- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 03-EVPN VPLS configuration | 254.15 KB |
Contents
Neighbor auto-discovery and PW establishment
MAC address learning, aging, and withdrawal
Traffic forwarding and flooding
Mapping a Layer 3 interface to a VSI
Configuring BGP to advertise BGP EVPN routes
Restrictions and guidelines for BGP EVPN route advertisement
Enabling BGP to advertise BGP EVPN routes
Configuring optimal route selection and route advertisement settings
Managing remote MAC address entries and remote ARP learning
Disabling MAC address advertisement
Enabling MAC mobility event suppression
Disabling learning of MAC addresses from ARP or ND information
Disabling ARP information advertisement
Enabling ARP flood suppression
Verifying and maintaining EVPN VPLS
Displaying BGP EVPN running status and statistics information
Displaying EVPN route information
EVPN VPLS configuration examples
Example: Configuring EVPN VPLS between singlehomed sites
Configuring EVPN VPLS
About EVPN VPLS
EVPN Virtual Private LAN Service (VPLS) is a Layer 2 VPN technology that uses MP-BGP to advertise EVPN routes in the control plane and MPLS for forwarding in the data plane. EVPN VPLS provides point-to-multipoint forwarding services for users with MAC address table lookup in VSIs.
EVPN VPLS network model
As shown in Figure 1, an EVPN VPLS network contains the following devices:
· Customer edge (CE)—Customer device directly connected to the service provider network.
· Provider edge (PE)—Service provider device connected to CEs. PEs provide access to the EVPN VPLS network and forward traffic between customer network sites by using public tunnels.
A PE uses ACs, PWs, tunnels, and VSIs to provide EVPN VPLS services.
· Attachment circuit (AC)—A physical or virtual link between a CE and a PE.
· Pseudowire (PW)—A virtual bidirectional connection between two PEs. A PW contains a pair of virtual links in opposite directions.
· Public tunnel—A connection that carries one or more PWs across the MPLS or IP backbone. A public tunnel can be an LSP, GRE, or MPLS TE tunnel.
· Virtual Switch Instance (VSI)—A virtual switch instance provides Layer 2 switching services for a VPLS instance (EVPN instance) on a PE. A VSI acts as a virtual switch that has all the functions of a conventional Ethernet switch, including source MAC address learning, MAC address aging, and flooding. VPLS uses VSIs to forward Layer 2 data packets in EVPN instances.
Neighbor auto-discovery and PW establishment
A PE uses Ethernet auto-discovery or IMET routes to automatically discover neighbors and establish PWs. When a PE receives an Ethernet auto-discovery or IMET route in a VSI, it compares the export route targets of the route with the import route targets of the EVPN instance associated with the VSI. If they are match, the PE will establish a unidirectional virtual link based on the PE address and PW label information carried in the route. PW establishment is finished when two virtual links in opposite directions are established between two PEs.
MAC address learning, aging, and withdrawal
Source MAC address learning
A PE uses the MAC address table of a VSI to forward Layer 2 unicast traffic for that VSI.
A PE learns source MAC addresses in the following ways:
· Local MAC address learning—Learns the source MAC addresses of local CEs.
When the PE receives a frame from a local CE, it first identifies the VSI of the frame. Then, the PE adds the source MAC address of the frame (the MAC address of the local CE) to the MAC address table of the VSI. The output interface of the MAC address entry is the AC that receives the frame.
· Remote MAC address learning—Learns the source MAC addresses of remote CEs.
A PE advertises the MAC addresses of local CEs to remote PEs through BGP EVPN MAC/IP advertisement routes. When a remote PE receives the routes, it adds the received MAC addresses to the MAC address table of the corresponding VSI. The output interface is the PW between the PEs.
MAC address aging
· Local MAC address aging—The MAC address table uses an aging timer for each dynamic MAC address entry. If no packet is received from a MAC address before the aging timer expires, VPLS deletes the MAC address.
· Remote MAC address aging—Remote MAC addresses advertised through MAC/IP advertisement routes are not removed from the MAC address table until routes to withdraw the MAC addresses are received.
MAC address withdrawal
When an AC goes down, the PE deletes MAC addresses on the AC. Then it sends an LDP address withdrawal message to notify all other PEs in the EVPN instance to delete those MAC addresses.
Traffic forwarding and flooding
Unicast traffic forwarding
After a PE receives a unicast packet with a known destination MAC address from an AC, the PE searches the MAC address table of the VSI bound to the AC for packet forwarding.
