- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 06-Anti-virus configuration | 166.86 KB |
Virus signature library management
Restrictions and guidelines: Anti-virus
Configuring an anti-virus policy
Configuring MD5 value-based anti-virus cloud query
Specifying a parameter profile for an anti-virus action
Applying an anti-virus policy to a DPI application profile
Activating anti-virus policy settings
Applying a DPI application profile to a virtual server
Managing the virus signature library
Scheduling automatic virus signature library update
Triggering an immediate automatic virus signature library update
Manually updating the virus signature library
Rolling back the virus signature library
Display and maintenance commands for anti-virus
Anti-virus configuration examples
Example: Using the default anti-virus policy in a virtual server
Configuring anti-virus
About anti-virus
Anti-virus identifies viruses in the application layer of packets based on an up-to-date virus signature library and takes actions to prevent a network from being infected. This feature is typically deployed on a gateway to insulate the internal network from viruses and protect the internal data.
Anti-virus supports inspecting packets transported through FTP, HTTP, IMAP, NFS, POP3, SMB, and SMTP.
Application scenario
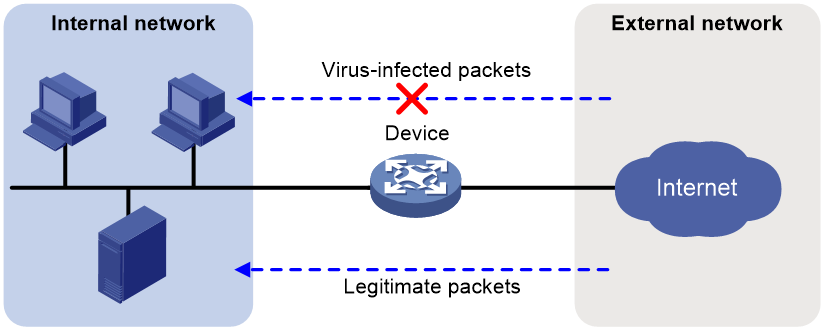
As shown in Figure 1, the device is the gateway of an internal network. Internal users access the external network and download data from the external network. The internal server accepts data uploaded by external users.
In this scenario, you can configure anti-virus on the gateway to protect the internal network. Anti-virus inspects incoming packets, permits legitimate packets to pass, and takes actions, such as alert, block, or redirect, on packets containing viruses.
Figure 1 Anti-virus application scenario
Terminology
Virus signature
A virus signature is a character string that uniquely identifies a specific virus. The virus signature library contains the predefined virus signatures.
MD5 rules
An MD5 rule is generated by the system based on the virus signatures in the virus signature library to identify virus-infected files.
Signature exception
Typically, anti-virus takes anti-virus actions on packets matching virus signatures. If a virus proves to be a false alarm, you can set the virus signature as a signature exception. Packets matching the signature exception are permitted to pass.
Application exception
Typically, anti-virus action is protocol specific and applies to all applications carried by the protocol. To take a different action on an application, you can set the application as an exception and specify a different anti-virus action for the application. Application exceptions use application-specific actions and the other applications use protocol-specific actions. For example, the anti-virus action for HTTP is alert. To block the games carried by HTTP, you can set the games as application exceptions and specify the block action for them.
MD5 exception
If false positives occur for a virus, you can set the MD5 value of the virus as an MD5 exception. The device will permit subsequent packets matching the MD5 exception to pass.
You can get the MD5 value of the virus through the threat log.
Anti-virus action
Anti-virus actions apply to the packets that match virus signatures. The actions include the following types:
· alert—Permits matching packets and generates logs.
· block—Blocks matching packets and generates logs.
· redirect—Redirects matching HTTP connections to a URL and generates logs. The redirection is applicable to only uploading connections.
The generated anti-virus logs can be sent to the device information center or to designated recipients by email.
Virus detection methods
The device supports the following virus detection methods:
· Virus signature-based detection—The device matches packets against virus signatures in the virus signature library, and determines that a packet contains viruses if a match is found.
