- Table of Contents
-
- 13-User Access and Authentication Configuration Guide
- 00-Preface
- 01-AAA configuration
- 02-802.1X configuration
- 03-MAC authentication configuration
- 04-Port security configuration
- 05-Portal configuration
- 06-WLAN authentication configuration
- 07-WLAN IP snooping configuration
- 08-802.1X client configuration
- 09-User identification configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 09-User identification configuration | 138.64 KB |
Contents
Configuring user identification
Identity-based user access control
Restrictions: Hardware compatibility with user identification
Restrictions and guidelines: User identification configuration
User identification tasks at a glance
Enabling the user identification feature
Configuring remote servers and an identity user import policy
Configuring an identity user import policy
Configuring a security management server set
Managing identity user accounts
Enabling automatic identity user account import
Manually importing identity user accounts from remote servers
Manually importing identity user accounts from a .csv file
Manually exporting identity user accounts
Deleting identity user accounts
Managing online identity users
Configuring static identity users
Specifying the username match mode for user identification
Importing online identity users from a remote server
Deleting online identity users
Display and maintenance commands for user identification
Configuring user identification
About user identification
The user identification feature works with other security features such as bandwidth management to control users' network access based on the users' IP addresses. This feature provides facilitation for the network administrators to deploy security policies and to collect statistics and analysis for network attack behaviors and traffic flow on a per-user basis. It also enables the network administrators to implement policy control regardless of changes to the user IP addresses.
Identity-based user access control
The following shows the process for identity-based user access control:
1. Identity authentication. A network access user passes identity authentication and comes online.
2. User identification. The device obtains the username and IP address of the online user, and associates the information with the local identity user account and the local identity group. Then, the username-IP mapping for the network access user is created. The administrator can also add static username-IP mappings to permit network access without identity authentication.
3. Identity-based access control. The device identifies the source IP address of the traffic destined for the network, and resolves the IP address to the username and user group based on the mapping. The device performs network access control for the user or user group based on other security feature settings.
Identity user management
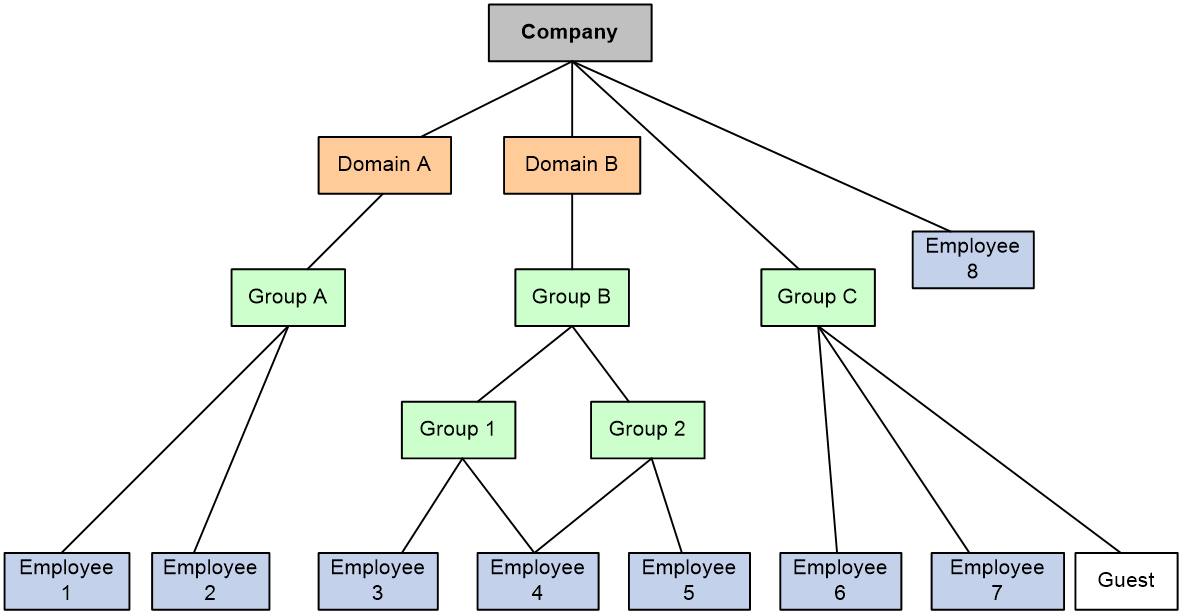
All identity users are organized in a tree structure. Identity user, identity group, and identity domain are management units, and their hierarchy levels are in ascending order.
· An identity user can belong to one or multiple identity groups.
· An identity group can belong to one or multiple higher-layer identity groups.
