- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 02-Application audit and management configuration | 124.05 KB |
Contents
Configuring application audit and management
About application audit and management
Application audit and management policy
Application audit and management workflow
Restrictions and guidelines: Application audit and management configuration
Prerequisites for application audit and management
Application audit and management tasks at a glance
Creating an application audit and management policy
Configuring match criteria for the policy
Specifying a time range for the policy
Configuring an audit rule for the policy
Managing and maintaining an application audit and management policy
Copying an application audit and management policy
Renaming an application audit and management policy
Moving an application audit and management policy
Disabling an application audit and management policy
Activating policy and rule settings of all DPI service modules
Application audit and management configuration examples
Example: Configuring account login audit
Example: Configuring sensitive information audit
Configuring application audit and management
About application audit and management
Application audit and management audits and records Internet access behaviors of users by identifying behaviors (for example, login and message sending in IM applications) and behavior objects (for example, account information for IM login).
|
|
NOTE: This feature parses personal information from user packets and must be used for legitimate purposes. |
Application audit and management policy
You can configure match criteria, audit rules, and actions in an application audit and management policy to audit matching packets.
Policy types
Application audit and management policies have the following types:
· Audit policy—Audits packets that meet match criteria in the policy.
· Audit-free policy—Does not audit packets that meet match criteria in the policy.
· Deny policy—Drops packets that meet match criteria in the policy.
Match criteria
Multiple match criteria can be configured in an application audit and management policy.
The following match criteria are available:
· Source and destination security zones.
· Source and destination IP addresses.
· Services.
· Users/user groups.
· Applications.
One match criterion can contain multiple match values. For example, you can configure multiple source security zones for a source security zone match criterion.
Audit rule
Audit rules can be configured for an audit policy to perform more granular control on user behaviors and to generate audit logs.
The following rule match modes are available:
· in-order—The device compares packets with audit rules in ascending order of rule ID. When a packet matches a rule, the device stops the match process and performs the action defined in the rule.
· all—The device compares packets with audit rules in ascending order of rule ID.
¡ If a packet matches a rule with the permit action, all subsequent rules continue to be matched.
The device takes the action with higher priority on matching packets. The deny action has higher priority than the permit action.
¡ If a packet matches a rule with the deny action, the device stops the match process and performs the deny action.
Audit log
The device can generate and output audit logs for packets that match an audit rule. The audit logs can be output as common logs or output by using the fast log output feature.
Application audit and management workflow
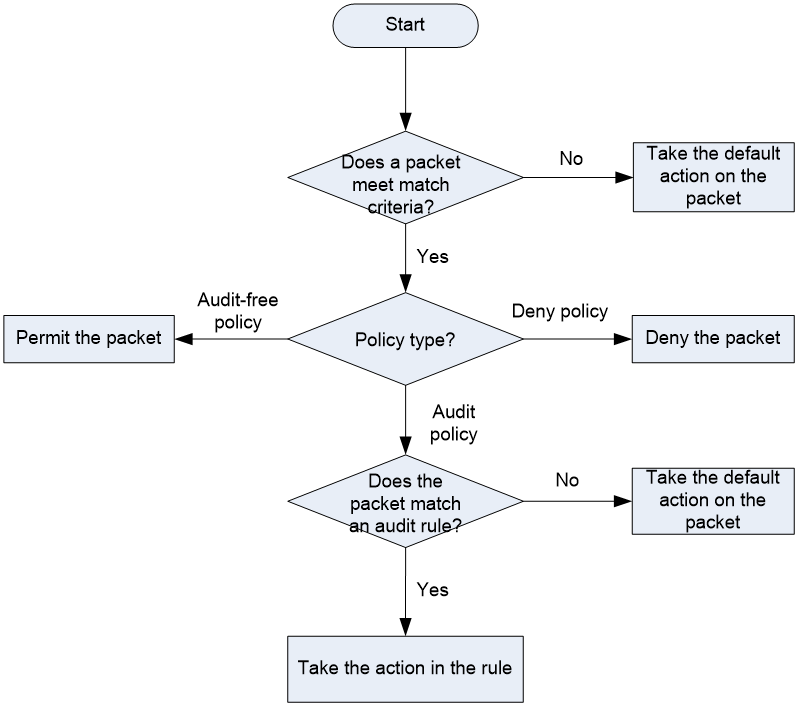
Figure 1 shows the application audit and management workflow.
Figure 1 Application audit and management workflow
The application audit and management workflow is as follows:
1. The device matches the packet against the match criteria in an application audit and management policy.
The packet meets a match criterion if it matches any of its match values. A packet does not match a match criterion if it matches none of its match values.
