- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-NAT configuration | 212.92 KB |
Contents
Restrictions and guidelines: NAT configuration
Interface-based NAT tasks at a glance
Restrictions and guidelines for static NAT configuration
Prerequisites for static NAT configuration
Configuring outbound one-to-one static NAT
Configuring outbound net-to-net static NAT
Configuring inbound one-to-one static NAT
Configuring inbound net-to-net static NAT
Restrictions and guidelines for dynamic NAT configuration
Configuring outbound dynamic NAT
Configuring inbound dynamic NAT
NAT overview
Network Address Translation (NAT) translates an IP address in the IP packet header to another IP address. Typically, NAT is configured on gateways to enable private hosts to access external networks and external hosts to access private network resources.
Basic NAT concepts
The following describes basic NAT concepts:
· NAT device—A device configured with NAT. Typically, NAT is configured on the edge device that connects the internal and external networks.
· NAT interface—An interface configured with NAT.
· NAT rule—A rule that NAT follows to translate addresses. The priority of a rule is determined by its location on the rule list. A NAT rule appearing earlier on the rule list has a higher priority for packet matching.
· NAT address—A public IP address used for address translation, and this address is reachable from the external network. The NAT address can be manually assigned or dynamically obtained.
· NAT entry—Stores the mapping between a private IP address and a public IP address. For more information, see "NAT entries."
· Easy IP—Uses the IP address of an interface as the NAT address. The IP address of the interface can be manually assigned or be obtained through DHCP or PPPoE.
Basic NAT operating mechanism
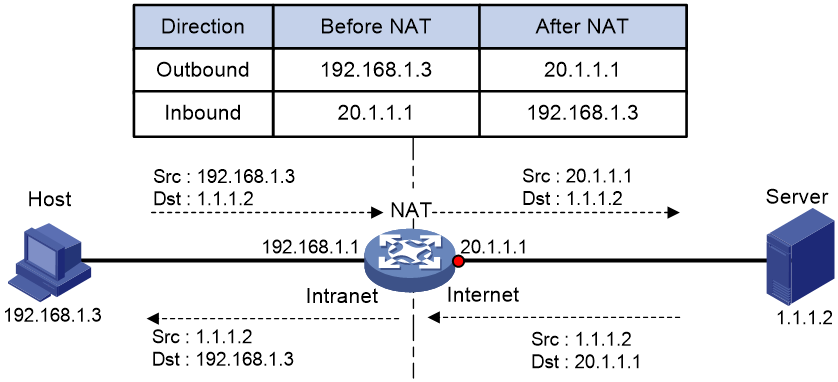
Figure 1 shows the basic NAT operating mechanism.
2. Upon receiving a response from the server, NAT translates the destination public address to the private address, and forwards the packet to the host.
The NAT operation is transparent to the terminals (the host and the server). NAT hides the private network from the external users and shows that the IP address of the internal host is 20.1.1.1.
NAT applications
Traditional NAT
Traditional NAT is configured on the interface that connects to the public network. It translates the source IP addresses of outgoing packets and destination IP addresses of incoming packets.
Twice NAT
Twice NAT translates the destination IP address on the receiving interface, and the source IP address on the sending interface. The receiving and sending interfaces are both NAT interfaces.
Twice NAT allows VPNs with overlapping addresses to access each other.
Bidirectional NAT
NAT translates the source and destination IP addresses of incoming packets on the receiving interface and outgoing packets on the sending interface.
Bidirectional NAT supports active access to external network resources from internal users when the internal and external IP addresses overlap.
NAT control
You can use ACLs to implement NAT control. The match criteria in the ACLs include the source IP address, source port number, destination IP address, destination port number, transport layer protocol, and VPN instance. Only packets permitted by an ACL are processed by NAT.
NAT translation methods
Static NAT
Static NAT creates a fixed mapping between a private address and a public address. It supports connections initiated from internal users to external network and from external users to the internal network. Static NAT applies to regular communications.
Dynamic NAT
Dynamic NAT uses an address pool to translate addresses. It applies to the scenario where a large number of internal users access the external network.