· If the output interface in the entry is a PW, the PE inserts the PW label to the packet, and adds the public tunnel header to the packet. It then forwards the packet to the remote PE over the PW. If the public tunnel is an LSP or MPLS TE tunnel, each packet on the PW contains two labels. The inner label is the PW label, which identifies the PW and ensures that the packet is forwarded to the correct VSI. The outer label is the public LSP or MPLS TE tunnel label, which ensures that the packet is correctly forwarded to the remote PE.
· If the output interface in the entry is a local interface, the PE directly forwards the packet to the local interface.
After a PE receives a unicast packet with a known destination MAC address from a PW, the PE searches the MAC address table of the VSI bound to the PW for packet forwarding. The PE forwards the packet through the output interface in the matching MAC address entry.
Flooding
When a PE receives flood traffic from an AC in a VSI, it will flood the traffic to the following interfaces:
· All ACs in the VSI except for the incoming AC.
· All PWs associated with the VSI.
When a PE receives flood traffic from a PW, it will flood the traffic to all ACs in the VSI bound to the PW.
Full mesh and split horizon
A Layer 2 network requires a loop prevention protocol such as STP to avoid loops. However, a loop prevention protocol on PEs brings management and maintenance difficulties. Therefore, EVPN VPLS uses the following methods to prevent loops:
· Full mesh—Every two PEs in an EVPN instance must establish a PW. The PWs form a full mesh among PEs in the EVPN instance.
· Split horizon—A PE does not forward packets received from a PW to any other PWs in the same VSI but only forwards those packets to ACs.
ARP flood suppression
ARP flood suppression reduces ARP request broadcasts by enabling a PE to reply to ARP requests on behalf of VMs.
As shown in Figure 2, this feature snoops ARP requests, ARP responses, and BGP EVPN routes to populate the ARP flood suppression table with local and remote MAC addresses. If an ARP request has a matching entry, the PE replies to the request on behalf of the VM. If no match is found, the PE floods the request to both local and remote sites.
Figure 2 ARP flood suppression
ARP flood suppression uses the following workflow:
1. CE1 sends an ARP request to obtain the MAC address of CE 2.
2. PE 1 creates a suppression entry for CE 1, floods the ARP request to local CEs and remote PEs (PE 2 and PE 3) in the VSI, and sends the suppression entry to PE 2 and PE 3 through BGP EVPN. Unicast-mode flooding is used to illustrate the workflow.
3. PE 2 and PE 3 de-encapsulate the ARP request and broadcast the request to local CEs in the VSI.
4. CE 2 sends an ARP reply after it receives the ARP request.
5. PE 2 creates a suppression entry for CE 2, forwards the ARP reply to PE 1, and sends the suppression entry to PE 1 and PE 3 through BGP EVPN.
6. PE 1 de-encapsulates the ARP reply and forwards the ARP reply to CE 1.
7. CE 4 sends an ARP request to obtain the MAC address of CE 1.
8. PE 1 creates a suppression entry for CE 4 and replies to the ARP request.
9. CE 3 sends an ARP request to obtain the MAC address of CE 1.
10. PE 3 creates a suppression entry for CE 3 and replies to the ARP request.
Control word
The control word field is between the MPLS label stack and the Layer 2 data. It carries control information for the Layer 2 frame, for example, the sequence number.
The control word feature has the following functions:
· Avoids fragment disorder. In multipath forwarding, fragments received might be disordered. The control word feature reorders the fragments according to the sequence number carried in the control word field.
· Identifies the original payload length for packets that include padding.
The control word field is optional for EVPN VPLS. You can configure whether to carry the control word field in packets sent on PWs. If you enable the control word feature on PEs at both ends of a PW, packets transmitted on the PW carry the control word field. Otherwise, the packets do not carry the control word field.