2. If the packet meets all match criteria in the policy (for the user and user group criteria, only one criterion needs to be matched), the packet matches the policy. Otherwise, the packet does not match the policy and continues to be matched by the next policy. If the packet does not match any policy, the device takes the policy's default action on the packet.
3. If the packet matches a policy, it is processed according to the policy type.
¡ If the policy is an audit-free policy, the packet is allowed to pass.
¡ If the policy is a deny policy, the packet is denied.
¡ If the policy is an audit policy, the packet is matched against the audit rules in the policy.
4. If the packet matches an audit rule, the device takes the action in the audit rule on the packet. If the packet does not match any audit rule, the device takes the audit rule's default action on the packet.
Restrictions and guidelines: Application audit and management configuration
As a best practice to audit packets more accurately, observe the depth-first principle when creating policies. Always create a policy with a smaller audit scope before a policy with a larger audit scope.
Prerequisites for application audit and management
Before configuring application audit and management, complete the following tasks:
· Update the APR signature library to the latest version (see APR configuration in Security Configuration Guide).
· Configure time ranges (see time range configuration in ACL and QoS Configuration Guide).
· Configure IP address object groups and service object groups (see object group configuration in Security Configuration Guide).
· Configure applications (see APR configuration in Security Configuration Guide).
· Configure users and user groups (see user identification configuration in Security Configuration Guide).
· Configure security zones (see security zone configuration in Security Configuration Guide).
Application audit and management tasks at a glance
To configure application audit and management, perform the following tasks:
5. Creating an application audit and management policy
6. Configuring match criteria for the policy
7. (Optional.) Specifying a time range for the policy
8. Configuring an audit rule for the policy
9. Configuring a keyword group
10. (Optional.) Managing and maintaining an application audit and management policy
11. Activating policy and rule settings of all DPI service modules
Creating an application audit and management policy
12. Enter system view.
system-view
13. Enter application audit and management view.
uapp-control
14. Create an application audit and management policy and enter its view.
policy name policy-name { audit | deny | noaudit }
15. Configure the default action for the policy.
policy default-action { deny | permit }
By default, the default action for a policy is permit.
Configuring match criteria for the policy
16. Enter system view.
system-view
17. Enter application audit and management view.
uapp-control
18. Enter application audit and management policy view.
policy name policy-name [ audit | deny | noaudit ]
19. Configure a security zone as a match criterion.
¡ Configure a source security zone as a match criterion.
source-zone source-zone-name
¡ Configure a destination security zone as a match criterion.
destination-zone destination-zone-name
By default, no security zone is used as a match criterion.
20. Configure an IP address object group as a match criterion.
¡ Configure a source IP address object group as a match criterion.
source-address { ipv4 | ipv6 } object-group-name
¡ Configure a destination IP address object group as a match criterion.
destination-address { ipv4 | ipv6 } object-group-name
By default, no IP address object group is used as a match criterion.
21. Configure a service object group as a match criterion.
service service-name
By default, no service object group is used as a match criterion.
22. Configure a user or user group as a match criterion.
¡ Configure a user as a match criterion.
user user-name [ domain domain-name ]
¡ Configure a user group as a match criterion.
user-group user-group-name [ domain domain-name ]
By default, no user or user group is used as a match criterion.
23. Configure an application or application group as a match criterion.
application { app application-name | app-group application-group-name }
By default, no application or application group is used as a match criterion.
The application and application group match criteria can be configured only in audit-free policies and deny policies.
Specifying a time range for the policy
24. Enter system view.
system-view
25. Enter application audit and management view.
uapp-control
26. Enter application audit and management policy view.
policy name policy-name { audit | deny | noaudit }
27. Specify a time range during which the policy is in effect.
time-range time-range-name
By default, an application audit and management policy is in effect at any time.
Configuring an audit rule for the policy
Restrictions and guidelines
You can configure audit rules only for an audit policy.
If you specify the audit-logging keyword for an audit rule, the following rules apply:
· The device sends audit log messages to the information center as common logs by default. With the information center, you can set log message filtering and output rules, including output destinations. The information center can output audit logs to any destinations except the console and the monitor terminal. If you configure the console or monitor terminal as an output destination, the output destination setting will not take effect. To view audit logs stored on the device, use the display logbuffer command. Make sure you do not disable log output to the log buffer, which is enabled by default. For more information about configuring the information center, see Network Management and Monitoring Configuration Guide.
