- Table of Contents
-
- 12-High Availability Configuration Guide
- 00-Preface
- 01-High Availability Overview
- 02-Active and Standby Switchover Configuration
- 03-Ethernet OAM Configuration
- 04-CFD Configuration
- 05-DLDP Configuration
- 06-RPR Configuration
- 07-RRPP Configuration
- 08-Smart Link Configuration
- 09-Monitor Link Configuration
- 10-VRRP Configuration
- 11-BFD Configuration
- 12-Track Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 10-VRRP Configuration | 630.32 KB |
Contents
VRRP application (taking IPv4-based VRRP for example)
Assigning virtual MAC addresses
Configuration restrictions and guidelines
VRRP for IPv4 configuration task list
Configuring a VRRP working mode
Specifying the type of MAC addresses mapped to virtual IP addresses
Creating a VRRP group and configuring virtual IP address
Configuring router priority, preemptive mode and tracking function
Configuring VRRP packet attributes
Enabling the trap function for VRRP
Displaying and maintaining VRRP for IPv4
VRRP for IPv6 configuration task list
Specifying the type of MAC addresses mapped to virtual IPv6 addresses
Creating a VRRP group and configuring a virtual IPv6 address
Configuring router priority, preemptive mode and tracking function
Configuring VRRP packet attributes
Displaying and maintaining VRRP for IPv6
IPv4-based VRRP configuration examples
Single VRRP group configuration example
VRRP interface tracking configuration example
VRRP with multiple VLANs configuration example
VRRP load balancing mode configuration example
IPv6-based VRRP configuration examples
Single VRRP group configuration example
VRRP interface tracking configuration example
VRRP with multiple VLANs configuration example
VRRP load balancing mode configuration example
The screen frequently displays error prompts
The term router in this document refers to both routers and Layer 3 switches.
VRRP overview
Typically, as shown in Figure 1, you can configure a default route with the gateway as the next hop for every host on a network segment. All packets destined to other network segments are sent over the default route to the gateway, which then forwards the packets. However, when the gateway fails, all the hosts that use the gateway as the default next-hop router fail to communicate with external networks.
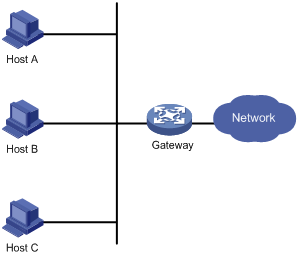
Configuring a default route for network hosts facilitates your configuration, but also requires high performance stability of the device that acts as the gateway. Using more egress gateways is a common way to improve system reliability, but introduces the problem of routing among the egresses.
Virtual Router Redundancy Protocol (VRRP) is designed to address this problem. VRRP adds a group of routers that can act as network gateways to a VRRP group, which forms a virtual router. Routers in the VRRP group elect a master through the VRRP election mechanism to act as a gateway, and hosts on a LAN only need to configure the virtual router as their default network gateway.
VRRP is an error-tolerant protocol, which improves the network reliability and simplifies configurations on hosts. On a multicast and broadcast LAN such as Ethernet, VRRP provides highly reliable default links without configuration changes (such as dynamic routing protocols, route discovery protocols) when a router fails, and prevent network interruption due to a single link failure.
VRRP operates in either of the following modes:
· Standard protocol mode—Includes two versions VRRPv2 and VRRPv3. IPv4 VRRPv2 is based on RFC 2338. IPv6 VRRPv2 is based on RFC 3768. VRRPv3 is based on RFC 5798. For more information, see "VRRP standard protocol mode."
· Load balancing mode—Extends the standard protocol mode and realizes load balancing. For more information, see "VRRP load balancing mode."
VRRP standard protocol mode
Introduction to VRRP group
VRRP combines a group of routers (including a master and multiple backups) on a LAN into a virtual router called VRRP group.
A VRRP group has the following features:
· A virtual router has a virtual IP address. A host on the LAN only needs to know the IP address of the virtual router and uses the IP address as the next hop of the default route.
· Every host on the LAN communicates with external networks through the virtual router.
· Routers in the VRRP group elect a master that acts as the gateway according to their priorities. The other routers function as the backups. When the master fails, to make sure that the hosts in the network segment can uninterruptedly communicate with the external networks, the backups in the VRRP group elect a new gateway to undertake the responsibility of the failed master.
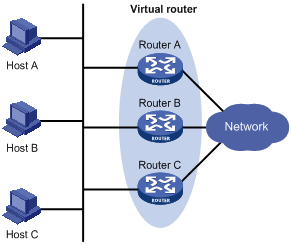
As shown in Figure 2, Router A, Router B, and Router C form a virtual router, which has its own IP address. Hosts on the Ethernet use the virtual router as the default gateway.
The router with the highest priority among the three routers is elected as the master to act as the gateway, and the other two are backups.
|
|
NOTE: · The IP address of the virtual router can be either an unused IP address on the segment where the VRRP group resides or the IP address of an interface on a router in the VRRP group. In the latter case, the router is called the IP address owner. · Only one IP address owner can be configured for a VRRP group. · Status of a router in a VRRP group includes master, backup, and initialize. |
VRRP priority
VRRP determines the role (master or backup) of each router in a VRRP group by priority. A router with a higher priority is more likely to become the master.
VRRP priority is in the range of 0 to 255. The greater the number, the higher the priority. Priorities 1 to 254 are configurable. Priority 0 is reserved for special uses and priority 255 for the IP address owner. When a router acts as the IP address owner, its running priority is always 255. That is, the IP address owner in a VRRP group acts as the master as long as it works correctly.
Working mode
A router in a VRRP group operates in either of the following modes:
· Non-preemptive mode—When a router in the VRRP group becomes the master, it stays as the master as long as it operates correctly, even if a backup is assigned a higher priority later.
· Preemptive mode—When a backup finds its priority higher than that of the master, the backup sends VRRP advertisements to start a new master election in the VRRP group and becomes the master. Accordingly, the original master becomes a backup.
Authentication mode
To avoid attacks from unauthorized users, VRRP adds authentication keys into packets for authentication. VRRP provides the following authentication modes:
· simple—Simple text authentication
A router sending a packet fills an authentication key into the packet, and the router receiving the packet compares its local authentication key with that of the received packet. If the two authentication keys are the same, the received VRRP packet is considered legitimate. Otherwise, the received packet is considered invalid.
· md5—MD5 authentication
A router computes the digest of a packet to be sent by using the authentication key and MD5 algorithm and saves the result in the authentication header. The router that receives the packet performs the same operation by using the authentication key and MD5 algorithm, and compares the result with the content in the authentication header. If the results are the same, the router that receives the packet considers the packet an authentic and valid VRRP packet. Otherwise, the router considers the packet invalid.
On a secure network, you can choose not to set the authentication mode.
VRRP timers
VRRP timers include VRRP advertisement interval timer and VRRP preemption delay timer.
VRRP advertisement interval timer
The master in a VRRP group periodically sends VRRP advertisements to inform the other routers in the VRRP group that it operates correctly.
You can adjust the interval for sending VRRP advertisements by setting the VRRP advertisement interval timer. If a backup receives no advertisements in a period three times the interval, the backup regards itself as the master and sends VRRP advertisements to start a new master election.
VRRP preemption delay timer
To avoid frequent state changes among members in a VRRP group and provide the backups enough time to collect information (such as routing information), each backup waits for a period of time (the preemption delay time) after it receives an advertisement with the priority lower than the local priority, then sends VRRP advertisements to start a new master election in the VRRP group and becomes the master.
Packet format
The master multicasts VRRP packets periodically to declare its existence. VRRP packets are also used for checking the parameters of the virtual router and electing the master.
VRRP packets are encapsulated in IP packets, with the protocol number being 112. Figure 3 shows the format of an IPv4 VRRPv2 packet. Figure 4 shows the format of an IPv6 VRRPv2 packet. Figure 5 shows the format of an IPv4/IPv6 VRRPv3 packet.
Figure 3 Format of an IPv4 VRRPv2 packet
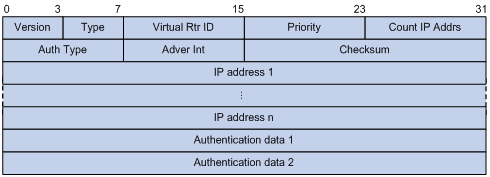
Figure 4 Format of an IPv6 VRRPv2 packet
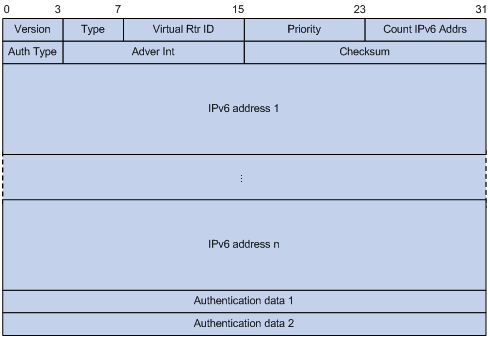
Figure 5 Format of an IPv4/IPv6 VRRPv3 packet
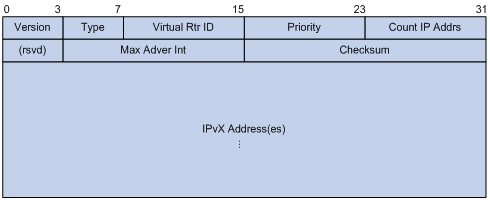
A VRRP packet comprises the following fields:
· Version—Version number of the protocol, 2 for IPv4 VRRPv2 and 3 for other versions.
· Type—Type of the VRRP packet. Only one VRRP packet type is present, that is, VRRP advertisement, which is represented by 1.
· Virtual Rtr ID (VRID)—ID of the virtual router, that is, ID of the VRRP group. It ranges from 1 to 255.
· Priority—Priority of the router in the VRRP group, in the range 0 to 255. A greater value represents a higher priority.
· Count IP Addrs/Count IPv6 Addrs—Number of virtual IPv4 or IPv6 addresses for the VRRP group. A VRRP group can have multiple virtual IPv4 or IPv6 addresses.
· Auth Type—Authentication type. For IPv4 VRRPv2, 0 means no authentication, 1 means simple text authentication, and 2 means MD5 authentication. For IPv6 VRRPv2, 0 means no authentication, 1 means simple text authentication, and MD5 authentication is not supported. For IPv4/IPv6 VRRPv3, authentication is not supported and this field is reserved.
· Adver Int—Interval for sending advertisement packets. For IPv4 VRRPv2, the interval is in seconds and defaults to 1. For other VRRP versions, the interval is in centiseconds and defaults to 100.
· Checksum—16-bit checksum for validating the data in VRRP packets.
· IP Address/IPv6 Address—Virtual IPv4 or IPv6 address entry of the VRRP group. The Count IP Addrs or Count IPv6 Addrs field defines the number of the virtual IPv4 or IPv6 addresses.
· Authentication Data—Authentication key. This field is used only for simple authentication and is 0 for any other authentication modes. This field is not available for IPv4/IPv6 VRRPv3 packets.
VRRP principles
· Routers in a VRRP group determine their roles by priority. The router with the highest priority is the master, and the others are the backups. The master periodically sends VRRP advertisements to notify the backups that it is working correctly, and each of the backups starts a timer to wait for advertisements from the master.
· In preemptive mode, when a backup receives a VRRP advertisement, it compares the priority in the packet with its own priority. If the priority of the backup is higher, the backup becomes the master. Otherwise, it remains as a backup. With the preemptive mode, a VRRP group always has a router with the highest priority as the master for packet forwarding.
· In non-preemptive mode, a router in the VRRP group remains as a master or backup as long as the master does not fail. A backup does not become the master even if it is configured with a higher priority. The non-preemptive mode helps avoid frequent switchover between the master and backups.
· If the timer of a backup expires but the backup still does not receive any VRRP advertisement, it considers that the master fails. In this case, the backup considers itself as the master and sends VRRP advertisements to start a new master election.
|
|
NOTE: · The VRRP group configuration might be different on routers, and network problems might exist, so multiple master routers might exist in one VRRP group. These master routers will elect one master according to their priorities and IP addresses. The router with the highest priority wins the election. If a tie exists in the priority, the router with the highest IP address wins. · After a backup router receives an advertisement, it compares its priority against that carried in the advertisement. If its priority is higher than that carried in the advertisement, it takes over the master. |
VRRP tracking
|
|
IMPORTANT: To enable the VRRP tracking function, configure the routers in the VRRP group to operate in preemptive mode first, so that only the router with the highest priority can always operate as the master for packet forwarding. |
Tracking a specified interface
The interface tracking function expands the backup functionality of VRRP. It provides backup not only when the interface to which a VRRP group is assigned fails but also when other interfaces (such as uplink interfaces) on the router become unavailable.
· If the uplink interface of a router in a VRRP group fails, usually the VRRP group cannot be aware of the uplink interface failure. If the router is the master of the VRRP group, hosts on the LAN are not able to access external networks because of the uplink failure. This problem can be solved by tracking a specified uplink interface. If the tracked uplink interface is down or removed, the priority of the master is automatically decreased by a specified value and a higher priority router in the VRRP group becomes the master.
Tracking a track entry
By monitoring a track entry, you can:
· Monitor an uplink and change the priority of the router according to the state of the uplink. If the uplink fails, hosts in the LAN cannot access external networks through the router. In this case, the state of the monitored track entry is negative and the priority of the router decreases by a specified value. Then, a higher priority router in the VRRP group becomes the master to maintain the proper communication between the hosts in the LAN and external networks.
· Monitor the master on a backup. When the master fails, the backup immediately preempts as the master to maintain normal communication.
For more information about track entries, see "Configuring Track."
VRRP application (taking IPv4-based VRRP for example)
Master/backup
In master/backup mode, only the master forwards packets. When the master fails, a new master is elected from the backups. This mode requires only one VRRP group, in which each router holds a different priority and the one with the highest priority becomes the master, as shown in Figure 6.
