- Table of Contents
-
- 10-Security Configuration Guide
- 00-Preface
- 01-AAA Configuration
- 02-802.1X Configuration
- 03-MAC Authentication Configuration
- 04-Portal Configuration
- 05-Password Control Configuration
- 06-Public Key Configuration
- 07-IPsec Configuration
- 08-SSH Configuration
- 09-Packet-Filter Firewall Configuration
- 10-ALG Configuration
- 11-Session Management Configuration
- 12-TCP and ICMP Attack Protection Configuration
- 13-IP Source Guard Configuration
- 14-ARP Attack Protection Configuration
- 15-URPF Configuration
- 16-COPS Configuration
- 17-FIPS Configuration
- 18-PKI Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 07-IPsec Configuration | 153.58 KB |
Contents
IPsec for IPv6 routing protocols
Applying an IPsec policy to an IPv6 routing protocol
Displaying and maintaining IPsec
IPsec for RIPng configuration example
IPsec overview
IP Security (IPsec) is a security framework defined by the Internet Engineering Task Force (IETF) for securing IP communications. It is a Layer 3 virtual private network (VPN) technology that transmits data in a secure tunnel established between two endpoints.
IPsec guarantees the confidentiality, integrity, and authenticity of data and provides anti-replay service at the IP layer in an insecure network environment.
· Confidentiality—The sender encrypts packets before transmitting them over the Internet.
· Data integrity—The receiver verifies the packets received from the sender to ensure they are not tampered with during transmission.
· Data origin authentication—The receiver verifies the authenticity of the sender.
· Anti-replay—The receiver examines packets and drops outdated or duplicate packets.
IPsec delivers these benefits:
· Reduced key negotiation overheads and simplified maintenance by supporting the Internet Key Exchange (IKE) protocol. IKE provides automatic key negotiation and automatic IPsec security association (SA) setup and maintenance.
· Good compatibility. IPsec can be applied to all IP-based application systems and services without any modification to them.
· Encryption on a per-packet rather than per-flow basis. Per-packet encryption allows for flexibility and greatly enhances IP security.
IPsec Implementation
IPsec comprises a set of protocols for IP data security, including Authentication Header (AH), Encapsulating Security Payload (ESP), IKE, and algorithms for authentication and encryption. AH and ESP provides security services and IKE performs key exchange.
IPsec provides two security mechanisms: authentication and encryption. The authentication mechanism allows the receiver of an IP packet to authenticate the sender and check if the packet has been tampered with. The encryption mechanism ensures data confidentiality and protects the data from being eavesdropped en route.
IPsec is available with two security protocols:
· AH (protocol 51), which provides data origin authentication, data integrity, and anti-replay services. For these purposes, an AH header is added to each IP packet. AH is suitable for transmitting non-critical data because it cannot prevent eavesdropping, although it can prevent data tampering. AH supports authentication algorithms such as Message Digest (MD5) and Secure Hash Algorithm (SHA-1).
· ESP (protocol 50), which provides data encryption in addition to data origin authentication, data integrity, and anti-replay services. ESP works by inserting an ESP header and an ESP trailer in IP packets. Unlike AH, ESP encrypts data before encapsulating the data to ensure data confidentiality. ESP supports encryption algorithms such as Data Encryption Standard (DES), 3DES, and Advanced Encryption Standard (AES), and authentication algorithms such as MD5 and SHA-1. The authentication function is optional to ESP.
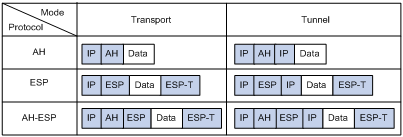
Both AH and ESP provide authentication services, but the authentication service provided by AH is stronger. In practice, you can choose either or both security protocols. When both AH and ESP are used, an IP packet is encapsulated first by ESP and then by AH. Figure 1 shows the format of IPsec packets.
