- Table of Contents
-
- 10-High Availability Configuration Guide
- 00-Preface
- 01-Ethernet OAM configuration
- 02-CFD configuration
- 03-DLDP configuration
- 04-RRPP configuration
- 05-Smart Link configuration
- 06-Monitor Link configuration
- 07-VRRP configuration
- 08-BFD configuration
- 09-Track configuration
- 10-Process placement configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 09-Track configuration | 221.38 KB |
Collaboration application example·
Associating the Track module with a detection module
Associating Track with interface management
Associating the Track module with an application module
Associating Track with static routing
Associating Track with Smart Link
Displaying and maintaining track entries
VRRP-Track-NQA collaboration configuration example
Configuring BFD for a VRRP backup to monitor the master
Configuring BFD for the VRRP master to monitor the uplinks
Static routing-Track-NQA collaboration configuration example
Static routing-Track-BFD collaboration configuration example
VRRP-Track-interface management collaboration configuration example
Smart Link-Track-CFD collaboration configuration example
Configuring Track
Overview
The Track module works between application modules and detection modules, as shown in Figure 1. It shields the differences between various detection modules from application modules.
Collaboration is enabled when you associate the Track module with a detection module and an application module, and it operates as follows:
1. The detection module probes specific objects such as interface status, link status, network reachability, and network performance, and informs the Track module of detection results.
2. The Track module sends the detection results to the application module.
3. When notified of changes for the tracked object, the application modules can react to avoid communication interruption and network performance degradation.
Figure 1 Collaboration through the Track module
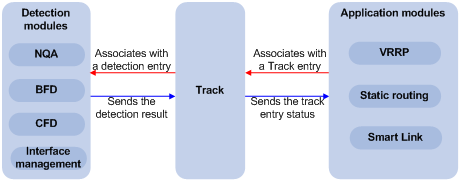
Collaboration fundamentals
The Track module collaborates with detection modules and application modules.
Collaboration between the Track module and a detection module
The detection module sends the detection result of the tracked object to the Track module. The Track module changes the status of the track entry as follows:
· If the tracked object operates correctly, the state of the track entry is Positive. For example, the track entry state is Positive in one of the following conditions:
¡ The target interface is up.
¡ The target network is reachable.
· If the tracked object does not operate correctly, the state of the track entry is Negative. For example, the track entry state is Negative in one of the following conditions:
¡ The target interface is down.
¡ The target network is unreachable.
· If the detection result is not valid, the state of the track entry is NotReady. For example, the track entry state is NotReady if its associated NQA operation does not exist.
The following detection modules can be associated with the Track module:
· NQA.
· BFD.
· CFD.
· Interface management.
Collaboration between the Track module and an application module
The following application modules can be associated with the Track module:
· VRRP.
· Static routing.
When configuring a track entry for an application module, you can set a notification delay to avoid immediate notification of status changes.
When the delay is not configured and the route convergence is slower than the link state change notification, communication failures occur. For example, when the master in a VRRP group detects an uplink interface failure through the Track module, the Track module immediately notifies the master to decrease its priority. A backup with a higher priority then preempts as the new master. When the failed uplink interface recovers, the Track module immediately notifies the original master to restore its priority. If the uplink route has not recovered, forwarding failure will occur.
Collaboration application example
The following is an example of collaboration between NQA, Track, and static routing.
Configure a static route with the next hop 192.168.0.88 on the device. If the next hop is reachable, the static route is valid. If the next hop becomes unreachable, the static route is invalid. For this purpose, configure collaboration between the NQA, track, and static routing modules:
1. Create an NQA operation to monitor the accessibility of IP address 192.168.0.88.
2. Create a track entry and associate it with the NQA operation.
¡ When the next hop 192.168.0.88 is reachable, NQA sends the result to the Track module. The Track module sets the track entry to Positive state.
¡ When the next hop becomes unreachable, NQA sends the result to the Track module. The Track module sets the track entry to Negative state.
3. Associate the track entry with the static route.
¡ When the track entry is in Positive state, the static routing module considers the static route to be valid.
¡ When the track entry is in Negative state, the static routing module considers the static route to be invalid.
Track configuration task list
To implement the collaboration function, establish associations between the Track module and detection modules, and between the Track module and application modules.
To configure the Track module, perform the following tasks:
|
Tasks at a glance |
|
(Required.) Associating the Track module with a detection module: |
|
(Required.) Associating the Track module with an application module: |
Associating the Track module with a detection module
Associating Track with NQA
NQA supports multiple operation types to analyze network performance and service quality. For example, an NQA operation can periodically detect whether a destination is reachable, or whether a TCP connection can be established.
An NQA operation operates as follows when it is associated with a track entry:
· If the consecutive failures reach the specified threshold, the NQA module notifies the Track module that the tracked object has malfunctioned. Then the Track module sets the track entry to Negative state.
· If the specified threshold is not reached, the NQA module notifies the Track module that the tracked object is operating correctly. The Track module then sets the track entry to Positive state.
For more information about NQA, see Network Management and Monitoring Configuration Guide.
To associate Track with NQA:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a track entry, associate it with an NQA reaction entry, and specify the delay time for the Track module to notify the associated application module when the track entry status changes. |
track track-entry-number nqa entry admin-name operation-tag reaction item-number [ delay { negative negative-time | positive positive-time } * ] |
By default, no track entry is created. If the specified NQA operation or the reaction entry in the track entry does not exist, the status of the track entry is NotReady. |
Associating Track with BFD
BFD supports the control packet mode and echo packet mode. A track entry can be associated only with the echo-mode BFD session. For more information about BFD, see "Configuring BFD."
The associated Track and BFD operate as follows:
· If the BFD detects that the link fails, it informs the Track module of the link failure. The Track module sets the track entry to Negative state.
· If the BFD detects that the link is operating correctly, the Track module sets the track entry to Positive state.
Before you associate Track with BFD, configure the source IP address of BFD echo packets. For more information, see "Configuring BFD."
To associate Track with BFD:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a track entry, associate it with a BFD session. |
track track-entry-number bfd echo interface interface-type interface-number remote ip remote-ip local ip local-ip [ delay { negative negative-time | positive positive-time } * ] |
No track entry is created by default. Do not configure the virtual IP address of a VRRP group as the local or remote address of a BFD session. |
Associating Track with CFD
The associated Track and CFD operate as follows:
· If the CFD detects that the link fails, it informs the track entry of the link failure. The Track module then sets the track entry to Negative state.