Figure 6 VRRP in master/backup mode
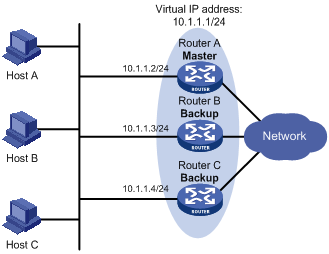
Assume that Router A is the master and therefore can forward packets to external networks, whereas Router B and Router C are backups and are thus in the state of listening. If Router A fails, Router B and Router C elect for a new master to forward packets to hosts on the LAN.
Load sharing
More than one VRRP group can be created on an interface of a router to allow the router to be the master of one VRRP group but a backup of another at the same time.
In load sharing mode, multiple routers provide services simultaneously. This mode requires two or more VRRP groups, each of which comprises a master and one or more backups. The masters of the VRRP groups are assumed by different routers, as shown in Figure 7.
Figure 7 VRRP in load sharing mode
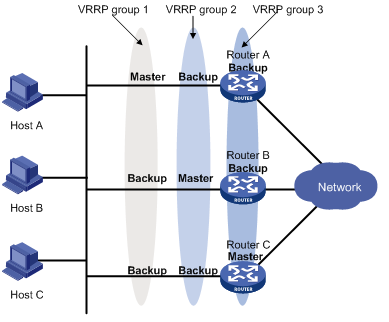
A router can be in multiple VRRP groups and hold a different priority in a different group.
As shown in Figure 7, the following VRRP groups are present:
· VRRP group 1—Router A is the master; Router B and Router C are the backups.
· VRRP group 2—Router B is the master; Router A and Router C are the backups.
· VRRP group 3—Router C is the master; Router A and Router B are the backups.
For load sharing among Router A, Router B, and Router C, hosts on the LAN need to be configured to use VRRP group 1, 2, and 3 as the default gateways. When you configure VRRP priorities, make sure that each router holds such a priority in each VRRP group that it will take the expected role in the group.
VRRP load balancing mode
Overview
In a standard-mode VRRP group, only the master can forward packets and the backups are in listening state. You can create multiple VRRP groups to share load, but must assign different gateways to the hosts on the LAN.
Load balancing mode simplifies configuration and improves forwarding efficiency. In load balancing mode, a VRRP group maps its virtual IP address to multiple virtual MAC addresses: one virtual MAC address for each group member. The master uses these virtual MAC addresses of the member routers to respond to IPv4 ARP requests or IPv6 ND requests from hosts. Therefore, every router in this VRRP group can forward traffic and traffic from hosts is distributed across the VRRP group members.
VRRP load balancing mode is based on VRRP standard protocol mode, so mechanisms, such as master election, preemption, and tracking functions, in the standard protocol mode are also supported in the load balancing mode. In addition, VRRP load balancing mode has new mechanisms, which are introduced in the following sections.
|
|
NOTE: To configure the VRRP load balancing function in IRF mode, you must configure the bridge MAC address to be permanently preserved (default setting). For more information about IRF mode, see IRF Configuration Guide. |
Assigning virtual MAC addresses
When VRRP is operating in load balancing mode, the master assigns virtual MAC addresses to the routers in the VRRP group and answers the ARP requests or ND requests from different hosts. The backup routers, however, do not answer the ARP requests or ND requests from the hosts.
In an IPv4 network, a load-balanced VRRP group works as follows:
1. The master assigns virtual MAC addresses to the routers (including the master itself and the backups) in the VRRP group. For example, as shown in Figure 8, the virtual IP address of the VRRP group is 10.1.1.1/24; Router A is the master; Router B and Router C are the backups. Router A assigns 000f-e2ff-0011 to itself, and 000f-e2ff-0012 to Router B.
Figure 8 Allocating virtual MAC addresses
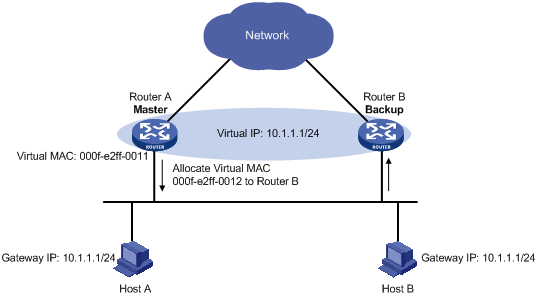
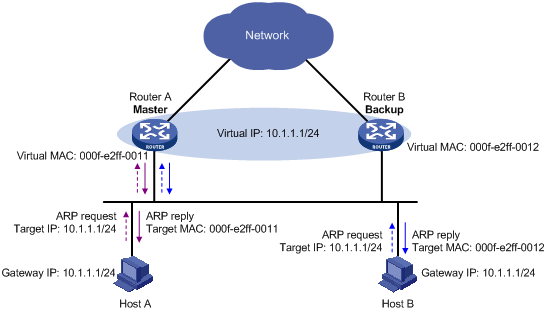
2. After receiving an ARP request destined for the virtual IP address of the VRRP group from a host, the master, based on the load balancing algorithm, uses a corresponding virtual MAC address to answer the ARP request. For example, as shown Figure 9, when Host A sends an ARP request to retrieve the MAC address of gateway 10.1.1.1, the master (Router A), after receiving the request, returns the virtual MAC address of Router A to Host A; when Host B sends an ARP request to retrieve the MAC address of gateway 10.1.1.1, the master (Router A), after receiving the request, returns the virtual MAC address of Router B to Host B.
Figure 9 Answering ARP requests
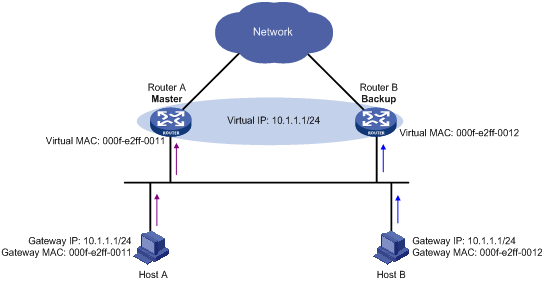
3. Different hosts send packets to different routers according to the requested virtual MAC addresses. For example, as shown in Figure 10, Host A regards the virtual MAC address of Router A as the gateway MAC address, so it sends packets to Router A for forwarding; Host B regards the virtual MAC address of Router B as the gateway MAC address, so it sends packets to Router B for forwarding.
Figure 10 Sending packets to different routers for forwarding
Virtual forwarder
Creating a virtual forwarder
Virtual MAC addresses help different hosts transmit packets to different routers in a VRRP group. To enable the routers in the VRRP group to forward the packets, be sure to create virtual forwarders (VFs) on the routers. Each VF associates with a virtual MAC address in the VRRP group and forwards packets destined to this virtual MAC address.
The following describes how VFs are created on the routers in a VRRP group:
1. The master assigns virtual MAC addresses to all routers in the VRRP group. After learning its virtual MAC address, a router in the VRRP group creates a VF that corresponds to this MAC address, and becomes the owner of this VF.
2. The router advertises the VF information to the other routers in the VRRP group.
3. After receiving the VF advertisement, each of the other routers creates the advertised VF.
As described in the preceding steps, each router in the VRRP group creates not only a VF corresponding to its virtual MAC address, but also VFs advertised by the other routes in the VRRP group.
VF weight and priority
The weight of a VF indicates the forwarding capability of a router. A higher weight indicates a higher forwarding capability. When the weight is lower than the lower limit of failure, the router cannot be capable of forwarding packets for the hosts.
The priority of a VF determines the VF state. Among the VFs that correspond to the same virtual MAC address on different routers in the VRRP group, the VF with the highest priority is in the active state and is known as the active virtual forwarder (AVF), which forwards packets; other VFs are in the listening state and are known as the listening virtual forwarders (LVFs), which monitor the state of the AVF. The priority value of a VF ranges from 0 to 255, where 255 is reserved for the VF owner. If the weight of a VF owner is higher than or equal to the lower limit of failure, the priority value of the VF owner is 255.
The priority value of a VF is calculated based on its weight:
· If the weight of a VF is higher than or equal to the lower limit of failure, and the router where the VF resides is the owner of the VF, the priority value of the VF is 255.
· If the weight of a VF is higher than or equal to the lower limit of failure, but the router where the VF resides is not the owner of the VF, the priority value of the VF is weight/(number of local AVFs +1)
· If the weight of a VF is lower than the lower limit of failure, the priority value of the VF is 0.
VF backup
The VFs corresponding to a virtual MAC address on different routers in the VRRP group back up one another.
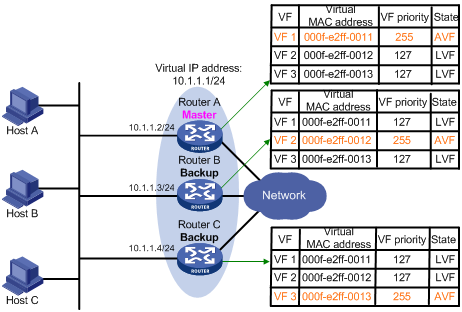
Figure 11 illustrates the VF information on each router in the VRRP group and how the routers back up one another. The master, Router A, assigns virtual MAC addresses 000f-e2ff-0011, 000f-e2ff-0012, and 000f-e2ff-0013 to itself, Router B, and Router C, respectively. The VFs corresponding to these three virtual MAC addresses, VF 1, VF 2, and VF 3, are created on each of the three routers, and the VFs corresponding to the same virtual MAC address on different routers back up one another. For example, VF 1 on Router A, Router B, and Router C can implement backup.
· Router A is the owner of VF 1, and the priority value of VF 1 on Router A is 255. In this case, VF 1 on Router A acts as the AVF to forward the packets destined for virtual MAC address 000f-e2ff-0011.
· The priority value of VF 1 on Router B and Router C is weight/(number of local AVFs + 1), that is, 255/(1 + 1) =127, which is lower than that of VF 1 on Router A. In this case, VF 1 on both Router B and Router C acts as the LVF to listen to the status of VF 1 on Router A.
· When VF 1 on Router A fails, VF 1 on Router B and Router C elects the one with a higher priority value as the new AVF, responsible for forwarding the packets destined for virtual MAC address 000f-e2ff-0011.
|
|
NOTE: A VF always operates in preemptive mode. When an LVF finds its priority value higher than that in the advertisement sent by the AVF, the LVF declares itself as the AVF. |
VF timers
When the AVF on a router fails, the newly elected AVF on another router creates a redirect timer and a timeout timer for the failed AVF.
· Redirect timer—Before this timer times out, the master still uses the virtual MAC address corresponding to the failed AVF to respond to ARP/ND requests from the hosts, and the VF owner can share traffic load if the VF owner resumes normal operation within this time. When this timer times out, the master stops using the virtual MAC address corresponding to the failed AVF to respond to ARP/ND requests from the hosts.
· Timeout timer—The duration that the new AVF takes over the VF owner. Before this timer times out, all the routers in the VRRP group keep the failed AVF, and the new AVF forwards the packets destined for the virtual MAC address corresponding to the failed AVF. When this timer times out, all the routers in the VRRP group remove the failed AVF, and the new AVF stops forwarding the packets destined for the virtual MAC address corresponding to the failed AVF.
VF tracking
The AVF forwards packets destined to the MAC address of the AVF. If the uplink of the AVF fails and no LVF is notified to take over the AVF role, hosts (on the LAN) that use the MAC address of the AVF as their gateway MAC address cannot access the external network.
This problem can be solved by the VF tracking function. You can monitor the uplink state by using network quality analyzer (NQA) and bidirectional forwarding detection (BFD), and establish the collaboration between the VF and the NQA or between the VF and the BFD through the tracking function. When the uplink fails, the state of the monitored track entry changes to negative and the weight of the VF decreases by a specified value. Then, the VF with a higher priority becomes the AVF and forwards packets.
The VF tracking function can also work on an LVF to monitor its corresponding AVF on another router. When the AVF fails, the LVF immediately takes over the AVF to ensure uninterrupted network communications.
Packet types
VRRP standard protocol mode defines only VRRP advertisement. Only the master in a VRRP group periodically sends VRRP advertisements, and the backups do not send VRRP advertisements.
VRRP load balancing mode defines the following types of packets:
· Advertisement—VRRP advertises VRRP group state and information about the VF that is in the active state. Both the master and the backups periodically send VRRP advertisements.
· Request—If a backup is not the VF owner, it sends a request to ask the master to assign a virtual MAC address.
· Reply—When receiving a request, the master sends a reply to the backup router to assign a virtual MAC address. After receiving the reply, the backup router creates a VF that corresponds to the virtual MAC address, and then becomes the owner of this VF.
· Release—When a VF owner fails, the router that takes over its responsibility sends a release after a specified period of time to notify the other routers in the VRRP group to delete the VF of the failed VF owner.
The format of these packets is similar to that of the advertisement in VRRP standard protocol mode except that a packet used in load balancing mode is appended with the option field, which contains information for load balancing.
In load balancing mode, the value of the version field is 8 for IPv4 VRRPv2 packets, 9 for IPv6 VRRPv2 packets, and 3 for IPv4/IPv6 VRRPv3 packets.
Configuration restrictions and guidelines
The interfaces that VRRP involves can be only Layer 3 Ethernet interfaces, VLAN interfaces, Layer 3 aggregate interfaces, and RPR logical interfaces unless otherwise specified.
VRRP cannot be configured on interfaces of aggregation groups.
Specifying a VRRP version
The version of VRRP on all routers in a VRRP group must be the same.
When the VRRP version of an interface is IPv4/IPv6 VRRPv3, the authentication configuration of the VRRP group does not take effect, and the maximum VRRP advertisement interval is 40 seconds (even if you configure an interval larger than 40 seconds).
To specify a VRRP version:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Specify the VRRP version on the interface. |
vrrp version version-number |
By default, VRRPv2 is used. |
Configuring VRRP for IPv4
VRRP for IPv4 configuration task list
To form a VRRP group, perform the following configurations on each device in the VRRP group.
