- Table of Contents
-
- 07-Layer 3—IP Services Configuration Guide
- 00-Preface
- 01-ARP configuration
- 02-IP addressing configuration
- 03-DHCP configuration
- 04-DNS configuration
- 05-HTTP configuration
- 06-IP forwarding basics configuration
- 07-Fast forwarding configuration
- 08-Adjacency table configuration
- 09-IRDP configuration
- 10-IP performance optimization configuration
- 11-UDP helper configuration
- 12-IPv6 basics configuration
- 13-IPv6 neighbor discovery configuration
- 14-DHCPv6 configuration
- 15-IPv6 fast forwarding configuration
- 16-WAAS configuration
- 17-HTTP redirect configuration
- 18-Web caching configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-ARP configuration | 404.45 KB |
Configuring a static ARP entry
Configuring a short static ARP entry
Configuring a long static ARP entry
Configuring features for dynamic ARP entries
Setting the dynamic ARP learning limit for a device
Setting the dynamic ARP learning limit for an interface
Setting the aging timer for dynamic ARP entries
Setting the maximum number of probes for dynamic ARP entries
Setting the interval for probing dynamic ARP entries
Enabling dynamic ARP entry check
Performing ARP entry synchronization
Configuring a customer-side or network-side port
Enabling an IP unnumbered interface to learn ARP entries for different subnets
Enabling unique ARP entry learning for IP addresses
Enabling recording user IP address conflicts
Enabling interface consistency check between ARP and MAC address entries
Enabling recording user port migrations
Displaying brief ARP log information
Example: Configuring a long static ARP entry
Example: Configuring a short static ARP entry
Gratuitous ARP packet learning
Periodic sending of gratuitous ARP packets
Gratuitous ARP tasks at a glance
Enabling IP conflict notification
Enabling gratuitous ARP packet learning
Enabling periodic sending of gratuitous ARP packets
Configuring gratuitous ARP packet retransmission for the device MAC address change
Verifying and maintaining proxy ARP
Common proxy ARP configuration example
Example: Configuring common proxy ARP
Verifying and maintaining ARP PnP
ARP PnP configuration examples
Display and maintenance commands for ARP suppression
ARP suppression configuration example
Example: Configuring ARP suppression
Configuring ARP direct route advertisement
About ARP direct route advertisement
Mechanism of ARP direct route advertisement
Application in Layer 3 access networks
Enabling ARP direct route advertisement
Displaying the direct routes generated based on ARP entries
Disabling sending ARP requests when data packets trigger ARP resolution
About disabling sending ARP requests when data packets trigger ARP resolution
Disabling sending ARP requests when data packets trigger ARP resolution
Configuring ARP ping for IPv4 addresses
Configuring ARP ping for MAC addresses
Configuring ARP
About ARP
ARP resolves IP addresses into MAC addresses on Ethernet networks.
ARP message format
ARP uses two types of messages: ARP request and ARP reply. Figure 1 shows the format of ARP request/reply messages. Numbers in the figure refer to field lengths.
· Hardware type—Hardware address type. The value 1 represents Ethernet.
· Protocol type—Type of the protocol address to be mapped. The hexadecimal value 0x0800 represents IP.
· Hardware address length and protocol address length—Length, in bytes, of a hardware address and a protocol address. For an Ethernet address, the value of the hardware address length field is 6. For an IPv4 address, the value of the protocol address length field is 4.
· OP—Operation code, which describes the type of ARP message. The value 1 represents an ARP request, and the value 2 represents an ARP reply.
· Sender hardware address—Hardware address of the device sending the message.
· Sender protocol address—Protocol address of the device sending the message.
· Target hardware address—Hardware address of the device to which the message is being sent.
· Target protocol address—Protocol address of the device to which the message is being sent.
ARP operating mechanism
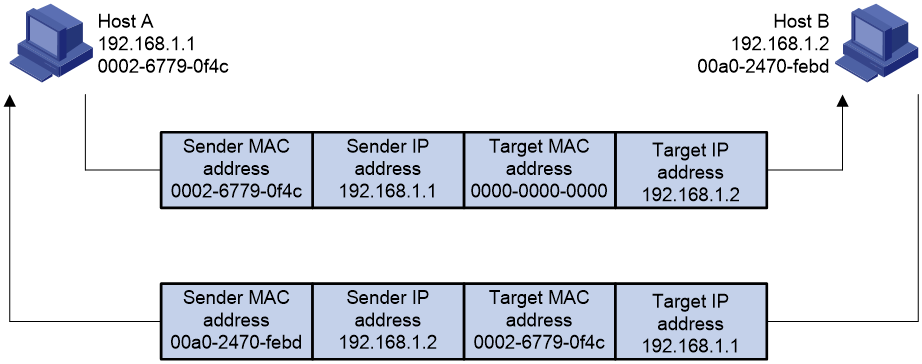
As shown in Figure 2, Host A and Host B are on the same subnet. Host A sends a packet to Host B as follows:
1. Host A looks through the ARP table for an ARP entry for Host B. If one entry is found, Host A uses the MAC address in the entry to encapsulate the IP packet into a data link layer frame. Then Host A sends the frame to Host B.
2. If Host A finds no entry for Host B, Host A buffers the packet and broadcasts an ARP request. The payload of the ARP request contains the following information:
¡ Sender IP address and sender MAC address—Host A's IP address and MAC address.
¡ Target IP address—Host B's IP address.
¡ Target MAC address—An all-zero MAC address.
All hosts on this subnet can receive the broadcast request, but only the requested host (Host B) processes the request.
3. Host B compares its own IP address with the target IP address in the ARP request. If they are the same, Host B operates as follows:
a. Adds the sender IP address and sender MAC address into its ARP table.
b. Encapsulates its MAC address into an ARP reply.
c. Unicasts the ARP reply to Host A.
4. After receiving the ARP reply, Host A operates as follows:
a. Adds the MAC address of Host B into its ARP table.
b. Encapsulates the MAC address into the packet and sends the packet to Host B.
Figure 2 ARP address resolution process
If Host A and Host B are on different subnets, Host A sends a packet to Host B as follows:
1. Host A broadcasts an ARP request where the target IP address is the IP address of the gateway.
2. The gateway responds with its MAC address in an ARP reply to Host A.
3. Host A uses the gateway's MAC address to encapsulate the packet, and then sends the packet to the gateway.
4. If the gateway has an ARP entry for Host B, it forwards the packet to Host B directly. If not, the gateway broadcasts an ARP request, in which the target IP address is the IP address of Host B.
