- Table of Contents
-
- 12-Network Management and Monitoring Configuration Guide
- 00-Preface
- 01-System Maintenance and Debugging Configuration
- 02-NQA Configuration
- 03-NTP Configuration
- 04-Clock Monitoring Configuration
- 05-IPC Configuration
- 06-SNMP Configuration
- 07-RMON Configuration
- 08-Sampler Configuration
- 09-Mirroring Configuration
- 10-NetStream Configuration
- 11-IPv6 NetStream Configuration
- 12-Protocol Packet Statistics Configuration
- 13-Information Center Configuration
- 14-Flow Logging Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-System Maintenance and Debugging Configuration | 195.23 KB |
Using ping, tracert, and system debugging
Introduction to system debugging
Ping and tracert configuration example
You can use the ping command to check the connectivity to a destination, use the tracert command to trace the path to a destination, and use the debug command to diagnose system faults based on the debugging information.
Ping
Introduction
Use the ping utility to check the reachability to a specific address.
Ping sends ICMP echo requests (ECHO-REQUEST) to the destination device. Upon receiving the requests, the destination device responds with ICMP echo replies (ECHO-REPLY) to the source device. The source device outputs statistics about the ping operation, including the number of packets sent, number of echo replies received, and the round-trip time. You can measure the network performance by analyzing these statistics.
Configuring ping
To configure the ping function:
|
Task |
Command |
Remarks |
|
Check whether a specified address in an IP network is reachable. |
·
For an IPv4 network: ·
For an IPv6 network: |
Use either approach. Available in any view. |
|
|
NOTE: · For a low-speed network, H3C recommends that you set a larger value for the timeout timer (indicated by the -t parameter in the command) when configuring the ping command. · Only the directly connected segment address can be pinged if the outgoing interface is specified with the -i argument. · For more information about the ping lsp command, see MPLS Command Reference. |
Ping configuration example
Network requirements
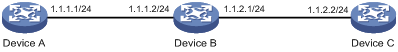
As shown in Figure 1, check whether Device A and Device C can reach each other. If the two devices can reach each other, get the detailed information about routes from Device A to Device C.
Configuration procedure
# Use the ping command to display whether Device A and Device C can reach each other.
<DeviceA> ping 1.1.2.2
PING 1.1.2.2: 56 data bytes, press CTRL_C to break
Reply from 1.1.2.2: bytes=56 Sequence=1 ttl=254 time=205 ms
Reply from 1.1.2.2: bytes=56 Sequence=2 ttl=254 time=1 ms
Reply from 1.1.2.2: bytes=56 Sequence=3 ttl=254 time=1 ms
Reply from 1.1.2.2: bytes=56 Sequence=4 ttl=254 time=1 ms
Reply from 1.1.2.2: bytes=56 Sequence=5 ttl=254 time=1 ms
--- 1.1.2.2 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 1/41/205 ms
# Get detailed information about routes from Device A to Device C.
<DeviceA> ping -r 1.1.2.2
PING 1.1.2.2: 56 data bytes, press CTRL_C to break
Reply from 1.1.2.2: bytes=56 Sequence=1 ttl=254 time=53 ms
Record Route:
1.1.2.1
1.1.2.2
1.1.1.2
1.1.1.1
Reply from 1.1.2.2: bytes=56 Sequence=2 ttl=254 time=1 ms
Record Route:
1.1.2.1
1.1.2.2
1.1.1.2
1.1.1.1
Reply from 1.1.2.2: bytes=56 Sequence=3 ttl=254 time=1 ms
Record Route:
1.1.2.1
1.1.2.2
1.1.1.2
1.1.1.1
Reply from 1.1.2.2: bytes=56 Sequence=4 ttl=254 time=1 ms
Record Route:
1.1.2.1
1.1.2.2
1.1.1.2
1.1.1.1
Reply from 1.1.2.2: bytes=56 Sequence=5 ttl=254 time=1 ms
Record Route:
1.1.2.1
1.1.2.2
1.1.1.2
1.1.1.1
--- 1.1.2.2 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 1/11/53 ms
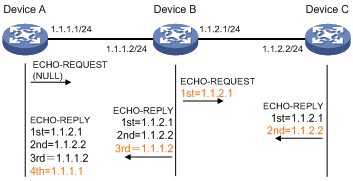
The principle of ping –r is as shown in Figure 1.
1. The source device (Device A) sends an ICMP echo request with the RR option being empty to the destination device (Device C).
2. The intermediate device (Device B) adds the IP address (1.1.2.1) of its outbound interface to the RR option of the ICMP echo request, and forwards the packet.
3. Upon receiving the request, the destination device copies the RR option in the request and adds the IP address (1.1.2.2) of its outbound interface to the RR option. Then the destination device sends an ICMP echo reply.
4. The intermediate device adds the IP address (1.1.1.2) of its outbound interface to the RR option in the ICMP echo reply, and then forwards the reply.
5. Upon receiving the reply, the source device adds the IP address (1.1.1.1) of its inbound interface to the RR option. Finally, you can get detailed information about routes from Device A to Device C: 1.1.1.1 <-> {1.1.1.2; 1.1.2.1} <-> 1.1.2.2.
Tracert
Introduction
Traceroute enables you to get the IP addresses of Layer 3 devices in the path to a specific destination. You can use traceroute to check network connectivity and identify the failed nodes in the event of network failure.
Figure 2 Tracert operation
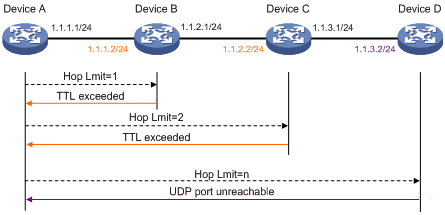
Traceroute uses received ICMP error messages to get the IP addresses of devices. As shown in Figure 2, traceroute works as follows:
1. The source device (Device A) sends a UDP packet with a TTL value of 1 to the destination device (Device D). The destination UDP port is not used by any application on the destination device.
