- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 04-EVPN VPWS configuration | 590.65 KB |
Contents
Remote connection establishment
Configuring a Layer 3 interface with Ethernet or VLAN encapsulation
Configuring EVPN route advertisement
Restrictions and guidelines for EVPN route advertisement configuration
Enabling BGP to advertise BGP EVPN routes
Configuring optimal route selection and route advertisement settings
Mapping an AC to a cross-connect
About mapping an AC to a cross-connect
Restrictions and guidelines for mapping an AC to a cross-connect
Mapping a Layer 3 interface to a cross-connect
Configuring EVPN VPWS multihoming
Restrictions and guidelines for EVPN VPWS multihoming
Assigning an ESI to an interface
Configuring the DF election algorithm
Setting the redundancy mode on an interface
Disabling advertisement of EVPN multihoming routes
Verifying and maintaining EVPN VPWS
Displaying EVPN running status and statistics
Displaying cross-connect group configuration and running status
Displaying AC configuration and running status
Displaying PW configuration and running status
EVPN VPWS configuration examples
Example: Configuring a remote connection between singlehomed sites
Example: Configuring EVPN VPWS multihoming
Example: Configuring PW concatenation
Example: Configuring inter-AS option A
Example: Configuring inter-AS option B
Example: Configuring inter-AS option C
Configuring EVPN VPWS
About EVPN VPWS
EVPN Virtual Private Wire Service (VPWS) is a Layer 2 VPN technology that uses MP-BGP for BGP EVPN route advertisement in the control plane and MPLS for forwarding in the data plane. EVPN VPWS provides point-to-point forwarding services for users by using ACs and PWs associated with cross-connects without MAC address table lookup.
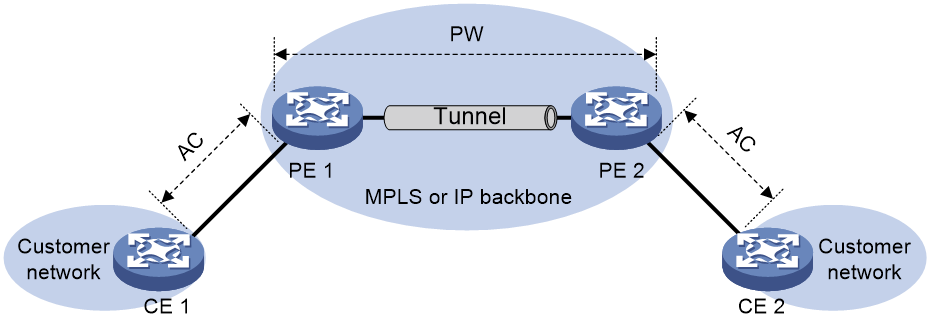
EVPN VPWS network model
As shown in Figure 1, an EVPN VPWS network contains the following devices:
· Customer edge (CE)—Customer device directly connected to the service provider network.
· Provider edge (PE)—Service provider device connected to CEs. PEs provide access to the EVPN VPWS network and forward traffic between customer network sites by using public tunnels.
A PE uses ACs, PWs, tunnels, and cross-connects to provide EVPN VPWS services.
· Attachment circuit (AC)—A physical or virtual link between a CE and a PE.
· Pseudowire (PW)—A virtual bidirectional connection between two PEs. A PW comprises a pair of LSPs in opposite directions.
· Public tunnel—A connection that carries one or more PWs across the MPLS or IP backbone. A public tunnel can be an LSP, GRE tunnel, or MPLS TE tunnel.
· Cross-connect—A connection formed by two physical or virtual circuits such as ACs and PWs. It switches packets between the two physical or virtual circuits. Cross-connects include AC to AC cross-connect and AC to PW cross-connect.
Remote connection establishment
To set up a remote EVPN VPWS connection:
1. Set up a public tunnel to carry one or more PWs between PEs.
2. Set up a PW to connect customer networks.
3. Set up an AC between a PE and a CE.
4. Bind the AC to the PW.
After the PE receives packets from the AC, it adds the PW label into the packets and sends the packets to the peer PE through the public tunnel.
After the peer PE receives the packets from the public tunnel, it removes the PW label of the packets and forwards the packets to the AC bound to the PW.
Public tunnel establishment
The public tunnel can be an LSP, MPLS TE, or GRE tunnel.
If multiple public tunnels are set up between two PEs, you can configure a tunnel policy to control tunnel selection. For more information about tunnel policies, see MPLS Configuration Guide.
If a PW is established over an LSP or MPLS TE tunnel, packets on the PW have two labels. The outer label is the public LSP or MPLS TE tunnel label that MPLS uses to forward the packet to the peer PE. The inner label is the PW label that the peer PE uses to forward the packet to the destination CE.
PW establishment
A PW is established between two PEs based on the local and remote service IDs configured on the PEs. In an EVPN VPWS network, each PE advertises its remote service ID through Ethernet auto-discovery routes and compares received remote service IDs with its local service ID. A PE establishes a unidirectional LSP to a peer If the remote service ID advertised by the peer matches the local service ID. PW establishment is finished when two LSPs in opposite directions are established between two PEs.
AC establishment
For EVPN VPWS, an AC is associated with a cross-connect and can be a Layer 3 Ethernet interface or Layer 3 Ethernet subinterface on a PE.
AC-to-PW bindings
For PEs to forward packets between an AC and a PW, bind the AC to the PW.
EVPN VPWS multihoming
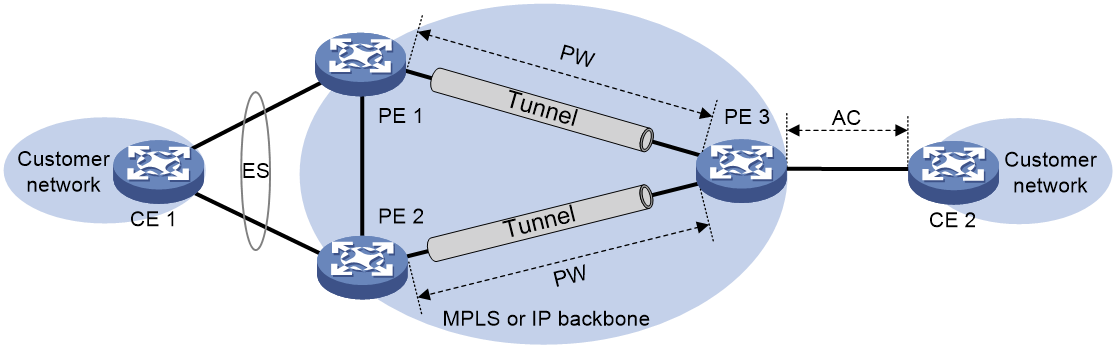
About this task
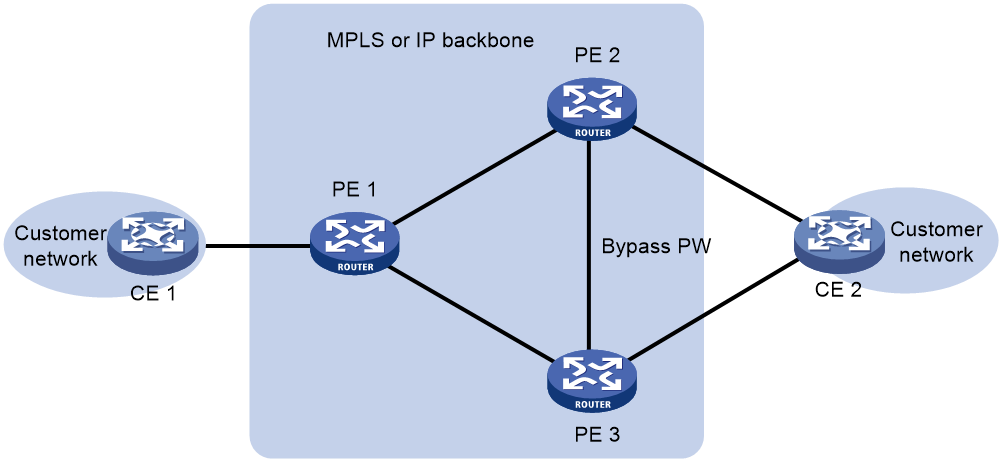
As shown in Figure 2, EVPN VPWS supports deploying multiple PEs at a site for redundancy and high availability. On the redundant PEs, Ethernet links connected to the site form an ES that is uniquely identified by an ESI. EVPN VPWS supports only dualhoming.
Figure 2 EVPN VPWS multihoming
Redundancy mode
The device supports single-active redundancy mode and all-active redundancy mode of EVPN VPWS multihoming.
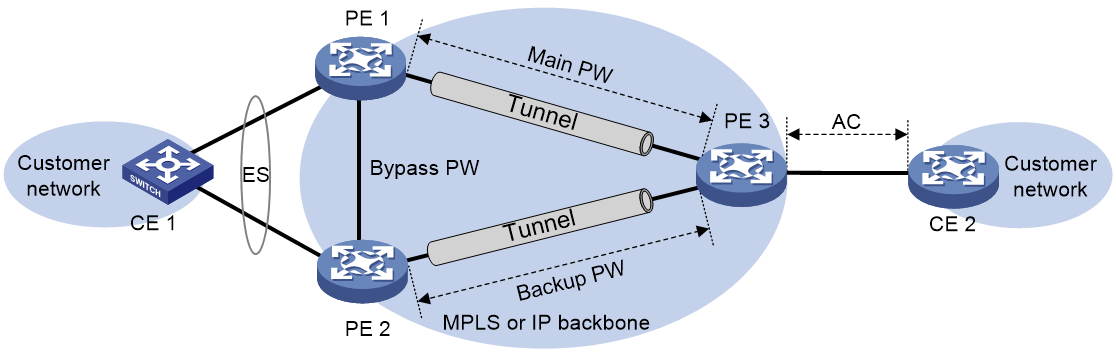
· Single-active mode—This mode allows one of the redundant PWs to forward traffic, as shown in Figure 3. When the main PW becomes unavailable because of device failure or link failure, traffic is switched to the backup PW for forwarding.
· All-active mode—This mode allows all redundant PWs to a multihomed site to load share traffic.
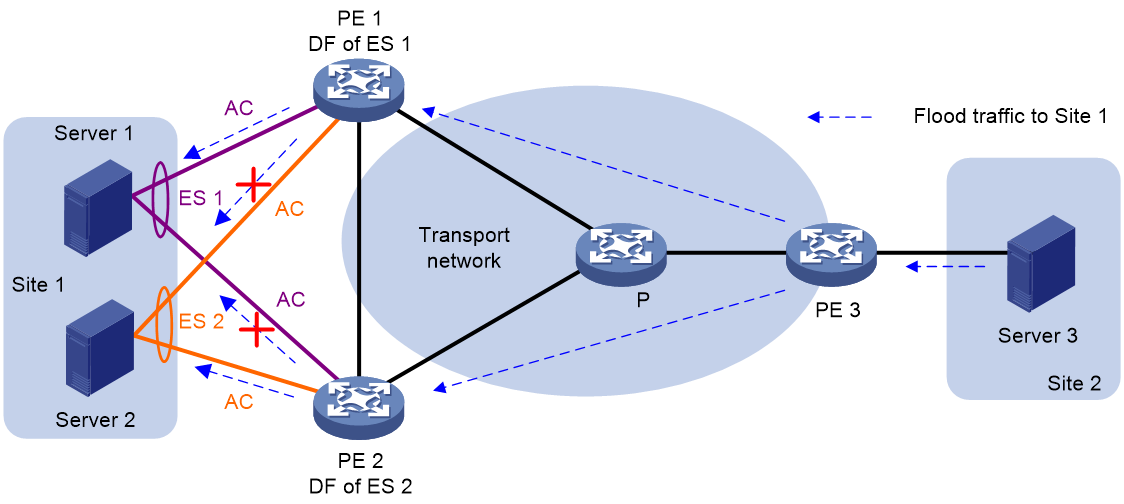
About DF election
In single-active mode, a DF is elected from the redundant PEs to determine the main PW. PEs that fail the election are assigned the BDF role. The PWs on BDFs do not forward traffic.
Redundant PEs at a site send Ethernet segment routes to one another to advertise ES and PE IP mappings. A PE accepts the Ethernet segment routes only when it is configured with an ESI. Then, the PEs select a DF based on the ES and PE IP mappings. DF election can be performed by using a VLAN tag-based algorithm or preference-based algorithm.
Figure 4 DF election
VLAN tag-based DF election
PEs select a DF for each AC based on the VLAN tag and PE IP address as follows:
1. Arrange source IP addresses in Ethernet segment routes with the same ESI in ascending order and assign a sequence number to each IP address, starting from 0.
2. Divide the lowest VLAN ID permitted on an AC by the number of the redundant PEs, and match the reminder to the sequence numbers of IP addresses.
3. Assign the DF role to the PE that uses the IP address with the matching sequence number.
The following uses PE 1 and PE 2 in Figure 5 as an example to explain the DF election procedure:
4. PE 1 and PE 2 send Ethernet segment routes to each other.
5. The PEs assign sequence numbers 0 and 1 to IP addresses 1.1.1.1 and 2.2.2.2 in the Ethernet segment routes, respectively.
6. The PEs divide 4 (the lowest VLAN ID permitted by the ACs) by 2 (the number of redundant PEs), and match the reminder 0 to the sequence numbers of the IP addresses.
7. The DF role is assigned to PE 1 at 1.1.1.1.
Figure 5 VLAN tag-based DF election
Preference-based DF election
PEs select a DF for each ES based on the DF election preference, the Don't Preempt Me (DP) bit in Ethernet segment routes, and PE IP address. The DP bit can be set to one of the following values:
· 1—DF preemption is disabled. A DF retains its role when a new DF is elected.
· 0—DF preemption is enabled.
Preference-based DF election uses the following rules to select a DF for an ES:
· The PE with higher preference becomes the DF.
· If two PEs have the same preference, the PE with the DP bit set to 1 becomes the DF. If both of the PEs have the DP bit set to 1, the PE with a lower IP address becomes the DF.
As shown in Figure 6, PE 2 is the DF for ES 1, and PE 1 is the DF for ES 2.
Figure 6 Preference-based DF election
FRR for EVPN VPWS
About FRR
Fast reroute (FRR) helps reduce the traffic loss caused by AC or PW failure on an EVPN VPWS network. FRR includes local FRR and remote FRR.
Local FRR
Local FRR enables two PEs at a multihomed EVPN VPWS network site to set up a bypass PW between them.
As shown in Figure 7, CE 2 is dualhomed to PE 2 and PE 3. When the AC on PE 2 fails, PE 2 advertises the local unreachable event to PE 1 and PE 3 for PE 1 to switch traffic to the PW to PE 3. In this situation, PE 3 drops the packets that PE 1 sends before it is notified of the local unreachable event. To resolve this issue, enable local FRR on PE 2 and PE 3. When receiving packets from PE 1 after PE 2's AC fails, PE 2 forwards the packets to PE 3 over the bypass PW to prevent traffic loss.
