- Table of Contents
-
- 04-DPI Configuration Guide
- 00-Preface
- 01-DPI overview
- 02-DPI engine configuration
- 03-IPS configuration
- 04-URL filtering configuration
- 05-Data filtering configuration
- 06-File filtering configuration
- 07-Anti-virus configuration
- 08-Data analysis center configuration
- 09-WAF configuration
- 10-Proxy policy configuration
- 11-IP reputation configuration
- 12-Domain reputation configuration
- 13-APT defense configuration
- 14-DLP configuration
- 15-Content moderation configuration
- 16-Network asset scan configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 15-Content moderation configuration | 217.83 KB |
Configuring content moderation
Restrictions: Hardware compatibility with content moderation
Enabling receiving of content moderation result
Configuring content moderation
About content moderation
Content moderation is a technology that intelligently inspects and recognizes sensitive contents in files transported over networks. It uses signature models trained by deep learning algorithms to recognize pornographic or terroristic contents in images or videos and measure the sensitivity level of the sensitive contents.
Content moderation is applicable only to files transmitted through FTP or SMTP.
Content moderation mechanism
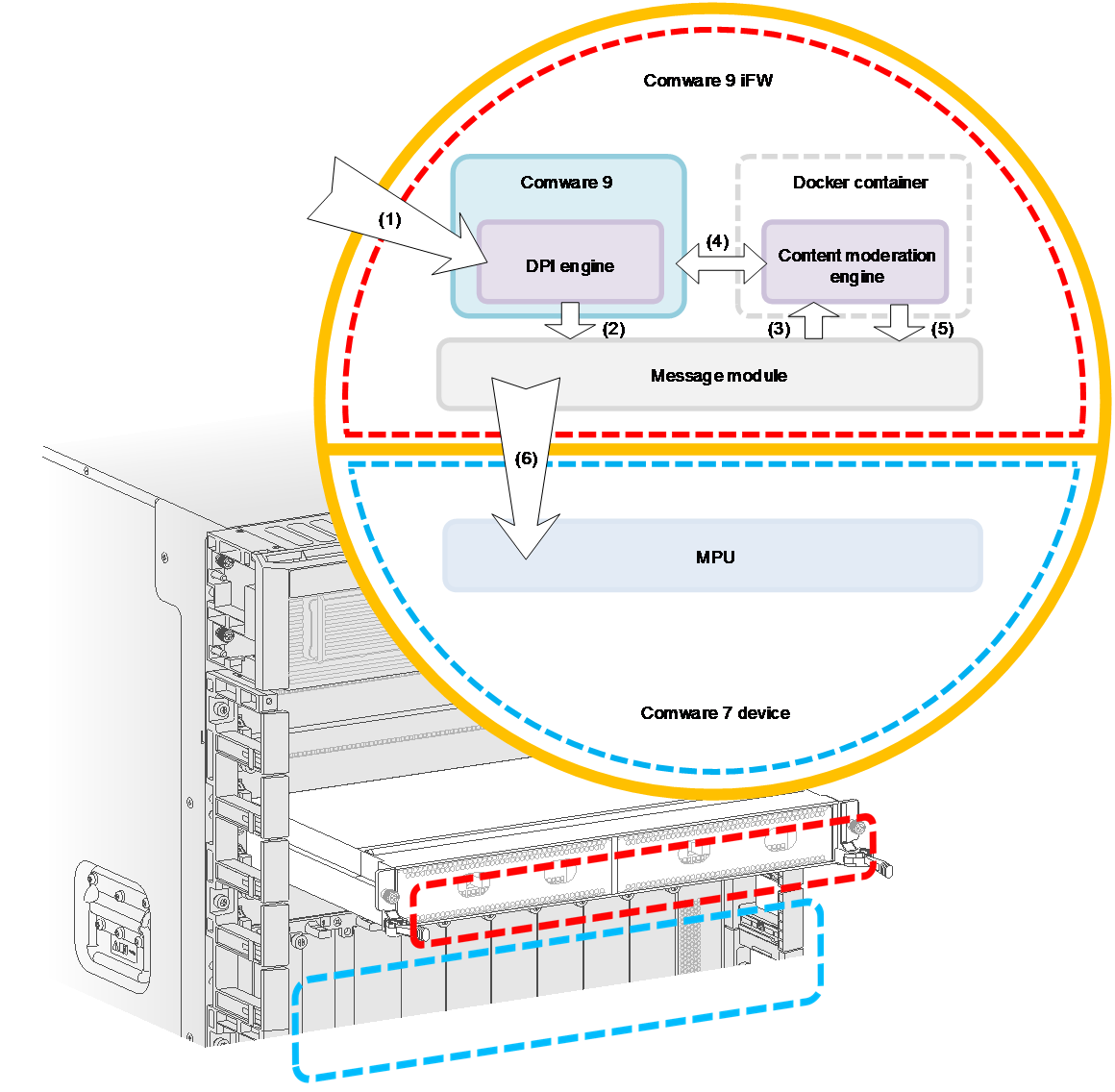
As shown in Figure 1, a content moderation system includes the following components:
· DPI engine—A Comware 9 module that provides file extraction, file decompression, and disassembly of compound files.