NO-PAT
Not Port Address Translation (NO-PAT) translates a private IP address to an IP public address. The public IP address cannot be used by another internal host until it is released.
NO-PAT supports all IP packets.
PAT
Port Address Translation (PAT) translates multiple private IP addresses to a single public IP address by mapping the private IP address and source port to the public IP address and a unique port. PAT supports TCP and UDP packets.
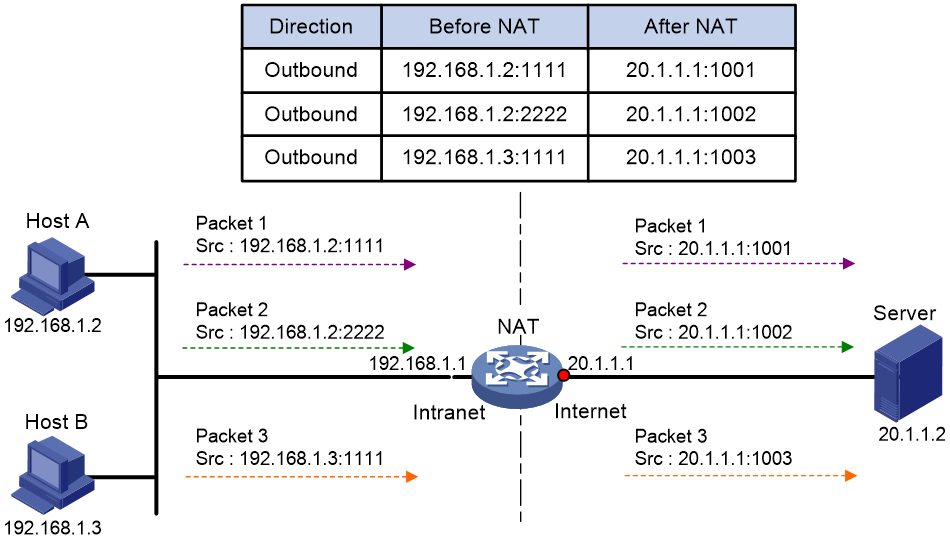
Figure 2 PAT operation
As shown in Figure 2, PAT translates the source IP addresses of the three packets to the same IP public address and translates their port numbers to different port numbers. Upon receiving a response, PAT translates the destination address and port number of the response, and forwards it to the target host.
NAT entries
NAT session entry
NAT creates a NAT session entry for a session and creates an address mapping for the first packet in the session.
A NAT session entry contains extended NAT information, such as interface and translation method. Subsequent packets of the session are translated by using this entry.
· If the direction of the subsequent packets is the same as the direction of the first translated packets, NAT performs the source and destination address translation the same as the first packet.
· If the direction of the subsequent packets is the opposite direction, NAT perform reverse address translation. For example, if the source address of the first packets is translated, then the destination address of the subsequent packets is translated.
NO-PAT entry
A NO-PAT entry maps a private address to a public address. The same mapping applies to subsequent connections originating from the same source IP.
A NO-PAT entry ages out after all related NAT session entries age out.
VRF-aware NAT
VRF-aware NAT allows users from different VRF (VPN instances) to access external networks and to access each other.
1. Upon receiving a request from a user in a VRF to an external network, NAT performs the following tasks:
¡ Translates the private source IP address and port number to a public IP address and port number.
¡ Records the VRF information, such as the VRF name.
2. When a response packet arrives, NAT performs the following tasks:
¡ Translates the destination public IP address and port number to the private IP address and port number.
¡ Forwards the packet to the target VRF.
Configuring NAT
Restrictions and guidelines: NAT configuration
The general restrictions and guidelines are as follows:
· You can use an ACL in a NAT rule to identify the IP addresses to be translated. The match criteria include the source IP address, source port number, destination IP address, destination port number, transport layer protocol, and VPN instance. For more information about ACLs, see ACL and QoS Configuration Guide.
· If NAT is configured on only one output interface in a dual uplink network, do not add the two output interfaces to the same security zone. Doing so will cause communication interruption. For more information about security zone, see Fundamentals Configuration Guide.
