- Table of Contents
-
- 10-Security Configuration Guide
- 00-Preface
- 01-AAA Configuration
- 02-802.1X Configuration
- 03-MAC Authentication Configuration
- 04-Portal Configuration
- 05-Password Control Configuration
- 06-Public Key Configuration
- 07-IPsec Configuration
- 08-SSH Configuration
- 09-Packet-Filter Firewall Configuration
- 10-ALG Configuration
- 11-Session Management Configuration
- 12-TCP and ICMP Attack Protection Configuration
- 13-IP Source Guard Configuration
- 14-ARP Attack Protection Configuration
- 15-URPF Configuration
- 16-COPS Configuration
- 17-FIPS Configuration
- 18-PKI Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 09-Packet-Filter Firewall Configuration | 98.24 KB |
Configuring packet-filter firewall
Packet-filter firewall overview
Packet-filter firewall configuration example
|
|
NOTE: In this documentation, SPC cards refer to the cards prefixed with SPC, for example, SPC-GT48L. |
Packet-filter firewall overview
A firewall can block unauthorized accesses from the Internet to a protected network while allowing internal network users to access the Internet through, for example, WWW, or to send/receive emails. A firewall can also be used to control access to the Internet, for example, to permit only specific hosts within the organization to access the Internet.
Another application of firewall is to protect mainframes and important resources (such as data) on the internal network. Any access to protected data must be first filtered by the firewall, even if such an access is initiated by a user within the internal network.
A packet-filter firewall uses an ACL to filter IP packet. For each IP packet to be forwarded, the firewall first obtains the header information of the packet, including the number of the upper layer protocol carried by the IP layer, the source address, destination address, source port number, and destination port number of the packet. Then, it compares the obtained header information against the preset ACL rules and processes the packet according to the comparison result.
A packet-filter firewall supports fragment inspection and filtering. It checks the following elements:
· Packet type, which can be non-fragmented packet, first fragment, or non-first fragment.
· Layer 3 information of the packet, for matching against basic ACL rules and advanced ACL rules without information above Layer 3.
· Upper layer Information, for matching against advanced ACL rules containing information above Layer 3.
|
|
NOTE: For more information about ACL, see ACL and QoS Configuration Guide. |
Configuring packet filtering
You can apply an ACL to filter incoming or outgoing IP packets on an interface. When an ACL is applied to an interface, the time range-based filtering will also work at the same time.
A basic ACL defines rules based on only the Layer 3 source IP addresses to analyze and process data packets. An advanced ACL defines rules according to the information such as source and destination IP addresses of packets, the type of protocol over IP, and TCP/UDP source and destination ports.
Configuring IPv4 packet filtering on an interface
When you use the packet-filter forwarding-layer route outbound command or its undo form to configure the outbound packet filter on a VLAN interface to filter only Layer 3 unicast packets or all packets, follow these guidelines:
· The packet-filter forwarding-layer route outbound command is available only for SPC cards.
· The packet-filter forwarding-layer route outbound or its undo form must be configured before the firewall packet-filter { acl-number | name acl-name } outbound command. If you have configured the firewall packet-filter { acl-number | name acl-name } outbound command on a VLAN interface of an SPC card, you must remove the packet filter setting, configure the packet-filter forwarding-layer route outbound or its undo form, and then re-configure the firewall packet-filter { acl-number | name acl-name } outbound command on the VLAN interface.
· The packet-filter forwarding-layer route outbound command can cause the router to discard BFD packets. To avoid this problem, configure an advanced IPv4 ACL rule by using the rule [ rule-id ] permit udp destination-port range 3784 3785 command to permit BFD packets.
· The rule you add to an ACL that has been used by the firewall packet-filter command cannot take effect if hardware resources are insufficient or the firewall packet-filter command does not support the rule. Such rules are marked as uncompleted in the output of the display acl { acl-number | all | name acl-name } slot slot-number command. To successfully apply the rule, you must delete the rule and then reconfigure it when hardware resources are sufficient.
To configure IPv4 packet filtering on an interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the outbound packet filters on the VLAN interfaces of an SPC card to filter only Layer 3 unicast packets. |
packet-filter forwarding-layer route outbound |
Optional. By default, an outbound IPv4 packet filter filters all packets, including Layer 2 packets, on a VLAN interface. |
|
3. Enter interface view. |
interface interface-type interface-number |
N/A |
|
4. Apply an IPv4 ACL to the interface to filter IPv4 packets. |
firewall packet-filter { acl-number | name acl-name } { inbound | outbound } |
If the packet-filter forwarding-layer route outbound command is configured, the outbound packet filter handles only Layer 3 unicast packets; if not, the outbound packet filter handles all packets. IPv4 packets are not filtered by default. |
Configuring IPv6 packet filtering on an interface
IPv6 packet filtering is a basic firewall function based on an IPv6 ACL. You can configure IPv6 packet filtering in the inbound or outbound direction of an interface, and you can configure multiple IPv6 ACLs in each direction.
