- Table of Contents
-
- H3C S6890 Switch Series Configuration Examples-Release 27xx-6W100
- 01-Login Management Configuration Examples
- 02-RBAC Configuration Examples
- 03-Software Upgrade Examples
- 04-ISSU Configuration Examples
- 05-Software Patching Examples
- 06-Ethernet Link Aggregation Configuration Examples
- 07-Port Isolation Configuration Examples
- 08-Spanning Tree Configuration Examples
- 09-VLAN Configuration Examples
- 10-VLAN Tagging Configuration Examples
- 11-DHCP Snooping Configuration Examples
- 12-Cross-Subnet Dynamic IP Address Allocation Configuration Examples
- 13-GRE Tunnel Configuration Examples
- 14-GRE with OSPF Configuration Examples
- 15-OSPF Configuration Examples
- 16-IS-IS Configuration Examples
- 17-BGP Configuration Examples
- 18-Policy-Based Routing Configuration Examples
- 19-OSPFv3 Configuration Examples
- 20-IPv6 IS-IS Configuration Examples
- 21-Routing Policy Configuration Examples
- 22-IGMP Snooping Configuration Examples
- 23-IGMP Configuration Examples
- 24-Multicast VPN Configuration Examples
- 25-Basic MPLS Configuration Examples
- 26-MPLS L3VPN Configuration Examples
- 27-ACL Configuration Examples
- 28-Control Plane-Based QoS Policy Configuration Examples
- 29-Traffic Policing Configuration Examples
- 30-GTS and Rate Limiting Configuration Examples
- 31-Priority Mapping and Queue Scheduling Configuration Examples
- 32-Traffic Filtering Configuration Examples
- 33-AAA Configuration Examples
- 34-SSH Configuration Examples
- 35-IP Source Guard Configuration Examples
- 36-Ethernet OAM Configuration Examples
- 37-CFD Configuration Examples
- 38-DLDP Configuration Examples
- 39-VRRP Configuration Examples
- 40-BFD Configuration Examples
- 41-NTP Configuration Examples
- 42-SNMP Configuration Examples
- 43-NQA Configuration Examples
- 44-Mirroring Configuration Examples
- 45-sFlow Configuration Examples
- 46-FCoE Configuration Examples
- 47-OpenFlow Configuration Examples
- 48-MAC Address Table Configuration Examples
- 49-Static Multicast MAC Address Entry Configuration Examples
- 50-IP Unnumbered Configuration Examples
- 51-MVRP Configuration Examples
- 52-MCE Configuration Examples
- 53-Congestion Avoidance and Queue Scheduling Configuration Examples
- 54-Attack Protection Configuration Examples
- 55-Smart Link Configuration Examples
- 56-RRPP Configuration Examples
- 57-BGP Route Selection Configuration Examples
- 58-IS-IS Route Summarization Configuration Examples
- 59-IRF Configuration Examples
- 60-MPLS OAM Configuration Examples
- 61-MPLS TE Configuration Examples
- 62-VXLAN Configuration Examples
- 63-DRNI Configuration Examples
- 64-DRNI and EVPN Configuration Examples
- 65-VCF Fabric Configuration Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 29-Traffic Policing Configuration Examples | 83.17 KB |
|
|
|
H3C S6890 Switch Series |
|
Traffic Policing Configuration Examples |
|
|
Document version: 6W100-20190628
Copyright © 2019 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Contents
Example: Policing traffic by IP address and protocol type
Example: Configuring aggregate CAR
Introduction
This chapter provides examples for configuring traffic policing and aggregate CAR to control network traffic.
Prerequisites
The configuration examples in this document were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
This document assumes that you have basic knowledge of traffic policing.
Example: Policing traffic by IP address and protocol type
Network configuration
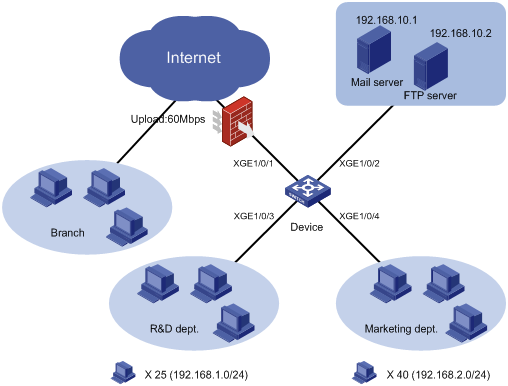
As shown in Figure 1, a company uses a dedicated line to access the Internet, with an uplink bandwidth of 60 Mbps. All end devices use the firewall as the gateway. The mail server forwards emails for all clients to the external network. The FTP server provides data services for the branch through the Internet.
