- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Device management configuration | 181.79 KB |
Restrictions: Command and hardware compatibility
Device management tasks at a glance
Restrictions and guidelines for configuring the system time
System time configuration tasks at a glance
Setting the system time at the CLI
Obtaining the UTC time through a time protocol
Setting the daylight saving time
Enabling displaying the copyright statement
Disabling password recovery capability
Setting the port status detection timer
Setting memory alarm thresholds
Setting the temperature alarm thresholds
Verifying and diagnosing transceiver modules
Hardware compatibility with transceiver module verification and diagnosis
Diagnosing transceiver modules
Enabling alarm upon detection of a third-party transceiver module
Restrictions and guidelines for device reboot
Rebooting devices immediately at the CLI
Restoring the factory-default configuration
Display and maintenance commands for device management configuration
Managing the device
About device management
This chapter describes how to configure basic device parameters and manage the device.
Restrictions: Command and hardware compatibility
The WX1800H series, WX2500H series, MAK series, and WX3000H series access controllers do not support parameters or commands that are available only in IRF mode.
Device management tasks at a glance
All device management tasks are optional. You can perform any of the tasks in any order.
· Configuring basic parameters
¡ Enabling displaying the copyright statement
· Configuring security parameters
¡ Disabling password recovery capability
· Adjusting device capacities
¡ Setting the port status detection timer
· Monitoring the device
¡ Setting memory alarm thresholds
¡ Setting the temperature alarm thresholds
· Managing resources
¡ Verifying and diagnosing transceiver modules
· Maintaining the device
¡ Restoring the factory-default configuration
Configuring the device name
About this task
A device name (also called hostname) identifies a device in a network and is used in CLI view prompts. For example, if the device name is Sysname, the user view prompt is <Sysname>.
Procedure
1. Enter system view.
system-view
sysname sysname
By default, the device name is H3C.
Configuring the system time
About the system time
Correct system time is essential to network management and communication. Configure the system time correctly before you run the device on the network.
The device can use one of the following methods to obtain the system time:
· Uses the locally set system time, and then uses the clock signals generated by its built-in crystal oscillator to maintain the system time.
· Periodically obtains the UTC time from an NTP source, and uses the UTC time, time zone, and daylight saving time to calculate the system time. For more information about NTP, see System Management Configuration Guide.
The system time calculated by using the UTC time from a time source is more precise.
Restrictions and guidelines for configuring the system time
After you execute the clock protocol none command, the clock datetime command determines the system time, whether or not the time zone or daylight saving time has been configured.
If you configure or change the time zone or daylight saving time after the device obtains the system time, the device recalculates the system time. To view the system time, use the display clock command.
System time configuration tasks at a glance
To configure the system time, perform the following tasks:
1. Configuring the system time
Choose one of the following tasks:
¡ Setting the system time at the CLI
¡ Obtaining the UTC time through a time protocol
2. (Optional.) Setting the time zone
Make sure each network device uses the time zone of the place where the device resides.
3. (Optional.) Setting the daylight saving time
Make sure each network device uses the daylight saving time parameters of the place where the device resides.
Setting the system time at the CLI
1. Enter system view.
system-view
2. Configure the device to use the local system time.
clock protocol none
By default, the device uses the NTP time source.
If you execute the clock protocol command multiple times, the most recent configuration takes effect.
3. Return to user view.
quit
4. Set the local system time.
clock datetime time date
By default, the system time is UTC time 00:00:00 01/01/2011.
|
CAUTION: This command changes the system time, which affects the execution of system time-related features (for example, scheduled tasks) and collaborative operations of the device with other devices (for example, log reporting and statistics collection). Before executing this command, make sure you fully understand its impact on your live network. |
Obtaining the UTC time through a time protocol
1. Enter system view.
system-view
2. Specify the system time source.
clock protocol ntp
By default, the device uses the NTP time source.
If you execute the clock protocol command multiple times, the most recent configuration takes effect.
3. Configure time protocol parameters.
For more information about NTP configuration, see System Management Configuration Guide.
Setting the time zone
1. Enter system view.
system-view
2. Set the time zone.
clock timezone zone-name { add | minus } zone-offset
By default, the system uses the UTC time zone.
Setting the daylight saving time
1. Enter system view.
system-view
2. Set the daylight saving time.
clock summer-time name start-time start-date end-time end-date add-time
By default, the daylight saving time is not set.