· An identity user or an identity group can belong to no or one identity domain.
The device uniquely identifies a managed object by the combination of identity domain and username or the combination of identity domain and identity group.
The tree structure facilitates user location and query. As shown in Figure 1, the network administrator creates identity groups and identity users for different departments and employees to implement identity-based network access control.
Figure 1 Identity user management architecture
Identity user accounts
Identity user accounts are used to record identification information of network access users from different sources. The identification information includes the username, user group name, and identity domain name of the users. The user identification module uniformly manages identity users from different sources.
The device supports the following methods to create identity user accounts:
· Learning from the local user database—The user identification module learns network access user information from the local user database and saves the user information as identity user accounts. For more information about network access users, see "Configuring AAA."
· Importing from a .csv file—The network administrator imports user information from a .csv file to the device and the device automatically creates identity user accounts based on the imported information.
· Importing from remote servers—The device initiates user information requests to remote servers, imports network access user information, and then creates identity user accounts based on the imported information. This method enables the network administrator to manage identity user accounts when user information is on the remote servers. Supported remote servers include LDAP servers and H3C IMC RESTful servers.
Online identity users
Online identity users are online network access users (including portal users) that are managed by the user identification module. The device records the username, identity domain name, IP address, and MAC address of online identity users.
Online identity users include dynamic online identity users and static online identity users.
Dynamic online identity users
Dynamic online identity users have the following sources:
· Online network access users that access the network through the device—After a user passes local or remote authentication and comes online, the user identification module searches the user's username and domain name in local identity user accounts. If a matching entry is found, the device creates an online identity user entry for the user.
· Online network access users obtained from remote servers—After the device obtains information about an online user from a remote server, the user identification module searches the user's username and domain name in local identity user accounts. If a matching entry is found, the device creates an online identity user entry for the user. The device can obtain information about all online users of remote servers (including online users on the other devices) for unified management and monitoring.
Supported remote servers include security management servers and H3C IMC RESTful servers.
¡ The device obtains online network access user information pushed by security management servers.
¡ The device actively imports online network access user information from an H3C IMC RESTful server.
Static online identity users
Static online identity users originate from static identity users configured by the network administrator. Each static identity user contains the mapping between the username and the IP addresses of the user. After a static identity user is created, the user identification module searches the user's username and domain name in local identity user accounts. If a matching entry is found, the device creates a static online identity user entry for the static identity user. Static online identity users can access the network without identity authentication but their access to the network is controlled by security features. The network administrator can configure static identity users when only few people need to temporarily access the network.
Application of online identity users
Application modules can impose security policies on online identity users. When online identity user entries are deleted, the user identification module will instruct the application modules to stop processing services for the users.
Identity groups
Identity users can be added to different groups for batch configuration and hierarchical user management. The groups are called identity groups. The user identification module uniformly manages identity groups from different sources.
Creation of identity groups
The device supports the following methods to create identity groups:
· Learning from the local user database—When a local user group is created, the device instructs the user identification module to create an identity group with the same group name. For more information about local user groups, see "Configuring AAA."
· Importing from a .csv file—The device imports identity user account information from a .csv file and then automatically creates identity groups based on the imported information.
· Importing from remote servers—The device can import identity user account information from an H3C IMC RESTful server or LDAP servers and then create identity groups based on the group information in the accounts. The device can also directly obtain user group information from LDAP servers and then creates identity groups.
Application of identity groups
An identity group is activated when it is used by an application module, and all services based on the identity group will take effect. When the application module stops using the identity group, the identity group is inactive.
Restrictions: Hardware compatibility with user identification
|
Hardware series |
Model |
User identification compatibility |
|
WX2500H series |
WX2508H-PWR-LTE WX2510H WX2540H WX2560H |
Yes |
|
WX3000H series |
WX3010H WX3010H-L WX3010H-X WX3024H WX3024H-L |
· WX3010H, WX3010H-X, WX3024H: Yes · WX3010H-L, WX3024H-L: No |
|
WX3500H series |
WX3508H WX3510H WX3520H WX3540H |
Yes |
|
WX5500E series |
WX5510E WX5540E |
Yes |
|
WX5500H series |
WX5540H WX5560H WX5580H |
Yes |
|
Access controller modules |
LSQM1WCMX20 LSQM1WCMX40 LSUM1WCME0 LSUM1WCMX20RT LSUM1WCMX40RT |
Yes |
|
Hardware series |
Model |
User identification compatibility |
|
WX1800H series |
WX1804H WX1810H WX1820H WX1840H |
No |
|
WX3800H series |
WX3820H WX3840H |
No |
|
WX5800H series |
WX5860H |
No |
Restrictions and guidelines: User identification configuration
The user identity feature on the device can interact with the following remote servers to learn user information:
· H3C IMC RESTful server—The device imports identity user accounts, identity groups, and online identity users from the H3C IMC RESTful server.
