Sysname-schedule-STOP-pc1/pc2] job shutdown-FortyGigE1/1/2
[Sysname-schedule-STOP-pc1/pc2] time repeating at 18:00 week-day mon tue wed thu fri
[Sysname-schedule-STOP-pc1/pc2] quit
Verifying the scheduling
# Display the configuration information of all jobs.
[Sysname] display scheduler job
Job name: shutdown-FortyGigE1/1/1
system-view
interface fortygige 1/1/1
shutdown
Job name: shutdown-FortyGigE1/1/2
system-view
interface fortygige 1/1/2
shutdown
Job name: start-FortyGigE1/1/1
system-view
interface fortygige 1/1/1
undo shutdown
Job name: start-FortyGigE1/1/2
system-view
interface fortygige 1/1/2
undo shutdown
# Display the schedule information.
[Sysname] display scheduler schedule
Schedule name : START-pc1/pc2
Schedule type : Run on every Mon Tue Wed Thu Fri at 08:00:00
Start time : Wed Sep 28 08:00:00 2011
Last execution time : Wed Sep 28 08:00:00 2011
Last completion time : Wed Sep 28 08:00:03 2011
Execution counts : 1
-----------------------------------------------------------------------
Job name Last execution status
start-FortyGigE1/1/1 Successful
start-FortyGigE1/1/2 Successful
Schedule name : STOP-pc1/pc2
Schedule type : Run on every Mon Tue Wed Thu Fri at 18:00:00
Start time : Wed Sep 28 18:00:00 2011
Last execution time : Wed Sep 28 18:00:00 2011
Last completion time : Wed Sep 28 18:00:01 2011
Execution counts : 1
-----------------------------------------------------------------------
Job name Last execution status
shutdown-FortyGigE1/1/1 Successful
shutdown-FortyGigE1/1/2 Successful
# Display schedule log information.
[Sysname] display scheduler logfile
Logfile Size: 16054 Bytes.
Job name : start-FortyGigE1/1/1
Schedule name : START-pc1/pc2
Execution time : Wed Sep 28 08:00:00 2011
Completion time : Wed Sep 28 08:00:02 2011
--------------------------------- Job output -----------------------------------
<Sysname>system-view
System View: return to User View with Ctrl+Z.
[Sysname]interface fortygige 1/1/1
[Sysname-FortyGigE1/1/1]undo shutdown
Job name : start-FortyGigE1/1/2
Schedule name : START-pc1/pc2
Execution time : Wed Sep 28 08:00:00 2011
Completion time : Wed Sep 28 08:00:02 2011
--------------------------------- Job output -----------------------------------
<Sysname>system-view
System View: return to User View with Ctrl+Z.
[Sysname]interface fortygige 1/1/2.
[Sysname-FortyGigE1/1/2]undo shutdown
Job name : shutdown-FortyGigE1/1/1
Schedule name : STOP-pc1/pc2
Execution time : Wed Sep 28 18:00:00 2011
Completion time : Wed Sep 28 18:00:01 2011
--------------------------------- Job output -----------------------------------
<Sysname>system-view
System View: return to User View with Ctrl+Z.
[Sysname]interface fortygige 1/1/1
[Sysname-FortyGigE1/1/1]shutdown
Job name : shutdown-FortyGigE1/1/2
Schedule name : STOP-pc1/pc2
Execution time : Wed Sep 28 18:00:00 2011
Completion time : Wed Sep 28 18:00:01 2011
--------------------------------- Job output -----------------------------------
<Sysname>system-view
System View: return to User View with Ctrl+Z.
[Sysname]interface fortygige 1/1/2
[Sysname-FortyGigE1/1/2]shutdown
Disabling password recovery capability
Password recovery capability controls console user access to the device configuration and SDRAM from Boot ROM menus.
If password recovery capability is enabled, a console user can access the device configuration without authentication to configure new passwords.
If password recovery capability is disabled, console users must restore the factory-default configuration before they can configure new passwords. Restoring the factory-default configuration deletes the next-startup configuration files.
To prevent illegal users to access the startup configuration files, disable password recovery capability.
Availability of Boot ROM menu options varies by password recovery capability setting. For more information, see the release notes.
To disable password recovery capability:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Disable password recovery capability. |
undo password-recovery enable |
By default, password recovery capability is enabled. |
Specifying the preferred airflow direction
The device supports the following airflow directions:
· From the port side to the power side.
· From the power side to the port side.
Select the correct fan tray model and set the preferred airflow direction to the airflow direction of the ventilation system in the equipment room. If a fan tray is not operating correctly or has a different airflow direction than the configured one, the system sends logs.