· MD5 rule-based detection—The device generates an MD5 hash value for a file to be inspected and compares the value with the system-defined MD5 rules. If a match is found, the file is identified to be virus-infected.
Anti-virus mechanism
Anti-virus takes effect after you apply an anti-virus policy to a DPI application profile and use the DPI application profile in a virtual server.
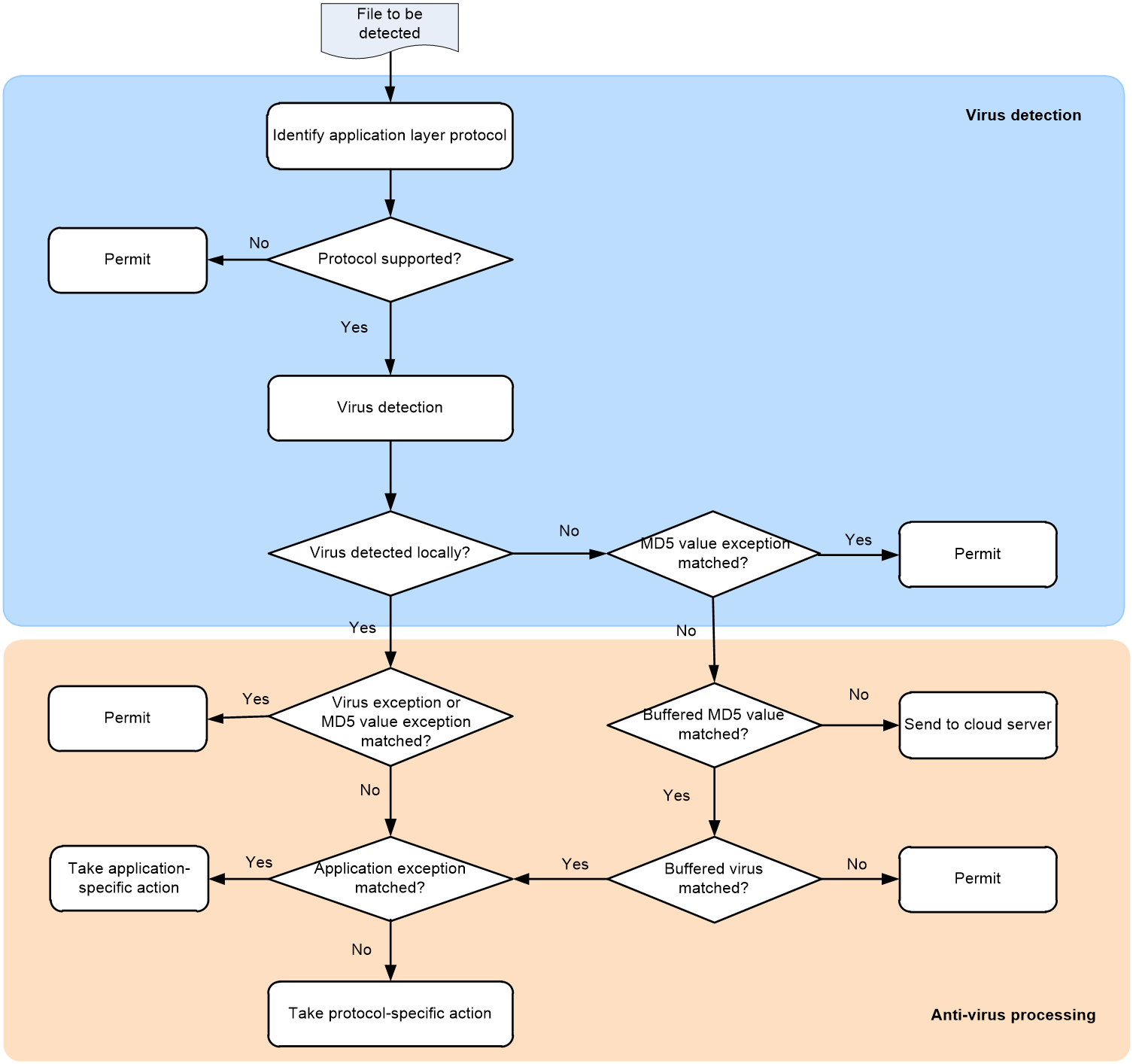
As shown in Figure 2, upon receiving a packet, the anti-virus device performs the following operations:
1. The device identifies whether the anti-virus supports the application layer protocol of the packet.
¡ If not, the device permits the packet to pass without virus detection.