· LDAP servers—The device imports identity user accounts and identity groups from LDAP servers.
· Security management servers—The device obtains online identity users from security management servers.
To use the H3C IMC RESTful server, make sure the server is installed with the SSM component and runs on IMC PLAT 7.0 (E0201) or its patch version.
User identification is not applicable to portal users that perform MAC-based quick portal authentication. For more information about MAC-based quick portal authentication, see "Configuring portal authentication."
User identification tasks at a glance
To configure user identification, perform the following tasks:
1. Enabling the user identification feature
2. Configuring remote servers and an identity user import policy
Perform this task if the device needs to import user information from RESTful or LDAP servers.
a. Configure remote server parameters
b. Configuring an identity user import policy
3. Configuring a security management server set
Perform this task if the device needs to obtain user information from security management servers.
4. (Optional.) Managing identity user accounts
¡ Enabling automatic identity user account import
¡ Manually importing identity user accounts from remote servers
¡ Manually importing identity user accounts from a .csv file
¡ Manually exporting identity user accounts
¡ Deleting identity user accounts
5. (Optional.) Managing online identity users
¡ Configuring static identity users
¡ Specifying the username match mode for user identification
¡ Importing online identity users from a remote server
¡ Deleting online identity users
6. (Optional.) Deleting identity groups
Enabling the user identification feature
About this task
With the user identification feature, the device learns information about online users (such as portal) from the user access modules. The device uses the obtained information for user identification and works with other security features for identity-based network access control.
Procedure
1. Enter system view.
system-view
2. Enable the user identification feature.
user-identity enable
By default, the user identification feature is disabled.
Configuring remote servers and an identity user import policy
Configuring a RESTful server
About this task
The RESTful server view defines the related parameter settings for the device to communicate with the RESTful server. The parameters include the login account and the URIs of the RESTful server. After establishing a connection with the RESTful server, the device can import identity user accounts, identity groups, and online identity users from the server.
Restrictions and guidelines
The system can have only one RESTful server.
Procedure
1. Enter system view.
system-view
2. Create a RESTful server and enter its view.
user-identity restful-server server-name
3. Specify the username and password to log in to the RESTful server.
login-name user-name password { cipher | simple } string
By default, no username or password is specified for the device to log in to the RESTful server.
The specified username and password must exist on the RESTful server. Otherwise, the device cannot establish a connection with the RESTful server.
4. Specify a URI for the RESTful server.
uri { get-online-user | get-user-database | get-user-group-database | put-offline-user | put-online-user } uri-string
By default, no URIs are specified for the RESTful server.
The specified URIs must be the same as those on the RESTful server. Otherwise, user information interaction will fail.
You can repeat this command to specify multiple URIs of the RESTful server.
5. (Optional.) Configure RESTful server reachability detection:
a. Enable RESTful server reachability detection.
connection-detect enable
By default, RESTful server reachability detection is disabled.
b. Configure parameters for RESTful server reachability detection.
connection-detect { interval interval | maximum max-times }
By default, the reachability detection interval is 5 minutes and the maximum number of probes per detection is 3.
Configuring an LDAP scheme
About this task
An LDAP scheme includes the LDAP server that interacts with the device and the related parameter settings. After establishing a connection with the LDAP server, the device can import identity user accounts and identity groups from the server.
For more information about LDAP attribute maps, see "Configuring AAA."
Restrictions and guidelines
The device cannot import online identity users from the LDAP server.
When importing identity user accounts and identity groups from the LDAP server, the device does not carry parent groups to which the identity users or identity groups belong by default. To configure the device to carry the parent group information, you must configure an LDAP attribute map and specify the LDAP attribute map in the LDAP scheme.
Procedure
1. Enter system view.
system-view
2. Configure an LDAP server.
The LDAP server configuration includes the server IP address, the administrator DN and password for binding with the LDAP server, DN search policy, and user group filter. For more information, see "Configuring AAA."
3. Create an LDAP attribute map and enter LDAP attribute map view.
ldap attribute-map map-name
4. Configure an LDAP attribute mapping entry for the user group attribute.
map ldap-attribute ldap-attribute-name [ prefix prefix-value delimiter delimiter-value ] aaa-attribute user-group
5. Create an LDAP scheme and enter LDAP scheme view.
ldap scheme ldap-scheme-name
6. Specify the LDAP authentication server.
authentication-server server-name
By default, no LDAP authentication server is specified.