5. After the gateway gets the MAC address of Host B, it sends the packet to Host B.
ARP entry types
An ARP table stores dynamic ARP entries, OpenFlow ARP entries, Rule ARP entries, and static ARP entries.
Dynamic ARP entry
ARP automatically creates and updates dynamic entries. A dynamic ARP entry is removed when its aging timer expires or the output interface goes down. In addition, a dynamic ARP entry can be overwritten by a static ARP entry.
Static ARP entry
A static ARP entry is manually configured and maintained. It does not age out and cannot be overwritten by any dynamic ARP entry.
Static ARP entries protect communication between devices because attack packets cannot modify the IP-to-MAC mapping in a static ARP entry.
The device supports the following types of static ARP entries:
· Long static ARP entry—It is directly used for forwarding packets. A long static ARP entry contains the IP address, MAC address, and one of the following combinations:
¡ VLAN and output interface.
¡ Input and output interfaces.
· Short static ARP entry—It contains only the IP address and MAC address.
If the output interface is a Layer 3 Ethernet interface, the short ARP entry can be directly used to forward packets.
If the output interface is a VLAN interface, the device sends an ARP request whose target IP address is the IP address in the short entry. If the sender IP and MAC addresses in the received ARP reply match the short static ARP entry, the device performs the following operations:
¡ Adds the interface that received the ARP reply to the short static ARP entry.
¡ Uses the resolved short static ARP entry to forward IP packets.
To communicate with a host by using a fixed IP-to-MAC mapping, configure a short static ARP entry on the device. To communicate with a host by using a fixed IP-to-MAC mapping through an interface in a VLAN, configure a long static ARP entry on the device.
OpenFlow ARP entry
ARP creates OpenFlow ARP entries by learning from the OpenFlow module. An OpenFlow ARP entry does not age out, and it cannot be updated. An OpenFlow ARP entry can be used directly to forward packets. For more information about OpenFlow, see OpenFlow Configuration Guide.
Rule ARP entry
Rule ARP entries can be directly used for packet forwarding. A Rule ARP entry does not age out, and it cannot be updated. It can be overwritten by a static ARP entry.
ARP creates Rule ARP entries by learning from the following modules:
· Portal. For more information about portal, see Security Configuration Guide.
· VXLAN. For more information about VXLAN, see VXLAN Configuration Guide.
· OVSDB. For more information about OVSDB, see VXLAN configuration in VXLAN Configuration Guide.
ARP tasks at a glance
All ARP tasks are optional.
· Configuring a static ARP entry
¡ Configuring a short static ARP entry
¡ Configuring a long static ARP entry
· Configuring features for dynamic ARP entries
¡ Setting the dynamic ARP learning limit for a device
¡ Setting the dynamic ARP learning limit for an interface
¡ Setting the aging timer for dynamic ARP entries
¡ Setting the maximum number of probes for dynamic ARP entries
¡ Setting the interval for probing dynamic ARP entries
¡ Enabling dynamic ARP entry check
· Performing ARP entry synchronization
· Configuring a customer-side or network-side port
· Enabling an IP unnumbered interface to learn ARP entries for different subnets
· Enabling unique ARP entry learning for IP addresses
· Enabling recording user IP address conflicts
· Enabling interface consistency check between ARP and MAC address entries
· Enabling recording user port migrations
Configuring a static ARP entry
Static ARP entries are effective when the device functions correctly.
Configuring a short static ARP entry
Restrictions and guidelines
A resolved short static ARP entry becomes unresolved upon certain events, for example, when the resolved output interface goes down, or the corresponding VLAN or VLAN interface is deleted.
Procedure
1. Enter system view.
system-view
2. Configure a short static ARP entry.
arp static ip-address mac-address [ vpn-instance vpn-instance-name ] [ description text ]
Configuring a long static ARP entry
About this task
Long static ARP entries can be effective or ineffective. Ineffective long static ARP entries cannot be used for packet forwarding. A long static ARP entry is ineffective when any of the following conditions exists:
· The IP address in the entry conflicts with a local IP address.
· No local interface has an IP address in the same subnet as the IP address in the ARP entry.
A long static ARP entry in a VLAN is deleted if the VLAN or VLAN interface is deleted.
Procedure
1. Enter system view.
system-view
2. Configure a long static ARP entry.
arp static ip-address mac-address [ vlan-id interface-type interface-number ] [ vpn-instance vpn-instance-name ] [ description text ]
Configuring features for dynamic ARP entries
Setting the dynamic ARP learning limit for a device
About this task
A device can dynamically learn ARP entries. To prevent a device from holding too many ARP entries, you can set the maximum number of dynamic ARP entries that the device can learn. When the limit is reached, the device stops ARP learning.
If you set a value lower than the number of existing dynamic ARP entries, the device does not delete the existing entries unless they age out. You can use the reset arp dynamic command to clear dynamic ARP entries.
Procedure
1. Enter system view.
system-view
2. Set the dynamic ARP learning limit for the device.
arp max-learning-number max-number slot slot-number
By default, the device can learn a maximum of 4096 dynamic ARP entries.
To disable the device from dynamic ARP learning, set the value to 0.
Setting the dynamic ARP learning limit for an interface
About this task
An interface can dynamically learn ARP entries. To prevent an interface from holding too many ARP entries, you can set the maximum number of dynamic ARP entries that the interface can learn. When the limit is reached, the interface stops ARP learning.
You can set limits for both a Layer 2 interface and the VLAN interface for a permitted VLAN on the Layer 2 interface. The Layer 2 interface learns an ARP entry only when neither limit is reached.
The total dynamic ARP learning limit for all interfaces will not be higher than the dynamic ARP learning limit for the device.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Set the dynamic ARP learning limit for the interface.
arp max-learning-num max-number [ alarm alarm-threshold ]
By default, an interface can learn a maximum of 4096 dynamic ARP entries.
To disable the interface from dynamic ARP learning, set the value to 0.
Setting the aging timer for dynamic ARP entries
About this task
Each dynamic ARP entry in the ARP table has a limited lifetime, called an aging timer. The aging timer of a dynamic ARP entry is reset each time the dynamic ARP entry is updated. A dynamic ARP entry that is not updated before its aging timer expires is deleted from the ARP table.
You can set the aging timer for dynamic ARP entries in system view or in interface view. The aging timer set in interface view takes precedence over the aging timer set in system view.
Procedure
1. Enter system view.
system-view
2. Set the aging timer for dynamic ARP entries.
¡ Set the aging timer for dynamic ARP entries in system view.
arp timer aging { aging-minutes | second aging-seconds }
The default setting is 20 minutes.
