- Released At: 29-03-2021
- Page Views:
- Downloads:
- Table of Contents
- Related Documents
-
|
|
|
|
|
H3C HDM |
|
Security Technology White Paper |
|
|
Copyright © 2021 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Overview
HDM meets the functional requirements of users, and externally exports the security support of server hardware. In addition, HDM improves its own security to meet the needs for the security of the management channel in various scenarios.
For support of hardware security features, a corresponding user interface is provided for the security features supported by the hardware of each specific server. Thus, the users can view the support status, operation log, and enable the related features.
For HDM, the security of server management operations is guaranteed from several dimensions such as access mode, account management, transmission link encryption, data storage, and operation audit.
Server hardware security
Server intrusion monitoring
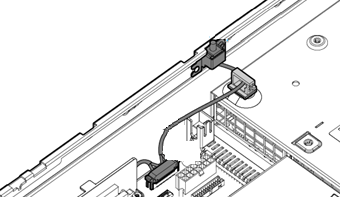
As shown in Figure 1, the chassis-open alarm module triggers a signal every time the access panel is removed. Then, the software receives the signal sent by the hardware GPIO pin, triggers a software interrupt, and then determines whether the access panel is removed. When the access panel is removed, the sensor monitors a server intrusion event, and an event log entry is generated to record the event.
Figure 1 Chassis-open alarm module on the server chassis
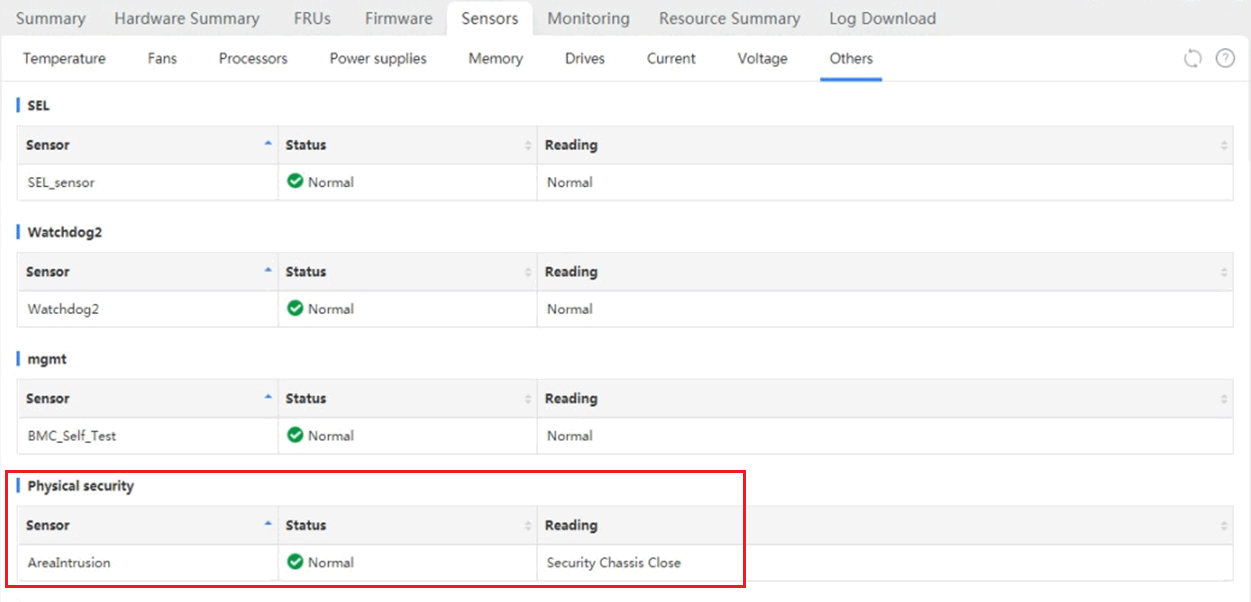
You can view the sensor reading on the HDM Web interface to identify that the access panel was opened or closed, as shown in Figure 2.
Figure 2 Viewing the sensor reading for server intrusion events
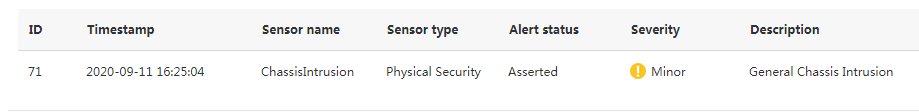
When the access pane was opened, an event log entry is generated on HDM, as shown in Figure 3.