7. Specify the LDAP attribute map.
attribute-map map-name
By default, no LDAP attribute map is specified.
After this command is executed, the device imports identity user accounts and identity groups with parent group information. However, the device does not create new identity groups based on the parent group information.
Configuring an identity user import policy
About this task
To import identity user accounts, online identity users, or identity groups from a RESTful server or LDAP servers, you must configure an identity user import policy. In this policy, you can set the parameters for the device to interact with the RESTful server or LDAP servers.
Restrictions and guidelines
The system can have only one identity user import policy. Before you configure a new identity user import policy, you must delete the existing one.
Procedure
1. Enter system view.
system-view
2. Create an identity user import policy and enter its view.
user-identity user-import-policy policy-name
3. Specify a RESTful server.
restful-server server-name
By default, no RESTful server is specified.
You can specify only one RESTful server. Before you specify a new RESTful server, remove the currently specified one.
4. Specify an LDAP scheme.
ldap-scheme ldap-scheme-name
By default, no LDAP schemes are specified.
You can specify a maximum of 16 LDAP schemes.
5. (Optional.) Set the interval for automatic identity user account import.
account-update-interval interval
By default, the interval for automatic identity user account import is 24 hours.
6. Specify the type of user information to be imported from LDAP servers.
import-type { all | group | user }
By default, the device imports both user information and user group information from LDAP servers.
Configuring a security management server set
About this task
The security management server set view defines the related parameters of the device to communicate with security management servers. The parameters include the IP addresses of the servers, the port number for listening to the servers, and the shared key to secure communication between the device and the servers.
When the device establishes connections with security management servers, it can receive user online and offline notifications that the servers push to the device.
· Based on user online notifications, the device obtains online user information and creates online identity user entries for users that match identity user accounts.
· Based on user offline notifications, the device obtains information about users that have gone offline and deletes the corresponding online identity user entries.
Restrictions and guidelines
The system can have only one security management server set.
Procedure
1. Enter system view.
system-view
2. Create a security management server set and enter its view.
user-identity security-manage-server server-set-name
3. Specify IP addresses of security management servers.
ip ip-address&<1-10>
By default, no IP addresses of security management servers are specified.
4. Configure the encryption algorithm and shared key for securing communication with security management servers.
encryption algorithm { 3des | aes128 } key { simple | cipher } string
By default, no encryption algorithm or shared key is configured for securing communication with security management servers.
5. Set the port number for listening to security management servers.
listen-port port-num
By default, the device listens to security management servers on port 8001.
Managing identity user accounts
Enabling automatic identity user account import
About this task
After this feature is enabled, the device first imports all identity user accounts and online identity user information from the servers specified in the identity user import policy. Then, the device periodically imports identity user accounts from the remote servers at the interval set by using the account-update-interval command.
Restrictions and guidelines
If automatic identity user account import is enabled but user identity is disabled, the device can import only identity user accounts from the remote servers specified in the policy.
Procedure
1. Enter system view.
system-view
2. Enable automatic identity user account import.
user-identity user-account auto-import policy policy-name
By default, automatic identity user account import is disabled.
Manually importing identity user accounts from remote servers
About this task
Perform this task to manually import identity user accounts from remote servers. The device initiates user information requests to the servers, imports network access user account information from the servers, and then creates corresponding identity user accounts. If the device fails to import an account, the device skips the account and continues to import the next account.
Prerequisites
Before you import identity user accounts from remote servers, make sure the following conditions are met:
· An identity user import policy is configured.
· The specified URIs of the RESTful server or the IP addresses of the LDAP servers in the policy must be valid.
Procedure
1. Enter system view.
system-view
2. Import identity user accounts from remote servers.
user-identity user-account import policy policy-name
Manually importing identity user accounts from a .csv file
About this task
Perform this task to manually import identity user accounts from a .csv file. If the device fails to import an account, it stops importing the remaining identity user accounts in the file.
Prerequisites
Before you import identity user accounts from a .csv file, make sure the .csv file is a standard .csv file. To see the format of a standard .csv file, use the user-identity user-account export url command to export a standard template.
Procedure
1. Enter system view.
system-view
2. Import identity user accounts from a .csv file.
user-identity user-account import url url-string [ auto-create-group | override | start-line line-number ] *
Manually exporting identity user accounts
About this task
Perform this task to export identity user accounts on the device to a .csv file. You can directly import identity user accounts in the exported file to other devices. Or, you can edit the exported file and then import identity user accounts in the file back to the device or to other devices.