· If the CFD detects that the link is operating correctly, the Track module sets the track entry to Positive state.
Before you associate Track with CFD, enable CFD and create a MEP. For more information, see "Configuring CFD."
To associate Track with CFD:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a track entry, associate it with the CFD session, and specify the delay time for the Track module to notify the associated application module when the track entry status changes. |
track track-entry-number cfd cc service-instance instance-id mep mep-id [ delay { negative negative-time | positive positive-time } * ] |
No track entry is created by default. |
Associating Track with interface management
The interface management module monitors the link status or network-layer protocol status of interfaces. The associated Track and interface management operate as follows:
· When the link or network-layer protocol status of the interface changes to up, the interface management module informs the Track module of the change. The Track module sets the track entry to Positive.
· When the link or network-layer protocol status of the interface changes to down, the interface management module informs the Track module of the change. The Track module sets the track entry to Negative.
To associate Track with interface management:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a track entry, and associate it with interface management. |
·
Associate Track with the interface management module to monitor the link
status of an interface: ·
Associate Track with the interface
management module to monitor the network-layer protocol status of an interface: |
By default, no track entry is created. |
Associating the Track module with an application module
Associating Track with VRRP
When VRRP is operating in standard mode or load balancing mode, associate the Track module with the VRRP group to implement the following actions:
· Change the priority of a router according to the status of the uplink. If a fault occurs on the uplink of the router, the VRRP group is not aware of the uplink failure. If the router is the master, hosts in the LAN cannot access the external network. To resolve this problem, configure the detection module-Track-VRRP collaboration. The detection module monitors the status of the uplink of the router and notifies the Track module of the detection result.
When the uplink fails, the detection module notifies the Track module to change the status of the monitored track entry to Negative. The priority of the master decreases by a user-specified value. A router with a higher priority in the VRRP group becomes the master.
· Monitor the master on a backup. If a fault occurs on the master, the backup operating in switchover mode will switch to the master immediately to maintain normal communication.
When VRRP is operating in load balancing mode, associate the Track module with the VRRP VF to implement the following functions:
· Change the priority of the AVF according to its uplink state. When the uplink of the AVF fails, the track entry changes to Negative state. The weight of the AVF decreases by a user-specified value. The VF with a higher priority becomes the new AVF to forward packets.
· Monitor the AVF status from the LVF. When the AVF fails, the LVF that is operating in switchover mode becomes the new AVF to ensure continuous forwarding.
When you associate Track with VRRP, follow these restrictions and guidelines:
· The vrrp vrid track priority reduced or vrrp vrid track switchover command does not take effect on an IP address owner. The command takes effect when the router does not act as the IP address owner.
An IP address owner is the router with its interface IP address used as the virtual IP address of the VRRP group.
· When the status of the track entry changes from Negative to Positive or NotReady, one of the following events occurs:
¡ The master router automatically restores its priority.
¡ The AVF automatically restores its weight.
¡ The failed master router becomes the master again.
¡ The failed AVF becomes active again.
· You can associate a nonexistent track entry with a VRRP group or VF. The association takes effect only after you create the track entry.
Associating Track with VRRP
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Associate Track with VRRP. |
By default, VRRP is not associated with any track entries. |
Associating Track with static routing
A static route is a manually configured route to route packets. For more information about static route configuration, see Layer 3—IP Routing Configuration Guide.
A disadvantage of using static routes is that they cannot adapt to network topology changes. Link failures or network topological changes can make the routes unreachable and cause communication interruption.
To resolve this problem, configure another route to back up the static route. When the static route is reachable, packets are forwarded through the static route. When the static route is unreachable, packets are forwarded through the backup route.
To check the accessibility of a static route in real time, associate the Track module with the static route.
If you specify the next hop but not the output interface when configuring a static route, you can configure the static routing-Track-detection module collaboration. This collaboration enables you to verify the accessibility of the static route based on the status of the track entry.
· If the track entry is in Positive state, the following conditions exist:
¡ The next hop of the static route is reachable.
¡ The configured static route is valid.
· If the track entry is in Negative state, the following conditions exist:
¡ The next hop of the static route is not reachable.
¡ The configured static route is invalid.
· If the track entry is in NotReady state, the following conditions exist:
¡ The accessibility of the next hop of the static route is unknown.
¡ The static route is valid.
When you associate Track with static routing, follow these restrictions and guidelines:
· You can associate a nonexistent track entry with a static route. The association takes effect only after you create the track entry.
· In static routing-Track-NQA collaboration, you must configure the same VPN instance name for the NQA operation and the next hop of the static route. Otherwise, the accessibility detection cannot operate correctly.
· If a static route needs route recursion, the associated track entry must monitor the next hop of the recursive route instead of that of the static route. Otherwise, a valid route might be considered invalid.
To associate Track with static routing:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Associate a static route with a track entry to check the accessibility of the next hop. |
·
Method 1: ·
Method 2: |
By default, Track is not associated with static routing. |
Associating Track with Smart Link
Smart Link cannot detect unidirectional links, misconnected fibers, or packet loss on intermediate devices or network paths of the uplink. It also cannot detect when faults are cleared. To check the link status, Smart Link ports must use link detection protocols. When a fault is detected or cleared, the link detection protocols inform Smart Link to switch over the links.
For more information about Smart Link, see "Configuring Smart Link."
Displaying and maintaining track entries
Execute display commands in any view.
|
Task |
Command |
|
Display information about a specific or all track entries. |
display track { track-entry-number | all } |
Track configuration examples
VRRP-Track-NQA collaboration configuration example
Network requirements
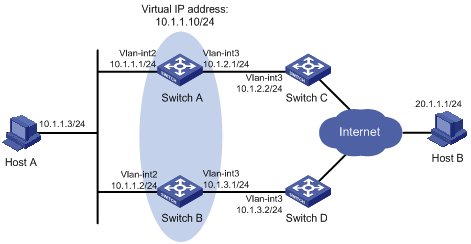
As shown in Figure 2:
· Host A requires access to Host B. The default gateway of Host A is 10.1.1.10/24.