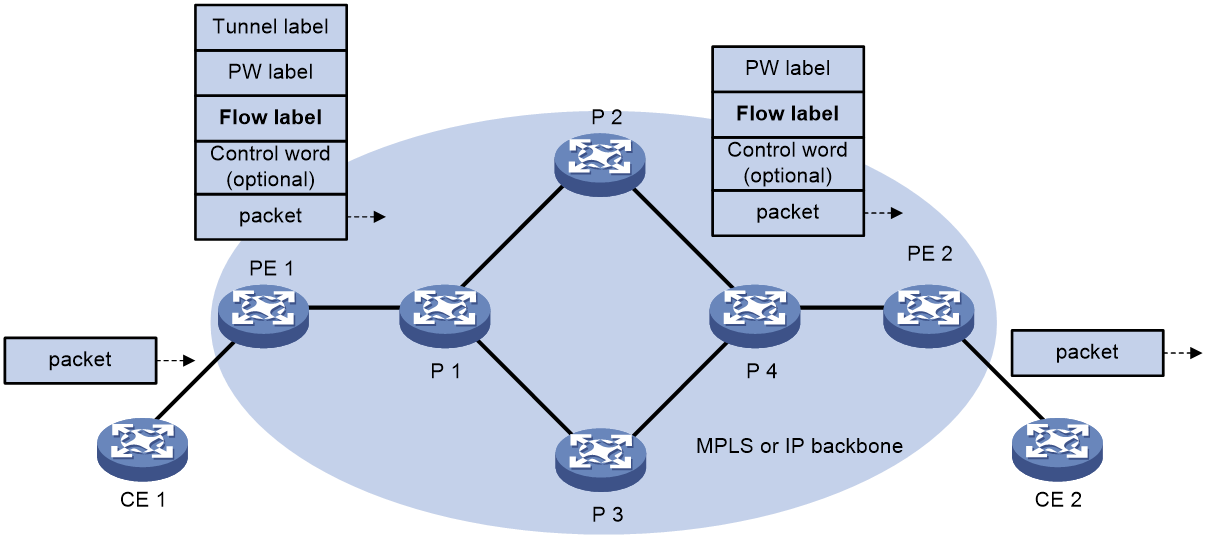
L2VPN flow label
Packets carrying different types of traffic might be transmitted through the same PW and encapsulated with the same PW label. The P devices forward the traffic flows of a PW over the same path even if Equal Cost Multiple Paths (ECMPs) exist.
The L2VPN flow label feature can enable a P device to perform load sharing on packets based on the flow types.
After you configure this feature, the P and PE devices process packets as follows:
· When the ingress PE encapsulates a packet, it adds a flow label before it adds a PW label, as shown in Figure 3.
The ingress PE adds different flow labels for packets of different traffic types.
· The P devices perform load sharing on packets based on the flow labels.
· The egress PE removes both the PW and flow labels from a packet before forwarding the packet.
Figure 3 L2VPN flow label feature
You can enable the flow label sending, receiving, or both sending and receiving capabilities on a PE.
· The sending capability enables a PE to send packets with flow labels. The PE adds a flow label before it adds a PW label to a packet during encapsulation.
· The receiving capability enables a PE to identify the flow label in a received packet and removes the flow label before forwarding the packet.
For two PEs to successfully negotiate the flow label capabilities, make sure one end has the sending capability and the other end has the receiving capability.
For EVPN VPLS, you must manually configure flow label capabilities for the local and remote PEs.
MAC mobility
MAC mobility refers to the movement of a VM or host from one ES to another. The source PE is unaware of the MAC move event. To notify other PEs of the change, the destination PE advertises a MAC/IP advertisement route for the MAC address. The source PE withdraws the old route for the MAC address after receiving the new route. The MAC/IP advertisement route has a sequence number that increases when the MAC address moves. The sequence number identifies the most recent move if the MAC address moves multiple times.
EVPN VPLS tasks at a glance
To configure EVPN VPLS, perform the following tasks:
b. (Optional.) Configure VSI parameters
2. Configuring an EVPN instance
¡ Mapping a Layer 3 interface to a VSI
4. Configuring BGP to advertise BGP EVPN routes
a. Enabling BGP to advertise BGP EVPN routes
b. (Optional.) Configuring optimal route selection and route advertisement settings
c. (Optional.) Maintaining BGP sessions
5. (Optional.) Configuring a PW class
6. (Optional.) Managing remote MAC address entries and remote ARP learning
¡ Disabling MAC address advertisement
¡ Enabling MAC mobility event suppression
¡ Disabling learning of MAC addresses from ARP or ND information
¡ Disabling ARP information advertisement
7. (Optional.) Optimizing and maintaining an EVPN VPLS network:
¡ Enabling ARP flood suppression
Configuring a VSI
Creating a VSI
1. Enter system view.
system-view
2. Enable L2VPN.
l2vpn enable
By default, L2VPN is disabled.
3. Create a VSI and enter VSI view.
vsi vsi-name
4. Bring up the VSI.
undo shutdown
By default, a VSI is not administratively down.