· If you also configure the customlog format dpi audit command, the device outputs audit logs by using the fast log output feature. For more information about fast log output, see fast log output configuration in Network Management and Monitoring Configuration Guide.
For WeChat and QQ, you can only block the entire application and cannot block them by behavior or content.
Procedure
1. Enter system view.
system-view
2. Enter application audit and management view.
uapp-control
3. Enter application audit and management policy view of the audit type.
policy name policy-name [ audit ]
4. Configure an audit rule for the policy.
rule rule-id { app app-name | app-category app-category-name | any } behavior { behavior-name | any } bhcontent { bhcontent-name | any } { keyword { equal | exclude | include | unequal } { keyword-group-name | any } | integer { equal | greater | greater-equal | less | less-equal | unequal } { number } } action { deny | permit } [ audit-logging ]
By default, a policy does not have audit rules.
5. Configure the match mode for audit rules in the policy.
rule match-method { all | in-order }
By default, the match mode for audit rules is in-order.
6. Configure the default action for audit rules in the policy.
rule default-action { deny | permit }
By default, the default action for audit rules is permit.
Configuring a keyword group
About this task
A keyword group can be used by an audit rule to match more specific information.
Procedure
1. Enter system view.
system-view
2. Enter application audit and management view.
uapp-control
3. Create a keyword group and enter its view.
keyword-group name keyword-group-name
4. (Optional.) Configure a description for the keyword group.
description text
By default, a keyword group does not have a description.
5. Add a keyword to the keyword group.
keyword keyword-value
By default, a keyword group does not contain keywords.
Managing and maintaining an application audit and management policy
Copying an application audit and management policy
1. Enter system view.
system-view
2. Enter application audit and management view.
uapp-control
3. Copy an application audit and management policy.
policy copy policy-name new-policy-name
Renaming an application audit and management policy
1. Enter system view.
system-view
2. Enter application audit and management view.
uapp-control
3. Rename an application audit and management policy.
policy rename old-policy-name new-policy-name
Moving an application audit and management policy
1. Enter system view.
system-view
2. Enter application audit and management view.
uapp-control
3. Move an application audit and management policy.
policy move policy-name1 { after | before } policy-name2
Disabling an application audit and management policy
1. Enter system view.
system-view
2. Enter application audit and management view.
uapp-control
3. Enter application audit and management policy view.
policy name policy-name
4. Disable the application audit and management policy.
disable
By default, an application audit and management policy is enabled.
Activating policy and rule settings of all DPI service modules
About this task
After a policy or rule of a DPI service module is created, modified, or deleted, you must perform this task for the configuration to take effect.
For more information about this task, see DPI engine configuration in DPI Configuration Guide.
Restrictions and guidelines
This task will interrupt DPI service processing. To reduce the impact on DPI services, perform this task after you complete policy and rule settings of all DPI service modules.
Procedure
1. Enter system view.
system-view
2. Activate policy and rule settings of all DPI service modules.
inspect activate
By default, policy and rule settings of all DPI service modules are deactivated.
Application audit and management configuration examples
Example: Configuring account login audit
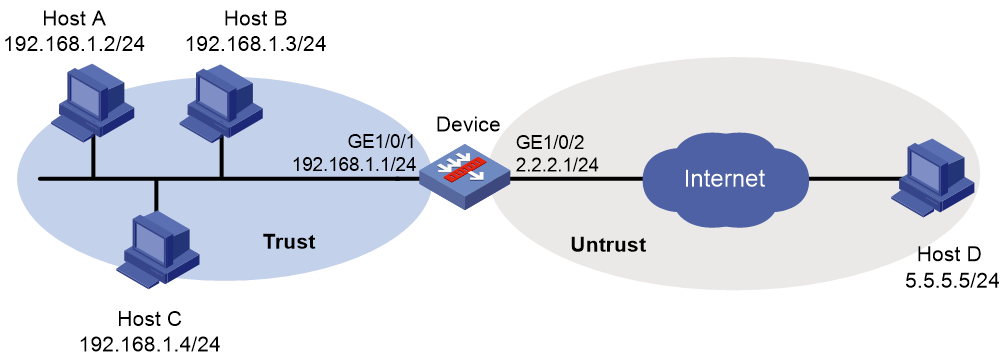
Network configuration
As shown in Figure 2, all departments of a company access the Internet through the device. The working hours of the company are 8:00:00 through 18:00:00 from Monday to Friday.
Configure an application audit and management policy on the device to meet the following requirements:
· Permit login from all QQ accounts during working hours.
· Generate audit logs.