Complete these tasks to configure VRRP for IPv4:
|
Task |
Remarks |
|
Optional. |
|
|
Specifying the type of MAC addresses mapped to virtual IP addresses |
Optional. This configuration does not apply to VRRP load balancing mode. |
|
Required. |
|
|
Configuring router priority, preemptive mode and tracking function |
Optional. |
|
Optional. The VF tracking function applies to only VRRP load balancing mode. |
|
|
Optional. |
|
|
Optional. |
Configuring a VRRP working mode
VRRP can operate in either of the following modes:
· Standard protocol mode—When VRRP is operating in this mode, only the master in a VRRP group is responsible for forwarding packets.
· Load balancing mode—When VRRP is operating in this mode, all the routers (master and backups) that have the AVF in a VRRP group can forward packets, thus implementing load balancing.
After the VRRP working mode is specified on a router, all VRRP groups on the router operate in the specified working mode.
To configure a VRRP working mode:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the VRRP working mode. |
· Configure VRRP to operate in standard protocol mode: · Configure VRRP to operate in load balancing
mode: |
Use either command. By default, VRRP operates in standard protocol mode. |
Specifying the type of MAC addresses mapped to virtual IP addresses
|
|
IMPORTANT: · Specify the type of the MAC addresses mapped to the virtual IP addresses before creating a VRRP group. Otherwise, you cannot change the type of the MAC addresses mapped to virtual IP addresses. · If VRRP groups with the same ID are created on multiple interfaces of a device, and the VRRP advertisements of these VRRP groups will be sent through QinQ networks, H3C recommends that you map the real MAC addresses of the interfaces to the virtual IP addresses of these VRRP groups. Otherwise, the VRRP advertisements of these VRRP groups cannot be sent successfully. |
After you specify the type of MAC addresses mapped to the virtual IP addresses of VRRP groups and create a VRRP group, the master in the VRRP group uses the specified type of MAC address as the source MAC address for sending packets and uses the specified type of MAC address to answer ARP requests from hosts so that the hosts in the internal network can learn the mapping between the IP address and the MAC address.
The following types of MAC addresses are available to be mapped to the virtual IP address of a VRRP group:
· Virtual MAC address—By default, a virtual MAC address is automatically created for a VRRP group when the VRRP group is created, and the virtual IP address of the VRRP group is mapped to the virtual MAC address. When such a mapping is adopted, the hosts in the internal network do not need to update the mapping between the IP address and MAC address when the master changes.
· Real MAC address of an interface—In case that an IP address owner exists in a VRRP group, if the virtual IP address is mapped to the virtual MAC address, two MAC addresses are mapped to one IP address. To avoid such as problem, map the virtual IP address of the VRRP group to the real MAC address of an interface to forward the packets from a host to the IP address owner.
To specify the type of MAC addresses mapped to virtual IP addresses:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify the type of MAC addresses mapped to virtual IP addresses. |
vrrp method { real-mac | virtual-mac } |
Optional. Virtual MAC address by default. |
|
|
NOTE: When VRRP is operating in load balancing mode, a virtual IP address is always mapped to a virtual MAC address regardless of which type of MAC addresses are specified to be mapped to virtual IP addresses. |
Creating a VRRP group and configuring virtual IP address
|
|
IMPORTANT: Do not create VRRP groups on the VLAN interface of a super VLAN. Otherwise, network performance might be affected. |
When creating a VRRP group on an interface, configure a virtual IP address for the VRRP group. If the interface connects to multiple sub-networks, you can configure multiple virtual IP addresses for the VRRP group to realize router backup on different sub-networks.
A VRRP group is automatically created when you specify the first virtual IP address for the VRRP group. If you specify another virtual IP address for the VRRP group later, the virtual IP address is added to the virtual IP address list of the VRRP group.
Configuration prerequisites
Before creating a VRRP group and configuring a virtual IP address on an interface, configure an IP address for the interface and make sure that it is in the same network segment as the virtual IP address to be configured.
Configuration guidelines
When you create a VRRP group and configure a virtual IP address, follow these guidelines:
· When VRRP is operating in standard protocol mode, the virtual IP address of a VRRP group can be either an unused IP address on the segment where the VRRP group resides or the IP address of an interface on a router in the VRRP group. In the latter case, the router is called the IP address owner.
· When a router is the IP address owner in a VRRP group, H3C recommends not using the IP address of the interface (virtual IP address of the VRRP group) to establish a neighbor relationship with the adjacent router, which means not using the network command to enable OSPF on the interface. For more information about network command, see Layer 3—IP Routing Command Reference.
· When VRRP is operating in load balancing mode, the virtual IP address of a VRRP group cannot be the same as the IP address of any interface in the VRRP group. In other words, in load balancing mode, the VRRP group does not have an IP address owner.
· You can create up to 16 VRRP groups on an interface and assign up to 16 virtual IP addresses in a VRRP group.
· A VRRP group is removed after you remove all the virtual IP addresses configured for it. In addition, configurations on that VRRP group do not take effect any longer.
· Removal of the VRRP group on the IP address owner causes IP address collision. To solve the collision, modify the IP address of the interface on the IP address owner first and then remove the VRRP group from the interface.
· The virtual IP address of a VRRP group cannot be 0.0.0.0, 255.255.255.255, loopback addresses, non class A/B/C addresses or other illegal IP addresses such as 0.0.0.1.
· A VRRP group operates correctly only when the configured virtual IP address and the interface IP address belong to the same segment and are legal host addresses. If the configured virtual IP address and the interface IP address do not belong to the same network segment, or the configured IP address is the network address or network broadcast address of the network segment to which the interface IP address belongs, the state of the VRRP group is always initialize though you can perform the configuration successfully. In this case, VRRP does not take effect.
· If the virtual IP addresses are mapped to virtual MAC addresses, the VRRP group configuration does not take effect on Layer 3 RPR logical interfaces.
Configuration procedure
To create a VRRP group and configure a virtual IP address:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter the specified interface view. |
interface interface-type interface-number |
N/A |
|
3. Create a VRRP group and configure a virtual IP address for the VRRP group. |
vrrp vrid virtual-router-id virtual-ip virtual-address |
VRRP group is not created by default. |
Configuring router priority, preemptive mode and tracking function
Configuration prerequisites
Before you configure router priority, preemptive mode and tracking function, create a VRRP group on an interface and configure a virtual IP address for it.
Configuration guidelines
When you configure router priority, preemptive mode and the tracking function, follow these guidelines:
· The running priority of an IP address owner is always 255 and you do not need to configure it. An IP address owner always operates in preemptive mode.
· If you configure an interface to be tracked or a track entry to be monitored on a router that is the IP address owner in a VRRP group, the configuration does not take effect. If the router is not the IP address owner in the VRRP group later, the configuration takes effect.
· The tracked interface can be a Layer 3 Ethernet interface, a VLAN interface, a Layer 3 aggregate interface, a POS interface, an HDLC link bundle interface, or an RPR logical interface.
· If the state of a tracked interface changes from down or removed to up, the priority of the router where the interface resides is automatically restored.
· If the state of a track entry changes from negative or invalid to positive, the priority of the router where the track entry is configured is automatically restored.
Configuration procedure
By configuring router priority, preemptive mode, interface tracking, or a track entry, you can determine which router in the VRRP group serves as the master.
To configure router priority, preemptive mode and the tracking function:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure router priority in the VRRP group. |
vrrp vrid virtual-router-id priority priority-value |
Optional. 100 by default. |
|
4. Configure the router in the VRRP group to operate in preemptive mode and configure preemption delay. |
vrrp vrid virtual-router-id preempt-mode [ timer delay delay-value ] |
Optional. The router in the VRRP group operates in preemptive mode and the preemption delay is 0 seconds by default. |
|
5. Configure the interface to be tracked. |
vrrp vrid virtual-router-id track interface interface-type interface-number [ reduced priority-reduced ] |
Optional. No interface is being tracked by default. |
|
6. Configure VRRP to track a specified track entry. |
vrrp vrid virtual-router-id track track-entry-number [ reduced priority-reduced | switchover ] |
Optional. Not configured by default. |
Configuring VF tracking
Configuration prerequisites
Before you configure the VF tracking function, create a VRRP group and configure a virtual IP address for it.
Configuration guidelines
When you configure VF tracking, follow these guidelines:
· You can configure the VF tracking function when VRRP is operating in either standard protocol mode or load balancing mode. However, the VF tracking function is effective only when VRRP is operating in load balancing mode.
· By default, the weight of a VF is 255, and its lower limit of failure is 10.
· If the weight of a VF owner is higher than or equal to the lower limit of failure, the priority of the VF owner is always 255 and does not change with the weight value. Therefore, in case of an uplink failure, another VF takes over the VF owner's work and becomes the AVF only when the weight of the VF owner decreases by a correctly specified value and becomes lower than the lower limit of failure. In other words, the weight of the VF owner decreases by more than 245.
Configuration procedure
Assume that VRRP is operating in load balancing mode, and you have configured the VF tracking function to monitor the track entry and specified the value by which the weight decreases. When the status of the track entry becomes negative, the weight values of all VFs on the router decrease by the specified value. When the status of the track entry becomes positive or invalid, the weight values of all VFs on the router restore their original values.
If you configure the VF tracking function on an LVF to monitor its corresponding AVF on a specified router, the LVF can take over the AVF immediately when the status of the track entry becomes negative, to ensure uninterrupted network communications.
To configure VF tracking:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter the specified interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure VF tracking. |
· Configure the VF tracking function to monitor
a specified track entry and specify the value by which the weight decreases: · Configure the VF tracking function to monitor an
AVF on a specified router: |
Use either method. The VF tracking function is not configured by default. |
Configuring VRRP packet attributes
Configuration prerequisites
Before you configure the relevant attributes of VRRP packets, create a VRRP group and configure a virtual IP address for it.
Configuration guidelines
When you configure VRRP packet attributes, follow these guidelines:
· You might configure different authentication modes and authentication keys for the VRRP groups on an interface. However, the members of the same VRRP group must use the same authentication mode and authentication key.
· Excessive traffic might cause a backup to trigger a change of its status because the backup does not receive any VRRP advertisements for a specified period of time. To solve this problem, prolong the time interval to send VRRP advertisements.
· Configuring different intervals for sending VRRP advertisements on the routers in a VRRP group might cause a backup to trigger a change of its status because the backup does not receive any VRRP advertisements for a specified period of time. To solve this problem, configure the same interval for sending VRRP advertisements on each router in the VRRP group.
Configuration procedure
To configure VRRP packet attributes:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter the specified interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the authentication mode and authentication key when the VRRP groups send and receive VRRP packets. |
vrrp vrid virtual-router-id authentication-mode { md5 | simple } [ cipher ] key |
Optional. Authentication is not performed by default. |
|
4. Configure the time interval for the master in the VRRP group to send VRRP advertisements. |
vrrp vrid virtual-router-id timer advertise adver-interval |
Optional. 1 second by default. |
|
5. Disable TTL check on VRRP packets. |
vrrp un-check ttl |
Optional. Enabled by default. You do not need to create a VRRP group before executing this command. |
Enabling the trap function for VRRP
When the trap function is enabled for VRRP, VRRP generates traps with severity level errors to report its key events. The traps are sent to the information center of the device, where you can configure whether to output the trap information and the output destination. For information about how to configure the information center, see Network Management and Monitoring Configuration Guide.
To enable the trap function for VRRP:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the trap function for VRRP. |
snmp-agent trap enable vrrp [ authfailure | newmaster ] |
Optional. Enabled by default. For more information about the command, see the snmp-agent trap enable command in Network Management and Monitoring Command Reference. |
Displaying and maintaining VRRP for IPv4
|
Task |
Command |
Remarks |
|
Display VRRP group status. |
display vrrp [ verbose ] [ interface interface-type interface-number [ vrid virtual-router-id ] ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display VRRP group statistics. |
display vrrp statistics [ interface interface-type interface-number [ vrid virtual-router-id ] ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Clear VRRP group statistics. |
reset vrrp statistics [ interface interface-type interface-number [ vrid virtual-router-id ] ] |
Available in user view. |
Configuring VRRP for IPv6
VRRP for IPv6 configuration task list
|
Task |
Remarks |
|
Optional. |
|
|
Specifying the type of MAC addresses mapped to virtual IPv6 addresses |
Optional. This configuration does not apply to VRRP load balancing mode. |
|
Creating a VRRP group and configuring a virtual IPv6 address |
Required. |
|
Configuring router priority, preemptive mode and tracking function |
Optional. |
|
Optional. The VF tracking function applies to only VRRP load balancing mode. |
|
|
Optional. |
Specifying the type of MAC addresses mapped to virtual IPv6 addresses
|
|
IMPORTANT: Specify the type of the MAC addresses mapped to the virtual IPv6 addresses before creating a VRRP group. Otherwise, you cannot change the type of the MAC addresses mapped to virtual IPv6 addresses. |
After you specify the type of MAC addresses mapped to the virtual IPv6 address of VRRP groups and create a VRRP group, the master in the VRRP group uses the specified type of MAC address as the source MAC address for sending packets and uses the specified type of MAC address to answer ND requests from hosts so that the hosts in the internal network can learn the mapping between the IPv6 address and the MAC address.
The following types of MAC addresses are available to be mapped to the virtual IPv6 address of a VRRP group:
· Virtual MAC address—By default, a virtual MAC address is automatically created for a VRRP group when the VRRP group is created, and the virtual IPv6 address of the VRRP group is mapped to the virtual MAC address. When such a mapping is adopted, the hosts in the internal network do not need to update the mapping between the IPv6 address and the MAC address when the master changes.
· Real MAC address of an interface—In case that an IP address owner exists in a VRRP group, if the virtual IPv6 address is mapped to the virtual MAC address, two MAC addresses are mapped to one IPv6 address. To avoid such as problem, map the virtual IPv6 address of the VRRP group to the real MAC address of an interface to forward the packets from a host to the IP address owner.