Remote FRR
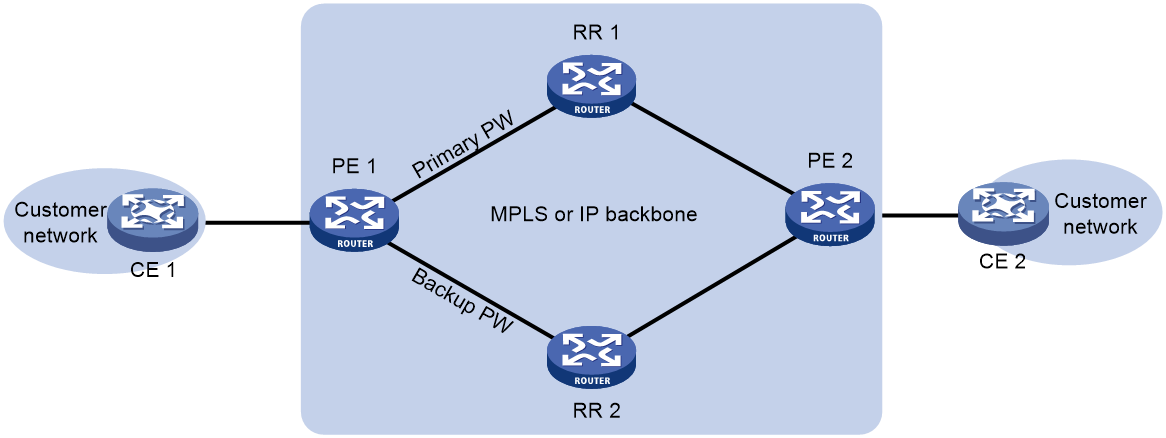
Remote FRR enables two PEs on an EVPN VPWS network to set up a primary PW and a backup PW between them to ensure high availability. This feature is applicable to both multihoming and singlehoming scenarios.
As shown in Figure 8, PE 1 and PE 2 are connected by RR 1 and RR 2. The RRs change the next hop attribute of routes and reassign MPLS labels to them based on routing policies when reflecting the routes. PE 1 and PE 2 select only RR 1 or RR 2 when establishing a PW. For high availability, you can enable remote FRR on PE 1 for it to set up PWs to both RRs. PE 1 uses the primary PW to forward traffic as long as it is available. When the primary PW fails, PE 1 switches traffic to the backup PW. For more information about optimal route selection on PE 1, see BGP configuration in Layer 3—IP Routing Configuration Guide.
Control word
The control word field is between the MPLS label stack and the Layer 2 data. It carries control information for the Layer 2 frame, for example, the sequence number.
The control word feature has the following functions:
· Avoids fragment disorder. In multipath forwarding, fragments received might be disordered. The control word feature reorders the fragments according to the sequence number carried in the control word field.
· Identifies the original payload length for packets that include padding.
The control word field is optional for EVPN PWs. You can configure whether to carry the control word field in packets sent on the PW. If you enable the control word feature on both PEs, packets transmitted on the PW carry the control word field. Otherwise, the packets do not carry the control word field.
L2VPN flow label
Packets carrying different types of traffic might be transmitted through the same PW and encapsulated with the same PW label. The P devices forward the traffic flows of a PW over the same path even if Equal Cost Multiple Paths (ECMPs) exist.
The L2VPN flow label feature can enable a P device to perform load sharing on packets based on the flow types.
After you configure this feature, the P and PE devices process packets as follows:
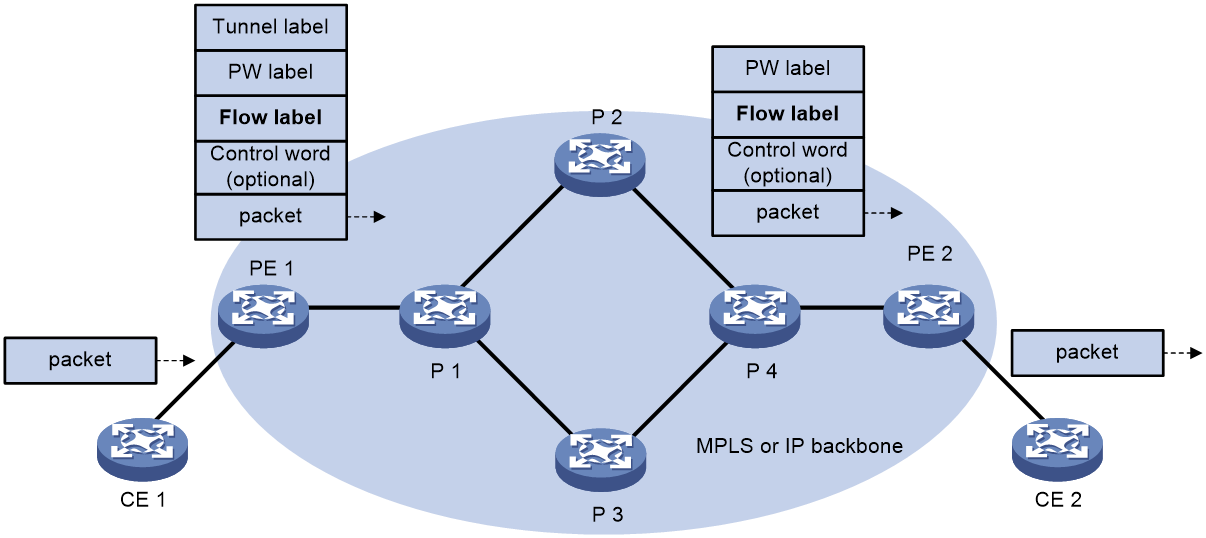
· When the ingress PE encapsulates a packet, it adds a flow label before it adds a PW label, as shown in Figure 9.
The ingress PE adds different flow labels for packets of different traffic types.
· The P devices perform load sharing on packets based on the flow labels.
· The egress PE removes both the PW and flow labels from a packet before forwarding the packet.
Figure 9 L2VPN flow label feature
You can enable the flow label sending, receiving, or both sending and receiving capabilities on a PE.
· The sending capability enables a PE to send packets with flow labels. The PE adds a flow label before it adds a PW label to a packet during PW encapsulation.
· The receiving capability enables a PE to identify the flow label in a received packet and removes the flow label before forwarding the packet.
For two PEs to successfully negotiate the flow label capabilities, make sure one end has the sending capability and the other end has the receiving capability.
For EVPN VPWS PWs, you must manually configure flow label capabilities for the local and remote PEs.
EVPN VPWS tasks at a glance
To configure EVPN VPWS, perform the following tasks:
2. Configure an AC
¡ Configuring a Layer 3 interface with Ethernet or VLAN encapsulation
3. Configuring EVPN route advertisement
a. Enabling BGP to advertise BGP EVPN routes
b. (Optional.) Configuring optimal route selection and route advertisement settings
c. (Optional.) Maintaining BGP sessions
4. Configuring a cross-connect
a. (Optional.) Configuring a PW class
6. Mapping an AC to a cross-connect
7. (Optional.) Configuring EVPN VPWS multihoming
a. Assigning an ESI to an interface
b. (Optional.) Configuring the DF election algorithm
c. Setting the redundancy mode on an interface
d. (Optional.) Setting the DF election delay
e. Disabling advertisement of EVPN multihoming routes
8. (Optional.) Configuring FRR for EVPN VPWS
Prerequisites for EVPN VPWS
To configure EVPN VPWS, you must perform the following tasks:
1. Configure an IGP to achieve IP connectivity within the backbone.
2. Configure basic MPLS, LDP, GRE, or MPLS TE to set up public tunnels across the backbone.
Enabling L2VPN
Prerequisites
Before you enable L2VPN, perform the following tasks:
· Configure an LSR ID for the PE by using the mpls lsr-id command.
· Enable MPLS by using the mpls enable command on the transport-facing interface of the PE.
For more information about the mpls lsr-id and mpls enable commands, see MPLS Command Reference.
Procedure
1. Enter system view.
system-view
2. Enable L2VPN.
l2vpn enable
By default, L2VPN is disabled.
Configuring a Layer 3 interface with Ethernet or VLAN encapsulation
About this task
Configure a Layer 3 interface on a PE to establish an AC to the CE. On a Layer 3 Ethernet interface (including Layer 3 Ethernet interface, Layer 3 virtual Ethernet interface, and VE-L2VPN interface), both the PW data encapsulation type and access mode are Ethernet. On a Layer 3 Ethernet subinterface, both the PW data encapsulation type and access mode are VLAN.
Restrictions and guidelines
The PE forwards packets received from a Layer 3 interface through the bound PW without network layer processing. Therefore, the Layer 3 interface does not need an IP address.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
Configuring EVPN route advertisement
Restrictions and guidelines for EVPN route advertisement configuration
For more information about the BGP commands used in this task, see Layer 3—IP Routing Command Reference.
Enabling BGP to advertise BGP EVPN routes
1. Enter system view.
system-view
2. Configure a global router ID.
router id router-id
By default, no global router ID is configured.
3. Enable a BGP instance and enter BGP instance view.
bgp as-number [ instance instance-name ]
By default, BGP is disabled and no BGP instances exist.
4. Specify remote PEs as BGP peers.
peer { group-name | ipv4-address [ mask-length ] } as-number as-number
5. Create the BGP EVPN address family and enter BGP EVPN address family view.
address-family l2vpn evpn
6. Enable BGP to exchange BGP EVPN routes with a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } enable
By default, BGP does not exchange BGP EVPN routes with peers.
Configuring optimal route selection and route advertisement settings
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP EVPN address family view.
address-family l2vpn evpn
4. Permit the local AS number to appear in routes from a peer or peer group and set the number of appearances.
peer { group-name | ipv4-address [ mask-length ] } allow-as-loop [ number ]
By default, the local AS number is not allowed in routes from peers.
5. Enable route target filtering for BGP EVPN routes.
policy vpn-target
By default, route target filtering is enabled for BGP EVPN routes.
6. (Optional.) Set the optimal route selection delay timer.
route-select delay delay-value
By default, the optimal route selection delay timer is 0 seconds, which means optimal route selection is not delayed.
7. (Optional.) Set the delay time for responding to recursive next hop changes.
nexthop recursive-lookup [ non-critical-event ] delay [ delay-value ]
By default, BGP responds to recursive next hop changes immediately.
8. Configure BGP route reflection settings:
a. Configure the device as an RR and specify a peer or peer group as its client.
peer { group-name | ipv4-address [ mask-length ] } reflect-client
By default, no RR or client is configured.
b. (Optional.) Enable BGP EVPN route reflection between clients.
reflect between-clients
By default, BGP EVPN route reflection between clients is enabled.
c. (Optional.) Configure the cluster ID of the RR.
reflector cluster-id { cluster-id | ipv4-address }
By default, an RR uses its own router ID as the cluster ID.
d. (Optional.) Create a reflection policy for the RR to filter reflected BGP EVPN routes.
rr-filter { ext-comm-list-number | ext-comm-list-name }
By default, an RR does not filter reflected BGP EVPN routes.
e. (Optional.) Create a reflection policy for the RR to filter reflected BGP EVPN routes.
reflect change-path-attribute
By default, an RR does not filter reflected BGP EVPN routes.
f. (Optional.) Add a peer or peer group to the nearby cluster.
peer { group-name | ipv4-address [ mask-length ] } reflect-nearby-group
By default, the nearby cluster does not have any peers or peer groups.
The RR does not change the next hop of routes reflected to peers and peer groups in the nearby cluster.
9. Configure the device to not change the next hop of routes advertised to an EBGP peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } next-hop-invariable
By default, the device uses its address as the next hop of routes advertised to EBGP peers.
10. Set a preferred value for routes received from a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] | ipv6-address [ prefix-length ] } preferred-value value
By default, the preferred value is 0 for routes received from a peer or peer group.
11. Apply a routing policy to routes received from or advertised to a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } route-policy route-policy-name { export | import }
By default, no routing policies are applied to routes received from or advertised to peers or peer groups.
12. Advertise the COMMUNITY attribute to a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } advertise-community
By default, the device does not advertise the COMMUNITY attribute to peers or peer groups.
Maintaining BGP sessions
Perform the following tasks in user view:
· Reset BGP sessions of the BGP EVPN address family.
reset bgp [ instance instance-name ] { as-number | ipv4-address [ mask-length ] | all | external | group group-name | internal } l2vpn evpn
· Soft-reset BGP sessions of the BGP EVPN address family.
refresh bgp [ instance instance-name ] { ipv4-address [ mask-length ] | all | external | group group-name | internal } { export | import } l2vpn evpn
Configuring a cross-connect
Restrictions and guidelines
For more information about the cross-connect commands used in this task, see MPLS L2VPN commands in MPLS Command Reference.
Procedure
1. Enter system view.
system-view
2. Create a cross-connect group and enter cross-connect group view.
xconnect-group group-name
3. (Optional.) Configure a description for the cross-connect group.
description text
By default, no description is configured for a cross-connect group.
4. (Optional.) Enable the cross-connect group.
undo shutdown
By default, the cross-connect group is enabled.
5. Create a cross-connect and enter cross-connect view.
connection connection-name
Configuring a PW
Configuring a PW class
About this task
You can configure PW attributes such as the PW data encapsulation type and enable control word in a PW class. PWs with the same attributes can use the same PW class.
Restrictions and guidelines
For more information about the PW class commands used in this task, see MPLS L2VPN commands in MPLS Command Reference.
You must configure the same data encapsulation type on two PEs that are connected by the same PW.
For correct PW setup, make sure the status of the control word feature is the same on the two PEs that are connected by the same PW.
Procedure
1. Enter system view.
system-view
2. Create a PW class and enter PW class view.
pw-class class-name
3. Enable control word.
control-word enable
By default, control word is disabled.
4. Specify the PW data encapsulation type.
pw-type { ethernet | vlan }
By default, the PW data encapsulation type is VLAN.
5. Enable the flow label feature and configure flow label capabilities.
flow-label { both | receive | send } static
By default, the flow label feature is disabled.
EVPN VPWS does not support flow label capability negotiation for dynamic PWs in the current software version. For this command to take effect, you must specify the static keyword.
Configuring an EVPN PW
About this task
To establish an EVPN PW between two PEs, specify a local service ID and a remote service ID on both PEs. The local service ID specified on one PE must be the same as the remote service ID specified on the other PE.
Restrictions and guidelines
To modify an EVPN PW, first use the undo evpn local-service-id remote-service-id command to delete the original EVPN PW.
Procedure
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Create an EVPN instance for the cross-connect group and enter its view.
evpn encapsulation mpls
4. Configure an RD for the EVPN instance.
route-distinguisher route-distinguisher
By default, no RD is configured for the EVPN instance of a cross-connect group.