Procedure
1. Assign IP addresses to interfaces and configure routes, security zones, zone pairs, and interzone policies. Make sure the network connections are available. (Details not shown.)
2. Configure a time range named work to cover 8:00:00 through 18:00:00 from Monday to Friday.
<Device> system-view
[Device] time-range work 08:00 to 18:00 working-day
3. Configure an application audit and management policy:
# Enter application audit and management view.
[Device] uapp-control
# Create an audit policy named audit-qq and enter its view.
[Device-uapp-control] policy name audit-qq audit
# Configure source security zone Trust as a match criterion for audit policy audit-qq.
[Device-uapp-control-policy-audit-qq] source-zone trust
# Configure destination security zone Untrust as a match criterion for audit policy audit-qq.
[Device-uapp-control-policy-audit-qq] destination-zone untrust
# Specify time range work for audit policy audit-qq.
[Device-uapp-control-policy-audit-qq] time-range work
# Configure an audit rule to permit login from all QQ accounts and generate audit logs.
[Device-uapp-control-policy-audit-qq] rule 1 app QQ behavior Login bhcontent any keyword equal any action permit audit-logging
[Device-uapp-control-policy-audit-qq] quit
[Device-uapp-control] quit
# Activate the configuration.
[Device] inspect activate
Verifying the configuration
When QQ accounts attempt to access the Internet, the device permits the login requests and generates audit log messages.
Example: Configuring sensitive information audit
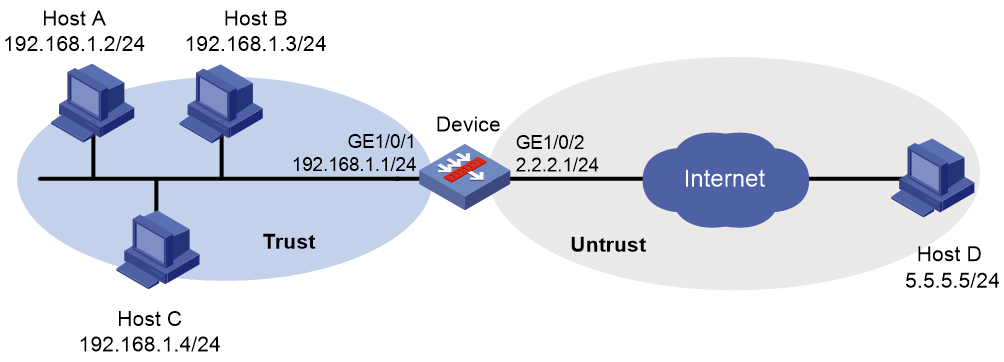
Network configuration
As shown in Figure 3, all departments of a company access the Internet through the device. The working hours of the company are 8:00:00 through 18:00:00 from Monday to Friday.
Configure an application audit and management policy on the device to meet the following requirements:
· Deny search requests for Bing that include keyword confidential or terrorist attack.
· Generate audit logs.
Procedure
1. Assign IP addresses to interfaces and configure routes, security zones, zone pairs, and interzone policies. Make sure the network connections are available. (Details not shown.)
2. Configure an application audit and management policy:
# Enter application audit and management view.
<Device> system-view
[Device] uapp-control
# Configure a keyword group named keyword-bing.
[Device-uapp-control] keyword-group name keyword-bing
# Add keywords confidential and terrorist attack to keyword group keyword-bing.
[Device-uapp-control-keyword-group-keyword-bing] keyword confidential
[Device-uapp-control-keyword-group-keyword-bing] keyword terrorist attack
[Device-uapp-control-keyword-group-keyword-bing] quit
# Create an audit policy named audit-bing and enter its view.
[Device-uapp-control] policy name audit-bing audit
# Configure source security zone Trust as a match criterion for audit policy audit-bing.
[Device-uapp-control-policy-audit-bing] source-zone trust
# Configure destination security zone Untrust as a match criterion for audit policy audit-bing.
[Device-uapp-control-policy-audit-bing] destination-zone untrust
# Configure an audit rule to deny search requests for Bing that include keyword confidential or terrorist attack, generating audit logs.
[Device-uapp-control-policy-audit-bing] rule 2 app Bing behavior Search bhcontent Keyword keyword include keyword-bing action deny audit-logging
[Device-uapp-control-policy-audit-bing] quit
[Device-uapp-control] quit
# Activate the configuration.
[Device] inspect activate
Verifying the configuration
When a user searches for information that includes keyword confidential or terrorist attack by using Bing, the device denies the search request and generates a log message.