¡ If yes, the device compares the packet with the virus signatures and MD5 rules.
2. If a matching signature or MD5 rule is found, the device determines if the matching signature is an exception.
¡ If yes, the device permits the packet to pass.
¡ If not, the device examines whether the application is an exception.
- If the application is an exception, the device takes the application-specific action (alert, block, or permit).
- If the application is not an exception, the device takes the protocol-specific action (alert, block, or redirect).
3. If no matching signature or MD5 rule is found, the device examines whether the MD5 value of the file in the packet matches an MD5 value exception.
¡ If yes, the device permits the packet to pass.
¡ If not, the device examines whether the MD5 value of the file in the packet matches a buffered MD5 value in the anti-virus buffer.
- If a buffered MD5 value labeled as virus is found, the device determines if the application is an exception. If yes, the device takes the application-specific action (alert, block, or permit). If not, the device takes the protocol-specific action (alert, block, or redirect).
- If a buffered MD5 value labeled as non-virus is found, the device permits the packet to pass.
- If no buffered MD5 value is found, the device sends the MD5 value of the file to the cloud server for future virus detection.
After the virus detection, the device saves the detection results returned from the cloud server to the anti-virus buffer so the virus detection for subsequent packets can be performed locally.
Virus signature library management
The device inspects packets for viruses based on the virus signature library. You can update the virus signature library to the latest version or roll it back to the previous version or the factory default version.
Updating the virus signature library
The following methods are available for updating the virus signature library:
· Automatic update.
The device automatically and periodically downloads the most up-to-date virus signature file to update the signature library.
· Triggered update.
The device downloads the most up-to-date virus signature file to update the signature library immediately after you trigger the operation.
· Manual update.
Use this method when the device cannot obtain the virus signature file automatically.
You must manually download the most up-to-date virus signature file and then use the downloaded file to update the signature library.
Rolling back the virus signature library
If the false alarm rate is high or abnormal situations frequently occur, you can roll back the virus signature library to the previous version or to the factory default version.
Licensing requirements
Before using the anti-virus feature, purchase and correctly install a license on the device. If the license expires, the anti-virus feature is still available but you can no longer update the virus signature library or perform MD5 value cloud query. For more information about licenses, see Fundamentals Configuration Guide.
Restrictions and guidelines: Anti-virus
Anti-virus supports inspecting packets transported through FTP, HTTP, IMAP, NFS, POP3, SMB, and SMTP.
Anti-virus tasks at a glance
To configure anti-virus, perform the following tasks:
1. Configuring an anti-virus policy
2. Configuring MD5 value-based anti-virus cloud query
3. Specifying a parameter profile for an anti-virus action
4. Applying an anti-virus policy to a DPI application profile
5. (Optional.) Activating anti-virus policy settings
6. Applying a DPI application profile to a virtual server
7. Managing the virus signature library
Configuring an anti-virus policy
About this task
An anti-virus policy defines the virus detection criteria, anti-virus actions, virus signature exceptions, and application exceptions.
The virus signatures in the virus signature library are available to all anti-virus policies on the device.
The device supports sending the alarm message defined in the warning parameter profile applied to the policy. If an endpoint user visits a virus-infected website, the device will display the alarm message on the user's browser. For more information about configuring a warning parameter profile, see "Configuring DPI engine."
Restrictions and guidelines
Anti-virus supports only NFSv3 of the NFS protocol, and SMBv1 and SMBv2 of the SMB protocol.
The logging keyword enables the anti-virus module to log the packet matching events and send log messages to the information center.
With the information center, you can set log message filtering and output rules, including output destinations.