· If you perform all the translation methods, the NAT rules are sorted in the following descending order:
a. Static NAT.
b. Dynamic NAT.
· The product does not support configuring NAT in IRF or M-LAG scenarios.
NAT tasks at a glance
Interface-based NAT tasks at a glance
To configure interface-based NAT, perform the following tasks:
1. Configuring a translation method on an interface
Configuring static NAT
Restrictions and guidelines for static NAT configuration
Typically, configure inbound static NAT with outbound dynamic NAT or outbound static NAT to implement bidirectional NAT.
For a hardware forwarding device to perform NAT, apply a QoS policy to the inbound direction of user traffic.
Prerequisites for static NAT configuration
Before configuring static NAT, you must perform the following tasks:
· Configure an ACL to identify the IP addresses to be translated. For more information about ACLs, see ACL and QoS Configuration Guide.
· Manually add a route for inbound static NAT. Use local-ip or local-network as the destination address, and use global-ip, an address in global-network, or the next hop directly connected to the output interface as the next hop.
Configuring outbound one-to-one static NAT
About this task
For address translation from a private IP address to a public IP address, configure outbound one-to-one static NAT on the interface connected to the external network.
· When the source IP address of an outgoing packet matches the local-ip, the source IP address is translated into the global-ip.
· When the destination IP address of an incoming packet matches the global-ip, the destination IP address is translated into the local-ip.
Restrictions and guidelines
If multiple outbound one-to-one static mappings are available for one private IP address, the device uses the following rules to determine their match order:
· A mapping with a smaller priority value has a higher priority.
· If the mappings have no priority value or their priority values are the same, their match order is determined by the ACLs in the mappings:
¡ Mappings with named ACLs have higher priority than mappings with numbered ACLs.
¡ Mappings with named ACLs are matched in alphanumeric order of their ACL names.
¡ Mappings with numbered ACLs are matched in descending order of their ACL numbers.
Procedure
1. Enter system view.
system-view
2. Configure a one-to-one mapping for outbound static NAT.
nat static outbound local-ip [ vpn-instance local-vpn-instance-name ] global-ip [ vpn-instance global-vpn-instance-name ] [ acl { ipv4-acl-number | name ipv4-acl-name } [ reversible ] ] [ rule rule-name ] [ priority priority ]
3. (Optional.) Rearrange outbound one-to-one mapping rules to adjust their priorities.
nat static outbound rule move nat-rule-name1 { after | before } nat-rule-name2
By default, the priority of a mapping rule is determined by its location on the rule list. A NAT rule appearing earlier on the rule list has a higher priority for packet matching.
4. Enter interface view.
interface interface-type interface-number
5. Enable static NAT on the interface.
nat static enable
By default, static NAT is disabled.
Configuring outbound net-to-net static NAT
About this task
For address translation from a private network to a public network, configure outbound net-to-net static NAT on the interface connected to the external network.
· When the source IP address of an outgoing packet matches the private address range, the source IP address is translated into a public address in the public address range.
· When the destination IP address of an incoming packet matches the public address range, the destination IP address is translated into a private address in the private address range.
Restrictions and guidelines
If multiple outbound net-to-net static mappings are available for translating addresses in a private IP network, the device uses the following rules to determine their match order:
· A mapping with a smaller priority value has a higher priority.
· If the mappings have no priority value or their priority values are the same, their match order is determined by the ACLs in the mappings:
¡ Mappings with named ACLs have higher priority than mappings with numbered ACLs.
¡ Mappings with named ACLs are matched in alphanumeric order of their ACL names.
¡ Mappings with numbered ACLs are matched in descending order of their ACL numbers.
Procedure
1. Enter system view.
system-view
2. Configure a net-to-net mapping for outbound static NAT.
nat static outbound net-to-net local-start-address local-end-address global global-network { mask-length | mask } [ acl { ipv4-acl-number | name ipv4-acl-name } [ reversible ] ] [ rule rule-name ] [ priority priority ]
3. (Optional.) Rearrange outbound net-to-net mapping rules to adjust their priorities.
nat static outbound net-to-net rule move nat-rule-name1 { after | before } nat-rule-name2
By default, the priority of a mapping rule is determined by its location on the rule list. A NAT rule appearing earlier on the rule list has a higher priority for packet matching.
