- Table of Contents
-
- 01-Fundamentals Configuration Guide
- 00-Preface
- 01-CLI configuration
- 02-FTP and TFTP configuration
- 03-RBAC configuration
- 04-File system management configuration
- 05-Login management configuration
- 06-Device management configuration
- 07-Software upgrade configuration
- 08-Configuration file management configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 06-Device management configuration | 295.71 KB |
Device management restrictions and guidelines
Device management tasks at a glance
Restrictions and guidelines for configuring the system time
System time configuration tasks at a glance
Setting the system time at the CLI
Obtaining the UTC time through NTP or PTP
Setting the daylight saving time
Enabling displaying the copyright statement
Disabling password recovery capability
Setting the operating mode for an interface card
Setting the port status detection timer
Monitoring kernel memory fragments
Configuring the power saving feature
Configuring an energy saving mode
Configuring device poweroff alarming
Verifying and diagnosing transceiver modules
Diagnosing transceiver modules
Restrictions and guidelines for task scheduling
Restrictions and guidelines for device reboot
Rebooting devices immediately at the CLI
Restoring the factory-default configuration
Display and maintenance commands for device management configuration
Managing the device
About device management
This chapter describes how to configure basic device parameters and manage the device. You can perform the configuration tasks in this chapter in any order.
Device management restrictions and guidelines
After being powered on, a card takes some time to start up and complete configuration and data restoration and synchronization. Before configuring the card, use the display device and display system stable state commands to verify that the card is in Normal and Stable states. Failing to follow this rule might cause configuration failures and even device exceptions.
Device management tasks at a glance
All device management tasks are optional. You can perform any of the tasks in any order.
· Configuring basic parameters
¡ Enabling displaying the copyright statement
· Configuring security parameters
¡ Disabling password recovery capability
· Monitoring the device
· Managing resources
¡ Configuring device poweroff alarming
¡ Verifying and diagnosing transceiver modules
· Maintaining the device
¡ Restoring the factory-default configuration
Configuring the device name
About this task
A device name (also called hostname) identifies a device in a network and is used in CLI view prompts. For example, if the device name is Sysname, the user view prompt is <Sysname>.
Procedure
1. Enter system view.
system-view
sysname sysname
By default, the device name is H3C.
Configuring the system time
About the system time
Correct system time is essential to network management and communication. Configure the system time correctly before you run the device on the network.
The device can use one of the following methods to obtain the system time:
· Uses the locally set system time, and then uses the clock signals generated by its built-in crystal oscillator to maintain the system time.
· Periodically obtains the UTC time from an NTP or PTP source and uses the UTC time, time zone, and daylight saving time to calculate the system time. For more information about NTP and PTP, see Network Management and Monitoring Configuration Guide.
The system time calculated by using the UTC time from a time source is more precise.
Restrictions and guidelines for configuring the system time
After you configure the clock protocol none command, the clock datetime command determines the system time, whether or not the time zone or daylight saving time has been configured.
If you configure or change the time zone or daylight saving time after the device obtains the system time, the device recalculates the system time. To view the system time, use the display clock command.
System time configuration tasks at a glance
To configure the system time, perform the following tasks:
1. Configuring the system time
Choose one of the following tasks:
¡ Setting the system time at the CLI
¡ Obtaining the UTC time through NTP or PTP
2. (Optional.) Setting the time zone
Make sure each network device uses the time zone of the place where the device resides.
3. (Optional.) Setting the daylight saving time
Make sure each network device uses the daylight saving time parameters of the place where the device resides.
Setting the system time at the CLI
1. Enter system view.
system-view
2. Configure the device to use the local system time.
clock protocol none
By default, the device uses NTP to obtain the UTC time.
If you execute this command multiple times, the most recent configuration takes effect.
3. Return to user view.
quit
4. Set the local system time.
clock datetime time date
By default, the system time is UTC time 09:00:00 12/07/2013.
|
CAUTION: This command changes the system time, which affects the execution of system time-related features (for example, scheduled tasks) and collaborative operations of the device with other devices (for example, log reporting and statistics collection). Before executing this command, make sure you fully understand its impact on your live network. |
Obtaining the UTC time through NTP or PTP
1. Enter system view.
system-view
2. Specify the system time source.
clock protocol { ntp | ptp } { context context-id | mdc mdc-id }
By default, the device uses NTP to obtain the UTC time.
If you execute this command multiple times, the most recent configuration takes effect.
3. Configure time protocol parameters.
For more information about NTP and PTP configuration, see Network Management and Monitoring Configuration Guide.
Setting the time zone
1. Enter system view.
system-view
2. Set the time zone.
clock timezone zone-name { add | minus } zone-offset
By default, the system uses the UTC time zone.
Setting the daylight saving time
1. Enter system view.
system-view
2. Set the daylight saving time.
clock summer-time name start-time start-date end-time end-date add-time
By default, the daylight saving time is not set.
Enabling displaying the copyright statement
About this task
This feature enables the device to display the copyright statement in the following situations:
· When a Telnet or SSH user logs in.
· When a console user quits user view. This is because the device automatically tries to restart the user session.
If you disable displaying the copyright statement, the device does not display the copyright statement in any situations.
Procedure
1. Enter system view.
system-view
2. Enable displaying the copyright statement.
copyright-info enable
By default, displaying the copyright statement is enabled.
Configuring banners
About this task
Banners are messages that the system displays when a user logs in.
The system supports the following banners:
· Legal banner—Appears after the copyright statement.
· Message of the Day (MOTD) banner—Appears after the legal banner and before the login banner.
· Login banner—Appears only when password or scheme authentication is configured.
· Shell banner.
The system displays the banners in the following order: legal banner, MOTD banner, login banner, and shell banner.
Banner input methods
You can configure a banner by using one of the following methods:
· Input the entire command line in a single line.
The banner cannot contain carriage returns. The entire command line, including the command keywords, the banner, and the delimiters, can have a maximum of 511 characters. The delimiters for the banner can be any printable character but must be the same. You cannot press Enter before you input the end delimiter.
For example, you can configure the shell banner "Have a nice day." as follows:
<Sysname> system-view
[Sysname] header shell %Have a nice day.%
· Input the command line in multiple lines.
The banner can contain carriage returns. A carriage return is counted as two characters.