The information center can output anti-virus logs to any destinations except the console and the monitor terminal. If you configure the console or monitor terminal as an output destination, the output destination setting will not take effect.
To view anti-virus logs stored on the device, use the display logbuffer command. Make sure you do not disable log output to the log buffer, which is enabled by default.
For more information about configuring the information center, see Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Create an anti-virus policy and enter its view.
anti-virus policy policy-name
A default anti-virus policy named default exists. The default anti-virus policy cannot be modified or deleted.
3. (Optional.) Configure a description for the anti-virus policy.
description text
4. Configure anti-virus for an application layer protocol.
inspect { ftp | http | imap | nfs | pop3 | smb | smtp } direction { both | download | upload } [ cache-file-size file-size ] action { alert | block | redirect }
By default, the device performs virus detection on upload and download packets for FTP, HTTP, IMAP, NFS, and SMB, on download packets for POP3, and on upload packets for SMTP. The anti-virus action for FTP, HTTP, NFS, and SMB is block and for IMAP, SMTP, and POP3 is alert. The maximum size for the file that can be cached for virus detection is 1 MB. The direction keyword is not available for the POP3 and SMTP protocols because the POP3 protocol supports only the download direction and the SMTP protocol supports only the upload direction.
5. (Optional.) Apply a warning parameter profile to an anti-virus policy and enable sending the alarm message defined in the profile.
warning parameter-profile profile-name
By default, no warning parameter profile is applied and the device does not support the sending of alarm messages.
The alarm message sending takes effect only when the HTTP protocol and the block action are configured for virus detection.
6. (Optional.) Set a signature as a signature exception.
exception signature signature-id
7. (Optional.) Set an application as an application exception and specify an anti-virus action for the application exception.
exception application application-name action { alert | block | permit }
8. (Optional.) Set an MD5 value as an MD5 exception.
exception md5 md5-value
9. Enable the virus signatures at and above a severity level.
signature severity { critical | high | medium } enable
By default, virus signatures of all severity levels are enabled.
Configuring MD5 value-based anti-virus cloud query
About this task
You can enable MD5 value-based anti-virus cloud query in an anti-virus policy. If no virus is found in the file, the device will send the MD5 value of the file to the cloud server for cloud query. The cloud server determines whether the MD5 value is a virus and returns the result to the device so appropriate action can be taken. The anti-virus module will save the result returned from the cloud server to the anti-virus buffer so the virus detection for subsequent packets can be performed locally.
For more information about the cloud query server, see "Configuring DPI engine."
Restrictions and guidelines
MD5 value-based anti-virus cloud query is available only for the following protocols:
· HTTP.
· IMAP.
· NFS. Only the NFS read operation is supported.
· POP3.
· SMTP.
Procedure
1. Enter system view.
system-view
2. Specify the cloud query server.
inspect cloud-server host-name
By default, cloud query server sec.h3c.com is used.
3. (Optional.) Set the anti-virus cache size.
anti-virus cache size cache-size
By default, the anti-virus cache can cache a maximum of 100000 entries.
4. (Optional.) Set the minimum cache period for an anti-virus MD5 entry.
anti-virus cache min-time value
By default, the minimum cache period of an anti-virus MD5 entry is 10 minutes.
5. Enter anti-virus policy view.
anti-virus policy policy-name
6. Enable MD5 value-based anti-virus cloud query.
cloud-query enable
By default, MD5 value-based anti-virus cloud query is disabled.
Specifying a parameter profile for an anti-virus action
About this task
Before you can specify a parameter profile for an anti-virus action, configure the parameter profile in the DPI engine. For more information, see "Configuring DPI engine."
A parameter profile defines the parameters for executing an action. For example, you can configure parameters such as the email server address and email recipients in the email parameter profile, and then apply the profile to the email action.
If no parameter profile is specified for an anti-virus action, or if the specified parameter profile does not exist, the default parameter settings of the action are used.
Procedure
1. Enter system view.
system-view
2. Specify a parameter profile for an anti-virus action.
anti-virus { email | logging | redirect } parameter-profile profile-name
By default, no parameter profile is specified for an anti-virus action.