Basic concepts
Security association
A security association is an agreement negotiated between two communicating parties called IPsec peers. It comprises a set of parameters for data protection, including security protocols, encapsulation mode, authentication and encryption algorithms, and shared keys and their lifetime. SAs can be set up manually or through IKE. The SR8800 routers support only manual SA creation.
An SA is unidirectional. At least two SAs are needed to protect data flows in a bidirectional communication. If two peers want to use both AH and ESP to protect data flows between them, they construct an independent SA for each protocol.
An SA is uniquely identified by a triplet, which consists of the security parameter index (SPI), destination IP address, and security protocol identifier (AH or ESP).
An SPI is a 32-bit number for uniquely identifying an SA. It is transmitted in the AH/ESP header. A manually configured SA requires an SPI to be specified manually for it. A manually configured SA never ages out.
Encapsulation modes
IPsec supports the following IP packet encapsulation modes:
· Tunnel mode—IPsec protects the entire IP packet, including both the IP header and the payload. It uses the entire IP packet to calculate an AH or ESP header, and then encapsulates the original IP packet and the AH or ESP header with a new IP header. If you use ESP, an ESP trailer is also encapsulated. Tunnel mode is typically used for protecting gateway-to-gateway communications.
· Transport mode—IPsec protects only the IP payload. It uses only the IP payload to calculate the AH or ESP header, and inserts the calculated header between the original IP header and payload. If you use ESP, an ESP trailer is also encapsulated. The transport mode is typically used for protecting host-to-host or host-to-gateway communications.
Figure 1 shows how the security protocols encapsulate an IP packet in different encapsulation modes.
Figure 1 Encapsulation by security protocols in different modes
Authentication algorithms and encryption algorithms
1. Authentication algorithms
IPsec uses hash algorithms to perform authentication. A hash algorithm produces a fixed-length digest for an arbitrary-length message. IPsec peers respectively calculate message digests for each packet. If the resulting digests are identical, the packet is considered intact.
IPsec supports the following hash algorithms for authentication:
¡ MD5, which takes a message of arbitrary length as input and produces a 128-bit message digest.
¡ SHA-1, which takes a message of a maximum length less than the 64th power of 2 in bits as input and produces a 160-bit message digest.
Compared with SHA-1, MD5 is faster but less secure.
2. Encryption algorithms
IPsec mainly uses symmetric encryption algorithms, which encrypt and decrypt data by using the same keys. The following encryption algorithms are available for IPsec on the device:
¡ Data Encryption Standard (DES), which encrypts a 64-bit plain text block with a 56-bit key. DES is the least secure but the fastest algorithm. It is sufficient for general security requirements.
¡ Triple DES (3DES), which encrypts plain text data with three 56-bit DES keys. The key length totals up to 168 bits. It provides moderate security strength and is slower than DES.
¡ Advanced Encryption Standard (AES), which encrypts plain text data with a 128-bit, 192-bit, or 256-bit key. AES provides the highest security strength and is slower than 3DES.
IPsec SA setup modes
The SR8800 routers support only the manual SA setup mode. You must manually configure all information that SAs need to use.
IPsec tunnel
An IPsec tunnel is a bidirectional channel created between two peers. An IPsec tunnel comprises one or more pairs of SAs.
IPsec for IPv6 routing protocols
The SR8800 implementation of IPsec only supports protecting routing information and defending attacks for these IPv6 routing protocols: OSPFv3, IPv6 BGP, and RIPng. IPsec enables these IPv6 routing protocols to encapsulate outbound protocol packets and de-encapsulate inbound protocol packets with the AH or ESP protocol. If an inbound protocol packet is not IPsec protected, or fails to be de-encapsulated, for example, due to decryption or authentication failure, the routing protocol discards that packet.
You must manually configure SA parameters in a security policy for IPv6 routing protocols. The IKE key exchange mechanism is applicable only to one-to-one communications. IPsec cannot implement automatic key exchange for one-to-many communications on a broadcast network, where devices must use the same SA parameters (SPI and key) to process packets for a routing protocol.
