- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-SDP zero trust configuration | 191.93 KB |
SDP zero trust network diagram
Restrictions and guidelines: SDP configuration
SDP zero trust configuration tasks at a glance
Prerequisites for SDP zero trust
Display and maintenance commands for SDP zero trust
SDP zero trust configuration examples
Configuring SDP zero trust
About SDP zero trust
With the rise of Internet technologies such as cloud computing, Internet of things, and mobile office, the enterprise resources are no longer limited to inside an enterprise. The demand is growing for employees to access the enterprise intranet anytime and anywhere. It is increasingly difficult for the traditional network security protection based on network boundaries to meet the demand. To resolve the issue, you can use the Software Defined Perimeter (SDP) zero trust. The core idea of SDP zero trust is to not trust any person, device, or system, and to perform continuous dynamic authentication and authorize the minimum permissions for all users accessing restricted resources.
SDP zero trust allows the device to act as an SDP gateway to cooperate with an SDP controller to authenticate and authorize users that access a specific application or API. This can centrally control user identities and access permissions to avoid illegal user access.
In a zero trust scenario, the SDP gateway acts as an enterprise edge device to connect remote users to the enterprise internal network.
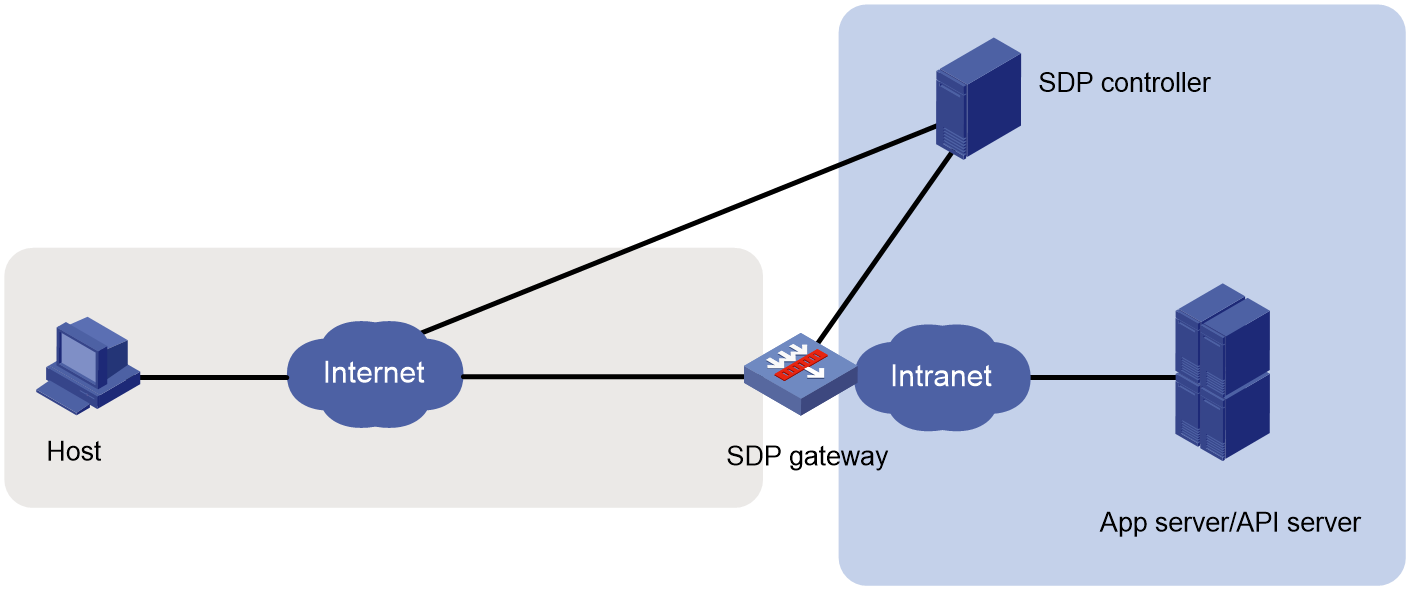
SDP zero trust network diagram
As shown in Figure 1, the following are the primary components of the SDP zero trust feature to provide the external services:
· SDP gateway—Does not authenticate users and only provides resource access services for users authorized by the SDP controller.
· SDP controller—Authenticates and authorizes users for resource access. The SDP controller has its own system for identity and permission management. You can configure users' identity information and access permissions to resources on the SDP controller.
Figure 2 SDP zero trust network diagram
SDP zero trust access modes
Web access mode
In Web access mode, remote users can log in to the SDP controller only through browsers for authentication. After authentication, a user can access internal resources only through a browser.