Enabling displaying the copyright statement
About this task
This feature enables the device to display the copyright statement in the following situations:
· When a Telnet or SSH user logs in.
· When a console user quits user view. This is because the device automatically tries to restart the user session.
If you disable displaying the copyright statement, the device does not display the copyright statement in any situations.
Procedure
1. Enter system view.
system-view
2. Enable displaying the copyright statement.
copyright-info enable
By default, displaying the copyright statement is enabled.
Configuring banners
About this task
Banners are messages that the system displays when a user logs in.
The system supports the following banners:
· Legal banner—Appears after the copyright statement. To continue login, the user must enter Y or press Enter. To quit the process, the user must enter N. Y and N are case insensitive.
· Message of the Day (MOTD) banner—Appears after the legal banner and before the login banner.
· Login banner—Appears only when password or scheme authentication is configured.
· Shell banner—Appears before the user enters user view.
The system displays the banners in the following order: legal banner, MOTD banner, login banner, and shell banner.
Banner input methods
You can configure a banner by using one of the following methods:
· Input the entire command line in a single line.
The banner cannot contain carriage returns. The entire command line, including the command keywords, the banner, and the delimiters, can have a maximum of 511 characters. The delimiters for the banner can be any printable character but must be the same. You cannot press Enter before you input the end delimiter.
For example, you can configure the shell banner "Have a nice day." as follows:
<System> system-view
[System] header shell %Have a nice day.%
· Input the command line in multiple lines.
The banner can contain carriage returns. A carriage return is counted as two characters.
To input a banner configuration command line in multiple lines, use one of the following methods:
¡ Press Enter after the final command keyword, type the banner, and end the final line with the delimiter character %. The banner plus the delimiter can have a maximum of 1999 characters.
For example, you can configure the banner "Have a nice day." as follows:
<System> system-view
[System] header shell
Please input banner content, and quit with the character '%'.
Have a nice day.%
¡ After you type the final command keyword, type any printable character as the start delimiter for the banner and press Enter. Then, type the banner and end the final line with the same delimiter. The banner plus the end delimiter can have a maximum of 1999 characters.
For example, you can configure the banner "Have a nice day." as follows:
<System> system-view
[System] header shell A
Please input banner content, and quit with the character 'A'.
Have a nice day.A
¡ After you type the final command keyword, type the start delimiter and part of the banner. Make sure the final character of the final string is different from the start delimiter. Then, press Enter, type the rest of the banner, and end the final line with the same delimiter. The banner plus the start and end delimiters can have a maximum of 2002 characters.
For example, you can configure the banner "Have a nice day." as follows:
<System> system-view
[System] header shell AHave a nice day.
Please input banner content, and quit with the character 'A'.
A
Procedure
1. Enter system view.
system-view
2. Configure the legal banner.
header legal text
3. Configure the MOTD banner.
header motd text
4. Configure the login banner.
header login text
5. Configure the shell banner.
header shell text
Disabling password recovery capability
About this task
Password recovery capability controls console user access to the device configuration and SDRAM from BootWare menus. For more information about BootWare menus, see the release notes.
If password recovery capability is enabled, a console user can access the device configuration without authentication to configure a new password.
If password recovery capability is disabled, console users must restore the factory-default configuration before they can configure new passwords. Restoring the factory-default configuration deletes the next-startup configuration files.
To enhance system security, disable password recovery capability.
Procedure
1. Enter system view.
system-view
2. Disable password recovery capability.
undo password-recovery enable
By default, password recovery capability is enabled.
Setting the port status detection timer
About this task
The device starts a port status detection timer when a port is shut down by a protocol. Once the timer expires, the device brings up the port so the port status reflects the port's physical status.
Procedure
1. Enter system view.
system-view
2. Set the port status detection timer.
shutdown-interval time
The default setting is 30 seconds.
