Security Announcement-Statement on TCPIP remote code execution vulnerability notification on Windows CVE-2020-16898
25-02-2021Overview
The Background of security vulnerability
TCP/IP (Transmission Control Protocol/Internet Protocol) refers to the collective name of the protocol group that must be used when communicating with IP. Recently, the Offensive and Defense Laboratory of New H3C monitored that Microsoft officially released an update patch for the Windows TCP/IP remote code execution vulnerability, the vulnerability number is CVE-2020-16898, and the CVSS score is 9.0 (high risk).
The details of vulnerability
The Windows TCP/IP stack has a flaw in processing the Recursive DNS Server (RDNSS) option of ICMPv6 Router Advertisement packets. Attackers can successfully exploit this vulnerability by sending carefully constructed ICMPv6 packets to a remote Window computer. The attacker can gain the ability to execute code on the target server or client.
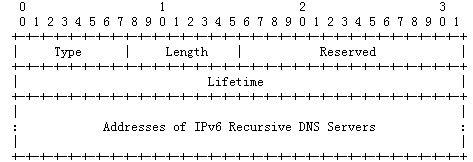
After being attacked, the Windows device will restart with a blue screen.
The scope of influence
Windows 10 Version 1709 for 32-bit Systems
Windows 10 Version 1709 for ARM64-based Systems
Windows 10 Version 1709 for x64-based Systems
Windows 10 Version 1803 for 32-bit Systems
Windows 10 Version 1803 for ARM64-based Systems
Windows 10 Version 1803 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1903 for 32-bit Systems
Windows 10 Version 1903 for ARM64-based Systems
Windows 10 Version 1903 for x64-based Systems
Windows 10 Version 1909 for 32-bit Systems
Windows 10 Version 1909 for ARM64-based Systems
Windows 10 Version 1909 for x64-based Systems
Windows 10 Version 2004 for 32-bit Systems
Windows 10 Version 2004 for ARM64-based Systems
Windows 10 Version 2004 for x64-based Systems
Windows Server 2019
Windows Server 2019 (Server Core installation)
Windows Server, version 1903 (Server Core installation)
Windows Server, version 1909 (Server Core installation)
Windows Server, version 2004 (Server Core installation)
Solution
The official patch
At present, Microsoft has officially released a patch for this vulnerability. It is recommended that users install the patch as soon as possible through the following link:
https://portal.msrc.microsoft.com/zh-cn/security-guidance/advisory/CVE-2020-16898
The temporary solution
If users cannot install the patch, they can temporarily disable ICMPv6 RDNSS.
Use the following PowerShell command to disable ICMPv6 RDNSS. This solution is only available for Windows 1709 and later.
netsh int ipv6 set int *INTERFACENUMBER* rabaseddnsconfig=disable
Note: After making changes, there is no need to restart.
You can use the following PowerShell command to re-enable ICMPv6 RDNSS.
netsh int ipv6 set int *INTERFACENUMBER* rabaseddnsconfig=enable
Note: After restarting ICMPv6 RDNSS, there is no need to restart.
H3C security emergency response external service
H3C advocates that every effort be made to safeguard the ultimate interests of product users, to abide by principles of responsible disclosure of security incidents, and to handle product security issues in accordance with security issues mechanisms. For information on H3C's security emergency response service and H3C product vulnerabilities, please visit https://www.h3c.com/en/Support/Online_Help/psirt/.