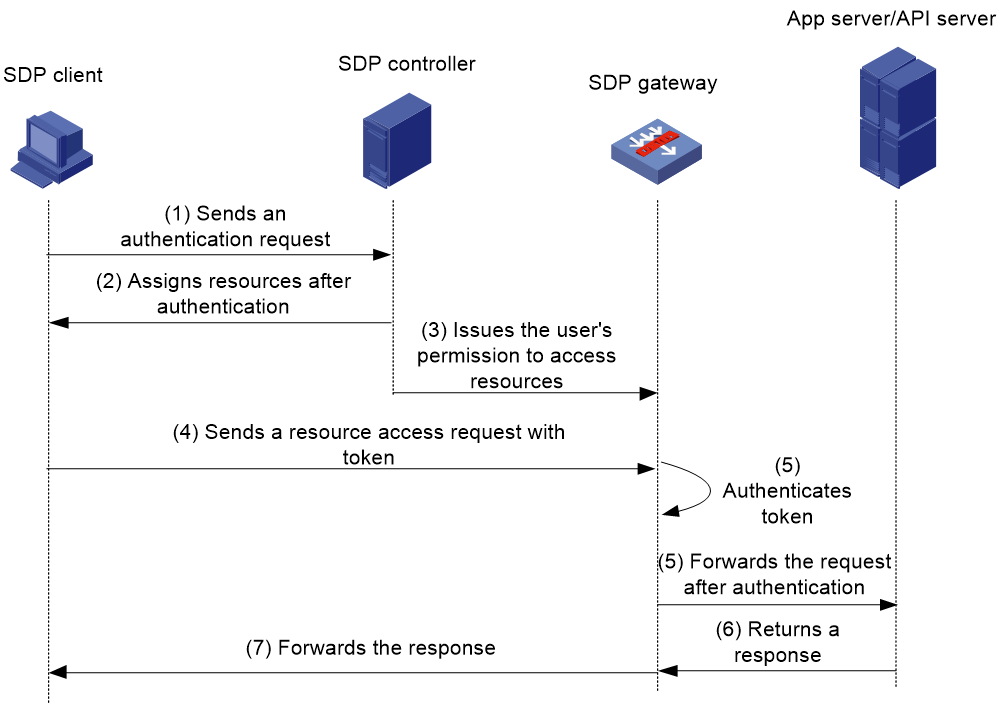
As shown in Figure 2, the Web access procedure is as follows:
1. A user accesses the SDP controller through a browser over HTTPS and enters the username and password on the authentication page.
2. After authentication, the SDP controller issues the SDP gateway address and applications/APIs that the user can access to the browser client.
3. The SDP controller issues the user's permission to access the applications/APIs to the SDP gateway. The permission is dynamically updated.
4. The user sends an access request with token through the browser for internal resources.
5. The SDP gateway authenticates the user token to identify whether the user is online.
¡ If the user is offline, the request will be rejected.
¡ If the user is online, the gateway compares the applications/APIs in the request with those that the user can access to determine whether the user has the access permission.
- If the user has the access permission, the gateway forwards the request.
- If not, the gateway rejects the request.
6. The internal app server or API server returns a response to the SDP gateway.
7. The SDP gateway forwards the response to the SDP client.
Figure 3 Network diagram for Web access
IP access mode
In IP access mode, a user can use only the iNode client to log in to the SDP controller for authentication. After authentication, the user can access internal resources only through the iNode client.