5. Configure route targets for the EVPN instance.
vpn-target { vpn-target&<1-8> } [ both | export-extcommunity | import-extcommunity ]
By default, no route targets are configured for the EVPN instance of a cross-connect group.
Make sure the following requirements are met:
¡ The import targets of the EVPN instance of a cross-connect group do not match the export targets of a VPN instance, the public instance, or the EVPN instance of a VSI.
¡ The export targets of the EVPN instance of a cross-connect group do not match the import targets of a VPN instance, the public instance, or the EVPN instance of a VSI.
6. (Optional.) Apply an export routing policy to EVPN.
export route-policy route-policy
By default, no export routing policy is applied to EVPN.
7. (Optional.) Apply an import routing policy to EVPN.
import route-policy route-policy
By default, no import routing policy is applied to EVPN. A VPN instance accepts a route when the route targets of the route match local import route targets.
8. Return to cross-connect group view.
quit
9. Enter cross-connect view.
connection connection-name
10. (Optional.) Set an MTU for the PW.
mtu size
The default MTU is 1500 bytes.
11. Configure an EVPN PW.
evpn local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ] [ pw-class class-name ]
Do not use this command together with the peer command for a cross-connect.
Mapping an AC to a cross-connect
About mapping an AC to a cross-connect
After you map an AC to a cross-connect, packets received from the mapped AC are forwarded to the PW or another AC bound to the cross-connect.
Restrictions and guidelines for mapping an AC to a cross-connect
This task is mutually exclusive with Ethernet link aggregation. If a Layer 3 Ethernet interface has been added to a link aggregation group, you cannot map the Layer 3 interface to a cross-connect, and vice versa.
Mapping a Layer 3 interface to a cross-connect
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect view.
connection connection-name
4. Map a Layer 3 interface to the cross-connect.
ac interface interface-type interface-number [ access-mode { ethernet | vlan } ]
By default, no Layer 3 interface is bound to the cross-connect.
Configuring EVPN VPWS multihoming
Restrictions and guidelines for EVPN VPWS multihoming
You must configure the same local and remote service IDs on the redundant PEs at a multihomed site.
As a best practice, set the same redundancy mode on the interfaces that act as ACs or are configured with ACs on the redundant PEs at a multihomed site.
You can assign ESIs to a main interface and its subinterfaces.
· If you assign an ESI to a subinterface, the subinterface-specific ESI and ES configuration take precedence over those configured on the main interface. The ES configuration includes the following:
¡ evpn df-election algorithm.
¡ evpn df-election preference.
¡ evpn df-election preference non-revertive.
· If you do not assign an ESI to a subinterface, it inherits the ESI and ES configuration (if configured) of the main interface. In this scenario, the ES configuration on the subinterface does not take effect.
Assigning an ESI to an interface
About this task
An ESI uniquely identifies an ES. The links on interfaces with the same ESI belong to the same ES. Traffic of the ES can be distributed among the links for load sharing.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
¡ Enter Layer 3 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 3 aggregate interface view.
interface route-aggregation interface-number
3. Assign an ESI to the interface.
esi esi-id
By default, no ESI is assigned to an interface.
Configuring the DF election algorithm
About this task
At a multihomed EVPN network site, you can modify the DF election algorithm to control the DF election result.
Restrictions and guidelines
You can configure the DF election algorithm in system view and in interface view. The global DF election algorithm takes effect on all ESs, and the interface-specific DF election algorithm takes effect only on the ESs on an interface. The interface-specific DF election algorithm takes precedence over the global DF election algorithm.
Configuring the DF election algorithm globally
1. Enter system view.
system-view
2. Configure the DF election algorithm.
evpn df-election algorithm algorithm
By default, the VLAN tag-based algorithm is used for DF election.
Configuring the DF election algorithm on an interface
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
¡ Enter Layer 3 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 3 aggregate interface view.
interface route-aggregation interface-number
3. Configure the DF election algorithm.
evpn df-election algorithm algorithm
By default, the DF election algorithm specified in system view takes effect.
Configuring preference-based DF election
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
¡ Enter Layer 3 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 3 aggregate interface view.
interface route-aggregation interface-number
3. Set the DF election preference.
evpn df-election preference preference
By default, the DF election preference is 32767.
The larger the value, the higher the preference.
4. (Optional.) Enable non-revertive mode for preference-based DF election.
evpn df-election preference non-revertive
By default, non-revertive mode is disabled for preference-based DF election.
Setting the redundancy mode on an interface
About this task
EVPN VPWS multihoming provides the single-active redundancy mode and all-active redundancy mode.
The redundant PEs at a dualhomed site each establish an EVPN PW to a remote PE. To use one PW as a backup of the other PW, use the single-active mode. To distribute traffic across the PWs for load sharing, use the all-active mode.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
¡ Enter Layer 3 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 3 aggregate interface view.
interface route-aggregation interface-number
3. Set the redundancy mode.
evpn redundancy-mode { all-active | single-active }
By default, the all-active redundancy mode is used.
Setting the DF election delay
About this task
The DF election can be triggered by site-facing interface status changes, redundant PE membership changes, and interface ESI changes. To prevent frequent DF elections from degrading network performance, set the DF election delay. The DF election delay defines the minimum interval allowed between two DF elections.
Procedure
1. Enter system view.
system-view
2. Set the DF election delay.
evpn multihoming timer df-delay delay-value
By default, the DF election delay is 3 seconds.
Disabling advertisement of EVPN multihoming routes
About this task
EVPN multihoming routes include Ethernet auto-discovery routes and Ethernet segment routes.
In a multihomed EVPN network, perform this task on a redundant PE before you reboot it. This operation allows other PEs to refresh their EVPN routing table to prevent traffic interruption caused by the reboot.
Procedure
1. Enter system view.
system-view
2. Disable advertisement of EVPN multihoming routes and withdraw the EVPN multihoming routes that have been advertised to remote sites.
evpn multihoming advertise disable
By default, the device advertises EVPN multihoming routes.
Configuring FRR for EVPN VPWS
Configuring local FRR
About this task
Local FRR enables two PEs at a multihomed EVPN VPWS network site to set up a bypass PW between them. This feature helps reduce the traffic loss caused by AC failure.
Restrictions and guidelines
On an EVPN instance, EVPN instance-specific local FRR configuration takes precedence over global local FRR configuration.
If you have executed the evpn frr local enable command on an EVPN instance, the undo evpn multihoming vpws-frr local command does not delete the bypass PW of the EVPN instance.
Enabling local FRR globally
1. Enter system view.
system-view
2. Enable local FRR globally.
evpn multihoming vpws-frr local
By default, local FRR is disabled globally.
Configuring local FRR on an EVPN instance
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter EVPN instance view.
evpn encapsulation mpls
4. Configure local FRR.
evpn frr local { disable | enable }
By default, an EVPN instance uses the global local FRR configuration of EVPN VPWS.
Configuring remote FRR
About this task
Remote FRR enables two PEs on an EVPN VPWS network to set up a primary PW and a backup PW between them to ensure high availability. The PEs use the primary PW to forward traffic as long as it is available. When the primary PW fails, the PEs switch traffic to the backup PW.
Restrictions and guidelines
On an EVPN instance, EVPN instance-specific remote FRR configuration takes precedence over global remote FRR configuration.
If you have executed the evpn frr remote enable command on an EVPN instance, the undo evpn vpws-frr remote command does not delete the backup PWs of the EVPN instance.
Enabling remote FRR globally
1. Enter system view.
system-view
2. Enable remote FRR globally.
evpn vpws-frr remote
By default, remote FRR is disabled globally.
Configuring remote FRR on an EVPN instance
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter EVPN instance view.
evpn encapsulation mpls
4. Configure remote FRR.
evpn frr remote { disable | enable }
By default, an EVPN instance uses the global remote FRR configuration of EVPN VPWS.
Verifying and maintaining EVPN VPWS
Displaying EVPN running status and statistics
Perform display tasks in any view.
· Display BGP peer group information.
display bgp [ instance instance-name ] group l2vpn [ group-name group-name ]
For more information about this command, see basic BGP commands in Layer 3—IP Routing Command Reference.
· Display BGP peer or peer group information.
display bgp [ instance instance-name ] peer l2vpn evpn [ ipv4-address mask-length | { ipv4-address | group-name group-name } log-info | [ ipv4-address ] verbose ]
For more information about this command, see basic BGP commands in Layer 3—IP Routing Command Reference.
· Display information about BGP update groups.
display bgp [ instance instance-name ] update-group l2vpn evpn [ ipv4-address ]
For more information about this command, see basic BGP commands in Layer 3—IP Routing Command Reference.
· Display EVPN routing table information.
display evpn routing-table [ ipv6 ] { public-instance | vpn-instance vpn-instance-name } [ count ]
· Display EVPN ES information.
display evpn es { local [ count | [ xconnect-group group-name ] [ esi esi-id ] [ verbose ] ] | remote [ xconnect-group group-name ] [ esi esi-id ] [ nexthop next-hop ] [ verbose ] }
Displaying cross-connect group configuration and running status
To display EVPN information about cross-connects, execute the following command in any view:
display evpn xconnect-group [ name group-name [ connection connection-name ] ] [ count ]
Displaying AC configuration and running status
Perform display tasks in any view.
· Display AC forwarding information.
display l2vpn forwarding ac [ xconnect-group group-name ] [ verbose ]
display l2vpn forwarding ac [ xconnect-group group-name ] [ slot slot-number [ cpu cpu-number ] ] [ verbose ]
display l2vpn forwarding ac [ xconnect-group group-name ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] [ verbose ]
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
· Display L2VPN information for Layer 3 interfaces bound to VSIs.
display l2vpn interface [ xconnect-group group-name | interface-type interface-number ] [ verbose ]
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
Displaying PW configuration and running status
Perform display tasks in any view.
· Display PW forwarding information.
display l2vpn forwarding pw [ xconnect-group group-name ] [ verbose ]
display l2vpn forwarding pw [ xconnect-group group-name ] [ slot slot-number [ cpu cpu-number ] ] [ verbose ]
display l2vpn forwarding pw [ xconnect-group group-name ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] [ verbose ]
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
· Display L2VPN PW information.
display l2vpn pw [ xconnect-group group-name ] [ protocol { bgp | evpn | ldp | static } ] [ verbose ]
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
· Display PW class information.
display l2vpn pw-class [ class-name ]
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
· Display BFD information for PWs.
display l2vpn pw bfd [ peer peer-ip remote-service-id remote-service-id ]
For more information about this command, see MPLS OAM commands in MPLS Command Reference.
EVPN VPWS configuration examples
Example: Configuring a remote connection between singlehomed sites
Network configuration
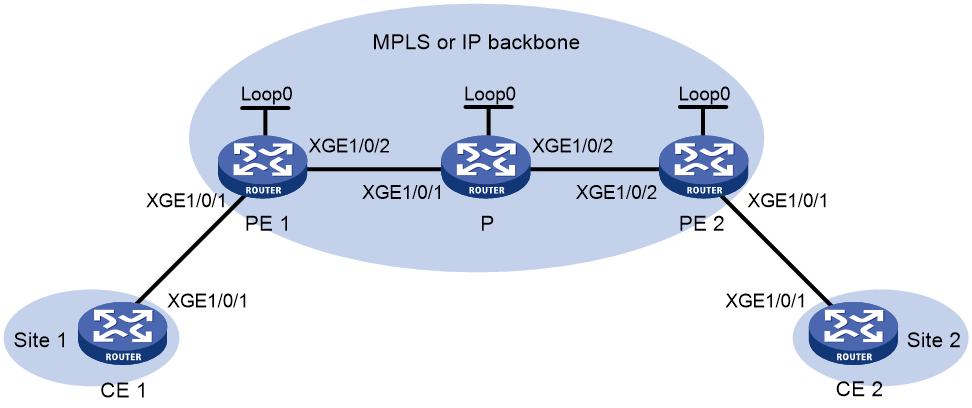
As shown in Figure 10, set up a remote connection between CE 1 and CE 2 for users in site 1 and site 2 to communicate through EVPN VPWS over the MPLS or IP backbone network.
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
XGE0/0/6 |
10.1.1.10/24 |
P |
Loop0 |
3.3.3.3/32 |
|
PE 1 |
Loop0 |
1.1.1.1/32 |
|
XGE0/0/6 |
11.1.1.2/24 |
|
|
XGE0/0/6 |
N/A |
|
XGE0/0/7 |
11.1.2.2/24 |
|
|
XGE0/0/7 |
11.1.1.1/24 |
PE 2 |
Loop0 |
2.2.2.2/32 |
|
CE 2 |
XGE0/0/6 |
10.1.1.20/24 |
|
XGE0/0/6 |
N/A |
|
|
|
|
|
XGE0/0/7 |
11.1.2.1/24 |
Procedure
1. Configure CE 1.
<CE1> system-view
[CE1] interface ten-gigabitethernet 0/0/6
[CE1-Ten-GigabitEthernet0/0/6] ip address 10.1.1.10 24
[CE1-Ten-GigabitEthernet0/0/6] quit
2. Configure PE 1:
# Configure the LSR ID.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 1.1.1.1 32
[PE1-LoopBack0] quit
[PE1] mpls lsr-id 1.1.1.1
# Enable L2VPN.
[PE1] l2vpn enable
# Enable global LDP.
[PE1] mpls ldp
[PE1-ldp] quit
# Configure Ten-GigabitEthernet 0/0/7 (the interface connected to the P device), and enable LDP on the interface.
[PE1] interface ten-gigabitethernet 0/0/7
[PE1-Ten-GigabitEthernet0/0/7] ip address 11.1.1.1 24
[PE1-Ten-GigabitEthernet0/0/7] mpls enable
[PE1-Ten-GigabitEthernet0/0/7] mpls ldp enable
[PE1-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[PE1] ospf
[PE1-ospf-1] area 0
[PE1-ospf-1-area-0.0.0.0] network 11.1.1.0 0.0.0.255
[PE1-ospf-1-area-0.0.0.0] network 1.1.1.1 0.0.0.0
[PE1-ospf-1-area-0.0.0.0] quit
[PE1-ospf-1] quit
# Create an IBGP connection to PE 2, and enable BGP to advertise L2VPN information to PE 2.
[PE1] bgp 100
[PE1-bgp-default] peer 2.2.2.2 as-number 100
[PE1-bgp-default] peer 2.2.2.2 connect-interface loopback 0
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 2.2.2.2 enable
[PE1-bgp-default-evpn] quit
[PE1-bgp-default] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE1] xconnect-group vpna
[PE1-xcg-vpna] evpn encapsulation mpls
[PE1-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE1-xcg-vpna-evpn-mpls] vpn-target 1:1 export-extcommunity
[PE1-xcg-vpna-evpn-mpls] vpn-target 1:1 import-extcommunity
[PE1-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE1-xcg-vpna] connection pw1
[PE1-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE1-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE1-xcg-vpna-pw1] evpn local-service-id 1 remote-service-id 2