To specify the preferred airflow direction:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify the preferred airflow direction. |
fan prefer-direction slot slot-number { power-to-port | port-to-power } |
The default preferred airflow direction is from the power side to the port side. |
Setting the port status detection timer
To set the port status detection timer:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the port status detection timer. |
shutdown-interval time |
The default setting is 30 seconds. |
Configuring CPU usage monitoring
You can enable CPU usage monitoring so the system periodically samples and saves CPU usage. To examine recent CPU usage, use the display cpu-usage history command.
You can also set CPU usage thresholds. When a CPU usage threshold is reached, the device sends a trap.
To configure CPU usage monitoring:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable CPU usage monitoring. |
monitor cpu-usage enable [ slot slot-number [ cpu cpu-number ] ] |
By default, CPU usage monitoring is enabled. |
|
3. Set the CPU usage sampling interval. |
monitor cpu-usage interval interval-value [ slot slot-number [ cpu cpu-number ] ] |
By default, the CPU usage sampling interval is 1 minute. |
|
4. Set CPU usage thresholds. |
monitor cpu-usage threshold cpu-threshold [ slot slot-number [ cpu cpu-number ] ] |
By default, the CPU usage threshold is 99%. |
Setting memory thresholds
To ensure correct operation and improve memory utilization, the system monitors the memory usage and the amount of free memory space in real time.
· If the memory usage threshold is exceeded, the system generates and sends a trap.
· If a free-memory threshold is exceeded, the system generates an alarm notification or an alarm-removed notification and sends it to affected service modules or processes.
The device supports the following free-memory thresholds:
¡ Normal state threshold.
¡ Minor alarm threshold.
¡ Severe alarm threshold.
¡ Critical alarm threshold.
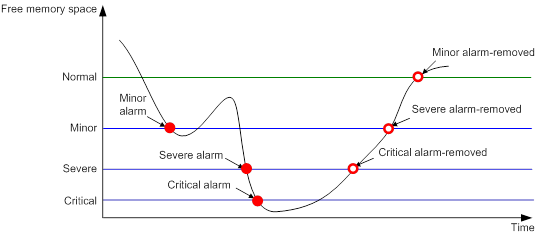
Table 3 and Figure 2 show how the device generates notifications based on the free-memory thresholds.
Table 3 Memory alarm notifications and memory alarm-removed notifications
|
Notification |
Triggering condition |
Remarks |
|
Minor alarm notification |
The amount of free memory space decreases to or below the minor alarm threshold for the first time. |
After generating and sending a minor alarm notification, the system does not generate and send any additional minor alarm notifications until the first minor alarm is removed. |
|
Severe alarm notification |
The amount of free memory space decreases to or below the severe alarm threshold for the first time. |
After generating and sending a severe alarm notification, the system does not generate and send any additional severe alarm notifications until the first severe alarm is removed. |
|
Critical alarm notification |
The amount of free memory space decreases to or below the critical alarm threshold for the first time. |
After generating and sending a critical alarm notification, the system does not generate and send any additional critical alarm notifications until the first critical alarm is removed. |
|
Critical alarm-removed notification |
The amount of free memory space increases to or above the severe alarm threshold. |
N/A |
|
Severe alarm-removed notification |
The amount of free memory space increases to or above the minor alarm threshold. |
N/A |
|
Minor alarm-removed notification |
The amount of free memory space increases to or above the normal state threshold. |
N/A |
Figure 2 Memory alarm notification and alarm-removed notification
To set memory thresholds:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set free-memory thresholds. |
memory-threshold [ slot slot-number [ cpu cpu-number ] ] minor minor-value severe severe-value critical critical-value normal normal-value |
The defaults are as follows: · Minor alarm threshold—96 MB. · Severe alarm threshold—64 MB. · Critical alarm threshold—48 MB. · Normal state threshold—128 MB. |
|
3. Set the memory usage threshold. |
memory-threshold usage [ slot slot-number [ cpu cpu-number ] ] memory-threshold |
By default, the memory usage threshold is 100%. |
Configuring the temperature alarm thresholds
The device monitors its temperature through temperature sensors, based on the following thresholds:
· Low-temperature threshold.
· High-temperature warning threshold.
· High-temperature alarming threshold.
When the temperature drops below the low-temperature threshold or reaches the high-temperature warning threshold, the device performs the following tasks:
· Logs the event.
· Sends a log message.
· Sends a trap.
When the temperature reaches the high-temperature alarming threshold, the device performs the following tasks:
· Logs the event.
· Sends log messages repeatedly.
· Sets the LEDs on the device panel.
To configure the temperature alarm thresholds:
Disabling all USB interfaces
You can use USB interfaces to upload or download files. By default, all USB interfaces are enabled. You can disable USB interfaces as needed.