2. The first hop (Device B, the first Layer 3 device that receives the packet) responds by sending a TTL-expired ICMP error message to the source device, with its IP address encapsulated. In this way, the source device can get the address of the first Layer 3 device (1.1.1.2).
3. The source device sends a packet with a TTL value of 2 to the destination device.
4. The second hop (Device C) responds with a TTL-expired ICMP error message, which gives the source device the address of the second Layer 3 device (1.1.2.2).
5. The above process continues until the packet sent by the source device reaches the ultimate destination device. Since no application uses the destination port specified in the packet, the destination device responds with a port-unreachable ICMP message to the source device, with its IP address encapsulated. In this way, the source device gets the IP address of the destination device (1.1.3.2).
6. The source device thinks that the packet has reached the destination device after receiving the port-unreachable ICMP message, and the path to the destination device is 1.1.1.2 to 1.1.2.2 to 1.1.3.2.
Configuring tracert
Configuration prerequisites
Enable sending of ICMP timeout packets on the intermediate device (the device between the source and destination devices). If the intermediate device is an H3C device, execute the ip ttl-expires enable command on the device. For more information about this command, see Layer 3—IP Services Command Reference.
Enable sending of ICMP destination unreachable packets on the destination device. If the destination device is an H3C device, execute the ip unreachables enable command. For more information about this command, see Layer 3—IP Services Command Reference.
Tracert configuration
To configure tracert:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Display the routes from source to destination. |
· For an IPv4 network: · For an IPv6 network: |
Use either approach. Available in any view. |
|
|
NOTE: For more information about the tracert lsp command, see MPLS Command Reference. |
System debugging
Introduction to system debugging
The router provides various debugging functions. For the majority of protocols and features supported, the system provides corresponding debugging information to help users diagnose errors.
The following two switches control the display of debugging information:
· Protocol debugging switch—Controls protocol-specific debugging information.
· Screen output switch—Controls whether to display the debugging information on a certain screen.
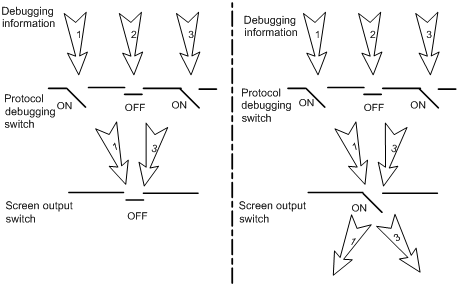
As Figure 3 illustrates, assume the router can provide debugging for the three modules 1, 2, and 3. The debugging information is output on a terminal only when both the protocol debugging switch and the screen output switch are turned on.
Figure 3 The relationship between the protocol and screen output switch
Configuring system debugging
Output of the debugging information may reduce system efficiency. Administrators usually use the debugging commands to diagnose network failure. After completing the debugging, disable the corresponding debugging function, or use the undo debugging all command to disable all the debugging functions.
Output of debugging information depends on the configurations of the information center and the debugging commands of each protocol and functional module. Displaying the debugging information on a terminal (including console or VTY) is a common way to output debugging information. You can also output debugging information to other destinations. For more information, see the chapter “Configuring the information center.”
To enable the output of debugging information to a terminal:
|
Step |
Command |
Remarks |
|
1. Enable the terminal monitoring of system information. |
terminal monitor |
Optional. By default, the terminal monitoring on the console is enabled and that on the monitoring terminal is disabled. Available in user view. |
|
2. Enable the terminal display of debugging information. |
terminal debugging |
By default, terminal display of debugging information is disabled. Available in user view. |
|
3. Enable debugging for a specified module. |
debugging { all [ timeout time ] | module-name [ option ] } |
By default, debugging for a specified module is disabled. Available in user view |
|
4. Display the enabled debugging functions. |
display debugging [ interface interface-type interface-number ] [ module-name ] [ | { begin | exclude | include } regular-expression ] |
Optional. Available in any view. |
|
|
NOTE: You must configure the debugging, terminal debugging and terminal monitor commands first to display the detailed debugging information on the terminal. For more information about the terminal debugging and terminal monitor commands, see Network Management and Monitoring Command Reference. |
Ping and tracert configuration example
Network requirements
As shown in Figure 4, Device A failed to telnet Device C. Check whether Device A and Device C can reach each other. If they cannot reach each other, locate the failed nodes in the network.
Configuration procedure
# Use the ping command to display whether Device A and Device C can reach each other.
<DeviceA> ping 1.1.2.2
PING 1.1.2.2: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
--- 1.1.2.2 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
# Device A and Device C cannot reach each other. Use the tracert command to determine failed nodes.
<DeviceA> system-view
[DeviceA] ip ttl-expires enable
[DeviceA] ip unreachables enable
[DeviceA] tracert 1.1.2.2
traceroute to 1.1.2.2(1.1.2.2) 30 hops max,40 bytes packet, press CTRL_C to bre
ak
1 1.1.1.2 14 ms 10 ms 20 ms
2 * * *
3 * * *
4 * * *
5
<DeviceA>
The output shows that Device A and Device C cannot reach other, Device A and Device B can reach each other, and an error occurred on the connection between Device B and Device C. In this case, use the debugging ip icmp command to enable ICMP debugging on Device A and Device C to check whether the devices send or receive the specified ICMP packets, or use the display ip routing-table command to display whether Device A and Device C can reach each other.