· Switch A and Switch B belong to VRRP group 1. The virtual IP address of VRRP group 1 is 10.1.1.10.
Configure VRRP-Track-NQA collaboration to monitor the uplink on the master and meet the following requirements:
· When Switch A operates correctly, it forwards packets from Host A to Host B.
· When NQA detects a fault on the uplink of Switch A, Switch B forwards packets from Host A to Host B.
Configuration procedure
1. Create VLANs and assign ports to them. Configure the IP address of each VLAN interface as shown in Figure 2. (Details not shown.)
2. Configure an NQA operation on Switch A:
# Create an NQA operation with the administrator name admin and the operation tag test.
<SwitchA> system-view
[SwitchA] nqa entry admin test
# Configure the operation type as ICMP echo.
[SwitchA-nqa-admin-test] type icmp-echo
# Configure the destination address of ICMP echo requests as 10.1.2.2.
[SwitchA-nqa-admin-test-icmp-echo] destination ip 10.1.2.2
# Configure the ICMP echo operation to repeat at an interval of 100 milliseconds.
[SwitchA-nqa-admin-test-icmp-echo] frequency 100
# Configure reaction entry 1, specifying that five consecutive probe failures trigger the Track module.
[SwitchA-nqa-admin-test-icmp-echo] reaction 1 checked-element probe-fail threshold-type consecutive 5 action-type trigger-only
[SwitchA-nqa-admin-test-icmp-echo] quit
# Start the NQA operation.
[SwitchA] nqa schedule admin test start-time now lifetime forever
3. On Switch A, configure track entry 1, and associate it with reaction entry 1 of the NQA operation.
[SwitchA] track 1 nqa entry admin test reaction 1
4. Configure VRRP on Switch A:
# Specify VRRPv2 to run on VLAN-interface 2.
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] vrrp version 2
# Create VRRP group 1, and configure the virtual IP address 10.1.1.10 for the group.
[SwitchA-Vlan-interface2] vrrp vrid 1 virtual-ip 10.1.1.10
# Set the priority of Switch A to 110 in VRRP group 1.
[SwitchA-Vlan-interface2] vrrp vrid 1 priority 110
# Set the authentication mode of VRRP group 1 to simple, and the authentication key to hello.
[SwitchA-Vlan-interface2] vrrp vrid 1 authentication-mode simple hello
# Configure the master to send VRRP packets at an interval of 500 centiseconds.
[SwitchA-Vlan-interface2] vrrp vrid 1 timer advertise 500
# Configure Switch A to operate in preemptive mode and set the preemption delay to 500 centiseconds.
[SwitchA-Vlan-interface2] vrrp vrid 1 preempt-mode delay 500
# Configure to monitor track entry 1 and decrease the router priority by 30 when the state of track entry 1 changes to negative.
[SwitchA-Vlan-interface2] vrrp vrid 1 track 1 reduced 30
5. Configure VRRP on Switch B:
# Specify VRRPv2 to run on VLAN-interface 2.
<SwitchB> system-view
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] vrrp version 2
# Create VRRP group 1, and configure the virtual IP address 10.1.1.10 for the group.
[SwitchB-Vlan-interface2] vrrp vrid 1 virtual-ip 10.1.1.10
# Set the authentication mode of VRRP group 1 to simple, and the authentication key to hello.
[SwitchB-Vlan-interface2] vrrp vrid 1 authentication-mode simple hello
# Configure the master to send VRRP packets at an interval of 500 centiseconds.
[SwitchB-Vlan-interface2] vrrp vrid 1 timer advertise 500
# Configure Switch B to operate in preemptive mode and set the preemption delay to 500 centiseconds.
[SwitchB-Vlan-interface2] vrrp vrid 1 preempt-mode timer delay 500
Verifying the configuration
# Ping Host B from Host A to verify that Host B is reachable. (Details not shown.)
# Display detailed information about VRRP group 1 on Switch A.
[SwitchA-Vlan-interface2] display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 500
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 500
Auth Type : Simple Key : ******
Virtual IP : 10.1.1.10
Virtual MAC : 0000-5e00-0101
Master IP : 10.1.1.1
VRRP Track Information:
Track Object : 1 State : Positive Pri Reduced : 30
# Display detailed information about VRRP group 1 on Switch B.
[SwitchB-Vlan-interface2] display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 500
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 500
Become Master : 2200ms left
Auth Type : Simple Key : ******
Virtual IP : 10.1.1.10
Master IP : 10.1.1.1
The output shows that in VRRP group 1, Switch A is the master, and Switch B is a backup. Switch A forwards packets from Host A to Host B.
# Disconnect the link between Switch A and Switch C, and verify that Host A can still ping Host B. (Details not shown.)
# Display detailed information about VRRP group 1 on Switch A.
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 500
Admin Status : Up State : Backup
Config Pri : 110 Running Pri : 80
Preempt Mode : Yes Delay Time : 500
Become Master : 2200ms left
Auth Type : Simple Key : ******
Virtual IP : 10.1.1.10
Master IP : 10.1.1.2
VRRP Track Information:
Track Object : 1 State : Negative Pri Reduced : 30
# Display detailed information about VRRP group 1 on Switch B.
[SwitchB-Vlan-interface2] display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 500
Admin Status : Up State : Master
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 500
Auth Type : Simple Key : ******
Virtual IP : 10.1.1.10
Virtual MAC : 0000-5e00-0101
Master IP : 10.1.1.2
The output shows that Switch A becomes the backup, and Switch B becomes the master. Switch B forwards packets from Host A to Host B.
Configuring BFD for a VRRP backup to monitor the master
Network requirements
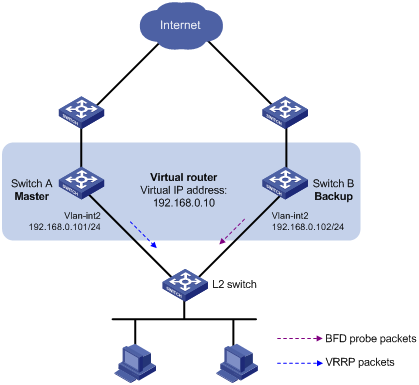
As shown in Figure 3:
· Switch A and Switch B belong to VRRP group 1. The virtual IP address of VRRP group 1 is 192.168.0.10.
