- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Security Policy Troubleshooting Guide | 44.39 KB |
Troubleshooting security policies
Traffic of an application permitted by a security policy is blocked
Symptom
In the security policy, an application and the basic protocols it relies on are configured to be permitted. However, the traffic of this application is still blocked.
Common causes
The following are the common causes for this type of issue:
· The traffic of this application hit a security policy rule with a higher priority, and the rule action is drop.
· The traffic of this application hit the expected security policy, but the traffic was eventually discarded by DPI.
Troubleshooting flow
The troubleshooting flow for issues of this type is as follows:
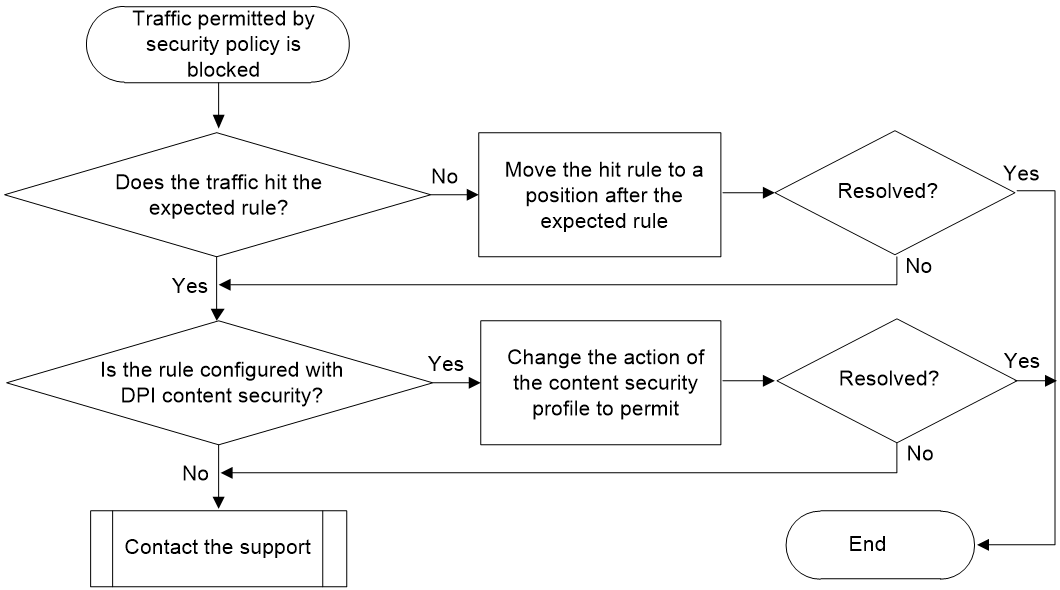
1. Examine whether the security policy rule hit by the traffic is the expected rule.
2. Examine the current security policy rule to verify if DPI content security is configured.
Figure 1 shows the troubleshooting flowchart.
Figure 1 Flowchart for troubleshooting traffic blocking issue of a permitted application
Solution
1. Examine whether the security policy rule hit by the traffic is the expected rule.
# Configure an ACL as a filtering condition. In this example, the source address is 10.10.10.10, destination address is 20.20.20.20, and destination port is 80.
[Device]acl advanced 3999
[Device-acl-ipv4-adv-3999]rule 0 permit tcp source 10.10.10.10 0 destination 20.20.20.20 0 destination-port eq 80
# Enable security policy debugging to view the traffic hit status.
<Device>debugging security-policy packet ip acl 3999
This command is CPU intensive and might affect ongoing services. Are you sure you want to continue? [Y/N]:y
<Device>terminal monitor
<Device>terminal debugging
# View the debug information and view the SecurityPolicy field to determine if the traffic hits the expected security policy rule.
¡ If the traffic hits another rule and the rule action is deny, it indicates that the traffic is discarded. In this case, edit this rule to permit the traffic or move the rule to a position after the expected hit rule.
*May 23 14:30:16:909 2022 H3C FILTER/7/PACKET: -Context=1; The packet is denied. Src-Zone=Trust, Dst-Zone=Local;If-In=GigabitEthernet0/0/1(1), If-Out=xxx(1284); Packet Info:Src-IP=10.10.10.10, Dst-IP=20.20.20.20, VPN-Instance=, Src-MacAddr=9ce8-95c9-6289,Src-Port=68, Dst-Port=80, Protocol=UDP(17), Application=invalid(0),Terminal=invalid(0), SecurityPolicy=1, Rule-ID=1.
¡ If the traffic hits the expected rule, and the action is permit, it indicates that the traffic might be discarded by DPI. In this case, proceed to step 2.
*May 23 14:30:16:909 2022 H3C FILTER/7/PACKET: -Context=1; The packet is permitted. Src-Zone=Trust, Dst-Zone=Local;If-In=GigabitEthernet0/0/1(1), If-Out=xxx(1284); Packet Info:Src-IP=10.10.10.10, Dst-IP=20.20.20.20, VPN-Instance=, Src-MacAddr=9ce8-95c9-6289,Src-Port=68, Dst-Port=80, Protocol=UDP(17), Application=invalid(0),Terminal=invalid(0), SecurityPolicy=1, Rule-ID=1.
2. Examine whether content security is configured for the security policy.
a. Execute the display security-policy rule name rule-name command to view the current security policy rule configuration.
[Device] display security-policy rule 0 name testpolicy
rule 0 name testpolicy
action pass
profile test
application name QQ mailbox
application name http
application name https
application name dns
application name tcp
b. Examine if the security policy rule is configured with a DPI content security profile. If the traffic is blocked by the content security profile, determine whether the traffic is safe and require to be permitted. If the traffic requires permitting, modify the action of the corresponding content security profile policy.
3. If the issue persists, collect the following information and contact Technical Support:
¡ Results of each step.
¡ Device configuration file.
Related alarm and log messages
Alarm messages
N/A
Log messages
N/A