Configure VSI parameters
1. Enter system view.
system-view
2. Enter VSI view.
vsi vsi-name
3. Configure a VSI description.
description text
By default, a VSI does not have a description.
4. Set the MTU of the VSI.
mtu mtu
The default MTU for a VSI is 1500 bytes.
5. Enable MAC address learning for the VSI.
mac-learning enable
By default, MAC address learning is enabled for a VSI.
Configuring an EVPN instance
About this task
An EVPN instance acts as a VPLS instance in an EVPN VPLS network. The EVPN routes advertised by the PE carry the RD and route targets configured for the EVPN instance associated with a VSI.
Procedure
1. Enter system view.
system-view
2. Enter VSI view.
vsi vsi-name
3. Create an EVPN instance and enter VSI EVPN instance view.
evpn encapsulation mpls
4. Configure an RD for the EVPN instance.
route-distinguisher route-distinguisher
By default, no RD is configured for an EVPN instance.
5. Configure route targets for the EVPN instance.
vpn-target { vpn-target&<1-8> | auto } [ both | export-extcommunity | import-extcommunity ]
By default, an EVPN instance does not have route targets.
Make sure the following requirements are met:
¡ The import targets of the EVPN instance do not match the export targets of the VPN instance associated with the VSI or the public instance.
¡ The export targets of the EVPN instance do not match the import targets of the VPN instance associated with the VSI or the public instance.
6. Apply a PW class to the EVPN instance.
pw-class class-name
By default, no PW class is applied to an EVPN instance.
The specified PW class applies to all PWs in the EVPN instance.
7. (Optional.) Apply an export routing policy to the EVPN instance.
export route-policy route-policy
By default, no export routing policy is applied to an EVPN instance.
8. (Optional.) Apply an import routing policy to the EVPN instance.
import route-policy route-policy
By default, no import routing policy is applied to an EVPN instance. The EVPN instance accepts a route when the export route targets of the route match local import route targets.
Mapping ACs to a VSI
Mapping a Layer 3 interface to a VSI
About this task
To assign the customer traffic on a Layer 3 interface to a VSI, map that interface to the VSI. The VSI uses its MAC address table to forward the customer traffic.
For more information about the commands in this task, see VPLS in MPLS Command Reference.
Procedure
1. Enter system view.
system-view
2. Enter Layer 3 interface view.
interface interface-type interface-number
3. Map the Layer 3 interface to a VSI.
xconnect vsi vsi-name [ access-mode { ethernet | vlan } ] [ track track-entry-number&<1-3> ]
By default, a Layer 3 interface is not mapped to a VSI.
Configuring BGP to advertise BGP EVPN routes
Restrictions and guidelines for BGP EVPN route advertisement
For more information about BGP commands in this task, see Layer 3—IP Routing Command Reference.
Enabling BGP to advertise BGP EVPN routes
1. Enter system view.
system-view
2. Configure a global router ID.
router id router-id
By default, no global router ID is configured.
3. Enable a BGP instance and enter BGP instance view.
bgp as-number [ instance instance-name ]
By default, BGP is disabled and no BGP instances exist.
4. Specify remote PEs as BGP peers.
peer { group-name | ipv4-address [ mask-length ] } as-number as-number
5. Create the BGP EVPN address family and enter BGP EVPN address family view.
address-family l2vpn evpn
6. Enable BGP to exchange BGP EVPN routes with a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } enable
By default, BGP does not exchange BGP EVPN routes with peers.
Configuring optimal route selection and route advertisement settings
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP EVPN address family view.
address-family l2vpn evpn
4. Permit the local AS number to appear in routes from a peer or peer group and set the number of appearances.
peer { group-name | ipv4-address [ mask-length ] } allow-as-loop [ number ]
By default, the local AS number is not allowed in routes from peers.
5. Enable route target filtering for BGP EVPN routes.
policy vpn-target
By default, route target filtering is enabled for BGP EVPN routes.
6. (Optional.) Set the optimal route selection delay timer.
route-select delay delay-value
By default, the optimal route selection delay timer is 0 seconds, which means optimal route selection is not delayed.
7. (Optional.) Set the delay time for responding to recursive next hop changes.
nexthop recursive-lookup [ non-critical-event ] delay [ delay-value ]
By default, BGP responds to recursive next hop changes immediately.