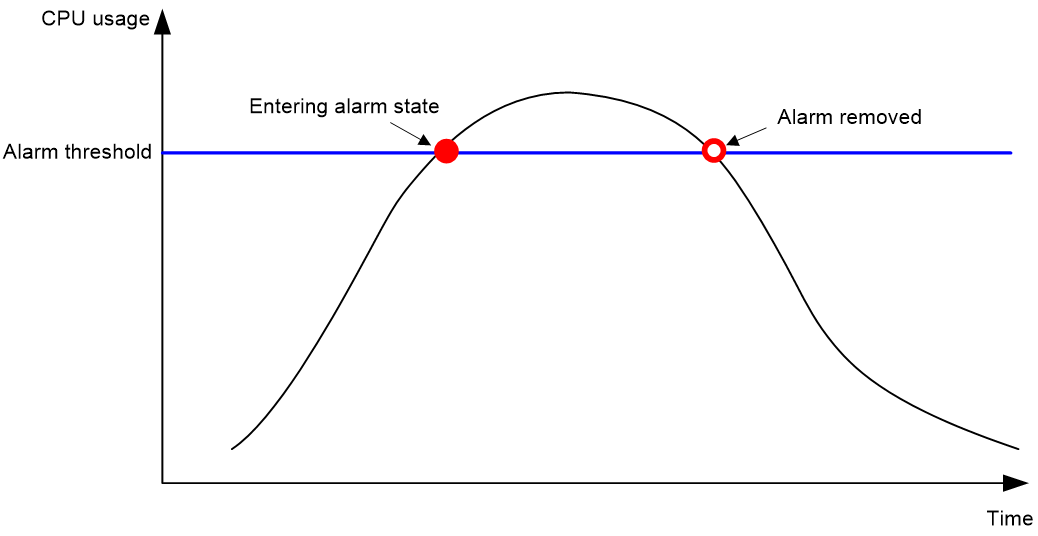
Monitoring CPU usage
About this task
To monitor CPU usage, the device performs the following operations:
· Samples CPU usage at 1-minute intervals and compares the samples with the CPU usage threshold and the CPU usage recovery threshold.
¡ If a sample is greater than or equal to the CPU usage threshold, the device determines the CPU usage is high and sends traps to affected service modules and processes.
¡ If a sample decreases to or below the CPU usage recovery threshold, the device determines the CPU usage has recovered and sends traps to affected service modules and processes.
· Samples and saves CPU usage at a configurable interval if CPU usage tracking is enabled. You can use the display cpu-usage history command to display the historical CPU usage statistics in a coordinate system.
Figure 1 CPU alarms and alarm-removed notifications
Procedure
1. Enter system view.
system-view
2. Set the CPU usage alarm thresholds.
In standalone mode:
monitor cpu-usage threshold severe-threshold
In IRF mode:
monitor cpu-usage threshold severe-threshold [ slot slot-number ]
By default, the CPU usage alarm threshold is 99%.
|
CAUTION: If you set the severe CPU usage alarm threshold to a too low value, the device will reach the threshold easily. Normal services will be affected. |
3. Set the sampling interval for CPU usage tracking.
In standalone mode:
monitor cpu-usage interval interval
In IRF mode:
monitor cpu-usage interval interval [ slot slot-number ]
By default, the sampling interval for CPU usage tracking is 1 minute.
4. Enable CPU usage tracking.
In standalone mode:
monitor cpu-usage enable
In IRF mode:
monitor cpu-usage enable [ slot slot-number ]
By default, CPU usage tracking is enabled.
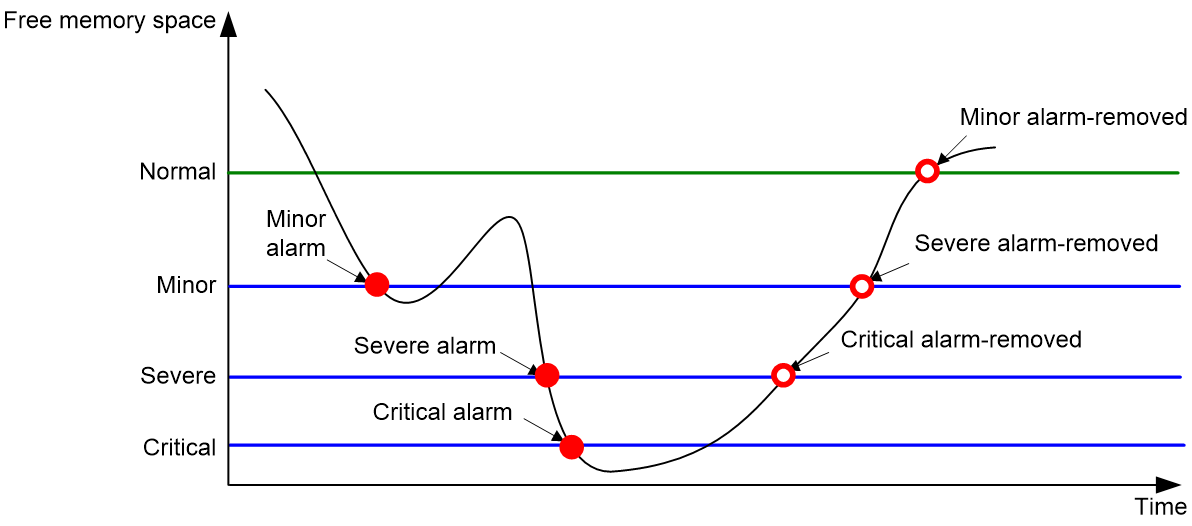
Setting memory alarm thresholds
About this task
To ensure correct operation and improve memory efficiency, the system monitors the amount of free memory space in real time. If the amount of free memory space reaches the minor, severe, or critical alarm threshold, the system issues an alarm to affected service modules and processes.