Protocols and standards
These protocols and standards are relevant to IPsec:
· RFC 2401, Security Architecture for the Internet Protocol
· RFC 2402, IP Authentication Header
· RFC 2406, IP Encapsulating Security Payload
· RFC 4552, Authentication/Confidentiality for OSPFv3
IPsec configuration task list
Complete the following tasks to configure IPsec for an IPv6 routing protocol:
|
Task |
Remarks |
|
|
Required. Configure IPsec protocols to specify authentication and encryption algorithms, and encapsulation mode. |
||
|
Required. Create an IPsec policy and assign IPsec proposals to the policy, and configure SA parameters. |
||
|
Required. Perform the task specific to the routing protocol. For more information, see Layer 3—IP Routing Configuration Guide. |
||
Configuring an IPsec proposal
An IPsec proposal, part of an IPsec policy, defines security parameters for IPsec SA negotiation, including the security protocol, the encryption and authentication algorithms, and the encapsulation mode.
To configure an IPsec proposal:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an IPsec proposal and enter its view. |
ipsec proposal proposal-name |
By default, no IPsec proposal exists. |
|
3. Specify the security protocol for the proposal. |
transform { ah | ah-esp | esp } |
Optional. ESP by default. |
|
4. Specify the security algorithms. |
· Specify the encryption algorithm for ESP: · Specify the authentication algorithm for ESP: · Specify the authentication algorithm for AH: |
Optional. Choose one or more commands according to the specified security protocol. By default, the encryption algorithm and authentication algorithm for ESP are DES and MD5, respectively, and the authentication algorithm for AH is MD5. |
|
5. Set the IP packet encapsulation mode to transport mode. |
encapsulation-mode transport |
Tunnel mode by default. Currently, the device supports only the transport mode. |
|
|
NOTE: · You can modify an IPsec proposal at any time, but the changes take effect only for SAs negotiated after your modification. To make the changes take effect for all SAs, use the reset ipsec sa to clear all SAs. · Only when a security protocol is selected, can you configure security algorithms for it. For example, you can specify the ESP-specific security algorithms only when you select ESP as the security protocol. ESP supports three IP packet protection schemes: encryption only, authentication only, or both encryption and authentication. · You can configure up to 10000 IPsec proposals. |
Configuring an IPsec policy
IPsec policies define which IPsec proposals should be used to protect which data flows. An IPsec policy is uniquely identified by its name and sequence number.
The SR8800 routers support only manual IPsec policies. You must manually configure all IPsec policy parameters, including the keys and SPIs for SAs.
Configuration guidelines
Follow these guidelines when configuring an IPsec policy for an IPv6 protocol:
· Within a certain routed network scope, the IPsec proposals used by the IPsec policies on all routers must have the same security protocols, security algorithms, and encapsulation mode. For OSPFv3, the scope can be directly connected neighbors or an OSPFv3 area. For RIPng, the scope can be directly connected neighbors or a RIPng process. For IPv6 BGP, the scope can be directly connected neighbors or a neighbor group.
· Each router must use the same SPIs and keys for its inbound and outbound SAs, and all routers must use the same SPIs and keys.
· Enter the keys in the same format on all routers. For example, if you enter the keys in hexadecimal format on one router, do so across the defined scope.
