- Table of Contents
-
- 03-Security Configuration Guide
- 00-Preface
- 01-Security zone configuration
- 02-Security policy configuration
- 03-ASPF configuration
- 04-Session management
- 05-Object group configuration
- 06-Object policy configuration
- 07-IP source guard configuration
- 08-AAA configuration
- 09-User identification configuration
- 10-Password control configuration
- 11-Portal configuration
- 12-MAC authentication configuration
- 13-IPoE configuration
- 14-Public key management
- 15-PKI configuration
- 16-SSH configuration
- 17-SSL configuration
- 18-Connection limit configuration
- 19-Attack detection and prevention configuration
- 20-Server connection detection configuration
- 21-ARP attack protection configuration
- 22-ND attack defense configuration
- 23-uRPF configuration
- 24-IP-MAC binding configuration
- 25-IP reputation configuration
- 26-APR configuration
- 27-Keychain configuration
- 28-Crypto engine configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 25-IP reputation configuration | 84.64 KB |
Contents
Restrictions: Licensing requirements for IP reputation
IP reputation tasks at a glance
Enabling IP reputation globally
Specifying actions for an attack category
Specifying an exception IP address
Enabling the top hit ranking feature
Display and maintenance commands for IP reputation
IP reputation configuration examples
Example: Configuring IP reputation
Configuring IP reputation
About IP reputation
The IP reputation feature uses IP addresses on the IP reputation list to filter network traffic. The list contains IP addresses with poor reputation, which are vulnerable to DDoS attacks, command injection attacks, Trojan virus download attacks, and port scan attacks. Each IP address entry on the reputation list contains the attributes of the attack category, match field, and actions for matching packets..
IP reputation workflow
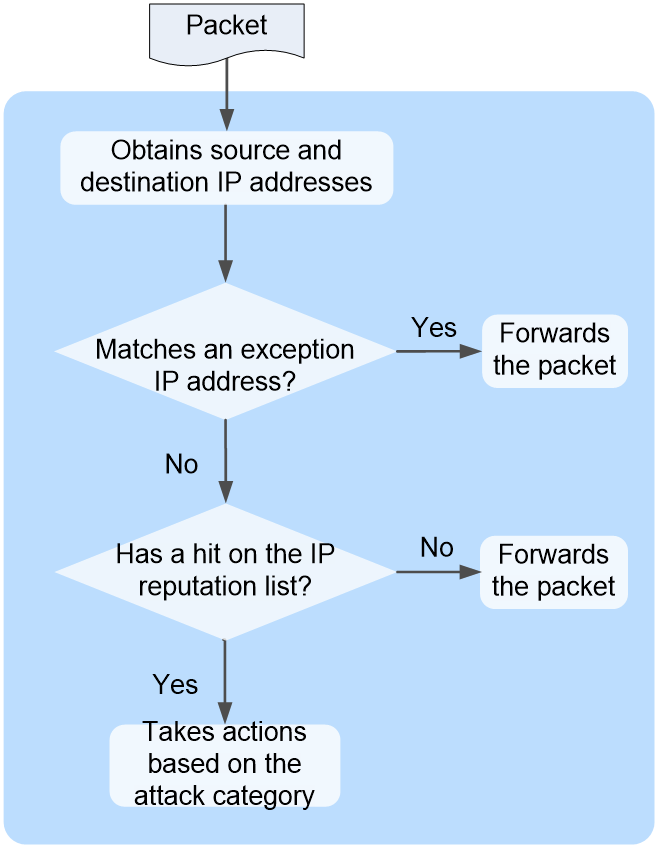
Figure 1 describes the IP reputation workflow.
Figure 1 IP reputation workflow
After receiving a packet, the device performs the following operations:
1. Determines whether the source or destination IP address of the packet matches an exception IP address.
¡ If a match is found, the device forwards the packet.
¡ If no match exists, the device proceeds to the next step.
2. Determines whether the packet matches an IP address on the IP reputation list.
Whether an IP address on the list is compared to the source or destination IP address in the packet depends on the match field attribute of the IP address entry. If the match field attribute is bidirectional, the reputation IP address is compared with both the source and destination IP addresses in the packet. A match is found when this reputation IP address is the same as either the source or destination IP address in the packet.
¡ If a match is found, the device takes actions for the attack category of the IP address. The device supports the following actions:
- Permit—Allows packets to pass through.
- Drop—Drops packets.
- Logging—Generates IP reputation logs for the matching IP address.
¡ If no match is found, the device forwards the packet.
Restrictions: Licensing requirements for IP reputation
To use the IP reputation feature, you must purchase a license for the feature and install it on the device. If the license expires, the IP reputation feature can operate normally for a grace period of seven days with the existing IP reputation list on the device. After seven days, the existing IP reputation list will be cleared if still no valid license is installed, and the IP reputation feature becomes unavailable. For more information about licenses, see license management in Fundamentals Configuration Guide.