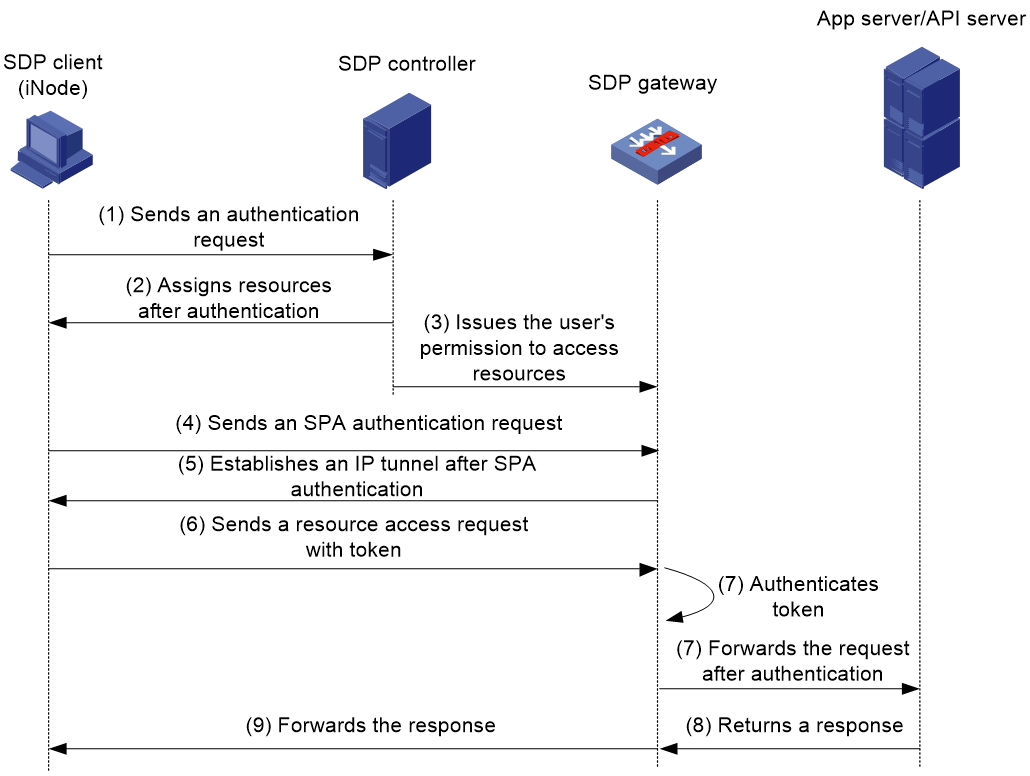
As shown in Figure 3, the IP access procedure is as follows:
1. A user uses the iNode client to send an authentication request to the SDP controller.
2. After authentication, the SDP controller issues the SDP gateway address and applications/APIs that the user can access to the iNode client.
3. The SDP controller issues the user's permission to access the applications/APIs to the SDP gateway. The permission is dynamically updated.
4. The iNode client sends a Single Packet Authorization (SPA) authentication request to the SDP gateway.
5. After SPA authentication, the iNode client establishes an IP tunnel with the SDP gateway.
6. The user uses the iNode client to send an access request with token for internal resources.
7. The SDP gateway authenticates the user token to identify whether the user is online.
¡ If the user is offline, the request will be rejected.
¡ If the user is online, the gateway compares the applications/APIs in the request with those that the user can access to determine whether the user has the access permission.
- If the user has the access permission, the gateway forwards the request.
- If not, the gateway rejects the request.
8. The internal app server or API server returns a response to the SDP gateway.
9. The SDP gateway forwards the response to the iNode client.
Figure 4 Network diagram for IP access
Mix access mode
In mix access mode, SDP zero trust operates as follows:
1. A user uses the iNode client to log in to the SDP controller for authentication.
2. After authentication, the user can access the internal resources through a browser or the iNode client. For more information, see "Web access" and "IP access."
vSystem support for features
vSystem supports all SDP zero trust features. For more information about vSystem, see Virtual Technologies Configuration Guide.
Restrictions and guidelines: SDP configuration
The SDP gateway uses the cloud connection feature to notify the SDP controller of the keepalive status. The keepalive interval set on the SDP controller is 30 seconds. To implement SDP trusted access control, use cloud-management keepalive to set the keepalive interval to 10 to 29 seconds for the device to send keepalive packets to the cloud server. For more information about cloud connections, see Fundamentals Configuration Guide.
SDP zero trust configuration tasks at a glance
To configure SDP zero trust, perform the following tasks on the SDP gateway:
4. Configuring the SDP access service by performing at least one of the following tasks:
Prerequisites for SDP zero trust
Before you configure the SDP gateway, make sure the SDP controller has been deployed for authenticating users and authorizing users to access resources. The SDP controller configuration includes IP address of the SDP gateway and the information protected by the SDP gateway such as applications/APIs and SDP users.
Configuring an SDP gateway
1. Enter system view.
system-view
2. Create an SDP gateway and enter its view.
sslvpn gateway gateway-name
3. Configure an IPv4 address and a port number for the SDP gateway.
ip address ip-address [ port port-number ]
By default, the SDP gateway uses IPv4 address 0.0.0.0 and port number 443.
If you execute the ip address command without specifying a port number, the default port number (443) is used.
4. Configure an IPv6 address and a port number for the SDP gateway.
ipv6 address ipv6-address [ port port-number ]
By default, no IPv6 address or port number is configured for the SDP gateway.
If you execute the ipv6 address command without specifying a port number, the default port number (443) is used.