[PE1-xcg-vpna-pw1] quit
[PE1-xcg-vpna] quit
3. Configure the P device:
# Configure the LSR ID.
<P> system-view
[P] interface loopback 0
[P-LoopBack0] ip address 3.3.3.3 32
[P-LoopBack0] quit
[P] mpls lsr-id 3.3.3.3
# Enable global LDP.
[P] mpls ldp
[P-ldp] quit
# Configure Ten-GigabitEthernet 0/0/6 (the interface connected to PE 1), and enable LDP on the interface.
[P] interface ten-gigabitethernet 0/0/6
[P-Ten-GigabitEthernet0/0/6] ip address 11.1.1.2 24
[P-Ten-GigabitEthernet0/0/6] mpls enable
[P-Ten-GigabitEthernet0/0/6] mpls ldp enable
[P-Ten-GigabitEthernet0/0/6] quit
# Configure Ten-GigabitEthernet 0/0/7 (the interface connected to PE 2), and enable LDP on the interface.
[P] interface ten-gigabitethernet 0/0/7
[P-Ten-GigabitEthernet0/0/7] ip address 11.1.2.2 24
[P-Ten-GigabitEthernet0/0/7] mpls enable
[P-Ten-GigabitEthernet0/0/7] mpls ldp enable
[P-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[P] ospf
[P-ospf-1] area 0
[P-ospf-1-area-0.0.0.0] network 11.1.1.0 0.0.0.255
[P-ospf-1-area-0.0.0.0] network 11.1.2.0 0.0.0.255
[P-ospf-1-area-0.0.0.0] network 3.3.3.3 0.0.0.0
[P-ospf-1-area-0.0.0.0] quit
[P-ospf-1] quit
4. Configure PE 2:
# Configure the LSR ID.
<PE2> system-view
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 2.2.2.2 32
[PE2-LoopBack0] quit
[PE2] mpls lsr-id 2.2.2.2
# Enable L2VPN.
[PE2] l2vpn enable
# Enable global LDP.
[PE2] mpls ldp
[PE2-ldp] quit
# Configure Ten-GigabitEthernet 0/0/7 (the interface connected to the P device), and enable LDP on the interface.
[PE2] interface ten-gigabitethernet 0/0/7
[PE2-Ten-GigabitEthernet0/0/7] ip address 11.1.2.1 24
[PE2-Ten-GigabitEthernet0/0/7] mpls enable
[PE2-Ten-GigabitEthernet0/0/7] mpls ldp enable
[PE2-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[PE2] ospf
[PE2-ospf-1] area 0
[PE2-ospf-1-area-0.0.0.0] network 2.2.2.2 0.0.0.0
[PE2-ospf-1-area-0.0.0.0] network 11.1.2.0 0.0.0.255
[PE2-ospf-1-area-0.0.0.0] quit
[PE2-ospf-1] quit
# Create an IBGP connection to PE 1, and enable BGP to advertise L2VPN information to PE 1.
[PE2] bgp 100
[PE2-bgp-default] peer 1.1.1.1 as-number 100
[PE2-bgp-default] peer 1.1.1.1 connect-interface loopback 0
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 1.1.1.1 enable
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE2] xconnect-group vpna
[PE2-xcg-vpna] evpn encapsulation mpls
[PE2-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE2-xcg-vpna-evpn-mpls] vpn-target 1:1 export-extcommunity
[PE2-xcg-vpna-evpn-mpls] vpn-target 1:1 import-extcommunity
[PE2-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE2-xcg-vpna] connection pw1
[PE2-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE2-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE2-xcg-vpna-pw1] evpn local-service-id 2 remote-service-id 1
[PE2-xcg-vpna-pw1] quit
[PE2-xcg-vpna] quit
5. Configure CE 2.
<CE2> system-view
[CE2] interface ten-gigabitethernet 0/0/6
[CE2-Ten-GigabitEthernet0/0/6] ip address 10.1.1.20 24
[CE2-Ten-GigabitEthernet0/0/6] quit
Verifying the configuration
# Verify that an EVPN PW has been established between PE 1 and PE 2.
[PE1] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
2.2.2.2 2 710127/710127 EVPN M 0 Up
# Verify that the EVPN information about the cross-connect on PE 1 is correct.
[PE1] display evpn xconnect-group
Flags: P - Primary, B - Backup, C - Control word
Xconnect group name: vpna
Connection Name: pw1
ESI : 0000.0000.0000.0000.0000
Local service ID : 1
Remote service ID : 2
Control word : Disable
In label : 710127
Local MTU : 1500
AC state : Up
PW type : Ethernet
Nexthop ESI Out label Flags MTU State
2.2.2.2 0000.0000.0000.0000.0000 710127 P 1500 Up
# Verify that the EVPN information about the cross-connect on PE 2 is correct.
[PE2] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
1.1.1.1 1 710127/710127 EVPN M 0 Up
# Verify that CE 1 and CE 2 can ping each other. (Details not shown.)
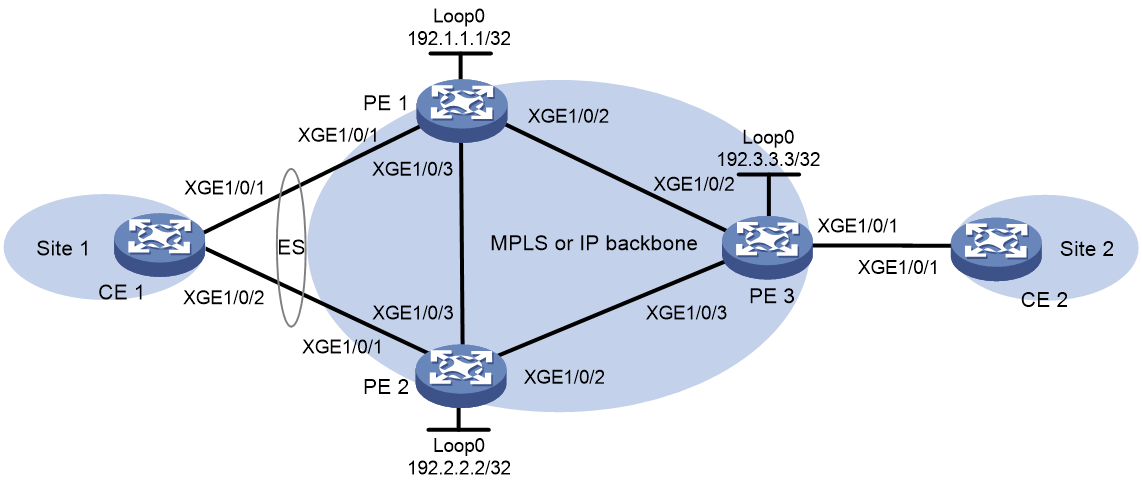
Example: Configuring EVPN VPWS multihoming
Network configuration
As shown in Figure 11, configure EVPN VPWS for dualhomed site 1 and singlehomed site 2 to communicate over the MPLS or IP backbone network.
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
PE 1 |
Loop0 |
192.1.1.1/32 |
CE 1 |
XGE0/0/6 |
100.1.1.1/24 |
|
|
XGE0/0/6 |
N/A |
CE 2 |
XGE0/0/6 |
100.1.1.2/24 |
|
|
XGE0/0/7 |
10.1.1.1/24 |
PE 3 |
Loop0 |
192.3.3.3/32 |
|
|
XGE0/0/8 |
10.1.3.1/24 |
|
XGE0/0/6 |
N/A |
|
PE 2 |
Loop0 |
192.2.2.2/32 |
|
XGE0/0/7 |
10.1.1.2/24 |
|
|
XGE0/0/6 |
N/A |
|
XGE0/0/8 |
10.1.2.2/24 |
|
|
XGE0/0/7 |
10.1.2.1/24 |
|
|
|
|
|
XGE0/0/8 |
10.1.3.2/24 |
|
|
|
Procedure
1. Configure CE 1:
# Create dynamic Layer 3 aggregate interface 1 and assign it an IP address.
<CE1> system-view
[CE1] interface route-aggregation 1
[CE1-Route-Aggregation1] ip address 100.1.1.1 24
[CE1-Route-Aggregation1] quit
# Assign Ten-GigabitEthernet 0/0/6 and Ten-GigabitEthernet 0/0/7 to aggregation group 1.
[CE1] interface ten-gigabitethernet 0/0/6
[CE1-Ten-GigabitEthernet0/0/6] port link-aggregation group 1
[CE1-Ten-GigabitEthernet0/0/6] quit
[CE1] interface ten-gigabitethernet 0/0/7
[CE1-Ten-GigabitEthernet0/0/7] port link-aggregation group 1
[CE1-Ten-GigabitEthernet0/0/7] quit
2. Configure PE 1:
# Configure the LSR ID.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 192.1.1.1 32
[PE1-LoopBack0] quit
[PE1] mpls lsr-id 192.1.1.1
# Enable L2VPN.
[PE1] l2vpn enable
# Enable global LDP.
[PE1] mpls ldp
[PE1-ldp] quit
# Configure Ten-GigabitEthernet 0/0/7 (the interface connected to PE 3), and enable LDP on the interface.
[PE1] interface ten-gigabitethernet 0/0/7
[PE1-Ten-GigabitEthernet0/0/7] ip address 10.1.1.1 24
[PE1-Ten-GigabitEthernet0/0/7] mpls enable
[PE1-Ten-GigabitEthernet0/0/7] mpls ldp enable
[PE1-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[PE1] ospf
[PE1-ospf-1] area 0
[PE1-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[PE1-ospf-1-area-0.0.0.0] network 10.1.3.0 0.0.0.255
[PE1-ospf-1-area-0.0.0.0] network 192.1.1.1 0.0.0.0
[PE1-ospf-1-area-0.0.0.0] quit
[PE1-ospf-1] quit
# Create IBGP connections to PE 2 and PE 3, and enable BGP to advertise routes to PE 2 and PE 3.
[PE1] bgp 100
[PE1-bgp-default] peer 192.2.2.2 as-number 100
[PE1-bgp-default] peer 192.2.2.2 connect-interface loopback 0
[PE1-bgp-default] peer 192.3.3.3 as-number 100
[PE1-bgp-default] peer 192.3.3.3 connect-interface loopback 0
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 192.2.2.2 enable
[PE1-bgp-default-evpn] peer 192.3.3.3 enable
[PE1-bgp-default-evpn] quit
[PE1-bgp-default] quit
# Assign an ESI to Ten-GigabitEthernet 0/0/6 and set its redundancy mode to all-active.
[PE1] interface ten-gigabitethernet 0/0/6
[PE1-Ten-GigabitEthernet0/0/6] esi 1.1.1.1.1
[PE1-Ten-GigabitEthernet0/0/6] evpn redundancy-mode all-active
[PE1-Ten-GigabitEthernet0/0/6] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE1] xconnect-group vpna
[PE1-xcg-vpna] evpn encapsulation mpls
[PE1-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE1-xcg-vpna-evpn-mpls] vpn-target 1:1 export-extcommunity
[PE1-xcg-vpna-evpn-mpls] vpn-target 1:1 import-extcommunity
[PE1-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE1] xconnect-group vpna
[PE1-xcg-vpna] connection pw1
[PE1-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE1-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE1-xcg-vpna-pw1] evpn local-service-id 1 remote-service-id 2
[PE1-xcg-vpna-pw1] quit
[PE1-xcg-vpna] quit
# Associate Ten-GigabitEthernet 0/0/7 with track entry 1.
[PE1] track 1 interface ten-gigabitethernet 0/0/7
[PE1-track-1] quit
# Configure CLI-defined monitor policy 1 to associate Ten-GigabitEthernet 0/0/7 with Ten-GigabitEthernet 0/0/6. This setting allows PE 1 to shut down Ten-GigabitEthernet 0/0/6 when Ten-GigabitEthernet 0/0/7 goes down.
[PE1] rtm cli-policy policy1
[PE1-rtm-policy1] event track 1 state negative
[PE1-rtm-policy1] action 0 cli system-view
[PE1-rtm-policy1] action 1 cli interface ten-gigabitethernet 0/0/6
[PE1-rtm-policy1] action 2 cli shutdown
[PE1-rtm-policy1] user-role network-admin
[PE1-rtm-policy1] commit
[PE1-rtm-policy1] quit
3. Configure PE 2:
# Configure the LSR ID.
<PE2> system-view
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 192.2.2.2 32
[PE2-LoopBack0] quit
[PE2] mpls lsr-id 192.2.2.2
# Enable L2VPN.
[PE2] l2vpn enable
# Enable global LDP.
[PE2] mpls ldp
[PE2-ldp] quit
# Configure Ten-GigabitEthernet 0/0/7 (the interface connected to PE 3), and enable LDP on the interface.
[PE2] interface ten-gigabitethernet 0/0/7
[PE2-Ten-GigabitEthernet0/0/7] ip address 10.1.2.1 24
[PE2-Ten-GigabitEthernet0/0/7] mpls enable
[PE2-Ten-GigabitEthernet0/0/7] mpls ldp enable
[PE2-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[PE2] ospf
[PE2-ospf-1] area 0
[PE2-ospf-1-area-0.0.0.0] network 10.1.2.0 0.0.0.255
[PE2-ospf-1-area-0.0.0.0] network 10.1.3.0 0.0.0.255
[PE2-ospf-1-area-0.0.0.0] network 192.2.2.2 0.0.0.0
[PE2-ospf-1-area-0.0.0.0] quit
[PE2-ospf-1] quit
# Create IBGP connections to PE 1 and PE 3, and enable BGP to advertise routes to PE 1 and PE 3.
[PE2] bgp 100
[PE2-bgp-default] peer 192.1.1.1 as-number 100
[PE2-bgp-default] peer 192.1.1.1 connect-interface loopback 0
[PE2-bgp-default] peer 192.3.3.3 as-number 100
[PE2-bgp-default] peer 192.3.3.3 connect-interface loopback 0
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 192.1.1.1 enable
[PE2-bgp-default-evpn] peer 192.3.3.3 enable
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] quit
# Assign an ESI to Ten-GigabitEthernet 0/0/6 and set its redundancy mode to all-active.
[PE2] interface ten-gigabitethernet 0/0/6
[PE2-Ten-GigabitEthernet0/0/6] esi 1.1.1.1.1
[PE2-Ten-GigabitEthernet0/0/6] evpn redundancy-mode all-active
[PE2-Ten-GigabitEthernet0/0/6] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE2] xconnect-group vpna
[PE2-xcg-vpna] evpn encapsulation mpls
[PE2-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE2-xcg-vpna-evpn-mpls] vpn-target 1:1 export-extcommunity
[PE2-xcg-vpna-evpn-mpls] vpn-target 1:1 import-extcommunity
[PE2-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE2] xconnect-group vpna
[PE2-xcg-vpna] connection pw1
[PE2-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE2-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE2-xcg-vpna-pw1] evpn local-service-id 1 remote-service-id 2
[PE2-xcg-vpna-pw1] quit
[PE2-xcg-vpna] quit
# Associate Ten-GigabitEthernet 0/0/7 with track entry 1.
[PE2] track 1 interface ten-gigabitethernet 0/0/7
[PE2-track-1] quit
# Configure CLI-defined monitor policy 1 to associate Ten-GigabitEthernet 0/0/7 with Ten-GigabitEthernet 0/0/6. This setting allows PE 2 to shut down Ten-GigabitEthernet 0/0/6 when Ten-GigabitEthernet 0/0/7 goes down.
