- Table of Contents
-
- 04-Layer 3—IP Services Configuration Guide
- 00-Preface
- 01-ARP configuration
- 02-DHCPv6 configuration
- 03-DHCP configuration
- 04-IPv6 basics configuration
- 05-IP addressing configuration
- 06-IP performance optimization configuration
- 07-IP forwarding basics configuration
- 08-Tunneling configuration
- 09-DNS configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 03-DHCP configuration | 533.50 KB |
Vendor-specific option (Option 43)
Relay agent option (Option 82)
Configuring the DHCP relay agent
DHCP relay agent support for Option 82
DHCP relay agent support for MCE
DHCP relay agent support for shared IP address pools
Restrictions and guidelines: DHCP relay configuration
DHCP relay agent tasks at a glance
Enabling the DHCP relay agent on an interface
Specifying DHCP servers on a relay agent
Configuring a remote BAS IP pool on a DHCP relay agent
Specifying the DHCP server selection algorithm
Configuring DHCP server liveness detection
Configuring the DHCP relay agent security features
Enabling the DHCP relay agent to record relay entries
Enabling periodic refresh of dynamic relay entries
Enabling lease release notification
Enabling DHCP starvation attack protection
Enabling DHCP proxy on the DHCP relay agent
Enabling client offline detection on the DHCP relay agent
Configuring the DHCP relay agent to release an IP address
Configuring DHCP relay agent support for Option 82
Disabling remote IP address check
Setting the DSCP value for DHCP packets sent by the DHCP relay agent
Specifying the DHCP relay agent address for the giaddr field
Manually specifying the DHCP relay agent address for the giaddr field
Configuring smart relay to specify the DHCP relay agent address for the giaddr field
Specifying the source IP address for relayed DHCP requests
About specifying the source IP address for relayed DHCP requests
Specifying the source IP address for relayed DHCP requests (interface view)
Specifying the source IP address for relayed DHCP requests (remote BAS IP pool view)
Configuring the DHCP relay agent to always unicast relayed DHCP responses
Configuring forwarding DHCP replies based on Option 82
Setting the maximum number of DHCP-NAK packets
Enabling the IP conflicting user offline feature
Specifying a DHCP request processing method for roaming DHCP clients
Enabling the non-first-hop DHCP relay agent feature
Enabling DHCP-NAK-triggered remote BAS IP pool switchover
Display and maintenance commands for DHCP relay agent
DHCP relay agent configuration examples
Example: Configuring basic DHCP relay agent
Example: Configuring Option 82
Example: Configuring DHCP server selection
Troubleshooting DHCP relay agent configuration
Failure of DHCP clients to obtain configuration parameters through the DHCP relay agent
Restrictions and guidelines: DHCP client configuration
Enabling DHCP client on an interface
Configuring a DHCP client ID for an interface
Enabling duplicated address detection
Setting the DSCP value for DHCP packets sent by the DHCP client
Configuring SNMP notifications for the DHCP client
Display and maintenance commands for DHCP client
DHCP client configuration examples
Example: Configuring DHCP client
Obtaining an IP address dynamically
Configuring an interface to use BOOTP for IP address acquisition
Display and maintenance commands for BOOTP client
BOOTP client configuration examples
Example: Configuring BOOTP client
DHCP overview
DHCP network model
The Dynamic Host Configuration Protocol (DHCP) provides a framework to assign configuration information to network devices.
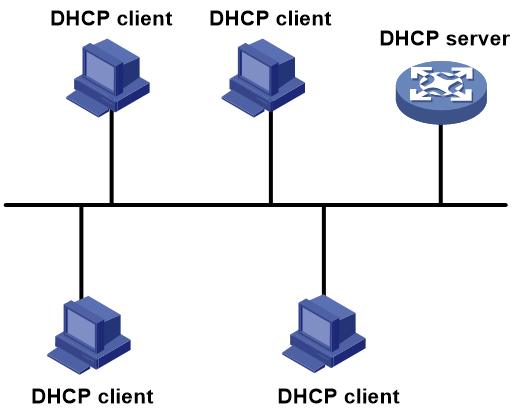
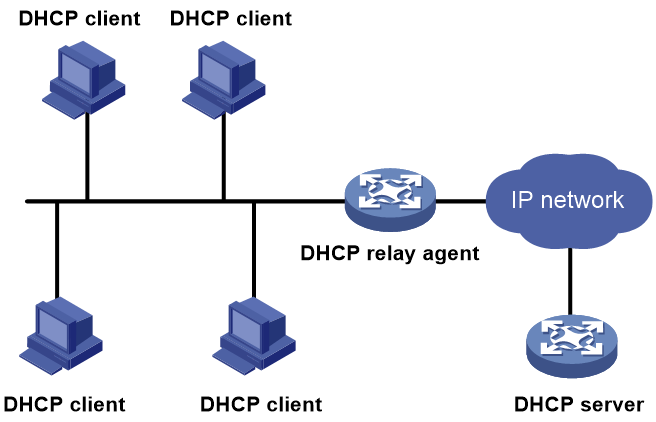
Figure 1 shows a typical DHCP application scenario in which the DHCP clients and the DHCP server reside on the same subnet. The DHCP clients on one subnet can also obtain configuration parameters from a DHCP server on another subnet through a DHCP relay agent. For more information about the DHCP relay agent, see "Configuring the DHCP relay agent."
Figure 1 A typical DHCP application
DHCP address allocation
Allocation mechanisms
DHCP supports the following allocation mechanisms:
· Static allocation—The network administrator assigns an IP address to a client, such as a WWW server, and DHCP conveys the assigned address to the client.
· Automatic allocation—DHCP assigns a permanent IP address to a client.
· Dynamic allocation—DHCP assigns an IP address to a client for a limited period of time, which is called a lease. Most DHCP clients obtain their addresses in this way.
IP address allocation process
Figure 2 IP address allocation process
As shown in Figure 2, a DHCP server assigns an IP address to a DHCP client in the following process:
1. The client broadcasts a DHCPDISCOVER message to locate a DHCP server.
2. Each DHCP server offers configuration parameters such as an IP address to the client in a DHCP-OFFER message. The sending mode of the DHCP-OFFER is determined by the flag field in the DHCPDISCOVER message. For more information, see "DHCP message format."
3. If the client receives multiple offers, it accepts the first received offer, and broadcasts it in a DHCPREQUEST message to formally request the IP address. (IP addresses offered by other DHCP servers can be assigned to other clients.)
4. All DHCP servers receive the DHCPREQUEST message. However, only the server selected by the client does one of the following operations:
¡ Returns a DHCP-ACK message to confirm that the client can use the requested IP address.
¡ Returns a DHCP-NAK message to deny the IP address allocation.
After receiving the DHCP-ACK message, the client verifies the following details before using the assigned IP address:
· The assigned IP address is not in use. To verify this, the client broadcasts a gratuitous ARP packet. The assigned IP address is not in use if no response is received within the specified time.
· The assigned IP address is not on the same subnet as any IP address in use on the client.
If the IP address does not pass verification, the client sends a DHCP-DECLINE message to the server, and then requests a new IP address.
IP address lease extension
A dynamically assigned IP address has a lease. When the lease expires, the IP address is reclaimed by the DHCP server. To continue using the IP address, the client must extend the lease duration.
When about half of the lease duration elapses, the DHCP client unicasts a DHCPREQUEST to the DHCP server to extend the lease. Depending on the availability of the IP address, the DHCP server returns a DHCP-ACK or DHCP-NAK unicast message.
· A DHCP-ACK message confirms that the client's lease duration has been extended.
· A DHCP-NAK message denies the request.
The client broadcasts another DHCPREQUEST message for lease extension if it has not received a DHCP-ACK or DHCP-NAK reply when about seven-eighths of the lease duration elapses. Again, depending on the availability of the IP address, the DHCP server returns either a DHCP-ACK or a DHCP-NAK message.
DHCP message format
All types of DHCP message use the same message, except that they have different values for some of the fields.
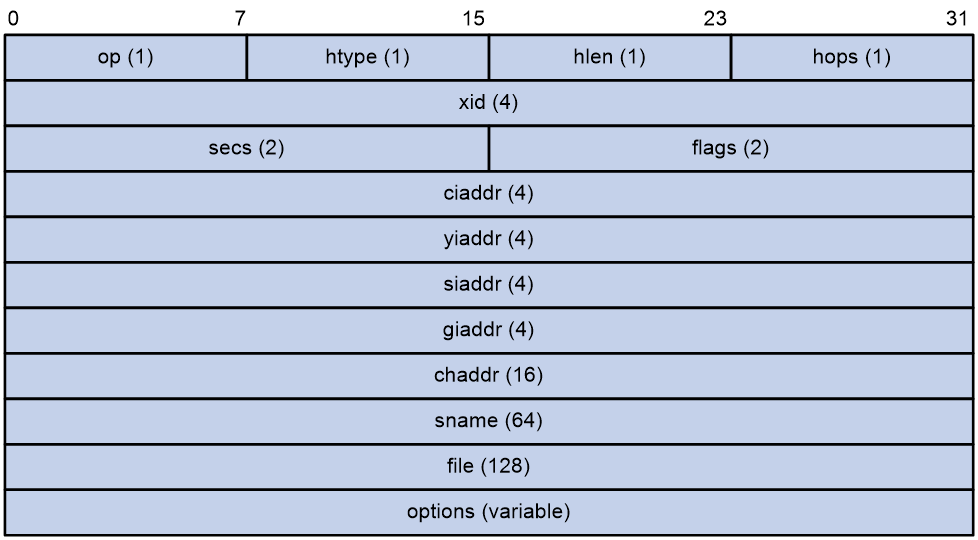
Figure 3 shows the DHCP message format. The numbers in parentheses indicate the size of each field in bytes.
· op—General type of the message. A value of 1 indicates a request message and a value of 2 indicates a reply message.
· htype, hlen—Hardware address type and length of the DHCP client.
· hops—Number of relay agents that a request message traveled.