As shown in Table 1 and Figure 2, the system supports the following free-memory thresholds:
· Normal state threshold.
· Minor alarm threshold.
· Severe alarm threshold.
· Critical alarm threshold.
Table 1 Memory alarm notifications and memory alarm-removed notifications
|
Notification |
Triggering condition |
Remarks |
|
Minor alarm notification |
The amount of free memory space decreases below the minor alarm threshold. |
After generating and sending a minor alarm notification, the system does not generate and send any additional minor alarm notifications until the minor alarm is removed. |
|
Severe alarm notification |
The amount of free memory space decreases below the severe alarm threshold. |
After generating and sending a severe alarm notification, the system does not generate and send any additional severe alarm notifications until the severe alarm is removed. |
|
Critical alarm notification |
The amount of free memory space decreases below the critical alarm threshold. |
After generating and sending a critical alarm notification, the system does not generate and send any additional critical alarm notifications until the critical alarm is removed. |
|
Critical alarm-removed notification |
The amount of free memory space increases above the severe alarm threshold. |
N/A |
|
Severe alarm-removed notification |
The amount of free memory space increases above the minor alarm threshold. |
N/A |
|
Minor alarm-removed notification |
The amount of free memory space increases above the normal state threshold. |
N/A |
Figure 2 Memory alarm notifications and alarm-removed notifications
Procedure
1. Enter system view.
system-view
2. Set the memory usage threshold.
In standalone mode:
memory-threshold usage memory-threshold
In IRF mode:
memory-threshold [ slot slot-number ] usage memory-threshold
By default, the memory usage threshold is 100%.
3. Set the free-memory thresholds.
In standalone mode:
memory-threshold minor minor-value severe severe-value critical critical-value normal normal-value
In IRF mode:
memory-threshold [ slot slot-number ] minor minor-value severe severe-value critical critical-value normal normal-value
The default settings vary by device model. To view the default settings, use the undo memory-threshold command to restore the default settings and then execute the display memory-threshold command.
Setting the temperature alarm thresholds
About this task
The device monitors its temperature based on the following thresholds:
· Low-temperature threshold.
· High-temperature warning threshold.
· High-temperature alarming threshold.
When the device temperature drops below the low-temperature threshold or reaches the high-temperature warning or alarming threshold, the device performs the following operations:
· Sends log messages and traps.
· Sets LEDs on the device panel.
Procedure
1. Enter system view.
system-view
2. Configure the temperature alarm thresholds.
In standalone mode:
temperature-limit { hotspot | inflow } sensor-number lowlimit warninglimit [ alarmlimit ]
In IRF mode:
temperature-limit slot slot-number { hotspot | inflow } sensor-number lowlimit warninglimit [ alarmlimit ]
The defaults vary by temperature sensor model. To view the defaults, execute the undo temperature-limit and display environment commands in turn.
The high-temperature alarming threshold must be higher than the high-temperature warning threshold, and the high-temperature warning threshold must be higher than the low-temperature threshold.