· Content moderation engine—An application deployed in a Docker container that identifies sensitive contents (including images and videos) in files.
· Message module—A module that exchanges messages between the DPI engine and the content moderation engine.
Figure 1 Content moderation system
Content moderation operates as follows:
1. The DPI engine on a Comware 9 device extracts files from the traffic to be inspected.
2. The DPI engine sends information about the files to the message module on the Comware 9 device.
3. The message module submits a content inspection task to the content moderation engine on the Comware 9 device.
4. The content moderation engine obtains the files to be inspected from the Comware 9 device and starts content inspection.
5. The content moderation engine sends the inspection result to the message module.
6. The message module sends the inspection result to a Comware 7 device for presentation.
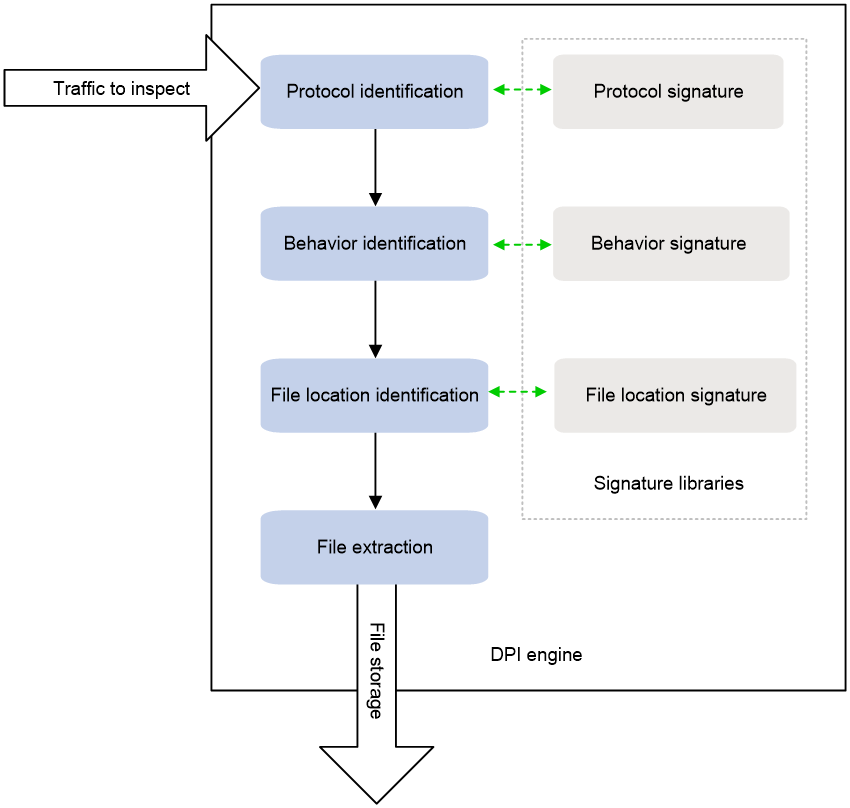
DPI engine
As shown in Figure 2, the DPI engine identifies the application information and extracts files in a packet as follows:
1. Identifies the application layer of the packet, FTP or SMTP, for example.
2. Identifies the behavior of the packet, for example, upload a file or send an email.
3. Searches the signature libraries to identify the start and end locations of the file to be extracted in the packet.
4. Extracts the file from the packet.
5. Processes the file as needed:
¡ For a compressed file, the DPI engine decompresses the file.
