- Table of Contents
-
- 04-Policies
- 01-Security policy
- 02-Security policy redundancy analysis
- 03-Security policy hit analysis
- 04-Security policy optimization
- 05-Attack defense
- 06-Risk analysis
- 07-Blacklist
- 08-Connection limit
- 09-uRPF
- 10-IPCAR
- 11-IP reputation
- 12-Domain reputation
- 13-Application audit
- 14-Bandwidth management
- 15-Server connection detection
- 16-Application proxy
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Security policy | 149.90 KB |
This help contains the following topics:
¡ Security policy filtering criteria
¡ Security policy matching order
¡ Policy matching acceleration
¡ Restrictions and guidelines: Security policies
¡ Restrictions and guidelines: Security policy groups
¡ Restrictions and guidelines: Import and export
¡ Create a security policy group
Introduction
A security policy defines a set of filtering criteria for identifying traffic. The filtering criteria include the following types: source security zone, destination security zone, source IP address and source MAC address, destination IP address, user, application, terminal, service, VRF, and time range. The device matches packets against the security policies and takes the action stated in the policy on the matched packets. Packets that match no security policies are discarded. A policy matches all packets if no criteria are specified for the policy.
Security policy name
You can configure multiple security policies, each of which must be uniquely identified by its name and type.
Security policy filtering criteria
The filtering criteria include the following types: source security zone, destination security zone, source IP address and source MAC address, destination IP address, user, application, terminal, service, VRF, and time range.
A packet is considered matched if it matches all the criterion types in a policy. Each criterion type includes one or more criteria, and a packet matches a criterion type if it matches any criterion of the type.
Security policy matching order
The device matches packets against security policies in the order the policies were created. Follow the depth-first order during policy creation to create policies with stricter match criteria first.
Security policies in the Policies > Security Policies > Security Policies page are displayed in the policy creation order. Policies created first come first in the list. You can move the policies to change the policy matching order.
Policy matching acceleration
This feature accelerates security policy matching to enhance connection establishment and packet forwarding performance, especially for a device using multiple policies to match packets from multiple users.
Matching of security policies switched from object policies is accelerated by default. You need to activate rule matching acceleration if a policy is modified or newly added or if the acceleration feature is deactivated for certain reasons. The following methods are available for activating policy matching acceleration:
· Manual activation—Activates security policy matching acceleration immediately after you click Activate. You can perform manual activation after a policy is modified or the acceleration feature is deactivated.
· Automatic activation—Enables the system to detect security policy changes at specific intervals and activate security policy matching acceleration automatically if any change has been made. If there are 100 or less security policies, the interval is 2 seconds. If there are over 100 security policies, the interval is 20 seconds.
Security policy group
Security policy grouping allows users to enable, disable, delete, and move security policies in the same security policy group in batches. You can specify a security policy group for each security policy or specify a range of security policies for each security policy group.
A security policy takes effect only when both the security policy and its security policy group are enabled.
Import and export
This feature allows the fast migration of security policy configurations. You can export the specific or all security policy settings and perform incremental import.
When importing a file, follow these restrictions and guidelines:
· If a configuration item (a time range for example) in the imported file has the same name as an existing item, the imported item will overwrite the existing one.
· The import process terminates if a policy fails to be imported, but the policies that have been imported are not affected and cannot be rolled back.
· Make sure the file is in CFG format.
Restrictions and guidelines
Restrictions and guidelines: Security policies
· You can move security policies to change their matching order among policies of the same type.
· A newly added security policy is listed below the existing security policies of the same type.
· If a security policy uses an object group that has no objects, the security policy cannot match any packets. For more information, see the online help for object groups.
· If policy matching acceleration fails to be activated by clicking Activate, the matching of policies that have been accelerated is not affected.
· You also need to activate policy matching acceleration if the objects in an object group used by a security policy change.
· The aging time configured for a security policy takes precedence over the aging times configured in Session Aging Time Set.
· When inter-VLAN bridge forwarding is configured, the statistics collection feature collects statistics only about packets discarded by the security policy. Statistics about permitted packets are not collected.
· Only IPv4 security policies support using source MAC addresses as the filtering criteria.
· Before configuring content security for a non-default context, make sure content security settings have been activated for the default context. To activate content security settings for a context, click Submit on the security policy page of the context.