· The default gateway of the hosts in the LAN is 192.168.0.10.
Configure VRRP-Track-BFD collaboration to monitor the master on the backup and meet the following requirements:
· When Switch A operates correctly, the hosts in the LAN access the Internet through Switch A.
· When Switch A fails, the backup (Switch B) can quickly detect the state change of the master through BFD and become the new master. The hosts in the LAN access the Internet through Switch B.
Configuration procedure
1. Create VLANs and assign ports to them. Configure the IP address of each VLAN interface as shown in Figure 3. (Details not shown.)
2. Configure Switch A:
# Create VRRP group 1, and configure the virtual IP address 192.168.0.10 for the group.
<SwitchA> system-view
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] vrrp vrid 1 virtual-ip 192.168.0.10
# Set the priority of Switch A to 110 in VRRP group 1.
[SwitchA-Vlan-interface2] vrrp vrid 1 priority 110
[SwitchA-Vlan-interface2] return
3. Configure Switch B:
# Configure the source address of BFD echo packets as 10.10.10.10.
<SwitchB> system-view
[SwitchB] bfd echo-source-ip 10.10.10.10
# Create track entry 1, and associate it with the BFD session to verify the reachability of Switch A.
[SwitchB] track 1 bfd echo interface vlan-interface 2 remote ip 192.168.0.101 local ip 192.168.0.102
# Create VRRP group 1, and configure the virtual IP address 192.168.0.10 for the group.
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] vrrp vrid 1 virtual-ip 192.168.0.10
# Configure VRRP group 1 to monitor the status of track entry 1.
[SwitchB-Vlan-interface2] vrrp vrid 1 track 1 switchover
[SwitchB-Vlan-interface2] return
Verifying the configuration
# Display detailed information about VRRP group 1 on Switch A.
<SwitchA> display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 0
Auth Type : None
Virtual IP : 192.168.0.10
Virtual MAC : 0000-5e00-0101
Master IP : 192.168.0.101
# Display detailed information about VRRP group 1 on Switch B.
<SwitchB> display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 0
Become Master : 2200ms left
Auth Type : None
Virtual IP : 192.168.0.10
Master IP : 192.168.0.101
VRRP Track Information:
Track Object : 1 State : Positive Switchover
# Display information about track entry 1 on Switch B.
<SwitchB> display track 1
Track ID: 1
State: Positive
Duration: 0 days 0 hours 0 minutes 32 seconds
Notification delay: Positive 0, Negative 0 (in seconds)
Tracked object:
BFD session mode: Echo
Outgoing interface: Vlan-interface2
VPN instance name: -
Remote IP: 192.168.0.101
Local IP: 192.168.0.102
The output shows that when the status of the track entry becomes Positive, Switch A is the master and Switch B is the backup.
# Enable VRRP state debugging and BFD event notification debugging on Switch B.
<SwitchB> terminal debugging
<SwitchB> terminal monitor
<SwitchB> debugging vrrp fsm
<SwitchB> debugging bfd ntfy
# When Switch A fails, the following output is displayed on Switch B.
*Dec 17 14:44:34:142 2014 SwitchB BFD/7/DEBUG: Notify application:TRACK State:DOWN
*Dec 17 14:44:34:144 2014 SwitchB VRRP4/7/FSM:
IPv4 Vlan-interface2 | Virtual Router 1 : Backup --> Master reason: The status of the tracked object changed
# Display detailed information about the VRRP group on Switch B.
<SwitchB> display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 0
Auth Type : None
Virtual IP : 192.168.0.10
Virtual MAC : 0000-5e00-0101
Master IP : 192.168.0.102
VRRP Track Information:
Track Object : 1 State : Negative Switchover
The output shows that when BFD detects that Switch A fails, the Track module notifies VRRP to change the status of Switch B to master. The backup can quickly preempt as the master without waiting for a period three times the advertisement interval plus the Skew_Time.
Configuring BFD for the VRRP master to monitor the uplinks
Network requirements
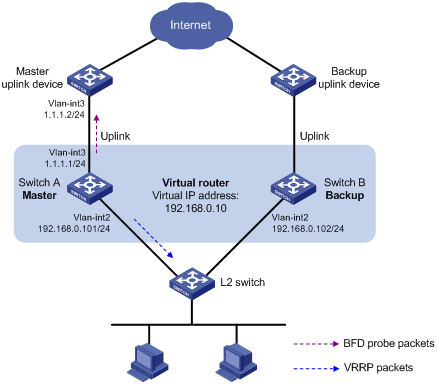
As shown in Figure 4:
· Switch A and Switch B belong to VRRP group 1. The virtual IP address of VRRP group 1 is 192.168.0.10.
· The default gateway of the hosts in the LAN is 192.168.0.10.
Configure VRRP-Track-BFD collaboration to monitor the uplink on the master and meet the following requirements:
· When Switch A operates correctly, the hosts in the LAN access the Internet through Switch A.
· When Switch A detects that the uplink is down through BFD, Switch B can preempt as the master. The hosts in the LAN can access the Internet through Switch B.
Configuration procedure
1. Create VLANs and assign ports to them. Configure the IP address of each VLAN interface as shown in Figure 4. (Details not shown.)
2. Configure Switch A:
# Configure the source address of BFD echo packets as 10.10.10.10.
<SwitchA> system-view
[SwitchA] bfd echo-source-ip 10.10.10.10
# Create track entry 1 for the BFD session to verify the reachability of the uplink device (1.1.1.2 ).
[SwitchA] track 1 bfd echo interface vlan-interface 3 remote ip 1.1.1.2 local ip 1.1.1.1
# Create VRRP group 1, and configure the virtual IP address of the group as 192.168.0.10.
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] vrrp vrid 1 virtual-ip 192.168.0.10
# Set the priority of Switch A to 110 in VRRP group 1.
[SwitchA-Vlan-interface2] vrrp vrid 1 priority 110
# Associate VRRP group 1 with track entry 1 and decrease the router priority by 20 when the state of track entry 1 changes to negative.