Verifying and diagnosing transceiver modules
Hardware compatibility with transceiver module verification and diagnosis
|
Hardware series |
Model |
Product code |
Feature compatibility |
|
WX1800H series |
WX1804H |
EWP-WX1804H-PWR-CN |
No |
|
WX2500H series |
WX2508H-PWR-LTE WX2510H WX2510H-F WX2540H WX2540H-F WX2560H |
EWP-WX2508H-PWR-LTE EWP-WX2510H-PWR EWP-WX2510H-F-PWR EWP-WX2540H EWP-WX2540H-F EWP-WX2560H |
Yes: · WX2540H · WX2560H No: · WX2508H-PWR-LTE · WX2510H · WX2510H-F · WX2540H-F |
|
MAK series |
MAK204 MAK206 |
EWP-MAK204 EWP-MAK206 |
Yes |
|
WX3000H series |
WX3010H WX3010H-X WX3010H-L WX3024H WX3024H-L WX3024H-F |
EWP-WX3010H EWP-WX3010H-X-PWR EWP-WX3010H-L-PWR EWP-WX3024H EWP-WX3024H-L-PWR EWP-WX3024H-F |
Yes |
|
WX3500H series |
WX3508H WX3510H WX3520H WX3520H-F WX3540H |
EWP-WX3508H EWP-WX3510H EWP-WX3520H EWP-WX3520H-F EWP-WX3540H |
Yes |
|
WX5500E series |
WX5510E WX5540E |
EWP-WX5510E EWP-WX5540E |
Yes |
|
WX5500H series |
WX5540H WX5560H WX5580H |
EWP-WX5540H EWP-WX5560H EWP-WX5580H |
Yes |
|
Access controller modules |
LSUM1WCME0 EWPXM1WCME0 LSQM1WCMX20 LSUM1WCMX20RT LSQM1WCMX40 LSUM1WCMX40RT EWPXM2WCMD0F EWPXM1MAC0F |
LSUM1WCME0 EWPXM1WCME0 LSQM1WCMX20 LSUM1WCMX20RT LSQM1WCMX40 LSUM1WCMX40RT EWPXM2WCMD0F EWPXM1MAC0F |
No |
|
Hardware series |
Model |
Product code |
Feature compatibility |
|
WX1800H series |
WX1804H WX1810H WX1820H WX1840H |
EWP-WX1804H-PWR EWP-WX1810H-PWR EWP-WX1820H EWP-WX1840H-GL |
Yes: WX1840H No: · WX1804H · WX1810H · WX1820H |
|
WX3800H series |
WX3820H WX3840H |
EWP-WX3820H-GL EWP-WX3840H-GL |
Yes |
|
WX5800H series |
WX5860H |
EWP-WX5860H-GL |
Yes |
Verifying transceiver modules
About this task
You can use one of the following methods to verify the genuineness of a transceiver module:
· Display the key parameters of a transceiver module, including its transceiver type, connector type, central wavelength of the transmit laser, transfer distance, and vendor name.
· Display its electronic label. The electronic label is a profile of the transceiver module and contains the permanent configuration, including the serial number, manufacturing date, and vendor name. The data was written to the transceiver module or the device's storage component during debugging or testing of the transceiver module or device.
The device regularly checks transceiver modules for their vendor names. If a transceiver module does not have a vendor name or the vendor name is not H3C, the device repeatedly outputs traps and log messages. For information about logging rules, see information center in System Management Configuration Guide.
Procedure
To verify transceiver modules, execute the following commands in any view:
· Display the key parameters of transceiver modules.
display transceiver interface [ interface-type interface-number ]
· Display the electrical label information of transceiver modules.
display transceiver manuinfo interface [ interface-type interface-number ]
Diagnosing transceiver modules
About this task
The device provides the alarm and digital diagnosis functions for transceiver modules. When a transceiver module fails or is not operating correctly, you can perform the following tasks:
· Check the alarms that exist on the transceiver module to identify the fault source.
· Examine the key parameters monitored by the digital diagnosis function, including the temperature, voltage, laser bias current, TX power, and RX power.
Procedure
To diagnose transceiver modules, execute the following commands in any view:
· Display transceiver alarms.
display transceiver alarm interface [ interface-type interface-number ]
· Display the current values of the digital diagnosis parameters on transceiver modules.
display transceiver diagnosis interface [ interface-type interface-number ]
Enabling alarm upon detection of a third-party transceiver module
About this task
Upon installation of a transceiver module, the system reads vendor information from it to determine whether it is a third-party transceiver module. If it is a third-party module, the device sends a notification and a log message to notify the user of replacing it with an H3C transceiver module. You can use display transceiver manuinfo to obtain vendor information for a transceiver module.
