- Table of Contents
-
- 13-Layer 3—IP Routing Configuration Guide
- 00-Preface
- 01-Basic IP routing configuration
- 02-Static routing configuration
- 03-RIP configuration
- 04-OSPF configuration
- 05-IS-IS configuration
- 06-BGP configuration
- 07-Policy-based routing configuration
- 08-IPv6 static routing configuration
- 09-IPv6 policy-based routing configuration
- 10-RIPng configuration
- 11-OSPFv3 configuration
- 12-Routing policy configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 02-Static routing configuration | 107.96 KB |
Configuring a static route group
Configuring BFD for static routes
Configuring bidirectional control mode
Configuring single-hop echo mode
Restrictions and guidelines for static route FRR
Configuring static route FRR by specifying a backup next hop
Configuring static route FRR to automatically select a backup next hop
Enabling BFD echo packet mode for static route FRR
Display and maintenance commands for static routing
Configuring static routing
About static routes
Static routes are manually configured. If a network's topology is simple, you only need to configure static routes for the network to work correctly.
Static routes cannot adapt to network topology changes. If a fault or a topological change occurs in the network, the network administrator must modify the static routes manually.
Configuring a static route
1. Enter system view.
system-view
2. Configure a static route.
Public network:
ip route-static dest-address { mask-length | mask } { interface-type interface-number [ next-hop-address ] | next-hop-address | vpn-instance d-vpn-instance-name next-hop-address } [ permanent | track track-entry-number ] [ preference preference ] [ tag tag-value ] [ description text ]
By default, no static route is configured.
You can associate Track with a static route to monitor the reachability of the next hops. For more information about Track, see High Availability Configuration Guide.
VPN:
ip route-static vpn-instance s-vpn-instance-name dest-address { mask-length | mask } { interface-type interface-number [ next-hop-address ] | next-hop-address [ public ] | vpn-instance d-vpn-instance-name next-hop-address } [ permanent | track track-entry-number ] [ preference preference ] [ tag tag-value ] [ description text ]
By default, no static route is configured.
You can associate Track with a static route to monitor the reachability of the next hops. For more information about Track, see High Availability Configuration Guide.
3. (Optional.) Configure the default preference for static routes.
ip route-static default-preference default-preference
The default setting is 60.
Configuring a static route group
About this task
This task allows you to batch create static routes with different prefixes but the same output interface and next hop.
You can create a static route group, and specify the static group in the ip route-static command. All prefixes in the static route group will be assigned the next hop and output interface specified in the ip route-static command.
Procedure
1. Enter system view.
system-view
2. Create a static route group and enter its view.
ip route-static-group group-name
By default, no static route group is configured.
3. Add a static route prefix to the static route group.
prefix dest-address { mask-length | mask }
By default, no static route prefix is added to the static route group.
4. Return to system view.
quit
5. Configure a static route.
Public network:
ip route-static group group-name { interface-type interface-number [ next-hop-address ] | next-hop-address | vpn-instance d-vpn-instance-name next-hop-address } [ permanent | track track-entry-number ] [ preference preference ] [ tag tag-value ] [ description text ]
VPN:
ip route-static vpn-instance s-vpn-instance-name group group-name { interface-type interface-number [ next-hop-address ] | next-hop-address [ public ] | vpn-instance d-vpn-instance-name next-hop-address } [ permanent | track track-entry-number ] [ preference preference ] [ tag tag-value ] [ description text ]
By default, no static route is configured.
Deleting static routes
About this task
To delete a static route, use the undo ip route-static command. To delete all static routes including the default route, use the delete static-routes all command.
Procedure
1. Enter system view.
system-view
2. Delete all static routes.
Public network:
delete static-routes all
VPN:
delete vpn-instance vpn-instance-name static-routes all
Configuring BFD for static routes
|
IMPORTANT: Enabling BFD for a flapping route could worsen the situation. |
About BFD
BFD provides a general-purpose, standard, medium-, and protocol-independent fast failure detection mechanism. It can uniformly and quickly detect the failures of the bidirectional forwarding paths between two routers for protocols, such as routing protocols.
For more information about BFD, see High Availability Configuration Guide.
Configuring bidirectional control mode
About this task
To use BFD bidirectional control detection between two devices, enable BFD control mode for each device's static route destined to the peer.
To configure a static route and enable BFD control mode, use one of the following methods:
· Specify an output interface and a direct next hop.
· Specify an indirect next hop and a specific BFD packet source address for the static route.
Configuring BFD control mode for a static route (direct next hop)
1. Enter system view.
system-view
2. Configure BFD control mode for a static route.
Public network:
ip route-static dest-address { mask-length | mask } interface-type interface-number next-hop-address bfd control-packet [ preference preference ] [ tag tag-value ] [ description text ]
VPN:
ip route-static vpn-instance s-vpn-instance-name dest-address { mask-length | mask } interface-type interface-number next-hop-address bfd control-packet [ preference preference ] [ tag tag-value ] [ description text ]
By default, BFD control mode for a static route is not configured.
Configuring BFD control mode for a static route (indirect next hop)
1. Enter system view.
system-view
2. Configure BFD control mode for a static route.
Public network:
ip route-static dest-address { mask-length | mask } { next-hop-address bfd control-packet bfd-source ip-address | vpn-instance d-vpn-instance-name next-hop-address bfd control-packet bfd-source ip-address } [ preference preference ] [ tag tag-value ] [ description text ]
VPN:
ip route-static vpn-instance s-vpn-instance-name dest-address { mask-length | mask } { next-hop-address bfd control-packet bfd-source ip-address | vpn-instance d-vpn-instance-name next-hop-address bfd control-packet bfd-source ip-address } [ preference preference ] [ tag tag-value ] [ description text ]
By default, BFD control mode for a static route is not configured.