8. Configure BGP route reflection settings:
a. Configure the device as an RR and specify a peer or peer group as its client.
peer { group-name | ipv4-address [ mask-length ] } reflect-client
By default, no RR or client is configured.
b. (Optional.) Enable BGP EVPN route reflection between clients.
reflect between-clients
By default, BGP EVPN route reflection between clients is enabled.
c. (Optional.) Configure the cluster ID of the RR.
reflector cluster-id { cluster-id | ipv4-address }
By default, an RR uses its own router ID as the cluster ID.
d. (Optional.) Create a reflection policy for the RR to filter reflected BGP EVPN routes.
rr-filter { ext-comm-list-number | ext-comm-list-name }
By default, an RR does not filter reflected BGP EVPN routes.
e. (Optional.) Create a reflection policy for the RR to filter reflected BGP EVPN routes.
reflect change-path-attribute
By default, an RR does not filter reflected BGP EVPN routes.
f. (Optional.) Add a peer or peer group to the nearby cluster.
peer { group-name | ipv4-address [ mask-length ] } reflect-nearby-group
By default, the nearby cluster does not have any peers or peer groups.
The RR does not change the next hop of routes reflected to peers or peer groups in the nearby cluster.
9. Configure the device to not change the next hop of routes advertised to an EBGP peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } next-hop-invariable
By default, the device uses its address as the next hop of routes advertised to EBGP peers.
10. Set a preferred value for routes received from a peer or peer group
peer { group-name | ipv4-address [ mask-length ] | ipv6-address [ prefix-length ] } preferred-value value
By default, the preferred value is 0 for routes received from a peer or peer group.
11. Apply a routing policy to routes received from or advertised to a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } route-policy route-policy-name { export | import }
By default, no routing policies are applied to routes received from or advertised to peers or peer groups.
12. Advertise the COMMUNITY attribute to a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] } advertise-community
By default, the device does not advertise the COMMUNITY attribute to peers or peer groups.
Maintaining BGP sessions
Perform the following tasks in user view:
· Reset BGP sessions of the BGP EVPN address family.
reset bgp [ instance instance-name ] { as-number | ipv4-address [ mask-length ] | all | external | group group-name | internal } l2vpn evpn
· Soft-reset BGP sessions of the BGP EVPN address family.
refresh bgp [ instance instance-name ] { ipv4-address [ mask-length ] | all | external | group group-name | internal } { export | import } l2vpn evpn
Configuring a PW class
About this task
In a PW class, you can configure PW attributes such as the PW data encapsulation type, and whether to enable control word. To simplify PW attribute configuration for PWs, you can configure a PW class and apply the PW class to the PWs.
Restrictions and guidelines
As a best practice, configure the same data encapsulation type for the two ends of a PW.
For more information about PW class commands, see MPLS L2VPN in MPLS Command Reference.
Procedure
1. Enter system view.
system-view
2. Create a PW class and enter PW class view.
pw-class class-name
3. Enable control word.
control-word enable
By default, control word is disabled.
4. Specify the PW data encapsulation type.
pw-type { ethernet | vlan }
By default, the PW data encapsulation type is VLAN.
5. Enable the flow label feature and configure flow label capabilities.
flow-label { both | receive | send } [ static ]
By default, the flow label feature is disabled.
Managing remote MAC address entries and remote ARP learning
Disabling MAC address advertisement
About this task
The MAC information and ARP or ND information advertised by the PE overlap. To avoid duplication, disable MAC address advertisement and withdraw the MAC addresses advertised to remote PEs.
Procedure
1. Enter system view.
system-view
2. Enter VSI view.
vsi vsi-name
3. Enter VSI EVPN instance view.
evpn encapsulation mpls
4. Disable MAC address advertisement and withdraw advertised MAC addresses.
mac-advertising disable
By default, MAC address advertisement is enabled.
Enabling MAC mobility event suppression
About this task
On an EVPN VPLS network, misconfiguration of MAC addresses might cause two sites to contain the same MAC address. In this condition, the PEs at the two sites constantly synchronize and update EVPN MAC address entries and determine that MAC mobility events occur. As a result, an inter-site loop might occur, and the bandwidth is occupied by MAC entry synchronization traffic. To eliminate loops and suppress those MAC mobility events, enable MAC mobility event suppression on the PEs.
The MAC mobility event suppression feature allows a MAC address to move at most the specified number of times (MAC mobility suppression threshold) out of a site within a MAC mobility detection cycle. If the suppression threshold has been reached for a MAC address within a detection cycle, the PE at the site suppresses the subsequent move after the MAC address moves back to the site. In addition, the PE learns the MAC address but does not advertise the MAC address.