¡ Execute the following commands in sequence to set the aging timer for dynamic ARP entries in interface view:
interface interface-type interface-number
arp timer aging { aging-minutes | second aging-seconds }
By default, the aging timer set in system view applies.
Setting the maximum number of probes for dynamic ARP entries
About this task
Dynamic ARP entry probing prevents legal dynamic ARP entries from aging out, avoiding unnecessary ARP resolution in forwarding.
This probe feature sends ARP requests for the IP address in a dynamic ARP entry before it ages out.
· If the device receives an ARP reply before the entry aging timer expires, the device resets the aging timer.
· If the device makes the maximum number of probes without receiving a reply, the device deletes the entry when the entry aging timer expires.
You can set the maximum number of probes in system view and in interface view. The setting in interface view takes precedence over that in system view.
Procedure
1. Enter system view.
system-view
2. Set the maximum number of probes for dynamic ARP entries.
¡ In system view, set the maximum number of probes for dynamic ARP entries.
arp timer aging probe-count count
By default, the maximum number of probes for dynamic ARP entries is 3 in system view.
¡ Execute the following commands in sequence to set the maximum number of probes for dynamic ARP entries on an interface:
interface interface-type interface-number
arp timer aging probe-count count
By default, the maximum number of probes for dynamic ARP entries set on an interface is that set in system view.
Setting the interval for probing dynamic ARP entries
About this task
Dynamic ARP entry probing prevents legal dynamic ARP entries from aging out, avoiding unnecessary ARP resolution in forwarding.
Before a dynamic ARP entry ages out, the device sends ARP requests for the IP address in the ARP entry.
· If the device receives an ARP reply before a probe interval expires, the device resets the aging timer.
· If the device has not received an ARP reply when a probe interval expires, the device starts a new probe.
· If the device makes the maximum number probes without receiving an ARP reply, the device deletes the entry.
If the aging timer for a dynamic ARP entry expires while a probing is done for it, the device does not delete the entry. Instead, the aging timer will reset if the device receives an ARP reply before the probing finishes.
You can set the probe interval in system view and in interface view. The probe interval in interface view takes precedence over the probe interval in system view.
Restrictions and guidelines
· Increase the probing interval if the network is heavily loaded.
· To have the device perform ARP probing as expected, make sure the aging timer for dynamic ARP entries is higher than the maximum number of probes multiplied by the probe interval.
Procedure
1. Enter system view.
system-view
2. Set the interval for probing dynamic ARP entries.
¡ Set the interval for probing dynamic ARP entries in system view.
arp timer aging probe-interval interval
By default, the probe interval is 5 seconds.
¡ Execute the following commands in sequence to set the interval for probing dynamic ARP entries on an interface:
interface interface-type interface-number
arp timer aging probe-interval interval
By default, the probe interval equals the setting in system view.
Enabling dynamic ARP entry check
About this task
The dynamic ARP entry check feature disables the device from supporting dynamic ARP entries that contain multicast MAC addresses. The device cannot learn dynamic ARP entries containing multicast MAC addresses. You cannot manually add static ARP entries containing multicast MAC addresses.
When dynamic ARP entry check is disabled, ARP entries containing multicast MAC addresses are supported. The device can learn dynamic ARP entries containing multicast MAC addresses obtained from the ARP packets sourced from a unicast MAC address. You can also manually add static ARP entries containing multicast MAC addresses.
Procedure
1. Enter system view.
system-view
2. Enable dynamic ARP entry check.
arp check enable
By default, dynamic ARP entry check is enabled.
Performing ARP entry synchronization
About this task
This task ensures that all cards on the device have the same ARP entries.
Restrictions and guidelines
To synchronize ARP entries across all cards in a timely manner, you can schedule the device to automatically execute the arp smooth command. For information about scheduling a task, see the device management in Fundamentals Configuration Guide.
Procedure
To synchronize ARP entries from the active MPU to all other cards, execute the following command in user view:
arp smooth
Configuring a customer-side or network-side port
About this task
The device generates a host route when it learns an ARP entry from a network-side port. To save hardware resources, you can specify a port that connects to a user terminal as a customer-side port. The device will not generate a host route for the learned ARP entry of the user terminal.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure the interface as a customer-side port or a network-side port.
¡ Configure the interface as a customer-side port.
arp mode uni
¡ Configure the interface as a network-side port.
undo arp mode
By default, a port operates as a network-side port.
Enabling an IP unnumbered interface to learn ARP entries for different subnets
About this task
An IP unnumbered interface might be unable to learn the ARP entry for the peer device if the unnumbered interface and the remote device are on different subnets. This is because some devices treat an ARP request as illegal and do not return a reply if the sender and target IP addresses in that ARP request are on different subnets.
To ensure communication between them, use this feature on the IP unnumbered interface to specify a sender IP address on the same subnet as the IP address of the peer interface on the remote device.
If you disable an IP unnumbered interface from learning ARP entries for different subnets, the device deletes the existing ARP entries learned for different subnets after they age out.
Restrictions and guidelines
To avoid ARP learning anomalies, do not execute the arp ip-unnumbered learning enable command on a non-IP-unnumbered interface.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure the interface to borrow the IP address of the specified interface.
ip address unnumbered interface interface-type interface-number
By default, the interface does not borrow IP addresses from other interfaces.
4. Enable the IP unnumbered interface to learn ARP entries for different subnets.
arp ip-unnumbered learning enable [ source-address ip-address ]
By default, an IP unnumbered interface cannot learn ARP entries for different subnets.
Enabling unique ARP entry learning for IP addresses
About this task
Unique ARP entry learning enables the device to learn only one ARP entry for one IP address. This feature prevents traffic loss that might occur in the IP numbered scenario because two ARP entries exist for an endpoint after it moves between interfaces of the same IP address.
As shown in Figure 3, Interface A and Interface B on the device have the same IP address, because Interface A borrows the IP address of Interface B. The host can move from interface A to interface B without changing its IP address (1.1.1.1 in this example.)
When the host connects to Interface A, the device learns an ARP entry in which the IP address is 1.1.1.1 and the output interface is Interface A. After the host moves to Interface B, the device learns a new ARP entry in which the IP address is 1.1.1.1 and the output interface is Interface B.
This will cause loss of packets destined for the host, because the FIB entry for the host is generated based on the ARP entry generated earlier for it. The output interface in the FIB entry is different from the actual interface to which the host is attached after its movement.
With unique ARP entry learning enabled, the device deletes the existing ARP entry for an IP address when it learns a new ARP entry with a different interface than the existing entry for that IP address. This ensures that the output interface in the FIB entry for the client is the one to which the endpoint is attached.