Figure 3 Viewing event log entries
In addition, HDM supports reporting an server intrusion event through SNMP traps and emails.
Trusted computing
Virus programs embed the virus code into the execution code to realize virus transmission by making use of the operating system's weakness of not checking the consistency of the execution code. Then, hackers use the vulnerabilities of the attacked system to steal super user permissions and install malicious programs for attacks. The most serious thing is that the system has no strict access control over legitimate users, and unauthorized access might cause security issues.
To solve the previous problems, in October 1999, a number of IT companies jointly initiated the Trusted Computing Platform Alliance (TCPA), which was later re-organized into the Trusted Computing Group (TCG). This is an effort to formulate the standards and specifications for reliable computers in terms of both hardware and software in the cross-platform and operating environment.
A Trusted Platform Module (TPM) must be secure itself, and have various functions required for a trusted computing platform and remote authentication, which is the core of the TPM.
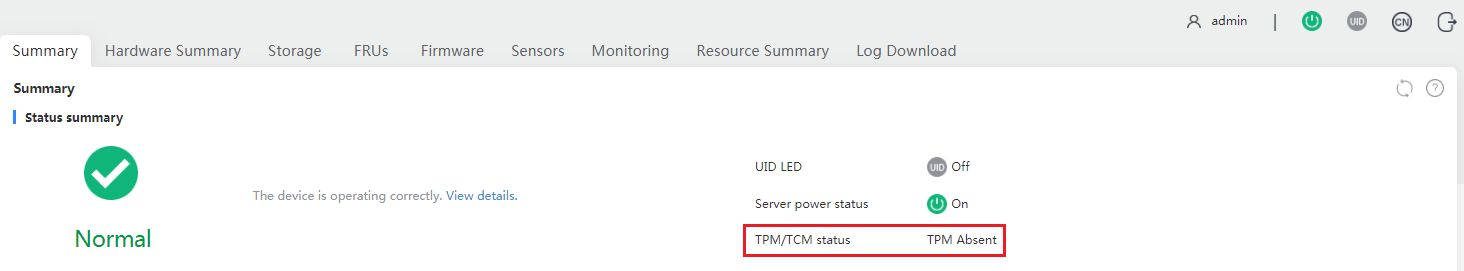
A trusted computing platform requires the support of microchips, firmware, and software. For H3C servers, both TPM and TCM modules are available. In terms of software, you can identify the enablement status of TPM/TCM from HDM, as shown in Figure 4.
Figure 4 Identifying the enablement status of TPM/TCM
Different places might use different standards based on security policies. For example, Hong Kong, China uses the standard TPM protocol.
Due to compatibility limitations, different functional modules might require different standards. For example, the BitLocker and virtual smart card feature of the Windows operating system is available only with the TPM.
Firmware security
Firmware has a vital influence on the normal operation of the system. Once the firmware is damaged, the system might become abnormal or even fail to start. To ensure firmware security, the following mechanisms are provided:
· HDM supports one primary firmware image and one backup firmware image. When a flash misoperation or storage block damage occurs, you can perform an image switchover to run HDM with the backup image.
· All released HDM and BIOS firmware versions have a signature mechanism. When the firmware is packaged, the SHA256 algorithm is used for digest calculation, and RSA2048 is used to encrypt the digest. When you upgrade the firmware, signature verification is used to avoid tampering. Only the firmware with the required signature can be upgraded on the device.
· When HDM is running, write protection is enabled on the running image, and a special method is required for write operations. In addition, upon HDM start, the system checks the integrity of the image files. If the image files are corrupt, the system can recover the image files as needed.
HDM security
As a best practice, access HDM in an independent private network. Because many privileged operations can be performed from HD such as server power-on and power-off, remote device access, BIOS editing, and firmware update. If you access HDM from a public network, make sure the access IP addresses are under the strictly control through a firewall.
Threats might be present even in a private network. Thus, HDM provides multiple access modes for users, balancing the performance, ease of use, and the security of related functions.
Management interfaces
All management interfaces must pass authentication before accessing relevant management information.