· xid—Transaction ID, a random number chosen by the client to identify an IP address allocation transaction.
· secs—The number of seconds elapsed since the client began address acquisition or renewal process. This field is reserved and fixed at 0.
· flags—The leftmost bit is defined as the BROADCAST (B) flag. If this flag is set to 0, the DHCP server sent a reply back by unicast. If this flag is set to 1, the DHCP server sent a reply back by broadcast. The remaining bits of the flags field are reserved for future use.
· ciaddr—Client IP address if the client has an IP address that is valid and usable. Otherwise, set to zero. (The client does not use this field to request an IP address to lease.)
· yiaddr—Your IP address. It is an IP address assigned by the DHCP server to the DHCP client.
· siaddr—Server IP address, from which the client obtained configuration parameters.
· giaddr—Gateway IP address. It is the IP address of the first relay agent to which a request message travels.
· chaddr—Client hardware address.
· sname—Server host name, from which the client obtained configuration parameters.
· file—Boot file (also called system software image) name and path information, defined by the server to the client.
· options—Optional parameters field that is variable in length. Optional parameters include the message type, lease duration, domain name server IP address, and WINS IP address.
DHCP options
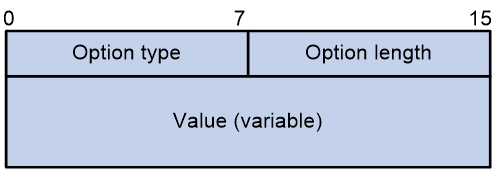
DHCP extends the message format as an extension to BOOTP for compatibility. DHCP uses the options field to carry information for dynamic address allocation and provide additional configuration information for clients.
Figure 4 DHCP option format
Common DHCP options
The following are common DHCP options:
· Option 3—Router option. It specifies the gateway address to be assigned to the clients. If Option 3 coexists with Option 121, Option 3 will be ingored.
· Option 6—DNS server option. It specifies the DNS server IP address to be assigned to the clients.
· Option 33—Static route option. It specifies a list of classful static routes (the destination addresses in these static routes are classful) that a client should add into its routing table. If both Option 33 and Option 121 exist, Option 33 is ignored.
· Option 51—IP address lease option.
· Option 53—DHCP message type option. It identifies the type of the DHCP message.
· Option 55—Parameter request list option. It is used by a DHCP client to request specified configuration parameters. The option includes values that correspond to the parameters requested by the client.
· Option 60—Vendor class identifier option. A DHCP client uses this option to identify its vendor. A DHCP server uses this option to distinguish DHCP clients, and assigns IP addresses to them.
· Option 66—TFTP server name option. It specifies the TFTP server domain name to be assigned to the clients.
· Option 67—Boot file name option. It specifies the boot file name to be assigned to the client.
· Option 121—Classless route option. It specifies a list of classless static routes (the destination addresses in these static routes are classless) that a client should add into its routing table. If Option 3, Option 33, and Option 121 exist, both Option 3 and Option 33 will be ignored.
· Option 150—TFTP server IP address option. It specifies the TFTP server IP address to be assigned to the clients.
For more information about DHCP options, see RFC 2132 and RFC 3442.
Custom DHCP options
Some options, such as Option 43, Option 82, and Option 184, have no standard definitions in RFC 2132.
Vendor-specific option (Option 43)
Option 43 function
DHCP servers and clients use Option 43 to exchange vendor-specific configuration information.
The DHCP client can obtain the following information through Option 43:
· ACS parameters, including the ACS URL, username, and password.
· Service provider identifier, which is acquired by the CPE from the DHCP server and sent to the ACS for selecting vender-specific configurations and parameters.
· PXE server address, which is used to obtain the boot file or other control information from the PXE server.
· AC address, which is used by an AP to obtain the boot file or other control information from the AC.
Option 43 format
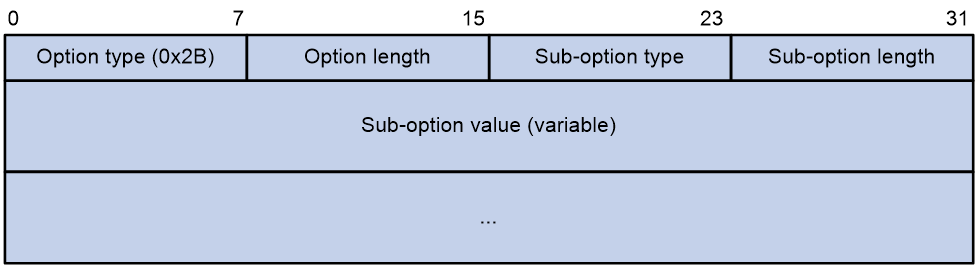
Figure 5 Option 43 format
Network configuration parameters are carried in different sub-options of Option 43 as shown in Figure 5.
· Sub-option type—The field value can be 0x01 (ACS parameter sub-option), 0x02 (service provider identifier sub-option), or 0x80 (PXE server address sub-option).
· Sub-option length—Excludes the sub-option type and sub-option length fields.
· Sub-option value—The value format varies by sub-option.
Sub-option value field format
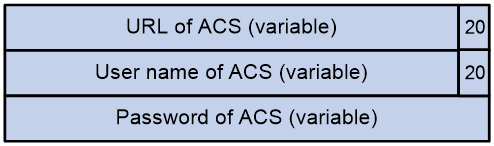
· ACS parameter sub-option value field—Includes the ACS URL, username, and password separated by spaces (hexadecimal number 20) as shown in Figure 6.
Figure 6 ACS parameter sub-option value field
· Service provider identifier sub-option value field—Includes the service provider identifier.
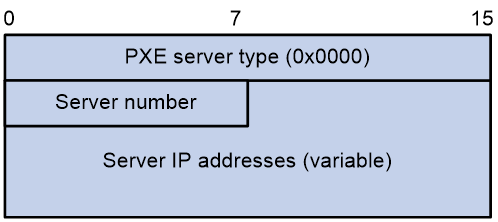
· PXE server address sub-option value field—Includes the PXE server type that can only be 0, the server number that indicates the number of PXE servers contained in the sub-option, and server IP addresses, as shown in Figure 7.
Figure 7 PXE server address sub-option value field
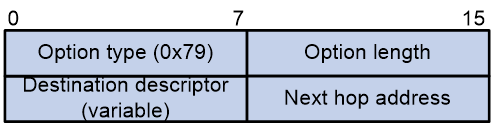
Relay agent option (Option 82)
Option 82 is the relay agent option. It records the location information about the DHCP client. When a DHCP relay agent or DHCP snooping device receives a client's request, it adds Option 82 to the request and sends it to the server.
The administrator can use Option 82 to locate the DHCP client and further implement security control and accounting. The DHCP server can use Option 82 to provide individual configuration policies for the clients.
Option 82 can include a maximum of 255 sub-options and must include a minimum of one sub-option. Option 82 supports two sub-options: sub-option 1 (Circuit ID) and sub-option 2 (Remote ID). Option 82 has no standard definition. Its padding formats vary by vendor.
· Circuit ID has the following padding modes:
¡ String padding mode—Includes a character string specified by the user.
¡ Normal padding mode—Includes the VLAN ID and interface number of the interface that receives the client's request.
¡ Verbose padding mode—Includes the access node identifier specified by the user, and the VLAN ID, interface number and interface type of the interface that receives the client's request.
· Remote ID has the following padding modes:
¡ String padding mode—Includes a character string specified by the user.
¡ Normal padding mode—Includes the MAC address of the DHCP relay agent interface or the MAC address of the DHCP snooping device that receives the client's request.
¡ Sysname padding mode—Includes the name of the device. To set the device name, use the sysname command in system view.
Option 184
Option 184 is a reserved option. You can define the parameters in the option as needed. The device supports Option 184 carrying voice related parameters, so a DHCP client with voice functions can get voice parameters from the DHCP server.
Option 184 has the following sub-options:
· Sub-option 1—Specifies the IP address of the primary network calling processor. The primary processor acts as the network calling control source and provides program download services. For Option 184, you must define sub-option 1 to make other sub-options take effect.
· Sub-option 2—Specifies the IP address of the backup network calling processor. DHCP clients contact the backup processor when the primary one is unreachable.
· Sub-option 3—Specifies the voice VLAN ID and the result whether the DHCP client takes this VLAN as the voice VLAN.
· Sub-option 4—Specifies the failover route that includes the IP address and the number of the target user. A SIP VoIP user uses this IP address and number to directly establish a connection to the target SIP user when both the primary and backup calling processors are unreachable.
Protocols and standards
· RFC 2131, Dynamic Host Configuration Protocol
· RFC 2132, DHCP Options and BOOTP Vendor Extensions
· RFC 1542, Clarifications and Extensions for the Bootstrap Protocol
· RFC 3046, DHCP Relay Agent Information Option
· RFC 3442, The Classless Static Route Option for Dynamic Host Configuration Protocol (DHCP) version 4
Configuring the DHCP relay agent
About DHCP relay agent
The DHCP relay agent enables clients to get IP addresses and configuration parameters from a DHCP server on another subnet.
Figure 8 shows a typical application of the DHCP relay agent.
Figure 8 DHCP relay agent application
DHCP relay agent operation
The DHCP server and client interact with each other in the same way regardless of whether the relay agent exists. For the interaction details, see "IP address allocation process." The following only describes steps related to the DHCP relay agent:
1. After receiving a DHCPDISCOVER or DHCPREQUEST broadcast message from a DHCP client, the DHCP relay agent processes the message as follows:
a. Fills the giaddr field of the message with its IP address.
b. Unicasts the message to the designated DHCP server.
2. Based on the giaddr field, the DHCP server returns an IP address and other configuration parameters in a response.
3. The relay agent conveys the response to the client.
Figure 9 DHCP relay agent operation
DHCP relay agent support for Option 82
Option 82 records the location information about the DHCP client. It enables the administrator to perform the following tasks:
· Locate the DHCP client for security and accounting purposes.
· Assign IP addresses in a specific range to clients.
For more information about Option 82, see "Relay agent option (Option 82)."