Configuration procedure
To configure an IPsec policy manually:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an IPsec policy and enter its view. |
ipsec policy policy-name seq-number manual |
By default, no IPsec policy exists. |
|
3. Assign IPsec proposals to the IPsec policy. |
proposal proposal-name |
By default, an IPsec policy references no IPsec proposal. |
|
4. Configure the SPIs for the SAs. |
sa spi { inbound | outbound } { ah | esp } spi-number |
N/A |
|
5. Configure keys for the SAs. |
· Configure an authentication key in hexadecimal for AH or ESP: · Configure an authentication key in characters for AH or ESP: · Configure a key in characters for ESP: · Configure an encryption key in hexadecimal for
ESP: |
Configure a key for AH, ESP, or both. If you configure a key in characters for ESP, the router automatically generates an authentication key and an encryption key for ESP. |
Applying an IPsec policy to an IPv6 routing protocol
Applying an IPsec policy to RIPng
To apply an IPsec policy in a process:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RIPng view. |
ripng [ process-id ] |
N/A |
|
3. Apply an IPsec policy in the process. |
enable ipsec-policy policy-name |
Not configured by default |
To apply an IPsec policy on an interface:
|
Step |
Command |
Remarks |
|
4. Enter system view. |
system-view |
N/A |
|
5. Enter interface view. |
interface interface-type interface-number |
N/A |
|
6. Apply an IPsec policy on the interface. |
ripng ipsec-policy policy-name |
Not configured by default |
Applying an IPsec policy to OSPFv3
To apply an IPsec policy in an area:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter OSPFv3 view. |
ospfv3 [ process-id ] |
N/A |
|
3. Enter OSPF area view. |
area area-id |
N/A |
|
4. Apply an IPsec policy in the area. |
enable ipsec-policy policy-name |
Not configured by default |
To apply an IPsec policy on an interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Apply an IPsec policy on the interface. |
ospfv3 ipsec-policy policy-name [ instance instance-id ] |
Not configured by default |
To apply an IPsec policy on a virtual link:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter OSPFv3 view. |
ospfv3 [ process-id ] |
N/A |
|
3. Enter OSPF area view. |
area area-id |
N/A |
|
4. Apply an IPsec policy on a virtual link. |
vlink-peer router-id [ hello seconds | retransmit seconds | trans-delay seconds | dead seconds | instance instance-id | ipsec-policy policy-name ] * |
Not configured by default |
Applying an IPsec policy to IPv6 BGP
To apply an IPsec policy to a peer/peer group
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Enter IPv6 address family view. |
ipv6-family |
N/A |
|
4. Apply an IPsec policy to a peer/peer group. |
peer { group-name | ip-address } ipsec-policy policy-name |
Not configured by default |
Displaying and maintaining IPsec
|
Task |
Command |
Remarks |
|
Display IPsec policy information. |
display ipsec policy [ brief | name policy-name [ seq-number ] ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display IPsec proposal information. |
display ipsec proposal [ proposal-name ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display IPsec SA information. |
display ipsec sa [ brief | policy policy-name [ seq-number ] ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display IPsec packet statistics. |
display ipsec statistics [ tunnel-id integer ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Clear SAs. |
reset ipsec sa [ policy policy-name [ seq-number ] ] |
Available in user view |
|
Clear IPsec statistics. |
reset ipsec statistics |
Available in user view |
IPsec for RIPng configuration example
|
|
NOTE: The IPsec configuration procedures for protecting OSPFv3 and IPv6 BGP are similar. For more information about RIPng, OSPFv3, and IPv6 BGP, see Layer 3—IP Routing Configuration Guide. |
Network requirements
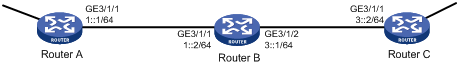
As shown in Figure 2, Router B connects Router A and Router C. These routers learn IPv6 routing information through RIPng. RIPng packets between any two routers must be transmitted through an IPsec tunnel that uses the security protocol ESP, encryption algorithm DES, and authentication algorithm SHA1-HMAC-96.
Figure 2 Network diagram for configuring IPsec for RIPng
Configuration considerations
To meet the requirements, you must perform the following configurations:
· Configure basic RIPng parameters.
· Configure a manual IPsec policy.
· Apply the IPsec policy to a RIPng process to protect RIPng packets in this process or to an interface to protect RIPng packets traveling through the interface.