Restrictions and guidelines: Security policy groups
· If you specify a security policy group for a security policy, the policy will be added to the security policy group as its last policy.
· If you remove the first security policy from a security policy group, the policy will be placed before the policy group. If you remove any other security policy from the security policy group, the policy will be placed after the policy group.
· You cannot move a security policy group that does not contain any policies or move a security policy group before or after an empty security policy group.
· You cannot move a security policy group to a place between policies in another security policy group.
· If you move a security policy to a place before or after a security policy group, the policy joins the group automatically.
Restrictions and guidelines: Import and export
· You can export only user-defined applications, terminals, and security zones. Predefined applications, terminals, and security zones cannot be exported.
· The file to be imported can contain only security settings available for export.
· When exporting security zone and VRF settings, their binding relations with interfaces are not exported. You must configure interface binding for imported security zones and VRFs.
· The export operation exports only security policy settings and does not export settings about objects used by the security policy.
· Only one user can perform importing or exporting at a time.
Configure security policies
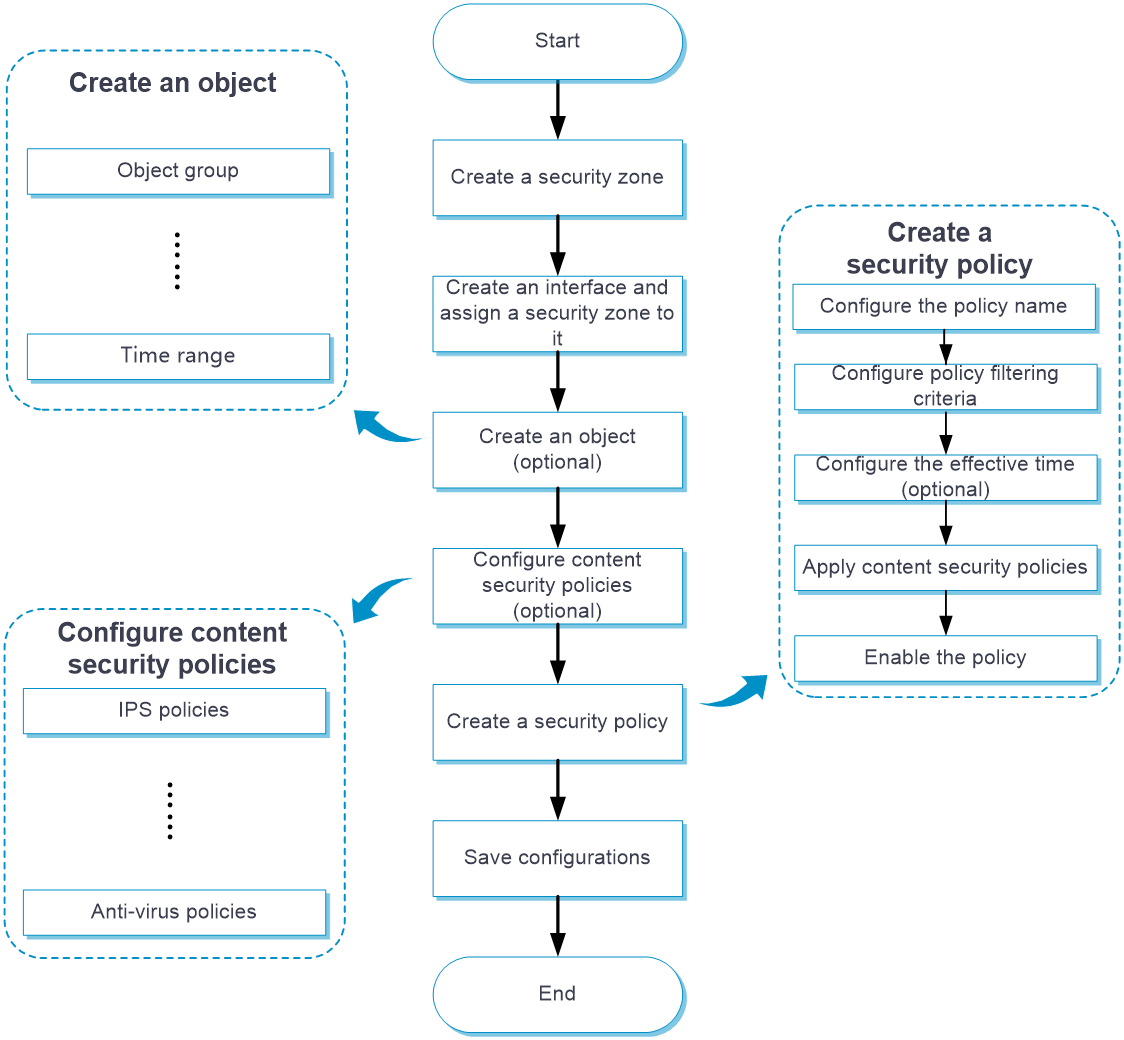
Configure a security policy as shown in Figure 1.