If the DHCP relay agent supports Option 82, it handles DHCP requests by following the strategies described in Table 1.
If a response returned by the DHCP server contains Option 82, the DHCP relay agent removes the Option 82 before forwarding the response to the client.
Table 1 Handling strategies of the DHCP relay agent
|
If a DHCP request has… |
Handling strategy |
The DHCP relay agent… |
|
Option 82 |
Drop |
Drops the message. |
|
Keep |
Forwards the message without changing Option 82. |
|
|
Replace |
Forwards the message after replacing the original Option 82 with the Option 82 padded according to the configured padding format, padding content, and code type. |
|
|
No Option 82 |
N/A |
Forwards the message after adding Option 82 padded according to the configured padding format, padding content, and code type. |
DHCP relay agent support for MCE
An MCE device acting as the DHCP relay agent can forward DHCP packets between a DHCP server and clients on either a public network or a private network. For more information about MCE, see MPLS Configuration Guide.
DHCP relay agent support for shared IP address pools
IP address pool sharing is an addressing policy used in DHCP relay networks. This policy enables a DHCP client to obtain an IP address that does not belongs to the same subnet as the giaddr address. When the address pool matching the giaddr address does not have usable addresses, the DHCP server can turn to other address pools that are in a sharing relationship with the matching address pool. This addressing policy ensures that DHCP clients can obtain valid IP addresses, thus guaranteeing stable network connections.
On the DHCP relay agent, IP address pools configured with the dhcp-server remote-ip-check bypass command form a sharing relationship.
Restrictions and guidelines: DHCP relay configuration
When the DHCP server uses a non-authorized address pool for address allocation on a DHCP relay network, you must configure IP addresses for the client-facing interfaces on the DHCP relay agent.
· When you configure the primary address of a client-facing interface, make sure the primary address and the address range specified for the non-authorized address pool belong to the same network segment.
· When you do not configure any primary address for a client-facing interface, make sure the following items belong to the same network segment:
¡ First secondary address of the client-facing interface.
¡ Address range specified for the non-authorized address pool.
An online user that comes online through a non-access method can go offline only passively after you change its online method to an access-type method on the DHCP relay agent. To have the user go offline in this situation, delete the IP address binding generated for the user on the DHCP server.
DHCP relay agent tasks at a glance
To configure a DHCP relay agent, perform the following tasks:
2. Enabling the DHCP relay agent on an interface
4. (Optional.) Configuring the DHCP relay agent security features
5. (Optional.) Configuring advanced functions:
¡ Configuring DHCP server liveness detection
¡ Configuring the DHCP relay agent to release an IP address
¡ Configuring DHCP relay agent support for Option 82
¡ Disabling remote IP address check
¡ Setting the DSCP value for DHCP packets sent by the DHCP relay agent
¡ Specifying the DHCP relay agent address for the giaddr field
¡ Specifying the source IP address for relayed DHCP requests
¡ Configuring the DHCP relay agent to always unicast relayed DHCP responses
¡ Configuring forwarding DHCP replies based on Option 82
¡ Setting the maximum number of DHCP-NAK packets
¡ Enabling the IP conflicting user offline feature
¡ Specifying a DHCP request processing method for roaming DHCP clients
¡ Enabling the non-first-hop DHCP relay agent feature
¡ Enabling DHCP-NAK-triggered remote BAS IP pool switchover
Enabling DHCP
Restrictions and guidelines
You must enable DHCP to make other DHCP relay agent settings take effect.
Procedure
1. Enter system view.
system-view
2. Enable DHCP.
dhcp enable
By default, DHCP is disabled.
Enabling the DHCP relay agent on an interface
About this task
With the DHCP relay agent enabled, an interface forwards incoming DHCP requests to a DHCP server.
An IP pool that contains the IP address of the DHCP relay interface must be configured on the DHCP server. Otherwise, the DHCP clients connected to the relay agent cannot obtain correct IP addresses.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable the DHCP relay agent.
dhcp select relay
By default, when DHCP is enabled, an interface operates in the DHCP server mode.
Specifying DHCP servers
Specifying DHCP servers on a relay agent
About this task
To improve availability, you can specify several DHCP servers on the DHCP relay agent. When the interface receives request messages from clients, the relay agent forwards them to all DHCP servers.
Restrictions and guidelines
The IP address of any specified DHCP server must not reside on the same subnet as the IP address of the relay interface. Otherwise, the clients might fail to obtain IP addresses.
If the desired DHCP server has both primary and secondary IP addresses, you can specify this DHCP server only by its primary IP address.
The DHCP relay agent forwards the packets from clients to the specified DHCP server in the specified virtual network (MPLS L3VPN instance or the public network). If you do not specify an MPLS L3VPN instance or the public network, the DHCP relay agent forwards the packets from a client in the same virtual network as the client.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Specify a DHCP server address on the relay agent.
dhcp relay server-address ip-address[ public | vpn-instance vpn-instance-name ]
By default, no DHCP server address is specified on the relay agent.
To specify multiple DHCP server addresses, repeat this step. You can specify a maximum of eight DHCP servers.
Configuring a remote BAS IP pool on a DHCP relay agent
About this task
You can create a remote BAS IP pool and specify DHCP servers in this IP pool. This feature allows DHCP clients of the same type to obtain IP addresses and other configuration parameters from the DHCP servers specified in the matching remote BAS IP pool.
It applies to scenarios where the DHCP relay agent connects to clients of the same access type but classified into different types by their locations. In this case, the relay interface typically has no IP address configured. You can use the gateway command to specify a gateway address for clients matching the same remote BAS IP pool and bind the gateway address to the device's MAC address. Example network is the IPoE network.
Upon receiving a DHCP DISCOVER or REQUEST from a client that matches a remote BAS IP pool, the relay agent processes the packet as follows:
· Fills the giaddr field of the packet with the specified gateway address.
· Forwards the packet to all DHCP servers in the matching IP pool.
The DHCP servers select an IP pool according to the gateway address.
Restrictions and guidelines
If IPoE or PPPoE users are in the network, the remote-server command also configures the device as a DHCP relay agent. You do not need to enable the DHCP relay agent by using the dhcp select relay command.
Procedure
1. Enter system view.
system-view
2. Create a remote BAS IP pool and enter its view.
ip pool pool-name bas remote
3. Specify a gateway address for the remote BAS IP pool.
gateway ip-address { mask mask | mask-len }
By default, no gateway address is specified.
4. Specify DHCP servers for the remote BAS IP pool.
remote-server ip-address&<1-8>
By default, no DHCP server is specified for the remote BAS IP pool.
You can specify a maximum of eight DHCP servers for one remote BAS IP pool for high availability.
Specifying the DHCP server selection algorithm
About this task
The DHCP relay agent supports the polling and master-backup DHCP server selection algorithms.
By default, the DHCP relay agent uses the polling algorithm. It forwards DHCP requests to all DHCP servers. The DHCP clients select the DHCP server from which the first received DHCP reply comes.
If the DHCP relay agent uses the master-backup algorithm, it forwards DHCP requests to the master DHCP server first. If the master DHCP server is not available, the relay agent forwards the subsequent DHCP requests to a backup DHCP server. If the backup DHCP server is not available, the relay agent selects the next backup DHCP server, and so on. If no backup DHCP server is available, it repeats the process starting from the master DHCP server.
The master DHCP server is determined in one of the following ways:
· In a common network where multiple DHCP server addresses are specified on the DHCP relay interface, the first specified DHCP server is the master. The other DHCP servers are backup.
· In a network where remote BAS IP pools are configured on the DHCP relay agent, the first specified DHCP server in a remote BAS IP pool is the master. The other DHCP servers in the IP pool are backup. Example networks are IPoE networks.
DHCP server selection supports the following functions:
· DHCP server response timeout time—The DHCP relay agent determines that a DHCP server is not available if it does not receive any response from the server within the DHCP server response timeout time. The DHCP server response timeout time is configurable and the default is 30 seconds.
· DHCP server switchback—If the DHCP relay agent selects a backup DHCP server, it does not switch back to the master DHCP server by default. You can configure the DHCP relay agent to switch back to the master DHCP server after a delay. If the master DHCP server is available, the DHCP relay agent forwards DHCP requests to the master DHCP server. If the master DHCP server is not available, the DHCP relay agent still uses the backup DHCP server.
Specifying the DHCP server selection algorithm in interface view
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Specify the DHCP server selection algorithm.
dhcp relay server-address algorithm { master-backup | polling }
By default, the polling algorithm is used. The DHCP relay agent forwards DHCP requests to all DHCP servers.
4. (Optional.) Set the DHCP server response timeout time for DHCP server switchover.
dhcp relay dhcp-server timeout time
By default, the DHCP server response timeout time is 30 seconds.
5. (Optional.) Enable the switchback to the master DHCP server and set the delay time.
dhcp relay master-server switch-delay delay-time
By default, the DHCP relay agent does not switch back to the master DHCP server.
Specifying the DHCP server selection algorithm in remote BAS IP pool view
1. Enter system view.
system-view
2. Enter remote BAS IP pool view.
ip pool pool-name bas remote
3. Specify the DHCP server selection algorithm.
dhcp relay server-address algorithm { master-backup | polling }
By default, the polling algorithm is used. The DHCP relay agent forwards DHCP requests to all DHCP servers.
4. (Optional.) Set the DHCP server response timeout time for DHCP server switchover.
dhcp-server timeout time
By default, the DHCP server response timeout time is 30 seconds.
5. (Optional.) Enable the switchback to the master DHCP server and set the delay time.
master-server switch-delay delay-time
By default, the DHCP relay agent does not switch back to the master DHCP server.
Configuring DHCP server liveness detection
About this task
The feature is applicable to a network where a DHCP server is selected from a remote BAS IP pool in an IP pool group.