Procedure
1. Enter system view.
system-view
2. Enable unique ARP entry learning for IP addresses.
arp ip-unique learning enable
By default, unique ARP entry learning for IP addresses is disabled.
Enabling recording user IP address conflicts
About this task
This feature enables the device to detect and record user IP address conflicts. The device determines that a conflict occurs if an incoming ARP packet has the same sender IP address as an existing ARP entry but a different sender MAC address. The device generates a user IP address conflict record, logs the conflict, and sends the log to the information center. For information about the log destination and output rule configuration in the information center, see the information center in System Management Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enable recording user IP address conflicts.
arp user-ip-conflict record enable
By default, recording user IP address conflicts is disabled.
Enabling interface consistency check between ARP and MAC address entries
About this task
In an unstable network, the receiving interface for packets from a user might change. The interface in the MAC address entry can be updated immediately while the interface in the ARP entry cannot. In this case, the packets matching the ARP entry will be sent out of an incorrect interface. To solve this problem, you can use this feature to periodically check the interface consistency between the ARP and MAC address entry for a user. If the interfaces are not the same, ARP sends ARP requests in the VLAN of the ARP entry and updates the entry with the ARP reply receiving interface.
Use display mac-address to display MAC address entries. For more information about this command, see MAC address table in Layer 2—LAN Switching Command Reference.
Procedure
1. Enter system view.
system-view
2. Enable interface consistency check between ARP and MAC address entries.
arp mac-interface-consistency check enable
By default, interface consistency check between ARP and MAC address entries is disabled.
Enabling recording user port migrations
About this task
This feature enables the device to detect and record user port migration events. A user port migrates if an incoming ARP packet has the same sender IP address and sender MAC address as an existing ARP entry but a different ingress port. The device generates a user port migration record, logs the migration event, sends the log to the information center, and updates the interface for the ARP entry. For information about the log destination and output rule configuration in the information center, see the information center in System Management Configuration Guide.
Restrictions and guidelines
To avoid device performance degradation, disable recording user port migrations if too many user port migration logs are generated.
Procedure
1. Enter system view.
system-view
2. Enable recording user port migrations.
arp user-move record enable
By default, recording user port migrations is disabled.
Enabling ARP logging
About this task
This feature enables a device to log ARP events when ARP cannot resolve IP addresses correctly. The log information helps administrators locate and solve problems. The device can log the following ARP events:
· On a proxy ARP-disabled interface, the target IP address of a received ARP packet is not one of the following IP addresses:
¡ The IP address of the receiving interface.
¡ The virtual IP address of the VRRP group.
¡ The public IP address after NAT.
· The sender IP address of a received ARP reply conflicts with one of the following IP addresses:
¡ The IP address of the receiving interface.
¡ The virtual IP address of the VRRP group.
¡ The public IP address after NAT.
The device sends ARP log messages to the information center. You can use the info-center source command to specify the log output rules for the information center. For more information about information center, see System Management Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enable ARP logging.
By default, ARP logging is disabled.
Verifying and maintaining ARP
Displaying ARP entries
Perform all display tasks in any view.
· Display ARP entries.
display arp [ [ all | dynamic | static ] [ slot slot-number ] | vlan vlan-id | interface interface-type interface-number ] [ count | verbose ]
· Display the differences in ARP entries between the specified slots.
display arp diff [ all | [ vpn-instance vpn-instance-name ] [ ip-address ] ] slot slot-number1 slot slot-number2
· Display the ARP entry for an IP address.
display arp ip-address [ slot slot-number ] [ verbose ]
· Display the ARP entries for a VPN instance.
display arp vpn-instance vpn-instance-name [ count | verbose ]
· Display the maximum number of ARP entries that a device supports.
display arp entry-limit
· Display the number of OpenFlow ARP entries.
display arp openflow count [ slot slot-number ]
· Display the aging timer of dynamic ARP entries.
display arp timer aging
· Display the ARP table usage.
display arp usage
· Display user IP address conflict records.
display arp user-ip-conflict record [ slot slot-number ]
· Display user port migration records.
display arp user-move record [ slot slot-number ]
Displaying brief ARP log information
Perform all display tasks in any view.
display arp log [ interface interface-type interface-number | ip ip-address ] [ slot slot-number ]
Clearing ARP entries
Restrictions and guidelines
Clearing ARP entries from the ARP table might cause communication failures. Make sure the entries to be cleared do not affect current communications.
Procedure
To clear ARP entries from the ARP table, execute the following command in user view:
reset arp { all | dynamic | interface interface-type interface-number | slot slot-number | static }
|
CAUTION: The reset arp command will clear existing ARP entries from the ARP table. It might cause that external users cannot quickly communicate with the LAN users. |
ARP configuration examples
Example: Configuring a long static ARP entry
Network configuration
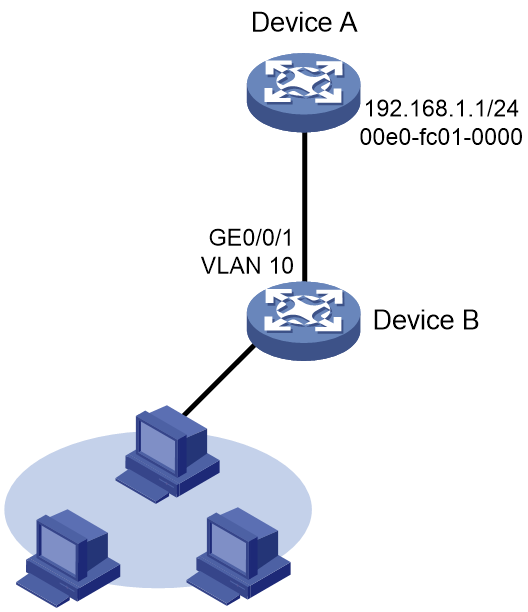
As shown in Figure 4, hosts are connected to Device B. Device B is connected to Device A through interface GigabitEthernet 0/0/1 in VLAN 10.
To ensure secure communications between Device A and Device B, configure a long static ARP entry for Device A on Device B.
Procedure
# Create VLAN 10.
<DeviceB> system-view
[DeviceB] vlan 10
[DeviceB-vlan10] quit
# Add interface GigabitEthernet 0/0/1 to VLAN 10.
[DeviceB] interface gigabitethernet 0/0/1
[DeviceB-GigabitEthernet0/0/1] port access vlan 10
[DeviceB-GigabitEthernet0/0/1] quit
# Create VLAN-interface 10 and configure its IP address.
[DeviceB] interface vlan-interface 10
[DeviceB-vlan-interface10] ip address 192.168.1.2 8
[DeviceB-vlan-interface10] quit
# Configure a long static ARP entry that has IP address 192.168.1.1, MAC address 00e0-fc01-0000, and output interface GigabitEthernet 0/0/1 in VLAN 10.