To input a banner configuration command line in multiple lines, use one of the following methods:
¡ Press Enter after the final command keyword, type the banner, and end the final line with the delimiter character %. The banner plus the delimiter can have a maximum of 1999 characters.
For example, you can configure the banner "Have a nice day." as follows:
<Sysname> system-view
[Sysname] header shell
Please input banner content, and quit with the character '%'.
Have a nice day.%
¡ After you type the final command keyword, type any printable character as the start delimiter for the banner and press Enter. Then, type the banner and end the final line with the same delimiter. The banner plus the end delimiter can have a maximum of 1999 characters.
For example, you can configure the banner "Have a nice day." as follows:
<Sysname> system-view
[Sysname] header shell A
Please input banner content, and quit with the character 'A'.
Have a nice day.A
¡ After you type the final command keyword, type the start delimiter and part of the banner. Make sure the final character of the final string is different from the start delimiter. Then, press Enter, type the rest of the banner, and end the final line with the same delimiter. The banner plus the start and end delimiters can have a maximum of 2002 characters.
For example, you can configure the banner "Have a nice day." as follows:
<Sysname> system-view
[Sysname] header shell AHave a nice day.
Please input banner content, and quit with the character 'A'.
A
Procedure
1. Enter system view.
system-view
2. Configure one or more banners:
¡ Configure the legal banner.
header legal text
¡ Configure the MOTD banner.
header motd text
¡ Configure the login banner.
header login text
¡ Configure the shell banner.
header shell text
By default, no banner is configured.
Disabling password recovery capability
About this task
Password recovery capability controls console user access to the device configuration and SDRAM from BootWare menus. For more information about BootWare menus, see the release notes.
If password recovery capability is enabled, a console user can access the device configuration without authentication to configure a new password.
If password recovery capability is disabled, console users must restore the factory-default configuration before they can configure new passwords. Restoring the factory-default configuration deletes the next-startup configuration files.
To enhance system security, disable password recovery capability.
Restrictions and guidelines
To access the device configuration without authentication, you must connect to the active MPU and access the BootWare menu while the MPU is starting up.
Procedure
1. Enter system view.
system-view
2. Disable password recovery capability.
undo password-recovery enable
By default, password recovery capability is enabled.
Setting the operating mode for an interface card
About this task
This feature supports setting an operating mode for the interface card in a slot. Some interface cards can operate in multiple modes to provide different types of interfaces. Use this feature to set the operating mode for an interface card.
Restrictions and guidelines
For a new operating mode to take effect immediately, you must perform one of the following tasks to activate the new operating mode:
· Hot swap the interface card if the interface card supports hot swapping.
· Restart the device.
Only the HRIC-XP8-H interface card supports this command, and it can switch to flexible Ethernet mode only when installed in slot 4, 5, 6, or 7.
Procedure
1. Enter system view.
system-view
2. Set the operating mode for an interface card.
line-card-mode slot slot-number mode-name
By default, the HRIC-XP8-H interface card operates in Ethernet mode.
Setting the port status detection timer
About this task
If the port has been in down state before the timer expires, the device will set the port status to the port's physical status.
Procedure
1. Enter system view.
system-view
2. Set the port status detection timer.
shutdown-interval time
The default setting is 30 seconds.
Monitoring CPU usage
About this task
To monitor CPU usage, the device performs the following operations:
· Samples CPU usage at 1-minute intervals, and compares the samples with CPU usage thresholds to identify the CPU usage status and send alarms or notifications accordingly.
· Samples and saves CPU usage at a configurable interval if CPU usage tracking is enabled. You can use the display cpu-usage history command to display the historical CPU usage statistics in a coordinate system.
The device supports the following CPU usage thresholds:
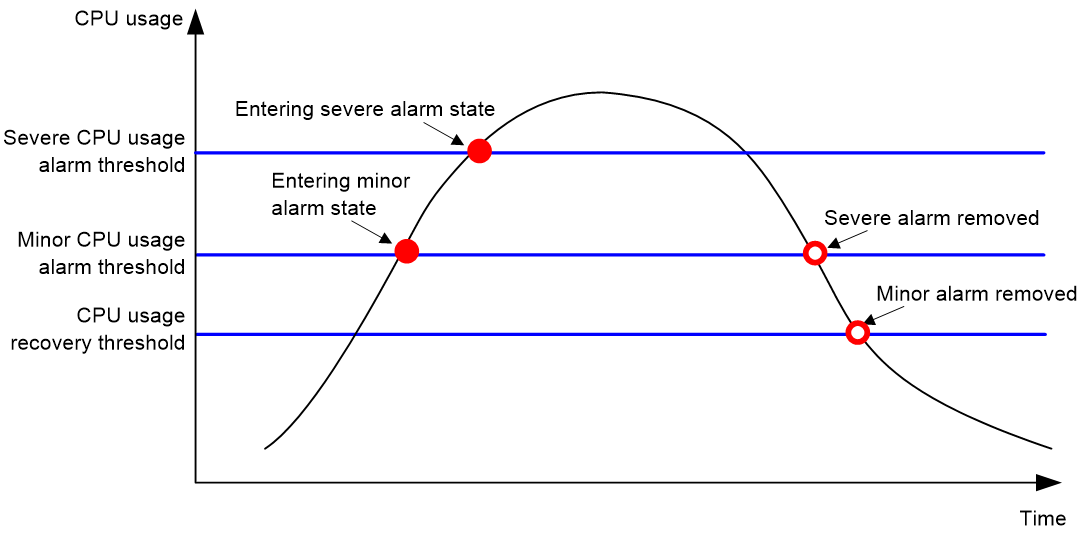
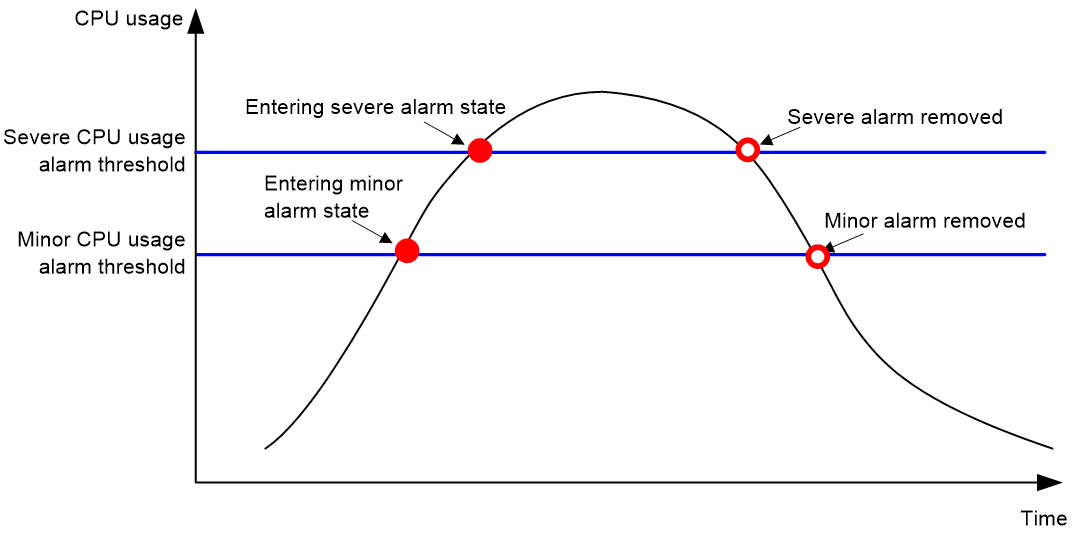
· Minor threshold—If the CPU usage increases above the minor threshold but is less than or equal to the severe threshold, the CPU usage enters minor alarm state. The device sends minor alarms periodically until the CPU usage increases above the severe threshold or the minor alarm is removed.