This feature enables the DHCP relay agent to detect the liveness of the specified remote DHCP servers. Upon relaying the first DHCP request to a DHCP server, the DHCP relay agent starts the timeout timer and the request counter. The DHCP relay agent starts the timeout timer each time it relays a DHCP request. When the timeout timer expires, the DHCP relay agent checks the total number of DHCP requests relayed to the DHCP server. A communication failure occurs if the relay agent does not receive a reply within the timeout timer.
The mechanism of DHCP server liveness detection varies by the DHCP server selection algorithm:
· If the DHCP server selection algorithm is master-backup, the server liveness detection mechanism is as follows:
¡ Upon relaying the first DHCP request to the selected DHCP server, the DHCP relay agent starts the timeout timer configured for the DHCP server, and the request counter.
¡ If a reply is received within the timeout timer, the DHCP relay agent marks the DHCP server available, resets the request counter, and disables the timeout timer. The relay agent starts the timer and the counter again when it relays a new request.
¡ At the end of every timeout period, the relay agent checks the total number of consecutive communication failures to determine whether the DHCP server is unavailable.
|
|
NOTE: An unavailable DHCP server is a DHCP server in down ("dead") state or has no assignable IP addresses. |
- If the failure count does not exceed the dead-count-value value, the DHCP relay agent continues counting the number of requests. The DHCP relay agent marks the DHCP server unavailable if the dead-count-value value is reached at next check.
- If the failure count exceeds the dead-count-value value, the DHCP relay agent marks the DHCP server unavailable. The DHCP relay agent will relay new requests to other available remote DHCP servers.
If all remote DHCP servers are marked unavailable, the DHCP relay agent will relay new requests to all remote DHCP servers without starting the timeout timer.
¡ If the total number of consecutively received DHCP-NAK messages for the relayed lease renewal packets reaches the nak-count value, the DHCP relay agent also marks the DHCP server unavailable.
· If the DHCP server selection algorithm is polling, the server liveness detection mechanism is as follows:
¡ Upon relaying the first DHCP request to all of the specified remote DHCP servers, the DHCP relay agent starts the timeout timer and the request counter.
When different liveness detection settings are configured for the remote DHCP servers specified in the remote BAS IP pool, the DHCP relay agent uses the liveness detection settings that include the greatest timeout value. The relay agent detects only the liveness of the DHCP server corresponding to the used liveness detection settings. If the DHCP server is marked unavailable, the other DHCP servers in the remote BAS IP pool are also marked unavailable.
¡ If a reply that contains a usable address is received from a DHCP server within the timeout timer, the DHCP relay agent marks the DHCP server available. Meanwhile, the DHCP relay agent resets the request counter, and disables the timeout timer. The relay agent starts the timer and the counter again when it relays a new request.
¡ If a reply that notifies an address assignment failure is received from a DHCP server within the timeout timer, the DHCP relay agent marks the DHCP server unavailable. In this situation, the timeout timer keeps running and the DHCP relay agent continues counting the number of requests.
¡ At the end of every timeout period, the relay agent checks the total number of consecutive communication failures to determine whether the DHCP server is unavailable.
- If the failure count does not exceed the dead-count-value value, the DHCP relay agent continues counting the number of requests and starts the timeout timer again when it relays a new request.
- If the failure count exceeds the dead-count-value value, the DHCP relay agent marks all remote DHCP servers unavailable. In this situation, the DHCP relay agent relays new requests to all remote DHCP servers without starting the timeout timer.
When a DHCP server is marked unavailable, the relay agent starts the dead-time timer for the server. Within the dead-time timer, the relay agent does not relay any requests to the DHCP server even if the DHCP server is matched. After the dead-time timer expires, the relay agent determines that the DHCP server becomes available, and starts forwarding packets to this server.
When the DHCP relay agent receives a new DHCP request and all DHCP servers are marked unavailable, it treats all DHCP servers as available and relays the request to the first DHCP server.
Restrictions and guidelines
If the DHCP server selection algorithm is polling:
· When different liveness detection settings are configured for the remote DHCP servers specified in the remote BAS IP pool, the DHCP relay agent uses the liveness detection settings that include the greatest timeout value. The relay agent detects only the liveness of the DHCP server corresponding to the used liveness detection settings. If the DHCP server is marked unavailable, the other DHCP servers in the remote BAS IP pool are also marked unavailable.
· If multiple DHCP servers are configured with the greatest timeout value, the relay agent detects the liveness of DHCP servers by using the liveness detection settings that include the greatest timeout value and are deployed earliest.
The liveness detection settings specific to a DHCP server have a higher priority than the shared settings. If no DHCP server-specific settings are configured, the shared ones apply.
Procedure
1. Enter system view.
system-view
2. Configure DHCP server liveness detection.
dhcp server [ ip-address [ vpn-instance vpn-instance-name ] ] { dead-count dead-count-value | dead-time dead-time | nak-count nak-count-value | timeout timeout } *
By default, the relay agent marks the DHCP server as dead if the DHCP relay agent does not receive a reply from a DHCP server within 25 seconds.
Configuring the DHCP relay agent security features
Enabling the DHCP relay agent to record relay entries
About this task
Perform this task to enable the DHCP relay agent to automatically record clients' IP-to-MAC bindings (relay entries) after they obtain IP addresses through DHCP.
Some security features use the relay entries to check incoming packets and block packets that do not match any entry. In this way, illegal hosts are not able to access external networks through the relay agent. Examples of the security features are ARP address check and authorization ARP.
Restrictions and guidelines
The following information applies to WAN access users (for example, IPoE or PPPoE):
· The relay agent does not record client information for WAN access users if it has an authorized IP pool.
· The relay agent always records client information for WAN access users if it does not have an authorized IP pool. You cannot disable the relay agent from doing so.
Procedure
1. Enter system view.
system-view
2. Enable the relay agent to record relay entries.
dhcp relay client-information record
By default, the relay agent does not record relay entries.
Enabling periodic refresh of dynamic relay entries
About this task
A DHCP client unicasts a DHCP-RELEASE message to the DHCP server to release its IP address. The DHCP relay agent conveys the message to the DHCP server and does not remove the IP-to-MAC entry of the client.
With this feature, the DHCP relay agent uses the following information to periodically send a DHCPREQUEST message to the DHCP server:
· The IP address of a relay entry.
· The MAC address of the DHCP relay interface.
The relay agent maintains the relay entries depending on what it receives from the DHCP server:
· If the server returns a DHCP-ACK message or does not return any message within an interval, the DHCP relay agent removes the relay entry. In addition, upon receiving the DHCP-ACK message, the relay agent sends a DHCP-RELEASE message to release the IP address.
· If the server returns a DHCP-NAK message, the relay agent keeps the relay entry.
Restrictions and guidelines
This feature does not take effect on WAN access users (for example, IPoE and PPPoE). If the relay agent does not have an authorized IP pool, the relay agent removes the relay entry for a WAN access user after the lease for that user expires.
Procedure
1. Enter system view.
system-view
2. Enable periodic refresh of dynamic relay entries.
dhcp relay client-information refresh enable
By default, periodic refresh of dynamic relay entries is enabled.
3. (Optional.) Set the refresh interval.
dhcp relay client-information refresh { auto | interval interval }
By default, the refresh interval is auto, which is calculated based on the number of total relay entries.
Enabling lease release notification
About this task
The lease release notification feature enables the DHCP relay agent to send a Release message to the DHCP server after it deletes a relay entry. After the DHCP server receives the message, it reclaims the IP address and marks the lease as expired.
If you do not enable this feature, the DHCP relay agent will not send a Release message after it deletes a relay entry. This might cause a waste of IP addresses. To delete relay entries from the relay agent, you can use the reset dhcp relay client-information command.
Restrictions and guidelines
This command does not take effect on PPPoE users after you use the cut access-user command to forcibly log out users. The DHCP relay agent will always send Release messages to the DHCP server. For more information about the cut access-user command, see UCM commands in Security Command Reference.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable lease release notification.
dhcp relay release-agent
By default, lease release notification is enabled.
Enabling DHCP starvation attack protection
About this task
A DHCP starvation attack occurs when an attacker constantly sends forged DHCP requests using different MAC addresses in the chaddr field to a DHCP server. This exhausts the IP address resources of the DHCP server so legitimate DHCP clients cannot obtain IP addresses. The DHCP server might also fail to work because of exhaustion of system resources. The following methods are available to relieve or prevent such attacks.
· To relieve a DHCP starvation attack that uses DHCP packets encapsulated with different source MAC addresses, you can use one of the following methods:
¡ Limit the number of ARP entries that a Layer 3 interface can learn.
¡ Set the MAC learning limit for a Layer 2 port, and disable unknown frame forwarding when the MAC learning limit is reached.
· To prevent a DHCP starvation attack that uses DHCP requests encapsulated with the same source MAC address, you can enable MAC address check on the DHCP relay agent. The DHCP relay agent compares the chaddr field of a received DHCP request with the source MAC address in the frame header. If they are the same, the DHCP relay agent forwards the request to the DHCP server. If not, the relay agent discards the request.
Enable MAC address check only on the DHCP relay agent directly connected to the DHCP clients. A DHCP relay agent changes the source MAC address of DHCP packets before sending them.
A MAC address check entry has an aging time. When the aging time expires, both of the following occur:
· The entry ages out.
· The DHCP relay agent rechecks the validity of DHCP requests sent from the MAC address in the entry.
Procedure
1. Enter system view.
system-view
2. Set the aging time for MAC address check entries.
dhcp relay check mac-address aging-time time
The default aging time is 30 seconds.
This command takes effect only after you execute the dhcp relay check mac-address command.
3. Enter the interface view.
interface interface-type interface-number
4. Enable MAC address check.
dhcp relay check mac-address
By default, MAC address check is disabled.
Enabling DHCP proxy on the DHCP relay agent
About this task
The DHCP proxy feature isolates DHCP servers from DHCP clients and protects DHCP servers against attacks.
Upon receiving a response from the server, the DHCP server proxy performs the following task:
1. Modifies the server's IP address as the IP address of the relay's output interface or the IP address in the giaddr field.
