- Table of Contents
-
- 09-Security Configuration Guide
- 00-Preface
- 01-AAA configuration
- 02-Password control configuration
- 03-Keychain configuration
- 04-Public key management
- 05-PKI configuration
- 06-IPsec configuration
- 07-SSH configuration
- 08-SSL configuration
- 09-Object group configuration
- 10-Attack detection and prevention configuration
- 11-TCP attack prevention configuration
- 12-IP source guard configuration
- 13-ARP attack protection configuration
- 14-ND attack defense configuration
- 15-uRPF configuration
- 16-SAVI configuration
- 17-SAVA configuration
- 18-Crypto engine configuration
- 19-FIPS configuration
- 20-MACsec configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 14-ND attack defense configuration | 84.91 KB |
Contents
ND attack defense tasks at a glance
Configuring ND packet rate limit
Enabling source MAC consistency check for ND messages
Configuring IPv6 destination guard
Restrictions and guidelines: IPv6 destination guard configuration
Enabling/disabling IPv6 destination guard globally
Enabling/disabling IPv6 destination guard on an interface
Display and maintenance commands for IPv6 destination guard
Enabling SNMP notifications for ND
Configuring ND attack defense
About ND attack defense
IPv6 Neighbor Discovery (ND) attack defense is able to identify forged ND messages to prevent ND attacks.
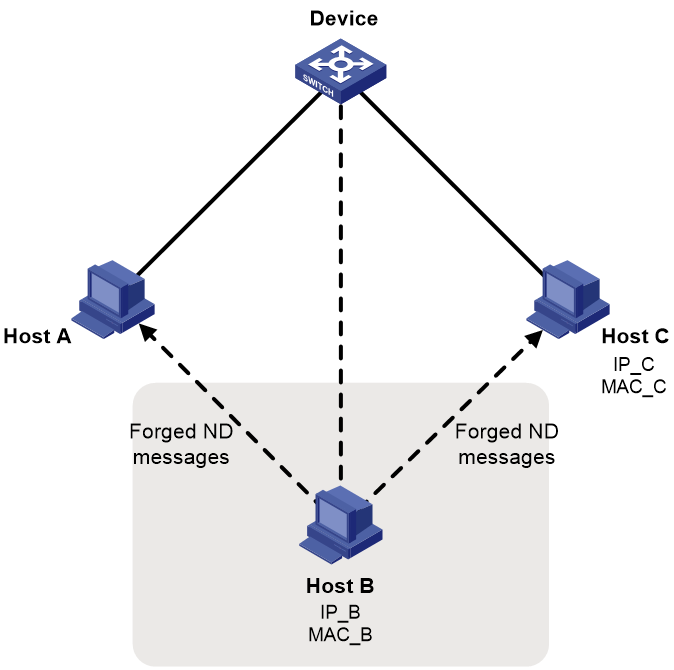
The IPv6 ND protocol does not provide any security mechanisms and is vulnerable to network attacks. As shown in Figure 1, an attacker can send the following forged ICMPv6 messages to perform ND attacks:
· Forged NS/NA/RS messages with an IPv6 address of a victim host. The gateway and other hosts update the ND entry for the victim with incorrect address information. As a result, all packets intended for the victim are sent to the attacking terminal.
· Forged RA messages with the IPv6 address of a victim gateway. As a result, all hosts attached to the victim gateway maintain incorrect IPv6 configuration parameters and ND entries.
ND attack defense tasks at a glance
All ND attack defense tasks are optional.
· Enabling source MAC consistency check for ND messages
· Configuring IPv6 destination guard
· Enabling SNMP notifications for ND
Configuring ND packet rate limit
About this task
This feature limits the receiving rate of ND packets that are to be delivered to the CPU, preventing the CPU from being overwhelmed by ND packets.
Enabled with ND attack detection, the device redirects the received ND packets to the CPU for security check. If attackers send a large number of forged ND packets to the device, the CPU will be overloaded. As a result, other features might malfunction and the device might crash. To avoid this situation, configure ND packet rate limit on ND packet receiving interfaces. When the receiving rate of ND packets on the interfaces exceeds the rate limit, the packets that exceed the limit will be discarded.
When logging for ND packet rate limit is enabled, the device sends the highest threshold-crossed ND packet rate within the sending interval in a log message to the information center. You can configure the information center module to set the log output rules. For more information about information center, see Network Management and Monitoring Configuration Guide.
Restrictions and guidelines
As a best practice, configure this feature if the device is configured with ND attack detection or ND snooping or has detected ND flood attacks.
To prevent the device from sending log messages frequently, set the log message sending interval to a high value.
On a Layer 2 aggregate interface, if you enable ND packet rate limit and the logging for this feature, the device sends log messages upon limit violations on its member ports.
Procedure
1. Enter system view.
system-view
2. (Optional.) Enable logging for ND packet rate limit.
ipv6 nd rate-limit log enable
By default, logging for ND packet rate limit is disabled.
3. (Optional.) Set the log message sending interval.
ipv6 nd rate-limit log interval interval
By default, the device sends log messages every 60 seconds.
4. Enter interface view.
interface interface-type interface-number
Supported interfaces include Layer 2 Ethernet interfaces, Layer 2 aggregate interfaces, Layer 3 Ethernet interfaces, and Layer 3 aggregate interfaces.
5. Enable ND packet rate limit.
ipv6 nd rate-limit [ pps ]
By default, ND packet rate limit is enabled.
Enabling source MAC consistency check for ND messages
About this task
The source MAC consistency check feature is typically configured on gateways to prevent ND attacks.
