- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 02-WLAN roaming center configuration | 161.16 KB |
Contents
Configuring the WLAN roaming center
WLAN roaming center tasks at a glance
Inter-AC roaming tasks at a glance
Address security tasks at a glance
IP address recovery tasks at a glance
Enabling the WLAN roaming center
Specifying a portal or client roaming center permitted by the WLAN roaming center
Setting the response timeout timer for packets to portal or client roaming centers
Setting the maximum transmission attempts for user offline notification requests
Enabling WLAN address security
Setting the aging timer for address security entries
Configuring the spoofing attack blacklist
Setting the aging time for client IP address cache entries
Display and maintenance commands for WLAN roaming center
Configuring the WLAN roaming center
About the WLAN roaming center
A WLAN roaming center is an AC that manages client roaming and address information to support seamless roaming of portal clients, address security, and IP address recovery for reassociated clients. For more information about inter-AC roaming of portal clients, see portal in User Access and Authentication Configuration Guide.
Address security requires the WLAN roaming center to work with client roaming centers to identify IP and MAC address spoofing attacks and prevent the attackers from coming online. For more information about client roaming centers, see "Configuring the client roaming center."
IP address recovery allows clients to retrieve their old addresses from the WLAN roaming center if the clients fail to obtain new addresses within the address recovery period after a roaming. Clients can use the old addresses to access the network temporarily. For more information about IP address recovery, see User Access and Authentication Configuration Guide.
Inter-AC roaming mechanism
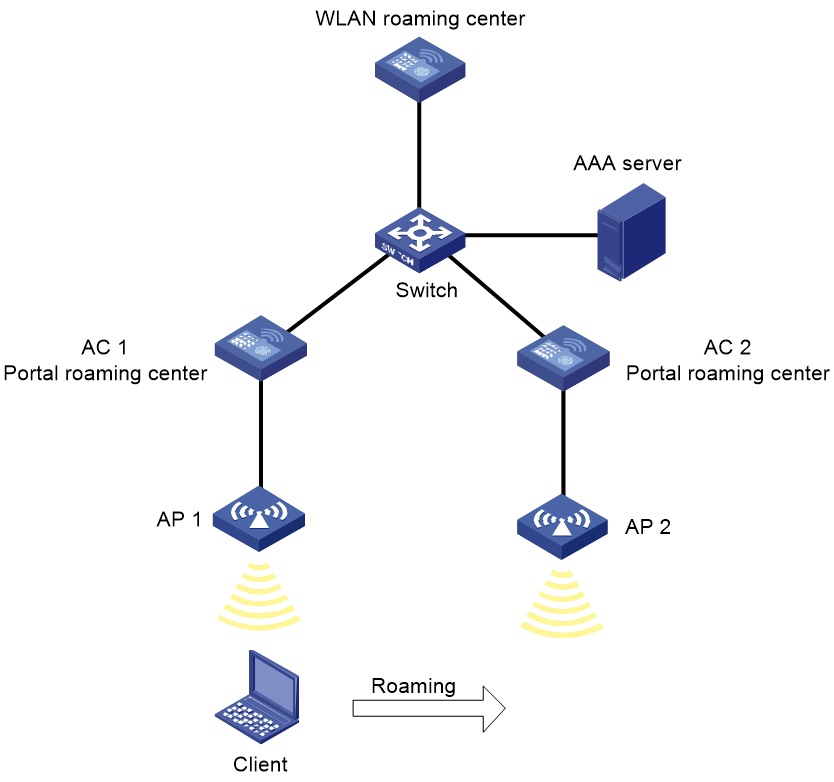
As shown in Figure 1, in a roaming center network, a client performs seamless inter-AC roaming as follows:
1. The client comes online on AC 1:
a. When the client requests to come online, AC 1 sends a user query request to the WLAN roaming center.
b. The WLAN roaming center sends a user query response to AC 1 to notify AC 1 that no matching portal user has been found.
c. AC 1 performs portal authentication on the client.
d. After the client passes portal authentication, AC 1 sends a user online packet to the WLAN roaming center to notify AC 1 that the client has come online. The user online packet contains authorization information that the AAA server assigns to the client.
e. Upon receiving the user online packet, the WLAN roaming center creates a user entry for the client and then sends a user online response to AC 1. The user entry contains the IP address, MAC address, access device list, authorization information, and roaming information for the client.