Applying an anti-virus policy to a DPI application profile
About this task
The DPI application profile is a template for configuring DPI security services. For an anti-virus policy to take effect, you must apply it to a DPI application profile.
A DPI application profile can use only one anti-virus policy. If you apply different anti-virus policies to the same DPI application profile, only the most recent configuration takes effect.
Procedure
1. Enter system view.
system-view
2. Enter DPI application profile view.
app-profile profile-name
For more information about this command, see DPI engine commands in DPI Command Reference.
3. Apply an anti-virus policy to the DPI application profile.
anti-virus apply policy policy-name mode { alert | protect }
By default, no anti-virus policy is applied to a DPI application profile.
Activating anti-virus policy settings
About this task
By default, the system will detect whether another configuration change (such as creation, modification, or deletion) occurs within a 20-second interval after a change to the anti-virus policy and rule settings:
· If no configuration change occurs within the interval, the system performs an activation operation at the end of the next interval (40 seconds later) to make the configuration take effect.
· If a configuration change occurs within the interval, the system continues to periodically check whether a configuration change occurs within the interval.
To activate the policy and rule configurations immediately, you can execute the inspect activate command.
Procedure
1. Enter system view.
system-view
2. Activate anti-virus policy settings.
inspect activate
By default, anti-virus policy settings will be activated automatically.
|
CAUTION: This command can cause temporary outage for the DPI service and other services based on DPI. For example, Layer 7 LB cannot perform application-based load balancing. |
Applying a DPI application profile to a virtual server
1. Enter system view.
system-view
2. Enter the view of an IP, TCP, UDP, or HTTP virtual server.
virtual-server virtual-server-name
3. Use a DPI application profile in the virtual server.
dpi-app-profile dpi-app-profile-name
By default, no DPI application profile is used in a virtual server.
For more information about virtual servers, see load balancing configuration in Load Balancing Configuration Guide.
Managing the virus signature library
As viruses constantly increase and change, you must update the virus signature library in time. You can also roll back the virus signature library.
Restrictions and guidelines
· Do not delete the /dpi/ folder in the root directory of the storage medium.
· Do not perform virus signature update and rollback when the device's free memory is below the normal state threshold. For more information about device memory thresholds, see device management in Fundamentals Configuration Guide.
· For successful automatic and immediate signature update, make sure the device can resolve the domain name of the H3C website into an IP address through DNS. For more information about DNS, see DNS configuration in Layer 3—IP Services Configuration Guide.
Scheduling automatic virus signature library update
About this task
You can schedule automatic virus signature library update if the device can access the signature database services on the H3C website. The device periodically obtains the latest signature file from the H3C website to update its local signature library according to the update schedule.
Procedure
1. Enter system view.
system-view
2. Enable automatic virus signature library update and enter automatic virus signature library update configuration view.
anti-virus signature auto-update
By default, automatic virus signature library update is disabled.
3. Schedule the update time.
update schedule { daily | weekly { fri | mon | sat | sun | thu | tue | wed } } start-time time tingle minutes
By default, the device updates the virus signature library at a random time between 02:01:00 and 04:01:00 every day.
Triggering an immediate automatic virus signature library update
About this task
Anytime you find a new release of virus signature file on the H3C website, you can trigger the device to immediately and automatically update the virus signature library.
Procedure
1. Enter system view.
system-view
2. Trigger an immediate virus signature library update.
anti-virus signature auto-update-now
Manually updating the virus signature library
About this task
If the device cannot access the signature database services on the H3C website, use one of the following methods to manually update the virus signature library:
· Local update—Updates the virus signature library by using the locally stored virus signature file.
Store the update file on the master device for successful signature library update.
· FTP/TFTP update—Updates the virus signature library by using the virus signature file stored on an FTP or TFTP server.