[PE2] rtm cli-policy policy1
[PE2-rtm-policy1] event track 1 state negative
[PE2-rtm-policy1] action 0 cli system-view
[PE2-rtm-policy1] action 1 cli interface ten-gigabitethernet 0/0/6
[PE2-rtm-policy1] action 2 cli shutdown
[PE2-rtm-policy1] user-role network-admin
[PE2-rtm-policy1] commit
[PE2-rtm-policy1] quit
4. Configure PE 3:
# Configure the LSR ID.
<PE3> system-view
[PE3] interface loopback 0
[PE3-LoopBack0] ip address 192.3.3.3 32
[PE3-LoopBack0] quit
[PE3] mpls lsr-id 192.3.3.3
# Enable L2VPN.
[PE3] l2vpn enable
# Enable global LDP.
[PE3] mpls ldp
[PE3-ldp] quit
# Configure Ten-GigabitEthernet 0/0/7 (the interface connected to PE 1) and Ten-GigabitEthernet 0/0/8 (the interface connected to PE 2), and enable LDP on the interfaces.
[PE3] interface ten-gigabitethernet 0/0/7
[PE3-Ten-GigabitEthernet0/0/7] ip address 10.1.1.2 24
[PE3-Ten-GigabitEthernet0/0/7] mpls enable
[PE3-Ten-GigabitEthernet0/0/7] mpls ldp enable
[PE3-Ten-GigabitEthernet0/0/7] quit
[PE3] interface ten-gigabitethernet 0/0/8
[PE3-Ten-GigabitEthernet0/0/8] ip address 10.1.2.2 24
[PE3-Ten-GigabitEthernet0/0/8] mpls enable
[PE3-Ten-GigabitEthernet0/0/8] mpls ldp enable
[PE3-Ten-GigabitEthernet0/0/8] quit
# Configure OSPF for LDP to create LSPs.
[PE3] ospf
[PE3-ospf-1] area 0
[PE3-ospf-1-area-0.0.0.0] network 192.3.3.3 0.0.0.0
[PE3-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[PE3-ospf-1-area-0.0.0.0] network 10.1.2.0 0.0.0.255
[PE3-ospf-1-area-0.0.0.0] quit
[PE3-ospf-1] quit
# Create IBGP connections to PE 1 and PE 2, and enable BGP to advertise routes to PE 1 and PE 2.
[PE3] bgp 100
[PE3-bgp-default] peer 192.1.1.1 as-number 100
[PE3-bgp-default] peer 192.1.1.1 connect-interface loopback 0
[PE3-bgp-default] peer 192.2.2.2 as-number 100
[PE3-bgp-default] peer 192.2.2.2 connect-interface loopback 0
[PE3-bgp-default] address-family l2vpn evpn
[PE3-bgp-default-evpn] peer 192.1.1.1 enable
[PE3-bgp-default-evpn] peer 192.2.2.2 enable
[PE3-bgp-default-evpn] quit
[PE3-bgp-default] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE3] xconnect-group vpna
[PE3-xcg-vpna] evpn encapsulation mpls
[PE3-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE3-xcg-vpna-evpn-mpls] vpn-target 1:1 export-extcommunity
[PE3-xcg-vpna-evpn-mpls] vpn-target 1:1 import-extcommunity
[PE3-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE3] xconnect-group vpna
[PE3-xcg-vpna] connection pw1
[PE3-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE3-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE3-xcg-vpna-pw1] evpn local-service-id 2 remote-service-id 1
[PE3-xcg-vpna-pw1] quit
[PE3-xcg-vpna] quit
5. Configure CE 2.
<CE2> system-view
[CE2] interface ten-gigabitethernet 0/0/6
[CE2-Vlan-interface10] ip address 100.1.1.2 24
[CE2-Vlan-interface10] quit
Verifying the configuration
# Verify that PE 1 has established EVPN PWs to PE 2 and PE 3.
<PE1> display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.3.3.3 2 710263/710265 EVPN M 0 Up
# Verify that the EVPN information about the cross-connect on PE 1 is correct.
<PE1> display evpn xconnect-group
Flags: P - Primary, B - Backup, C - Control word
Xconnect group name: vpna
Connection name: 1
ESI : 0001.0001.0001.0001.0001
Local service ID : 1
Remote service ID : 2
Control word : Disabled
In label : 710263
Local MTU : 1500
AC state : Up
PW type : Ethernet
Nexthop ESI Out label Flags MTU state
192.3.3.3 0000.0000.0000.0000.0000 710265 P 1500 Up
# Verify that PE 1 has local ES information.
<PE1> display evpn es local
Redundancy mode: A - All-active, S - Single-active
Xconnect-group name : vpna
ESI Tag ID DF address Mode State ESI label
0001.0001.0001.0001.0001 - 192.1.1.1 A Up -
# Verify that PE 1 has remote ES information.
<PE1> display evpn es remote
Control Flags: P - Primary, B - Backup, C - Control word
Xconnect group name : vpna
ESI : 0001.0001.0001.0001.0001
Ethernet segment routes :
192.2.2.2
A-D per ES routes :
Peer IP Remote Redundancy mode
192.2.2.2 All-active
A-D per EVI routes :
Tag ID Peer IP Control Flags
1 192.2.2.2 B
# Verify that PE 2 has established EVPN PWs to PE 1 and PE 3.
<PE2> display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.3.3.3 2 710124/710265 EVPN M 1 Up
# Verify that PE 3 has established EVPN PWs to PE 1 and PE 2.
<PE3> display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 2
2 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.1.1.1 1 710265/710263 EVPN E 0 Up
192.2.2.2 1 710265/710124 EVPN E 0 Up
# Verify that CE 1 and CE 2 can ping each other when the PW on PE 1 or PE 2 fails. (Details not shown.)
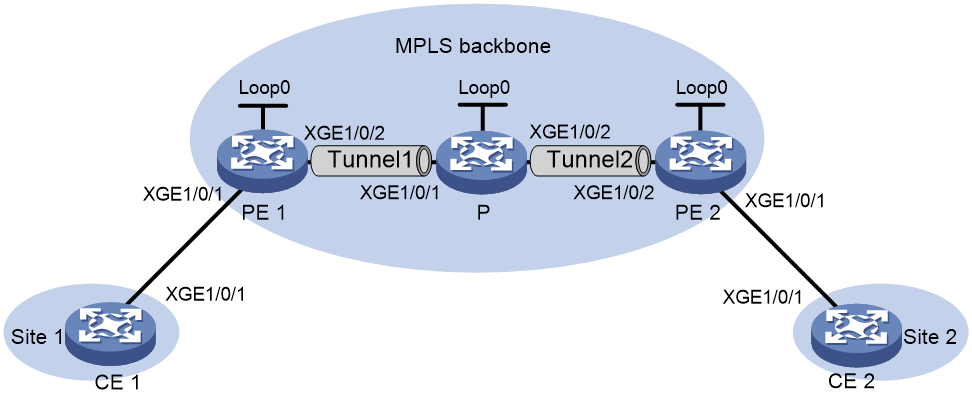
Example: Configuring PW concatenation
Network configuration
As shown in Figure 12:
· Set up an MPLS TE tunnel between each PE and the P device, and configure each MPLS TE tunnel to convey an EVPN PW.
· Concatenate the EVPN PWs on the P device for the CEs to communicate at Layer 2 over the MPLS backbone.
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
XGE0/0/6 |
100.1.1.1/24 |
P |
Loop0 |
192.4.4.4/32 |
|
PE 1 |
Loop0 |
192.2.2.2/32 |
|
XGE0/0/6 |
23.1.1.2/24 |
|
|
XGE0/0/7 |
23.1.1.1/24 |
|
XGE0/0/7 |
26.2.2.2/24 |
|
CE 2 |
XGE0/0/6 |
100.1.1.2/24 |
PE 2 |
Loop0 |
192.3.3.3/32 |
|
|
|
|
|
XGE0/0/7 |
26.2.2.1/24 |
Procedure
1. Configure CE 1.
<CE1> system-view
[CE1] interface ten-gigabitethernet 0/0/6
[CE1-Ten-GigabitEthernet0/0/6] ip address 100.1.1.1 24
[CE1-Ten-GigabitEthernet0/0/6] quit
2. Configure PE 1:
# Configure the LSR ID.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 192.2.2.2 32
[PE1-LoopBack0] quit
[PE1] mpls lsr-id 192.2.2.2
# Enable L2VPN.
[PE1] l2vpn enable
# Set up an MPLS TE tunnel between PE 1 and the P device as described in MPLS TE configuration in MPLS Configuration Guide.
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE1] xconnect-group vpna
[PE1-xcg-vpna] evpn encapsulation mpls
[PE1-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE1-xcg-vpna-evpn-mpls] vpn-target 1:1 export-extcommunity
[PE1-xcg-vpna-evpn-mpls] vpn-target 1:2 import-extcommunity
[PE1-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE1-xcg-vpna] connection pw1
[PE1-xcg-vpna-pw1] evpn local-service-id 2 remote-service-id 1
[PE1-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE1-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE1-xcg-vpna-pw1] quit
[PE1-xcg-vpna] quit
# Create an IBGP connection to the P device, and enable BGP to advertise BGP EVPN routes to the P device.
[PE1] bgp 100
[PE1-bgp-default] peer 192.4.4.4 as-number 100
[PE1-bgp-default] peer 192.4.4.4 connect-interface LoopBack0
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 194.4.4.4 enable
[PE1-bgp-default-evpn] quit
[PE1-bgp-default] quit
3. Configure the P device:
# Configure the LSR ID.
<P> system-view
[P] interface loopback 0
[P-LoopBack0] ip address 192.4.4.4 32
[P-LoopBack0] quit
[P] mpls lsr-id 192.4.4.4
# Enable L2VPN.
[P] l2vpn enable
# Set up an MPLS TE tunnel to each PE as described in MPLS TE configuration in MPLS Configuration Guide.
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[P] xconnect-group vpna
[P-xcg-vpna] evpn encapsulation mpls
[P-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[P-xcg-vpna-evpn-mpls] vpn-target 1:2 export-extcommunity
[P-xcg-vpna-evpn-mpls] vpn-target 1:1 1:3 import-extcommunity
[P-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and create two EVPN PWs on the cross-connect.
[P-xcg-vpna] connection pw1
[P-xcg-vpna-pw1] evpn local-service-id 1 remote-service-id 2
[P-xcg-vpna-pw1] evpn local-service-id 3 remote-service-id 4
[P-xcg-vpna-pw1] quit
[P-xcg-vpna] quit
# Create an IBGP connection to each PE, and enable BGP to advertise BGP EVPN routes to the PEs.
[P] bgp 100
[P-bgp-default] peer 192.2.2.2 as-number 100
[P-bgp-default] peer 192.2.2.2 connect-interface LoopBack0
[P-bgp-default] peer 192.3.3.3 as-number 100
[P-bgp-default] peer 192.3.3.3 connect-interface LoopBack0
[P-bgp-default] address-family l2vpn evpn
[P-bgp-default-evpn] peer 192.2.2.2 enable
[P-bgp-default-evpn] peer 192.3.3.3 enable
[P-bgp-default-evpn] quit
[P-bgp-default] quit
4. Configure PE 2:
# Configure the LSR ID.
<PE2> system-view
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 192.3.3.3 32
[PE2-LoopBack0] quit
[PE2] mpls lsr-id 192.3.3.3
# Enable L2VPN.
[PE2] l2vpn enable
# Set up an MPLS TE tunnel between PE 2 and the P device as described in MPLS TE configuration in MPLS Configuration Guide.
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE2] xconnect-group vpna
[PE2-xcg-vpna] evpn encapsulation mpls
[PE2-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE2-xcg-vpna-evpn-mpls] vpn-target 1:3 export-extcommunity
[PE2-xcg-vpna-evpn-mpls] vpn-target 1:2 import-extcommunity
[PE2-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE2-xcg-vpna] connection pw1
[PE2-xcg-vpna-pw1] evpn local-service-id 4 remote-service-id 3
[PE2-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE2-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE2-xcg-vpna-pw1] quit
[PE2-xcg-vpna] quit
# Create an IBGP connection to the P device, and enable BGP to advertise BGP EVPN routes to the P device.
[PE2] bgp 100
[PE2-bgp-default] peer 192.4.4.4 as-number 100
[PE2-bgp-default] peer 192.4.4.4 connect-interface LoopBack0
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 192.4.4.4 enable
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] quit
5. Configure CE 2.
<CE2> system-view
[CE2] interface ten-gigabitethernet 0/0/6
[CE2-Ten-GigabitEthernet0/0/6] ip address 100.1.1.2 24
[CE2-Ten-GigabitEthernet0/0/6] quit
Verifying the configuration
# Verify that an EVPN PW has been established on PE 1.
[PE1] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.4.4.4 1 1151/1150 EVPN M 0 Up
# Verify that two EVPN PWs are concatenated on the P device.
[P] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 2
2 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.2.2.2 2 1150/1151 EVPN M 0 Up
192.3.3.3 4 1151/1151 EVPN M 1 Up
# Verify that an EVPN PW has been established on PE 2.
[PE2] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpn1a
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.4.4.4 3 1151/1151 EVPN M 0 Up
# Verify that CE 1 and CE 2 can ping each other. (Details not shown.)
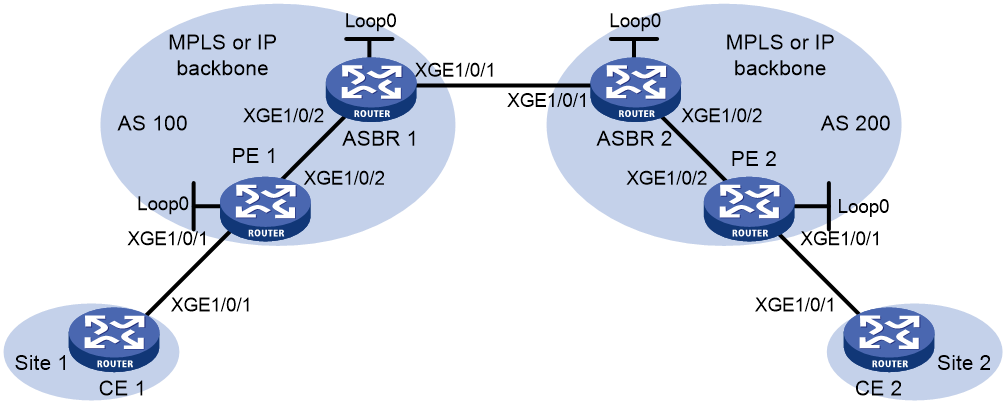
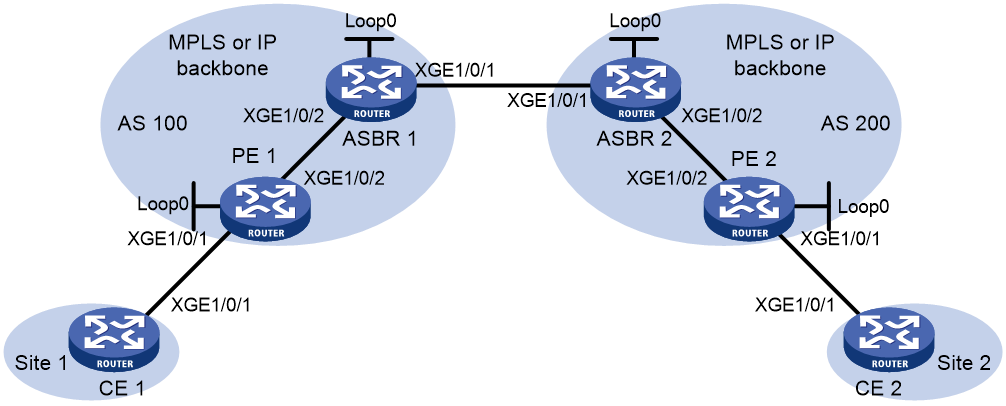
Example: Configuring inter-AS option A
Network configuration
As shown in Figure 13:
· Establish an EVPN PW between the PE and the ASBR in each AS.