IPMI 1.5 and IPMI 2.0 management interfaces
HDM is compatible with IPMI 1.5 and IPMI 2.0 standards. It can effectively manage a server by using a third-party tool, such as IPMITool, through the LPC-based KCS or LAN-based UDP or IP.
· If LPC-based KCS is used, the third-party tool must operate on the OS of the server.
· If LAN-based UDP or IP is used, the third-party tool can remotely manage the server and support RMCP+ authentication.
HTTPS management interface
HDM uses HTTPS-based Web interfaces, which can protect your data from prying eyes. TLSv1.0, TLSv1.1, and TLSv1.2 are supported, and the following cipher suites are available: RSA_WITH_AES_128_CBC_SHA256, RSA_WITH_AES_256_CBC_SHA256, RSA_WITH_CAMELLIA_256_CBC_SHA, RSA_WITH_AES_128_GCM_SHA256, and RSA_WITH_AES_256_GCM_SHA384.
SNMP management interface
SNMP supports SNMPv3, and provides authentication and encryption mechanisms and uses the user-based access control function in SNMPv3 for security enhancement.
Redfish management interface
To access HDM through Redfish APIs, you must pass the session authentication. The relevant data is transmitted over the SSL link.
Link security
In addition to the previous standard management interfaces, HDM also has some links for data transmission, such as KVM, virtual media, and VNC. These links also support data transmission through encryption.
KVM
KVM allows you to monitor and control remote devices in real time by using the local client. You can operate remote devices through KVM.
To ensure that the server information connected to the user is not leaked, the data during the interaction process is not monitored, and the KVM channel supports encrypted communication for data transmission.
H5 KVM supports single port authentication. The KVM and virtual media-related functions are realized uniformly through the Web service port, which can reduce the use of the external Web interfaces to improve security.
Virtual media
The virtual media feature allows you to use a virtual USB DVD-ROM drive or a floppy disk drive to remotely access the local media over the network. The local media might be the DVD-ROM drive, floppy disk drive, DVD-ROM image file, floppy disk image file, or hard drive folder. To use virtual media is to virtualize the media devices on the local client to the media devices on the remote server over the network.
The following virtual storage media are available:
· CD/DVD drives.
· Floppy disk drives.
· ISO files and IMG files.
· Virtual folders.
· USB keys.
To prevent data from being monitored on the link when you access virtual media, H5 KVM applies the same encryption method as HTTPS for data transmission. The virtual media data can be encrypted by using the aes128-cbc encryption algorithm based on implementation of OpenJDK.
VNC
Virtual Network Console (VNC) transmits the original images of the server to the client. VNC allows you to access and manage the server from a local PC without logging in to HDM.
For the VNC client to connect to the VNC server, the IPv4 or IPv6 address of the remote server and the VNC password are required. The authentication process is as follows:
1. The server sends a 16-byte random code to the client.
2. The client uses the VNC password as the KEY, encrypts the random code through DES encryption, and then sends it to the server for verification.
During the access process, you can decide whether to encrypt the data over the link according to the selected connection type.
Some versions of HDM support the following secure VNC connection types:
· VNC over SSH—Data is transmitted through an SSH tunnel.
· VNC over stunnel—Data is transmitted through the TLS/SSL channel established by the stunnel program.
Operation and audit records
The operation log includes audit log entries, configuration log entries, firmware update log entries, and hardware update log entries.
· Audit log entries record HDM administrative events, including access to HDM and remote console startup.
· Configuration log entries record user configuration operations as well as their results.
· Firmware update log entries record HDM firmware updates as well as their results.
· Hardware update log entries record hardware updates as well as their results.
You can obtain information about user login, hardware replacement, and configuration changes from the operation log. Thus, the operations on the device can be audited and tracked.
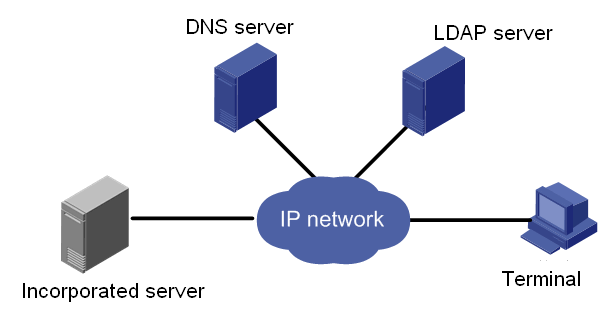
Domain management and directory service
Domain management
You can add all managed servers to a management domain and access HDM of a server by using the domain name. Domain management can manage user accounts in a convenient and centralized way with higher security. It is conducive to the management of confidential information and greatly improves the efficiency of user management. Domains provide a single login process for users to access network resources. A domain determines that only users with legal privileges to specific resources can access the resources by assigning user permissions, thereby ensuring the legality and safety of resource use.