[DeviceB] arp static 192.168.1.1 00e0-fc01-0000 10 gigabitethernet 0/0/1
Verifying the configuration
# Verify that Device B has a long static ARP entry for Device A.
[DeviceB] display arp static
Type: S-Static D-Dynamic O-Openflow R-Rule I-Invalid
IP address MAC address VLAN/VSI name Interface Aging Type
192.168.1.1 00e0-fc01-0000 10 GE0/0/1 -- S
Example: Configuring a short static ARP entry
Network configuration
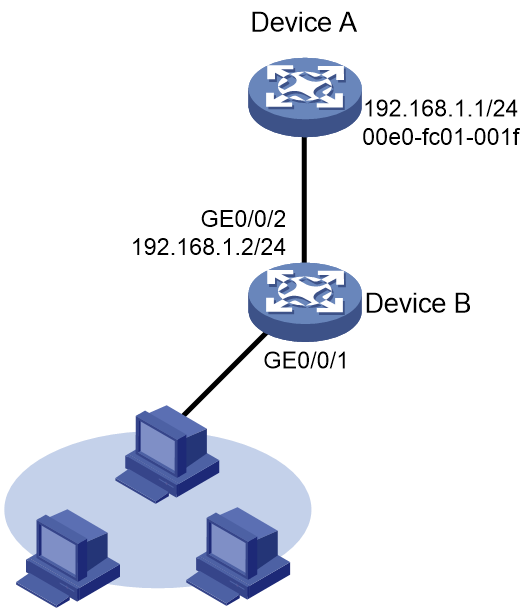
As shown in Figure 5, hosts are connected to Device B. Device B is connected to Device A through interface GigabitEthernet 0/0/2.
To ensure secure communications between Device A and Device B, configure a short static ARP entry for Device A on Device B.
Procedure
# Configure an IP address for GigabitEthernet 0/0/2.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 0/0/2
[DeviceB-GigabitEthernet0/0/2] ip address 192.168.1.2 24
[DeviceB-GigabitEthernet0/0/2] quit
# Configure a short static ARP entry that has IP address 192.168.1.1 and MAC address 00e0-fc01-001f.
[DeviceB] arp static 192.168.1.1 00e0-fc01-001f
Verifying the configuration
# Verify that Device B has a short static ARP entry for Device A.
[DeviceB] display arp static
Type: S-Static D-Dynamic O-Openflow R-Rule I-Invalid
IP address MAC address VLAN/VSI name Interface Aging Type
192.168.1.1 00e0-fc01-001f -- -- -- S
Configuring gratuitous ARP
About gratuitous ARP
In a gratuitous ARP packet, the sender IP address and the target IP address are the IP address of the sending device.
A device sends a gratuitous ARP packet for either of the following purposes:
· Determine whether its IP address is already used by another device. If the IP address is already used, the device is informed of the conflict by an ARP reply.
· Inform other devices of a MAC address change.
IP conflict detection
When an interface obtains an IP address, the device broadcasts gratuitous ARP packets in the LAN where the interface resides. If the device receives an ARP reply, its IP address conflicts with the IP address of another device in the LAN. The device displays a log message about the conflict and informs the administrator to change the IP address. The device will not use the conflicting IP address. If no ARP reply is received, the device uses the IP address.
Gratuitous ARP packet learning
This feature enables a device to create or update ARP entries by using the sender IP and MAC addresses in received gratuitous ARP packets.
When this feature is disabled, the device uses received gratuitous ARP packets to update existing ARP entries only. ARP entries are not created based on the received gratuitous ARP packets, which saves ARP table space.
Periodic sending of gratuitous ARP packets
Periodic sending of gratuitous ARP packets helps downstream devices update ARP entries or MAC entries in a timely manner.
This feature can implement the following functions:
· Prevent gateway spoofing.
Gateway spoofing occurs when an attacker uses the gateway address to send gratuitous ARP packets to the hosts on a network. The traffic destined for the gateway from the hosts is sent to the attacker instead. As a result, the hosts cannot access the external network.
To prevent such gateway spoofing attacks, you can enable the gateway to send gratuitous ARP packets at intervals. Gratuitous ARP packets contain the primary IP address and manually configured secondary IP addresses of the gateway, so hosts can learn correct gateway information.
· Prevent ARP entries from aging out.
If network traffic is heavy or if the host CPU usage is high, received ARP packets can be discarded or are not promptly processed. Eventually, the dynamic ARP entries on the receiving host age out. The traffic between the host and the corresponding devices is interrupted until the host re-creates the ARP entries.
To prevent this problem, you can enable the gateway to send gratuitous ARP packets periodically. Gratuitous ARP packets contain the primary IP address and manually configured secondary IP addresses of the gateway, so the receiving hosts can update ARP entries in a timely manner.
· Prevent the virtual IP address of a VRRP group from being used by a host.
The master router of a VRRP group can periodically send gratuitous ARP packets to the hosts on the local network. The hosts can then update local ARP entries and avoid using the virtual IP address of the VRRP group. The sender MAC address in the gratuitous ARP packet is the virtual MAC address of the virtual router. For more information about VRRP, see High Availability Configuration Guide.
Gratuitous ARP tasks at a glance
All gratuitous ARP tasks are optional. If all of the following features are disabled, gratuitous ARP still provides the IP conflict detection function.
· Enabling IP conflict notification
· Enabling gratuitous ARP packet learning
· Enabling periodic sending of gratuitous ARP packets
· Configuring gratuitous ARP packet retransmission for the device MAC address change
Enabling IP conflict notification
About this task
Upon detecting an IP conflict, the device will sends a gratuitous ARP request. By default, the device displays an error message only after it receives an ARP reply. You can enable this feature to allow the device to display an error message immediately upon detecting an IP conflict.
Procedure
1. Enter system view.
system-view
2. Enable IP conflict notification.
arp ip-conflict log prompt
By default, IP conflict notification is disabled.
Enabling gratuitous ARP packet learning
1. Enter system view.
system-view
2. Enable gratuitous ARP packet learning.
gratuitous-arp-learning enable
By default, gratuitous ARP packet learning is enabled.
Enabling periodic sending of gratuitous ARP packets
Restrictions and guidelines
· You can enable periodic sending of gratuitous ARP packets on a maximum of 1024 interfaces.