To specify the type of MAC addresses mapped to virtual IPv6 addresses:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify the type of MAC addresses mapped to virtual IPv6 addresses. |
vrrp ipv6 method { real-mac | virtual-mac } |
Optional. Virtual MAC address by default. |
|
|
NOTE: When VRRP is operating in load balancing mode, a virtual IPv6 address is always mapped to a virtual MAC address regardless of which type of MAC addresses are specified to be mapped to virtual IPv6 addresses. |
Creating a VRRP group and configuring a virtual IPv6 address
|
|
IMPORTANT: Do not create VRRP groups on the VLAN interface of a super VLAN. Otherwise, network performance might be affected. |
When creating a VRRP group, configure a virtual IPv6 address for the VRRP group. You can configure multiple virtual IPv6 addresses for a VRRP group.
A VRRP group is automatically created when you specify the first virtual IPv6 address for the VRRP group. If you specify another virtual IPv6 address for the VRRP group later, the virtual IPv6 address is added to the virtual IPv6 address list of the VRRP group.
Configuration prerequisites
Before creating a VRRP group and configuring a virtual IPv6 address on an interface, configure an IPv6 address for the interface and make sure that it is in the same network segment as the virtual IPv6 address to be configured.
Configuration guidelines
When you create a VRRP group and configure its virtual IPv6 address, follow these guidelines:
· When a router is the IP address owner in a VRRP group, H3C recommends not using the IPv6 address of the interface (virtual IPv6 address of the VRRP group) to establish an OSPFv3 neighbor relationship with the adjacent router, which means not using the ospfv3 area command to enable OSPFv3 on the interface. For more information about ospfv3 area command, see Layer 3—IP Routing Command Reference.
· When VRRP is operating in load balancing mode, the virtual IPv6 address of a VRRP group cannot be the same as the IPv6 address of any interface in the VRRP group. In other words, a VRRP group does not have an IP address owner in load balancing mode.
· You can create up to 16 VRRP groups on an interface and assign up to 16 virtual IPv6 addresses in a VRRP group.
· A VRRP group is removed after you remove all the virtual IPv6 addresses in it. In addition, configurations on that VRRP group do not take effect any longer.
· Removal of the VRRP group on the IP address owner causes IP address collision. To resolve the collision, change the IPv6 address of the interface on the IP address owner first and then remove the VRRP group from the interface.
Configuration procedure
To create a VRRP group and configure its virtual IPv6 address:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter the specified interface view. |
interface interface-type interface-number |
N/A |
|
3. Create a VRRP group and configure its virtual IPv6 address, which is a link local address. |
vrrp ipv6 vrid virtual-router-id virtual-ip virtual-address link-local |
No VRRP group is created by default. The first virtual IPv6 address of the VRRP group must be a link local address. Only one link local address is allowed in a VRRP group, and must be removed the last. |
|
4. Configure the VRRP group with a virtual IPv6 address, which is a global unicast address. |
vrrp ipv6 vrid virtual-router-id virtual-ip virtual-address |
Optional. By default, no global unicast address is configured as the virtual IPv6 address of a VRRP group. |
Configuring router priority, preemptive mode and tracking function
Configuration prerequisites
Before you configure router priority, preemptive mode and tracking function, create a VRRP group and configure its virtual IPv6 address.
Configuration guidelines
When you configure router priority, preemptive mode and interface tracking, follow these guidelines:
· The running priority of an IP address owner is always 255 and you do not need to configure it. An IP address owner always operates in preemptive mode.
· Interface tracking is not configurable on an IP address owner.
· If you configure an interface to be tracked or a track entry to be monitored on a router that is the IP address owner in a VRRP group, the configuration does not take effect. If the router is not the IP address owner in the VRRP group later, the configuration takes effect.
· The tracked interface can be a Layer 3 Ethernet interface, a VLAN interfaces, a Layer 3 aggregate interface, a POS interface, an HDLC link bundle interface, or an RPR logical interfaces.
· If the state of a tracked interface changes from down or removed to up, the priority of the router that owns the interface is automatically restored.
· If the state of a track entry changes from negative or invalid to positive, the priority of the router where the track entry is configured is automatically restored.
Configuration procedure
By configuring router priority, preemptive mode, interface tracking, or a track entry, determine which router in the VRRP group serves as the master.
To configure router priority, preemptive mode and interface tracking:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter the specified interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the priority of the router in the VRRP group. |
vrrp ipv6 vrid virtual-router-id priority priority-value |
Optional. 100 by default. |
|
4. Configure the router in the VRRP group to operate in preemptive mode and configure preemption delay of the VRRP group. |
vrrp ipv6 vrid virtual-router-id preempt-mode [ timer delay delay-value ] |
Optional. The router in the VRRP group operates in preemptive mode and the preemption delay is 0 seconds by default. |
|
5. Configure the interface to be tracked. |
vrrp ipv6 vrid virtual-router-id track interface interface-type interface-number [ reduced priority-reduced ] |
Optional. No interface is being tracked by default. |
|
6. Configure VRRP to track a specified track entry. |
vrrp ipv6 vrid virtual-router-id track track-entry-number [ reduced priority-reduced | switchover ] |
Optional. Not configured by default. |
Configuring VF tracking
Configuration prerequisites
Before you configure the VF tracking function, create a VRRP group and configure a virtual IPv6 address for it.
Configuration guidelines
When you configure VF tracking, follow these guidelines:
· You can configure the VF tracking function when VRRP is operating in either standard protocol mode or load balancing mode. However, the VF tracking function is effective only when VRRP is operating in load balancing mode.
· By default, the weight of a VF is 255, and its lower limit of failure is 10.
· If the weight of a VF owner is higher than or equal to the lower limit of failure, the priority of the VF owner is always 255 and does not change with the weight value. Therefore, if an uplink fails, another VF takes over the VF owner's work and becomes the AVF only when the weight of the VF owner decreases by a correctly specified value and becomes lower than the lower limit of failure. In other words, the weight of the VF owner decreases by more than 245.
Configuration procedure
Assume that VRRP is operating in load balancing mode, and you have configured the VF tracking function to monitor a track entry and specified the value by which the weight decreases. When the status of the track entry becomes negative, the weight values of all VFs on the router decrease by the specified value. When the status of the track entry becomes positive or invalid, the weight values of all VFs on the router restore their original values.
If you configure the VF tracking function on an LVF to monitor its corresponding AVF on a specified router, the LVF can take over the AVF immediately when the status of the track entry becomes negative, to ensure uninterrupted network communications.
To configure VF tracking:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter the specified interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure VF tracking. |
· Configure the VF tracking function to monitor
a specified track entry and specify the value by which the weight decreases: · Configure the VF tracking function to monitor an
AVF on a specified router: |
Use either method. The VF tracking function is not configured by default. |
Configuring VRRP packet attributes
Configuration prerequisites
Before you configure the relevant attributes of VRRP packets, create a VRRP group and configure a virtual IPv6 address.
Configuration guidelines
When you configure VRRP packet attributes, follow these guidelines:
· You might configure different authentication modes and authentication keys for the VRRP groups on an interface. However, the members of the same VRRP group must use the same authentication mode and authentication key.
· Excessive traffic might cause a backup to trigger a change of its status because the backup does not receive any VRRP advertisements for a specified period of time. To solve this problem, prolong the time interval to send VRRP advertisements.
· Configuring different intervals for sending VRRP advertisements on the routers in a VRRP group might cause a backup to trigger a change of its status because the backup does not receive any VRRP advertisements for a specified period of time. To solve this problem, configure the same interval for sending VRRP advertisements on each router in the VRRP group.
Configuration procedure
To configure VRRP packet attributes:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter the specified interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the authentication mode and authentication key when the VRRP groups send or receive VRRP packets. |
vrrp ipv6 vrid virtual-router-id authentication-mode simple [ cipher ] key |
Optional. Authentication is not performed by default. |
|
4. Configure the time interval for the master in the VRRP group to send VRRP advertisement. |
vrrp ipv6 vrid virtual-router-id timer advertise adver-interval |
Optional. 100 centiseconds by default. |
Displaying and maintaining VRRP for IPv6
|
Task |
Command |
Remarks |
|
Display VRRP group status. |
display vrrp ipv6 [ verbose ] [ interface interface-type interface-number [ vrid virtual-router-id ] ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display VRRP group statistics. |
display vrrp ipv6 statistics [ interface interface-type interface-number [ vrid virtual-router-id ] ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Clear VRRP group statistics. |
reset vrrp ipv6 statistics [ interface interface-type interface-number [ vrid virtual-router-id ] ] |
Available in user view. |
IPv4-based VRRP configuration examples
|
IMPORTANT: By default, an Ethernet, VLAN, or aggregate interface is in DOWN state. To configure such an interface, use the undo shutdown command to bring it up first. |
Single VRRP group configuration example
Network requirements
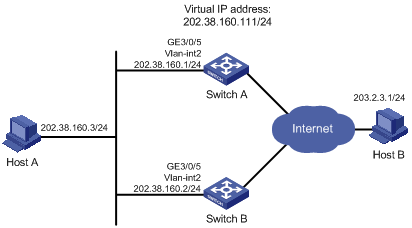
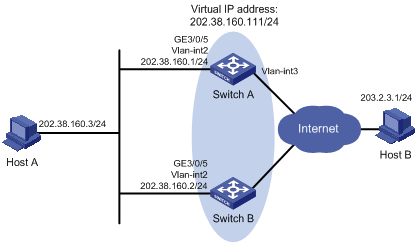
Host A wants to access Host B on the Internet, using 202.38.160.111/24 as its default gateway.
Switch A and Switch B belong to VRRP group 1 with the virtual IP address of 202.38.160.111/24.
When Switch A operates correctly, packets sent from Host A to Host B are forwarded by Switch A; when Switch A fails, packets sent from Host A to Host B are forwarded by Switch B.
Figure 12 Network diagram
Configuration procedure
1. Configure Switch A:
# Configure VLAN 2.
<SwitchA> system-view
[SwitchA] vlan 2
[SwitchA-vlan2] port gigabitethernet 3/0/5
[SwitchA-vlan2] quit
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] ip address 202.38.160.1 255.255.255.0
# Create VRRP group 1 and set its virtual IP address to 202.38.160.111.
[SwitchA-Vlan-interface2] vrrp vrid 1 virtual-ip 202.38.160.111
# Set the priority of Switch A in VRRP group 1 to 110, which is higher than that of Switch B (100), so that Switch A can become the master.
[SwitchA-Vlan-interface2] vrrp vrid 1 priority 110
# Configure Switch A to operate in preemptive mode so that it can become the master whenever it works correctly, and configure the preemption delay as 5 seconds to avoid frequent status switchover.
[SwitchA-Vlan-interface2] vrrp vrid 1 preempt-mode timer delay 5
2. Configure Switch B:
# Configure VLAN 2.
<SwitchB> system-view
[SwitchB] vlan 2
[SwitchB-Vlan2] port Gigabitethernet 3/0/5
[SwitchB-vlan2] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] ip address 202.38.160.2 255.255.255.0
# Create VRRP group 1 and set its virtual IP address to 202.38.160.111.
[SwitchB-Vlan-interface2] vrrp vrid 1 virtual-ip 202.38.160.111
# Set Switch B to operate in preemptive mode. The preemption delay is 5 seconds.
[SwitchB-Vlan-interface2] vrrp vrid 1 preempt-mode timer delay 5
3. Verify the configuration:
After the configuration, Host B can be pinged successfully on Host A. To verify your configuration, use the display vrrp verbose command.
# Display the detailed information of VRRP group 1 on Switch A.
[SwitchA-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : 202.38.160.111
Virtual MAC : 0000-5e00-0101
Master IP : 202.38.160.1
# Display the detailed information of VRRP group 1 on Switch B.
[SwitchB-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Become Master : 4200ms left
Auth Type : None
Virtual IP : 202.38.160.111
Master IP : 202.38.160.1
The output shows that in VRRP group 1 Switch A is the master, Switch B is the backup and packets sent from Host A to Host B are forwarded by Switch A.
When Switch A fails, you can still ping through Host B on Host A. Use the display vrrp verbose command to view the detailed information of the VRRP group on Switch B.
# When Switch A fails, the detailed information of VRRP group 1 on Switch B is displayed.
[SwitchB-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Master
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : 202.38.160.111
Virtual MAC : 0000-5e00-0101
Master IP : 202.38.160.2
The output shows that when Switch A fails, Switch B becomes the master, and packets sent from Host A to Host B are forwarded by Switch B.
# After Switch A resumes normal operation, use the display vrrp verbose command to display the detailed information of VRRP group 1 on Switch A.
[SwitchA-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : 202.38.160.111
Virtual MAC : 0000-5e00-0101
Master IP : 202.38.160.1
The output shows that after Switch A resumes normal operation, it becomes the master, and packets sent from host A to host B are forwarded by Switch A.
VRRP interface tracking configuration example
Network requirements
Host A wants to access Host B on the Internet, using 202.38.160.111/24 as its default gateway.
Switch A and Switch B belong to VRRP group 1 with the virtual IP address of 202.38.160.111/24.
If Switch A operates correctly, packets sent from Host A to Host B are forwarded by Switch A. If VLAN-interface 3 through which Switch A connects to the Internet is not available, packets sent from Host A to Host B are forwarded by Switch B.
To prevent attacks to the VRRP group from illegal users by using spoofed packets, configure the authentication mode as plain text to authenticate the VRRP packets in VRRP group 1, and specify the authentication key as hello.
Figure 13 Network diagram
Configuration procedure
1. Configure Switch A:
# Configure VLAN 2.
<SwitchA> system-view
[SwitchA] vlan 2
[SwitchA-vlan2] port Gigabitethernet 3/0/5
[SwitchA-vlan2] quit
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] ip address 202.38.160.1 255.255.255.0
# Create a VRRP group 1 and set its virtual IP address to 202.38.160.111.
[SwitchA-Vlan-interface2] vrrp vrid 1 virtual-ip 202.38.160.111
# Configure the priority of Switch A in the VRRP group to 110, which is higher than that of Switch B (100), so that Switch A can become the master.