Restrictions and guidelines
After you execute the undo evpn route mac-mobility suppression command or when the MAC mobility suppression time expires, a PE acts as follows:
· Advertises MAC address entries immediately for the suppressed MAC address entries that have not aged out.
· Relearns the MAC addresses for the suppressed MAC address entries that have aged out and advertises the MAC address entries.
If both MAC address entry conflicts and ARP entry conflicts exist for a MAC address, you must enable both MAC mobility event suppression and ARP mobility event suppression. If you enable only MAC mobility event suppression, the system cannot suppress MAC mobility events for the MAC address.
Procedure
1. Enter system view.
system-view
2. Enable MAC mobility event suppression.
evpn route mac-mobility suppression [ detect-cycle detect-time | detect-threshold move-times | suppression-time [ suppression-time | permanent ] ] *
By default, MAC mobility event suppression is disabled.
Disabling learning of MAC addresses from ARP or ND information
About this task
The MAC information and ARP or ND information advertised by a remote PE overlap. To avoid duplication, disable the learning of MAC addresses from ARP or ND information. EVPN will learn remote MAC addresses only from the MAC information advertised from remote sites.
Procedure
1. Enter system view.
system-view
2. Enter VSI view.
vsi vsi-name
3. Enter VSI EVPN instance view.
evpn encapsulation mpls
4. Disable the EVPN instance from learning MAC addresses from ARP information.
arp mac-learning disable
By default, an EVPN instance learns MAC addresses from ARP information.
5. Disable the EVPN instance from learning MAC addresses from ND information.
nd mac-learning disable
By default, an EVPN instance learns MAC addresses from ND information.
Disabling ARP information advertisement
About this task
In an EVPN VPLS network, you can disable ARP information advertisement for an EVPN instance to save resources if all user terminals in the EVPN instance are attached to one PE. The EVPN instance will stop advertising ARP information through MAC/IP advertisement routes and withdraw advertised ARP information.
Procedure
1. Enter system view.
system-view
2. Enter VSI view.
vsi vsi-name
3. Enter VSI EVPN instance view.
evpn encapsulation mpls
4. Disable ARP information advertisement for the EVPN instance.
arp-advertising disable
By default, ARP information advertisement is enabled for an EVPN instance.
Enabling ARP flood suppression
About this task
Use ARP flood suppression to reduce ARP request broadcasts.
Procedure
1. Enter system view.
system-view
2. Enter VSI view.
vsi vsi-name
3. Enable ARP flood suppression.
arp suppression enable
By default, ARP flood suppression is disabled.
Verifying and maintaining EVPN VPLS
Displaying BGP EVPN running status and statistics information
Perform display tasks in any view.
· Display BGP peer group information.
display bgp [ instance instance-name ] group l2vpn evpn [ group-name group-name ]
For more information about this command, see basic BGP commands in Layer 3—IP Routing Command Reference.
· Display BGP peer or peer group information.
display bgp [ instance instance-name ] peer l2vpn evpn [ ipv4-address mask-length | { ipv4-address | group-name group-name } log-info | [ ipv4-address ] verbose ]
For more information about this command, see basic BGP commands in Layer 3—IP Routing Command Reference.
· Display information about BGP update groups.
display bgp [ instance instance-name ] update-group l2vpn evpn [ ipv4-address ]
For more information about this command, see basic BGP commands in Layer 3—IP Routing Command Reference.
· Display information about peers that are automatically discovered through BGP.
display evpn auto-discovery { { imet | mac-ip } [ mpls ] [ peer ip-address] [ vsi vsi-name ] | macip-prefix [ nexthop next-hop ] [ count ] }
· Display BGP EVPN routes.
display bgp [ instance instance-name ] l2vpn evpn [ peer { ipv4-address | ipv6-address } { advertised-routes | received-routes } [ statistics ] | [ route-distinguisher route-distinguisher | route-type { auto-discovery | es | imet | mac-ip } ] * [ { evpn-route route-length | evpn-prefix } [ advertise-info ] | ipv4-address | ipv6-address | mac-address ] | statistics ]
Displaying EVPN route information
Perform display tasks in any view.
· Display EVPN MAC address entries.
display evpn route mac [ mpls ] [ local | remote ] [ vsi vsi-name ] [ mac-address mac-address ] [ count ]
· Display the routing table for a VPN instance.
display evpn routing-table [ ipv6 ] { public-instance | vpn-instance vpn-instance-name } [ count ]
EVPN VPLS configuration examples
Example: Configuring EVPN VPLS between singlehomed sites
Network configuration
As shown in Figure 4, set up a path between PE 1 and PE 2 for the CEs in site 1 and site 2 to communicate through EVPN VPLS over the MPLS or IP backbone network.