Configuring single-hop echo mode
About this task
With BFD echo mode enabled for a static route, the output interface sends BFD echo packets to the destination device, which loops the packets back to test the link reachability.
|
IMPORTANT: Do not use BFD for a static route with the output interface in spoofing state. |
Procedure
1. Enter system view.
system-view
2. Configure the source address of echo packets.
bfd echo-source-ip ip-address
By default, the source address of echo packets is not configured.
For more information about this command, see High Availability Command Reference.
3. Configure BFD echo mode for a static route.
Public network:
ip route-static dest-address { mask-length | mask } interface-type interface-number next-hop-address bfd echo-packet [ preference preference ] [ tag tag-value ] [ description text ]
VPN:
ip route-static vpn-instance s-vpn-instance-name dest-address { mask-length | mask } interface-type interface-number next-hop-address bfd echo-packet [ preference preference ] [ tag tag-value ] [ description text ]
Configuring static route FRR
About static route FRR
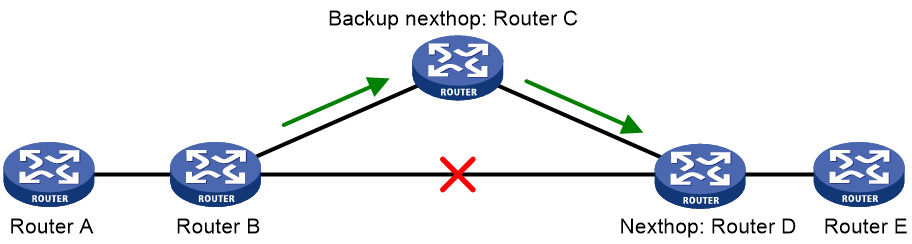
A link or router failure on a path can cause packet loss. Static route fast reroute (FRR) enables fast rerouting to minimize the impact of link or node failures.
As shown in Figure 1, upon a link failure, packets are directed to the backup next hop to avoid traffic interruption. You can either specify a backup next hop for FRR or enable FRR to automatically select a backup next hop (which must be configured in advance).
Restrictions and guidelines for static route FRR
Do not use static route FRR and BFD (for a static route) at the same time.
Equal-cost routes do not support static route FRR.
Besides the configured static route for FRR, the device must have another route to reach the destination. When the state of the primary link (with Layer 3 interfaces staying up) changes from bidirectional to unidirectional or down, static route FRR quickly redirects traffic to the backup next hop. When the Layer 3 interfaces of the primary link are down, static route FRR temporarily redirects traffic to the backup next hop. In addition, the device searches for another route to reach the destination and redirects traffic to the new path if a route is found. If no route is found, traffic interruption occurs.
Configuring static route FRR by specifying a backup next hop
Restrictions and guidelines
A static route does not take effect when the backup output interface is unavailable.
To change the backup output interface or next hop, you must first remove the current setting. The backup output interface and next hop must be different from the primary output interface and next hop.
Procedure
1. Enter system view.
system-view
2. Configure static route FRR.
Public network:
ip route-static dest-address { mask-length | mask } interface-type interface-number [ next-hop-address [ backup-interface interface-type interface-number [ backup-nexthop backup-nexthop-address ] ] ] [ permanent ] [ preference preference ] [ tag tag-value ] [ description text ]
VPN:
ip route-static vpn-instance s-vpn-instance-name dest-address { mask-length | mask } interface-type interface-number [ next-hop-address [ backup-interface interface-type interface-number [ backup-nexthop backup-nexthop-address ] ] ] [ permanent ] [ preference preference ] [ tag tag-value ] [ description text ]
By default, static route FRR is disabled.
Configuring static route FRR to automatically select a backup next hop
1. Enter system view.
system-view
2. Configure static route FRR to automatically select a backup next hop.
ip route-static fast-reroute auto
By default, static route FRR is disabled from automatically selecting a backup next hop.
Enabling BFD echo packet mode for static route FRR
About this task
By default, static route FRR uses ARP to detect primary link failures. Perform this task to enable static route FRR to use BFD echo packet mode for fast failure detection on the primary link.
Procedure
1. Enter system view.
system-view
2. Configure the source IP address of BFD echo packets.
bfd echo-source-ip ip-address
By default, the source IP address of BFD echo packets is not configured.
The source IP address cannot be on the same network segment as any local interface's IP address.
For more information about this command, see High Availability Command Reference.
3. Enable BFD echo packet mode for static route FRR.
ip route-static primary-path-detect bfd echo
By default, BFD echo mode for static route FRR is disabled.
Display and maintenance commands for static routing
Execute display commands in any view.
|
Task |
Command |
|
Display static route information. |
display ip routing-table protocol static [ inactive | verbose ] |
|
Display static route next hop information. |
display route-static nib [ nib-id ] [ verbose ] |
|
Display static routing table information. |
display route-static routing-table [ vpn-instance vpn-instance-name ] [ ip-address { mask-length | mask } ] |
For more information about the display ip routing-table protocol static [ inactive | verbose ] command, see basic IP routing in Layer 3—IP Routing Command Reference.
Configuring a default route
A default route is used to forward packets that do not match any specific routing entry in the routing table. Without a default route, packets that do not match any routing entries are discarded and an ICMP destination-unreachable packet is sent to the source.
A default route can be configured in either of the following ways:
· The network administrator can configure a default route with both destination and mask being 0.0.0.0. For more information, see "Configuring static routing."
· Some dynamic routing protocols (such as OSPF, IS-IS, and RIP) can generate a default route. For example, an upstream router running OSPF can generate a default route and advertise it to other routers. These routers install the default route with the next hop being the upstream router. For more information, see the respective chapters on these routing protocols in this configuration guide.