[SwitchA-Vlan-interface2] vrrp vrid 1 priority 110
# Configure the authentication mode of the VRRP group as simple and authentication key as hello.
[SwitchA-Vlan-interface2] vrrp vrid 1 authentication-mode simple hello
# Set the interval for Master to send VRRP advertisement to 4 seconds.
[SwitchA-Vlan-interface2] vrrp vrid 1 timer advertise 4
# Configure Switch A to operate in preemptive mode, so that it can become the master whenever it works correctly; configure the preemption delay as 5 seconds to avoid frequent status switchover.
[SwitchA-Vlan-interface2] vrrp vrid 1 preempt-mode timer delay 5
# Set VLAN interface 3 on Switch A to be tracked, and configure the amount by which the priority value decreases to be more than 10 (30 in this example), so that when VLAN-interface 3 fails, the priority of Switch A in VRRP group 1 decreases to a value lower than 100 and thus Switch B can become the master.
[SwitchA-Vlan-interface2] vrrp vrid 1 track interface vlan-interface 3 reduced 30
2. Configure Switch B:
# Configure VLAN 2.
<SwitchB> system-view
[SwitchB] vlan 2
[SwitchB-vlan2] port Gigabitethernet 3/0/5
[SwitchB-vlan2] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] ip address 202.38.160.2 255.255.255.0
# Create a VRRP group 1 and set its virtual IP address to 202.38.160.111.
[SwitchB-Vlan-interface2] vrrp vrid 1 virtual-ip 202.38.160.111
# Configure the authentication mode of the VRRP group as simple and authentication key as hello.
[SwitchB-Vlan-interface2] vrrp vrid 1 authentication-mode simple hello
# Set the interval for master to send VRRP advertisement to 4 seconds.
[SwitchB-Vlan-interface2] vrrp vrid 1 timer advertise 4
# Configure Switch B to operate in preemptive mode, so that Switch B can become the master after the priority of Switch A decreases to a value lower than 100. Configure the preemption delay as 5 seconds to avoid frequent status switchover.
[SwitchB-Vlan-interface2] vrrp vrid 1 preempt-mode timer delay 5
3. Verify the configuration:
After the configuration, Host B can be pinged successfully on Host A. To verify your configuration, use the display vrrp verbose command.
# Display the detailed information of VRRP group 1 on Switch A.
[SwitchA-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 4
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 5
Auth Type : Simple Key : ******
Virtual IP : 202.38.160.111
Virtual MAC : 0000-5e00-0101
Master IP : 202.38.160.1
VRRP Track Information:
Track Interface: Vlan3 State : Up Pri Reduced : 30
# Display the detailed information of VRRP group 1 on Switch B.
[SwitchB-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 4
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Become Master : 2200ms left
Auth Type : Simple Key : ******
Virtual IP : 202.38.160.111
Master IP : 202.38.160.1
The output shows that in VRRP group 1 Switch A is the master, Switch B is the backup and packets sent from Host A to Host B are forwarded by Switch A.
If interface VLAN-interface 3 through which Switch A connects to the Internet is not available, you can still ping Host B successfully on Host A. To view the detailed information of the VRRP group, use the display vrrp verbose command.
# If VLAN-interface 3 on Switch A is not available, the detailed information of VRRP group 1 on Switch A is displayed.
[SwitchA-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 4
Admin Status : Up State : Backup
Config Pri : 110 Running Pri : 80
Preempt Mode : Yes Delay Time : 5
Become Master : 2200ms left
Auth Type : Simple Key : ******
Virtual IP : 202.38.160.111
Master IP : 202.38.160.2
VRRP Track Information:
Track Interface: Vlan3 State : Down Pri Reduced : 30
# When VLAN-interface 3 on Switch A is not available, the detailed information of VRRP group 1 on Switch B is displayed.
[SwitchB-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 4
Admin Status : Up State : Master
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Auth Type : Simple Key : ******
Virtual IP : 202.38.160.111
Virtual MAC : 0000-5e00-0101
Master IP : 202.38.160.2
The output shows that when VLAN-interface 3 on Switch A is not available, the priority of Switch A is reduced to 80 and it becomes the backup. Switch B becomes the master and packets sent from Host A to Host B are forwarded by Switch B.
VRRP with multiple VLANs configuration example
Network requirements
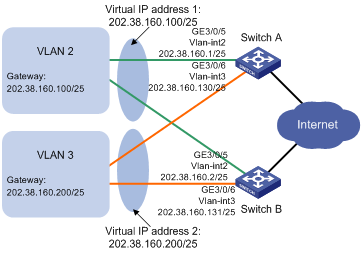
Hosts in VLAN 2 use 202.38.160.100/25 as their default gateway and hosts in VLAN 3 use 202.38.160.200/25 as their default gateway.
Switch A and Switch B belong to both VRRP group 1 and VRRP group 2. The virtual IP address of VRRP group 1 is 202.38.160.100/25, and that of VRRP group 2 is 202.38.160.200/25.
In VRRP group 1, Switch A has a higher priority than Switch B. In VRRP group 2, Switch B has a higher priority than Switch A. In this case, hosts in VLAN 2 and VLAN 3 can communicate with external networks through Switch A and Switch B, respectively, and when Switch A or Switch B fails, the hosts can use the other switch to communicate with external networks to avoid communication interruption.
Figure 14 Network diagram
Configuration procedure
1. Configure Switch A:
# Configure VLAN 2.
<SwitchA> system-view
[SwitchA] vlan 2
[SwitchA-vlan2] port Gigabitethernet 3/0/5
[SwitchA-vlan2] quit
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] ip address 202.38.160.1 255.255.255.128
# Create a VRRP group 1 and set its virtual IP address to 202.38.160.100.
[SwitchA-Vlan-interface2] vrrp vrid 1 virtual-ip 202.38.160.100
# Configure the priority of Switch A in VRRP group 1 as 110, which is higher than that of Switch B (100), so that Switch A can become the master in VRRP group 1.
[SwitchA-Vlan-interface2] vrrp vrid 1 priority 110
[SwitchA-Vlan-interface2] quit
# Configure VLAN 3.
[SwitchA] vlan 3
[SwitchA-vlan3] port Gigabitethernet 3/0/6
[SwitchA-vlan3] quit
[SwitchA] interface vlan-interface 3
[SwitchA-Vlan-interface3] ip address 202.38.160.130 255.255.255.128
# Create a VRRP group 2 and set its virtual IP address to 202.38.160.200.
[SwitchA-Vlan-interface3] vrrp vrid 2 virtual-ip 202.38.160.200
2. Configure Switch B:
# Configure VLAN 2.
<SwitchB> system-view
[SwitchB] vlan 2
[SwitchB-vlan2] port Gigabitethernet 3/0/5
[SwitchB-vlan2] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] ip address 202.38.160.2 255.255.255.128
# Create a VRRP group 1 and set its virtual IP address to 202.38.160.100.
[SwitchB-Vlan-interface2] vrrp vrid 1 virtual-ip 202.38.160.100
[SwitchB-Vlan-interface2] quit
# Configure VLAN 3.
[SwitchB] vlan 3
[SwitchB-vlan3] port Gigabitethernet 3/0/6
[SwitchB-vlan3] quit
[SwitchB] interface vlan-interface 3
[SwitchB-Vlan-interface3] ip address 202.38.160.131 255.255.255.128
# Create a VRRP group 2 and set its virtual IP address to 202.38.160.200.
[SwitchB-Vlan-interface3] vrrp vrid 2 virtual-ip 202.38.160.200
# Configure the priority of Switch B in VRRP group 2 to 110, which is higher than that of Switch A (100), so that Switch B can become the master in VRRP group 2.
[SwitchB-Vlan-interface3] vrrp vrid 2 priority 110
3. Verify the configuration:
To verify your configuration, use the display vrrp verbose command.
# Display the detailed information of the VRRP group on Switch A.
[SwitchA-Vlan-interface3] display vrrp verbose
IPv4 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 2
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 0
Auth Type : None
Virtual IP : 202.38.160.100
Virtual MAC : 0000-5e00-0101
Master IP : 202.38.160.1
Interface Vlan-interface3
VRID : 2 Adver Timer : 1
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 0
Become Master : 2200ms left
Auth Type : None
Virtual IP : 202.38.160.200
Master IP : 202.38.160.131
# Display the detailed information of the VRRP group on Switch B.
[SwitchB-Vlan-interface3] display vrrp verbose
IPv4 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 2
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 0
Become Master : 2200ms left
Auth Type : None
Virtual IP : 202.38.160.100
Master IP : 202.38.160.1
Interface Vlan-interface3
VRID : 2 Adver Timer : 1
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 0
Auth Type : None
Virtual IP : 202.38.160.200
Virtual MAC : 0000-5e00-0102
Master IP : 202.38.160.131
The output shows that in VRRP group 1 Switch A is the master, Switch B is the backup and hosts with the default gateway of 202.38.160.100/25 accesses the Internet through Switch A; in VRRP group 2 Switch A is the backup, Switch B is the master and hosts with the default gateway of 202.38.160.200/25 accesses the Internet through Switch B.
VRRP load balancing mode configuration example
Network requirements
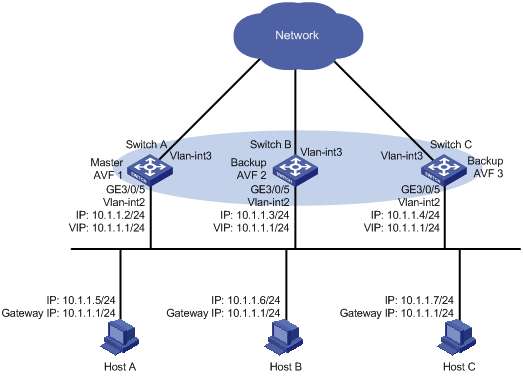
Switch A, Switch B, and Switch C belong to VRRP group 1 with the virtual IP address of 10.1.1.1/24.
Hosts on network segment 10.1.1.0/24 use 10.1.1.1/24 as their default gateway. Use the VRRP group to make sure that when a gateway (Switch A, Switch B, or Switch C) fails, the hosts on the LAN can access external networks through another gateway.
VRRP group 1 is operating in load balancing mode to make good use of network resources.
Configure a track entry on Switch A, Switch B, and Switch C to monitor their own VLAN-interface 3. When the interface on Switch A, Switch B, or Switch C fails, the weight of the corresponding switch decreases so that another switch with a higher weight can take over.
Configure track entries on Switch C to monitor Switch A and Switch B. When Switch A or Switch B fails, Switch C immediately takes over the AVF on Switch A or Switch B.
Figure 15 Network diagram
Configuration procedure
1. Configure Switch A:
# Configure VLAN 2.
<SwitchA> system-view
[SwitchA] vlan 2
[SwitchA-vlan2] port Gigabitethernet 3/0/5
[SwitchA-vlan2] quit
# Configure VRRP to operate in load balancing mode.
[SwitchA] vrrp mode load-balance
# Create VRRP group 1 and configure its virtual IP address as 10.1.1.1.
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] ip address 10.1.1.2 24
[SwitchA-Vlan-interface2] vrrp vrid 1 virtual-ip 10.1.1.1
# Set the priority of Switch A in VRRP group 1 to 120, which is higher than that of Switch B (110) and that of Switch C (100), so that Switch A can become the master.
[SwitchA-Vlan-interface2] vrrp vrid 1 priority 120
# Configure Switch A to operate in preemptive mode, so that it can become the master whenever it works correctly; configure the preemption delay as 5 seconds to avoid frequent status switchover.
[SwitchA-Vlan-interface2] vrrp vrid 1 preempt-mode timer delay 5
[SwitchA-Vlan-interface2] quit
# Create track entry 1 to associate with the physical status of VLAN-interface 3 on Switch A. When the track entry becomes negative, it means that the interface fails.
[SwitchA] track 1 interface vlan-interface 3
# Configure VF tracking to monitor track entry 1 and specify the value by which the weight decreases, making the weight of Switch A decrease by more than 245 (250 in this example) when track entry 1 turns to negative. In such a case, another router with a higher weight can take over.
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] vrrp vrid 1 weight track 1 reduced 250
2. Configure Switch B:
# Configure VLAN 2.
<SwitchB> system-view
[SwitchB] vlan 2
[SwitchB-vlan2] port Gigabitethernet 3/0/5
[SwitchB-vlan2] quit
# Configure VRRP to operate in load balancing mode.
[SwitchB] vrrp mode load-balance
# Create VRRP group 1 and configure its virtual IP address as 10.1.1.1.
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] ip address 10.1.1.3 24
[SwitchB-Vlan-interface2] vrrp vrid 1 virtual-ip 10.1.1.1
# Set the priority of Switch B in VRRP group 1 to 110, which is higher than that of Switch C (100), so that Switch B can become the master when Switch A fails.
[SwitchB-Vlan-interface2] vrrp vrid 1 priority 110
# Set Switch B to operate in preemptive mode. The preemption delay is 5 seconds.
[SwitchB-Vlan-interface2] vrrp vrid 1 preempt-mode timer delay 5
[SwitchB-Vlan-interface2] quit
# Create track entry 1 to associate with the physical status of VLAN-interface 3 on Switch B. When the track entry becomes negative, it means that the interface fails.
[SwitchB] track 1 interface vlan-interface 3
# Configure VF tracking to monitor track entry 1 and specify the value by which the weight decreases, making the weight of Switch B decrease by more than 245 (250 in this example) when track entry 1 turns to negative. In such a case, another router with a higher weight can take over.