2. The client roams from AC 1 to AC 2:
a. When the client requests to come online on AC 2, AC 2 sends a user query request to the WLAN roaming center.
b. The WLAN roaming center sends a user query response to AC 2 to notify AC 2 that a matching user has been found. The user query response contains the authorization information that the user obtained when it came online from AC 1.
c. Upon receiving the user query response, AC 2 allows the client to come online without authentication and then sends a user online packet to the WLAN roaming center.
d. Upon receiving the user online packet, the WLAN roaming center updates the roaming information in the user entry for the client and then sends a user online response to AC 2.
3. The client requests to go offline or the client is forcibly logged out by AC 2:
¡ If the client requests to go offline, the AC (AC 1) from which the client comes online for the first time starts the offline process.
¡ When the client requests to go offline, AC 1 deletes the user and sends a user offline packet to the WLAN roaming center. Upon receiving the user offline packet, the WLAN roaming center removes AC 1 from the access device list of the user entry. It also sends a user offline packet to the other access devices (AC 2 in this example) in the list. Upon receiving the user offline packet, AC 2 deletes the user entry and sends a user offline response to the WLAN roaming center.
¡ If the client is forcibly logged out by AC 2, AC 2 sends a user offline packet to the WLAN roaming center. Upon receiving the user offline packet, the WLAN roaming center deletes AC 2 from the access device list of the user entry and sends a user offline response to AC 2.
¡ The reasons why a portal user is forcibly logged out include the following:
¡ The administrator executes a command on the access device to log out the user.
¡ The AP from which the user accesses the WLAN has gone offline.
¡ The DHCP lease of the user has expired.
¡ The authorization idle timeout timer or the authorization session timeout timer of the user has expired.
¡ The administrator logs out the user on the AAA server.
Address security mechanism
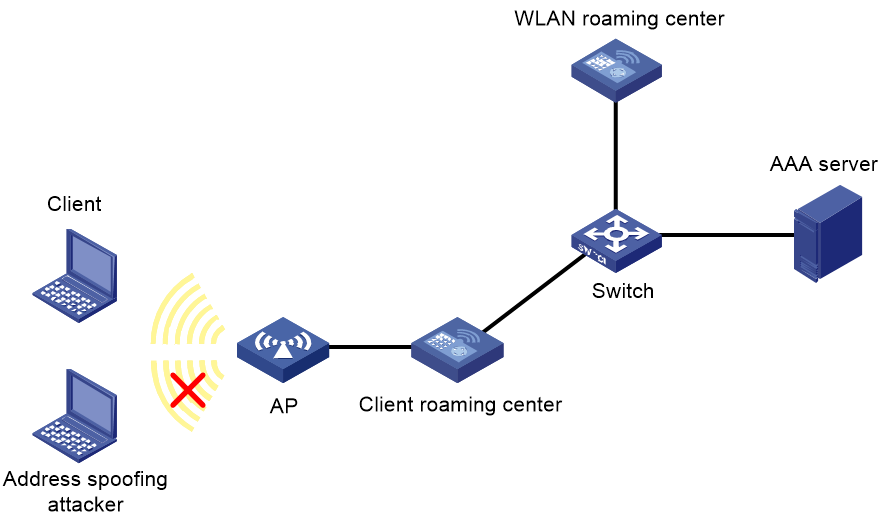
As shown in Figure 2, two ACs are deployed in the network. One AC acts as the WLAN roaming center to manage MAC and IP address entries of online clients and the spoofing attack blacklist, and the other AC acts as a client roaming center to identify rogue clients.
With address security configured, a client roaming center examines the local MAC and IP address entries for matches every time a client attempts to come online or the IP address of a client changes.
· If no match is found, the client roaming center sends a conflict query request to the WLAN roaming center. Then, the WLAN roaming center examines its MAC and IP address entries for conflicts.
¡ If no conflict is found, the WLAN roaming center notifies the client roaming center of the address check result, and generates a MAC address entry and an IP address entry for the client. Then, the system starts accounting for the client.
¡ If any address conflict is found, the WLAN roaming center checks the spoofing attack blacklist, and notifies the client roaming center to updates its local blacklist.
- If the address spoofing attacker, the spoofed client, or both exist in the blacklist, the WLAN roaming center does not update its blacklist.
- If neither the address spoofing attacker nor the spoofed client exists in the blacklist, the WLAN roaming center adds both the attacker and spoofed client to the blacklist.
Clients in the blacklist are not allowed to come online.
· If an IP address match is found, the client roaming center compares the username of the new client and the username of the online client.