LDAP directory service
Lightweight Directory Access Protocol (LDAP) enables you to efficiently access online directory services over an IP network. You can save multiple types of data, such as email addresses and email routing information in LDAP directories, and filter them in a convenient and centralized way.
As shown in Figure 5, enabling LDAP directory service centralizes user, permission, and validity period management to the LDAP server, which reduces duplicate configuration, improves management efficiency, and improves system security.
You can customize user permissions in LDAP user role groups. Combined with domain user management of domain controllers, you can configure different access permissions for different users, which improves HDM security.
Figure 5 LDAP directory service diagram
LDAP provides the following advantages:
· High scalability—Dynamically adds users on the LDAP server for all HDMs at the same time.
· Enhanced security—Implements the user password policies on the LDAP server. SSL encryption is supported.
· Real-time performance—Applies user account update on the LDAP server to all HDMs immediately.
· Improved efficiency—Integrates user management for HDM, which minimizes repeated user configuration tasks and improves management efficiency.
AD directory service
Active Directory (AD) is a directory service developed for the Windows Server operating system. The directory service integrates organization and management of and access to network resources, making the network topology and protocols transparent to users.
The AD service is implemented based on domains, which can support expansion as an enterprise grows.
HDM supports AD authentication. AD authentication enables users to access HDM by using the username and password of user accounts in a valid AD group configured on the AD server. The privileges of a user account depends on the network privileges of the AD group to which the user account belongs.
Firewall
HDM supports firewall features to implement scenario-based login management for security. HDM can control the server management interface access to a minimum in terms of time, IP address and IP version (IPv4 or IPv6), MAC, port, and transmission protocol (TCP/UDP). The firewall feature is available for login control on the Web, SSH, SNMP v1/v2c/v3, and IPMI LAN interfaces.
You can create whitelist rules for the firewall. A login attempt can succeed only when a whitelist rule is matched. The firewall rules apply to all local users and LDAP user groups.
User account security
You can enhance HDM access security by setting rules that the passwords of user accounts must follow in the password policy.
Procedure
1. In the navigation pane, select Configuration > User Accounts.
2. In the work pane, click Settings.
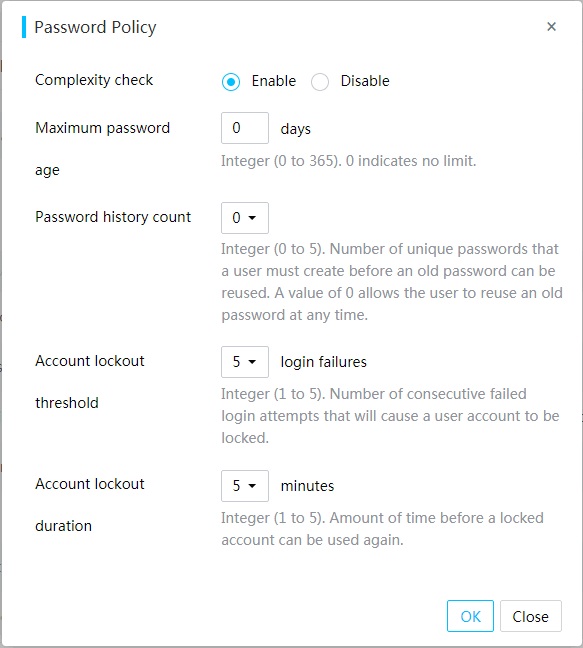
3. In the dialog box that opens, configure the password policy, and then click OK, as shown in Figure 6.
Figure 6 Configuring the password policy
Parameters
· Complexity check: Disable or enable password complexity check.
¡ If this feature is enabled, passwords must meet the following enhanced complexity requirements:
- 8 to 20 characters in length.
- Case sensitive. Valid characters are letters, digits, spaces, and the following special characters: ` ~ ! @ # $ % ^ & * ( ) _ + - = [ ] \ { } | ; ' : " , . / < > ?