If you specify the template keyword, the device exports a standard .csv file template. You can use this file template as a reference when you edit .csv files.
Procedure
1. Enter system view.
system-view
2. Export identity user accounts to a .csv file.
user-identity user-account export url url-string [ { domain domain-name | null-domain } [ user user-name ] | template ]
Deleting identity user accounts
About this task
Identity user accounts can be deleted by using the following methods:
· Manual deletion—The administrator uses a command to delete identity user accounts imported from remote servers or .csv files.
· Dynamic deletion—Deletion of network access users in the local user database triggers the deletion of corresponding identity user accounts.
Manually deleting identity user accounts
To manually delete identity user accounts, execute the following command in user view:
reset user-identity user-account { all | { domain domain-name | null-domain } [ name user-name ] }
Managing online identity users
Configuring static identity users
Restrictions and guidelines
A username can be bound with multiple IP addresses or with multiple IP-MAC address combinations. However, an IP address or an IP-MAC address combination cannot be bound with multiple usernames.
Procedure
1. Enter system view.
system-view
2. Configure a static identity user.
user-identity static-user user-name [ domain domain-name ] bind { ipv4 ipv4-address | ipv6 ipv6-address } [ mac mac-address ]
Specifying the username match mode for user identification
About this task
Perform this task to specify the username match mode for user identification. The device creates online identity users only for online users whose usernames can match the usernames in the local identity user accounts.
Procedure
1. Enter system view.
system-view
2. Specify the username match mode for user identification.
user-identity online-user-name-match { keep-original | with-domain | without-domain }
By default, the username match mode for user identification is keep-original.
Importing online identity users from a remote server
About this task
Perform this task to import online identity user information from a remote server. The device initiates a realtime online user information request to the server and then imports all online user information.
Restrictions and guidelines
The device can import online identity users only from an H3C IMC RESTful server.
For the device to successfully import online identity users from a remote server, make sure the user identification feature is enabled.
Prerequisites
Before you import online identity users from a remote server, make sure the following conditions are met:
· An identity user import policy is configured.
· The specified URIs of the RESTful server in the policy must be valid.
Procedure
1. Enter system view.
system-view
2. Import online identity users.
user-identity online-user import policy policy-name
Deleting online identity users
About this task
Online identity users can be deleted by using the following methods:
· Manual deletion—The administrator uses a command to delete dynamic online identity users imported from remote servers and static online identity users.
· Dynamic deletion—Multiple events trigger the deletion of identity users.
¡ After a network access user goes offline, the access module instructs the user identification module to delete the associated online identity users.
¡ After the device reboots, all dynamic online identity users are deleted.
¡ After the user identification feature is disabled, all dynamic online identity users are deleted.
¡ After a user on a remote server goes offline, the remote server instructs the device to delete the associated online identity user.
Manually deleting dynamic online identity users
To manually delete dynamic online identity users, execute the following command in user view:
reset user-identity dynamic-online-user { all | { domain domain-name | null-domain } [ name user-name ] | { ip ipv4-address | ipv6 ipv6-address } [ mac mac-address ] }
Manually deleting static online identity users
1. Enter system view.
system-view
2. Delete static online identity users.
undo user-identity static-user [ domain domain-name ] [ bind { ipv4 ipv4-address | ipv6 ipv6-address } [ mac mac-address ] ]
Deleting identity groups
About this task
Identity groups can be deleted by using the following methods:
· Manual deletion—The administrator uses a command to delete identity groups imported from remote servers or .csv files.
· Dynamic deletion—Deletion of user groups in the local user database triggers the deletion of corresponding identity groups.
Manually deleting identity groups
To manually delete identity groups, execute the following command in user view:
reset user-identity user-group { all | { domain domain-name | null-domain } [ name group-name ] }
Display and maintenance commands for user identification
Execute display commands in any view.
|
Task |
Command |
|
Display information about identity users or identity groups. |
display user-identity { domain domain-name | null-domain } { user [ user-name [ group ] ] | user-group [ group-name [ member { group | user } ] ] } |
|
Display information about active identity groups. |
display user-identity active-user-group { all | domain domain-name | null-domain } |
|
Display information about all identity users or identity groups. |
display user-identity all { user | user-group } |
|
Display information about online identity users. |
display user-identity online-user { domain domain-name | null-domain } name user-name |
|
Display RESTful server configuration. |
display user-identity restful-server [ server-name ] |
|
Display configuration information for security management server sets. |
display user-identity security-manage-server [ server-set-name ] |
|
Display identity user import policy information. |
display user-identity user-import-policy [ policy-name ] |