5. Enable the SD gateway.
service enable
By default, the SDP gateway is disabled.
Configuring SDP
1. Enter system view.
system-view
2. Create an SDP controller, and enter its view.
trusted-access controller sdp
3. Enable SDP for trusted access control.
sdp enable
By default, SDP is disabled for trusted access control.
4. Specify the access mode for resource access through the SDP gateway.
sdp access-method { ip-tunnel | mix | web-access }
By default, the mix access mode is used for resource access through the SDP gateway.
5. Configure the default API access control rule.
sdp api-access default { deny | permit }
By default, users are permitted to access internal APIs through the SDP gateway.
6. Enable SPA authentication.
spa enable
By default, SPA authentication is disabled.
This feature is supported only in IP access mode and mix access mode.
Configuring an SDP context
1. Enter system view.
system-view
2. Create an SDP context and enter its view.
sslvpn context context-name
The name of the SDP context must be default.
3. Associate the context with an SDP gateway.
gateway gateway-name [ domain domain-name | virtual-host virtual-host-name ]
By default, the context is not associated with an SDP gateway.
4. Enable the context.
service enable
By default, the context is disabled.
Configuring Web access
1. Enter system view.
system-view
2. Enter SSL VPN context view.
sslvpn context context-name
3. Create a URL item and enter its view.
url-item name
4. Specify the resource URL in the URL item.
url url
By default, no resource URL is specified in a URL item.
If you do not specify a protocol type in the resource URL, the default protocol (HTTP) is used.
5. (Optional.) Configure the URL mapping method.
url-mapping { domain-mapping domain-name | port-mapping gateway gateway-name [ virtual-host virtual-host-name ] } [ rewrite-enable ]
By default, the normal rewriting method is used.
Configuring IP access
1. Enter system view.
system-view
2. Create an SSL VPN AC interface and enter its view.
interface sslvpn-ac interface-number
3. Configure an IPv4 address for the interface.
ip address ip-address { mask | mask-length }
By default, no IPv4 address is configured for an AC interface.
4. Configure an IPv6 address for the interface.
ipv6 address { ipv6-address prefix-length | ipv6-address/ prefix-length }
By default, no IPv6 address is configured for an AC interface.
5. Bring up the interface.
undo shutdown
By default, an SSL VPN AC interface is up.
6. Return to system view.
quit
7. Enter SSL VPN context view.
sslvpn context context-name
8. Specify the SSL VPN AC interface for IP access.
ip-tunnel interface sslvpn-ac interface-number
By default, no SSL VPN AC interface is specified for IP access in the SSL VPN context.
Display and maintenance commands for SDP zero trust
Execute display commands in any view.
|
Task |
Command |
|
Display internal resources assigned to users by the SDP controller. |
display trusted-access controller sdp assigned-resource { api | app } [ context context-name ] |
|
Display SDP session information. |
display trusted-access controller sdp session [ context context-name ] [ user user-name ] |
|
Display TCP proxy application connection information. |
In standalone mode: display trusted-access controller sdp tcp-proxy-connection [ context context-name ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display trusted-access controller sdp tcp-proxy-connection [ context context-name ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
SDP zero trust configuration examples
Example: Configuring Web access
Network configuration
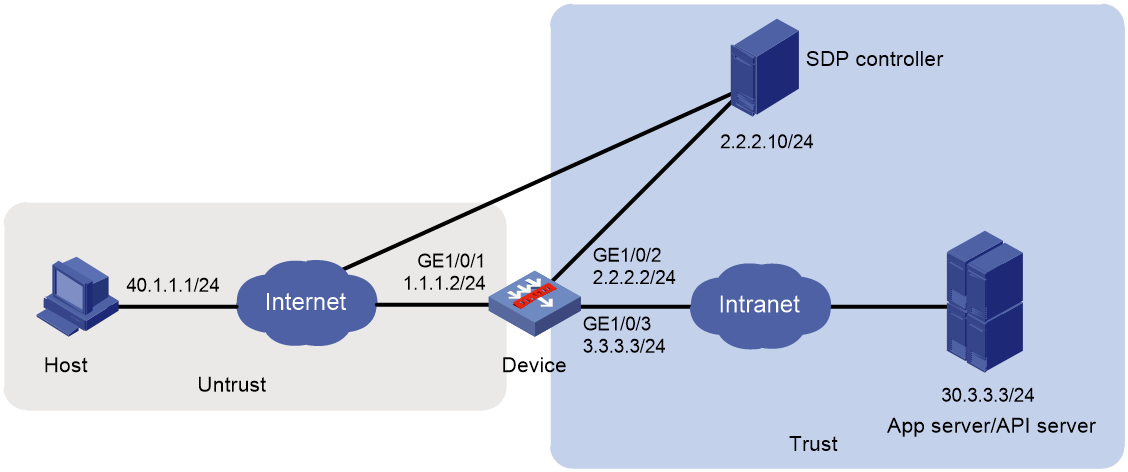
As shown in Figure 5, the device acts as the SDP gateway that connects the public network and private network. To access the internal resources, follow these steps:
1. A user sends an authentication request to the SDP controller.
2. After authentication is passed, the SDP controller assigns the resources that the user can access.
3. The user accesses the assigned resources through the SDP gateway.
Network diagram
Prerequisites
Before configuring Web access, make sure the SDP controller has been deployed for authenticating users and authorizing users to access resources.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 1.1.1.2 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures static routes, and the next hop in the routes is 3.3.3.4 to the app server or API server, and 1.1.1.3 to the host.
[Device] ip route-static 30.3.3.3 24 3.3.3.4
[Device] ip route-static 40.1.1.1 24 1.1.1.3
3. Add interfaces to security zones.
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/1
[Device-security-zone-Untrust] quit
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/2
[Device-security-zone-Trust] import interface gigabitethernet 1/0/3
[Device-security-zone-Trust] quit
4. Configure rules in a security policy to permit the traffic between the specified security zones for the user to access the SDP gateway:
# Configure a rule named sdplocalout1 to permit the packets from the device to the user.
[Device] security-policy ip
[Device-security-policy-ip] rule name sdplocalout1
[Device-security-policy-ip-1-sdplocalout1] source-zone local
[Device-security-policy-ip-1-sdplocalout1] destination-zone untrust
[Device-security-policy-ip-1-sdplocalout1] source-ip-host 1.1.1.2
[Device-security-policy-ip-1-sdplocalout1] destination-ip-host 40.1.1.1
[Device-security-policy-ip-1-sdplocalout1] action pass
[Device-security-policy-ip-1-sdplocalout1] quit
# Configure a rule named sdplocalin1 to permit the packets from the user to the device.
[Device-security-policy-ip] rule name sdplocalin1
[Device-security-policy-ip-2-sdplocalin1] source-zone untrust
[Device-security-policy-ip-2-sdplocalin1] destination-zone local
[Device-security-policy-ip-2-sdplocalin1] source-ip-host 40.1.1.1
[Device-security-policy-ip-2-sdplocalin1] destination-ip-host 1.1.1.2
[Device-security-policy-ip-2-sdplocalin1] action pass
[Device-security-policy-ip-2-sdplocalin1] quit
# Configure a rule named sdplocalout2 to permit the packets from the device to the app server, API server, and SDP controller.
[Device-security-policy-ip] rule name sdplocalout2
[Device-security-policy-ip-3-sdplocalout2] source-zone local
[Device-security-policy-ip-3-sdplocalout2] destination-zone trust
[Device-security-policy-ip-3-sdplocalout2] source-ip-host 2.2.2.2
[Device-security-policy-ip-3-sdplocalout2] source-ip-host 3.3.3.3
[Device-security-policy-ip-3-sdplocalout2] destination-ip-host 2.2.2.10
[Device-security-policy-ip-3-sdplocalout2] destination-ip-host 30.3.3.3
[Device-security-policy-ip-3-sdplocalout2] action pass
[Device-security-policy-ip-3-sdplocalout2] quit
# Configure a rule named sdplocalin2 to permit the packets from the app server, API server, and the SDP controller to the device.
[Device-security-policy-ip] rule name sdplocalin2
[Device-security-policy-ip-4-sdplocalin2] source-zone trust
[Device-security-policy-ip-4-sdplocalin2] destination-zone local
[Device-security-policy-ip-4-sdplocalin2] source-ip-host 2.2.2.10
[Device-security-policy-ip-4-sdplocalin2] source-ip-host 30.3.3.3
[Device-security-policy-ip-4-sdplocalin2] destination-ip-host 2.2.2.2
[Device-security-policy-ip-4-sdplocalin2] destination-ip-host 3.3.3.3
[Device-security-policy-ip-4-sdplocalin2] action pass
[Device-security-policy-ip-4-sdplocalin2] quit
[Device-security-policy-ip] quit
5. Configure the SDP gateway for user access to internal resources:
# Configure the IP address for SDP gateway gw as 1.1.1.2 and port number as 2000. The IP address and port number of the SDP gateway must be registered on the SDP controller.