· Periodic sending of gratuitous ARP packets takes effect on an interface only when the following conditions are met:
¡ The data link layer state of the interface is up.
¡ The interface has an IP address.
· If you change the sending interval for gratuitous ARP packets, the configuration takes effect at the next sending interval.
· The sending interval for gratuitous ARP packets might be much longer than the specified sending interval in any of the following circumstances:
¡ This feature is enabled on multiple interfaces.
¡ Each interface is configured with multiple secondary IP addresses.
¡ A small sending interval is configured when the previous two conditions exist.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable periodic sending of gratuitous ARP packets.
arp send-gratuitous-arp [ interval interval ]
By default, periodic sending of gratuitous ARP packets is disabled.
Enabling sending gratuitous ARP packets for ARP requests with sender IP address on a different subnet
1. Enter system view.
system-view
2. Enable the device to send gratuitous ARP packets upon receiving ARP requests whose sender IP address belongs to a different subnet.
gratuitous-arp-sending enable
By default, a device does not send gratuitous ARP packets upon receiving ARP requests whose sender IP address belongs to a different subnet.
Configuring gratuitous ARP packet retransmission for the device MAC address change
About this task
The device sends a gratuitous ARP packet to inform other devices of its MAC address change. However, the other devices might fail to receive the packet because the device sends the gratuitous ARP packet once only by default. Configure the gratuitous ARP packet retransmission feature to ensure that the other devices can receive the packet.
Procedure
1. Enter system view.
system-view
2. Set the times and the interval for retransmitting a gratuitous ARP packet for the device MAC address change.
gratuitous-arp mac-change retransmit times interval seconds
By default, the device sends a gratuitous packet to inform its MAC address change once only.
Configuring proxy ARP
About proxy ARP
Proxy ARP enables a device on one network to answer ARP requests for an IP address on another network. With proxy ARP, hosts on different broadcast domains can communicate with each other as they would on the same broadcast domain.
Proxy ARP includes common proxy ARP and local proxy ARP.
· Common proxy ARP—Allows communication between hosts that connect to different Layer 3 interfaces and reside in different broadcast domains.
· Local proxy ARP—Allows communication between hosts that connect to the same Layer 3 interface and reside in different broadcast domains.
Enabling common proxy ARP
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
Common proxy ARP is available on the following types of interfaces:
¡ VLAN interface.
¡ Layer 3 Ethernet interface.
¡ Layer 3 Ethernet subinterface.
¡ Layer 3 aggregate interface.
¡ Layer 3 aggregate subinterface.
3. Enable common proxy ARP.
By default, common proxy ARP is disabled.
Enabling local proxy ARP
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
Local proxy ARP is available on the following types of interfaces:
¡ VLAN interface.
¡ Layer 3 Ethernet interface.
¡ Layer 3 Ethernet subinterface.
¡ Layer 3 aggregate interface.
¡ Layer 3 aggregate subinterface.
3. Enable local proxy ARP.
local-proxy-arp enable [ ip-range start-ip-address to end-ip-address ]
By default, local proxy ARP is disabled.
Verifying and maintaining proxy ARP
Perform all display tasks in any view.
· Display common proxy ARP status.
display proxy-arp [ interface interface-type interface-number ]
· Display local proxy ARP status.
display local-proxy-arp [ interface interface-type interface-number ]
· Display statistics about proxy ARP reply packets.
display proxy-arp statistics
Common proxy ARP configuration example
Example: Configuring common proxy ARP
Network configuration
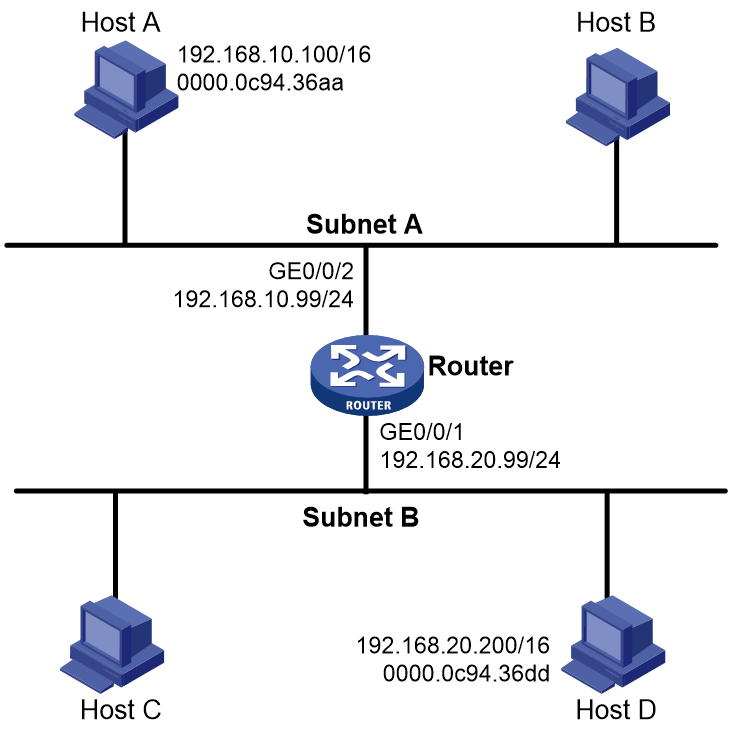
As shown in Figure 6, Host A and Host D have the same prefix and mask, but they are located on different subnets. No default gateway is configured on Host A and Host D.
Configure common proxy ARP on the router to ensure communication between Host A and Host D.
Procedure
# Configure the IP address of GigabitEthernet 0/0/2.
<Router> system-view
[Router] interface gigabitethernet 0/0/2
[Router-GigabitEthernet0/0/2] ip address 192.168.10.99 255.255.255.0
# Enable common proxy ARP on GigabitEthernet 0/0/2.
[Router-GigabitEthernet0/0/2] proxy-arp enable
[Router-GigabitEthernet0/0/2] quit
# Configure the IP address of GigabitEthernet 0/0/1.
[Router] interface gigabitethernet 0/0/1
[Router-GigabitEthernet0/0/1] ip address 192.168.20.99 255.255.255.0
# Enable common proxy ARP on GigabitEthernet 0/0/1.
[Router-GigabitEthernet0/0/1] proxy-arp enable
[Router-GigabitEthernet0/0/1] quit
Verifying the configuration
# Verify that Host A and Host D can ping each other.
Configuring ARP PnP
About ARP PnP
The ARP plug and play (PnP) feature is typically configured on a gateway. This feature allows end users to access the gateway without changing their IP addresses on subnets different from the subnet where the gateway resides.