· Severe threshold—If the CPU usage increases above the severe threshold, the CPU usage enters severe alarm state. The device sends severe alarms periodically until the severe alarm is removed.
· Recovery threshold—If the CPU usage decreases below the recovery threshold, the CPU usage enters recovered state. The device sends a recovery notification.
CPU usage alarms and notifications are sent to NETCONF, SNMP, and the information center to be encapsulated as NETCONF events, SNMP traps and informs, and log messages. For more information, see NETCONF, SNMP, and information center in Network Management and Monitoring Configuration Guide.
Figure 1 CPU alarms and alarm-removed notifications
Figure 2 CPU alarms and alarm-removed notifications
Procedure
1. Enter system view.
system-view
2. Set the CPU usage thresholds.
monitor cpu-usage threshold cpu-threshold [ minor-threshold minor-threshold ] [ slot slot-number [ cpu cpu-number ] ]
By default, the severe CPU usage alarm threshold is 99%, and the minor CPU usage alarm threshold is 79%.
|
CAUTION: If you set the severe CPU usage threshold to a too low value, the device will reach the threshold easily. Normal service processing will be affected. |
3. Set the CPU usage alarm resending intervals.
monitor resend cpu-usage { minor-interval minor-interval | severe-interval severe-interval } * [ slot slot-number [ cpu cpu-number ] ]
By default, the minor CPU usage alarm resending interval and severe CPU usage alarm resending interval are 300 seconds and 60 seconds, respectively.
4. Set the sampling interval for CPU usage tracking.
monitor cpu-usage interval interval [ slot slot-number [ cpu cpu-number ] ]
By default, the sampling interval for CPU usage tracking is 1 minute.
5. Enable CPU usage tracking.
monitor cpu-usage enable [ slot slot-number [ cpu cpu-number ] ]
By default, CPU usage tracking is enabled.
Monitoring CPU core usage
About this task
The device samples CPU core usage at 5-second intervals and calculates the average value during each CPU core usage statistics interval. If the value during an interval is greater than a CPU core usage threshold, the device sends an alarm notification.
CPU core usage alarm notifications are sent to NETCONF, SNMP, and the information center to be encapsulated as NETCONF events, SNMP traps and informs, and log messages. For more information about NETCONF, SNMP, and information center, see Network Management and Monitoring Configuration Guide.
Restrictions and guidelines
As a best practice, set the CPU core usage statistics interval to a multiple of 5. If you do not do so, the effective statistics interval is the biggest multiple of 5 that is smaller than the setting. For example, if you set this statistics interval to 18 seconds, the effective statistics interval is 15 seconds.
Procedure
1. Enter system view.
system-view
2. Set the CPU core usage statistics interval.
monitor cpu-usage statistics-interval interval slot slot-number cpu cpu-number core core-id-list
By default, the CPU core usage statistics interval is 60 seconds.
3. Set CPU core alarm resending intervals.
monitor resend cpu-usage core-interval { minor-interval minor-interval | severe-interval severe-interval } * [ slot slot-number [ cpu cpu-number ] ]
By default, the minor CPU core usage alarm resending interval is 300 seconds and severe CPU core usage alarm resending interval is 60 seconds.
4. Set CPU core usage alarm thresholds.
monitor cpu-usage threshold severe-threshold [ minor-threshold minor-threshold recovery-threshold recovery-threshold ] slot slot-number cpu cpu-number core core-id-list
By default, the minor CPU core usage alarm threshold is 79% and severe CPU core usage alarm threshold is 99%.
Monitoring memory
Monitoring memory usage
About this task
The device samples memory usage at 1-minute intervals, and compares the sampled value with the memory usage threshold. If the sampled value exceeds the threshold, the device sends an alarm notification.
Memory usage alarm notifications are sent to NETCONF, SNMP, and the information center to be encapsulated as NETCONF events, SNMP traps and informs, and log messages. For more information about NETCONF, SNMP, and information center, see Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Set the memory usage threshold.
memory-threshold [ slot slot-number [ cpu cpu-number ] ] usage memory-threshold
By default, the memory usage threshold is 100%.
3. Set the memory usage alarm resending interval.
memory-threshold [ slot slot-number [ cpu cpu-number ] ] usage resend-interval interval-value
By default, the memory usage alarm resending interval is 300 seconds.
Monitoring free memory
About this task
The device monitors the amount of free memory space in real time. If the amount of free memory space reaches a free-memory threshold, the system generates an alarm notification and sends it to affected service modules or processes. If the amount of free memory space drops below a free-memory threshold, the system generates an alarm-removed notification and sends it to affected service modules or processes.
Free memory alarm notifications are sent to NETCONF, SNMP, and the information center to be encapsulated as NETCONF events, SNMP traps and informs, and log messages. For more information about NETCONF, SNMP, and information center, see Network Management and Monitoring Configuration Guide.