¡ For a compound file, the DPI engine extracts images and videos from the file as independent files.
6. Saves the extracted files locally on the device and assigns a unique URL to each file for the content moderation engine to access.
Figure 2 DPI engine operation process
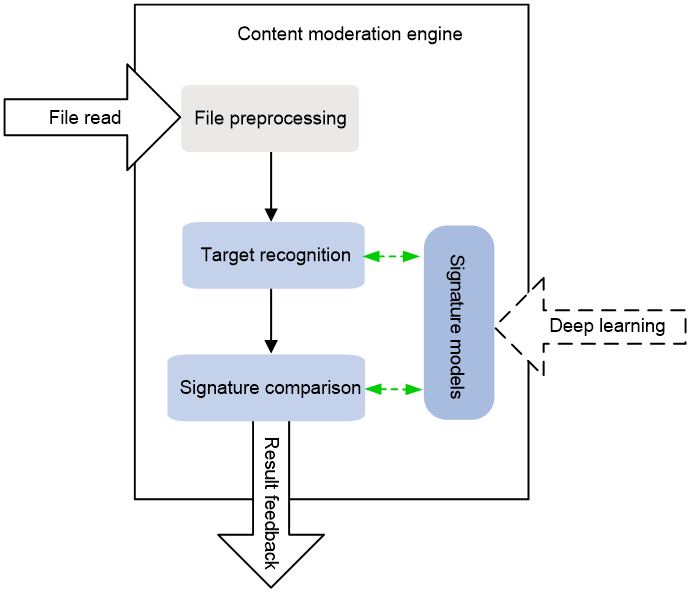
Content moderation engine
The content moderation engine is deployed with a series of offline sensitive content signature models, which are neutral networks trained by deep learning algorithms and support periodic update.
Figure 3 shows the process that the content moderation engine performs sensitive content identification on files extracted by the DPI engine.
1. Accesses the files to be inspected on the Comware 9 device at the URLs assigned by the DPI engine.
2. Standardizes the files, including light compensation, gray adjustment, and noise filtering.
3. Recognizes signatures (such as faces and flags) in the images or video frames based on the neural networks and cuts out the signatures.
4. Compares the signatures with sensitive content signature models and recognizes sensitive contents.
5. Sends the recognition result to a Comware 7 device for presentation.
Figure 3 Content moderation engine operation process
Restrictions: Hardware compatibility with content moderation
|
Hardware platform |
Module type |
Content moderation compatibility |
|
M9006 M9010 M9014 |
Blade IV firewall module |
No |
|
Blade V firewall module |
No |
|
|
NAT module |
No |
|
|
M9010-GM |
Encryption module |
No |
|
M9016-V |
Blade V firewall module |
No |
|
M9008-S M9012-S |
Blade IV firewall module |
No |
|
Intrusion prevention service (IPS) module |
No |
|
|
Video network gateway module |
No |
|
|
M9008-S-V |
Blade IV firewall module |
No |
|
M9000-AI-E4 |
Blade V firewall module |
No |
|
M9000-AI-E8 M9000-AI-E16 |
Blade V firewall module |
Yes |
|
M9000-AK001 |
Blade V firewall module |
No |
|
M9000-X06 M9000-X06-B M9000-X06-B-G M9000-X06-G M9000-X10 |
Blade VI firewall module |
Yes |
|
M9000-AI-X06 M9000-AI-X10 |
Blade VI firewall module |
Yes |
Enabling receiving of content moderation result
About this task
In the content moderation service, Comware 7 devices present the content moderation results. After you enable this feature on a Comware 7 device, the Comware 7 device can receive content moderation results from the Comware 9 device and records logs.
Prerequisites
Before you enable this feature on the device, you must configure content moderation on a Comware 9 device. For more information, see the configuration manual for the Comware 9 device.
Procedure
1. Enter system view.
system-view
2. Enable receiving of content moderation results.
content-moderation enable
By default, receiving of content moderation result is disabled.