4. Enter interface view.
interface interface-type interface-number
5. Enable static NAT on the interface.
nat static enable
By default, static NAT is disabled.
Configuring inbound one-to-one static NAT
About this task
For address translation from a public IP address to a private IP address, configure inbound one-to-one static NAT.
· When the source IP address of an incoming packet matches the global-ip, the source IP address is translated into the local-ip.
· When the destination IP address of an outgoing packet matches the local-ip, the destination IP address is translated into the global-ip.
Restrictions and guidelines
If multiple inbound one-to-one static mappings are available for translating one public IP address, the device uses the following rules to determine their match order:
· A mapping with a smaller priority value has a higher priority.
· If the mappings have no priority value or their priority values are the same, their match order is determined by the ACLs in the mappings:
¡ Mappings with named ACLs have higher priority than mappings with numbered ACLs.
¡ Mappings with named ACLs are matched in alphanumeric order of their ACL names.
¡ Mappings with numbered ACLs are matched in descending order of their ACL numbers.
Procedure
1. Enter system view.
system-view
2. Configure a one-to-one mapping for inbound static NAT.
nat static inbound global-ip local-ip [ acl { ipv4-acl-number | name ipv4-acl-name } [ reversible ] ] [ rule rule-name ] [ priority priority ]
3. (Optional.) Rearrange inbound one-to-one mapping rules to adjust their priorities.
nat static inbound rule move nat-rule-name1 { after | before } nat-rule-name2
By default, the priority of a rule is determined by its location on the rule list. A NAT rule appearing earlier on the rule list has a higher priority for packet matching.
4. Enter interface view.
interface interface-type interface-number
5. Enable static NAT on the interface.
nat static enable
By default, static NAT is disabled.
Configuring inbound net-to-net static NAT
About this task
For address translation from a public network to a private network, configure inbound net-to-net static NAT.
· When the source IP address of an incoming packet matches the public address range, the source IP address is translated into a private address in the private address range.
· When the destination IP address of an outgoing packet matches the private address range, the destination IP address is translated into a public address in the public address range.
Restrictions and guidelines
If multiple inbound net-to-net static mappings are available for translating addresses in a public network, the device uses the following rules to determine their match order:
· A mapping with a smaller priority value has a higher priority.
· If the mappings have no priority value or their priority values are the same, their match order is determined by the ACLs in the mappings:
¡ Mappings with named ACLs have higher priority than mappings with numbered ACLs.
¡ Mappings with named ACLs are matched in alphanumeric order of their ACL names.
¡ Mappings with numbered ACLs are matched in descending order of their ACL numbers.
Procedure
1. Enter system view.
system-view
2. Configure a net-to-net mapping for inbound static NAT.
nat static inbound net-to-net global-start-address global-end-address local local-network { mask-length | mask } [ acl { ipv4-acl-number | name ipv4-acl-name } [ reversible ] ] [ rule rule-name ] [ priority priority ]
3. (Optional.) Rearrange inbound net-to-net mapping rules to adjust their priorities.
nat static inbound net-to-net rule move nat-rule-name1 { after | before } nat-rule-name2
By default, the priority of a mapping rule is determined by its location on the rule list. A NAT rule appearing earlier on the rule list has a higher priority for packet matching.
4. Enter interface view.
interface interface-type interface-number
5. Enable static NAT on the interface.
nat static enable
By default, static NAT is disabled.
Configuring dynamic NAT
Restrictions and guidelines for dynamic NAT configuration
You can configure multiple inbound or outbound dynamic NAT rules. The device follows these guidelines to determine their match order:
· A NAT rule with a smaller priority value has a higher priority.
· If NAT rules have no priority value or their priority values are the same, their match order is determined by ACLs in the rules:
¡ NAT rules with named ACLs have higher priority than NAT rules with numbered ACLs.
¡ NAT rules with named ACLs are matched in alphanumeric order of their ACL names.