- Must contain characters from at least two of the following categories: uppercase letters, lowercase letters, and digits.
- Must contain at least one space or special character.
- Cannot be identical to the username or the reverse of the username.
- Must meet the old password reuse requirement.
· Maximum password age: Maximum number of days that a password can be used. When a password is about to expire, HDM prompts the user to change the password.
· Password history count: Number of unique passwords that a user must create before an old password can be reused.
· Account lockout threshold: Number of consecutive login failures that will cause a user account to be locked.
· Account lockout duration: Amount of time before a locked account can be used again.
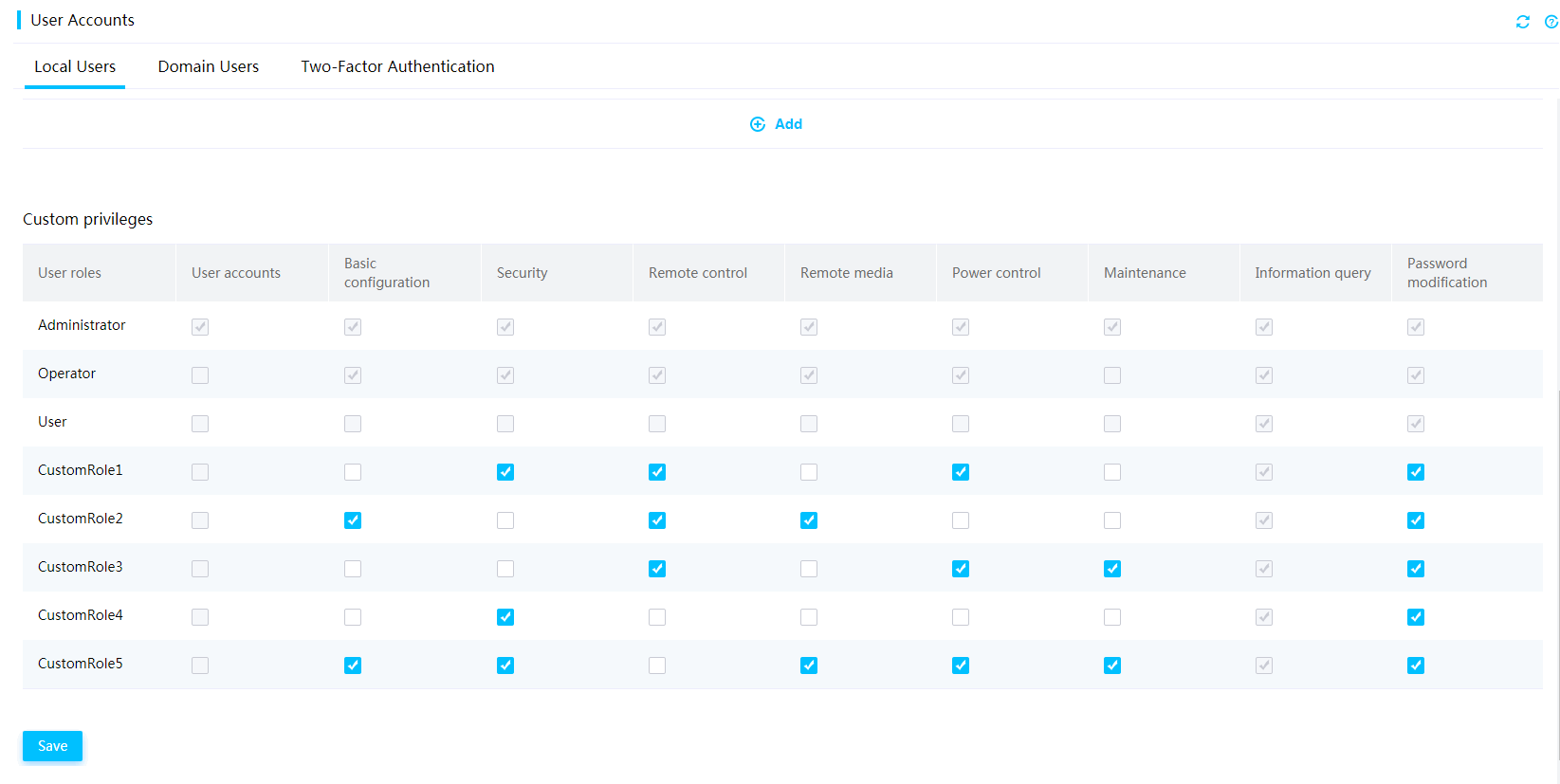
User privileges
To meet the requirements for security, you can configure a user role and customize the extended privileges for a user account as needed. Available user roles include Administrator, Operator, and User. You can disable a user account or part of user privileges through the IPMI interface, Redfish interface, or Web interface. For example, you can select the KVM, VMedia, Web, IPMI, and SNMP access privileges as needed.