To configure IPv6 packet filtering on an interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Apply an IPv6 ACL to the interface to filter IPv6 packets. |
firewall packet-filter ipv6 { acl6-number | name acl6-name } { inbound | outbound } |
IPv6 packets are not filtered by default. |
|
|
NOTE: The rule you add to an ACL that has been used by the firewall packet-filter ipv6 command cannot take effect if hardware resources are insufficient or the firewall packet-filter ipv6 command does not support the rule. Such rules are marked as uncompleted in the output of the display acl { acl-number | all | name acl-name } slot slot-number command. To successfully apply the rule, you must delete the rule and then reconfigure it when hardware resources are sufficient. |
Configuring port mapping
Two mapping mechanisms exist: general port mapping and basic ACL–based host port mapping.
· A general port mapping refers to a mapping of a user-defined port number to an application layer protocol. If port 8080 is mapped to HTTP, for example, all TCP packets the destination port of which is port 8080 are regarded as HTTP packets.
· A host port mapping refers to a mapping of a user-defined port number to an application layer protocol for packets to some specific hosts. For example, you can establish a host port mapping so that all TCP packets using port 8080 sent to the network segment 10.110.0.0 are regarded as HTTP packets. The address range of hosts can be specified by means of a basic ACL.
To configure port mapping
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure mapping between the port and the application protocol. |
port-mapping application-name port port-number [ acl acl-number ] |
The application layer protocols supported by this function include FTP, GTP, H323, HTTP, RTSP, SCCP, SIP, SMTP, and SQLNET. |
Packet-filter firewall configuration example
Network requirements
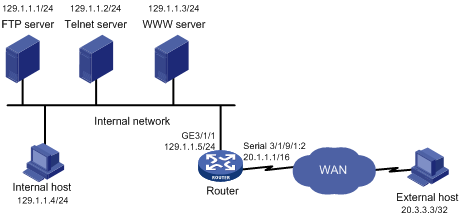
As shown in Figure 1:
· The internal network of a company is connected to Serial 3/1/9/1:2 of the router, and the internal users access the Internet through GigabitEthernet 3/1/1 of the router.
· The company provides WWW, FTP and Telnet services to the outside. The internal subnet of the company is 129.1.1.0, on which the internal FTP server address is 129.1.1.1, the Telnet server address is 129.1.1.2, the internal WWW server address is 129.1.1.3, and the public address of the company is 20.1.1.1. NAT is enabled on the router so that hosts on the internal network can access to the Internet and external hosts can access the internal servers.
· By using the firewall feature, the company intends to achieve the following aim: only specific users on external networks are given access to the internal servers, and only specific hosts on the internal network are permitted to access external networks.
· Assume that the IP address of a specific external user is 20.3.3.3.
Configuration procedure
# Enable the firewall function on the router.
<Router> system-view
[Router] firewall enable
# Create advanced ACL 3001.
[Router] acl number 3001
# Configure rules to permit specific hosts to access external networks and permit internal servers to access external networks.
[Router-acl-adv-3001] rule permit ip source 129.1.1.1 0
[Router-acl-adv-3001] rule permit ip source 129.1.1.2 0
[Router-acl-adv-3001] rule permit ip source 129.1.1.3 0
[Router-acl-adv-3001] rule permit ip source 129.1.1.4 0
# Configure a rule to prohibit all IP packets from passing the firewall.
[Router-acl-adv-3001] rule deny ip
[Router-acl-adv-3001] quit
# Create advanced ACL 3002.
[Router] acl number 3002
# Configure a rule to allow a specific external user to access internal servers.
[Router-acl-adv-3002] rule permit tcp source 20.3.3.3 0 destination 129.1.1.0 0.0.0.255
# Configure a rule to permit specific data (only packets of which the port number is greater than 1024) to get access to the internal network.
[Router-acl-adv-3002] rule permit tcp destination 20.1.1.1 0 destination-port gt 1024
[Router-acl-adv-3002] rule deny ip
[Router-acl-adv-3002] quit
# Apply ACL 3001 to filter packets that come in through GigabitEthernet 3/1/1.
[Router] interface gigabitEthernet 3/1/1
[Router-GigabitEthernet3/1/1] firewall packet-filter 3001 inbound
# Apply ACL 3002 to filter packets that come in through Serial 3/1/9/1:2.
[Router-GigabitEthernet3/1/1] quit
[Router] interface serial 3/1/9/1:2
[Router-Serial3/1/9/1:2] firewall packet-filter 3002 inbound