¡ NAT rules with numbered ACLs are matched in descending order of their ACL numbers.
· The NAT rule configured with no ACL has the lowest priority.
For a hardware forwarding device to perform NAT, apply a QoS policy to the inbound direction of user traffic.
Prerequisites
Before configuring dynamic NAT, you must perform the following tasks:
· Configure an ACL to identify the IP addresses to be translated. For more information about ACLs, see ACL and QoS Configuration Guide.
· Determine whether to enable the Easy IP feature. If you use the IP address of an interface as the NAT address, you are configuring Easy IP.
· Determine a public IP address pool for address translation.
· Determine whether to translate port numbers. Use NO-PAT to translate only IP addresses and PAT to translate both IP addresses and port numbers.
Configuring outbound dynamic NAT
About this task
To translate private IP addresses into public IP addresses, configure outbound dynamic NAT on the interface connected to the external network.
Procedure
1. Enter system view.
system-view
2. Create a NAT address group and enter its view.
nat address-group group-id
3. Add an address range to the address group.
address start-address end-address
By default, no address ranges exist.
You can add multiple address ranges to an address group, but the address ranges must not overlap.
4. Return to system view.
quit
5. Enter interface view.
interface interface-type interface-number
6. Configure outbound dynamic NAT. Choose the options to configure as needed:
¡ Configure NO-PAT.
nat outbound [ ipv4-acl-number | name ipv4-acl-name ] address-group group-id no-pat [ reversible ] [ rule rule-name ] [ priority priority ]
¡ Configure PAT.
nat outbound [ ipv4-acl-number | name ipv4-acl-name ] [ address-group group-id ] [ port-preserved ] [ rule rule-name ] [ priority priority ]
You can configure multiple outbound dynamic NAT rules on an interface.
|
Parameter |
Description |
|
address-group |
If you do not specify this keyword, the IP address of the interface is used as the NAT address. Easy IP is implemented. |
|
no-pat reversible |
If you specify these keywords, you enable reverse address translation. Reverse address translation uses existing NO-PAT entries to translate the destination address for connections actively initiated from the external network to the internal network. The destination address is translated into the private IP address in the matching NO-PAT entry. |
7. (Optional.) Rearrange outbound dynamic NAT rules to adjust their priorities.
nat outbound rule move nat-rule-name1 { after | before } nat-rule-name2
By default, the priority of a rule is determined by its location on the rule list. A NAT rule appearing earlier on the rule list has a higher priority for packet matching.
Configuring inbound dynamic NAT
Restrictions and guidelines
Do not configure inbound dynamic NAT alone. Typically, inbound dynamic NAT functions with outbound dynamic NAT or outbound static NAT to implement bidirectional NAT.
As a best practice, manually create a route because it takes time to automatically add routes.
Procedure
1. Enter system view.
system-view
2. Create a NAT address group and enter its view.
nat address-group group-id
3. Add an address range to the address group.
address start-address end-address
By default, no address ranges exist.
You can add multiple address ranges to an address group, but the address ranges in address groups must not overlap.
4. Return to system view.
quit
5. Enter interface view.
interface interface-type interface-number
6. Configure inbound dynamic NAT.
nat inbound { ipv4-acl-number | name ipv4-acl-name } address-group group-id [ no-pat [ reversible ] [ add-route ] ] [ rule rule-name ] [ priority priority ]
You can configure multiple inbound dynamic NAT rules on an interface.
|
Parameter |
Description |
|
no-pat reversible |
If you specify these keywords, you enable reverse address translation. Reverse address translation uses existing NO-PAT entries to translate the destination address for connections actively initiated from the external network to the internal network. The destination address is translated into the private IP address in the matching NO-PAT entry. |
|
add-route |
This keyword enables the device to automatically add a route destined for the private address when an inbound dynamic NAT rule is matched. The output interface is the NAT interface, and the next hop is the source address before translation. If you do not specify this keyword, you must manually add the route. |
7. (Optional.) Rearrange inbound dynamic NAT rules to adjust their priorities.
nat inbound rule move nat-rule-name1 { after | before } nat-rule-name2
By default, the priority of a rule is determined by its location on the rule list. A NAT rule appearing earlier on the rule list has a higher priority for packet matching.