[SwitchA-Vlan-interface2] vrrp vrid 1 track 1 priority reduced 20
[SwitchA-Vlan-interface2] return
3. On Switch B, create VRRP group 1, and configure the virtual IP address of the group as 192.168.0.10.
<SwitchB> system-view
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] vrrp vrid 1 virtual-ip 192.168.0.10
[SwitchB-Vlan-interface2] return
Verifying the configuration
# Display detailed information about the VRRP group on Switch A.
<SwitchA> display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 0
Auth Type : None
Virtual IP : 192.168.0.10
Virtual MAC : 0000-5e00-0101
Master IP : 192.168.0.101
VRRP Track Information:
Track Object : 1 State : Positive Pri Reduced : 20
# Display information about track entry 1 on Switch A.
<SwitchA> display track 1
Track ID: 1
State: Positive
Duration: 0 days 0 hours 0 minutes 32 seconds
Notification delay: Positive 0, Negative 0 (in seconds)
Tracked object:
BFD session mode: Echo
Outgoing interface: Vlan-interface2
VPN instance name: -
Remote IP: 1.1.1.2
Local IP: 1.1.1.1
# Display detailed information about the VRRP group on Switch B.
<SwitchB> display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 0
Become Master : 2200ms left
Auth Type : None
Virtual IP : 192.168.0.10
Master IP : 192.168.0.101
The output shows that when the status of track entry 1 becomes Positive, Switch A is the master and Switch B is the backup.
# Display information about track entry 1 when the uplink of Switch A goes down.
<SwitchA> display track 1
Track ID: 1
State: Negative
Duration: 0 days 0 hours 0 minutes 32 seconds
Notification delay: Positive 0, Negative 0 (in seconds)
Tracked object:
BFD session mode: Echo
Outgoing interface: Vlan-interface2
VPN instance name: -
Remote IP: 1.1.1.2
Local IP: 1.1.1.1
# Display detailed information about VRRP group 1 on Switch A.
<SwitchA> display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 110 Running Pri : 90
Preempt Mode : Yes Delay Time : 0
Become Master : 2200ms left
Auth Type : None
Virtual IP : 192.168.0.10
Master IP : 192.168.0.102
VRRP Track Information:
Track Object : 1 State : Negative Pri Reduced : 20
# Display detailed information about VRRP group 1 on Switch B.
<SwitchB> display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 0
Auth Type : None
Virtual IP : 192.168.0.10
Virtual MAC : 0000-5e00-0101
Master IP : 192.168.0.102
The output shows that when Switch A detects that the uplink fails through BFD, it decreases its priority by 20. Switch B then preempts as the master.
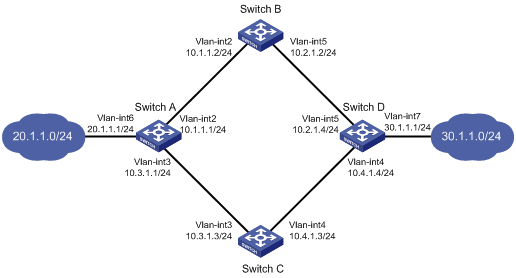
Static routing-Track-NQA collaboration configuration example
Network requirements
As shown in Figure 5:
· Switch A is the default gateway of the hosts in subnet 20.1.1.0/24.
· Switch D is the default gateway of the hosts in subnet 30.1.1.0/24.
· Hosts in the two subnets communicate with each other through static routes.
To ensure network availability, configure route backup and static routing-Track-NQA collaboration on Switch A and Switch D as follows:
· On Switch A, assign a higher priority to the static route to 30.1.1.0/24 with Switch B as the next hop. This route is the master route. The static route to 30.1.1.0/24 as the next hop acts as the backup route. When the master route is unavailable, the backup route takes effect. Switch A forwards packets to 30.1.1.0/24 through Switch C.
· On Switch D, assign a higher priority to the static route to 20.1.1.0/24 with Switch B as the next hop. This route is the master route. The static route to 20.1.1.0/24 with Switch C as the next hop acts as the backup route. When the master route is unavailable, the backup route takes effect. Switch D forwards packets to 20.1.1.0/24 through Switch C.
Configuration procedure
1. Create VLANs and assign ports to them. Configure the IP address of each VLAN interface as shown in Figure 5. (Details not shown.)
2. Configure Switch A:
# Configure a static route to 30.1.1.0/24 with the next hop 10.1.1.2 and the default priority 60. Associate this static route is with track entry 1.
<SwitchA> system-view
[SwitchA] ip route-static 30.1.1.0 24 10.1.1.2 track 1
# Configure a static route to 30.1.1.0/24 with the next hop 10.3.1.3 and the priority 80.
[SwitchA] ip route-static 30.1.1.0 24 10.3.1.3 preference 80
# Configure a static route to 10.2.1.4 with the next hop 10.1.1.2.
[SwitchA] ip route-static 10.2.1.4 24 10.1.1.2
# Create an NQA operation with the administrator admin and the operation tag test.
[SwitchA] nqa entry admin test
# Configure the operation type as ICMP echo.
[SwitchA-nqa-admin-test] type icmp-echo
# Configure the destination address of the operation as 10.2.1.4 and the next hop address as 10.1.1.2.
[SwitchA-nqa-admin-test-icmp-echo] destination ip 10.2.1.4
[SwitchA-nqa-admin-test-icmp-echo] next-hop 10.1.1.2
# Configure the ICMP echo operation to repeat at an interval of 100 milliseconds.
[SwitchA-nqa-admin-test-icmp-echo] frequency 100
# Configure reaction entry 1, specifying that five consecutive probe failures trigger the Track module.
[SwitchA-nqa-admin-test-icmp-echo] reaction 1 checked-element probe-fail threshold-type consecutive 5 action-type trigger-only
[SwitchA-nqa-admin-test-icmp-echo] quit
# Start the NQA operation.
[SwitchA] nqa schedule admin test start-time now lifetime forever
# Configure track entry 1, and associate it with reaction entry 1 of the NQA operation.
[SwitchA] track 1 nqa entry admin test reaction 1
3. Configure Switch B:
# Configure a static route to 30.1.1.0/24 with the next hop 10.2.1.4.
<SwitchB> system-view
[SwitchB] ip route-static 30.1.1.0 24 10.2.1.4
# Configure a static route to 20.1.1.0/24 with the next hop 10.1.1.1.
[SwitchB] ip route-static 20.1.1.0 24 10.1.1.1
4. Configure Switch C:
# Configure a static route to 30.1.1.0/24 with the next hop 10.4.1.4.
<SwitchC> system-view
[SwitchC] ip route-static 30.1.1.0 24 10.4.1.4
# Configure a static route to 20.1.1.0/24 with the next hop 10.3.1.1.
[SwitchC] ip route-static 20.1.1.0 24 10.3.1.1
5. Configure Switch D:
# Configure a static route to 20.1.1.0/24 with the next hop 10.2.1.2 and the default priority 60. Associate this static route with track entry 1.