¡ If the usernames are the same, the client roaming center logs off the online client. Then, it updates its local MAC and IP address entries, notifies the WLAN roaming center to update the address entry, and adds the old client to the blacklist.
¡ If the usernames are different, the client roaming center logs off the online client, adds both clients to the blacklist, and forbids both clients to come online within the entry aging period.
· If a MAC address match is found, the client roaming center requests the WLAN roaming center to check the manually configured spoofing attack blacklist, and logs off the client in the blacklist. Then, the client roaming center adds the client to the local blacklist and forbids the client to come online within the entry aging period.
Figure 2 Address security mechanism
WLAN roaming center tasks at a glance
Inter-AC roaming tasks at a glance
To configure inter-AC roaming of portal users, perform the following tasks:
1. Enabling the WLAN roaming center
2. (Optional.) Specifying a portal or client roaming center permitted by the WLAN roaming center
3. (Optional.) Specifying the port number used by the WLAN roaming center to communicate with portal and client roaming centers
4. (Optional.) Setting the response timeout timer for packets to portal or client roaming centers
5. (Optional.) Setting the maximum transmission attempts for user offline notification requests
Address security tasks at a glance
To configure address security, perform the following tasks:
1. Enabling the WLAN roaming center
2. Enabling WLAN address security
3. (Optional.) Specifying a portal or client roaming center permitted by the WLAN roaming center
4. (Optional.) Specifying the port number used by the WLAN roaming center to communicate with portal and client roaming centers
5. (Optional.) Setting the response timeout timer for packets to portal or client roaming centers
6. (Optional.) Setting the aging timer for address security entries
7. (Optional.) Configuring the spoofing attack blacklist
IP address recovery tasks at a glance
To configure IP address recovery, perform the following tasks:
1. Enabling IP address recovery for reassociated clients
For more information, see User Access and Authentication Configuration Guide.
2. (Optional.) Setting the aging time for client IP address cache entries
Enabling the WLAN roaming center
Restrictions and guidelines
For portal users to roam between ACs, make sure the portal roaming center is enabled on both ACs.
You can enable the WLAN roaming center on only one AC in a network.
Disabling the WLAN roaming center feature deletes all portal client information.
Procedure
1. Enter system view.
system-view
2. Create a WLAN roaming center and enter its view.
wlan roaming-center
3. Enable the WLAN roaming center.
roaming-center enable
By default, the WLAN roaming center is disabled.
Specifying a portal or client roaming center permitted by the WLAN roaming center
About this task
By default, the WLAN roaming center processes packets from all portal roaming centers and client roaming centers, which might threat network security if rogue devices access the network. To resolve the security issue, you can perform this task to allow the WLAN roaming center to process packets only from specified portal or client roaming centers.
Procedure
1. Enter system view.
system-view
1. Enter WLAN roaming center view.
wlan roaming-center
2. Specify a portal or client roaming center permitted by the WLAN roaming center.
control-access { bas-ip ipv4-address | bas-ipv6 ipv6-address }
By default, no permitted portal roaming center or client roaming center is specified.
Specifying the port number used by the WLAN roaming center to communicate with portal and client roaming centers
Restrictions and guidelines
Make sure the UDP port number is the same as the UDP port number specified in portal or client roaming center view.
Changing the port number of a portal roaming center when portal users are online might cause data inconsistency, client roaming failures, and even client disassociations. The affected clients must be reauthenticated to come online again.
As a best practice to avoid data residual, disable the WLAN roaming center before you change the UDP port number of the WLAN roaming center.
Procedure
1. Enter system view.
system-view
2. Enter WLAN roaming center view.
wlan roaming-center
3. Specify the port used by the WLAN roaming center to communicate with portal and client roaming centers.
port port-number
By default, the WLAN roaming center uses port 1088 to communicate with portal and client roaming centers.
Setting the response timeout timer for packets to portal or client roaming centers
About this task
In inter-AC roaming, when a portal user goes offline, it informs the associated portal roaming center, which then informs the WLAN roaming center. Then, the WLAN roaming center informs the other portal roaming centers. If the WLAN roaming center fails to receive a response from a portal roaming center before the response timeout timer expires, it retransmits the packet. If it fails to receive any response from a portal roaming center after the last retransmission attempt, it deletes the timeout timer.
In a WLAN configured with WLAN address security, the WLAN roaming center sends requests to client roaming centers to query the aging time of MAC address and IP address entries. If it fails to receive a response before the response timeout timer expires, it deletes the specific MAC address and IP address entry.