Procedure
1. Enter system view.
system-view
2. Enable alarm upon detection of a third-party transceiver module.
transceiver third-party alarm enable
By default, alarm is enabled upon detection of a third-party transceiver module.
Scheduling a task
About task scheduling
You can schedule the device to automatically execute a command or a set of commands without administrative interference.
You can configure a periodic schedule or a non-periodic schedule. A non-periodic schedule is not saved to the configuration file and is lost when the device reboots. A periodic schedule is saved to the startup configuration file and is automatically executed periodically.
Restrictions and guidelines
· To assign a command (command A) to a job, you must first assign the job the command or commands for entering the view of command A.
· Make sure all commands in a schedule are compliant to the command syntax. The system does not check the syntax when you assign a command to a job.
· A schedule cannot contain any one of these commands: telnet, ftp, ssh2, and monitor process.
· A schedule does not support user interaction. If a command requires a yes or no answer, the system always assumes that a Y or Yes is entered. If a command requires a character string input, the system assumes that either the default character string (if any) or a null string is entered.
· A schedule is executed in the background, and no output (except for logs, traps, and debug information) is displayed for the schedule.
Procedure
1. Enter system view.
system-view
2. Create a job.
scheduler job job-name
3. Assign a command to the job.
command id command
By default, no command is assigned to a job.
You can assign multiple commands to a job. A command with a smaller ID is executed first.
4. Exit to system view.
quit
5. Create a schedule.
scheduler schedule schedule-name
6. Assign a job to the schedule.
job job-name
By default, no job is assigned to a schedule.
You can assign multiple jobs to a schedule. The jobs will be executed concurrently.
7. Assign user roles to the schedule.
user-role role-name
By default, a schedule has the user role of the schedule creator.
You can assign a maximum of 64 user roles to a schedule. A command in a schedule can be executed if it is permitted by one or more user roles of the schedule.
8. Specify the execution time for the schedule.
Choose one option as needed:
¡ Execute the schedule at specific points of time.
time at time date
time once at time [ month-date month-day | week-day week-day&<1-7> ]
¡ Execute the schedule after a period of time.
time once delay time
¡ Execute the schedule at the specified time on every specified day in a month or week.
time repeating at time [ month-date [ month-day | last ] | week-day week-day&<1-7> ]
¡ Execute the schedule periodically from the specified time on.
time repeating [ at time [date ] ] interval interval
By default, no execution time is specified for a schedule.
The time commands overwrite each other. The most recently executed command takes effect.
Example: Scheduling a task
Network configuration
As shown in Figure 3, the client needs to access the AC. The AP is connected to the AC through the switch. The AC acts as the DHCP server to assign IP addresses to the AP and client.
To save energy, configure the AC to perform the following operations:
· Enable the interface connected to the AP (Radio 1) at 8:00 a.m. every day.
· Disable the interface connected to the AP (Radio 1) at 20:00 every day.
Procedure
# Configure wireless access on the AC. For more information, see WLAN access configuration in WLAN Access Configuration Guide.
# Enter system view.
<AC> system-view
# Configure a job for disabling the interface.
[AC] scheduler job radio_disable
[AC-job-radio_disable] command 1 system-view
[AC-job-radio_disable] command 2 wlan ap ap1 model WA6320
[AC-job-radio_disable] command 3 radio 1
[AC-job-radio_disable] command 4 radio disable
[AC-job-radio_disable] quit
# Configure a periodic schedule for disabling the interface at 20:00 every day.
[AC] scheduler schedule stop_radio
[AC-schedule-stop_radio] job radio_disable
[AC-schedule-stop_radio] time repeating at 20:00
[AC-schedule-stop_radio] quit
# Configure a job for enabling the interface.
[AC] scheduler job radio_enable
[AC-job-radio_enable] command 1 system-view
[AC-job-radio_enable] command 2 wlan ap ap1 model WA6320
[AC-job-radio_enable] command 3 radio 1
[AC-job-radio_enable] command 4 radio enable
[AC-job-radio_enable] quit
# Configure a periodic schedule for enabling the interface at 8:00 a.m. every day.
[AC] scheduler schedule start_radio
[AC-schedule-start_radio] job radio_enable
[AC-schedule-start_radio] time repeating at 8:00
[AC-schedule-start_radio] quit
Verifying the configuration
# On the AC, display detailed information about AP1. Verify that the value of the Admin State field is UP between 8:00 and 20:00 and is DOWN at any other time.
