| Title | Size | Downloads |
|---|---|---|
| H3C S3600 Series Ethernet Switches Operation Manual-Release 1702(V1.01)-HTTPS Operation.pdf | 69.96 KB |
- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 49-HTTPS Operation | 69.96 KB |
Table of Contents
Associating the HTTPS Service with an SSL Server Policy
Associating the HTTPS Service with a Certificate Attribute Access Control Policy
Associating the HTTPS Service with an ACL
Displaying and Maintaining HTTPS
When configuring HTTPS, go to these sections for information you are interested in:
l HTTPS Configuration Task List
l Associating the HTTPS Service with an SSL Server Policy
l Associating the HTTPS Service with a Certificate Attribute Access Control Policy
l Associating the HTTPS Service with an ACL
l Displaying and Maintaining HTTPS
HTTPS Overview
The Secure HTTP (HTTPS) refers to the HTTP protocol that supports the Security Socket Layer (SSL) protocol.
The SSL protocol of HTTPS enhances the security of the device in the following ways:
l Uses the SSL protocol to ensure the legal clients to access the device securely and prohibit the illegal clients;
l Encrypts the data exchanged between the HTTPS client and the device to ensure the data security and integrity, thus realizing the security management of the device;
l Defines certificate attribute-based access control policy for the device to control the access right of the client, in order to further avoid attacks from illegal clients.
![]()
l The total number of HTTP connections and HTTPS connections on a device cannot exceed ten.
l For SSL details, refer to SSL Configuration.
HTTPS Configuration Task List
Complete these tasks to configure HTTPS:
|
Configuration task |
Remarks |
|
Required |
|
|
Required |
|
|
Associating the HTTPS Service with a Certificate Attribute Access Control Policy |
Optional |
|
Optional |
Associating the HTTPS Service with an SSL Server Policy
You need to associate the HTTPS service with a created SSL server policy before enabling the HTTPS service.
Follow these steps to associate the HTTPS service with an SSL server policy:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Associate the HTTPS service with an SSL server policy |
ip https ssl-server-policy policy-name |
Required Not associated by default |
![]()
l If the ip https ssl-server-policy command is executed repeatedly, the HTTPS service is only associated with the last specified SSL server policy.
l When the HTTPS service is enabled, no modification of its associated SSL server policy takes effect.
Enabling the HTTPS Service
The device can act as the HTTPS server and users can access and control the device through the Web function only when the HTTPS service is enabled.
Follow these steps to enable the HTTPS service:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the HTTPS service |
ip https enable |
Required Disabled by default. |
![]()
l After the HTTPS service is enabled, you can use the display ip https command to view the state of the HTTPS service and verify the configuration.
l Enabling of the HTTPS service will trigger an SSL handshake negotiation process. During the process, if the local certificate of the device already exists, the SSL negotiation is successfully performed, and the HTTPS service can be started normally. If no local certificate exists, a certificate application process will be triggered by the SSL negotiation. Since the application process takes much time, the SSL negotiation may fail and the HTTPS service cannot be started normally. Therefore, the ip https enable command must be executed for multiple times to ensure normal startup of the HTTPS service.
Associating the HTTPS Service with a Certificate Attribute Access Control Policy
Associating the HTTPS service with a configured certificate access control policy helps control the access right of the client, thus providing the device with enhanced security.
Follow these steps to associate the HTTPS service with a certificate attribute access control policy:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Associate the HTTPS service with a certificate attribute access control policy |
ip https certificate access-control-policy policy-name |
Required Not associated by default. |
![]()
l If the ip https certificate access-control-policy command is executed repeatedly, the HTTPS server is only associated with the last specified certificate attribute access control policy.
l If the HTTPS service is associated with a certificate attribute access control policy, the client-verify enable command must be configured in the SSL server policy. Otherwise, the client cannot log onto the device.
l If the HTTPS service is associated with a certificate attribute access control policy, the latter must contain at least one permit rule. Otherwise, no HTTPS client can log onto the device.
Associating the HTTPS Service with an ACL
Associating the HTTPS service with an ACL can filter out requests from some clients to let pass only clients that pass the ACL filtering.
Follow these steps to associate the HTTPS service with an ACL:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Associate the HTTPS service with an ACL |
ip https acl acl-number |
Required Not associated by default. |
Displaying and Maintaining HTTPS
|
To do… |
Use the command… |
Remarks |
|
Display information about HTTPS |
display ip https |
Available in any view |
HTTPS Configuration Example
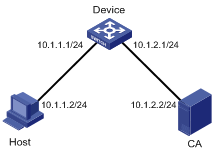
Network requirements
l Host acts as the HTTPS client and Device acts as the HTTPS server.
l Host accesses Device through Web to control Device.
l CA (Certificate Authority) issues certificate to Device. The common name of CA is new-ca.
![]()
In this configuration example, Windows Server serves as CA and you need to install Simple Certificate Enrollment Protocol (SCEP) component.
Figure 1-1 Network diagram for HTTPS configuration
Configuration procedure
Perform the following configurations on Device:
1) Apply for a certificate for Device
# Configure a PKI entity.
<Device> system-view
[Device] pki entity en
[Device-pki-entity-en] common-name http-server1
[Device-pki-entity-en] fqdn ssl.security.com
[Device-pki-entity-en] quit
# Configure a PKI domain.
[Device] pki domain 1
[Device-pki-domain-1] ca identifier new-ca
[Device-pki-domain-1] certificate request url http://10.1.2.2:8080/certsrv/mscep/mscep.dll
[Device-pki-domain-1] certificate request from ra
[Device-pki-domain-1] certificate request entity en
[Device-pki-domain-1] quit
# Generate a local RSA key pair.
[Device] public-key local create rsa
# Obtain a server certificate from CA.
[Device] pki retrieval-certificate ca domain 1
# Apply for a local certificate.
[Device] pki request-certificate domain 1
2) Configure an SSL server policy associated with the HTTPS service
# Configure an SSL server policy.
[Device] ssl server-policy myssl
[Device-ssl-server-policy-myssl] pki-domain 1
[Device-ssl-server-policy-myssl] client-verify enable
[Device-ssl-server-policy-myssl] quit
3) Configure a certificate access control policy
# Configure a certificate attribute group.
[Device] pki certificate attribute-group mygroup1
[Device-cert-attribute-group-mygroup1] attribute 1 issuer-name dn ctn new-ca
[Device-cert-attribute-group-mygroup1] quit
# Configure certificate access control policy myacp and create a control rule.
[Device] pki certificate access-control-policy myacp
[Device-pki-cert-acp-myacp] rule 1 permit mygroup1
[Device-pki-cert-acp-myacp] quit
4) Reference an SSL server policy
# Associate the HTTPS service with the SSL server policy myssl.
[Device] ip https ssl-server-policy myssl
5) Associate the HTTPS service with a certificate attribute access control policy
# Associate the HTTPS service with certificate attribute access control policy myacp.
[Device] ip https certificate access-control-policy myacp
6) Enable the HTTPS service
# Enable the HTTPS service.
[Device] ip https enable
7) Verify the configuration
Launch the IE explorer on Host, and enter https://10.1.1.1. You can log in to Device and control it.
![]()
l The URL of the HTTPS server starts with https://,
l For details of PKI commands, refer to PKI Commands.
l For details of SSL commands, refer to SSL Commands.