2. Sends the response to the DHCP client.
On receipt of the response, the DHCP client will take the DHCP relay agent as the DHCP server.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable DHCP proxy on the interface.
dhcp-proxy enable
By default, the interface operates in DHCP server mode after DHCP is enabled.
Enabling client offline detection on the DHCP relay agent
About this task
The client offline detection on the DHCP relay agent detects the user online status based on the ARP entry aging. When an ARP entry ages out, the DHCP client offline detection feature deletes the relay entry for the IP address and sends a RELEASE message to the DHCP server.
Restrictions and guidelines
The feature does not function if an ARP entry is manually deleted.
Procedure
1. Enter system view.
system-view
2. Enable the relay agent to record relay entries.
dhcp relay client-information record
By default, the relay agent does not record relay entries.
Without relay entries, client offline detection cannot function correctly.
3. Enter interface view.
interface interface-type interface-number
4. Enable the DHCP relay agent.
dhcp select relay
By default, when DHCP is enabled, an interface operates in the DHCP server mode.
5. Enable client offline detection.
dhcp client-detect
By default, client offline detection is disabled on the DHCP relay agent.
Configuring the DHCP relay agent to release an IP address
About this task
Configure the relay agent to release the IP address for a relay entry. The relay agent sends a DHCP-RELEASE message to the server and meanwhile deletes the relay entry. Upon receiving the DHCP-RELEASE message, the DHCP server releases the IP address.
This command can release only the IP addresses in the recorded relay entries.
Procedure
1. Enter system view.
system-view
2. Configure the DHCP relay agent to release an IP address.
dhcp relay release ip ip-address [ vpn-instance vpn-instance-name ]
Configuring DHCP relay agent support for Option 82
To support Option 82, you must perform related configuration on both the DHCP server and relay agent.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable the relay agent to handle Option 82.
dhcp relay information enable
By default, handling of Option 82 is disabled.
4. (Optional.) Configure the strategy for handling DHCP requests that contain Option 82.
dhcp relay information strategy { drop | keep | replace }
By default, the handling strategy is replace.
If the handling strategy is replace, configure a padding mode and a padding format for Option 82. If the handling strategy is keep or drop, you do not need to configure a padding mode or padding format for Option 82.
5. (Optional.) Configure the padding mode and padding format for the Circuit ID sub-option.
dhcp relay information circuit-id { bas [ sub-interface-vlan ] [ with-vxlan ] | string circuit-id | { normal | verbose [ node-identifier { mac | sysname | user-defined node-identifier } ] [ interface [ vlan-in-vlan ] ] } [ sub-interface-vlan ] [ format { ascii | hex } ] }
By default, the padding mode for Circuit ID sub-option is normal, and the padding format is hex.
The device name (sysname) must not include spaces if it is configured as the padding content for sub-option 1. Otherwise, the DHCP relay agent will fail to add or replace Option 82.
6. (Optional.) Configure the padding mode and padding format for the Remote ID sub-option.
dhcp relay information remote-id { normal [ format { ascii | hex } ] | string remote-id | sysname }
By default, the padding mode for the Remote ID sub-option is normal, and the padding format is hex.
Disabling remote IP address check
About this task
In a DHCP relay network where no shared IP address pool is deployed, remote IP address check is enabled in IP address pools on the DHCP relay agent by default. Upon receiving an IP address from the server, the relay agent identifies whether that IP address belongs to the same subnet as the related gateway address in the relay address pool. If they do not belong to the same subnet, the DHCP user will fail to come online. To resolve this issue, use this feature to disable remote IP address check in the related IP address pools and configure them as shared IP address pools.
When the DHCP server cannot find an assignable IP address in the address pool matching the giaddr address, it assigns the requesting DHCP user an IP address from an address pool that is in a sharing relationship with the matching address pool. Upon receiving the assigned IP address, the relay agent directly sends it to the requesting DHCP user. As a result, the user can come online normally.
Procedure
1. Enter system view.
system-view
2. Enter the view of a relay IP address pool.
ip pool pool-name [ bas remote ]
3. Disable remote IP address check.
dhcp-server remote-ip-check bypass
By default, remote IP address check is enabled in the relay IP address pool. Upon receiving an IP address from the server, the relay agent identifies whether that IP address belongs to the same subnet as the related gateway address in the relay address pool. If they do not belong to the same subnet, the DHCP user will fail to come online.
Setting the DSCP value for DHCP packets sent by the DHCP relay agent
About this task
The DSCP value of a packet specifies the priority level of the packet and affects the transmission priority of the packet.
Procedure
1. Enter system view.
system-view
2. Set the DSCP value for DHCP packets sent by the DHCP relay agent.
dhcp dscp dscp-value
By default, the DSCP value in DHCP packets sent by the DHCP relay agent is 56.
Specifying the DHCP relay agent address for the giaddr field
Manually specifying the DHCP relay agent address for the giaddr field
About this task
This task allows you to specify the IP addresses to be encapsulated to the giaddr field of the DHCP requests. If you do not specify any DHCP relay agent address, the primary IP address of the DHCP relay interface is encapsulated to the giaddr field of DHCP requests.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Specify the DHCP relay agent address to be encapsulated in relayed DHCP requests.
dhcp relay gateway ip-address
By default, the primary IP address of the DHCP relay interface is encapsulated in the relayed DHCP requests.
Configuring smart relay to specify the DHCP relay agent address for the giaddr field
About this task
By default, the relay agent only encapsulates the primary IP address to the giaddr field of all requests before relaying them to the DHCP server. The DHCP server then selects an IP address on the same subnet as the address in the giaddr filed. If no assignable addresses on the subnet are available, the DHCP server does not assign any IP address. The DHCP smart relay feature is introduced to allow the DHCP relay agent to encapsulate secondary IP addresses when the DHCP server does not send back a DHCP-OFFER message.
The relay agent initially encapsulates its primary IP address to the giaddr field before forwarding a DHCP-DISCOVER message to the DHCP server. If no DHCP-OFFER is received, the relay agent allows the client to send a maximum of two DHCP-DISCOVER messages to the DHCP server by using the primary IP address. If no DHCP-OFFER message is returned after two retries, the relay agent switches to a secondary IP address. If the DHCP server still does not respond, the next secondary IP address is used. After the secondary IP addresses are all tried and the DHCP server does not respond, the relay agent repeats the process by starting from the primary IP address.
Procedure
1. Enter system view.
system-view
2. Enable the DHCP smart relay feature.
dhcp smart-relay enable
By default, the DHCP smart relay feature is disabled.
Specifying the source IP address for relayed DHCP requests
About specifying the source IP address for relayed DHCP requests
By default, the source IP address for relayed DHCP requests depends on the locations of the DHCP server and the server-facing interface on the relay agent:
· If the locations are the same, the relay agent uses the IP address of the output interface for relayed requests as the source IP address. For example, the source IP address is the IP address of Interface B in Figure 10.
Figure 10 The DHCP server and the server-facing interface are in the same VPN
· If the locations are different, the relay agent uses the lowest IP address that is in the same VPN instance as the DHCP server as the source address.
For example, the source IP address is the IP address of Interface C in Figure 11. If Interface C has multiple IP addresses that are in the same VPN instance as the DHCP server, the relay agent selects the lowest IP address as the source address.
Figure 11 The DHCP server and the server-facing interface are in different VPNs
The relay agent determines the location of that DHCP server as follows:
|
|
NOTE: In this task, the location of a DHCP server depends on the configuration of the public or vpn-instance keyword in the dhcp relay server-address command. For DHCP requests to reach a DHCP server, the relay agent must forward them to the location of that DHCP server. |
· When you specify the public keyword in the dhcp relay server-address command, the DHCP server location is the public network.
· When you specify the vpn-instance keyword in the dhcp relay server-address command, the DHCP server location is the specified VPN instance.
· When you use the dhcp relay server-address command without specifying the public or vpn-instance keyword, the DHCP server location depends on the location of the DHCP client. The DHCP client always runs on the same network (VPN instance or public network).
This task is required if multiple relay interfaces share the same IP address or if a relay interface does not have routes to DHCP servers. You can perform this task to specify an IP address or the IP address of another interface on the DHCP relay agent as the source IP address for relayed DHCP requests.
For common networks, you can perform this task on the DHCP relay interface. If you specify the ip-address argument, the relay agent changes not only the source IP address but also the giaddr field of a DHCP request. The DHCP server assigns the client an IP address on the same subnet as the specified IP address in the giaddr field. As a result, the client might not be on the same subnet as the DHCP relay interface (the gateway). To avoid this problem, you must configure Option 82 on the relay interface before specifying the ip-address argument. This configuration enables the DHCP relay agent to insert the primary IP address of the relay interface in Option 82. Based on this option, the DHCP server assigns an IP address on the same subnet as the IP address of the relay interface. The DHCP relay agent looks up the MAC address table for the output interface to forward the DHCP reply packets.
For some networks such as the IPoE networks, you must configure a remote BAS IP pool and specify the source IP address for DHCP requests in remote BAS IP pool view.
Specifying the source IP address for relayed DHCP requests (interface view)
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Specify the source IP address for DHCP requests.
dhcp relay source-address { ip-address [ option code [ option-text ] ] | gateway | relay-interface }
By default, the relay agent chooses the default source IP address for relayed requests depending on whether its server-side interface and the DHCP server belong to the same VPN instance:
¡ If they belong to the same VPN instance, the relay agent uses the IP address of the output interface for relayed requests as the default source IP address.
¡ If they belong to different VPN instances, the relay agent uses the lowest IP address that is in the same VPN instance as the DHCP server as the default source address.
|
Keyword |
Description |
|
ip-address [ option code [ option-text ] ] |
If a DHCP request carries the specified option, the relay agent changes the source IP address and the giaddr field of the DHCP request to the specified IP address. |
|
gateway |
The relay agent uses the IP address in the giaddr field as the source IP address. If the giaddr field is empty, the relay agent follows the default rule to specify the source IP address for DHCP requests. |
|
relay-interface |
The relay agent uses the primary IP address of the relay interface as the source IP address. If this interface does not have an IP address, the relay agent follows the default rule to specify the source IP address for DHCP requests. |
Specifying the source IP address for relayed DHCP requests (remote BAS IP pool view)
1. Enter system view.
system-view
2. Create a remote BAS IP pool and enter its view.
ip pool pool-name bas remote
3. Specify the source IP address for DHCP requests.
dhcp-server source-address { ip-address | gateway | interface interface-type interface-number }
By default, the relay agent chooses the default source IP address for relayed requests depending on whether its server-side interface and the DHCP server belong to the same VPN instance:
¡ If they belong to the same VPN instance, the relay agent uses the IP address of the output interface for relayed requests as the default source IP address.