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] vrrp vrid 1 weight track 1 reduced 250
3. Configure Switch C:
# Configure VLAN 2.
<SwitchC> system-view
[SwitchC] vlan 2
[SwitchC-vlan2] port Gigabitethernet 3/0/5
[SwitchC-vlan2] quit
# Configure VRRP to operate in load balancing mode.
[SwitchC] vrrp mode load-balance
# Create VRRP group 1 and configure its virtual IP address as 10.1.1.1.
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] ip address 10.1.1.4 24
[SwitchC-Vlan-interface2] vrrp vrid 1 virtual-ip 10.1.1.1
# Set Switch C to operate in preemptive mode. The preemption delay is 5 seconds.
[SwitchC-Vlan-interface2] vrrp vrid 1 preempt-mode timer delay 5
[SwitchC-Vlan-interface2] quit
# Create track entry 1 to associate with the physical status of VLAN-interface 3 on Switch C. When the track entry becomes negative, it means that the interface fails.
[SwitchC] track 1 interface vlan-interface 3
# Configure VF tracking to monitor track entry 1 and specify the value by which the weight decreases, making the weight of Switch C decrease by more than 245 (250 in this example) when track entry 1 turns to negative. In such a case, another router with a higher weight can take over.
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] vrrp vrid 1 weight track 1 reduced 250
[SwitchC-Vlan-interface2] quit
# Create track entries 2 and 3 to monitor Switch A and Switch B, respectively. If a track entry becomes negative, it indicates that the corresponding switch fails.
[SwitchC] bfd echo-source-ip 1.2.3.4
[SwitchC] track 2 bfd echo interface vlan-interface 2 remote ip 10.1.1.2 local ip 10.1.1.4
[SwitchC] track 3 bfd echo interface vlan-interface 2 remote ip 10.1.1.3 local ip 10.1.1.4
# Configure VF tracking to monitor track entry 2. When track entry 2 becomes negative, the LVF on Switch C whose corresponding AVF is on the switch with the IP address of 10.1.1.2 immediately becomes active. Switch C takes over the AVF on Switch A.
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] vrrp vrid 1 track 2 forwarder-switchover member-ip 10.1.1.2
# Configure VF tracking to monitor track entry 3. When track entry 2 becomes negative, the LVF on Switch C whose corresponding AVF is on the switch with the IP address of 10.1.1.3 immediately becomes active. Switch C takes over the AVF on Switch B.
[SwitchC-Vlan-interface2] vrrp vrid 1 track 3 forwarder-switchover member-ip 10.1.1.3
4. Verify the configuration:
After the configuration, Host A can ping the external network. To verify your configuration, use the display vrrp verbose command.
# Display the detailed information of VRRP group 1 on Switch A.
[SwitchA-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Master
Config Pri : 120 Running Pri : 120
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : 10.1.1.1
Member IP List : 10.1.1.2 (Local, Master)
10.1.1.3 (Backup)
10.1.1.4 (Backup)
Forwarder Information: 3 Forwarders 1 Active
Config Weight : 255
Running Weight : 255
Forwarder 01
State : Active
Virtual MAC : 000f-e2ff-0011 (Owner)
Owner ID : 0000-5e01-1101
Priority : 255
Active : local
Forwarder 02
State : Listening
Virtual MAC : 000f-e2ff-0012 (Learnt)
Owner ID : 0000-5e01-1103
Priority : 127
Active : 10.1.1.3
Forwarder 03
State : Listening
Virtual MAC : 000f-e2ff-0013 (Learnt)
Owner ID : 0000-5e01-1105
Priority : 127
Active : 10.1.1.4
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
# Display the detailed information of VRRP group 1 on Switch B.
[SwitchB-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Backup
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 5
Become Master : 4200ms left
Auth Type : None
Virtual IP : 10.1.1.1
Member IP List : 10.1.1.3 (Local, Backup)
10.1.1.2 (Master)
10.1.1.4 (Backup)
Forwarder Information: 3 Forwarders 1 Active
Config Weight : 255
Running Weight : 255
Forwarder 01
State : Listening
Virtual MAC : 000f-e2ff-0011 (Learnt)
Owner ID : 0000-5e01-1101
Priority : 127
Active : 10.1.1.2
Forwarder 02
State : Active
Virtual MAC : 000f-e2ff-0012 (Owner)
Owner ID : 0000-5e01-1103
Priority : 255
Active : local
Forwarder 03
State : Listening
Virtual MAC : 000f-e2ff-0013 (Learnt)
Owner ID : 0000-5e01-1105
Priority : 127
Active : 10.1.1.4
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
# Display the detailed information of VRRP group 1 on Switch C.
[SwitchC-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Become Master : 4200ms left
Auth Type : None
Virtual IP : 10.1.1.1
Member IP List : 10.1.1.4 (Local, Backup)
10.1.1.2 (Master)
10.1.1.3 (Backup)
Forwarder Information: 3 Forwarders 1 Active
Config Weight : 255
Running Weight : 255
Forwarder 01
State : Listening
Virtual MAC : 000f-e2ff-0011 (Learnt)
Owner ID : 0000-5e01-1101
Priority : 127
Active : 10.1.1.2
Forwarder 02
State : Listening
Virtual MAC : 000f-e2ff-0012 (Learnt)
Owner ID : 0000-5e01-1103
Priority : 127
Active : 10.1.1.3
Forwarder 03
State : Active
Virtual MAC : 000f-e2ff-0013 (Owner)
Owner ID : 0000-5e01-1105
Priority : 255
Active : local
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
Forwarder Switchover Track Information:
Track Object : 2 State : Positive
Member IP : 10.1.1.2
Track Object : 3 State : Positive
Member IP : 10.1.1.3
The output shows that in VRRP group 1, Switch A is the master and Switch B and Switch C are the backups. Each switch has one AVF and two LVFs that act as the backups.
# When VLAN-interface 3 on Switch A fails, use the display vrrp verbose command to display the detailed information of VRRP group 1 on Switch A.
[SwitchA-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Master
Config Pri : 120 Running Pri : 120
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : 10.1.1.1
Member IP List : 10.1.1.2 (Local, Master)
10.1.1.3 (Backup)
10.1.1.4 (Backup)
Forwarder Information: 3 Forwarders 0 Active
Config Weight : 255
Running Weight : 5
Forwarder 01
State : Initialize
Virtual MAC : 000f-e2ff-0011 (Owner)
Owner ID : 0000-5e01-1101
Priority : 0
Active : 10.1.1.4
Forwarder 02
State : Initialize
Virtual MAC : 000f-e2ff-0012 (Learnt)
Owner ID : 0000-5e01-1103
Priority : 0
Active : 10.1.1.3
Forwarder 03
State : Initialize
Virtual MAC : 000f-e2ff-0013 (Learnt)
Owner ID : 0000-5e01-1105
Priority : 0
Active : 10.1.1.4
Forwarder Weight Track Information:
Track Object : 1 State : Negative Weight Reduced : 250
# Use the display vrrp verbose command to display the detailed information of VRRP group 1 on Switch C.
[SwitchC-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Become Master : 4200ms left
Auth Type : None
Virtual IP : 10.1.1.1
Member IP List : 10.1.1.4 (Local, Backup)
10.1.1.2 (Master)
10.1.1.3 (Backup)
Forwarder Information: 3 Forwarders 2 Active
Config Weight : 255
Running Weight : 255
Forwarder 01
State : Active
Virtual MAC : 000f-e2ff-0011 (Take Over)
Owner ID : 0000-5e01-1101
Priority : 85
Active : local
Redirect Time : 93 secs
Time-out Time : 1293 secs
Forwarder 02
State : Listening
Virtual MAC : 000f-e2ff-0012 (Learnt)
Owner ID : 0000-5e01-1103
Priority : 85
Active : 10.1.1.3
Forwarder 03
State : Active
Virtual MAC : 000f-e2ff-0013 (Owner)
Owner ID : 0000-5e01-1105
Priority : 255
Active : local
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
Forwarder Switchover Track Information:
Track Object : 2 State : Positive
Member IP : 10.1.1.2
Track Object : 3 State : Positive
Member IP : 10.1.1.3
The output shows that when VLAN interface 3 on Switch A fails, the weight of the AVF on Switch A decreases to 5, which is lower than the lower limit of failure. All VFs on Switch A turn to initialized state and cannot be used for packet forwarding. The VF corresponding to MAC address 000f-e2ff-0011 on Switch C becomes the AVF, and Switch C takes over Switch A for packet forwarding.
# When the timeout timer (about 1800 seconds) expires, display the detailed information of VRRP group 1 on Switch C.
[SwitchC-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Become Master : 4200ms left
Auth Type : None
Virtual IP : 10.1.1.1
Member IP List : 10.1.1.4 (Local, Backup)
10.1.1.2 (Master)
10.1.1.3 (Backup)
Forwarder Information: 2 Forwarders 1 Active
Config Weight : 255
Running Weight : 255
Forwarder 02
State : Listening
Virtual MAC : 000f-e2ff-0012 (Learnt)
Owner ID : 0000-5e01-1103
Priority : 127
Active : 10.1.1.3
Forwarder 03
State : Active
Virtual MAC : 000f-e2ff-0013 (Owner)
Owner ID : 0000-5e01-1105
Priority : 255
Active : local
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
Forwarder Switchover Track Information:
Track Object : 2 State : Positive
Member IP : 10.1.1.2
Track Object : 3 State : Positive
Member IP : 10.1.1.3
The output shows that when the timeout timer expires, the VF corresponding to virtual MAC address 000f-e2ff-0011 is removed, and does not forward the packets destined for the MAC address any more.
# When Switch A fails, use the display vrrp verbose command to display the detailed information of VRRP group 1 on Switch B.
[SwitchB-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : 10.1.1.1
Member IP List : 10.1.1.3 (Local, Master)
10.1.1.4 (Backup)
Forwarder Information: 2 Forwarders 1 Active
Config Weight : 255
Running Weight : 255
Forwarder 02
State : Active
Virtual MAC : 000f-e2ff-0012 (Owner)
Owner ID : 0000-5e01-1103
Priority : 255
Active : local
Forwarder 03
State : Listening
Virtual MAC : 000f-e2ff-0013 (Learnt)
Owner ID : 0000-5e01-1105
Priority : 127
Active : 10.1.1.4
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
The output shows that when Switch A fails, Switch B becomes the master because its priority is higher than that of Switch C.
# When Switch B fails, use the display vrrp verbose command to display the detailed information of VRRP group 1 on Switch C.
[SwitchC-Vlan-interface2] display vrrp verbose
IPv4 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 1
Admin Status : Up State : Master
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : 10.1.1.1
Member IP List : 10.1.1.4 (Local, Master)
Forwarder Information: 2 Forwarders 2 Active
Config Weight : 255
Running Weight : 255
Forwarder 02
State : Active
Virtual MAC : 000f-e2ff-0012 (Take Over)
Owner ID : 0000-5e01-1103
Priority : 85
Active : local
Redirect Time : 93 secs
Time-out Time : 1293 secs
Forwarder 03
State : Active
Virtual MAC : 000f-e2ff-0013 (Owner)
Owner ID : 0000-5e01-1105
Priority : 255
Active : local
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
Forwarder Switchover Track Information:
Track Object : 2 State : Negative
Member IP : 10.1.1.2
Track Object : 3 State : Negative
Member IP : 10.1.1.3
The output shows that when Switch B fails, Switch C becomes the master, and Forwarder 02 on Switch C immediately becomes active. Switch C takes over the AVF on Switch B.
IPv6-based VRRP configuration examples
|
IMPORTANT: By default, an Ethernet, VLAN, or aggregate interface is in DOWN state. To configure such an interface, use the undo shutdown command to bring it up first. |
Single VRRP group configuration example
Network requirements
Switch A and Switch B belong to VRRP group 1 with the virtual IP addresses of 1::10/64 and FE80::10.
Host A wants to access Host B on the Internet, and learns 1::10/64 as its default gateway through RA messages sent by the switches.
When Switch A operates correctly, packets sent from Host A to Host B are forwarded by Switch A; when Switch A fails, packets sent from Host A to Host B are forwarded by Switch B.
Figure 16 Network diagram
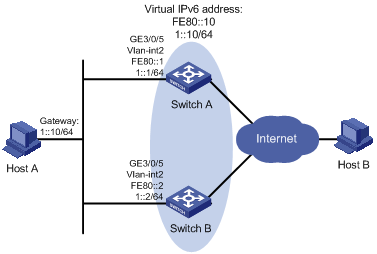
Configuration procedure
1. Configure Switch A:
# Configure VLAN 2.
<SwitchA> system-view
[SwitchA] ipv6
[SwitchA] vlan 2
[SwitchA-vlan2] port Gigabitethernet 3/0/5
[SwitchA-vlan2] quit
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] ipv6 address fe80::1 link-local
[SwitchA-Vlan-interface2] ipv6 address 1::1 64
# Create a VRRP group 1 and set its virtual IPv6 addresses to FE80::10 and 1::10.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip fe80::10 link-local
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip 1::10
# Set the priority of Switch A in VRRP group 1 to 110, which is higher than that of Switch B (100), so that Switch A can become the master.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 priority 110
# Configure Switch A to operate in preemptive mode so that it can become the master whenever it works correctly, and configure the preemption delay as 5 seconds to avoid frequent status switchover.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 preempt-mode timer delay 5
# Enable Switch A to send RA messages, so that Host A can learn the default gateway address.
[SwitchA-Vlan-interface2] undo ipv6 nd ra halt
2. Configure Switch B:
# Configure VLAN 2.
<SwitchB> system-view
[SwitchB] ipv6
[SwitchB] vlan 2
[SwitchB-vlan2] port Gigabitethernet 3/0/5
[SwitchB-vlan2] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] ipv6 address fe80::2 link-local
[SwitchB-Vlan-interface2] ipv6 address 1::2 64
# Create a VRRP group 1 and set its virtual IPv6 addresses to FE80::10 and 1::10.
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip fe80::10 link-local
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip 1::10
# Configure Switch B to operate in preemptive mode, with the preemption delay set to 5 seconds.
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 preempt-mode timer delay 5
# Enable Switch B to send RA messages, so that Host A can learn the default gateway address.
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 preempt-mode timer delay 5
3. Verify the configuration:
After the configuration, Host B can be pinged successfully on Host A. To verify your configuration, use the display vrrp ipv6 verbose command.