Configuration procedure
1. Configure Router A
# Assign an IPv6 address to each interface. (Details not shown)
# Create a RIPng process and enable it on GigabitEthernet 3/1/1.
<RouterA> system-view
[RouterA] ripng 1
[RouterA-ripng-1] quit
[RouterA] interface GigabitEthernet 3/1/1
[RouterA-GigabitEthernet3/1/1] ripng 1 enable
[RouterA-GigabitEthernet3/1/1] quit
# Create an IPsec proposal named tran1, and set the encapsulation mode to transport mode, the security protocol to ESP, the encryption algorithm to DES, and authentication algorithm to SHA1-HMAC-96.
[RouterA] ipsec proposal tran1
[RouterA-ipsec-proposal-tran1] encapsulation-mode transport
[RouterA-ipsec-proposal-tran1] transform esp
[RouterA-ipsec-proposal-tran1] esp encryption-algorithm des
[RouterA-ipsec-proposal-tran1] esp authentication-algorithm sha1
[RouterA-ipsec-proposal-tran1] quit
# Create an IPsec policy named policy001, set the SPIs of the inbound and outbound SAs to 123456, and the keys for the inbound and outbound SAs using ESP to abcdefg.
[RouterA] ipsec policy policy001 10 manual
[RouterA-ipsec-policy-manual-policy001-10] proposal tran1
[RouterA-ipsec-policy-manual-policy001-10] sa spi outbound esp 123456
[RouterA-ipsec-policy-manual-policy001-10] sa spi inbound esp 123456
[RouterA-ipsec-policy-manual-policy001-10] sa string-key outbound esp abcdefg
[RouterA-ipsec-policy-manual-policy001-10] sa string-key inbound esp abcdefg
[RouterA-ipsec-policy-manual-policy001-10] quit
# Apply IPsec policy policy001 to the RIPng process.
[RouterA] ripng 1
[RouterA-ripng-1] enable ipsec-policy policy001
[RouterA-ripng-1] quit
2. Configure Router B
# Assign an IPv6 address to each interface. (Details not shown)
# Create a RIPng process and enable it on GigabitEthernet 3/1/1 and GigabitEthernet 3/1/2.
<RouterB> system-view
[RouterB] ripng 1
[RouterB-ripng-1] quit
[RouterB] interface GigabitEthernet 3/1/1
[RouterB-GigabitEthernet3/1/1] ripng 1 enable
[RouterB-GigabitEthernet3/1/1] quit
[RouterB] interface GigabitEthernet 3/1/2
[RouterB-GigabitEthernet3/1/2] ripng 1 enable
[RouterB-GigabitEthernet3/1/2] quit
# Create an IPsec proposal named tran1, and set the encapsulation mode to transport mode, the security protocol to ESP, the encryption algorithm to DES, and authentication algorithm to SHA1-HMAC-96.
[RouterB] ipsec proposal tran1
[RouterB-ipsec-proposal-tran1] encapsulation-mode transport
[RouterB-ipsec-proposal-tran1] transform esp
[RouterB-ipsec-proposal-tran1] esp encryption-algorithm des
[RouterB-ipsec-proposal-tran1] esp authentication-algorithm sha1
[RouterB-ipsec-proposal-tran1] quit
# Create an IPsec policy named policy001, configure the SPIs of the inbound and outbound SAs as 123456, and the keys for the inbound and outbound SAs using ESP as abcdefg.