IP reputation tasks at a glance
To configure IP reputation, perform the following tasks:
1. Enabling IP reputation globally
2. Specifying actions for an attack category
3. (Optional.) Specifying an exception IP address
4. (Optional.) Enabling the top hit ranking feature
Enabling IP reputation globally
About this task
This feature identifies packets based on the source or destination IP address on the reputation list and processes the matching packets based on the attack category of the IP address.
Procedure
1. Enter system view.
system-view
2. Enter IP reputation view.
ip-reputation
3. Enable IP reputation globally.
global enable
By default, IP reputation is disabled globally.
Specifying actions for an attack category
About this task
On the IP reputation list, an IP address can belong to multiple attack categories. Each attack category has its own actions.
If an IP address belongs to only one attack category, the device takes the actions in this attack category. If an IP address belongs to multiple attack categories, the device takes an action that has higher priority among all actions in those attack categories. The drop action has higher priority than the permit action.
If logging is enabled for one of attack categories to which an IP address belongs, the device generates a log when the IP address is matched.
The device supports fast output of IP reputation logs. For more information about fast log output, see fast log output configuration in Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter IP reputation view.
ip-reputation
3. Specify actions for an attack category.
attack-category attack-id { action { deny | permit } | logging { disable | enable } } *
By default, no actions are configured for an attack category and each attack category has its own pre-defined actions.
Specifying an exception IP address
About this task
The device forwards a packet if the source or destination IP address of the packet is an exception IP address.
Procedure
1. Enter system view.
system-view
2. Enter IP reputation view.
ip-reputation
3. Specify an exception IP address.
exception ipv4 ipv4-address
By default, no exception IP address is specified.
Enabling the top hit ranking feature
About this task
This feature enables the device to collect hit statistics for IP addresses on the IP reputation list and rank them. After you disable this feature, the device clears hit statistics for IP reputation.
Procedure
1. Enter system view.
system-view
2. Enter IP reputation view.
ip-reputation
3. Enabling the top hit ranking feature.
top-hit-statistics enable
By default, the top hit ranking feature is disabled.
Display and maintenance commands for IP reputation
Execute display commands in any view.
|
Task |
Command |
|
Display information about attack categories for IP reputation. |
display ip-reputation attack-category |
|
Display exception IP addresses. |
display ip-reputation exception |
|
Display statistics for IP addresses with the highest hits on the IP reputation list. |
display ip-reputation top-hit-statistics [ top-number ] [chassis chassis-number slot slot-number ] |
|
Display IP reputation information about an IP address. |
display ip-reputation ipv4 ipv4-address |
IP reputation configuration examples
Example: Configuring IP reputation
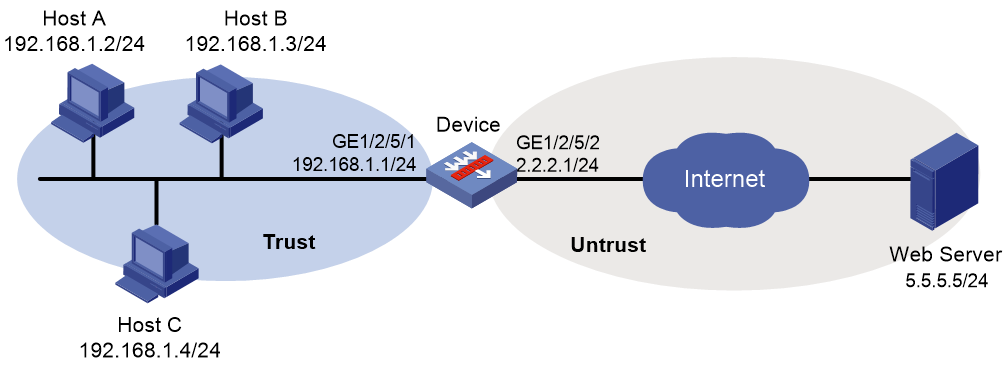
Network configuration
As shown in Figure 2, the device connects to the LAN and Internet through security zones Trust and Untrust, respectively. Configure IP reputation on the device to filter incoming and outgoing traffic on the device.
Procedure
1. Assign IP addresses to interfaces and configure routes, security zones, zone pairs, and interzone policies. Make sure the network connections are available. (Details not shown.)
2. Enable IP reputation globally.
<Device> system-view
[Device] ip-reputation
[Device-ip-reputation] global enable
3. Enable the top hit ranking feature.
[Device-ip-reputation] top-hit-statistics enable
4. Specify 192.168.1.1 as an exception IP address.
[Device-ip-reputation] exception ipv4 192.168.1.1
5. Specify actions deny and logging for attack category 1.
[Device-ip-reputation] attack-category 1 action deny logging enable
Verifying the configuration
Verify that the device permits packets from 192.168.1.1 to pass through and drops packets that match attack category 1 and generates logs for IP addresses that are matched.