Security Announcement-Statement on OpenSDB Remote Code Execution CVE-2020-35476
25-02-2021Overview
The Background of security vulnerability
OpenSDB (Open Time Series Data Base) is a distributed and extensible Time Series database based on HBase. OpenSDB can obtain the time series data collected and generated by various types of real-time monitoring, inspection and analysis equipment in the power industry, chemical industry, Internet of Things industry, and provide storage, indexing and graphical services to make it easy to access and visualization. Recently, the new H3C offensive and defense laboratory has monitored the occurrence of OpenSDB remote code execution vulnerability (CVE-2020-35476) on the network, and carried out the replication and analysis.
The principle of the vulnerability
OpenSDB 2.4.0 and earlier had a remote code execution vulnerability, User submits yrange parameters or other related parameter values in the /src/tsd/GraphHandler.java file for simple backquotes and after encoding filtering, it is written directly to the gnuplot file in the /tmp directory.
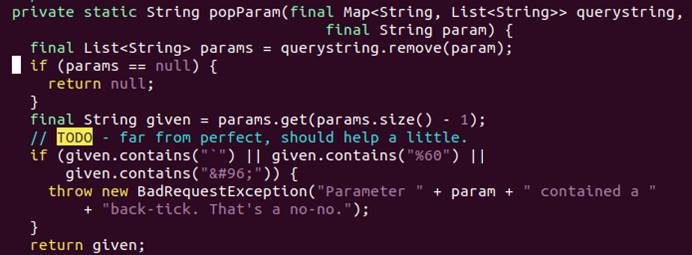
The gnuplot file will be executed by the /src/mygnuplot.sh script in the OpenTSDB directory, and the attacker can use other ways to bypass the above limitation and trigger the remote code execution vulnerability through command injection.
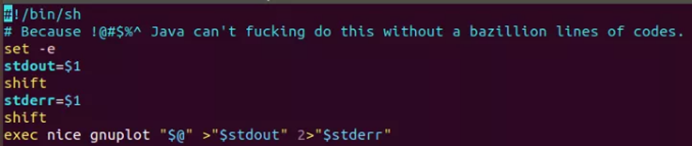
The reproduce of security vulnerability
1. Build an environment with vulnerabilities (OpenSDB 2.3.2), which can be accessed normally.
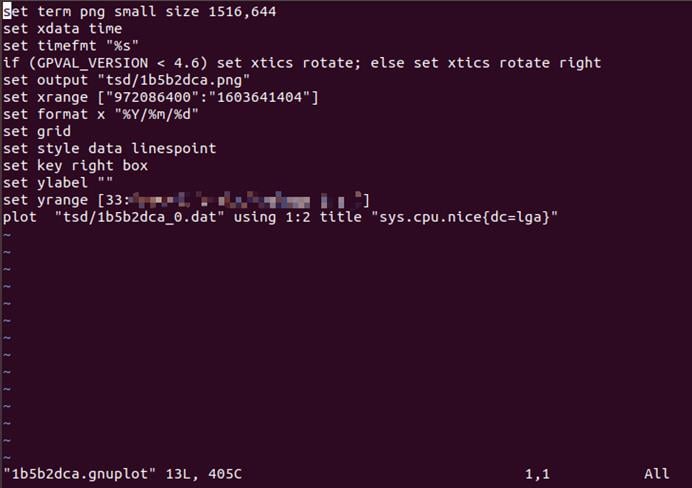
2.Create a metric and construct the payload to send to OpenTSDB, the gnuplot file was successfully created in/TMP
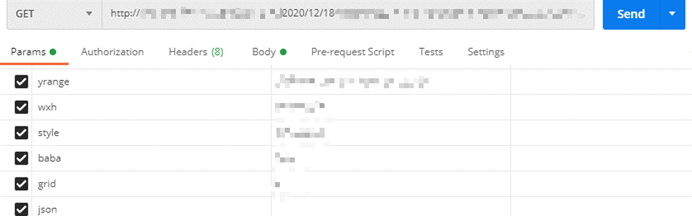
Sphere of influence
OpenTSDB <= 2.4.0
Severity level
High Risk
Solution
The official patch
OpenSDB has not officially released a patch for the vulnerability, please pay attention to the manufacturer's home page: http://opentsdb.net/
The solution of H3C
Visit the OpenSDB page and click the Version TAB to see whether the current Version of OpenSDB is within the affected Version range.

H3C solution
1. H3C safety equipment protection scheme
The IPS rule base of H3C will support the identification of this vulnerability in version 1.0.115. The whole security products of H3C can identify the attack traffic of this vulnerability by upgrading the IPS feature library and take the initiative to intercept it.
2. H3C situational awareness solution
H3C situational awareness has supported the detection of this vulnerability. Through comprehensive research and judgment methods such as information collection and integration, data association analysis, etc., assets that are attacked and lost by this vulnerability in the network are found.
3. Solution of H3C Cloud Security Capability Center
The knowledge base of H3C Cloud Security Capability Center has been updated with the vulnerability information, and the corresponding vulnerability generation principle, upgrade patch and repair measures can be inquired.
https://github.com/OpenTSDB/opentsdb/issues/2051
H3C security emergency response external service
H3C advocates that every effort be made to safeguard the ultimate interests of product users, to abide by principles of responsible disclosure of security incidents, and to handle product security issues in accordance with security issues mechanisms. For information on H3C's security emergency response service and H3C product vulnerabilities, please visit https://www.h3c.com/en/Support/Online_Help/psirt/.