After ARP PnP is enabled on an interface, it provides the following functions:
· ARP PnP enables the interface to always reply to users' ARP requests with the interface's MAC address.
· Upon receiving a packet from the user, ARP PnP replaces the source IP address of the packet with an agent IP address. The agent IP address is on the same subnet as the interface IP address.
· Upon receiving the return packet destined to the agent IP address, ARP PnP replaces the agent IP with the user's original IP address.
Prerequisites
Before you configure the ARP PnP feature on an interface, perform the following tasks:
· Assign the interface a primary IP address. ARP PnP generates agent IP addresses based on the primary IP address and mask length of the interface.
· Use the reset arp command to delete all ARP entries on the interface.
· Configure NAT on the device. The configuration includes configuring an address group, adding an IP address range to the address group, and configuring outbound dynamic NAT on the interface that connects to the external network. For more information about NAT, see "Configuring NAT."
Enabling ARP PnP
1. Enter system view.
system-view
2. Enter interface view of the interface that connects to the internal network.
interface interface-type interface-number
The following interface types are supported:
¡ Layer 3 Ethernet interfaces.
¡ Layer 3 Ethernet subinterfaces.
3. Enable the ARP PnP feature.
arp pnp
By default, the ARP PnP feature is disabled.
|
CAUTION: Features that use ARP entries, for example, static routes and proxy ARP, cannot operate correctly when the ARP PnP feature is enabled. |
Verifying and maintaining ARP PnP
To display ARP PnP mappings, execute the following command in any view:
display arp pnp [ interface interface-type interface-number ]
ARP PnP configuration examples
Example: Configuring ARP PnP
Network configuration
As shown in Figure 7, configure the ARP PnP feature to allow the host at 1.2.3.4 to access the external server through GigabitEthernet 0/0/1.
Procedure
1. Configure NAT:
# Specify IP addresses for GigabitEthernet 0/0/1 and GigabitEthernet 0/0/2.
<Router> system-view
[Router] interface gigabitethernet 0/0/1
[Router-GigabitEthernet0/0/1] ip address 192.168.0.2 24
[Router-GigabitEthernet0/0/1] quit
[Router] interface gigabitethernet 0/0/2
[Router-GigabitEthernet0/0/2] ip address 202.38.1.100 24
[Router-GigabitEthernet0/0/2] quit
# Configure ACL 2000 to identify packets from subnet 192.168.0.0/24.
[Router] acl basic 2000
[Router-acl-ipv4-basic-2000] rule permit source 192.168.0.0 0.0.0.255
[Router-acl-ipv4-basic-2000] quit
# Create address group 1, and add address 202.38.1.100 to the group.
[Router] nat address-group 1
[Router-nat-address-group-1] address 202.38.1.100 202.38.1.100
[Router-nat-address-group-1] quit
# Enable outbound PAT on interface GigabitEthernet 0/0/2 to translate the source address of outgoing packets matching ACL 2000 into the address in address group 1.
[Router] interface gigabitethernet 0/0/2
[Router-GigabitEthernet0/0/2] nat outbound 2000 address-group 1
2. Enable the ARP PnP feature on GigabitEthernet 0/0/1.
[Router] interface gigabitethernet 0/0/1
[Router-GigabitEthernet0/0/1] arp pnp
[Router-GigabitEthernet0/0/1] quit
Verifying the configuration
# Verify that the router creates an ARP PnP mapping for the host IP address 1.2.3.4 on GigabitEthernet 0/0/1.
[Router] display arp pnp interface gigabitethernet 0/0/1
Total number of entries : 1
Agent IP address User IP address MAC address Interface Aging
192.168.0.3 1.2.3.4 00e0-fc00-0001 GE0/0/1 10
Configuring ARP suppression
About ARP suppression
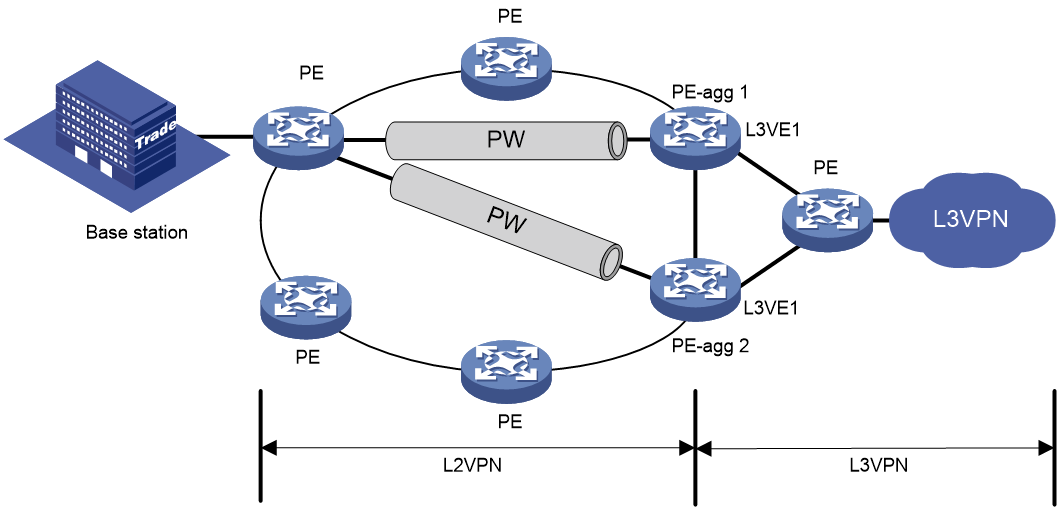
The ARP suppression feature enables a device to directly answer ARP requests by using ARP suppression entries. The device generates ARP suppression entries based on dynamic ARP entries. This feature is typically configured on the PEs connected to base stations in an MPLS L2VPN that provides access to an L3VPN network.
You can also configure the ARP suppression push feature to push ARP suppression entries by broadcasting gratuitous ARP packets.
Figure 8 shows a typical application scenario. ARP suppression is enabled on the PE that connects to the base station. The PE generates ARP suppression entries for the base station, PE-agg 1, and PE-agg 2, and it directly replies subsequent ARP requests for these devices.
Enabling ARP suppression
Restrictions and guidelines
You must enable L2VPN before you enter cross-connect view. For more information about L2VPN, see MPLS L2VPN configuration in MPLS Configuration Guide.
Procedure
1. Enter system view.
system-view
2. (Optional.) Enable the ARP suppression push feature and set a push interval.
arp suppression push interval interval
By default, the ARP suppression push feature is disabled.
3. Create a cross-connect group and enter its view.
xconnect-group group-name
For more information about this command, see the MPLS L2VPN commands in MPLS Command Reference.