[Device] sslvpn gateway gw
[Device-sslvpn-gateway-gw] ip address 1.1.1.2 port 2000
[Device-sslvpn-gateway-gw] service enable
[Device-sslvpn-gateway-gw] quit
# Enable SDP for trusted access control and configure the related settings.
[Device] trusted-access controller sdp
[Device-tac-sdp] sdp access-method web-access
[Device-tac-sdp] sdp api-access default deny
[Device-tac-sdp] sdp enable
6. Configure SDP contexts to provide Web access service. Create an SDP context and associate SDP context default with SDP gateway gw.
[Device] sslvpn context default
[Device-sslvpn-context-default] gateway gw
[Device-sslvpn-context-default] url-item urlitem
[Device-sslvpn-context-default-url-item-urlitem] url https://30.3.3.3
[Device-sslvpn-context-default-url-item-urlitem] url-mapping domain-mapping www.domain.example.com
[Device-sslvpn-context-default-url-item-urlitem] quit
[Device-sslvpn-context-default] quit
7. Configure a cloud connection to establish a cloud management tunnel for communication between the SDP gateway and the SDP controller. In this example, the domain name and IP address of the SDP controller is www.sdpexample.com and 2.2.2.10, respectively.
[Device] ip host www.sdpexample.com 2.2.2.10
[Device] cloud-management server domain www.sdpexample.com
[Device] cloud-management server port 19002
[Device] cloud-management keepalive 10
8. Enable protocols for the cloud connection feature. Enable RESTful, NETCONF, HTTP, and HTTPS for communication between the SDP controller and the SDP gateway.
[Device] restful http enable
[Device] restful https enable
[Device] netconf soap http enable
[Device] netconf soap https enable
[Device] ip http enable
[Device] ip https enable
Verifying the configuration
# Verify that the SDP gateway information contains the application resources assigned by the SDP controller to users.
[Device] display trusted-access controller sdp assigned-resource app
Context : default
App ID : 12345
App Name : urlitem
AccessType : web proxy
Protocol : HTTPS
IPv4Address : 30.3.3.3
HostName : host1
Port : 4430
# Verify that the SDP session information is as follows:
[Device] display trusted-access controller sdp session
User : user1
Authentication method : SDP authentication
Context : default
Created at : 13:49:27 UTC Wed 04/14/2021
Latest : 17:50:58 UTC Wed 04/14/2021
Session ID : 1
Send rate : 0.00 B/s
Receive rate : 0.00 B/s
Sent bytes : 0.00 B
Received bytes : 0.00 B
Apps : urlitem/permit;
app2/deny;
…
APIs : api1/permit;
api2/deny;
…
Example: Configuring IP access
Network configuration
As shown in Figure 5, the device acts as the SDP gateway that connects the public network and private network. To access the internal resources, follow these steps:
1. A user sends an authentication request to the SDP controller.
2. After authentication is passed, the SDP controller assigns the resources that the user can access.
3. The user accesses the assigned resources through the SDP gateway.
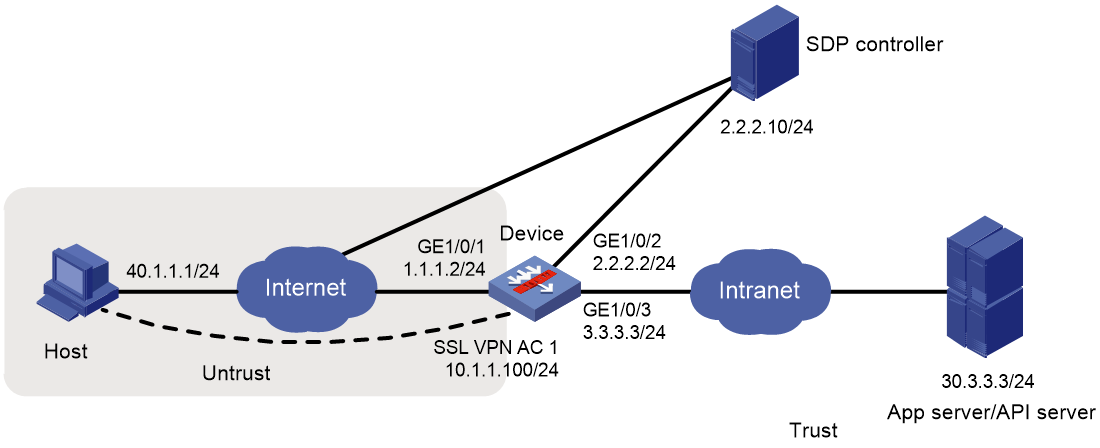
Network diagram
Figure 6 Network diagram
Prerequisites
Before configuring IP access, make sure the SDP controller has been deployed for authenticating users and authorizing users to access resources.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 1.1.1.2 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Create SSL VPN AC interface AC 1 and configure the IP address as 10.1.1.100/24 for the interface. Make sure the IP address is in the same subnet as the address pool on the SDP controller.