[RouterB] ipsec policy policy001 10 manual
[RouterB-ipsec-policy-manual-policy001-10] proposal tran1
[RouterB-ipsec-policy-manual-policy001-10] sa spi outbound esp 123456
[RouterB-ipsec-policy-manual-policy001-10] sa spi inbound esp 123456
[RouterB-ipsec-policy-manual-policy001-10] sa string-key outbound esp abcdefg
[RouterB-ipsec-policy-manual-policy001-10] sa string-key inbound esp abcdefg
[RouterB-ipsec-policy-manual-policy001-10] quit
# Apply IPsec policy policy001 to the RIPng process.
[RouterB] ripng 1
[RouterB-ripng-1] enable ipsec-policy policy001
[RouterB-ripng-1] quit
3. Configure Router C
# Assign an IPv6 address to each interface. (Details not shown)
# Create a RIPng process and enable it on GigabitEthernet 3/1/1.
<RouterC> system-view
[RouterC] ripng 1
[RouterC-ripng-1] quit
[RouterC] interface GigabitEthernet 3/1/1
[RouterC-GigabitEthernet3/1/1] ripng 1 enable
[RouterC-GigabitEthernet3/1/1] quit
# Create an IPsec proposal named tran1, and set the encapsulation mode to transport mode, the security protocol to ESP, the encryption algorithm to DES, and authentication algorithm to SHA1-HMAC-96.
[RouterC] ipsec proposal tran1
[RouterC-ipsec-proposal-tran1] encapsulation-mode transport
[RouterC-ipsec-proposal-tran1] transform esp
[RouterC-ipsec-proposal-tran1] esp encryption-algorithm des
[RouterC-ipsec-proposal-tran1] esp authentication-algorithm sha1
[RouterC-ipsec-proposal-tran1] quit
# Create an IPsec policy named policy001, and configure the SPIs of the inbound and outbound SAs as 123456, and the keys for the inbound and outbound SAs using ESP as abcdefg.
[RouterC] ipsec policy policy001 10 manual
[RouterC-ipsec-policy-manual-policy001-10] proposal tran1
[RouterC-ipsec-policy-manual-policy001-10] sa spi outbound esp 123456
[RouterC-ipsec-policy-manual-policy001-10] sa spi inbound esp 123456
[RouterC-ipsec-policy-manual-policy001-10] sa string-key outbound esp abcdefg
[RouterC-ipsec-policy-manual-policy001-10] sa string-key inbound esp abcdefg
[RouterC-ipsec-policy-manual-policy001-10] quit
# Apply IPsec policy policy001 to the RIPng process.
[RouterC] ripng 1
[RouterC-ripng-1] enable ipsec-policy policy001
[RouterC-ripng-1] quit
4. Verify the configuration
After the configuration, Router A, Router B, and Router C learn IPv6 routing information through RIPng. SAs are set up successfully, and the IPsec tunnel between two peers is up for protecting the RIPng packets.
Using the display ripng command on Router A, you will see the running status and configuration information of the specified RIPng process. The output shows that IPsec policy policy001 is applied to this process successfully.
<RouterA> display ripng 1
RIPng process : 1
Preference : 100
Checkzero : Enabled
Default Cost : 0
Maximum number of balanced paths : 8
Update time : 30 sec(s) Timeout time : 180 sec(s)
Suppress time : 120 sec(s) Garbage-Collect time : 120 sec(s)
Number of periodic updates sent : 186
Number of trigger updates sent : 1
IPsec policy name: policy001, SPI: 123456
Using the display ipsec sa command on Router A, you will see the information about the inbound and outbound SAs.
<RouterA> display ipsec sa
===============================
Protocol: RIPng
===============================
-----------------------------
IPsec policy name: "policy001"
sequence number: 10
mode: manual
-----------------------------
connection id: 1
encapsulation mode: transport
perfect forward secrecy:
tunnel:
flow:
[inbound ESP SAs]
spi: 123456 (0x3039)
proposal: ESP-ENCRYPT-DES ESP-AUTH-SHA1
No duration limit for this sa
[outbound ESP SAs]
spi: 123456 (0x3039)
proposal: ESP-ENCRYPT-DES ESP-AUTH-SHA1
No duration limit for this sa
Similarly, you can view the information on Router B and Router C. (Details not shown)