To disable all USB interfaces:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Disable all USB interfaces. |
usb disable |
By default, all USB interfaces are enabled. Before executing this command, use the umount command to unmount all USB partitions. For more information about this command, see Fundamentals Command Reference. |
Verifying and diagnosing transceiver modules
Verifying transceiver modules
You can use one of the following methods to verify the genuineness of a transceiver module:
· Display the key parameters of a transceiver module, including its transceiver type, connector type, central wavelength of the transmit laser, transfer distance, and vendor name.
· Display its electronic label. The electronic label is a profile of the transceiver module and contains the permanent configuration, including the serial number, manufacturing date, and vendor name. The data is written to the storage component during debugging or testing.
To verify transceiver modules, execute the following commands in any view:
|
Task |
Command |
Remarks |
|
Display the key parameters of transceiver modules. |
display transceiver { interface [ interface-type interface-number ] } |
N/A |
|
Display the electrical label information of transceiver modules. |
display transceiver manuinfo interface [ interface-type interface-number ] } |
This command cannot display information for some transceiver modules. |
Diagnosing transceiver modules
The device provides the alarm and digital diagnosis functions for transceiver modules. When a transceiver module fails or is not operating correctly, you can perform the following tasks:
· Check the alarms that exist on the transceiver module to identify the fault source.
· Examine the key parameters monitored by the digital diagnosis function, including the temperature, voltage, laser bias current, TX power, and RX power.
To diagnose transceiver modules, execute the following commands in any view:
|
Task |
Command |
Remarks |
|
Display transceiver alarms. |
display transceiver alarm { interface [ interface-type interface-number ] } |
N/A |
|
Display the current values of the digital diagnosis parameters on transceiver modules. |
display transceiver diagnosis { interface [ interface-type interface-number ] } |
This command cannot display information about some transceiver modules. |
Restoring the factory-default settings and states
|
|
CAUTION: This feature is disruptive. Use this feature only when you cannot troubleshoot the device by using other methods, or you want to use the device in a different scenario. |
This feature performs the following tasks:
· Deletes all configuration files (.cfg files) in the root directories of the storage media.
· Deletes all log files (.log files in the folder /logfile).
· Clears all log information (in the log buffer), trap information, and debugging information.
· Restores the parameters for the Boot ROM options to the factory-default settings.
· Deletes all license files (.ak files).
· Deletes all files on an installed hot-swappable storage medium, such as a USB disk.
Before this operation, remove all hot-swappable storage media from the device.
After this operation, only the items required for device operation are retained, including the .bin files, the MAC addresses, and the electronic label information.
To restore the factory-default settings and states, use the following command in user view:
|
Task |
Command |
Remarks |
|
Restore the factory-default settings and states. |
restore factory-default |
This command takes effect after a device reboot. |
Displaying and maintaining device management configuration
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display the system time, date, local time zone, and daylight saving time. |
display clock |
|
Display the copyright statement. |
display copyright |
|
Display CPU usage statistics. |
display cpu-usage [ slot slot-number [ cpu cpu-number ] ] |
|
Display CPU usage monitoring settings. |
display cpu-usage configuration [ slot slot-number [ cpu cpu-number ] ] |
|
Display historical CPU usage statistics in a chart. |
display cpu-usage history [ job job-id ] [ slot slot-number [ cpu cpu-number ] ] |
|
Display hardware information. |
display device [ flash | usb ] [ slot slot-number [ subslot subslot-number ] | verbose ] |
|
Display the electronic label information of the device. |
display device manuinfo [ slot slot-number ] |
|
Display the electronic label information of a fan. |
display device manuinfo slot slot-number fan fan-id |
|
Display the electronic label information of a power supply. |
display device manuinfo slot slot-number power power-id |
|
Display the operating statistics for multiple feature modules. |
display diagnostic-information [ hardware | infrastructure | l2 | l3 | service ] [ file-name ] |
|
Display device temperature statistics. |
display environment [ slot slot-number ] |
|
Display the operating states of fans. |
display fan [ slot slot-number [ fan-id ] ] |
|
Display memory usage statistics. |
display memory [ slot slot-number [ cpu cpu-number ] ] |
|
Display memory usage thresholds. |
display memory-threshold [ slot slot-number [ cpu cpu-number ] ] |
|
Display power supply information. |
display power [ slot slot-number [ power-id ] ] |
|
Display job configuration information. |
display scheduler job [ job-name ] |
|
Display job execution log information. |
display scheduler logfile |
|
Display the automatic reboot schedule. |
display scheduler reboot |
|
Display schedule information. |
display scheduler schedule [ schedule-name ] |
|
Display system working mode information. |
display system-working-mode |
|
Display table capacity mode information. |
|
|
Display system version information. |
display version |
|
Display the startup software image upgrade history records of the master. |
display version-update-record |
|
Clear job execution log information. |
reset scheduler logfile |