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
GE0/0/1 |
10.1.1.10/24 |
P |
Loop0 |
3.3.3.3/32 |
|
PE 1 |
Loop0 |
1.1.1.1/32 |
|
GE0/0/1 |
11.1.1.2/24 |
|
|
GE0/0/1 |
N/A |
|
GE0/0/2 |
11.1.2.2/24 |
|
|
GE0/0/2 |
11.1.1.1/24 |
PE 2 |
Loop0 |
2.2.2.2/32 |
|
CE 2 |
GE0/0/1 |
10.1.1.20/24 |
|
GE0/0/1 |
N/A |
|
|
|
|
|
GE0/0/2 |
11.1.2.1/24 |
Procedure
1. Configure CE 1.
<CE1> system-view
[CE1] interface gigabitethernet 0/0/1
[CE1-GigabitEthernet0/0/1] ip address 10.1.1.10 24
[CE1-GigabitEthernet0/0/1] quit
2. Configure PE 1:
# Configure the LSR ID.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 1.1.1.1 32
[PE1-LoopBack0] quit
[PE1] mpls lsr-id 1.1.1.1
# Enable L2VPN.
[PE1] l2vpn enable
# Enable global LDP.
[PE1] mpls ldp
[PE1-ldp] quit
# Configure GigabitEthernet 0/0/2 (the interface connected to the P device), and enable LDP on the interface.
[PE1] interface gigabitethernet 0/0/2
[PE1-GigabitEthernet0/0/2] ip address 11.1.1.1 24
[PE1-GigabitEthernet0/0/2] mpls enable
[PE1-GigabitEthernet0/0/2] mpls ldp enable
[PE1-GigabitEthernet0/0/2] undo shutdown
[PE1-GigabitEthernet0/0/2] quit
# Configure OSPF for LDP to create LSPs.
[PE1] ospf
[PE1-ospf-1] area 0
[PE1-ospf-1-area-0.0.0.0] network 11.1.1.0 0.0.0.255
[PE1-ospf-1-area-0.0.0.0] network 1.1.1.1 0.0.0.0
[PE1-ospf-1-area-0.0.0.0] quit
[PE1-ospf-1] quit
# Create an IBGP connection to PE 2, and enable BGP to advertise L2VPN information to PE 2.
[PE1] bgp 100
[PE1-bgp-default] peer 2.2.2.2 as-number 100
[PE1-bgp-default] peer 2.2.2.2 connect-interface loopback 0
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 2.2.2.2 enable
[PE1-bgp-default-evpn] quit
[PE1-bgp-default] quit
# Create VSI vpna, create an EVPN instance on the VSI, enable MPLS encapsulation, and configure an RD and route targets for the EVPN instance.