Configure traffic policing to classify and rate limit the uplink traffic as follows:
· HTTP traffic—Rate limit HTTP traffic to a total rate of 40 Mbps (15 Mbps for the 25 hosts in the R&D department and 25 Mbps for the 40 hosts in the Marketing department).
· Email traffic—Rate limit email traffic to 2 Mbps.
· FTP traffic—Rate limit FTP traffic to 10 Mbps.
Analysis
To meet the network requirements, you must perform the following tasks:
· Configure ACLs to classify packets of different types.
· Associate classes with policing actions to rate limit packets of different types.
Software versions used
This configuration example was created and verified on S6890-CMW710-R2712.
Restrictions and guidelines
In a traffic behavior, the traffic policing action cannot be configured together with the following priority marking actions:
· Local precedence marking.
· Drop precedence marking.
· 802.1p priority marking.
· DSCP marking.
· IP precedence marking.
Otherwise, the class-behavior association for that traffic behavior cannot be applied correctly.
Procedures
1. Police HTTP traffic from the R&D department:
# Create advanced IPv4 ACL 3000 to match HTTP traffic from the R&D department.
<Device> system-view
[Device] acl advanced 3000
[Device-acl-ipv4-adv-3000] rule permit tcp destination-port eq 80 source 192.168.1.0 0.0.0.255
[Device-acl-ipv4-adv-3000] quit
# Create a class named rd_http, and use advanced IPv4 ACL 3000 as the match criterion.
[Device] traffic classifier rd_http
[Device-classifier-rd_http] if-match acl 3000
[Device-classifier-rd_http] quit
# Create a behavior named rd_http, and configure traffic policing with the CIR of 15 Mbps.
[Device] traffic behavior rd_http
[Device-behavior-rd_http] car cir 15360
[Device-behavior-rd_http] quit
# Create a QoS policy named rd_http, and associate the class rd_http with the behavior rd_http in the QoS policy.
[Device] qos policy rd_http
[Device-qospolicy-rd_http] classifier rd_http behavior rd_http
[Device-qospolicy-rd_http] quit
# Apply the QoS policy rd_http to the inbound direction of interface Ten-GigabitEthernet 1/0/3.
[Device] interface ten-gigabitethernet 1/0/3
[Device-Ten-GigabitEthernet1/0/3] qos apply policy rd_http inbound
[Device-Ten-GigabitEthernet1/0/3] quit
2. Police HTTP traffic from the Marketing department:
# Create advanced IPv4 ACL 3001 to match HTTP traffic from the Marketing department.
[Device] acl advanced 3001
[Device-acl-ipv4-adv-3001] rule permit tcp destination-port eq 80 source 192.168.2.0 0.0.0.255
[Device-acl-ipv4-adv-3001] quit
# Create a class named mkt_http, and use advanced IPv4 ACL 3001 as the match criterion.
[Device] traffic classifier mkt_http
[Device-classifier-mkt_http] if-match acl 3001
[Device-classifier-mkt_http] quit
# Create a behavior named mkt_http, and configure traffic policing with the CIR of 25 Mbps.
[Device] traffic behavior mkt_http
[Device-behavior-mkt_http] car cir 25600
[Device-behavior-mkt_http] quit
# Create a QoS policy named mkt_http, and associate the class mkt_http with the behavior mkt_http in the QoS policy.
[Device] qos policy mkt_http
[Device-qospolicy-mkt_http] classifier mkt_http behavior mkt_http
[Device-qospolicy-mkt_http] quit
# Apply the QoS policy mkt_http to the inbound direction of interface Ten-GigabitEthernet 1/0/4.
[Device] interface ten-gigabitethernet 1/0/4
[Device-Ten-GigabitEthernet1/0/4] qos apply policy mkt_http inbound
[Device-Ten-GigabitEthernet1/0/4] quit
3. Police email traffic and FTP traffic:
# Create advanced IPv4 ACL 3002 to match email traffic.
[Device] acl advanced 3002
[Device-acl-ipv4-adv-3002] rule permit tcp destination-port eq smtp source 192.168.10.1 0.0.0.0