You can configure user accounts, including local users, LDAP users, and AD groups, to control access to HDM on the User Accounts page.
The network access privileges of a user is determined by the user role. Available user roles include:
· Administrator—The user has read and write permissions to all features.
· Operator—The user has read permission to all features and has write permission to some features.
· User—The user has read-only permission.
· CustomRoleN—The user has the privileges specified for the custom role by an administrator user. The system supports a maximum of five custom user roles.
Figure 7 Configuring privileges for custom users
HDM improves security by dividing features and interfaces, such as Redfish and IPMI interfaces, into different modules for network access privileges. Available modules include user accounts, basic configuration, remote console, remote media, security, power control, maintenance, password modification, and information query.
SSL certificate
You can generate and upload an SSL certificate to HDM to replace the default certificate and private key.
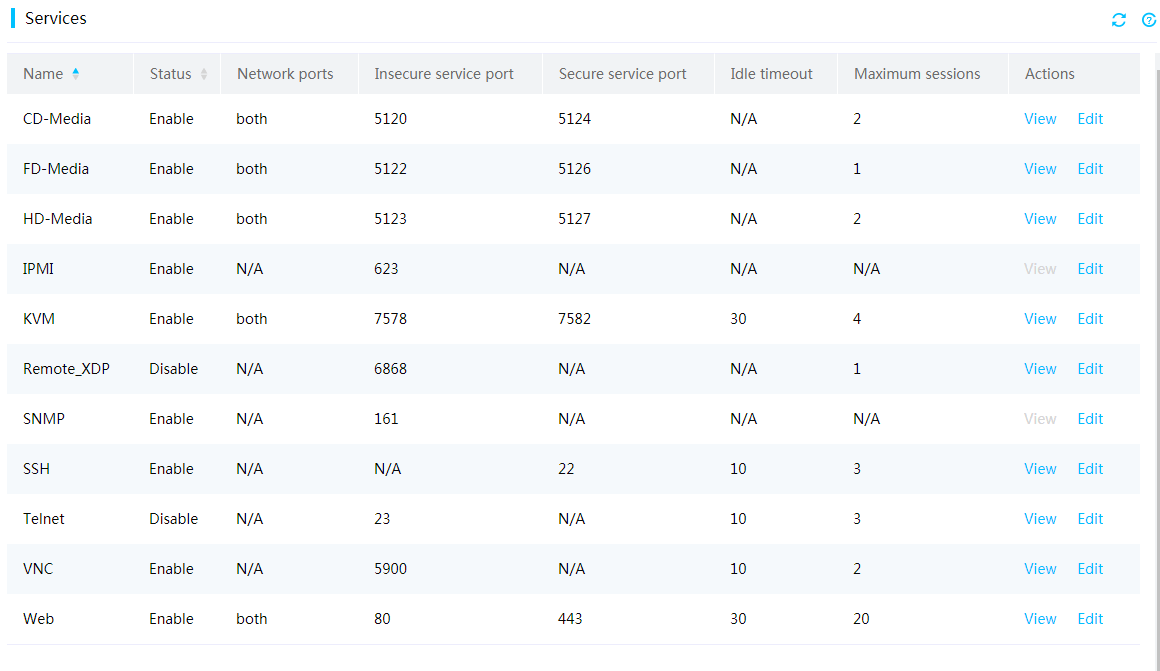
Access services
To meet service and security requirements, HDM allows users to control the enablement status of the following services: CD-Media, FD-Media, HD-Media, IPMI, KVM, Remote_XDP, SNMP, SSH, Telnet, Web, and VNC.