[PE1] vsi vpna
[PE1-vsi-vpna] evpn encapsulation mpls
[PE1-vsi-vpna-evpn-mpls] route-distinguisher 1:1
[PE1-vsi-vpna-evpn-mpls] vpn-target 1:1 export-extcommunity
[PE1-vsi-vpna-evpn-mpls] vpn-target 1:1 import-extcommunity
[PE1-vsi-vpna-evpn-mpls] quit
[PE1-vsi-vpna] quit
# Map GigabitEthernet 0/0/1 (the interface connected to CE 1) to VSI vpna.
[PE1] interface gigabitethernet 0/0/1
[PE1-GigabitEthernet0/0/1] xconnect vsi vpna
[PE1-GigabitEthernet0/0/1] quit
3. Configure the P device:
# Configure the LSR ID.
<P> system-view
[P] interface loopback 0
[P-LoopBack0] ip address 3.3.3.3 32
[P-LoopBack0] quit
[P] mpls lsr-id 3.3.3.3
# Enable global LDP.
[P] mpls ldp
[P-ldp] quit
# Configure GigabitEthernet 0/0/1 (the interface connected to PE 1), and enable LDP on the interface.
[P] interface gigabitethernet 0/0/1
[P-GigabitEthernet0/0/1] ip address 11.1.1.2 24
[P-GigabitEthernet0/0/1] mpls enable
[P-GigabitEthernet0/0/1] mpls ldp enable
[P-GigabitEthernet0/0/1] undo shutdown
[P-GigabitEthernet0/0/1] quit
# Configure GigabitEthernet 0/0/2 (the interface connected to PE 2), and enable LDP on the interface.
[P] interface gigabitethernet 0/0/2
[P-GigabitEthernet0/0/2] ip address 11.1.2.2 24
[P-GigabitEthernet0/0/2] mpls enable
[P-GigabitEthernet0/0/2] mpls ldp enable
[P-GigabitEthernet0/0/2] undo shutdown
[P-GigabitEthernet0/0/2] quit
# Configure OSPF for LDP to create LSPs.
[P] ospf
[P-ospf-1] area 0
[P-ospf-1-area-0.0.0.0] network 11.1.1.0 0.0.0.255
[P-ospf-1-area-0.0.0.0] network 11.1.2.0 0.0.0.255
[P-ospf-1-area-0.0.0.0] network 3.3.3.3 0.0.0.0
[P-ospf-1-area-0.0.0.0] quit
[P-ospf-1] quit
4. Configure PE 2:
# Configure the LSR ID.
<PE2> system-view
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 2.2.2.2 32
[PE2-LoopBack0] quit
[PE2] mpls lsr-id 2.2.2.2
# Enable L2VPN.
[PE2] l2vpn enable
# Enable global LDP.
[PE2] mpls ldp
[PE2-ldp] quit
# Configure GigabitEthernet 0/0/2 (the interface connected to the P device), and enable LDP on the interface.
[PE2] interface gigabitethernet 0/0/2
[PE2-GigabitEthernet0/0/2] ip address 11.1.2.1 24
[PE2-GigabitEthernet0/0/2] mpls enable
[PE2-GigabitEthernet0/0/2] mpls ldp enable
[PE2-GigabitEthernet0/0/2] undo shutdown
[PE2-GigabitEthernet0/0/2] quit
# Configure OSPF for LDP to create LSPs.
[PE2] ospf
[PE2-ospf-1] area 0
[PE2-ospf-1-area-0.0.0.0] network 2.2.2.2 0.0.0.0
[PE2-ospf-1-area-0.0.0.0] network 11.1.2.0 0.0.0.255
[PE2-ospf-1-area-0.0.0.0] quit
[PE2-ospf-1] quit
# Create an IBGP connection to PE 1, and enable BGP to advertise L2VPN information to PE 1.
[PE2] bgp 100
[PE2-bgp-default] peer 1.1.1.1 as-number 100
[PE2-bgp-default] peer 1.1.1.1 connect-interface loopback 0
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 1.1.1.1 enable
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] quit
# Create VSI vpna, create an EVPN instance on the VSI, enable MPLS encapsulation, and configure an RD and route targets for the EVPN instance.
[PE2] vsi vpna
[PE2-vsi-vpna] evpn encapsulation mpls
[PE2-vsi-vpna-evpn-mpls] route-distinguisher 1:1
[PE2-vsi-vpna-evpn-mpls] vpn-target 1:1 export-extcommunity
[PE2-vsi-vpna-evpn-mpls] vpn-target 1:1 import-extcommunity
[PE2-vsi-vpna-evpn-mpls] quit
[PE2-vsi-vpna] quit
# Map GigabitEthernet 0/0/1 (the interface connected to CE 2) to VSI vpna.
[PE2] interface gigabitethernet 0/0/1
[PE2-GigabitEthernet0/0/1] xconnect vsi vpna
[PE2-GigabitEthernet0/0/1] quit
5. Configure CE 2.
<CE2> system-view
[CE2] interface gigabitethernet 0/0/1
[CE2-GigabitEthernet0/0/1] ip address 10.1.1.20 24
[CE2-GigabitEthernet0/0/1] quit
Verifying the configuration
# Verify that an EVPN PW has been established between PE 1 and PE 2.
[PE1] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
VSI Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
2.2.2.2 - 775127/775127 EVPN M 8 Up
# Display PW information on PE 2.
[PE2] display l2vpn pw
Flags: M - main, B - backup, E - ecmp, BY - bypass, H - hub link, S - spoke link
N - no split horizon, A - administration, ABY - ac-bypass
PBY - pw-bypass
Total number of PWs: 1
1 up, 0 blocked, 0 down, 0 defect, 0 idle, 0 duplicate
VSI Name: vpna
Peer PWID/RmtSite/SrvID In/Out Label Proto Flag Link ID State
1.1.1.1 - 775127/775127 EVPN M 8 Up
# Verify that CE 1 and CE 2 can ping each other. (Details not shown.)