[Device-acl-ipv4-adv-3002] quit
# Create a class named email, and use advanced IPv4 ACL 3002 as the match criterion.
[Device] traffic classifier email
[Device-classifier-email] if-match acl 3002
[Device-classifier-email] quit
# Create a behavior named email, and configure traffic policing with the CIR of 2 Mbps.
[Device] traffic behavior email
[Device-behavior-email] car cir 2048
[Device-behavior-email] quit
# Create basic IPv4 ACL 2001 to match FTP traffic.
[Device] acl basic 2001
[Device-acl-ipv4-basic-2001] rule permit source 192.168.10.2 0.0.0.0
[Device-acl-ipv4-basic-2001] quit
# Create a class named ftp, and use basic IPv4 ACL 2001 as the match criterion.
[Device] traffic classifier ftp
[Device-classifier-ftp] if-match acl 2001
[Device-classifier-ftp] quit
# Create a behavior named ftp, and configure traffic policing with the CIR of 10 Mbps.
[Device] traffic behavior ftp
[Device-behavior-ftp] car cir 10240
[Device-behavior-ftp] quit
# Create a QoS policy named email&ftp, and associate the classes email and ftp with the behavior email and ftp in the QoS policy, respectively.
[Device] qos policy email&ftp
[Device-qospolicy-email&ftp] classifier email behavior email
[Device-qospolicy-email&ftp] classifier ftp behavior ftp
[Device-qospolicy-email&ftp] quit
# Apply the QoS policy email&ftp to the inbound direction of interface Ten-GigabitEthernet 1/0/2.
[Device] interface ten-gigabitethernet 1/0/2
[Device-Ten-GigabitEthernet1/0/2] qos apply policy email&ftp inbound
[Device-Ten-GigabitEthernet1/0/2] quit
Verifying the configuration
# Verify QoS policies applied to interfaces.
[Device] display qos policy interface
Interface: Ten-GigabitEthernet1/0/2
Direction: Inbound
Policy: email&ftp
Classifier: email
Operator: AND
Rule(s) :
If-match acl 3002
Behavior: email
Committed Access Rate:
CIR 2048 (kbps), CBS 128000 (Bytes), EBS 0 (Bytes)
Green action : pass
Yellow action : pass
Red action : discard
Green packets : 0 (Packets)
Red packets : 0 (Packets)
Classifier: ftp
Operator: AND
Rule(s) :
If-match acl 2001
Behavior: ftp
Committed Access Rate:
CIR 10240 (kbps), CBS 640000 (Bytes), EBS 0 (Bytes)
Green action : pass
Yellow action : pass
Red action : discard
Green packets : 0 (Packets)
Red packets : 0 (Packets)
Interface: Ten-GigabitEthernet1/0/3
Direction: Inbound
Policy: rd_http
Classifier: rd_http
Operator: AND
Rule(s) :
If-match acl 3000
Behavior: rd_http
Committed Access Rate:
CIR 15360 (kbps), CBS 960000 (Bytes), EBS 0 (Bytes)
Green action : pass
Yellow action : pass
Red action : discard
Green packets : 0 (Packets)
Red packets : 0 (Packets)
Interface: Ten-GigabitEthernet1/0/4
Direction: Inbound
Policy: mkt_http
Classifier: mkt_http
Operator: AND
Rule(s) :
If-match acl 3001
Behavior: mkt_http
Committed Access Rate:
CIR 25600 (kbps), CBS 1600000 (Bytes), EBS 0 (Bytes)
Green action : pass
Yellow action : pass
Red action : discard
Green packets : 0 (Packets)
Red packets : 0 (Packets)
Configuration files
#
traffic classifier email operator and
if-match acl 3002
#
traffic classifier ftp operator and
if-match acl 2001
#
traffic classifier mkt_http operator and
if-match acl 3001
#
traffic classifier rd_http operator and
if-match acl 3000
#
traffic behavior email
car cir 2048 cbs 128000 ebs 0 green pass red discard yellow pass
#
traffic behavior ftp
car cir 10240 cbs 640000 ebs 0 green pass red discard yellow pass
#
traffic behavior mkt_http
car cir 25600 cbs 1600000 ebs 0 green pass red discard yellow pass
#
traffic behavior rd_http
car cir 15360 cbs 960000 ebs 0 green pass red discard yellow pass
#
qos policy email&ftp
classifier email behavior email
classifier ftp behavior ftp
#
qos policy mkt_http
classifier mkt_http behavior mkt_http
#
qos policy rd_http
classifier rd_http behavior rd_http
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
qos apply policy email&ftp inbound
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
qos apply policy rd_http inbound
#
interface Ten-GigabitEthernet1/0/4
port link-mode bridge
qos apply policy mkt_http inbound
#
acl basic 2001
rule 0 permit source 192.168.10.2 0
#
acl advanced 3000
rule 0 permit tcp source 192.168.1.0 0.0.0.255 destination-port eq www
#
acl advanced 3001
rule 0 permit tcp source 192.168.2.0 0.0.0.255 destination-port eq www
#
acl advanced 3002
rule 0 permit tcp source 192.168.10.1 0 destination-port eq smtp
Example: Configuring aggregate CAR
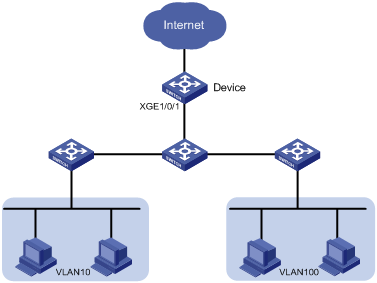
Network configuration
As shown in Figure 2, the access layer devices add VLAN tags to the traffic from VLAN 10 and VLAN 100 before sending the traffic to the device.