[Device] interface sslvpn-ac 1
[Device-SSLVPN-AC1] ip address 10.1.1.100 24
[Device-SSLVPN-AC1] quit
3. Configure settings for routing.
This example configures static routes, and the next hop in the routes is 3.3.3.4 to the app server or API server, and 1.1.1.3 to the host.
[Device] ip route-static 30.3.3.3 24 3.3.3.4
[Device] ip route-static 40.1.1.1 24 1.1.1.3
4. Add interfaces to security zones.
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/1
[Device-security-zone-Untrust] import interface sslvpn-ac 1
[Device-security-zone-Untrust] quit
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/2
[Device-security-zone-Trust] import interface gigabitethernet 1/0/3
[Device-security-zone-Trust] quit
5. Configure rules in a security policy to permit the traffic between the specified security zones for the user to access the SDP gateway:
# Configure a rule named sdplocalout1 to permit the packets from the device to the user.
[Device] security-policy ip
[Device-security-policy-ip] rule name sdplocalout1
[Device-security-policy-ip-1-sdplocalout1] source-zone local
[Device-security-policy-ip-1-sdplocalout1] destination-zone untrust
[Device-security-policy-ip-1-sdplocalout1] source-ip-host 1.1.1.2
[Device-security-policy-ip-1-sdplocalout1] destination-ip-host 40.1.1.1
[Device-security-policy-ip-1-sdplocalout1] action pass
[Device-security-policy-ip-1-sdplocalout1] quit
# Configure a rule named sdplocalin1 to permit the packets from the user to the device.
[Device-security-policy-ip] rule name sdplocalin1
[Device-security-policy-ip-2-sdplocalin1] source-zone untrust
[Device-security-policy-ip-2-sdplocalin1] destination-zone local
[Device-security-policy-ip-2-sdplocalin1] source-ip-host 40.1.1.1
[Device-security-policy-ip-2-sdplocalin1] destination-ip-host 1.1.1.2
[Device-security-policy-ip-2-sdplocalin1] action pass
[Device-security-policy-ip-2-sdplocalin1] quit
# Configure a rule named sdplocalout2 to permit the packets from the device to the app server, API server, and SDP controller.
[Device-security-policy-ip] rule name sdplocalout2
[Device-security-policy-ip-3-sdplocalout2] source-zone local
[Device-security-policy-ip-3-sdplocalout2] destination-zone trust
[Device-security-policy-ip-3-sdplocalout2] source-ip-host 2.2.2.2
[Device-security-policy-ip-3-sdplocalout2] source-ip-host 3.3.3.3
[Device-security-policy-ip-3-sdplocalout2] destination-ip-host 2.2.2.10
[Device-security-policy-ip-3-sdplocalout2] destination-ip-host 30.3.3.3
[Device-security-policy-ip-3-sdplocalout2] action pass
[Device-security-policy-ip-3-sdplocalout2] quit
# Configure a rule named sdplocalin2 to permit the packets from the app server, API server, and the SDP controller to the device.
[Device-security-policy-ip] rule name sdplocalin2
[Device-security-policy-ip-4-sdplocalin2] source-zone trust
[Device-security-policy-ip-4-sdplocalin2] destination-zone local
[Device-security-policy-ip-4-sdplocalin2] source-ip-host 2.2.2.10
[Device-security-policy-ip-4-sdplocalin2] source-ip-host 30.3.3.3
[Device-security-policy-ip-4-sdplocalin2] destination-ip-host 2.2.2.2
[Device-security-policy-ip-4-sdplocalin2] destination-ip-host 3.3.3.3
[Device-security-policy-ip-4-sdplocalin2] action pass
[Device-security-policy-ip-4-sdplocalin2] quit
[Device-security-policy-ip] quit
# Configure a rule named untrust-trust to allow the user to access the app server or API server through the SSL VPN AC interface.