<SwitchD> system-view
[SwitchD] ip route-static 20.1.1.0 24 10.2.1.2 track 1
# Configure a static route to 20.1.1.0/24 with the next hop 10.4.1.3 and the priority 80.
[SwitchD] ip route-static 20.1.1.0 24 10.4.1.3 preference 80
# Configure a static route to 10.1.1.1, with the next hop 10.2.1.2.
[SwitchD] ip route-static 10.1.1.1 24 10.2.1.2
# Create an NQA operation with the administrator admin and the operation tag test.
[SwitchD] nqa entry admin test
# Configure the operation type as ICMP echo.
[SwitchD-nqa-admin-test] type icmp-echo
# Configure the destination address of the operation as 10.1.1.1 and the next hop address as 10.2.1.2.
[SwitchD-nqa-admin-test-icmp-echo] destination ip 10.1.1.1
[SwitchD-nqa-admin-test-icmp-echo] next-hop 10.2.1.2
# Configure the ICMP echo operation to repeat at an interval of 100 milliseconds.
[SwitchD-nqa-admin-test-icmp-echo] frequency 100
# Configure reaction entry 1, specifying that five consecutive probe failures trigger the Track module.
[SwitchD-nqa-admin-test-icmp-echo] reaction 1 checked-element probe-fail threshold-type consecutive 5 action-type trigger-only
[SwitchD-nqa-admin-test-icmp-echo] quit
# Start the NQA operation.
[SwitchD] nqa schedule admin test start-time now lifetime forever
# Configure track entry 1, and associate it with reaction entry 1 of the NQA operation.
[SwitchD] track 1 nqa entry admin test reaction 1
Verifying the configuration
# Display information about the track entry on Switch A.
[SwitchA] display track all
Track ID: 1
State: Positive
Duration: 0 days 0 hours 0 minutes 32 seconds
Notification delay: Positive 0, Negative 0 (in seconds)
Tracked object:
NQA entry: admin test
Reaction: 1
The output shows that the status of the track entry is Positive, indicating that the NQA operation has succeeded and the master route is available.
# Display the routing table of Switch A.
[SwitchA] display ip routing-table
Destinations : 10 Routes : 10
Destination/Mask Proto Pre Cost NextHop Interface
10.1.1.0/24 Direct 0 0 10.1.1.1 Vlan2
10.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
10.2.1.0/24 Static 60 0 10.1.1.2 Vlan2
10.3.1.0/24 Direct 0 0 10.3.1.1 Vlan3
10.3.1.1/32 Direct 0 0 127.0.0.1 InLoop0
20.1.1.0/24 Direct 0 0 20.1.1.1 Vlan6
20.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
30.1.1.0/24 Static 60 0 10.1.1.2 Vlan2
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
The output shows that Switch A forwards packets to 30.1.1.0/24 through Switch B.
# Remove the IP address of interface VLAN-interface 2 on Switch B.
<SwitchB> system-view
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] undo ip address
# Display information about the track entry on Switch A.
[SwitchA] display track all
Track ID: 1
State: Negative
Duration: 0 days 0 hours 0 minutes 32 seconds
Notification delay: Positive 0, Negative 0 (in seconds)
Tracked object:
NQA entry: admin test
Reaction: 1
The output shows that the status of the track entry is Negative, indicating that the NQA operation has failed and the master route is unavailable.
# Display the routing table of Switch A.
[SwitchA] display ip routing-table
Routing Tables: Public
Destinations : 10 Routes : 10
Destination/Mask Proto Pre Cost NextHop Interface
10.1.1.0/24 Direct 0 0 10.1.1.1 Vlan2
10.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
10.2.1.0/24 Static 60 0 10.1.1.2 Vlan2
10.3.1.0/24 Direct 0 0 10.3.1.1 Vlan3
10.3.1.1/32 Direct 0 0 127.0.0.1 InLoop0
20.1.1.0/24 Direct 0 0 20.1.1.1 Vlan6
20.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
30.1.1.0/24 Static 80 0 10.3.1.3 Vlan3
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
The output shows that Switch A forwards packets to 30.1.1.0/24 through Switch C. The backup static route has taken effect.
# Verify that the hosts in 20.1.1.0/24 can communicate with the hosts in 30.1.1.0/24 when the master route fails.
[SwitchA] ping -a 20.1.1.1 30.1.1.1
Ping 30.1.1.1: 56 data bytes, press CTRL_C to break
Reply from 30.1.1.1: bytes=56 Sequence=1 ttl=254 time=2 ms
Reply from 30.1.1.1: bytes=56 Sequence=2 ttl=254 time=1 ms
Reply from 30.1.1.1: bytes=56 Sequence=3 ttl=254 time=1 ms
Reply from 30.1.1.1: bytes=56 Sequence=4 ttl=254 time=2 ms
Reply from 30.1.1.1: bytes=56 Sequence=5 ttl=254 time=1 ms
--- Ping statistics for 30.1.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.00% packet loss
round-trip min/avg/max/std-dev = 1/1/2/1 ms
# Verify that the hosts in 30.1.1.0/24 can communicate with the hosts in 20.1.1.0/24 when the master route fails.
[SwitchB] ping -a 30.1.1.1 20.1.1.1
Ping 20.1.1.1: 56 data bytes, press CTRL_C to break
Reply from 20.1.1.1: bytes=56 Sequence=1 ttl=254 time=2 ms
Reply from 20.1.1.1: bytes=56 Sequence=2 ttl=254 time=1 ms
Reply from 20.1.1.1: bytes=56 Sequence=3 ttl=254 time=1 ms
Reply from 20.1.1.1: bytes=56 Sequence=4 ttl=254 time=1 ms
Reply from 20.1.1.1: bytes=56 Sequence=5 ttl=254 time=1 ms
--- Ping statistics for 20.1.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.00% packet loss
round-trip min/avg/max/std-dev = 1/1/2/1 ms
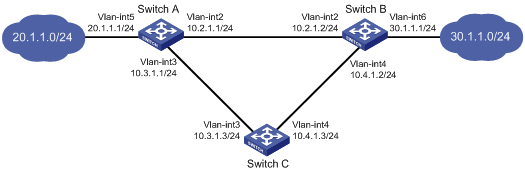
Static routing-Track-BFD collaboration configuration example
Network requirements
As shown in Figure 6:
· Switch A is the default gateway of the hosts in subnet 20.1.1.0/24.