¡ If they belong to different VPN instances, the relay agent uses the lowest IP address that is in the same VPN instance as the DHCP server as the default source address.
|
Keyword |
Description |
|
ip-address |
The relay agent uses the specified IP address as the source IP address for relay DHCP requests. |
|
gateway |
The relay agent uses the IP address in the giaddr field as the source IP address. If the giaddr field is empty, the relay agent follows the default rule to specify the source IP address for DHCP requests. |
|
interface interface-type interface-number |
The relay agent uses the IP address of the specified interface as the source IP address. If this interface does not have an IP address, the relay agent follows the default rule to specify the source IP address for DHCP requests. |
Configuring the DHCP relay agent to always unicast relayed DHCP responses
About this task
This feature enables the DHCP relay agent to ignore the broadcast flag and always unicast relayed responses. This feature is useful in some LANs, such as a WLAN network, where broadcast communication is not recommended.
Procedure
1. Enter system view.
system-view
2. Enable the DHCP relay agent to always unicast relayed DHCP responses.
dhcp relay always-unicast
By default, the DHCP relay agent reads the broadcast flag to decide whether to broadcast or unicast a response.
Configuring forwarding DHCP replies based on Option 82
About this task
Configure this feature if the DHCP relay agent is required to forward DHCP replies to DHCP clients based on Option 82.
For example, an IPRAN network has a primary gateway and a secondary gateway. An L3VE interface is configured as the relay interface on each of the gateways. Multiple L2VE subinterfaces are configured to receive packets. One L2VE subinterface corresponds to one PW. Only the primary gateway receives DHCP requests, but both the primary and secondary gateways might receive DHCP replies. The primary gateway can forward DHCP replies based on locally recorded user information, but the secondary gateway cannot. The secondary gateway can only forward DHCP replies to all PWs.
To enable the secondary gateway to forward a DHCP reply to only the intended PW, perform the following tasks:
· Configure the dhcp relay information enable and dhcp relay information circuit-id (with sub-interface-vlan specified) commands on the primary gateway. Then, when the primary gateway receives a DHCP request, it adds Option 82 to the reply and record the VLAN ID of the L2VE subinterface.
· Configure the dhcp relay information enable, dhcp relay information circuit-id (with sub-interface-vlan specified), and dhcp relay forward reply by-option82 commands on the secondary gateway. Then, when the secondary gateway receives a DHCP reply, it resolves Option 82, records the VLAN ID of the L2VE subinterface, and forwards the reply to the PW.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable the relay agent to handle Option 82.
dhcp relay information enable
By default, handling of Option 82 is disabled.
4. Configure the padding mode and padding format for the Circuit ID sub-option.
dhcp relay information circuit-id { bas [ sub-interface-vlan ] [ with-vxlan ] | string circuit-id | { normal | verbose [ node-identifier { mac | sysname | user-defined node-identifier } ] [ interface [ vlan-in-vlan ] ] } [ sub-interface-vlan ] [ format { ascii | hex } ] }
By default, the padding mode for the Circuit ID sub-option is normal, and the padding format is hex.
The device name (set by using the sysname command) must not include spaces if it is configured as the padding content for sub-option 1. Otherwise, the DHCP relay agent will fail to add or replace Option 82.
You must set the padding mode to bas, normal, or verbose, and specify the sub-interface-vlan keyword for this command.
5. Configure the DHCP relay agent to forward DHCP replies based on Option 82.
dhcp relay forward reply by-option82
By default, the DHCP relay agent does not forward DHCP replies based on Option 82.
Setting the maximum number of DHCP-NAK packets
About this task
This value limits the maximum number of DHCP-NAK packets that the DHCP relay can receive from one DHCP server. Use this feature only in a network when the master-backup server selection is configured in the remote BAS IP pool. In such a network, you can use the gateway command to specify gateway addresses for users that match the remote BAS IP pool. When the relay agent receives a lease renew request from a DHCP client, the relay agent forwards the request to the currently selected DHCP server. When the number of DHCP-NAK packets from the DHCP server reaches the upper limit, the DHCP relay agent performs one of the following operations, depending on the configuration:
· If the gateway-only keyword is not configured, the DHCP relay agent forwards the request to the next DHCP server.
· If the gateway-only keyword is configured and smart relay is enabled, the relay agent uses the next gateway address configured in the gateway command to fill the giaddr field.
· If the gateway-only keyword is not configured, and smart relay is enabled, the relay agent performs the following operations:
a. Uses the next gateway address in the gateway command to fill the giaddr field.
b. Forwards the request to the next DHCP server.
Procedure
1. Enter system view.
system-view
2. Enter remote BAS IP pool view.
ip pool pool-name bas remote
3. Set the maximum of DHCP-NAK packets that the DHCP relay agent can receive from one DHCP server.
dhcp-server nak-count nak-count-value [ gateway-only ]
By default, the DHCP relay agent can receive a maximum of 10 DHCP-NAK packets from one DHCP server.
Enabling the IP conflicting user offline feature
About this task
The following IP address conflicts might occur in a network:
· The IP address assigned by the authentication and authorization module to a new user is the same as the IP address of an online DHCP client.
· The IP address assigned by the DHCP server to a new DHCP client is the same as the IP address in the DHCP relay entry of an online DHCP client.
If these conflicts occur, by default, the conflicting online DHCP clients still stay online, and new users cannot come online.
This feature enables the server to release the conflicting IP address when an IP conflict occurs, and informs the access module that the address is not available. Both the online user and requesting users are offline. It ensures that a new user can obtain an IP address next time the user request the IP address through DHCP.
With this feature enabled on the DHCP relay agent, the relay agent processes the conflicts as follows:
· If the IP address assigned to a new user by the authentication and authorization module conflicts with the DHCP relay entry of an online client, the relay agent performs the following operations:
a. Sends a DHCP-RELEASE packet to the DHCP server to release the conflicting IP address.
b. Informs the access module of the new user that this IP address is not available.
· If the IP address in the DHCP reply for a new user conflicts with the DHCP relay entry of an online client, the relay agent performs the following operations:
a. Sends a DHCP-RELEASE packet to the server to release the conflicting IP address.
b. Drops the DHCP reply.
Restrictions and guidelines
This feature takes effect on the DHCP relay agent only after you enable the recording of relay entries on it.
Enable this feature on the DHCP relay device if one DHCP relay agent-enabled interface connects to an IPoE network and the other DHCP relay agent-enabled interface connects to a common network. This is because the following commands are required on the device for IPoE:
· dhcp relay client-information record
· undo dhcp relay client-information refresh enable
In this case, the common network-facing interface records DHCP relay entries but does not update them. An IP address conflict occurs if the IP address assigned to a new client already exists in a recorded DHCP relay entry. With this feature enabled, DHCP clients can obtain IP addresses correctly.
Procedure
1. Enter system view.
system-view
2. Enable the IP conflicting user offline feature.
dhcp conflict-ip-address offline
By default, the IP conflicting user offline feature is disabled. When the IP address assigned to a new DHCP client conflicts with the IP address of an online DHCP client, the online DHCP client still stays online.
Specifying a DHCP request processing method for roaming DHCP clients
About this task
When a DHCP client roams in a network, the client sends an offline request to the DHCP relay agent before requesting a new address. If the DHCP relay agent does not receive the offline request, it will discard the DHCP client's new address request because it determines that the request is an attack packet.
This feature allows the DHCP relay agent to process address requests as follows upon receiving them from roaming DHCP clients:
· The fast-renew method enables the relay agent to inform the DHCP server to release existing address leases of roaming clients and forward the requests to the DHCP server.
· The roam method enables the relay agent to forward the address requests to the DHCP server. The clients can use the original IP addresses to access the network without another authentication.
Restrictions and guidelines
This feature is applicable to only IPoE networks.
The roam keyword in the dhcp session-mismatch action { fast-renew | roam } command can take effect only after you enable roaming for IPoE individual users by using the ip subscriber roaming enable command.
For more information about IPoE roaming, see IPoE configuration in Layer 2—WAN Access Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Specify a method for the DHCP relay agent to process address requests of roaming clients.
dhcp session-mismatch action { fast-renew | roam }
By default, the DHCP relay agent discards DHCP address requests sent from roaming DHCP clients.
Enabling the non-first-hop DHCP relay agent feature
About this task
Multiple DHCP relay agents might exist between a DHCP client and the DHCP server. By default, only the first DHCP relay agent that the DHCP request passes through processes the request and the subsequent DHCP relay agents only forward the request. If access authentication is enabled on a non-first DHCP relay agent, execute this command on this relay agent for the relay agent to deliver the packet to the authentication module for authentication and authorization.
Enable this feature only on the non-first-hop DHCP relay agent where access authentication is enabled.
Restrictions and guidelines
To have this feature function correctly, follow these restrictions and guidelines when you configure it on a non-first-hop DHCP relay device:
· Enable DHCP relay agent on the downstream interface of the device.
· Enable the non-first-hop DHCP relay agent feature on both the upstream and downstream interfaces of the device.
· Do not use the following commands to change the value in the giaddr field:
¡ dhcp relay gateway
¡ dhcp relay source-address
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable the non-first-hop DHCP relay agent feature.
dhcp relay non-first-hop enable
By default, the non-first-hop DHCP relay agent feature is disabled.