# Display the detailed information of VRRP group 1 on Switch A.
[SwitchA-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : FE80::10
1::10
Virtual MAC : 0000-5e00-0201
Master IP : FE80::1
# Display the detailed information of VRRP group 1 on Switch B.
[SwitchB-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Become Master : 4200ms left
Auth Type : None
Virtual IP : FE80::10
1::10
Master IP : FE80::1
The output shows that in VRRP group 1 Switch A is the master, Switch B is the backup and packets sent from Host A to Host B are forwarded by Switch A.
When Switch A fails, you can still successfully ping Host B on Host A. To view the detailed information of the VRRP group on Switch B, use the display vrrp ipv6 verbose command.
# When Switch A fails, the detailed information of VRRP group 1 on Switch B is displayed.
[SwitchB-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : FE80::10
1::10
Virtual MAC : 0000-5e00-0201
Master IP : FE80::2
The output shows that when Switch A fails, Switch B becomes the master, and packets sent from Host A to Host B are forwarded by Switch B.
# After Switch A resumes normal operation, use the display vrrp ipv6 verbose command to display the detailed information of VRRP group 1 on Switch A.
[SwitchA-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : FE80::10
1::10
Virtual MAC : 0000-5e00-0201
Master IP : FE80::1
The output shows that after Switch A resumes normal operation, it becomes the master, and packets sent from host A to host B are forwarded by Switch A.
VRRP interface tracking configuration example
Network requirements
Switch A and Switch B belong to VRRP group 1 with the virtual IP addresses of 1::10/64 and FE80::10.
Host A wants to access Host B on the Internet, and learns 1::10/64 as its default gateway through RA messages sent by the switches.
When Switch A operates correctly, packets sent from Host A to Host B are forwarded by Switch A. If VLAN-interface 3 through which Switch A connects to the Internet is not available, packets sent from Host A to Host B are forwarded by Switch B.
To prevent attacks to the VRRP group from illegal users by using spoofed packets, configure the authentication mode as plain text to authenticate the VRRP packets in VRRP group 1, and specify the authentication key as hello.
Figure 17 Network diagram
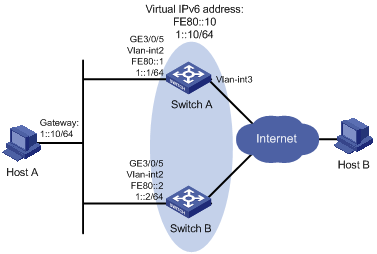
Configuration procedure
1. Configure Switch A:
# Configure VLAN 2.
<SwitchA> system-view
[SwitchA] ipv6
[SwitchA] vlan 2
[SwitchA-vlan2] port Gigabitethernet 3/0/5
[SwitchA-vlan2] quit
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] ipv6 address fe80::1 link-local
[SwitchA-Vlan-interface2] ipv6 address 1::1 64
# Create a VRRP group 1 and set its virtual IPv6 addresses to FE80::10 and 1::10.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip fe80::10 link-local
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip 1::10
# Set the priority of Switch A in VRRP group 1 to 110, which is higher than that of Switch B (100), so that Switch A can become the master.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 priority 110
# Set the authentication mode for VRRP group 1 to simple and authentication key to hello.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 authentication-mode simple hello
# Set the VRRP advertisement interval to 400 centiseconds.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 timer advertise 400
# Configure Switch A to operate in preemptive mode, so that it can become the master whenever it works correctly; configure the preemption delay as 5 seconds to avoid frequent status switchover.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 preempt-mode timer delay 5
# Set VLAN-interface 3 on Switch A to be tracked, and configure the amount by which the priority value decreases to be more than 10 (30 in this example), so that when VLAN interface 3 fails, the priority of Switch A in VRRP group 1 decreases to a value lower than 100 and thus Switch B can become the master.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 track interface vlan-interface 3 reduced 30
# Enable Switch A to send RA messages, so that Host A can learn the default gateway address.
[SwitchA-Vlan-interface2] undo ipv6 nd ra halt
2. Configure Switch B:
# Configure VLAN 2.
<SwitchB> system-view
[SwitchB] ipv6
[SwitchB] vlan 2
[SwitchB-vlan2] port Gigabitethernet 3/0/5
[SwitchB-vlan2] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] ipv6 address fe80::2 link-local
[SwitchB-Vlan-interface2] ipv6 address 1::2 64
# Create a VRRP group 1 and set its virtual IPv6 addresses to FE80::10 and 1::10.
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip fe80::10 link-local
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip 1::10
# Set the authentication mode for VRRP group 1 to simple and authentication key to hello.
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 authentication-mode simple hello
# Set the VRRP advertisement interval to 400 centiseconds.
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 timer advertise 400
# Configure Switch B to operate in preemptive mode, so that Switch B can become the master after the priority of Switch A decreases to a value lower than 100. Configure the preemption delay as 5 seconds to avoid frequent status switchover.
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 preempt-mode timer delay 5
# Enable Switch B to send RA messages, so that Host A can learn the default gateway address.
[SwitchB-Vlan-interface2] undo ipv6 nd ra halt
3. Verify the configuration:
After the configuration, Host B can be pinged successfully on Host A. To verify the configuration, use the display vrrp ipv6 verbose command.
# Display the detailed information of VRRP group 1 on Switch A.
[SwitchA-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 400
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 5
Auth Type : Simple Key : ******
Virtual IP : FE80::10
1::10
Virtual MAC : 0000-5e00-0201
Master IP : FE80::1
VRRP Track Information:
Track Interface: Vlan3 State : Up Pri Reduced : 30
# Display the detailed information of VRRP group 1 on Switch B.
[SwitchB-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 400
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Become Master : 4200ms left
Auth Type : Simple Key : ******
Virtual IP : FE80::10
1::10
Master IP : FE80::1
The output shows that in VRRP group 1 Switch A is the master, Switch B is the backup and packets sent from Host A to Host B are forwarded by Switch A.
When interface VLAN-interface 3 on Switch A is not available, you can still ping Host B successfully on Host A. To view the detailed information of the VRRP group, use the display vrrp ipv6 verbose command.
# When interface VLAN-interface 3 on Switch A is not available, the detailed information of VRRP group 1 on Switch A is displayed.
[SwitchA-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 400
Admin Status : Up State : Backup
Config Pri : 110 Running Pri : 80
Preempt Mode : Yes Delay Time : 5
Become Master : 4200ms left
Auth Type : Simple Key : ******
Virtual IP : FE80::10
1::10
Master IP : FE80::2
VRRP Track Information:
Track Interface: Vlan3 State : Down Pri Reduced : 30
# When interface VLAN-interface 3 on Switch A is not available, the detailed information of VRRP group 1 on Switch B is displayed.
[SwitchB-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 400
Admin Status : Up State : Master
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Auth Type : Simple Key : ******
Virtual IP : FE80::10
1::10
Virtual MAC : 0000-5e00-0201
Master IP : FE80::2
The output shows that when VLAN-interface 3 on Switch A is not available, the priority of Switch A is reduced to 80 and Switch A becomes the backup. Switch B becomes the master and packets sent from Host A to Host B are forwarded by Switch B.
VRRP with multiple VLANs configuration example
Network requirements
Switch A and Switch B belong to both VRRP group 1 and VRRP group 2. The virtual IPv6 addresses of VRRP group 1 are 1::10/64 and FE80::10, and those of VRRP group 2 are 2::10/64 and FE90::10.
Hosts in VLAN 2 learn 1::10/64 as their default gateway and hosts in VLAN 3 learn 2::10/64 as their default gateway through RA messages sent by the switches.
In VRRP group 1, Switch A has a higher priority than Switch B. In VRRP group 2, Switch B has a higher priority than Switch A. In this case, hosts in VLAN 2 and VLAN 3 can communicate with external networks through Switch A and Switch B, respectively, and when Switch A or Switch B fails, the hosts can use the other switch to communicate with external networks to avoid communication interruption.
Figure 18 Network diagram
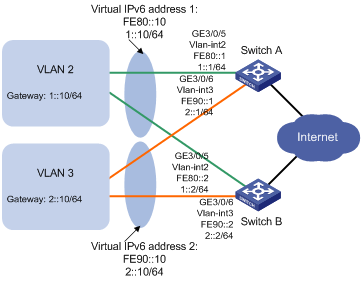
Configuration procedure
1. Configure Switch A:
# Configure VLAN 2.
<SwitchA> system-view
[SwitchA] ipv6
[SwitchA] vlan 2
[SwitchA-vlan2] port Gigabitethernet 3/0/5
[SwitchA-vlan2] quit
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] ipv6 address fe80::1 link-local
[SwitchA-Vlan-interface2] ipv6 address 1::1 64
# Create VRRP group 1 and set its virtual IPv6 addresses to FE80::10 to 1::10.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip fe80::10 link-local
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip 1::10
# Set the priority of Switch A in VRRP group 1 to 110, which is higher than that of Switch B (100), so that Switch A can become the master in VRRP group 1.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 priority 110
[SwitchA-Vlan-interface2] quit
# Enable Switch A to send RA messages, so that hosts in VLAN 2 can learn the default gateway address.
[SwitchA-Vlan-interface2] undo ipv6 nd ra halt
[SwitchA-Vlan-interface2] quit
# Configure VLAN 3.
[SwitchA] vlan 3
[SwitchA-vlan3] port Gigabitethernet 3/0/6
[SwitchA-vlan3] quit
[SwitchA] interface vlan-interface 3
[SwitchA-Vlan-interface3] ipv6 address fe90::1 link-local
[SwitchA-Vlan-interface3] ipv6 address 2::1 64
# Create VRRP group 2 and set its virtual IPv6 addresses to FE90::10 and 2::10.
[SwitchA-Vlan-interface3] vrrp ipv6 vrid 2 virtual-ip fe90::10 link-local
[SwitchA-Vlan-interface3] vrrp ipv6 vrid 2 virtual-ip 2::10
# Enable Switch A to send RA messages, so that hosts in VLAN 3 can learn the default gateway address.
[SwitchA-Vlan-interface2] undo ipv6 nd ra halt
2. Configure Switch B:
# Configure VLAN 2.
<SwitchB> system-view
[SwitchB] ipv6
[SwitchB-vlan2] port Gigabitethernet 3/0/5
[SwitchB-vlan2] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] ipv6 address fe80::2 link-local
[SwitchB-Vlan-interface2] ipv6 address 1::2 64
# Create VRRP group 1 and set its virtual IPv6 addresses to FE80::10 and 1::10.
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip fe80::10 link-local
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip 1::10
[SwitchB-Vlan-interface2] quit
# Enable Switch B to send RA messages, so that hosts in VLAN 2 can learn the default gateway address.
[SwitchB-Vlan-interface2] undo ipv6 nd ra halt
[SwitchB-Vlan-interface2] quit
# Configure VLAN 3.
[SwitchB] vlan 3
[SwitchB-vlan3] port Gigabitethernet 3/0/6
[SwitchB-vlan3] quit
[SwitchB] interface vlan-interface 3
[SwitchB-Vlan-interface3] ipv6 address fe90::2 link-local
[SwitchB-Vlan-interface3] ipv6 address 2::2 64
# Create VRRP group 2 and set its virtual IPv6 addresses to FE90::10 and 2::10.
[SwitchB-Vlan-interface3] vrrp ipv6 vrid 2 virtual-ip fe90::10 link-local
[SwitchB-Vlan-interface3] vrrp ipv6 vrid 2 virtual-ip 2::10
# Set the priority of Switch B in VRRP group 2 to 110, which is higher than that of Switch A (100), so that Switch B can become the master in VRRP group 2.
[SwitchB-Vlan-interface3] vrrp ipv6 vrid 2 priority 110
# Enable Switch B to send RA messages, so that hosts in VLAN 3 can learn the default gateway address.
[SwitchB-Vlan-interface3] undo ipv6 nd ra halt
3. Verify the configuration:
To verify the configuration, use the display vrrp ipv6 verbose command.
# Display the detailed information of the VRRP group on Switch A.
[SwitchA-Vlan-interface3] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 2
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 0
Auth Type : None
Virtual IP : FE80::10
1::10
Virtual MAC : 0000-5e00-0201
Master IP : FE80::1
Interface Vlan-interface3
VRID : 2 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 0
Become Master : 2200ms left
Auth Type : None
Virtual IP : FE90::10
2::10
Master IP : FE90::2
# Display the detailed information of the VRRP group on Switch B.
[SwitchB-Vlan-interface3] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Standard
Run Method : Virtual MAC
Total number of virtual routers : 2
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 0
Become Master : 2200ms left
Auth Type : None
Virtual IP : FE80::10
1::10
Master IP : FE80::1
Interface Vlan-interface3
VRID : 2 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 0
Auth Type : None
Virtual IP : FE90::10
2::10
Virtual MAC : 0000-5e00-0202
Master IP : FE90::2
The output shows that in VRRP group 1 Switch A is the master, Switch B is the backup and hosts with the default gateway of 1::10/64 accesses the Internet through Switch A; in VRRP group 2 Switch A is the backup, Switch B is the master and hosts with the default gateway of 2::10/64 accesses the Internet through Switch B.
|
|
NOTE: Multiple VRRP groups are commonly used in actual networking. In an IPv6 network, to implement load sharing among multiple VRRP groups, manually configure the default gateway for hosts. |
VRRP load balancing mode configuration example
Network requirements
Switch A, Switch B, and Switch C belong to VRRP group 1 with the virtual IPv6 addresses of FE80::10 and 1::10.
Hosts on network segment 1::/64 learn 1::10 as their default gateway through RA messages sent by the switches. Use the VRRP group to make sure that when a gateway (Switch A, Switch B, or Switch C) fails, the hosts on the LAN can access the external network through another gateway.
VRRP group 1 is operating in load balancing mode to make good use of network resources.