[AC] display wlan ap name ap1 verbose
AP name : ap1
AP ID : 1
AP group name : default-group
State : Run
Backup Type : NULL
Online time : 0 days 2 hours 18 minutes 10 seconds
System up time : 0 days 2 hours 19 minutes 11 seconds
Model : WA6320
Region code : CN
Region code lock : Disable
Serial ID : 210235A1BSC123000050
MAC address : 586a-b1fb-e2c0
IP address : 100.1.0.1
H/W version : Ver.C
S/W version : V700R001B64D003
Boot version : 7.01
Description : Not configured
Priority : 4
Echo interval : 10 seconds
Statistics report interval : 50 seconds
Jumbo frame value : 1500
MAC type : Local MAC & Split MAC
Tunnel mode : Local Bridging & 802.3 Frame & Native Frame
Discovery type : Unknown
Retransmission count : 3
Retransmission interval : 5 seconds
Firmware upgrade : Enabled
Sent control packets : 3159
Received control packets : 3159
Connection count : 1
Backup Ipv4 : Not configured
Backup Ipv6 : Not configured
Tunnel encryption : Disabled
LED mode : Normal
Radio 1:
Basic BSSID : 586a-b1fb-e2c0
Admin state : Up
Radio type : 802.11ax
Antenna type : internal
Client dot11ac-only : Disabled
Client dot11n-only : Disabled
Channel band-width : 20/40/80MHz
Operating bandwidth : 20/40/80MHz
Secondary channel mode : SCA
Short GI for 20MHz : Supported
Short GI for 40MHz : Supported
Short GI for 80MHz : Supported
Short GI for 160MHz : Not supported
MIMO : Not Config
Green-Energy-Management : Disabled
A-MSDU : Enabled
A-MPDU : Enabled
LDPC : Not Supported
STBC : Supported
Operational VHT-MCS Set:
Mandatory : Not configured
Supported : NSS1 0,1,2,3,4,5,6,7,8,9
NSS2 0,1,2,3,4,5,6,7,8,9
Multicast : Not configured
Operational HT MCS Set:
Mandatory : Not configured
Supported : 0, 1, 2, 3, 4, 5, 6, 7, 8, 9,
10, 11, 12, 13, 14, 15
Multicast : Not configured
Channel : 149
Max power : 20 dBm
Operational rate:
Mandatory : 6, 12, 24 Mbps
Multicast : Auto
Supported : 9, 18, 36, 48, 54 Mbps
Disabled : Not configured
Distance : 1 km
ANI : Enabled
Fragmentation threshold : 2346 bytes
Beacon interval : 100 TU
Protection threshold : 2346 bytes
Long retry threshold : 4
Short retry threshold : 7
Maximum rx duration : 2000 ms
Noise floor : -102 dBm
Rebooting the device
About device reboot
The following device reboot methods are available:
· Schedule a reboot at the CLI, so the device automatically reboots at the specified time or after the specified period of time.
· Immediately reboot the device at the CLI.
During the reboot process, the device performs the following operations:
a. Resets all of its chips.
b. Uses the BootWare to verify the startup software package, decompress the package, and load the images.
c. Initializes the system.
· Power off and then power on the device. This method might cause data loss, and is the least-preferred method.
Using the CLI, you can reboot the device from a remote host.
Restrictions and guidelines for device reboot
A device reboot might result in a service outage.
For data security, the device does not reboot while it is performing file operations.
Rebooting devices immediately at the CLI
Prerequisites
Perform the following steps in any view:
1. Verify that the next-startup configuration file is correctly specified.
display startup
For more information about the display startup command, see Fundamentals Command Reference.
2. Verify that the startup image files are correctly specified.
display boot-loader
If one main startup image file is damaged or does not exist, you must specify another main startup image file before rebooting the device.
For more information about the display boot-loader command, see Fundamentals Command Reference.
3. Save the running configuration to the next-startup configuration file.
save
To avoid configuration loss, save the running configuration before a reboot.
For more information about the save command, see Fundamentals Command Reference.