This feature checks the source MAC address and the source link-layer address for consistency for each arriving ND message.
· If the source MAC address and the source link-layer address are not the same, the device drops the packet.
· If the addresses are the same, the device continues learning ND entries.
The ND logging feature logs source MAC inconsistency events, and it sends the log messages to the information center. The information center can then output log messages from different source modules to different destinations. For more information about the information center, see Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enable source MAC consistency check for ND messages.
ipv6 nd mac-check enable
By default, source MAC consistency check is disabled for ND messages.
3. (Optional.) Enable the ND logging feature.
ipv6 nd check log enable
By default, the ND logging feature is disabled.
As a best practice, disable the ND logging feature to avoid excessive ND logs.
Configuring IPv6 destination guard
About IPv6 destination guard
IPv6 destination guard ensures that the device resolves IPv6 destination IP addresses only when the IP addresses have matching DHCPv6 relay entries or IP source guard bindings. The feature ensures that users can access only valid and active terminals, and reduces the number of ND entries on the device, improving device performance.
Before sending out a packet to an IPv6 address, the device performs the IPv6 destination guard as follows:
1. Searches DHCPv6 relay entries for a match based on the destination IPv6 address and packet output interface.
¡ If a match is found, the device initiates ND resolution from the output interface. If the resolution succeeds, the device sends out the packet. If the resolution fails, the device drops the packet.
¡ If no match is found, the device proceeds to the next step.
2. Searches IP source guard binding table for a match based on the destination IPv6 address and packet output interface.
¡ If a match is found, the device initiates ND resolution from the output interface. If the resolution succeeds, the device sends out the packet. If the resolution fails, the device drops the packet.
¡ If no match is found, the device does not initiate ND resolution and drops the packet.
The device enters stressed mode when the CPU or memory usage exceeds their thresholds or the number of unresolved ND entries exceeds a specific value. If the device continues resolving a large number of IPv6 addresses in stressed mode, the CPU will be overloaded and the device will crash. To reduce the workload of the device, specify the stressed keyword. In this case, IPv6 destination guard is enabled after device enters stressed mode. The device resolves only IPv6 addresses that pass the IPv6 destination guard check.
For more information about DHCPv6 relay entries, see DHCPv6 relay agent configuration in Layer 3—IP Services Configuration Guide. For more information about IP source guard entries, see "Configuring IP source guard."
Restrictions and guidelines: IPv6 destination guard configuration
You can enable IPv6 destination guard globally or on an interface.
For an interface, the interface-specific IPv6 destination guard status configuration has higher priority than the global IPv6 destination guard status.
If IPv6 destination guard is not enabled on an interface, the IPv6 destination guard status on the interface is determined by the global IPv6 destination guard status.
Enabling/disabling IPv6 destination guard globally
1. Enter system view.
system-view
2. Enable or disable IPv6 destination guard globally.
¡ Enable IPv6 destination guard globally.
ipv6 destination-guard global enable [ stressed ]
¡ Disable IPv6 destination guard globally.
undo ipv6 destination-guard global enable
By default, IPv6 destination guard is disabled globally.
Enabling/disabling IPv6 destination guard on an interface
1. Enter system view.
system-view
2. Enter system view.
interface interface-type interface-number
3. Enable or disable IPv6 destination guard on an interface.
¡ Enable IPv6 destination guard on an interface.
ipv6 destination-guard enable [ stressed ]
¡ Disable IPv6 destination guard on an interface.
ipv6 destination-guard disable
By default, the interface-specific IPv6 destination guard status is consistent with the global IPv6 destination guard status.
Display and maintenance commands for IPv6 destination guard
Execute display commands in any view.
|
Task |
Command |
|
Display IPv6 destination guard status. |
display ipv6 destination-guard [ interface interface-type interface-number ] |
Enabling SNMP notifications for ND
About this task
Enable SNMP notifications for ND as required.
· If you enable ND entry limit notifications, the device sends the current ND entry information as a notification to the SNMP module when the number of ND entries exceeds the alarm threshold.
· If you enable endpoint and local device conflict notifications, the device sends a notification to the SNMP module when an endpoint and local device conflict occurs. The notification includes the source IPv6 address, source MAC address, destination IPv6 address, and destination MAC address in the conflicting ND packet.
· If you enable rate limit notifications for sending ND Miss messages or ND packets, the device sends the highest threshold-crossed rate as a notification to the SNMP module. When the device receives an IP packet in which the destination IP address is unresolvable, it sends a ND Miss message to the CPU.
· If you enable rate limit notifications for receiving ND packets, the device sends the highest threshold-crossed rate as a notification to the SNMP module. For more information about ND packet rate limit, see "Configuring ND packet rate limit."
· If you enable user IPv6 address conflict notifications, the device sends a notification to the SNMP module when a user IPv6 address conflict occurs. The notification includes the source IPv6 and MAC addresses in the conflicting ND packet, and MAC address in the corresponding local ND entry. For more information about enabling recording user IPv6 address conflicts, see IPv6 basics configuration in Layer 3—IP Services Configuration Guide.
For ND event notifications to be sent correctly, you must also configure SNMP on the device. For more information, see SNMP configuration in Network Management and Monitoring Configuration Guide.
Software version and feature compatibility
This feature is supported only in Release 2825 and later.
Procedure
1. Enter system view.
system-view
2. Enable SNMP notifications for ND.
snmp-agent trap enable nd [ entry-limit | local-conflict | nd-miss | rate-limit | user-ip-conflict ] *
By default, SNMP notifications for ND are disabled.
If you do not specify any keywords, this command enables all SNMP notifications for ND.