Configure a track entry on Switch A, Switch B, and Switch C to monitor their own VLAN-interface 3. When the interface on Switch A, Switch B, or Switch C fails, the weight of the corresponding switch decreases so that another switch with a higher weight can take over.
Figure 19 Network diagram
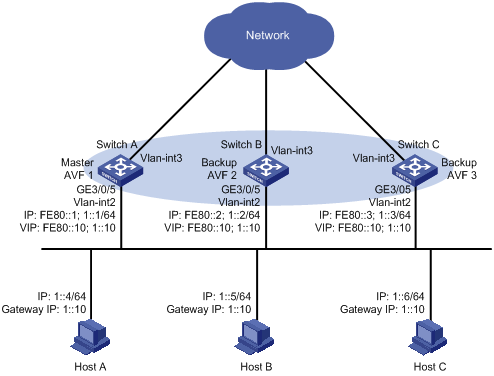
Configuration procedure
1. Configure Switch A:
# Configure VLAN 2.
<SwitchA> system-view
[SwitchA] vlan 2
[SwitchA-vlan2] port Gigabitethernet 3/0/5
[SwitchA-vlan2] quit
# Configure VRRP to operate in load balancing mode.
[SwitchA] vrrp mode load-balance
# Create VRRP group 1 and configure its virtual IPv6 addresses as FE80::10 and 1::10.
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] ipv6 address fe80::1 link-local
[SwitchA-Vlan-interface2] ipv6 address 1::1 64
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip fe80::10 link-local
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip 1::10
# Set the priority of Switch A in VRRP group 1 to 120, which is higher than that of Switch B (110) and that of Switch C (100), so that Switch A can become the master.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 priority 120
# Configure Switch A to operate in preemptive mode so that it can become the master whenever it works correctly; configure the preemption delay as 5 seconds to avoid frequent status switchover.
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 preempt-mode timer delay 5
# Enable Switch A to send RA messages so that hosts on network segment 1::/64 can learn the default gateway address.
[SwitchA-Vlan-interface2] undo ipv6 nd ra halt
[SwitchA-Vlan-interface2] quit
# Create track entry 1 to associate with the physical status of VLAN-interface 3 on Switch A. When the track entry becomes negative, it means that the interface fails.
[SwitchA] track 1 interface vlan-interface 3
# Configure VF tracking to monitor track entry 1 and specify the value by which the weight decreases, making the weight of Switch A decrease by more than 245 (250 in this example) when track entry 1 turns to negative. In such a case, another router with a higher weight can take over.
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] vrrp ipv6 vrid 1 weight track 1 reduced 250
2. Configure Switch B:
# Configure VLAN 2.
<SwitchB> system-view
[SwitchB] vlan 2
[SwitchB-vlan2] port Gigabitethernet 3/0/5
[SwitchB-vlan2] quit
# Configure VRRP to operate in load balancing mode.
[SwitchB] vrrp mode load-balance
# Create VRRP group 1 and configure its virtual IPv6 addresses as FE80::10 and 1::10.
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] ipv6 address fe80::2 link-local
[SwitchB-Vlan-interface2] ipv6 address 1::2 64
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip fe80::10 link-local
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip 1::10
# Set the priority of Switch B in VRRP group 1 to 110, which is higher than that of Switch C (100) so that Switch B can become the master when Switch A fails.
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 priority 110
# Set Switch B to operate in preemptive mode and set the preemption delay to 5 seconds.
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 preempt-mode timer delay 5
# Enable Switch B to send RA messages so that hosts on network segment 1::/64 can learn the default gateway address.
[SwitchB-Vlan-interface2] undo ipv6 nd ra halt
[SwitchB-Vlan-interface2] quit
# Create track entry 1 to associate with the physical status of VLAN-interface 3 on Switch B. When the track entry becomes negative, it means that the interface fails.
[SwitchB] track 1 interface vlan-interface 3
# Configure VF tracking to monitor track entry 1 and specify the value by which the weight decreases, making the weight of Switch B decrease by more than 245 (250 in this example) when track entry 1 turns to negative. In such a case, another router with a higher weight can take over.
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] vrrp ipv6 vrid 1 weight track 1 reduced 250
3. Configure Switch C:
# Configure VLAN 2.
<SwitchC> system-view
[SwitchC] vlan 2
[SwitchC-vlan2] port gigabitethernet 3/0/5
[SwitchC-vlan2] quit
# Configure VRRP to operate in load balancing mode.
[SwitchC] vrrp mode load-balance
# Create VRRP group 1 and configure its virtual IPv6 addresses as FE80::10 and 1::10.
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] ipv6 address fe80::3 link-local
[SwitchC-Vlan-interface2] ipv6 address 1::3 64
[SwitchC-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip fe80::10 link-local
[SwitchC-Vlan-interface2] vrrp ipv6 vrid 1 virtual-ip 1::10
# Set Switch C to operate in preemptive mode and set the preemption delay to 5 seconds.
[SwitchC-Vlan-interface2] vrrp ipv6 vrid 1 preempt-mode timer delay 5
# Enable Switch C to send RA messages, so that hosts on network segment 1::/64 can learn the default gateway address.
[SwitchC-Vlan-interface2] undo ipv6 nd ra halt
[SwitchC-Vlan-interface2] quit
# Create track entry 1 to associate with the physical status of VLAN-interface 3 on Switch C. When the track entry becomes negative, it means that the interface fails.
[SwitchC] track 1 interface vlan-interface 3
# Configure VF tracking to monitor track entry 1 and specify the value by which the weight decreases, making the weight of Switch C decrease by more than 245 (250 in this example) when track entry 1 turns to negative. In such a case, another router with a higher weight can take over.
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] vrrp ipv6 vrid 1 weight track 1 reduced 250
4. Verify the configuration:
After the configuration, Host A can ping the external network. To verify the configuration, use the display ipv6 vrrp verbose command.
# Display the detailed information of VRRP group 1 on Switch A.
[SwitchA-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 120 Running Pri : 120
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : FE80::10
1::10
Member IP List : FE80::1 (Local, Master)
FE80::2 (Backup)
FE80::3 (Backup)
Forwarder Information: 3 Forwarders 1 Active
Config Weight : 255
Running Weight : 255
Forwarder 01
State : Active
Virtual MAC : 000f-e2ff-4011 (Owner)
Owner ID : 0000-5e01-1101
Priority : 255
Active : local
Forwarder 02
State : Listening
Virtual MAC : 000f-e2ff-4012 (Learnt)
Owner ID : 0000-5e01-1103
Priority : 127
Active : FE80::2
Forwarder 03
State : Listening
Virtual MAC : 000f-e2ff-4013 (Learnt)
Owner ID : 0000-5e01-1105
Priority : 127
Active : FE80::3
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
# Display the detailed information of VRRP group 1 on Switch B.
[SwitchB-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 5
Become Master : 2200ms left
Auth Type : None
Virtual IP : FE80::10
1::10
Member IP List : FE80::2 (Local, Backup)
FE80::1 (Master)
FE80::3 (Backup)
Forwarder Information: 3 Forwarders 1 Active
Config Weight : 255
Running Weight : 255
Forwarder 01
State : Listening
Virtual MAC : 000f-e2ff-4011 (Learnt)
Owner ID : 0000-5e01-1101
Priority : 127
Active : FE80::1
Forwarder 02
State : Active
Virtual MAC : 000f-e2ff-4012 (Owner)
Owner ID : 0000-5e01-1103
Priority : 255
Active : local
Forwarder 03
State : Listening
Virtual MAC : 000f-e2ff-4013 (Learnt)
Owner ID : 0000-5e01-1105
Priority : 127
Active : FE80::3
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
# Display the detailed information of VRRP group 1 on Switch C.
[SwitchC-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Become Master : 4200ms left
Auth Type : None
Virtual IP : FE80::10
1::10
Member IP List : FE80::3 (Local, Backup)
FE80::1 (Master)
FE80::2 (Backup)
Forwarder Information: 3 Forwarders 1 Active
Config Weight : 255
Running Weight : 255
Forwarder 01
State : Listening
Virtual MAC : 000f-e2ff-4011 (Learnt)
Owner ID : 0000-5e01-1101
Priority : 127
Active : FE80::1
Forwarder 02
State : Listening
Virtual MAC : 000f-e2ff-4012 (Learnt)
Owner ID : 0000-5e01-1103
Priority : 127
Active : FE80::2
Forwarder 03
State : Active
Virtual MAC : 000f-e2ff-4013 (Owner)
Owner ID : 0000-5e01-1105
Priority : 255
Active : local
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
The output shows that in VRRP group 1, Switch A is the master and Switch B and Switch C are the backups. Each switch has one AVF and two LVFs acting as the backups.
# When VLAN interface 3 on Switch A fails, use the display vrrp ipv6 verbose command to display the detailed information of VRRP group 1 on Switch A.
[SwitchA-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 120 Running Pri : 120
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : FE80::10
1::10
Member IP List : FE80::1 (Local, Master)
FE80::2 (Backup)
FE80::3 (Backup)
Forwarder Information: 3 Forwarders 0 Active
Config Weight : 255
Running Weight : 5
Forwarder 01
State : Initialize
Virtual MAC : 000f-e2ff-4011 (Owner)
Owner ID : 0000-5e01-1101
Priority : 0
Active : FE80::3
Forwarder 02
State : Initialize
Virtual MAC : 000f-e2ff-4012 (Learnt)
Owner ID : 0000-5e01-1103
Priority : 0
Active : FE80::2
Forwarder 03
State : Initialize
Virtual MAC : 000f-e2ff-4013 (Learnt)
Owner ID : 0000-5e01-1105
Priority : 0
Active : FE80::3
Forwarder Weight Track Information:
Track Object : 1 State : Negative Weight Reduced : 250
# Use the display vrrp ipv6 verbose command to display the detailed information of VRRP group 1 on Switch C.
[SwitchC-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Become Master : 4200ms left
Auth Type : None
Virtual IP : FE80::10
1::10
Member IP List : FE80::3 (Local, Backup)
FE80::1 (Master)
FE80::2 (Backup)
Forwarder Information: 3 Forwarders 2 Active
Config Weight : 255
Running Weight : 255
Forwarder 01
State : Active
Virtual MAC : 000f-e2ff-4011 (Take Over)
Owner ID : 0000-5e01-1101
Priority : 85
Active : local
Redirect Time : 93 secs
Time-out Time : 1293 secs
Forwarder 02
State : Listening
Virtual MAC : 000f-e2ff-4012 (Learnt)
Owner ID : 0000-5e01-1103
Priority : 85
Active : FE80::2
Forwarder 03
State : Active
Virtual MAC : 000f-e2ff-4013 (Owner)
Owner ID : 0000-5e01-1105
Priority : 255
Active : local
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
The output shows that when VLAN interface 3 on Switch A fails, the weight of the AVF on Switch A decreases to 5, which is lower than the lower limit of failure. All VFs on Switch A turn to initialized state and cannot be used for packet forwarding. The VF corresponding to MAC address 000f-e2ff-4011 on Switch C becomes the AVF, and Switch C takes over Switch A for packet forwarding.
# When the timeout timer (about 1800 seconds) expires, display the detailed information of VRRP group 1 on Switch C.
[SwitchC-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 5
Become Master : 4200ms left
Auth Type : None
Virtual IP : FE80::10
1::10
Member IP List : FE80::3 (Local, Backup)
FE80::1 (Master)
FE80::2 (Backup)
Forwarder Information: 2 Forwarders 1 Active
Config Weight : 255
Running Weight : 255
Forwarder 02
State : Listening
Virtual MAC : 000f-e2ff-4012 (Learnt)
Owner ID : 0000-5e01-1103
Priority : 127
Active : FE80::2
Forwarder 03
State : Active
Virtual MAC : 000f-e2ff-4013 (Owner)
Owner ID : 0000-5e01-1105
Priority : 255
Active : local
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
The output shows that when the timeout timer expires, the VF corresponding to virtual MAC address 000f-e2ff-4011 is removed, and does not forward the packets destined for the MAC address any more.
# When Switch A fails, use the display vrrp ipv6 verbose command to display the detailed information of VRRP group 1 on Switch B.
[SwitchB-Vlan-interface2] display vrrp ipv6 verbose
IPv6 Standby Information:
Run Mode : Load Balance
Run Method : Virtual MAC
Total number of virtual routers : 1
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 5
Auth Type : None
Virtual IP : FE80::10
1::10
Member IP List : FE80::2 (Local, Master)
FE80::3 (Backup)
Forwarder Information: 2 Forwarders 1 Active
Config Weight : 255
Running Weight : 255
Forwarder 02
State : Active
Virtual MAC : 000f-e2ff-4012 (Owner)
Owner ID : 0000-5e01-1103
Priority : 255
Active : local
Forwarder 03
State : Listening
Virtual MAC : 000f-e2ff-4013 (Learnt)
Owner ID : 0000-5e01-1105
Priority : 127
Active : FE80::3
Forwarder Weight Track Information:
Track Object : 1 State : Positive Weight Reduced : 250
The output shows that when Switch A fails, Switch B becomes the master because its priority is higher than that of Switch C.
Troubleshooting VRRP
The screen frequently displays error prompts
Analysis
This error is probably caused by:
· Inconsistent configuration of the devices in the VRRP group.
· A device is attempting to send illegitimate VRRP packets.
Solution
· In the first case, modify the configuration.
· In the latter case, resort to non-technical measures.
Multiple masters are present in the same VRRP group
Analysis
· Multiple masters coexist for a short period: This is normal and requires no manual intervention.
· Multiple masters coexist for a long period: This is because devices in the VRRP group cannot receive VRRP packets, or the received VRRP packets are illegal.
Solution
Ping between these masters, and do the following:
· If the ping fails, check network connectivity.
· If the ping succeeds, check that their configurations are consistent in terms of number of virtual IP addresses, virtual IP addresses, advertisement interval, and authentication.
Frequent VRRP state transition
Analysis
The VRRP advertisement interval is set too short.
Solution
Increase the interval to sent VRRP advertisement or introduce a preemption delay.