Procedure
1. Enter system view.
system-view
2. Manually update the virus signature library.
anti-virus signature update file-path
|
CAUTION: The H3C website provides different signature libraries for devices with different memory sizes and software versions. You must obtain the signature library that is suitable for your device. If your device has a small memory (8 GB or less) but you choose a signature library that is for a large memory (more than 8 GB), the signature update might result in device anomaly. |
Rolling back the virus signature library
About this task
If a virus signature library update causes abnormal situations or a high false alarm rate, you can roll back the virus signature library.
Before rolling back the virus signature library, the device backs up the current signature library as the previous version. For example, the previous version is V1 and the current version is V2. If you perform a rollback to the previous version, version V1 becomes the current version and version V2 becomes the previous version. If you perform a rollback to the previous version again, version V2 becomes the current version and version V1 becomes the previous version.
Procedure
1. Enter system view.
system-view
2. Roll back the virus signature library.
anti-virus signature rollback { factory | last }
Display and maintenance commands for anti-virus
Execute the display commands in any view.
|
Task |
Command |
|
Display anti-virus cache information. |
display anti-virus cache [ slot slot-number ] |
|
Display virus signature information. |
display anti-virus signature [ [ signature-id ] | [ severity { critical | high | low | medium } ] ] |
|
Display virus signature family information. |
display anti-virus signature family-info |
|
Display virus signature library information. |
display anti-virus signature library |
|
Display anti-virus statistics. |
display anti-virus statistics [ policy policy-name ] [ slot slot-number ] |
Anti-virus configuration examples
Example: Using the default anti-virus policy in a virtual server
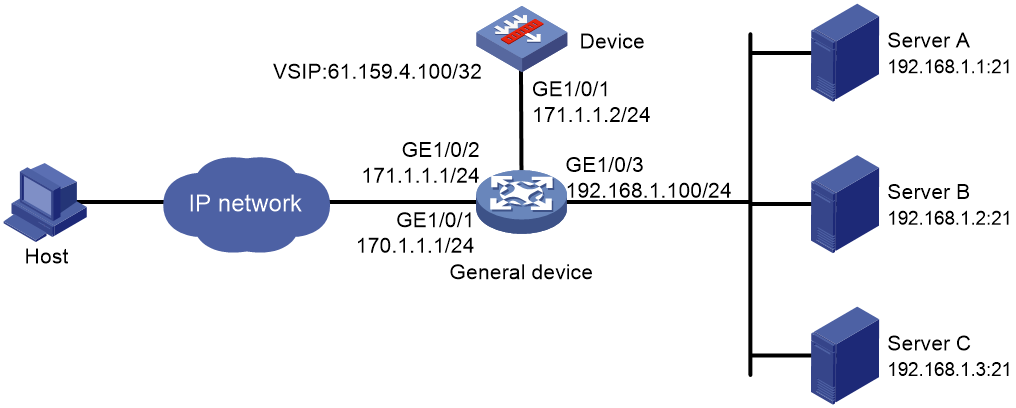
Network configuration
As shown in Figure 3, physical servers Server A, Server B, and Server C provide HTTP services.
Perform the following tasks:
· Configure server load balancing on the device to distribute user requests among the servers.
· Configure the device to use the default anti-virus policy for virus detection and prevention.
Procedure
1. Assign IP addresses to interfaces and configure routes. Make sure the network connections are available. (Details not shown.)
2. Configure server load balancing. (Details not shown.)
For more information about load balancing configuration, see Load Balancing Configuration Guide.
3. Configure a DPI application profile:
# Create a DPI application profile named sec and enter its view.
[Device] app-profile sec
# Apply the default anti-virus policy to the DPI application profile and set the policy mode to protect.
[Device-app-profile-sec] anti-virus apply policy default mode protect
[Device-app-profile-sec] quit
4. Activate the anti-virus policy settings.
[Device] inspect activate
5. Enter the view of HTTP virtual server vs, and specify DPI application profile sec for the virtual server.
[Device] virtual-server vs type http
[Device-vs-http-vs] dpi-app-profile sec
[Device-vs-http-vs] quit
Verifying the configuration
# Verify that HTTP services are distributed among three servers. (Details not shown.)
# Verify that the device can use the default anti-virus policy to detect and prevent known viruses. (Details not shown.)