[Device-security-policy-ip] rule name untrust-trust
[Device-security-policy-ip-5-untrust-trust] source-zone untrust
[Device-security-policy-ip-5-untrust-trust] destination-zone trust
[Device-security-policy-ip-5-untrust-trust] source-ip-subnet 10.1.1.0 24
[Device-security-policy-ip-5-untrust-trust] destination-ip-host 30.3.3.3
[Device-security-policy-ip-5-untrust-trust] action pass
[Device-security-policy-ip-5-untrust-trust] quit
# Configure a rule named trust-untrust to permit the packets from the app server or API server to the user through the SSL VPN AC interface.
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-6-trust-untrust] source-zone trust
[Device-security-policy-ip-6-trust-untrust] destination-zone untrust
[Device-security-policy-ip-6-trust-untrust] source-ip-host 30.3.3.3
[Device-security-policy-ip-6-trust-untrust] destination-ip-subnet 10.1.1.0 24
[Device-security-policy-ip-6-trust-untrust] action pass
[Device-security-policy-ip-6-trust-untrust] quit
[Device-security-policy-ip] quit
6. Configure the SDP gateway for user access to internal resources:
# Configure the IP address for SDP gateway gw as 1.1.1.2 and port number as 2000. The IP address and port number of the SDP gateway must be registered on the SDP controller.
[Device] sslvpn gateway gw
[Device-sslvpn-gateway-gw] ip address 1.1.1.2 port 2000
[Device-sslvpn-gateway-gw] service enable
[Device-sslvpn-gateway-gw] quit
# Enable SDP for trusted access control and configure the related settings.
[Device] trusted-access controller sdp
[Device-tac-sdp] sdp access-method ip-tunnel
[Device-tac-sdp] sdp api-access default deny
[Device-tac-sdp] spa enable
[Device-tac-sdp] sdp enable
7. Configure SDP contexts to provide IP access service. Create an SDP context and associate SDP context default with SDP gateway gw.
[Device] sslvpn context default
[Device-sslvpn-context-default] gateway gw
[Device-sslvpn-context-default] ip-tunnel interface sslvpn-ac 1
[Device-sslvpn-context-default] quit
8. Configure a cloud connection to establish a cloud management tunnel for communication between the SDP gateway and the SDP controller. In this example, the domain name and IP address of the SDP controller is www.sdpexample.com and 2.2.2.10, respectively.
[Device] ip host www.sdpexample.com 2.2.2.10
[Device] cloud-management server domain www.sdpexample.com
[Device] cloud-management server port 19002
[Device] cloud-management keepalive 10
9. Enable protocols for the cloud connection feature. Enable RESTful, NETCONF, HTTP, and HTTPS for communication between the SDP controller and the SDP gateway.
[Device] restful http enable
[Device] restful https enable
[Device] netconf soap http enable
[Device] netconf soap https enable
[Device] ip http enable
[Device] ip https enable
10. Configure the device to make sure that the SDP controller can access the device through the following protocols without being restricted by security policies:
SPA authentication is not required between the SDP gateway and SDP controller, so the specified protocol packets that are not affected by security policies can bypass SPA authentication.
[Device] interface gigabitethernet 1/0/2
[Device-GigabitEthernet1/0/2] manage http inbound
[Device-GigabitEthernet1/0/2] manage https inbound
[Device-GigabitEthernet1/0/2] manage netconf-http inbound
[Device-GigabitEthernet1/0/2] manage netconf-https inbound
[Device-GigabitEthernet1/0/2] manage netconf-ssh inbound
[Device-GigabitEthernet1/0/2] manage ping inbound
[Device-GigabitEthernet1/0/2] manage snmp inbound
[Device-GigabitEthernet1/0/2] manage ssh inbound
[Device-GigabitEthernet1/0/2] manage telnet inbound
Verifying the configuration
# Verify that the SDP gateway information contains the application resources assigned by the SDP controller to users.
[Device] display trusted-access controller sdp assigned-resource app
Context : default
App ID : 12345
App Name : urlitem
AccessType : ip-tunnel
Protocol : HTTPS
IPv4Address : 30.3.3.3
HostName : host1
Port : 4430
# Verify that the SDP session information is as follows:
[Sysname] display trusted-access controller sdp session
User : user1
Authentication method : SDP authentication
Context : default
Created at : 13:49:27 UTC Wed 04/14/2021
Latest : 17:50:58 UTC Wed 04/14/2021
Allocated IPv4 address : 10.1.1.1
Session ID : 1
Send rate : 0.00 B/s
Receive rate : 0.00 B/s
Sent bytes : 0.00 B
Received bytes : 0.00 B
Apps : app1/permit;
app2/deny;
…
APIs : api1/permit;
api2/deny;
…