(On devices that do not support low memory.) You can use the display memory command to display memory usage information.
(On devices that support low memory.) The system monitors only the amount of free low-memory space. You can use the display memory command to display memory usage information.
(On devices with slots that support low memory.) For slots that support low memory, the system monitors only the amount of free low-memory space. You can use the display memory command to display memory usage information. If the LowMem field is displayed for a slot, the slot supports low memory.
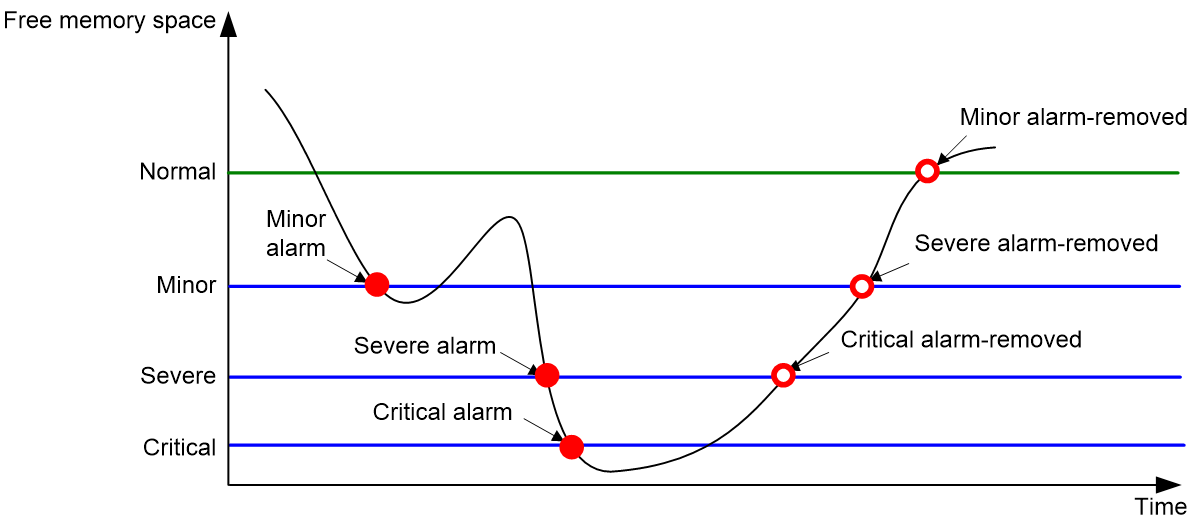
As shown in Table 1 and Figure 3, the system supports the following free-memory thresholds:
· Normal state threshold.
· Minor alarm threshold.
· Severe alarm threshold.
· Critical alarm threshold.
Table 1 Memory alarm notifications and memory alarm-removed notifications
|
Notification |
Triggering condition |
Remarks |
|
Minor alarm notification |
The amount of free memory space decreases below the minor alarm threshold. |
After generating and sending a minor alarm notification, the system does not generate and send any additional minor alarm notifications until the minor alarm is removed. |
|
Severe alarm notification |
The amount of free memory space decreases below the severe alarm threshold. |
After generating and sending a severe alarm notification, the system does not generate and send any additional severe alarm notifications until the severe alarm is removed. |
|
Critical alarm notification |
The amount of free memory space decreases below the critical alarm threshold. |
After generating and sending a critical alarm notification, the system does not generate and send any additional critical alarm notifications until the critical alarm is removed. |
|
Critical alarm-removed notification |
The amount of free memory space increases above the severe alarm threshold. |
N/A |
|
Severe alarm-removed notification |
The amount of free memory space increases above the minor alarm threshold. |
N/A |
|
Minor alarm-removed notification |
The amount of free memory space increases above the normal state threshold. |
N/A |
Figure 3 Memory alarm notifications and alarm-removed notifications
Procedure
1. Enter system view.
system-view
2. Set the free-memory thresholds.
memory-threshold [ ratio ] [ slot slot-number [ cpu cpu-number ] ] minor minor-value severe severe-value critical critical-value normal normal-value
The default settings are as follows:
¡ Minor alarm threshold—96 MB.
¡ Severe alarm threshold—64 MB.
¡ Critical alarm threshold—48 MB.
¡ Normal state threshold—128 MB.
3. Set memory depletion alarm resending intervals.
monitor resend memory-threshold { critical-interval critical-interval | minor-interval minor-interval | severe-interval severe-interval } * [ slot slot-number [ cpu cpu-number ] ]
The default settings are as follows:
¡ Early warning resending interval—1 hour.
¡ Minor alarm resending interval—12 hours.
¡ Severe alarm resending interval—3 hours.
¡ Critical alarm resending interval—1 hour.
Monitoring kernel memory fragments
About this task
A running kernel thread's process requires memory allocation from the system. The system allocates and releases this memory as a whole. If the process is still running and some memory blocks have been used but are no longer used, these memory blocks will not be released in advance. These free but currently unusable memory blocks are also referred to as memory fragments. This feature allows the device to monitor the kernel memory fragment ratio at intervals. If the kernel memory fragment ratio increases to or above the alarm threshold, the kernel memory usage is low and an alarm notification is generated. If the kernel memory fragment ratio decreases below the alarm threshold, the kernel memory usage returns to the normal state and a recovery notification is generated.
Procedure
1. Enter system view.
system-view
2. Set the kernel memory fragment ratio alarm threshold.
monitor kernel memory fragment ratio ratio-value [ slot slot-number [ cpu cpu-number ] ]
By default, the kernel memory fragment ratio alarm threshold is 20%.
3. Set the interval for collecting kernel memory fragment information.
monitor kernel memory fragment interval interval-value [ slot slot-number [ cpu cpu-number ] ]
By default, the interval is five minutes for collecting kernel memory fragment information.
Monitoring DMA memory
About this task
To ensure correct operation of services that use Direct Memory Access (DMA) memory, the system monitors the amount of free DMA memory space regularly. If the amount of free DMA memory space decreases to or below the alarm threshold, the system generates a notification that the DMA memory space is insufficient. If the amount of free DMA memory space increases above the normal state threshold, the system generates a notification that the DMA memory space is sufficient.