Enabling DHCP-NAK-triggered remote BAS IP pool switchover
About this task
Some DHCP servers respond with DHCP-NAK messages to the DHCP-DISCOVER messages from clients when they have no assignable IP addresses. By default, the relay agent continues to forward DHCP-DISCOVER messages to the server, regardless of how many DHCP-NAK messages it has received from that server. If the server is in one remote BAS IP pool in an IP pool group, the server does not move to the next remote BAS IP pool, if any.
For clients to obtain an IP address as soon as possible from one of the remote BAS IP pools in an IP pool group, set the DHCP-NAK threshold and statistic period to trigger remote BAS IP pool switchover
Procedure
1. Enter system view.
system-view
2. Enter IP pool group view.
ip pool-group pool-group-name
3. Set the DHCP-NAK threshold and statistic period for DHCP-NAK-triggered remote BAS IP pool switchover.
discover-nak-count nak-count seconds
By default, the relay agent forwards DHCP-DISCOVER messages to the server in the current remote BAS IP pool, regardless of how many DHCP-NAK messages it has received from that server.
Display and maintenance commands for DHCP relay agent
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display information about DHCP servers on an interface. |
display dhcp relay server-address [ interface interface-type interface-number ] |
|
Display Option 82 configuration information on the DHCP relay agent. |
display dhcp relay information [ interface interface-type interface-number ] |
|
Display relay entries on the DHCP relay agent. |
display dhcp relay client-information [ interface interface-type interface-number | [ ip ip-address ] [ vpn-instance vpn-instance-name ] ] |
|
Display the DHCP server configuration and status in the remote BAS IP pool on the DHCP relay agent. |
display dhcp relay remote-server-info [ vpn-instance vpn-name ] [ slot slot-number ] |
|
Display packet statistics on the DHCP relay agent. |
display dhcp relay packet statistics [ interface interface-type interface-number ] |
|
Display MAC address check entries on the DHCP relay agent. |
display dhcp relay check mac-address |
|
Clear relay entries on the DHCP relay agent. |
reset dhcp relay client-information [ interface interface-type interface-number | ip ip-address [ vpn-instance vpn-instance-name ] ] |
|
Clear packet statistics on the DHCP relay agent. |
reset dhcp relay packet statistics [ interface interface-type interface-number ] |
DHCP relay agent configuration examples
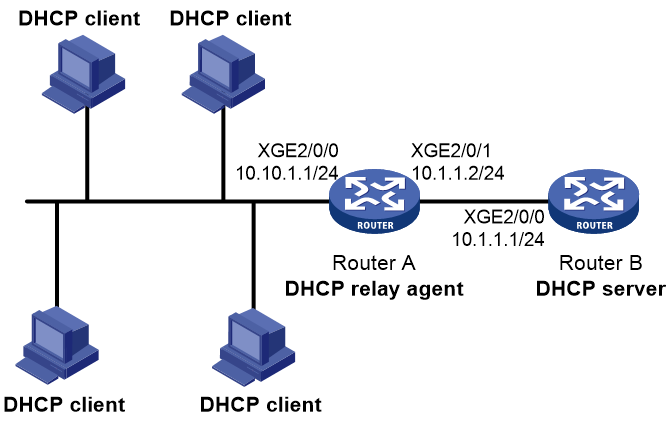
Example: Configuring basic DHCP relay agent
Network configuration
As shown in Figure 12, configure the DHCP relay agent on Router A. The DHCP relay agent enables DHCP clients to obtain IP addresses and other configuration parameters from the DHCP server on another subnet.
Prerequisites
Because the DHCP relay agent and server are on different subnets, configure static or dynamic routing to make them reachable to each other.
Configure the required settings (such as address pools) on the DHCP server to guarantee the client-server communication through the DHCP relay agent.
Procedure
# Specify IP addresses for the interfaces. (Details not shown.)
# Enable DHCP.
<RouterA> system-view
# Enable the DHCP relay agent on Ten-GigabitEthernet 2/0/0.
[RouterA] interface ten-gigabitethernet 2/0/0
[RouterA-Ten-GigabitEthernet2/0/0] dhcp select relay
# Specify the IP address of the DHCP server on the relay agent.
[RouterA-Ten-GigabitEthernet2/0/0] dhcp relay server-address 10.1.1.1
Verifying the configuration
# Verify that DHCP clients can obtain IP addresses and all other network parameters from the DHCP server through the DHCP relay agent. (Details not shown.)
# Display the statistics of DHCP packets forwarded by the DHCP relay agent.
[RouterA] display dhcp relay packet statistics
# Display relay entries if you have enabled relay entry recording on the DHCP relay agent.
[RouterA] display dhcp relay client-information
Example: Configuring Option 82
Network configuration
As shown in Figure 12, the DHCP relay agent (Router A) replaces Option 82 in DHCP requests before forwarding them to the DHCP server (Router B).
· The Circuit ID sub-option is company001.
· The Remote ID sub-option is device001.
Prerequisites
To use Option 82, enable the DHCP server to handle Option 82.
Procedure
# Specify IP addresses for the interfaces. (Details not shown.)
# Enable DHCP.
<RouterA> system-view
[RouterA] dhcp enable
# Enable the DHCP relay agent on Ten-GigabitEthernet 2/0/0.
[RouterA] interface ten-gigabitethernet 2/0/0
[RouterA-Ten-GigabitEthernet2/0/0] dhcp select relay
# Specify the IP address of the DHCP server on the relay agent.
[RouterA-Ten-GigabitEthernet2/0/0] dhcp relay server-address 10.1.1.1
# Enable the DHCP relay agent to handle Option 82, and perform Option 82 related configuration.
[RouterA-Ten-GigabitEthernet2/0/0] dhcp relay information enable
[RouterA-Ten-GigabitEthernet2/0/0] dhcp relay information strategy replace
[RouterA-Ten-GigabitEthernet2/0/0] dhcp relay information circuit-id string company001
[RouterA-Ten-GigabitEthernet2/0/0] dhcp relay information remote-id string device001
Example: Configuring DHCP server selection
Network configuration
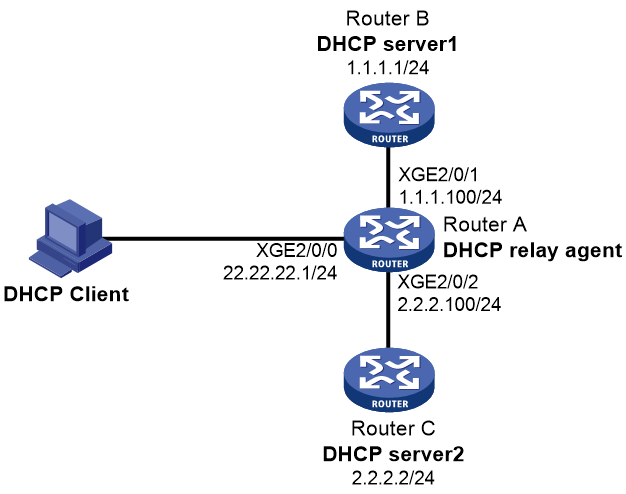
As shown in Figure 13, the DHCP client and the DHCP servers are in different subnets. DHCP server 1 and DHCP server 2 both have an IP pool that contains IP addresses in subnet 22.22.22.0/24, but neither has DHCP enabled.
Configure the DHCP relay agent for the DHCP client to obtain an IP address in subnet 22.22.22.0/24 and other configuration parameters from a DHCP server. The DHCP relay agent is connected to the DHCP client through Ten-GigabitEthernet 2/0/0, to DHCP server 1 through Ten-GigabitEthernet 2/0/1, and to DHCP server 2 through Ten-GigabitEthernet 2/0/2.
Procedure
1. Assign IP addresses to interfaces on the routers. (Details not shown.)
2. Configure Router B and Router C as DHCP servers. (Details not shown.)
3. Configure the DHCP relay agent on Router A:
# Enable DHCP.
<RouterA> system-view
[RouterA] dhcp enable
# Enable the DHCP relay agent on Ten-GigabitEthernet 2/0/0.
[RouterA] interface ten-gigabitethernet 2/0/0
[RouterA-Ten-GigabitEthernet2/0/0] dhcp select relay
# Specify the IP addresses of the DHCP servers.
[RouterA-Ten-GigabitEthernet2/0/0] dhcp relay server-address 1.1.1.1
[RouterA-Ten-GigabitEthernet2/0/0] dhcp relay server-address 2.2.2.2
# Specify the DHCP server selection algorithm as master-backup.
[RouterA-Ten-GigabitEthernet2/0/0] dhcp relay server-address algorithm master-backup
# Configure the DHCP relay agent to switch back to the master DHCP server 3 minutes after it switches to the backup DHCP server.
[RouterA-Ten-GigabitEthernet2/0/0] dhcp relay master-server switch-delay 3
[RouterA-Ten-GigabitEthernet2/0/0] quit
Verifying the configuration
# Verify that the DHCP client cannot obtain an IP address and that the following log is output in about 30 seconds.
DHCPR/3/DHCPR_SERVERCHANGE:
Switched to the server at 2.2.2.2 because the current server did not respond.
# Enable DHCP on the DHCP server at 1.1.1.1. (Details not shown.)
# Verify that the DHCP client cannot obtain an IP address and that the following log is output in about 3 minutes.
DHCPR/3/DHCPR_SWITCHMASTER:
Switched to the master DHCP server at 1.1.1.1.
# Verify that the DHCP client obtains an IP address. (Details not shown.)
Troubleshooting DHCP relay agent configuration
Failure of DHCP clients to obtain configuration parameters through the DHCP relay agent
Symptom
DHCP clients cannot obtain configuration parameters through the DHCP relay agent.
Solution
Some problems might occur with the DHCP relay agent or server configuration.
To locate the problem, enable debugging and execute the display command on the DHCP relay agent to view the debugging information and interface state information.
Check that:
· DHCP is enabled on the DHCP server and relay agent.
· The DHCP server has an IP pool on the same subnet as the DHCP clients.
· The DHCP server and DHCP relay agent can reach each other.
· The DHCP server address specified on the DHCP relay interface connected to the DHCP clients is correct.