· Switch B is the default gateway of the hosts in subnet 30.1.1.0/24.
· Hosts in the two subnets communicate with each other through static routes.
To ensure network availability, configure route backup and static routing-Track-BFD collaboration on Switch A and Switch B as follows:
· On Switch A, assign a higher priority to the static route to 30.1.1.0/24 with Switch B as the next hop. This route is the master route. The static route to 30.1.1.0/24 with Switch C as the next hop acts as the backup route. When the master route is unavailable, BFD can quickly detect the route failure to make the backup route take effect.
· On Switch B, assign a higher priority to the static route to 20.1.1.0/24 with Switch A as the next hop. This route is the master route. The static route to 20.1.1.0/24 with Switch C as the next hop acts as the backup route. When the master route is unavailable, BFD can quickly detect the route failure to make the backup route take effect.
Configuration procedure
1. Create VLANs and assign ports to them. Configure the IP address of each VLAN interface as shown in Figure 6. (Details not shown.)
2. Configure Switch A:
# Configure a static route to 30.1.1.0/24 with the next hop 10.2.1.2 and the default priority 60, and associate this static route with track entry 1.
<SwitchA> system-view
[SwitchA] ip route-static 30.1.1.0 24 10.2.1.2 track 1
# Configure a static route to 30.1.1.0/24 with the next hop 10.3.1.3 and the priority 80.
[SwitchA] ip route-static 30.1.1.0 24 10.3.1.3 preference 80
# Configure the source address of BFD echo packets as 10.10.10.10.
[SwitchA] bfd echo-source-ip 10.10.10.10
# Configure track entry 1, and associate it with the BFD session to verify the connectivity between Switch A and Switch B.
[SwitchA] track 1 bfd echo interface vlan-interface 2 remote ip 10.2.1.2 local ip 10.2.1.1
3. Configure Switch B:
# Configure a static route to 20.1.1.0/24, with the next hop 10.2.1.1 and the default priority 60, and associate this static route with track entry 1.
<SwitchB> system-view
[SwitchB] ip route-static 20.1.1.0 24 10.2.1.1 track 1
# Configure a static route to 20.1.1.0/24 with the next hop 10.4.1.3 and the priority 80.
[SwitchB] ip route-static 20.1.1.0 24 10.4.1.3 preference 80
# Configure the source address of BFD echo packets as 1.1.1.1.
[SwitchB] bfd echo-source-ip 1.1.1.1
# Configure track entry 1, and associate it with the BFD session to verify the connectivity between Switch B and Switch A.
[SwitchB] track 1 bfd echo interface vlan-interface 2 remote ip 10.2.1.1 local ip 10.2.1.2
4. Configure Switch C:
# Configure a static route to 30.1.1.0/24 with the next hop 10.4.1.2.
<SwitchC> system-view
[SwitchC] ip route-static 30.1.1.0 24 10.4.1.2
# Configure a static route to 20.1.1.0/24 with the next hop 10.3.1.1.
[SwitchB] ip route-static 20.1.1.0 24 10.3.1.1
Verifying the configuration
# Display information about the track entry on Switch A.
[SwitchA] display track all
Track ID: 1
State: Positive
Duration: 0 days 0 hours 0 minutes 32 seconds
Notification delay: Positive 0, Negative 0 (in seconds)
Tracked object:
BFD session mode: Echo
Outgoing interface: Vlan-interface2
Remote IP: 10.2.1.2
Local IP: 10.2.1.1
The output shows that the status of the track entry is Positive, indicating that the next hop 10.2.1.2 is reachable.
# Display the routing table of Switch A.
[SwitchA] display ip routing-table
Destinations : 9 Routes : 9
Destination/Mask Proto Pre Cost NextHop Interface
10.2.1.0/24 Direct 0 0 10.2.1.1 Vlan2
10.2.1.1/32 Direct 0 0 127.0.0.1 InLoop0
10.3.1.0/24 Direct 0 0 10.3.1.1 Vlan3
10.3.1.1/32 Direct 0 0 127.0.0.1 InLoop0
20.1.1.0/24 Direct 0 0 20.1.1.1 Vlan5
20.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
30.1.1.0/24 Static 60 0 10.2.1.2 Vlan2
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
The output shows that Switch A forwards packets to 30.1.1.0/24 through Switch B. The master static route has taken effect.
# Remove the IP address of VLAN-interface 2 on Switch B.
<SwitchB> system-view
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] undo ip address
# Display information about the track entry on Switch A.
[SwitchA] display track all
Track ID: 1
State: Negative
Duration: 0 days 0 hours 0 minutes 32 seconds
Notification delay: Positive 0, Negative 0 (in seconds)
Tracked object:
BFD session mode: Echo
Outgoing interface: Vlan-interface2
VPN instance name: -
Remote IP: 10.2.1.2
Local IP: 10.2.1.1
The output shows that the status of the track entry is Negative, indicating that the next hop 10.2.1.2 is unreachable.
# Display the routing table of Switch A.
[SwitchA] display ip routing-table
Destinations : 9 Routes : 9
Destination/Mask Proto Pre Cost NextHop Interface
10.2.1.0/24 Direct 0 0 10.2.1.1 Vlan2
10.2.1.1/32 Direct 0 0 127.0.0.1 InLoop0
10.3.1.0/24 Direct 0 0 10.3.1.1 Vlan3
10.3.1.1/32 Direct 0 0 127.0.0.1 InLoop0
20.1.1.0/24 Direct 0 0 20.1.1.1 Vlan5
20.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
30.1.1.0/24 Static 80 0 10.3.1.3 Vlan3
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
The output shows that Switch A forwards packets to 30.1.1.0/24 through Switch C and Switch B. The backup static route has taken effect.