DMA memory alarm notifications are sent to NETCONF, SNMP, and the information center to be encapsulated as NETCONF events, SNMP traps and informs, and log messages. For more information about NETCONF, SNMP, and information center, see Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Set the DMA memory thresholds.
memory-threshold dma [ slot slot-number [ cpu cpu-number ] ] [ ratio ] critical critical-value normal normal-value
By default, the DMA memory alarm threshold is 2048 KB, and the normal state threshold is 4096 KB.
3. Set the DMA memory alarm resending interval.
monitor resend memory-threshold dma critical-interval critical-interval [ slot slot-number [ cpu cpu-number ] ]
The default settings vary by device model.
Monitoring disk usage
About this task
This feature enables the device to periodically sample the usage of a disk and compare the usage with the threshold. If the disk usage exceeds the threshold, the device sends an alarm notification.
Disk usage alarm notifications are sent to NETCONF, SNMP, and the information center to be encapsulated as NETCONF events, SNMP traps and informs, and log messages. For more information about NETCONF, SNMP, and information center, see Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Set the disk usage sampling interval.
monitor disk-usage interval interval
By default, the disk usage sampling interval is 300 seconds.
3. Set the disk usage threshold.
monitor disk-usage [ slot slot-number ] disk disk-name threshold threshold-value
By default, the disk usage threshold is 90%.
Configuring the power saving feature
About this task
When the power saving feature is enabled, the device will power down or place the inactive components into sleep mode to reduce power consumption.
Enabling the power saving feature
1. Enter system view.
system-view
2. Enable the power saving feature.
save-power enable
By default, power saving is disabled.
Support for this feature varies by device model.
Managing energy saving
About energy saving
The device supports the following energy saving features:
· Intelligent fan speed control
The device adopts intelligent fan speed control to monitor the temperature of key components. When the temperature of a key component rises, the fan speed increases. When the temperature drops, the fan speed decreases. This ultimately ensures that the device stays in a stable and energy-efficient state with reduced noise.
· Auto laser shutdown
Auto laser shutdown protects users against laser injury and saves energy. This feature determines whether the laser of a transceiver module can emit light by detecting the LOS on a fiber interface.
If auto laser shutdown is disabled when a fiber link fails, data communication is interrupted but the fiber interface of the device remains active, allowing the laser to continue emitting light. In this case, light emission during data communication interruption not only wastes energy but also poses a certain danger to eyes.
If auto laser shutdown is enabled when a fiber link fails, the system will automatically shut down the laser of the transceiver module upon detecting the LOS on the fiber interface. After the fiber link recovers, the system detects that the LOS on the fiber interface is cleared and automatically brings up the laser again.
· Energy saving modes
Table 2 shows the energy saving modes available for the device. An energy saving mode will takes effect immediately after you specify it.
|
Energy saving mode |
Description |
|
Standard |
Default energy saving mode in the factory-default configuration of the device. |
|
Basic |
Supports the following functions except for those in standard mode: · Intelligent fan speed control. · Auto transceiver module sleep. |
Configuring an energy saving mode
Restrictions and guidelines
An energy saving mode takes effect immediately after you specify it.
Procedure
1. Enter system view.
system-view
2. Specify an energy saving mode for the device.
energy-saving mode { standard | basic }
By default, the device uses the standard energy saving mode.
The following compatibility matrix shows the support of hardware platforms for this command:
|
Hardware |
MPU model |
Command compatibility |
|
RA5300, RA5300-X, RA5300-AC |
RSU-400, RSU-400S |
No |
|
RSU-400-G |
Yes |
Displaying NSR status
About this task
Nonstop routing (NSR) backs up protocol status and data from the active process to the standby process to ensure forwarding continuity. You can display NSR status information for all modules that support NSR.
Procedure
To display NSR status information for modules that support the NSR feature, execute the following command in any view:
display non-stop-routing status
Managing power supply
About power supply management
Power modules might have problems such as overload overcurrent, overvoltage, overtemperature, and short circuit. Some power modules use a hardware protection measure, for example, powering off the device, to protect the entire device from being damaged. The hardware protection measure helps protect the device but causes service outage. The power supply management feature can minimize service outage while protecting the device against overload problems.
The power supply management feature constantly monitors the available power and the system loads. If a potential power supply overload problem is found, this feature takes protective measures immediately to remove requirements for power supply hardware protection. Examples of protective measures include sending a notification, starting redundant power modules, and powering off certain interface cards.
Powering on or off a card
About this task
You can manually power on or off cards. To view the power module status, use the display power-supply command.
Powering on a card
To power on a card, execute the following command in user view:
power-supply on slot slot-number
Powering off a card
To power off a card, execute the following command in user view:
power-supply off slot slot-number
|
CAUTION: A card will not send or receive packets after you power off it. Execute this command with caution. |
Configuring device poweroff alarming
About this task
This feature enables the device to detect a device poweroff event and send an alarm notification on the poweroff event.
Poweroff alarm notifications are sent to SNMP and the information center to be encapsulated as SNMP traps and log messages. For more information, see SNMP and information center in Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Specify the source interface for sending the poweroff alarm.
dying-gasp source interface-type { interface-number | interface-number.subnumber }
By default, no source interface is specified. On an IPv4 network, the device uses the primary IPv4 address of the output interface for the route to the destination host as the source address. On an IPv6 network, the device selects a source IPv6 address as defined in RFC 3484.
3. Configure SNMP notification destination host settings.
dying-gasp host { ip-address | ipv6 ipv6-address } [ vpn-instance vpn-instance-name ] snmp-trap version { v1 | v2c } securityname security-string
By default, no SNMP notification destination host settings are configured.
You can configure the device to send poweroff alarm SNMP notifications to multiple destination hosts.
4. Configure log message destination host settings.
dying-gasp host { ip-address | ipv6 ipv6-address } [ vpn-instance vpn-instance-name ] syslog
By default, no log message destination host settings are configured.
You can configure the device to send the poweroff alarm log messages to multiple destination hosts.
Verifying and diagnosing transceiver modules
Verifying transceiver modules
About this task
You can use one of the following methods to verify the genuineness of a transceiver module:
· Display the key parameters of a transceiver module, including its transceiver type, connector type, central wavelength of the transmit laser, transfer distance, and vendor name.
· Display its electronic label. The electronic label is a profile of the transceiver module and contains the permanent configuration, including the serial number, manufacturing date, and vendor name. The data was written to the transceiver module or the device's storage component during debugging or testing of the transceiver module or device.