· Associate Ten-GigabitEthernet 0/0/6 with the EVPN PW on each ASBR.
· Associate Ten-GigabitEthernet 0/0/6 with the EVPN PW on each PE.
· Run OSPF on the MPLS backbone of each AS.
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
XGE0/0/6 |
100.1.1.1/24 |
ASBR 1 |
Loop0 |
192.2.2.2/32 |
|
PE 1 |
Loop0 |
192.1.1.1/32 |
|
XGE0/0/7 |
23.1.1.2/24 |
|
|
XGE0/0/7 |
23.1.1.1/24 |
|
XGE0/0/6 |
26.2.2.2/24 |
|
PE 2 |
Loop0 |
192.4.4.4/32 |
ASBR 2 |
Loop0 |
192.3.3.3/32 |
|
|
XGE0/0/7 |
22.2.2.1/24 |
|
XGE0/0/6 |
26.2.2.3/24 |
|
CE 2 |
XGE0/0/6 |
100.1.1.2/24 |
|
XGE0/0/7 |
22.2.2.3/24 |
Procedure
1. Configure CE 1.
<CE1> system-view
[CE1] interface ten-gigabitethernet 0/0/6
[CE1-Ten-GigabitEthernet0/0/6] ip address 100.1.1.1 24
[CE1-Ten-GigabitEthernet0/0/6] quit
2. Configure PE 1:
# Configure the LSR ID.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 192.1.1.1 32
[PE1-LoopBack0] quit
[PE1] mpls lsr-id 192.1.1.1
# Enable L2VPN.
[PE1] l2vpn enable
# Enable global LDP.
[PE1] mpls ldp
[PE1-ldp] quit
# Enable LDP on Ten-GigabitEthernet 0/0/7, the interface connected to ASBR 1.
[PE1] interface ten-gigabitethernet 0/0/7
[PE1-Ten-GigabitEthernet0/0/7] ip address 23.1.1.1 24
[PE1-Ten-GigabitEthernet0/0/7] mpls enable
[PE1-Ten-GigabitEthernet0/0/7] mpls ldp enable
[PE1-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[PE1] ospf
[PE1-ospf-1] area 0
[PE1-ospf-1-area-0.0.0.0] network 23.1.1.0 0.0.0.255
[PE1-ospf-1-area-0.0.0.0] network 192.1.1.1 0.0.0.0
[PE1-ospf-1-area-0.0.0.0] quit
[PE1-ospf-1] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE1] xconnect-group vpna
[PE1-xcg-vpna] evpn encapsulation mpls
[PE1-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE1-xcg-vpna-evpn-mpls] vpn-target 1:1 export-extcommunity
[PE1-xcg-vpna-evpn-mpls] vpn-target 1:2 import-extcommunity
[PE1-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE1-xcg-vpna] connection pw1
[PE1-xcg-vpna-pw1] evpn local-service-id 2 remote-service-id 1
[PE1-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE1-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE1-xcg-vpna-pw1] quit
[PE1-xcg-vpna] quit
# Create an IBGP connection to ASBR 1, and enable BGP to advertise BGP EVPN routes to ASBR 1.
[PE1] bgp 100
[PE1-bgp-default] peer 192.2.2.2 as-number 100
[PE1-bgp-default] peer 192.2.2.2 connect-interface LoopBack0
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 192.2.2.2 enable
[PE1-bgp-default-evpn] quit
[PE1-bgp-default] quit
3. Configure ASBR 1:
# Configure the LSR ID.
<ASBR1> system-view
[ASBR1] interface loopback 0
[ASBR1-LoopBack0] ip address 192.2.2.2 32
[ASBR1-LoopBack0] quit
[ASBR1] mpls lsr-id 192.2.2.2
# Enable L2VPN.
[ASBR1] l2vpn enable
# Enable global LDP.
[ASBR1] mpls ldp
[ASBR1-ldp] quit
# Enable LDP on Ten-GigabitEthernet 0/0/7, the interface connected to PE 1.
[ASBR1] interface ten-gigabitethernet 0/0/7
[ASBR1-Ten-GigabitEthernet0/0/7] ip address 23.1.1.2 24
[ASBR1-Ten-GigabitEthernet0/0/7] mpls enable
[ASBR1-Ten-GigabitEthernet0/0/7] mpls ldp enable
[ASBR1-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[ASBR1] ospf
[ASBR1-ospf-1] area 0
[ASBR1-ospf-1-area-0.0.0.0] network 23.1.1.0 0.0.0.255
[ASBR1-ospf-1-area-0.0.0.0] network 192.2.2.2 0.0.0.0
[ASBR1-ospf-1-area-0.0.0.0] quit
[ASBR1-ospf-1] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[ASBR1] xconnect-group vpna
[ASBR1-xcg-vpna] evpn encapsulation mpls
[ASBR1-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[ASBR1-xcg-vpna-evpn-mpls] vpn-target 1:2 export-extcommunity
[ASBR1-xcg-vpna-evpn-mpls] vpn-target 1:1 import-extcommunity
[ASBR1-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 (the interface connected to ASBR 2) to it. Create an EVPN PW on the cross-connect.
[ASBR1-xcg-vpna] connection pw1
[ASBR1-xcg-vpna-pw1] evpn local-service-id 1 remote-service-id 2
[ASBR1-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[ASBR1-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[ASBR1-xcg-vpna-pw1] quit
[ASBR1-xcg-vpna] quit
# Create an IBGP connection to PE 1, and enable BGP to advertise BGP EVPN routes to PE 1.
[ASBR1] bgp 100
[ASBR1-bgp-default] peer 192.1.1.1 as-number 100
[ASBR1-bgp-default] peer 192.1.1.1 connect-interface LoopBack0
[ASBR1-bgp-default] address-family l2vpn evpn
[ASBR1-bgp-default-evpn] peer 192.1.1.1 enable
[ASBR1-bgp-default-evpn] quit
[ASBR1-bgp-default] quit
4. Configure ASBR 2:
# Configure the LSR ID.
<ASBR2> system-view
[ASBR2] interface loopback 0
[ASBR2-LoopBack0] ip address 192.3.3.3 32
[ASBR2-LoopBack0] quit
[ASBR2] mpls lsr-id 192.3.3.3
# Enable L2VPN.
[ASBR2] l2vpn enable
# Enable global LDP.
[ASBR2] mpls ldp
[ASBR2-ldp] quit
# Enable LDP on Ten-GigabitEthernet 0/0/7, the interface connected to PE 2.
[ASBR2] interface ten-gigabitethernet 0/0/7
[ASBR2-Ten-GigabitEthernet0/0/7] ip address 22.2.2.3 24
[ASBR2-Ten-GigabitEthernet0/0/7] mpls enable
[ASBR2-Ten-GigabitEthernet0/0/7] mpls ldp enable
[ASBR2-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[ASBR2] ospf
[ASBR2-ospf-1] area 0
[ASBR2-ospf-1-area-0.0.0.0] network 22.2.2.0 0.0.0.255
[ASBR2-ospf-1-area-0.0.0.0] network 192.3.3.3 0.0.0.0
[ASBR2-ospf-1-area-0.0.0.0] quit
[ASBR2-ospf-1] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[ASBR2] xconnect-group vpna
[ASBR2-xcg-vpna] evpn encapsulation mpls
[ASBR2-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[ASBR2-xcg-vpna-evpn-mpls] vpn-target 2:2 export-extcommunity
[ASBR2-xcg-vpna-evpn-mpls] vpn-target 2:1 import-extcommunity
[ASBR2-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 (the interface connected to ASBR 1) to it. Create an EVPN PW on the cross-connect.
[ASBR2-xcg-vpna] connection pw1
[ASBR2-xcg-vpna-pw1] evpn local-service-id 3 remote-service-id 4
[ASBR2-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[ASBR2-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[ASBR2-xcg-vpna-pw1] quit
[ASBR2-xcg-vpna] quit
# Create an IBGP connection to PE 2, and enable BGP to advertise BGP EVPN routes to PE 2.
[ASBR2] bgp 200
[ASBR2-bgp-default] peer 192.4.4.4 as-number 200
[ASBR2-bgp-default] peer 192.4.4.4 connect-interface LoopBack0
[ASBR2-bgp-default] address-family l2vpn evpn
[ASBR2-bgp-default-evpn] peer 192.4.4.4 enable
[ASBR2-bgp-default-evpn] quit
[ASBR2-bgp-default] quit
5. Configure PE 2:
# Configure the LSR ID.
<PE2> system-view
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 192.4.4.4 32
[PE2-LoopBack0] quit
[PE2] mpls lsr-id 192.4.4.4
# Enable L2VPN.
[PE2] l2vpn enable
# Enable global LDP.
[PE2] mpls ldp
[PE2-ldp] quit
# Enable LDP on Ten-GigabitEthernet 0/0/7, the interface connected to ASBR 2.
[PE2] interface ten-gigabitethernet 0/0/7
[PE2-Ten-GigabitEthernet0/0/7] ip address 22.2.2.1 24
[PE2-Ten-GigabitEthernet0/0/7] mpls enable
[PE2-Ten-GigabitEthernet0/0/7] mpls ldp enable
[PE2-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[PE2] ospf
[PE2-ospf-1] area 0
[PE2-ospf-1-area-0.0.0.0] network 192.4.4.4 0.0.0.0
[PE2-ospf-1-area-0.0.0.0] network 22.2.2.0 0.0.0.255
[PE2-ospf-1-area-0.0.0.0] quit
[PE2-ospf-1] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE2] xconnect-group vpna
[PE2-xcg-vpna] evpn encapsulation mpls
[PE2-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE2-xcg-vpna-evpn-mpls] vpn-target 2:1 export-extcommunity
[PE2-xcg-vpna-evpn-mpls] vpn-target 2:2 import-extcommunity
[PE2-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE2-xcg-vpna] connection pw1
[PE2-xcg-vpna-pw1] evpn local-service-id 4 remote-service-id 3
[PE2-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE2-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE2-xcg-vpna-pw1] quit
[PE2-xcg-vpna] quit
# Create an IBGP connection to ASBR 2, and enable BGP to advertise BGP EVPN routes to ASBR 2.
[PE2] bgp 200
[PE2-bgp-default] peer 192.3.3.3 as-number 200
[PE2-bgp-default] peer 192.3.3.3 connect-interface LoopBack0
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 192.3.3.3 enable
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] quit
6. Configure CE 2.
<CE2> system-view
[CE2] interface ten-gigabitethernet 0/0/6
[CE2-Ten-GigabitEthernet0/0/6] ip address 100.1.1.2 24
[CE2-Ten-GigabitEthernet0/0/6] quit
Verifying the configuration
# Verify that an EVPN PW has been established on PE 1.
[PE1] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.2.2.2 1 710127/710126 EVPN M 0 Up
# Verify that an EVPN PW has been established on ASBR 1.
[ASBR1] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 2
2 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpn1
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.1.1.1 2 710126/710127 EVPN M 0 Up
# Verify that an EVPN PW has been established on ASBR 2.
[ASBR2] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 2
2 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.4.4.4 4 710127/710127 EVPN M 1 Up
# Verify that an EVPN PW has been established on PE 2.
[PE2] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.3.3.3 3 710127/710127 EVPN M 0 Up
# Verify that CE 1 and CE 2 can ping each other. (Details not shown.)
Example: Configuring inter-AS option B
Network configuration
As shown in Figure 14:
· Establish an EVPN PW between the PE and the ASBR in each AS, and use LDP to establish the public tunnels that convey the EVPN PWs.
· Establish an EVPN PW between the ASBRs, and configure BGP to advertise labeled IPv4 unicast routes to establish the public tunnel that conveys the EVPN PW.
· Concatenate the EVPN PWs on the ASBRs.