Procedure
To reboot the device immediately at the CLI, execute one of the following commands in user view:
In standalone mode:
reboot [ force ]
In IRF mode:
reboot [ slot slot-number ] [ force ]
|
CAUTION: · A device reboot might result in service interruption. Before configuring this command, make sure you fully understand its impact on your live network. · Use the force keyword to reboot the device only when the system is faulty or fails to start up normally. A forced device reboots might cause file system damage. Before using the force keyword to reboot the device, make sure you understand its impact. |
Scheduling a device reboot
Restrictions and guidelines
(In IRF mode.) The automatic reboot configuration takes effect on all member devices. It will be canceled if a master/subordinate switchover occurs.
The device supports only one device reboot schedule. If you execute the scheduler reboot command multiple times, the most recent configuration takes effect.
Procedure
To schedule a reboot, execute one of the following commands in user view:
· scheduler reboot at time [ date ]
· scheduler reboot delay time
By default, no device reboot time is specified.
|
CAUTION: This command enables the device to reboot at a scheduled time, which causes service interruption. Before configuring this command, make sure you fully understand its impact on your live network. |
Restoring the factory-default configuration
About this task
If you want to use the device in a different scenario or you cannot troubleshoot the device by using other methods, use this task to restore the factory-default configuration.
This task does not delete the following items:
· .bin files and license files.
· Directory apimge on the WX1800H series, WX2500H series, MAK series, and WX3000H series.
Restrictions and guidelines
This feature is disruptive.
Procedure
1. Execute the following command in user view to restore the factory-default configuration for the device:
restore factory-default
|
CAUTION: This command restores the device to the factory default settings. Before configuring this command, make sure you fully understand its impact on your live network. |
2. Reboot the device.
reboot
When the command prompts you to choose whether to save the running configuration, enter N. If you choose to save the running configuration, the device loads the saved configuration at startup.
Display and maintenance commands for device management configuration
|
IMPORTANT: The access controller modules do not support parameters or commands that are available only in IRF mode. |
Execute display commands in any view. Execute the reset scheduler logfile command in user view. Execute the reset version-update-record command in system view.
|
Task |
Command |
|
Display the system time, date, time zone, and daylight saving time. |
display clock |
|
Display the copyright statement. |
display copyright |
|
Display CPU usage statistics. |
In standalone mode: display cpu-usage [ summary ] display cpu-usage [ control-plane | data-plane ] [ summary ] In IRF mode: display cpu-usage [ summary ] [ slot slot-number ] display cpu-usage [ control-plane | data-plane ] [ summary ] [ slot slot-number ] |
|
Display CPU usage monitoring settings. |
In standalone mode: display cpu-usage configuration In IRF mode: display cpu-usage configuration [ slot slot-number ] |
|
Display the historical CPU usage statistics in a coordinate system. |
In standalone mode: display cpu-usage history [ job job-id ] In IRF mode: display cpu-usage history [ job job-id ] [ slot slot-number ] |
|
Display hardware information. |
In standalone mode: display device [ cf-card ] [ verbose ] In IRF mode: display device [ cf-card ] [ slot slot-number | verbose ] |
|
Display electronic label information for the device. |
In standalone mode: display device manuinfo In IRF mode: display device manuinfo [ slot slot-number ] |
|
Display or save operating information for features and hardware modules. |
display diagnostic-information [ hardware | infrastructure | l2 | l3 | service ] [ key-info ] [ filename ] |
|
Display device temperature information. |
In standalone mode: display environment In IRF mode: display environment [ slot slot-number ] |
|
Display the operating states of fan trays. |
In standalone mode: display fan [ fan-id ] In IRF mode: display fan [ slot slot-number [ fan-id ] ] |
|
Display memory usage statistics. |
In standalone mode: display memory [ summary ] In IRF mode: display memory [ summary ] [ slot slot-number ] |
|
Display memory alarm thresholds and statistics. |
In standalone mode: display memory-threshold In IRF mode: display memory-threshold [ slot slot-number ] |
|
Display power supply information. |
In standalone mode: display power [ power-id ] In IRF mode: display power [ slot slot-number [ power-id ] ] |
|
Display job configuration information. |
display scheduler job [ job-name ] |
|
Display job execution log information. |
display scheduler logfile |
|
Display the automatic reboot schedule. |
display scheduler reboot |
|
Display schedule information. |
display scheduler schedule [ schedule-name ] |
|
Display system stability and status information. |
display system stable state |
|
Display system version information. |
display version |
|
Display startup software image upgrade records. |
display version-update-record |
|
Clear job execution log information. |
reset scheduler logfile |
|
Clear startup software image upgrade records. |
reset version-update-record |