The device regularly checks transceiver modules for their vendor names. If a transceiver module does not have a vendor name or the vendor name is not H3C, the device repeatedly outputs traps and log messages. For information about logging rules, see Network Management and Monitoring Configuration Guide.
Procedure
To verify transceiver modules, execute the following commands in any view:
· Display the key parameters of transceiver modules.
display transceiver interface [ interface-type interface-number ]
· Display the electrical label information of transceiver modules.
display transceiver manuinfo interface [ interface-type interface-number ]
Diagnosing transceiver modules
About this task
The device provides the alarm and digital diagnosis functions for transceiver modules. When a transceiver module fails or is not operating correctly, you can perform the following tasks:
· Check the alarms that exist on the transceiver module to identify the fault source.
· Examine the key parameters monitored by the digital diagnosis function, including the temperature, voltage, laser bias current, TX power, and RX power.
Poweroff alarm notifications are sent to SNMP and the information center to be encapsulated as SNMP traps or informs and log messages. For more information, see SNMP and information center in Network Management and Monitoring Configuration Guide.
Procedure
To diagnose transceiver modules, execute the following commands in any view:
· Display transceiver alarms.
display transceiver alarm interface [ interface-type interface-number ]
· Display the current values of the digital diagnosis parameters on transceiver modules.
display transceiver diagnosis interface [ interface-type interface-number ]
Scheduling a task
About task scheduling
You can schedule the device to automatically execute a command or a set of commands without administrative interference.
You can configure a periodic schedule or a non-periodic schedule. A non-periodic schedule is not saved to the configuration file and is lost when the device reboots. A periodic schedule is saved to the startup configuration file and is automatically executed periodically.
Restrictions and guidelines for task scheduling
· The default system time is always restored at reboot. To make sure a task schedule can be executed as expected, reconfigure the system time or configure NTP after you reboot the device. For more information about NTP, see Network Management and Monitoring Configuration Guide.
· To assign a command (command A) to a job, you must first assign the job the command or commands for entering the view of command A.
· Make sure all commands in a schedule are compliant to the command syntax. The system does not check the syntax when you assign a command to a job.
· A schedule cannot contain any one of these commands: telnet, ftp, ssh2, and monitor process.
· A schedule does not support user interaction. If a command requires a yes or no answer, the system always assumes that a Y or Yes is entered. If a command requires a character string input, the system assumes that either the default character string (if any) or a null string is entered.
· A schedule is executed in the background, and no output (except for logs, traps, and debug information) is displayed for the schedule.
· You can assign multiple user roles to a schedule. A command in a schedule can be executed if it is permitted by one or more user roles of the schedule.
The security log manager user role is mutually exclusive with other user roles. That is, if the security log manager user role has been assigned, the system will automatically remove the existing other user roles. If the other user roles have been assigned, the system will automatically remove the existing security log manager user role.
Procedure
1. Enter system view.
system-view
2. Create a job.
scheduler job job-name
3. Assign a command to the job.
command id command
By default, no command is assigned to a job.
You can assign multiple commands to a job. A command with a smaller ID is executed first.
4. Exit to system view.
quit
5. Create a schedule.
scheduler schedule schedule-name
6. Assign a job to the schedule.
job job-name
By default, no job is assigned to a schedule.
You can assign multiple jobs to a schedule. The jobs will be executed concurrently.
7. Assign user roles to the schedule.
user-role role-name
By default, a schedule has the user role of the schedule creator.
8. Specify the execution time for the schedule.
Choose one option as needed:
¡ Execute the schedule at specific points of time.
time at time date
time once at time [ month-date month-day | week-day week-day&<1-7> ]
¡ Execute the schedule after a period of time.
time once delay time
¡ Execute the schedule at the specified time on every specified day in a month or week.
time repeating at time [ month-date [ month-day | last ] | week-day week-day&<1-7> ]
¡ Execute the schedule at intervals from the specified time on.
time repeating [ at time [date ] ] interval interval
By default, no execution time is specified for a schedule.
The time commands overwrite each other. The most recently configured command takes effect.
9. (Optional.) Set the schedule log file size limit.
scheduler logfile size value
By default, the schedule log file size limit is 16 KB.
The schedule log file stores log messages for execution results of commands in jobs. After the limit is reached, the system deletes the oldest log messages to store the new log messages. If the remaining space of the log file is not enough for a single log message, the system truncates the message and does not store the extra part.
Example: Scheduling a task
Network configuration
As shown in Figure 4, two interfaces of the device are connected to users.
To save energy, configure the device to perform the following operations:
· Enable the interfaces at 8:00 a.m. every Monday through Friday.
· Disable the interfaces at 18:00 every Monday through Friday.
Procedure
# Enter system view.
<Sysname> system-view
# Configure a job for disabling interface Ten-GigabitEthernet 2/0/0.
[Sysname] scheduler job shutdown-Ten-GigabitEthernet2/0/0
[Sysname-job-shutdown-Ten-GigabitEthernet2/0/0] command 1 system-view
[Sysname-job-shutdown-Ten-GigabitEthernet2/0/0] command 2 interface ten-gigabitethernet 2/0/0
[Sysname-job-shutdown-Ten-GigabitEthernet2/0/0] command 3 shutdown
[Sysname-job-shutdown-Ten-GigabitEthernet2/0/0] quit
# Configure a job for enabling interface Ten-GigabitEthernet 2/0/0.
[Sysname] scheduler job start-Ten-GigabitEthernet2/0/0
[Sysname-job-start-Ten-GigabitEthernet2/0/0] command 1 system-view
[Sysname-job-start-Ten-GigabitEthernet2/0/0] command 2 interface ten-gigabitethernet 2/0/0