Figure 8 Configuring access services
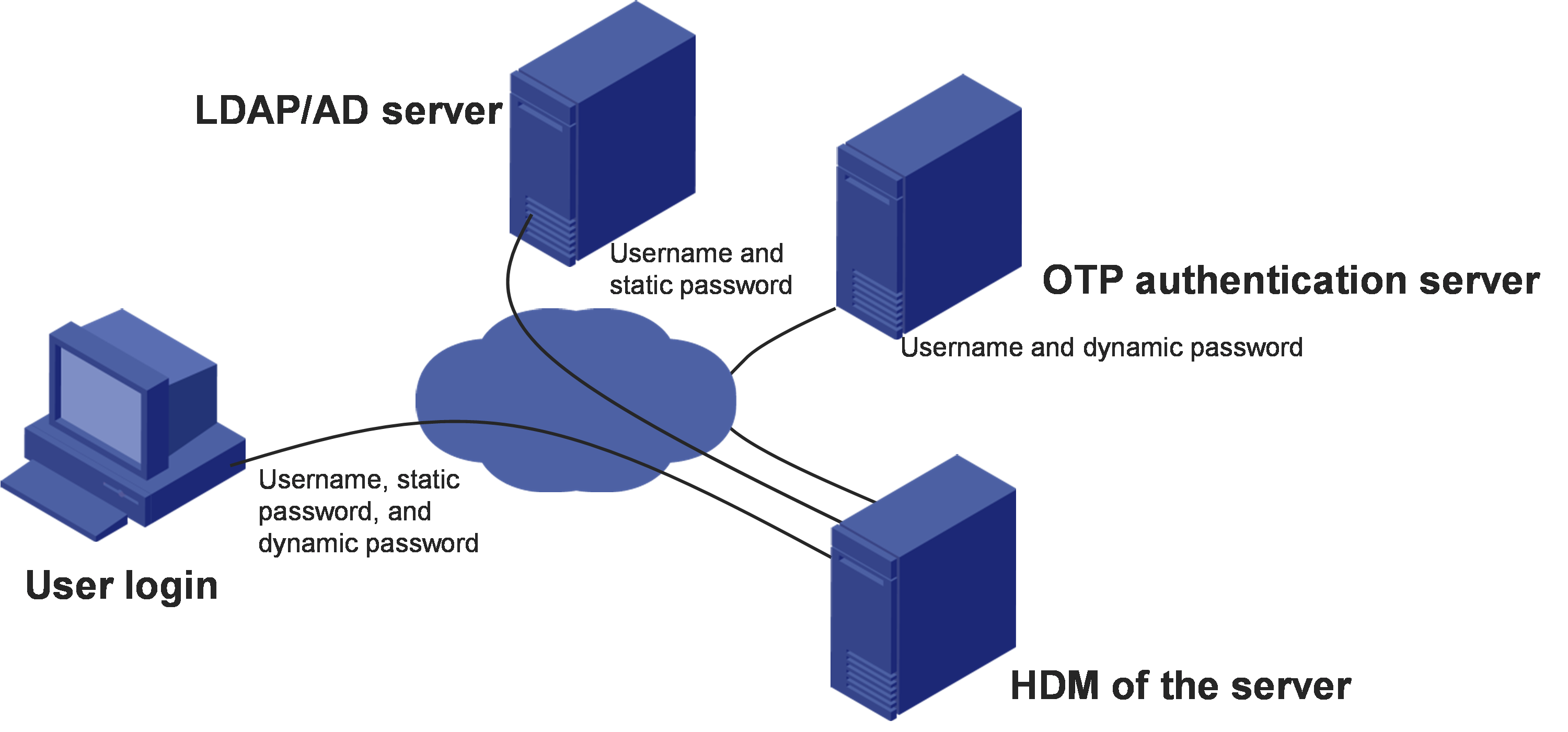
Two-factor authentication
Two-factor authentication requires a static password and a dynamic password for each login attempt to provide enhanced network security.
HDM supports DKEY token and can collaborate with a one-time password (OTP) server to provide two-factor authentication for user login. The DKEY token also supports the GM algorithm and has obtained the certification for the GM algorithm. With this feature configured, a user must enter the correct username, static password, and dynamic password obtained from a mobile phone or hardware token to log in to HDM. The static password must pass authentication on the OTP server.