4. Create a cross-connect and enter its view.
connection connection-name
For more information about this command, see the MPLS L2VPN commands in MPLS Command Reference.
5. Enable ARP suppression.
arp suppression enable
By default, ARP suppression is disabled.
Display and maintenance commands for ARP suppression
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display ARP suppression entries. |
display arp suppression xconnect-group [ name group-name ] [ slot slot-number ] [ count ] |
|
Clear ARP suppression entries. |
reset arp suppression xconnect-group [ name group-name ] |
ARP suppression configuration example
Example: Configuring ARP suppression
Network configuration
As shown in Figure 9, the base station, Router A, and Router B are in an MPLS L2VPN.
Enable ARP suppression on Router A to directly reply to ARP requests for Router B.
Procedure
1. Configure IP addresses for the interfaces, and make sure the base station can reach the L3VE interface VE-L3VPN 1 of Router B. (Details not shown.)
2. Configure ARP suppression on Router A:
# Create a cross-connect group named vpna and create a cross-connect named svc in the group.
<RouterA> system-view
[RouterA] xconnect-group vpna
[RouterA-xcg-vpna] connection svc
# Enable ARP suppression for cross-connect svc in cross-connect group vpna.
[RouterA-xcg-vpna-svc] arp suppression enable
Verifying the configuration
1. On the base station, clear ARP entries, and ping the L3VE interface VE-L3VPN 1 of Router B. (Details not shown.)
2. Verify that Router A has ARP suppression entries for the base station and Router B.
[RouterA-xcg-vpna-svc] display arp suppression xconnect-group
IP address MAC address Xconnect-group Connection Aging
10.1.1.1 00e0-fc04-582c vpna svc 25
10.1.1.3 0023-89b7-0861 vpna svc 25
3. Enable ARP debugging on Router B to verify that Router B does not receive an ARP request from the base station under the following conditions (details not shown):
a. Clear ARP entries on the base station.
b. Ping the L3VE interface VE-L3VPN 1 of Router B from the base station.
Configuring ARP direct route advertisement
About ARP direct route advertisement
Mechanism of ARP direct route advertisement
This feature generates host routes based on ARP entries for packet forwarding and route advertisement. The route preference value determines the match order of a route. Dynamic routing protocols use the tag value as the route identifier when they redistribute the route.
After you enable ARP direct route advertisement on an interface, the device generates direct routes and adjacency table entries based on ARP entries learned on that interface. If the direct routes are generated before the adjacency table entries, temporary packet loss will occur due to lack of Layer 2 information for packet encapsulation. To avoid such an issue, set a route generation delay for ARP direct route advertisement on the interface.
If you edit the direct route advertisement configuration before the delay timer expires, the device advertises the direct route based on the new configuration immediately.
Application in Layer 3 access networks
As shown in Figure 10, ARP direct route advertisement is enabled on Interface A and Interface B. This feature generates a host route to Server A and a host route to Server B for the routing protocols to advertise. So each device forwards only the traffic destined to the server within the network, which saves bandwidth.
Figure 10 Application in a Layer 3 access network
Enabling ARP direct route advertisement
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. (Optional.) Set a route generation delay for ARP direct route advertisement.
arp route-direct advertise delay delay-time
By default, the device generates a direct route immediately after an ARP entry is learned on an interface enabled with ARP direct route advertisement.
4. Enable the ARP direct route advertisement feature.
arp route-direct advertise [ preference preference-value | tag tag-value ] *
By default, the ARP direct route advertisement feature is disabled.
Displaying the direct routes generated based on ARP entries
To display the direct routes generated based on ARP entries, execute the following command in any view:
display arp route-direct advertise interface interface-type interface-number
Disabling sending ARP requests when data packets trigger ARP resolution
About disabling sending ARP requests when data packets trigger ARP resolution
By default, when the device receives a data packet not destined for it and cannot find a match for the next hop in the ARP table, it performs the following tasks:
1. Sends an ARP request to obtain the MAC address of the next hop.
2. Generates an ARP entry based on the obtained MAC address.
A large number of ARP requests consume too many network resources, affecting normal service operation. To resolve the issue, use this feature to disable the device from sending ARP requests for ARP learning when data packets trigger ARP resolution. This suppresses ARP flooding by reducing ARP packets on the network.
Disabling sending ARP requests when data packets trigger ARP resolution
Restrictions and guidelines
As a best practice, configure this feature only when the network is attacked by ARP flooding.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Disable the device from sending ARP requests for ARP learning when data packets trigger ARP resolution.
arp fib-miss drop
By default, the device sends ARP requests for ARP learning when data packets trigger ARP resolution.
Configuring ARP ping
Configuring ARP ping for IPv4 addresses
About this task
This feature enables you to test whether an IPv4 address is in use on a LAN by sending ARP requests.
After the device sends an ARP request to an IPv4 address, if it receives an ARP reply before the ARP request timeout timer expires, it determines that the IP address is being used. If no ARP reply is received before the ARP request timeout timer expires, the device sends another ARP request. After the device sends the maximum number of ARP requests without receiving a reply, the device stops sending ARP requests and regards the IPv4 address as an unused address.
Compared with the ping command, the ping arp ip command avoids a wrong result when the destination host is enabled with a firewall that blocks ICMP packets. In addition, it consumes fewer network resources because an ARP request is shorter than an ICMP packet.
Restrictions and guidelines
If multiple devices exist on the LAN, executing the ping arp ip command will take some time. To stop an ongoing test, press Ctrl + C.
Prerequisites
To execute the ping arp ip command by specifying the destination host name, configure the DNS feature first. For more information about DNS, see "Configuring DNS."
Procedure
Execute the following command in any view:
ping arp ip host [ interface interface-type interface-number [ vlan vlan-id ] ] [ timeout timeout ] [ count count ]
Configuring ARP ping for MAC addresses
About this task
To obtain the IPv4 address associated with a MAC address, use this command to broadcast Layer 3 ICMP packets.
The device retransmits an ICMP echo request if it has failed to receive an ICMP echo reply before the request timeout timer expires. The device stops sending ICMP echo requests and determines that the MAC address is not on the network after it has sent the maximum number of requests without receiving a reply.
Restrictions and guidelines
If multiple devices exist on the network, executing the ping arp mac command will take some time. To stop an ongoing test, press Ctrl + C.
Procedure
Execute the following command in any view:
ping arp mac mac-address { interface interface-type interface-number | ip ipv4-address [ vpn-instance vpn-instance-name ] } [ timeout timeout ] [ count count ]