[Sysname-job-start-Ten-GigabitEthernet2/0/0] command 3 undo shutdown
[Sysname-job-start-Ten-GigabitEthernet2/0/0] quit
# Configure a job for disabling interface Ten-GigabitEthernet 2/0/1.
[Sysname] scheduler job shutdown-Ten-GigabitEthernet2/0/1
[Sysname-job-shutdown-Ten-GigabitEthernet2/0/1] command 1 system-view
[Sysname-job-shutdown-Ten-GigabitEthernet2/0/1] command 2 interface ten-gigabitethernet 2/0/1
[Sysname-job-shutdown-Ten-GigabitEthernet2/0/1] command 3 shutdown
[Sysname-job-shutdown-Ten-GigabitEthernet2/0/1] quit
# Configure a job for enabling interface Ten-GigabitEthernet 2/0/1.
[Sysname] scheduler job start-Ten-GigabitEthernet2/0/1
[Sysname-job-start-Ten-GigabitEthernet2/0/1] command 1 system-view
[Sysname-job-start-Ten-GigabitEthernet2/0/1] command 2 interface ten-gigabitethernet 2/0/1
[Sysname-job-start-Ten-GigabitEthernet2/0/1] command 3 undo shutdown
[Sysname-job-start-Ten-GigabitEthernet2/0/1] quit
# Configure a periodic schedule for enabling the interfaces at 8:00 a.m. every Monday through Friday.
[Sysname] scheduler schedule START-pc1/pc2
[Sysname-schedule-START-pc1/pc2] job start-Ten-GigabitEthernet2/0/0
[Sysname-schedule-START-pc1/pc2] job start-Ten-GigabitEthernet2/0/1
[Sysname-schedule-START-pc1/pc2] time repeating at 8:00 week-day mon tue wed thu fri
[Sysname-schedule-START-pc1/pc2] quit
# Configure a periodic schedule for disabling the interfaces at 18:00 every Monday through Friday.
[Sysname] scheduler schedule STOP-pc1/pc2
[Sysname-schedule-STOP-pc1/pc2] job shutdown-Ten-GigabitEthernet2/0/0
[Sysname-schedule-STOP-pc1/pc2] job shutdown-Ten-GigabitEthernet2/0/1
[Sysname-schedule-STOP-pc1/pc2] time repeating at 18:00 week-day mon tue wed thu fri
[Sysname-schedule-STOP-pc1/pc2] quit
Verifying the configuration
# Display the configuration information of all jobs.
[Sysname] display scheduler job
Job name: shutdown-Ten-GigabitEthernet2/0/0
system-view
interface ten-gigabitethernet 2/0/0
shutdown
Job name: shutdown-Ten-GigabitEthernet2/0/1
system-view
interface ten-gigabitethernet 2/0/1
shutdown
Job name: start-Ten-GigabitEthernet2/0/0
system-view
interface ten-gigabitethernet 2/0/0
undo shutdown
Job name: start-Ten-GigabitEthernet2/0/1
system-view
interface ten-gigabitethernet 2/0/1
undo shutdown
# Display the schedule information.
[Sysname] display scheduler schedule
Schedule name : START-pc1/pc2
Schedule type : Run on every Mon Tue Wed Thu Fri at 08:00:00
Start time : Wed Sep 28 08:00:00 2011
Last execution time : Wed Sep 28 08:00:00 2011
Last completion time : Wed Sep 28 08:00:03 2011
Execution counts : 1
-----------------------------------------------------------------------
Job name Last execution status
start-Ten-GigabitEthernet2/0/0 Successful
start-Ten-GigabitEthernet2/0/1 Successful
Schedule name : STOP-pc1/pc2
Schedule type : Run on every Mon Tue Wed Thu Fri at 18:00:00
Start time : Wed Sep 28 18:00:00 2011
Last execution time : Wed Sep 28 18:00:00 2011
Last completion time : Wed Sep 28 18:00:01 2011
Execution counts : 1
-----------------------------------------------------------------------
Job name Last execution status
shutdown-Ten-GigabitEthernet2/0/0 Successful
shutdown-Ten-GigabitEthernet2/0/1 Successful
# Display schedule log information.
[Sysname] display scheduler logfile
Job name : start-Ten-GigabitEthernet2/0/0
Schedule name : START-pc1/pc2
Execution time : Wed Sep 28 08:00:00 2011
Completion time : Wed Sep 28 08:00:02 2011
--------------------------------- Job output -----------------------------------
<Sysname>system-view
System View: return to User View with Ctrl+Z.
[Sysname]interface ten-gigabitethernet 2/0/0
[Sysname-Ten-GigabitEthernet2/0/0]undo shutdown
Job name : start-Ten-GigabitEthernet2/0/1
Schedule name : START-pc1/pc2
Execution time : Wed Sep 28 08:00:00 2011
Completion time : Wed Sep 28 08:00:02 2011
--------------------------------- Job output -----------------------------------
<Sysname>system-view
System View: return to User View with Ctrl+Z.
[Sysname]interface ten-gigabitethernet 2/0/1
[Sysname-Ten-GigabitEthernet2/0/1]undo shutdown
Job name : shutdown-Ten-GigabitEthernet2/0/0
Schedule name : STOP-pc1/pc2
Execution time : Wed Sep 28 18:00:00 2011
Completion time : Wed Sep 28 18:00:01 2011
--------------------------------- Job output -----------------------------------
<Sysname>system-view
System View: return to User View with Ctrl+Z.
[Sysname]interface ten-gigabitethernet 2/0/0
[Sysname-Ten-GigabitEthernet2/0/0]shutdown
Job name : shutdown-Ten-GigabitEthernet2/0/1
Schedule name : STOP-pc1/pc2
Execution time : Wed Sep 28 18:00:00 2011
Completion time : Wed Sep 28 18:00:01 2011
--------------------------------- Job output -----------------------------------
<Sysname>system-view
System View: return to User View with Ctrl+Z.
[Sysname]interface ten-gigabitethernet 2/0/1
[Sysname-Ten-GigabitEthernet2/0/1]shutdown
Rebooting the device
About device reboot
The following device reboot methods are available:
· Schedule a reboot at the CLI, so the device automatically reboots at the specified time or after the specified period of time.
· Immediately reboot the device at the CLI.
During the reboot process, the device performs the following operations:
a. Resets all of its chips.
b. Uses the BootWare to verify the startup software package, decompress the package, and load the images.
c. Initializes the system.
· Power off and then power on the device. This method might cause data loss, and is the least-preferred method.
Using the CLI, you can reboot the device from a remote host.
Restrictions and guidelines for device reboot
For data security, the device does not reboot while it is performing file operations.
Rebooting devices immediately at the CLI
Prerequisites
Perform the following steps in any view:
1. Verify that the next-startup configuration file is correctly specified.
display startup
For more information about the display startup command, see Fundamentals Command Reference.