Procedure
1. Enter system view.
system-view
2. Enter WLAN roaming center view.
wlan roaming-center
3. Set the response timeout timer for packets to portal or client roaming centers.
response-timeout timeout
By default, the response timeout timer is 3 seconds.
Setting the maximum transmission attempts for user offline notification requests
About this task
After sending a user offline notification request to an AC, the WLAN roaming center resends the request if it fails to receive a response before the wait timer expires. If it fails to receive any response after the maximum transmission attempt limit is reached, the WLAN roaming center deletes the timeout timer and removes the AC from the access device list of the client.
Procedure
1. Enter system view.
system-view
2. Create a WLAN roaming center and enter its view.
wlan roaming-center
3. Set the maximum transmission attempts for user offline notification requests.
retry retries
By default, the maximum number of transmission attempts for user offline notification requests is 5.
Enabling WLAN address security
About this task
This feature enables the WLAN roaming center to check clients coming online from the specified service template for MAC address or IP address spoofing attacks. If a MAC or IP address spoofing attack is detected, the AC adds the attacker to the blacklist, and logs off both the attacker and the client whose address is spoofed.
Restrictions and guidelines
For WLAN address security to take effect, configure 802.1X authentication.
WLAN address security takes effect only on clients that come online afterwards.
Procedure
1. Enter system view.
system-view
2. Enter service template view.
wlan service-template service-template-name
3. Enable address security.
address-security enable [ alarm-only ]
By default, address security is disabled.
Setting the aging timer for address security entries
About this task
Client roaming centers generate address security entries at client associations to record client MAC address, IP address, and username information, and synchronize the entries to the WLAN roaming center. When the aging timer of an entry expires, the WLAN roaming center deletes the entry. For more infromation about client roaming centers, see "Configuring the client roaming center."
Procedure
1. Enter system view.
system-view
2. Enter WLAN roaming center view.
wlan roaming-center
3. Set the aging timer for address security entries.
address-security cache { ipv4-aging-time aging-time | ipv6-aging-time aging-time }
By default, the aging timer is 14400 seconds for IPv4 entries and 604800 seconds for IPv6 entries.
Configuring the spoofing attack blacklist
About this task
With address security configured, the WLAN roaming center logs off both the detected MAC or IP address spoofing attackers and the spoofed clients, and adds the attackers to the blacklist. This prevents attackers from coming online again.
Restrictions and guidelines
You can add a maximum of 5000 clients to the spoofing attack blacklist.
The spoofing attack blacklist takes effect only on the WLAN roaming center.
Procedure
1. Enter system view.
system-view
2. Enter WLAN address security view.
wlan address-security
3. Add a client to the spoofing attack blacklist by username.
spoofing-attack blacklist username username
By default, no client exists in the spoofing attack blacklist.
Setting the aging time for client IP address cache entries
About this task
With IP address recovery enabled for reassociated clients, the WLAN roaming center maintains IP and MAC binding entries for clients that leave an AP. When the aging time of such a cache entry expires, the WLAN roaming center deletes the entry.
Procedure
1. Enter system view.
system-view
2. Enter WLAN roaming center view.
wlan roaming-center
3. Set the aging time for client IP address cache entries.
client ip-cache aging-time aging-time
By default, the aging time is 1800 seconds for client IP address cache entries.
Display and maintenance commands for WLAN roaming center
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display offline client history on the WLAN roaming center. |
display wlan roaming-center history user { all | ip ipv4-address | ipv6 ipv6-address | mac mac-address } |
|
Display packet statistics on the WLAN roaming center. |
display wlan roaming-center statistics packet [ bas-ip ipv4-address | bas-ipv6 ipv6-address ] |
|
Display client information on the WLAN roaming center. |
display wlan roaming-center user { all | bas-ip ipv4-address | bas-ipv6 ipv6-address | ip ipv4-address | ipv6 ipv6-address | mac mac-address } [ verbose ] |
|
Clear client history information on the WLAN roaming center. |
reset wlan roaming-center history user { all | ip ipv4-address | ipv6 ipv6-address | mac mac-address } |
|
Clear packet statistics on the WLAN roaming center. |
reset wlan roaming-center statistics packet [ bas-ip ipv4-address | bas-ipv6 ipv6-address ] |
|
Clear client information on the WLAN roaming center. |
reset wlan roaming-center user { all | bas-ip ipv4-address | bas-ipv6 ipv6-address | ip ipv4-address | ipv6 ipv6-address | mac mac-address } |