Figure 9 Network diagram for two-factor authentication
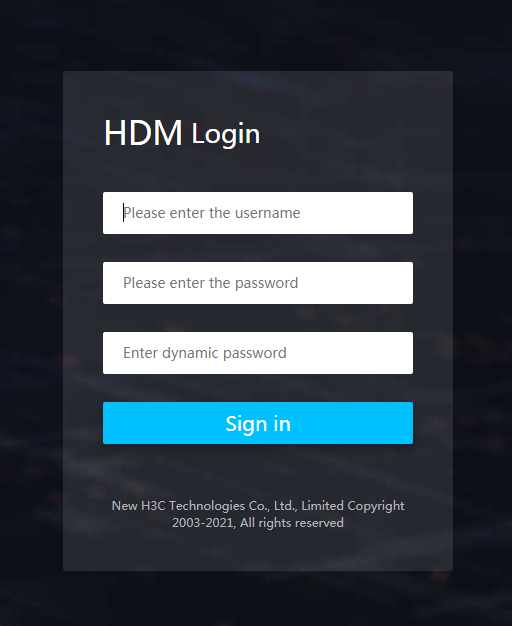
After two-factor authentication is enabled, the HDM login page will add an input box for dynamic passwords, as shown in Figure 10.
Figure 10 HDM login page for two-factor authentication
The Web and Telnet services support two-factor authentication.
Use two-factor authentication with caution. Enabling two-factor authentication will disable some interfaces and services, such as SSH, VNC, IPMI, SNMPv3, and Redfish.
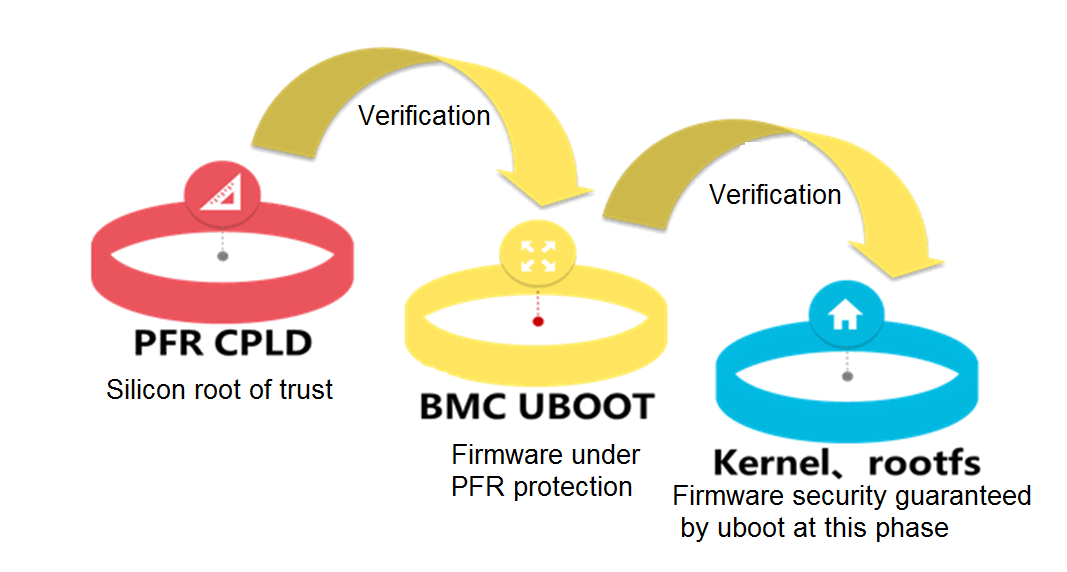
Silicon root of trust
Intel Platform Firmware Resiliency (PFR) improves the reliability of system security by providing firmware protection and inspection.
Intel PFR places the root of trust (RoT) on PFR CPLD for the Intel Xeon processors and the system, and uses the silicon RoT for HDM uboot verification. HDM uboot further performs verification on HDM firmware for trusted system security.
Figure 11 Intel PFR mechanism
Hardware encryption
HDM's SoC supports hardware security acceleration, which enhances the performance of security related functions. The acceleration module primarily applies to authentication and data encryption and decryption. It supports the following algorithms: AES, DES, 3DES, RC4, MD5, SHA1, SHA224, SHA256, HMAC-MD5, HMAC-SHA1, HMAC-SHA224, and HMAC-SHA256.