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
XGE0/0/6 |
100.1.1.1/24 |
ASBR 1 |
Loop0 |
192.2.2.2/32 |
|
PE 1 |
Loop0 |
192.1.1.1/32 |
|
XGE0/0/7 |
23.1.1.2/24 |
|
|
XGE0/0/7 |
23.1.1.1/24 |
|
XGE0/0/6 |
26.2.2.2/24 |
|
PE 2 |
Loop0 |
192.4.4.4/32 |
ASBR 2 |
Loop0 |
192.3.3.3/32 |
|
|
XGE0/0/7 |
22.2.2.1/24 |
|
XGE0/0/6 |
26.2.2.3/24 |
|
CE 2 |
XGE0/0/6 |
100.1.1.2/24 |
|
XGE0/0/7 |
22.2.2.3/24 |
Procedure
1. Configure CE 1.
<CE1> system-view
[CE1] interface ten-gigabitethernet 0/0/6
[CE1-Ten-GigabitEthernet0/0/6] ip address 100.1.1.1 24
[CE1-Ten-GigabitEthernet0/0/6] quit
2. Configure PE 1:
# Configure the LSR ID.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 192.1.1.1 32
[PE1-LoopBack0] quit
[PE1] mpls lsr-id 192.1.1.1
# Enable L2VPN.
[PE1] l2vpn enable
# Enable global LDP.
[PE1] mpls ldp
[PE1-ldp] quit
# Enable LDP on Ten-GigabitEthernet 0/0/7, the interface connected to ASBR 1.
[PE1] interface ten-gigabitethernet 0/0/7
[PE1-Ten-GigabitEthernet0/0/7] ip address 23.1.1.1 24
[PE1-Ten-GigabitEthernet0/0/7] mpls enable
[PE1-Ten-GigabitEthernet0/0/7] mpls ldp enable
[PE1-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[PE1] ospf
[PE1-ospf-1] area 0
[PE1-ospf-1-area-0.0.0.0] network 23.1.1.0 0.0.0.255
[PE1-ospf-1-area-0.0.0.0] network 192.1.1.1 0.0.0.0
[PE1-ospf-1-area-0.0.0.0] quit
[PE1-ospf-1] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE1] xconnect-group vpna
[PE1-xcg-vpna] evpn encapsulation mpls
[PE1-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE1-xcg-vpna-evpn-mpls] vpn-target 1:1 export-extcommunity
[PE1-xcg-vpna-evpn-mpls] vpn-target 1:2 import-extcommunity
[PE1-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE1-xcg-vpna] connection pw1
[PE1-xcg-vpna-pw1] evpn local-service-id 2 remote-service-id 1
[PE1-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE1-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE1-xcg-vpna-pw1] quit
[PE1-xcg-vpna] quit
# Create an IBGP connection to ASBR 1, and enable BGP to advertise BGP EVPN routes to ASBR 1.
[PE1] bgp 100
[PE1-bgp-default] peer 192.2.2.2 as-number 100
[PE1-bgp-default] peer 192.2.2.2 connect-interface LoopBack0
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 192.2.2.2 enable
[PE1-bgp-default-evpn] quit
[PE1-bgp-default] quit
3. Configure ASBR 1:
# Configure the LSR ID.
<ASBR1> system-view
[ASBR1] interface loopback 0
[ASBR1-LoopBack0] ip address 192.2.2.2 32
[ASBR1-LoopBack0] quit
[ASBR1] mpls lsr-id 192.2.2.2
# Enable L2VPN.
[ASBR1] l2vpn enable
# Enable global LDP.
[ASBR1] mpls ldp
[ASBR1-ldp] quit
# Enable LDP on Ten-GigabitEthernet 0/0/7, the interface connected to PE 1.
[ASBR1] interface ten-gigabitethernet 0/0/7
[ASBR1-Ten-GigabitEthernet0/0/7] ip address 23.1.1.2 24
[ASBR1-Ten-GigabitEthernet0/0/7] mpls enable
[ASBR1-Ten-GigabitEthernet0/0/7] mpls ldp enable
[ASBR1-Ten-GigabitEthernet0/0/7] quit
# Enable MPLS on Ten-GigabitEthernet 0/0/6, the interface connected to ASBR 2.
[ASBR1] interface ten-gigabitethernet 0/0/6
[ASBR1-Ten-GigabitEthernet0/0/6] ip address 26.2.2.2 24
[ASBR1-Ten-GigabitEthernet0/0/6] mpls enable
[ASBR1-Ten-GigabitEthernet0/0/6] quit
# Configure OSPF for LDP to create LSPs.
[ASBR1] ospf
[ASBR1-ospf-1] area 0
[ASBR1-ospf-1-area-0.0.0.0] network 23.1.1.0 0.0.0.255
[ASBR1-ospf-1-area-0.0.0.0] network 192.2.2.2 0.0.0.0
[ASBR1-ospf-1-area-0.0.0.0] quit
[ASBR1-ospf-1] quit
# Create an IBGP connection to PE 1, and enable BGP to advertise BGP EVPN routes to PE 1.
[ASBR1] bgp 100
[ASBR1-bgp-default] peer 192.1.1.1 as-number 100
[ASBR1-bgp-default] peer 192.1.1.1 connect-interface LoopBack0
[ASBR1-bgp-default] address-family l2vpn evpn
[ASBR1-bgp-default-evpn] peer 192.1.1.1 enable
[ASBR1-bgp-default-evpn] quit
[ASBR1-bgp-default] quit
# Create an EBGP connection to ASBR 2, and enable BGP to advertise BGP EVPN routes and labeled unicast routes to ASBR 2.
[ASBR1] bgp 100
[ASBR1-bgp-default] peer 26.2.2.3 as-number 200
[ASBR1-bgp-default] address-family ipv4 unicast
[ASBR1-bgp-default-ipv4] import-route direct
[ASBR1-bgp-default-ipv4] peer 26.2.2.3 enable
[ASBR1-bgp-default-ipv4] peer 26.2.2.3 route-policy policy1 export
[ASBR1-bgp-default-ipv4] peer 26.2.2.3 label-route-capability
[ASBR1-bgp-default] address-family l2vpn evpn
[ASBR1-bgp-default-evpn] peer 26.2.2.3 enable
[ASBR1-bgp-default-evpn] quit
[ASBR1-bgp-default] quit
[ASBR1] route-policy policy1 permit node 1
[ASBR1-route-policy-policy1-1] apply mpls-label
[ASBR1-route-policy-policy1-1] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[ASBR1] xconnect-group vpna
[ASBR1-xcg-vpna] evpn encapsulation mpls
[ASBR1-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[ASBR1-xcg-vpna-evpn-mpls] vpn-target 1:2 export-extcommunity
[ASBR1-xcg-vpna-evpn-mpls] vpn-target 1:1 2:2 import-extcommunity
[ASBR1-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and create two EVPN PWs on the cross-connect.
[ASBR1-xcg-vpna] connection pw1
[ASBR1-xcg-vpna-pw1] evpn local-service-id 1 remote-service-id 2
[ASBR1-xcg-vpna-pw1] evpn local-service-id 3 remote-service-id 4
[ASBR1-xcg-vpna-pw1] quit
[ASBR1-xcg-vpna] quit
4. Configure ASBR 2:
# Configure the LSR ID.
<ASBR2> system-view
[ASBR2] interface loopback 0
[ASBR2-LoopBack0] ip address 192.3.3.3 32
[ASBR2-LoopBack0] quit
[ASBR2] mpls lsr-id 192.3.3.3
# Enable L2VPN.
[ASBR2] l2vpn enable
# Enable global LDP.
[ASBR2] mpls ldp
[ASBR2-ldp] quit
# Enable LDP on Ten-GigabitEthernet 0/0/7, the interface connected to PE 2.
[ASBR2] interface ten-gigabitethernet 0/0/7
[ASBR2-Ten-GigabitEthernet0/0/7] ip address 22.2.2.3 24
[ASBR2-Ten-GigabitEthernet0/0/7] mpls enable
[ASBR2-Ten-GigabitEthernet0/0/7] mpls ldp enable
[ASBR2-Ten-GigabitEthernet0/0/7] quit
# Enable MPLS on Ten-GigabitEthernet 0/0/6, the interface connected to ASBR 1.
[ASBR2] interface ten-gigabitethernet 0/0/6
[ASBR2-Ten-GigabitEthernet0/0/6] ip address 26.2.2.3 24
[ASBR2-Ten-GigabitEthernet0/0/6] mpls enable
[ASBR2-Ten-GigabitEthernet0/0/6] quit
# Configure OSPF for LDP to create LSPs.
[ASBR2] ospf
[ASBR2-ospf-1] area 0
[ASBR2-ospf-1-area-0.0.0.0] network 22.2.2.0 0.0.0.255
[ASBR2-ospf-1-area-0.0.0.0] network 192.3.3.3 0.0.0.0
[ASBR2-ospf-1-area-0.0.0.0] quit
[ASBR2-ospf-1] quit
# Create an IBGP connection to PE 2, and enable BGP to advertise BGP EVPN routes to PE 2.
[ASBR2] bgp 200
[ASBR2-bgp-default] peer 192.4.4.4 as-number 200
[ASBR2-bgp-default] peer 192.4.4.4 connect-interface LoopBack0
[ASBR2-bgp-default] address-family l2vpn evpn
[ASBR2-bgp-default-evpn] peer 192.4.4.4 enable
[ASBR2-bgp-default-evpn] quit
[ASBR2-bgp-default] quit
# Create an EBGP connection to ASBR 1, and enable BGP to advertise BGP EVPN routes and labeled unicast routes to ASBR 1.
[ASBR1] bgp 100
[ASBR2-bgp-default] peer 26.2.2.2 as-number 100
[ASBR2-bgp-default] address-family ipv4 unicast
[ASBR2-bgp-default-ipv4] import-route direct
[ASBR2-bgp-default-ipv4] peer 26.2.2.2 enable
[ASBR2-bgp-default-ipv4] peer 26.2.2.2 route-policy policy1 export
[ASBR2-bgp-default-ipv4] peer 26.2.2.2 label-route-capability
[ASBR2-bgp-default-ipv4] quit
[ASBR2-bgp-default] address-family l2vpn evpn
[ASBR2-bgp-default-evpn] peer 26.2.2.2 enable
[ASBR2-bgp-default-evpn] quit
[ASBR2-bgp-default] quit
[ASBR2] route-policy policy1 permit node 1
[ASBR2-route-policy-policy1-1] apply mpls-label
[ASBR2-route-policy-policy1-1] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[ASBR2] xconnect-group vpna
[ASBR2-xcg-vpna] evpn encapsulation mpls
[ASBR2-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[ASBR2-xcg-vpna-evpn-mpls] vpn-target 2:2 export-extcommunity
[ASBR2-xcg-vpna-evpn-mpls] vpn-target 1:2 2:1 import-extcommunity
[ASBR2-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and create two EVPN PWs on the cross-connect.
[ASBR2-xcg-vpna] connection pw1
[ASBR2-xcg-vpna-pw1] evpn local-service-id 4 remote-service-id 3
[ASBR2-xcg-vpna-pw1] evpn local-service-id 5 remote-service-id 6
[ASBR2-xcg-vpna-pw1] quit
[ASBR2-xcg-vpna] quit
5. Configure PE 2:
# Configure the LSR ID.
<PE2> system-view
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 192.4.4.4 32
[PE2-LoopBack0] quit
[PE2] mpls lsr-id 192.4.4.4
# Enable L2VPN.
[PE2] l2vpn enable
# Enable global LDP.
[PE2] mpls ldp
[PE2-ldp] quit
# Enable LDP on Ten-GigabitEthernet 0/0/7, the interface connected to ASBR 2.
[PE2] interface ten-gigabitethernet 0/0/7
[PE2-Ten-GigabitEthernet0/0/7] ip address 22.2.2.1 24
[PE2-Ten-GigabitEthernet0/0/7] mpls enable
[PE2-Ten-GigabitEthernet0/0/7] mpls ldp enable
[PE2-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[PE2] ospf
[PE2-ospf-1] area 0
[PE2-ospf-1-area-0.0.0.0] network 192.4.4.4 0.0.0.0
[PE2-ospf-1-area-0.0.0.0] network 22.2.2.0 0.0.0.255
[PE2-ospf-1-area-0.0.0.0] quit
[PE2-ospf-1] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE2] xconnect-group vpna
[PE2-xcg-vpna] evpn encapsulation mpls
[PE2-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE2-xcg-vpna-evpn-mpls] vpn-target 2:1 export-extcommunity
[PE2-xcg-vpna-evpn-mpls] vpn-target 2:2 import-extcommunity
[PE2-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE2-xcg-vpna] connection pw1
[PE2-xcg-vpna-pw1] evpn local-service-id 6 remote-service-id 5
[PE2-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE2-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE2-xcg-vpna-pw1] quit
[PE2-xcg-vpna] quit
# Create an IBGP connection to ASBR 2, and enable BGP to advertise BGP EVPN routes to ASBR 2.
[PE2] bgp 200
[PE2-bgp-default] peer 192.3.3.3 as-number 200
[PE2-bgp-default] peer 192.3.3.3 connect-interface LoopBack0
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 192.3.3.3 enable
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] quit
6. Configure CE 2.
<CE2> system-view
[CE2] interface ten-gigabitethernet 0/0/6
[CE2-Ten-GigabitEthernet0/0/6] ip address 100.1.1.2 24
[CE2-Ten-GigabitEthernet0/0/6] quit
Verifying the configuration
# Verify that an EVPN PW has been established on PE 1.
[PE1] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass,
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.2.2.2 1 710127/710126 EVPN M 0 Up
# Verify that two EVPN PWs are concatenated on ASBR 1.
[ASBR1] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 2
2 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpn1
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.1.1.1 2 710126/710127 EVPN M 0 Up
26.2.2.3 4 710127/710126 EVPN M 1 Up
# Verify that two EVPN PWs are concatenated on ASBR 2.
[ASBR2] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 2
2 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
26.2.2.2 3 710126/710127 EVPN M 0 Up
192.4.4.4 6 710127/710127 EVPN M 1 Up
# Verify that an EVPN PW has been established on PE 2.
[PE2] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.3.3.3 5 710127/710127 EVPN M 0 Up
# Verify that CE 1 and CE 2 can ping each other. (Details not shown.)
Example: Configuring inter-AS option C
Network configuration
As shown in Figure 15:
· Configure the PE and the ASBR in each AS to use IBGP to exchange labeled IPv4 routes.
· Configure the PEs to exchange BGP EVPN routes to establish an EVPN PW.
· Establish an EVPN PW between the ASBRs, and configure BGP to advertise labeled IPv4 unicast routes to establish the public tunnel that conveys the EVPN PW.
· Configure a PBR policy on each ASBR for it to insert labels into received routes.
· Configure the ASBRs to exchange labeled IPv4 routes through EBGP.