Verifying and maintaining NAT
Verifying NAT configuration
Perform all display tasks in in any view.
· Display all NAT configuration information.
display nat all
· Display NAT address group information.
display nat address-group [ group-id ]
· Display inbound dynamic NAT configuration.
display nat inbound
· Display outbound dynamic NAT configuration.
display nat outbound
Monitoring NAT running status
Perform display tasks in any view.
· Display information about NAT NO-PAT entries.
display nat no-pat [ slot slot-number ]
· Display NAT sessions.
display nat session [ { source-ip source-ip | destination-ip destination-ip } * [ vpn-instance vpn -instance-name ] ] [ slot slot-number ] [ verbose ]
Displaying NAT statistics
Perform all display tasks in in any view.
· Display NAT statistics.
display nat statistics [ summary ] [ slot slot-number ]
Clearing NAT sessions
To clear NAT sessions, execute the following command in user view:
reset nat session [ protocol { tcp | udp } ] [ slot slot-number ]
NAT configuration examples
Example: Configuring outbound one-to-one static NAT
Network configuration
Configure static NAT to allow the host at 10.110.10.8/24 to access the Internet.
Procedure
# Specify IP addresses for the interfaces on the switch. (Details not shown.)
# Configure a one-to-one static NAT mapping between the private address 10.110.10.8 and the public address 202.38.1.100.
<Switch> system-view
[Switch] nat static outbound 10.110.10.8 202.38.1.100
# Enable static NAT on Vlan-interface 200.
[Switch] interface vlan-interface 200
[Switch-Vlan-interface200] nat static enable
[Switch-Vlan-interface200] quit
# Configure ACL 2000 to identify packets from subnet 10.110.10.0/24 to pass through.
[Switch] acl basic 2000
[Switch-acl-ipv4-basic-2000] rule permit source 10.110.10.0 0.0.0.255
[Switch-acl-ipv4-basic-2000] quit
# Configure traffic class nat to match advanced ACL 2000.
[Switch] traffic classifier nat
[Switch-classifier-nat] if-match acl 2000
[Switch-classifier-nat] quit
# Configure traffic behavior nat to redirect packets matching ACL 2000 to the CPU.
[Switch] traffic behavior nat
[Switch-behavior-nat] redirect cpu
[Switch-behavior-nat] quit
# Configure a QoS policy and associate the traffic class with the traffic behavior.
[Switch] qos policy p1
[Switch-qospolicy-p1] classifier nat behavior nat
[Switch-qospolicy-p1] quit
# Apply the QoS policy to the inbound traffic on GigabitEthernet 1/0/1.
[Switch] interface gigabitethernet 1/0/1
[Switch-GigabitEthernet1/0/1] qos apply policy p1 inbound
[Switch-GigabitEthernet1/0/1] quit
Verifying the configuration
# Verify that the host at 10.110.10.8/24 can access the server on the Internet. (Details not shown.)
# Display static NAT configuration.
[Switch] display nat static
Static NAT mappings:
Totally 1 outbound static NAT mappings.
IP-to-IP:
Local IP : 10.110.10.8
Global IP : 202.38.1.100
Config status: Active
Interfaces enabled with static NAT:
Totally 1 interfaces enabled with static NAT.
Interface: Vlan-interface200
Config status: Active
# Display NAT session information.
[Switch] display nat session verbose
Initiator:
Source IP/port: 10.110.10.8/42496
Destination IP/port: 202.38.1.111/2048
DS-Lite tunnel peer: -
VPN instance/VLAN ID/VLL ID: -/-/-
Protocol: UDP(17)
Inbound interface: Vlan-interface100
Responder:
Source IP/port: 202.38.1.111/42496
Destination IP/port: 202.38.1.100/0
DS-Lite tunnel peer: -
VPN instance/VLAN ID/VLL ID: -/-/-
Protocol: UDP(17)
Inbound interface: Vlan-interface200
State: UDP_REPLY
Application: GENERAL_UDP
Start time: 2023-06-29 10:06:55 TTL: 27s
Initiator->Responder: 5 packets 420 bytes
Responder->Initiator: 5 packets 420 bytes
Total sessions found: 1
Example: Configuring outbound dynamic NAT
Network configuration
As shown in Figure 4, a company has a private address 192.168.0.0/16 and two public IP addresses 202.38.1.2 and 202.38.1.3. Configure outbound dynamic NAT to allow only internal users on subnet 192.168.1.0/24 to access the Internet.