Configure aggregate CAR on Ten-GigabitEthernet 1/0/1 to meet the following requirements:
· Limit the incoming traffic from VLAN 10 and VLAN 100 to 200 Mbps.
· Drop the excess traffic.
Software versions used
This configuration example was created and verified on S6890-CMW710-R2712.
Procedures
# Configure interface Ten-GigabitEthernet 1/0/1 as a trunk port.
<Device> system-view
[Device] interface ten-gigabitethernet 1/0/1
[Device-Ten-GigabitEthernet1/0/1] port link-type trunk
# Assign the interface to VLANs 10 and 100.
[Device-Ten-GigabitEthernet1/0/1] port trunk permit vlan 10 100
# Remove the interface from VLAN 1.
[Device-Ten-GigabitEthernet1/0/1] undo port trunk permit vlan 1
[Device-Ten-GigabitEthernet1/0/1] quit
# Create an aggregate CAR action.
[Device] qos car aggcar-1 aggregative cir 204800
# Create class 1, and use SVLAN ID 10 as the match criterion.
[Device] traffic classifier 1
[Device-classifier-1] if-match service-vlan-id 10
[Device-classifier-1] quit
# Create behavior 1, and reference the aggregate CAR action in the behavior.
[Device] traffic behavior 1
[Device-behavior-1] car name aggcar-1
[Device-behavior-1] quit
# Create class 2, and use SVLAN ID 100 as the match criterion.
[Device] traffic classifier 2
[Device-classifier-2] if-match service-vlan-id 100
[Device-classifier-2] quit
# Create behavior 2, and reference the aggregate CAR action in the behavior.
[Device] traffic behavior 2
[Device-behavior-2] car name aggcar-1
[Device-behavior-2] quit
# Create a QoS policy named car, and associate the classes with the behaviors in the QoS policy.
[Device] qos policy car
[Device-qospolicy-car] classifier 1 behavior 1
[Device-qospolicy-car] classifier 2 behavior 2
[Device-qospolicy-car] quit
# Apply the QoS policy car to the inbound direction of Ten-GigabitEthernet 1/0/1.
[Device] interface ten-gigabitethernet 1/0/1
[Device-Ten-GigabitEthernet1/0/1] qos apply policy car inbound
Verifying the configuration
Verify the configuration on any interface, for example, Ten-GigabitEthernet 1/0/1.
# Verify QoS policies applied to interface Ten-GigabitEthernet 1/0/1.
[Device] display qos policy interface ten-gigabitethernet 1/0/1
Interface: Ten-GigabitEthernet1/0/1
Direction: Inbound
Policy: car
Classifier: 1
Operator: AND
Rule(s) :
If-match service-vlan-id 10
Behavior: 1
Committed Access Rate:
Car name: aggcar-1
Classifier: 2
Operator: AND
Rule(s) :
If-match service-vlan-id 100
Behavior: 2
Committed Access Rate:
Car name: aggcar-1
Configuration files
#
qos car aggcar-1 aggregative cir 204800 cbs 12800000 ebs 0 green pass yellow pass red discard
#
traffic classifier 1 operator and
if-match service-vlan-id 10
traffic classifier 2 operator and
if-match service-vlan-id 100
#
traffic behavior 1
car name aggcar-1
traffic behavior 2
car name aggcar-1
#
qos policy car
classifier 1 behavior 1
classifier 2 behavior 2
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 10 100
qos apply policy car inbound
Related documentation
· H3C S6890 Switch Series ACL and QoS Command Reference (R27xx)
· H3C S6890 Switch Series ACL and QoS Configuration Guide (R27xx)