Configuring the DHCP client
About DHCP client
With DHCP client enabled, an interface uses DHCP to obtain configuration parameters from the DHCP server, for example, an IP address.
Restrictions and guidelines: DHCP client configuration
The DHCP client configuration is supported only on Layer 3 Ethernet interfaces (or subinterfaces) and Layer 3 aggregate interfaces..
DHCP client tasks at a glance
To configure a DHCP client, perform the following tasks:
1. Enabling DHCP client on an interface
2. Configuring a DHCP client ID for an interface
Perform this task if the DHCP client uses the client ID to obtain IP addresses.
3. (Optional.) Enabling duplicated address detection
4. (Optional.) Setting the DSCP value for DHCP packets sent by the DHCP client
5. (Optional.) Configuring SNMP notifications for the DHCP client
Enabling DHCP client on an interface
Restrictions and guidelines
· If the number of IP address request failures reaches the system-defined amount, the DHCP client-enabled interface uses a default IP address.
· An interface can be configured to acquire an IP address in multiple ways. The new configuration overwrites the old.
· Secondary IP addresses cannot be configured on an interface that is enabled with the DHCP client.
· If the interface obtains an IP address on the same segment as another interface on the device, the interface does not use the assigned address. Instead, it requests a new IP address from the DHCP server.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure an interface to use DHCP for IP address acquisition.
ip address dhcp-alloc
By default, an interface does not use DHCP for IP address acquisition.
Configuring a DHCP client ID for an interface
About this task
A DHCP client ID is added to the DHCP option 61 to uniquely identify a DHCP client. A DHCP server can assign IP addresses to clients based on their DHCP client IDs.
DHCP client ID includes an ID type and a type value. Each ID type has a fixed type value. You can specify a DHCP client ID by using one of the following methods:
· Use an ASCII string as the client ID. If an ASCII string is used, the type value is 00.
· Use a hexadecimal number as the client ID. If a hexadecimal number is used, the type value is the first two characters in the number.
· Use the MAC address of an interface to generate a client ID. If this method is used, the type value is 01.
The type value of a DHCP client ID can be displayed by the display dhcp server ip-in-use or display dhcp client command.
Restrictions and guidelines
Make sure the ID for each DHCP client is unique.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure a DHCP client ID for the interface.
dhcp client identifier { ascii ascii-string | hex hex-string | mac interface-type interface-number }
By default, an interface generates the DHCP client ID based on its MAC address. If the interface has no MAC address, it uses the MAC address of the first Ethernet interface to generate its client ID.
Enabling duplicated address detection
About this task
DHCP client detects IP address conflict through ARP packets. An attacker can act as the IP address owner to send an ARP reply. The spoofing attack makes the client unable to use the IP address assigned by the server. As a best practice, disable duplicate address detection when ARP attacks exist on the network.
Procedure
1. Enter system view.
system-view
2. Enable duplicate address detection.
dhcp client dad enable
By default, the duplicate address detection feature is disabled on an interface.
Setting the DSCP value for DHCP packets sent by the DHCP client
About this task
The DSCP value of a packet specifies the priority level of the packet and affects the transmission priority of the packet.
Procedure
1. Enter system view.
system-view
2. Set the DSCP value for DHCP packets sent by the DHCP client.
dhcp client dscp dscp-value
By default, the DSCP value in DHCP packets sent by the DHCP client is 56.
Configuring SNMP notifications for the DHCP client
About this task
This task enables the DHCP client module to report critical events in SNMP notifications to network administrators.
· ARP conflict notifications—An ARP conflict notification is generated when the DHCP client module detects an IP address conflict through gratuitous ARP after obtaining an IP address.
· Local address conflict notifications—A local address conflict notification is generated when the DHCP client module obtains an IP address that is in the same subnet as one of the local interface addresses.
The SNMP notifications are sent to the SNMP module. For the SNMP notifications to be sent correctly, you must also configure SNMP. For more information about SNMP configuration, see SNMP configuration in Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enable SNMP notifications for the DHCP client module.
snmp-agent trap enable dhcp-client [ arp-conflict | local-conflict ] *
By default, all SNMP notifications are enabled for the DHCP client module.
Display and maintenance commands for DHCP client
Execute display command in any view.
|
Task |
Command |
|
Display DHCP client information. |
display dhcp client [ verbose ] [ interface interface-type interface-number ] |
DHCP client configuration examples
Example: Configuring DHCP client
Network configuration
As shown in Figure 15, Router B contacts the DHCP server through Ten-GigabitEthernet 2/0/0 to obtain an IP address, a DNS server address, and static route information. The DHCP client's IP address resides on subnet 10.1.1.0/24. The DNS server address is 20.1.1.1. The next hop of the static route to subnet 20.1.1.0/24 is 10.1.1.2.
The DHCP server uses Option 121 to assign static route information to DHCP clients. Figure 14 shows the Option 121 format. The destination descriptor field contains the following parts: subnet mask length and destination network address, both in hexadecimal notation. In this example, the destination descriptor is 18 14 01 01 (the subnet mask length is 24 and the network address is 20.1.1.0 in dotted decimal notation). The next hop address is 0A 01 01 02 (10.1.1.2 in dotted decimal notation).
Procedure
1. Configure Router A. Details are not shown.
2. Configure Router B:
# Configure Ten-GigabitEthernet 2/0/0 to use DHCP for IP address acquisition.
<RouterB> system-view
[RouterB] interface ten-gigabitethernet 2/0/0
[RouterB-Ten-GigabitEthernet2/0/0] ip address dhcp-alloc
[RouterB-Ten-GigabitEthernet2/0/0] quit
Verifying the configuration
# Display the IP address and other network parameters assigned to Router B.
[RouterB] display dhcp client verbose
Ten-GigabitEthernet2/0/0 DHCP client information:
Current state: BOUND
Allocated IP: 10.1.1.3 255.255.255.0
Allocated lease: 864000 seconds, T1: 331858 seconds, T2: 756000 seconds
Lease from May 21 19:00:29 2012 to May 31 19:00:29 2012
DHCP server: 10.1.1.1
Transaction ID: 0xcde72232
Classless static routes:
Destination: 20.1.1.0, Mask: 255.255.255.0, NextHop: 10.1.1.2
DNS servers: 20.1.1.1
Client ID type: acsii(type value=00)
Client ID value: 000c.29d3.8659-XGE2/0/0
Client ID (with type) hex: 0030-3030-632e-3239-
6433-2e38-3635-392d-
4574-6830-2f30-2f32
T1 will timeout in 3 days 19 hours 48 minutes 43 seconds
# Display the route information on Router B. The output shows that a static route to subnet 20.1.1.0/24 is added to the routing table.
[RouterB] display ip routing-table
Destinations : 11 Routes : 11
Destination/Mask Proto Pre Cost NextHop Interface
10.1.1.0/24 Direct 0 0 10.1.1.3 XGE2/0/0
10.1.1.3/32 Direct 0 0 127.0.0.1 InLoop0
20.1.1.0/24 Static 70 0 10.1.1.2 XGE2/0/0
10.1.1.255/32 Direct 0 0 10.1.1.3 XGE2/0/0
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
Configuring the BOOTP client
About BOOTP client
BOOTP client application
An interface that acts as a BOOTP client can use BOOTP to obtain information (such as IP address) from the BOOTP server.
To use BOOTP, an administrator must configure a BOOTP parameter file for each BOOTP client on the BOOTP server. The parameter file contains information such as MAC address and IP address of a BOOTP client. When a BOOTP client sends a request to the BOOTP server, the BOOTP server searches for the BOOTP parameter file and returns the corresponding configuration information.
BOOTP is usually used in relatively stable environments. In network environments that change frequently, DHCP is more suitable.
Because a DHCP server can interact with a BOOTP client, you can use the DHCP server to assign an IP address to the BOOTP client. You do not need to configure a BOOTP server. The DHCP server will assign an IP address to the BOOTP client based on the IP address allocation sequence.
Obtaining an IP address dynamically
A BOOTP client dynamically obtains an IP address from a BOOTP server as follows:
1. The BOOTP client broadcasts a BOOTP request, which contains its own MAC address.
2. Upon receiving the request, the BOOTP server searches the configuration file for the IP address and other information according to the BOOTP client's MAC address.
3. The BOOTP server returns a BOOTP response to the BOOTP client.
4. The BOOTP client obtains the IP address from the received response.
A DHCP server can take the place of the BOOTP server in the following dynamic IP address acquisition.
Protocols and standards
· RFC 951, Bootstrap Protocol (BOOTP)
· RFC 2132, DHCP Options and BOOTP Vendor Extensions
· RFC 1542, Clarifications and Extensions for the Bootstrap Protocol
Configuring an interface to use BOOTP for IP address acquisition
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
BOOTP client configuration applies only to Layer 3 Ethernet interfaces (including subinterfaces), and Layer 3 aggregate interfaces.
3. Configure an interface to use BOOTP for IP address acquisition.
ip address bootp-alloc
By default, an interface does not use BOOTP for IP address acquisition.
Display and maintenance commands for BOOTP client
Execute display command in any view.
|
Task |
Command |
|
Display BOOTP client information. |
display bootp client [ interface interface-type interface-number ] |
BOOTP client configuration examples
Example: Configuring BOOTP client
Network configuration
As shown in Figure 16, Ten-GigabitEthernet 2/0/0 of Router B connects to the LAN to obtain an IP address from the DHCP server by using BOOTP.
Prerequisites
To make the BOOTP client obtain an IP address from the DHCP server, configure the required settings (such as address pools) on the DHCP server.
Procedure
The following describes the configuration on Router B, which acts as a client.
# Configure Ten-GigabitEthernet 2/0/0 to use BOOTP to obtain an IP address.
<RouterB> system-view
[RouterB] interface ten-gigabitethernet 2/0/0
[RouterB-Ten-GigabitEthernet2/0/0] ip address bootp-alloc
Verifying the configuration
# Display the IP address assigned to the BOOTP client.
[RouterB] display bootp client