# Verify that the hosts in 20.1.1.0/24 can communicate with the hosts in 30.1.1.0/24 when the master route fails.
[SwitchA] ping -a 20.1.1.1 30.1.1.1
Ping 30.1.1.1: 56 data bytes, press CTRL_C to break
Reply from 30.1.1.1: bytes=56 Sequence=1 ttl=254 time=2 ms
Reply from 30.1.1.1: bytes=56 Sequence=2 ttl=254 time=1 ms
Reply from 30.1.1.1: bytes=56 Sequence=3 ttl=254 time=1 ms
Reply from 30.1.1.1: bytes=56 Sequence=4 ttl=254 time=2 ms
Reply from 30.1.1.1: bytes=56 Sequence=5 ttl=254 time=1 ms
--- Ping statistics for 30.1.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.00% packet loss
round-trip min/avg/max/std-dev = 1/1/2/1 ms
# Verify that the hosts in 30.1.1.0/24 can communicate with the hosts in 20.1.1.0/24 when the master route fails.
[SwitchB] ping -a 30.1.1.1 20.1.1.1
Ping 20.1.1.1: 56 data bytes, press CTRL_C to break
Reply from 20.1.1.1: bytes=56 Sequence=1 ttl=254 time=2 ms
Reply from 20.1.1.1: bytes=56 Sequence=2 ttl=254 time=1 ms
Reply from 20.1.1.1: bytes=56 Sequence=3 ttl=254 time=1 ms
Reply from 20.1.1.1: bytes=56 Sequence=4 ttl=254 time=1 ms
Reply from 20.1.1.1: bytes=56 Sequence=5 ttl=254 time=1 ms
--- Ping statistics for 20.1.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.00% packet loss
round-trip min/avg/max/std-dev = 1/1/2/1 ms
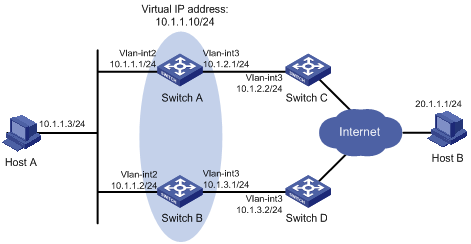
VRRP-Track-interface management collaboration configuration example
Network requirements
As shown in Figure 7:
· Host A requires access to Host B. The default gateway of Host A is 10.1.1.10/24.
· Switch A and Switch B belong to VRRP group 1. The virtual IP address of VRRP group 1 is 10.1.1.10.
Configure VRRP-Track-interface management collaboration to monitor the uplink interface on the master and meet the following requirements:
· When Switch A operates correctly, it forwards packets from Host A to Host B.
· When VRRP detects a fault on the uplink interface of Switch A through the interface management module, Switch B forwards packets from Host A to Host B.
Configuration procedure
1. Create VLANs and assign ports to them. Configure the IP address of each VLAN interface as shown in Figure 7. (Details not shown.)
2. Configure Switch A:
# Configure track entry 1 and associate it with the link status of the uplink interface VLAN-interface 3.
[SwitchA] track 1 interface vlan-interface 3
# Create VRRP group 1 and configure the virtual IP address 10.1.1.10 for the group.
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] vrrp vrid 1 virtual-ip 10.1.1.10
# Set the priority of Switch A to 110 in VRRP group 1.
[SwitchA-Vlan-interface2] vrrp vrid 1 priority 110
# Associate VRRP group 1 with track entry 1 and decrease the router priority by 30 when the state of track entry 1 changes to negative.
[SwitchA-Vlan-interface2] vrrp vrid 1 track 1 priority reduced 30
3. On Switch B, create VRRP group 1 and configure the virtual IP address 10.1.1.10 for the group.
<SwitchB> system-view
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] vrrp vrid 1 virtual-ip 10.1.1.10
Verifying the configuration
# Ping Host B from Host A to verify that Host B is reachable. (Details not shown.)
# Display detailed information about VRRP group 1 on Switch A.
[SwitchA-Vlan-interface2] display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 0
Auth Type : None
Virtual IP : 10.1.1.10
Virtual MAC : 0000-5e00-0101
Master IP : 10.1.1.1
VRRP Track Information:
Track Object : 1 State : Positive Pri Reduced : 30
# Display detailed information about VRRP group 1 on Switch B.
[SwitchB-Vlan-interface2] display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 0
Become Master : 2200ms left
Auth Type : None
Virtual IP : 10.1.1.10
Master IP : 10.1.1.1
The output shows that in VRRP group 1, Switch A is the master, and Switch B is a backup. Switch A forwards packets from Host A to Host B.
# Shut down the uplink interface VLAN-interface 3 on Switch A.
[SwitchA-Vlan-interface2] interface vlan-interface 3
[SwitchA-Vlan-interface3] shutdown
# Ping Host B from Host A to verify that Host B is reachable. (Details not shown.)
# Display detailed information about VRRP group 1 on Switch A.
[SwitchA-Vlan-interface3] display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 110 Running Pri : 80
Preempt Mode : Yes Delay Time : 0
Become Master : 2200ms left
Auth Type : None
Virtual IP : 10.1.1.10
Master IP : 10.1.1.2
VRRP Track Information:
Track Object : 1 State : Negative Pri Reduced : 30
# Display detailed information about VRRP group 1 on Switch B.
[SwitchB-Vlan-interface2] display vrrp verbose
IPv4 Virtual Router Information:
Running Mode : Standard
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 0
Auth Type : None
Virtual IP : 10.1.1.10
Virtual MAC : 0000-5e00-0101
Master IP : 10.1.1.2
The output shows that Switch A becomes the backup, and Switch B becomes the master. Switch B forwards packets from Host A to Host B.
Smart Link-Track-CFD collaboration configuration example
For information about the Smart Link-Track-CFD collaboration configuration example, see "Configuring Smart Link."