Figure 1 Security policy configuration procedure
Create a security policy
1. Select Policies > Security Policies > Security Policies.
2. Click Create and then select Create a policy.
3. Create a security policy.
Table 1 Security policy configuration items
|
Item |
Description |
|
Name |
Enter a name for the security policy. Security policies of the same type cannot have the same name. |
|
Auto naming |
Select whether to enable the system to automatically name the security policy. With this feature enabled, you can specify only one source security policy and one destination security policy. |
|
Source zone |
|
|
Destination zone |
Specify a destination security zone as a filtering criterion. |
|
Type |
Specify the security policy type. Options include: · IPv4. · IPv6. |
|
Policy group |
Specify a security policy group for the security policy. |
|
Description |
Configure a description for the security policy. |
|
Action |
Specify the security policy action. Options include: · Permit—Allows matched packets to pass. · Deny—Discards matched packets. |
|
Source IP/MAC address |
Specify a source IP/MAC address as a filtering criterion. Only IPv4 security policies support using source MAC addresses for packet filtering. |
|
Destination address |
Specify a destination IP address as a filtering criterion. |
|
Service |
Specify a service as a filtering criterion. |
|
Application |
Specify an application or application group as a filtering criterion. |
|
Terminal |
Specify a terminal or terminal group as a filtering criterion. |
|
User |
Specify a user or user group as a filtering criterion. |
|
Time range |
Specify the time range during which the security policy rule is in effect. |
|
VRF |
Configure the security policy rule to take effect on packets of the specified VRF. |
|
Content security |
Configure Deep Packet Inspection (DPI) services for matched packets. |
|
Logging |
Enable logging for matched packets. |
|
Match counting |
Enable statistics collection for matched packets. |
|
Statistics collection period |
Specify the statistics collection period. Options include Permanent and Custom. |
|
Session aging |
Set the aging time for stable sessions created for packets matching the security policy. If the aging time is not configured, stable sessions use the aging time configured on the System > Session Aging Time Set > Protocol Session Aging Set page. |
|
Persistent session aging |
Set the aging time for persistent sessions created for packets matching the security policy. If the aging time is not configured, stable sessions use the aging time configured on the System > Session Aging Time Set > Protocol Session Aging Set page. |
|
Policy status |
Select whether to enable this policy. |
|
Redundancy analysis |
Select whether to access the Redundancy Analysis page after the policy creation. |
4. Click OK.
5. For the security policy to take effect immediately, click Activate.
Insert a security policy
1. Select Policies > Security Policies > Security Policies.
2. To insert a security policy to the place before or after all existing security policies, click Insert and select First or Last. To insert a security policy to the place before or after a specific policy, select the target policy, click Insert, and then select Before or After.
3. Configure the policy to be inserted and then click OK. For more information, see Table 1.
The inserted policy will be displayed on the Security Policies page.
4. For the security policy to take effect immediately, click Activate.
Create a security policy group
1. Select Policies > Security Policies > Security Policies.
2. Click Create and then select Create a policy group.
3. Create a security policy group.
Table 2 Security policy group configuration items
|
Item |
Description |
|
Name |
Enter a name for the security policy group. |
|
Description |
Configure a description for the security policy group. |
|
Type |
Specify the security policy group type. Options include: · IPv4. · IPv6. |
|
Start policy |
Specify the name of the start policy of a policy range in which all the security policies will be add to the group. |
|
End policy |
Specify the name of the end policy of a policy range in which all the security policies will be added to the group. Make sure the end policy is listed below the start policy and policies in the specified policy range do not belong to any other policy groups. |
4. Click OK.