Procedure
# Specify IP addresses for the interfaces on the switch. (Details not shown.)
# Configure address group 0 and add an address range from 202.38.1.2 to 202.38.1.3.
<Switch> system-view
[Switch] nat address-group 0
[Switch-address-group-0] address 202.38.1.2 202.38.1.3
[Switch-address-group-0] quit
# Configure ACL 2000 to identify packets from subnet 192.168.1.0/24.
[Switch] acl basic 2000
[Switch-acl-ipv4-basic-2000] rule permit source 192.168.1.0 0.0.0.255
[Switch-acl-ipv4-basic-2000] quit
# Enable outbound dynamic PAT on Vlan-interface 200. The source IP addresses of the packets permitted by ACL 2000 are translated into the addresses in address group 0.
[Switch] interface vlan-interface 200
[Switch-Vlan-interface200] nat outbound 2000 address-group 0
[Switch-Vlan-interface200] quit
# Configure traffic class nat to match advanced ACL 2000.
[Switch] traffic classifier nat
[Switch-classifier-nat] if-match acl 2000
[Switch-classifier-nat] quit
# Configure traffic behavior nat to redirect packets matching ACL 2000 to the CPU.
[Switch] traffic behavior nat
[Switch-behavior-nat] redirect cpu
[Switch-behavior-nat] quit
# Configure a QoS policy and associate the traffic class with the traffic behavior.
[Switch] qos policy p1
[Switch-qospolicy-p1] classifier nat behavior nat
[Switch-qospolicy-p1] quit
# Apply the QoS policy to the inbound traffic on GigabitEthernet 1/0/1.
[Switch] interface gigabitethernet 1/0/1
[Switch-GigabitEthernet1/0/1] qos apply policy p1 inbound
[Switch-GigabitEthernet1/0/1] quit
Verifying the configuration
# Verify that Host A can access the WWW server, but Host B and Host C cannot. (Details not shown.)
# Display all NAT configuration information.
[Switch] display nat all
NAT address group information:
Totally 1 NAT address groups.
Address group 0:
Port range: 1-65535
Address information:
Start address End address
202.38.1.2 202.38.1.3
NAT outbound information:
Totallu 1 NAT outbound rules.
Interface: Vlan-interface200
ACL: 2000 Address group: 0 Port-preserved: N
NO-PAT: N Reversible: N
Config status: Active
NAT logging:
Log enable : Disabled
Flow-begin : Disabled
Flow-end : Disabled
Flow-active : Disabled
Port-block-assign : Disabled
Port-block-withdraw : Disabled
Alarm : Disabled
NAT mapping behavior:
Mapping mode : Address and Port-Dependent
ACL : ---
Config status: Active
Static NAT load balancing: Disabled
# Verify that Host A access to the WWW server generates NAT sessions.
[Switch] display nat session verbose
Initiator:
Source IP/port: 192.168.1.10/52992
Destination IP/port: 200.1.1.10/2048
DS-Lite tunnel peer: -
VPN instance/VLAN ID/VLL ID: -/-/-
Protocol: UDP(17)
Inbound interface: Vlan-interface100
Responder:
Source IP/port: 200.1.1.10/4
Destination IP/port: 202.38.1.3/0
DS-Lite tunnel peer: -
VPN instance/VLAN ID/VLL ID: -/-/-
Protocol: UDP(17)
Inbound interface: Vlan-interface200
State: UDP_REPLY
Application: GENERAL_UDP
Start time: 2023-06-29 10:39:49 TTL: 12s
Initiator->Responder: 1 packets 84 bytes
Responder->Initiator: 1 packets 84 bytes
Total sessions found: 1