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
XGE0/0/6 |
100.1.1.1/24 |
ASBR 1 |
Loop0 |
192.2.2.2/32 |
|
PE 1 |
Loop0 |
192.1.1.1/32 |
|
XGE0/0/7 |
23.1.1.2/24 |
|
|
XGE0/0/7 |
23.1.1.1/24 |
|
XGE0/0/6 |
26.2.2.2/24 |
|
PE 2 |
Loop0 |
192.4.4.4/32 |
ASBR 2 |
Loop0 |
192.3.3.3/32 |
|
|
XGE0/0/7 |
22.2.2.1/24 |
|
XGE0/0/6 |
26.2.2.3/24 |
|
CE 2 |
XGE0/0/6 |
100.1.1.2/24 |
|
XGE0/0/7 |
22.2.2.3/24 |
Procedure
1. Configure CE 1.
<CE1> system-view
[CE1] interface ten-gigabitethernet 0/0/6
[CE1-Ten-GigabitEthernet0/0/6] ip address 100.1.1.1 24
[CE1-Ten-GigabitEthernet0/0/6] quit
2. Configure PE 1:
# Configure the LSR ID.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 192.1.1.1 32
[PE1-LoopBack0] quit
[PE1] mpls lsr-id 192.1.1.1
# Enable L2VPN.
[PE1] l2vpn enable
# Enable global LDP.
[PE1] mpls ldp
[PE1-ldp] quit
# Enable LDP on Ten-GigabitEthernet 0/0/7, the interface connected to ASBR 1.
[PE1] interface ten-gigabitethernet 0/0/7
[PE1-Ten-GigabitEthernet0/0/7] ip address 23.1.1.1 24
[PE1-Ten-GigabitEthernet0/0/7] mpls enable
[PE1-Ten-GigabitEthernet0/0/7] mpls ldp enable
[PE1-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[PE1] ospf
[PE1-ospf-1] area 0
[PE1-ospf-1-area-0.0.0.0] network 23.1.1.0 0.0.0.255
[PE1-ospf-1-area-0.0.0.0] network 192.1.1.1 0.0.0.0
[PE1-ospf-1-area-0.0.0.0] quit
[PE1-ospf-1] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE1] xconnect-group vpna
[PE1-xcg-vpna] evpn encapsulation mpls
[PE1-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE1-xcg-vpna-evpn-mpls] vpn-target 1:1 export-extcommunity
[PE1-xcg-vpna-evpn-mpls] vpn-target 2:2 import-extcommunity
[PE1-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE1-xcg-vpna] connection pw1
[PE1-xcg-vpna-pw1] evpn local-service-id 2 remote-service-id 1
[PE1-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE1-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE1-xcg-vpna-pw1] quit
[PE1-xcg-vpna] quit
# Create an IBGP connection to ASBR 1, and enable BGP to advertise BGP EVPN routes and labeled unicast routes to ASBR 1.
[PE1] bgp 100
[PE1-bgp-default] peer 192.2.2.2 as-number 100
[PE1-bgp-default] peer 192.2.2.2 connect-interface LoopBack0
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 192.2.2.2 enable
[PE1-bgp-default] address-family ipv4 unicast
[PE1-bgp-default-ipv4] peer 192.2.2.2 enable
[PE1-bgp-default-ipv4] peer 192.2.2.2 label-route-capability
[PE1-bgp-default-ipv4] quit
[PE1-bgp-default] quit
# Configure BGP to advertise BGP EVPN routes to PE 2 to establish an EVPN PW.
[PE1] bgp 100
[PE1-bgp-default] peer 192.4.4.4 as-number 200
[PE1-bgp-default] peer 192.4.4.4 connect-interface LoopBack0
[PE1-bgp-default] peer 192.4.4.4 ebgp-max-hop 10
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 192.4.4.4 enable
[PE1-bgp-default-evpn] quit
[PE1-bgp-default] quit
3. Configure ASBR 1:
# Configure the LSR ID.
<ASBR1> system-view
[ASBR1] interface loopback 0
[ASBR1-LoopBack0] ip address 192.2.2.2 32
[ASBR1-LoopBack0] quit
[ASBR1] mpls lsr-id 192.2.2.2
# Enable L2VPN.
[ASBR1] l2vpn enable
# Enable global LDP.
[ASBR1] mpls ldp
[ASBR1-ldp] quit
# Enable LDP on Ten-GigabitEthernet 0/0/7, the interface connected to PE 1.
[ASBR1] interface ten-gigabitethernet 0/0/7
[ASBR1-Ten-GigabitEthernet0/0/7] ip address 23.1.1.2 24
[ASBR1-Ten-GigabitEthernet0/0/7] mpls enable
[ASBR1-Ten-GigabitEthernet0/0/7] mpls ldp enable
[ASBR1-Ten-GigabitEthernet0/0/7] quit
# Enable MPLS on Ten-GigabitEthernet 0/0/6, the interface connected to ASBR 2.
[ASBR1] interface ten-gigabitethernet 0/0/6
[ASBR1-Ten-GigabitEthernet0/0/6] ip address 26.2.2.2 24
[ASBR1-Ten-GigabitEthernet0/0/6] mpls enable
[ASBR1-Ten-GigabitEthernet0/0/6] quit
# Configure OSPF for LDP to create LSPs.
[ASBR1] ospf
[ASBR1-ospf-1] area 0
[ASBR1-ospf-1-area-0.0.0.0] network 23.1.1.0 0.0.0.255
[ASBR1-ospf-1-area-0.0.0.0] network 192.2.2.2 0.0.0.0
[ASBR1-ospf-1-area-0.0.0.0] quit
[ASBR1-ospf-1] quit
# Create routing policies.
[ASBR1] route-policy policy1 permit node 1
[ASBR1-route-policy-policy1-1] apply mpls-label
[ASBR1-route-policy-policy1-1] quit
[ASBR1] route-policy policy2 permit node 1
[ASBR1-route-policy-policy2-1] if-match mpls-label
[ASBR1-route-policy-policy2-1] apply mpls-label
[ASBR1-route-policy-policy2-1] quit
# Enable BGP on ASBR 1, and apply the routing policy policy2 to routes advertised to IBGP peer 192.1.1.1.
[ASBR1] bgp 100
[ASBR1-bgp-default] peer 192.1.1.1 as-number 100
[ASBR1-bgp-default] peer 192.1.1.1 connect-interface LoopBack0
[ASBR1-bgp-default] address-family ipv4 unicast
[ASBR1-bgp-default-ipv4] peer 192.1.1.1 enable
[ASBR1-bgp-default-ipv4] peer 192.1.1.1 route-policy policy2 export
# Enable the capability to advertise labeled routes to IBGP peer 192.1.1.1 and to receive labeled routes from the peer.
[ASBR1-bgp-default-ipv4] peer 192.1.1.1 label-route-capability
# Redistribute routes from OSPF process 1 to BGP.
[ASBR1-bgp-default-ipv4] import-route ospf 1
[ASBR1-bgp-default-ipv4] quit
# Advertise BGP EVPN routes to IBGP peer 192.1.1.1.
[ASBR1-bgp-default] address-family l2vpn evpn
[ASBR1-bgp-default-evpn] peer 192.1.1.1 enable
[ASBR1-bgp-default-evpn] quit
# Apply routing policy policy1 to routes advertised to EBGP peer 26.2.2.3.
[ASBR1-bgp-default] peer 26.2.2.3 as-number 200
[ASBR1-bgp-default] address-family ipv4 unicast
[ASBR1-bgp-default-ipv4] peer 26.2.2.3 enable
[ASBR1-bgp-default-ipv4] peer 26.2.2.3 route-policy policy1 export
# Enable the capability to advertise labeled routes to EBGP peer 26.2.2.3 and to receive labeled routes from the peer.
[ASBR1-bgp-default-ipv4] peer 26.2.2.3 label-route-capability
[ASBR1-bgp-default-ipv4] quit
# Advertise BGP EVPN routes to EBGP peer 26.2.2.3.
[ASBR1-bgp-default] address-family l2vpn evpn
[ASBR1-bgp-default-evpn] peer 26.2.2.3 enable
[ASBR1-bgp-default-evpn] quit
[ASBR1-bgp-default] quit
4. Configure ASBR 2:
# Configure the LSR ID.
<ASBR2> system-view
[ASBR2] interface loopback 0
[ASBR2-LoopBack0] ip address 192.3.3.3 32
[ASBR2-LoopBack0] quit
[ASBR2] mpls lsr-id 192.3.3.3
# Enable L2VPN.
[ASBR2] l2vpn enable
# Enable global LDP.
[ASBR2] mpls ldp
[ASBR2-ldp] quit
# Enable LDP on Ten-GigabitEthernet 0/0/7, the interface connected to PE 2.
[ASBR2] interface ten-gigabitethernet 0/0/7
[ASBR2-Ten-GigabitEthernet0/0/7] ip address 22.2.2.3 24
[ASBR2-Ten-GigabitEthernet0/0/7] mpls enable
[ASBR2-Ten-GigabitEthernet0/0/7] mpls ldp enable
[ASBR2-Ten-GigabitEthernet0/0/7] quit
# Enable MPLS on Ten-GigabitEthernet 0/0/6, the interface connected to ASBR 1.
[ASBR2] interface ten-gigabitethernet 0/0/6
[ASBR2-Ten-GigabitEthernet0/0/6] ip address 26.2.2.3 24
[ASBR2-Ten-GigabitEthernet0/0/6] mpls enable
[ASBR2-Ten-GigabitEthernet0/0/6] quit
# Configure OSPF for LDP to create LSPs.
[ASBR2] ospf
[ASBR2-ospf-1] area 0
[ASBR2-ospf-1-area-0.0.0.0] network 22.2.2.0 0.0.0.255
[ASBR2-ospf-1-area-0.0.0.0] network 192.3.3.3 0.0.0.0
[ASBR2-ospf-1-area-0.0.0.0] quit
[ASBR2-ospf-1] quit
# Create routing policies.
[ASBR2] route-policy policy1 permit node 1
[ASBR2-route-policy-policy1-1] apply mpls-label
[ASBR2-route-policy-policy1-1] quit
[ASBR2] route-policy policy2 permit node 1
[ASBR2-route-policy-policy2-1] if-match mpls-label
[ASBR2-route-policy-policy2-1] apply mpls-label
[ASBR2-route-policy-policy2-1] quit
# Enable BGP on ASBR 2, and apply the routing policy policy2 to routes advertised to IBGP peer 192.4.4.4.
[ASBR2] bgp 200
[ASBR2-bgp-default] peer 192.4.4.4 as-number 200
[ASBR2-bgp-default] peer 192.4.4.4 connect-interface LoopBack0
[ASBR2-bgp-default] address-family ipv4 unicast
[ASBR2-bgp-default-ipv4] peer 192.4.4.4 enable
[ASBR2-bgp-default-ipv4] peer 192.4.4.4 route-policy policy2 export
# Enable the capability to advertise labeled routes to IBGP peer 192.4.4.4 and to receive labeled routes from the peer.
[ASBR2-bgp-default-ipv4] peer 192.4.4.4 label-route-capability
# Redistribute routes from OSPF process 1 to BGP.
[ASBR2-bgp-default-ipv4] import-route ospf 1
[ASBR2-bgp-default-ipv4] quit
# Advertise BGP EVPN routes to IBGP peer 192.4.4.4.
[ASBR2-bgp-default] address-family l2vpn evpn
[ASBR2-bgp-default-evpn] peer 192.4.4.4 enable
[ASBR2-bgp-default-evpn] quit
# Apply routing policy policy1 to routes advertised to EBGP peer 26.2.2.2.
[ASBR2-bgp-default] peer 26.2.2.2 as-number 100
[ASBR2-bgp-default] address-family ipv4 unicast
[ASBR2-bgp-default-ipv4] peer 26.2.2.2 enable
[ASBR2-bgp-default-ipv4] peer 26.2.2.2 route-policy policy1 export
# Enable the capability to advertise labeled routes to EBGP peer 26.2.2.2 and to receive labeled routes from the peer.
[ASBR2-bgp-default-ipv4] peer 26.2.2.2 label-route-capability
[ASBR2-bgp-default-ipv4] quit
# Advertise BGP EVPN routes to EBGP peer 26.2.2.2.
[ASBR2-bgp-default] address-family l2vpn evpn
[ASBR2-bgp-default-evpn] peer 26.2.2.2 enable
[ASBR2-bgp-default-evpn] quit
[ASBR2-bgp-default] quit
5. Configure PE 2:
# Configure the LSR ID.
<PE2> system-view
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 192.4.4.4 32
[PE2-LoopBack0] quit
[PE2] mpls lsr-id 192.4.4.4
# Enable L2VPN.
[PE2] l2vpn enable
# Enable global LDP.
[PE2] mpls ldp
[PE2-ldp] quit
# Enable LDP on Ten-GigabitEthernet 0/0/7, the interface connected to ASBR 2.
[PE2] interface ten-gigabitethernet 0/0/7
[PE2-Ten-GigabitEthernet0/0/7] ip address 22.2.2.1 24
[PE2-Ten-GigabitEthernet0/0/7] mpls enable
[PE2-Ten-GigabitEthernet0/0/7] mpls ldp enable
[PE2-Ten-GigabitEthernet0/0/7] quit
# Configure OSPF for LDP to create LSPs.
[PE2] ospf
[PE2-ospf-1] area 0
[PE2-ospf-1-area-0.0.0.0] network 192.4.4.4 0.0.0.0
[PE2-ospf-1-area-0.0.0.0] network 22.2.2.0 0.0.0.255
[PE2-ospf-1-area-0.0.0.0] quit
[PE2-ospf-1] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable MPLS encapsulation. Configure an RD and route targets for the EVPN instance.
[PE2] xconnect-group vpna
[PE2-xcg-vpna] evpn encapsulation mpls
[PE2-xcg-vpna-evpn-mpls] route-distinguisher 1:1
[PE2-xcg-vpna-evpn-mpls] vpn-target 2:2 export-extcommunity
[PE2-xcg-vpna-evpn-mpls] vpn-target 1:1 import-extcommunity
[PE2-xcg-vpna-evpn-mpls] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 0/0/6 to it. Create an EVPN PW on the cross-connect.
[PE2-xcg-vpna] connection pw1
[PE2-xcg-vpna-pw1] evpn local-service-id 1 remote-service-id 2
[PE2-xcg-vpna-pw1] ac interface ten-gigabitethernet 0/0/6
[PE2-xcg-vpna-pw1-Ten-GigabitEthernet0/0/6] quit
[PE2-xcg-vpna-pw1] quit
[PE2-xcg-vpna] quit
# Create an IBGP connection to ASBR 2, and enable BGP to advertise BGP EVPN routes and labeled unicast routes to ASBR 2.
[PE2] bgp 200
[PE2-bgp-default] peer 192.3.3.3 as-number 200
[PE2-bgp-default] peer 192.3.3.3 connect-interface LoopBack0
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 192.3.3.3 enable
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] address-family ipv4 unicast
[PE2-bgp-default-ipv4] peer 192.3.3.3 enable
[PE2-bgp-default-ipv4] peer 192.3.3.3 label-route-capability
[PE2-bgp-default-ipv4] quit
[PE1-bgp-default] quit
# Configure BGP to advertise BGP EVPN routes to PE 1 to establish an EVPN PW.
[PE2] bgp 200
[PE2-bgp-default] peer 192.1.1.1 as-number 100
[PE2-bgp-default] peer 192.1.1.1 connect-interface LoopBack0
[PE2-bgp-default] peer 192.1.1.1 ebgp-max-hop 10
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 192.1.1.1 enable
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] quit
6. Configure CE 2.
<CE2> system-view
[CE2] interface ten-gigabitethernet 0/0/6
[CE2-Ten-GigabitEthernet0/0/6] ip address 100.1.1.2 24
[CE2-Ten-GigabitEthernet0/0/6] quit
Verifying the configuration
# Verify that an EVPN PW has been established on PE 1.
[PE1] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass,
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.4.4.4 1 710127/710126 EVPN M 0 Up
# Verify that an EVPN PW has been established on PE 2.
[PE2] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
Xconnect-group Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
192.1.1.1 2 710126/710127 EVPN M 0 Up
# Verify that CE 1 and CE 2 can ping each other. (Details not shown.)