2. Verify that the startup image files are correctly specified.
display boot-loader
If one main startup image file is damaged or does not exist, you must specify another main startup image file before rebooting the device.
For more information about the display boot-loader command, see Fundamentals Command Reference.
3. Save the running configuration to the next-startup configuration file.
save
To avoid configuration loss, save the running configuration before a reboot.
For more information about the save command, see Fundamentals Command Reference.
Restrictions and guidelines
You cannot use the reboot command to reboot a card that is powered off by the power-supply off command. You can reboot the card only after the card is powered on.
Procedure
To reboot the device immediately at the CLI, execute one of the following commands in user view:
reboot [ slot slot-number ] [ force ]
Scheduling a device reboot
Restrictions and guidelines
The automatic reboot configuration is canceled if an active/standby switchover occurs.
The device supports only one device reboot schedule. If you execute the scheduler reboot command multiple times, the most recent configuration takes effect.
Procedure
To schedule a reboot, execute one of the following commands in user view:
· scheduler reboot at time [ date ]
· scheduler reboot delay time
By default, no device reboot time is specified.
|
CAUTION: This task enables the device to reboot at a scheduled time, which causes service interruption. Before configuring this task, make sure you fully understand its impact on your live network. |
Restoring the factory-default configuration
About this task
If you want to use the device in a different scenario or you cannot troubleshoot the device by using other methods, use this task to restore the factory-default configuration.
This task does not delete .bin files and license files.
Restrictions and guidelines
Procedure
1. Execute the following command in user view to restore the factory-default configuration for the device:
restore factory-default
2. Reboot the device.
reboot
|
CAUTION: This command restores the device to the factory default settings. Before executing this command, make sure you fully understand its impact on your live network. |
When the command prompts you to choose whether to save the running configuration, enter N. If you choose to save the running configuration, the device loads the saved configuration at startup.
Display and maintenance commands for device management configuration
Execute display commands in any view. Execute the reset scheduler logfile and reset transceiver interface commands in user view. Execute the reset alarm active and reset version-update-record commands in system view.
|
Task |
Command |
|
Display device alarm information. |
display alarm [ slot slot-number ] |
|
Display information about active alarms. |
display alarm active [ module module-name ] [ verbose ] |
|
Display information about historical alarms. |
display alarm history [ module module-name ] [ verbose ] |
|
Display the system time, date, time zone, and daylight saving time. |
display clock |
|
Display the copyright statement. |
display copyright |
|
Display CPU usage statistics. |
display cpu-usage [ summary ] [ slot slot-number [ cpu cpu-number [ core { core-number| all } ] ] ] display cpu-usage [ control-plane | data-plane ] [ summary ] [ slot slot-number [ cpu cpu-number ] |
|
Display CPU usage monitoring settings. |
display cpu-usage configuration [ slot slot-number [ cpu cpu-number ] ] |
|
Display the historical CPU usage statistics in a coordinate system. |
display cpu-usage history [ job job-id ] [ slot slot-number [ cpu cpu-number ] ] |
|
Display information about the energy saving mode and energy saving policies on the device. |
display current energy-saving |
|
Display device information. |
display device [ cf-card ] [ slot slot-number [ subslot subslot-number ] | verbose ] |
|
Display electronic label information for the device. |
display device manuinfo [ slot slot-number [ subslot subslot-number ] ] |
|
Display electronic label information for a fan tray. |
display device manuinfo fan fan-id |
|
Display electronic label information for a power module. |
display device manuinfo power power-id |
|
Display or save diagnostic information for features and hardware modules. |
display diagnostic-information [ hardware | infrastructure | l2 | l3 | service ] [ key-info | verbose ] [ filename ] [ background ] |
|
Display poweroff alarm destination host settings. |
display dying-gasp host |
|
Display detailed information about the energy saving modes of the device. |
display energy-saving mode |
|
Display device temperature information. |
display environment [ slot slot-number ] |
|
Display fan tray operating status information. |
display fan [ fan-id ] |
|
Display hardware failure detection and fix information. |
display hardware-failure-detection |
|
Display CPU and memory usage. |
display health [ slot slot-number [ cpu cpu-number ] ] |
|
Display kernel memory allocation failure information. |
display kernel memory alloc-failure [ slot slot-number [ cpu cpu-number ] ] |
|
Display kernel memory fragment statistics. |
display kernel memory fragment free [ slot slot-number [ cpu cpu-number ] ] |
|
Display memory usage statistics. |
display memory [ summary ] [ slot slot-number [ cpu cpu-number ] ] |
|
Display DMA memory usage statistics. |
display memory dma [ slot slot-number [ cpu cpu-number ] ] |
|
Display memory alarm thresholds and statistics. |
display memory-threshold [ slot slot-number [ cpu cpu-number ] ] |
|
Display DMA memory alarm information. |
display memory-threshold dma [ slot slot-number [ cpu cpu-number ] ] |
|
Display NSR status information for modules that support the NSR feature. |
display non-stop-routing status |
|
Display power module information. |
display power [ power-id | verbose ] |
|
Display power saving information. |
display save-power |
|
Display job configuration information. |
display scheduler job [ job-name ] |
|
Display job execution log information. |
display scheduler logfile |
|
Display the automatic reboot schedule. |
display scheduler reboot |
|
Display schedule information. |
display scheduler schedule [ schedule-name ] |
|
Display system stability and status information. |
display system stable state[ summary ] |
|
Display transceiver alarms. |
display transceiver alarm interface [ interface-type interface-number ] |
|
Display transceiver types, receive power, and transmit power of all transceiver modules on the device. |
display transceiver brief |
|
Display the current values of the digital diagnosis parameters on transceiver modules. |
display transceiver diagnosis interface [ interface-type interface-number ] |
|
Display the key parameters of transceiver modules. |
display transceiver interface [ interface-type interface-number ] |
|
Display electronic label information for transceiver modules. |
display transceiver manuinfo interface [ interface-type interface-number ] |
|
Display system version information. |
display version |
|
Display startup software image upgrade records. |
display version-update-record |
|
Display voltage information. |
display voltage [ slot slot-number ] |
|
Clear job execution log information. |
reset scheduler logfile |
|
Clear startup software image upgrade records. |
reset version-update-record |