- Table of Contents
-
- 01-Fundamentals Configuration Guide
- 00-Preface
- 01-CLI configuration
- 02-RBAC configuration
- 03-Login management configuration
- 04-FTP and TFTP configuration
- 05-File system management configuration
- 06-Configuration file management configuration
- 07-Software upgrade configuration
- 08-ISSU configuration
- 09-Automatic configuration
- 10-Device management configuration
- 11-Tcl configuration
- 12-Python configuration
- 13-License management
- 14-MAC learning through a Layer 3 device configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 14-MAC learning through a Layer 3 device configuration | 80.20 KB |
Contents
Configuring MAC address learning through a Layer 3 device
About MAC address learning through a Layer 3 device
Restrictions and guidelines: MAC address learning through a Layer 3 device configuration
MAC address learning through a Layer 3 device configuration tasks at a glance
Enabling ARP entry synchronization through SNMP
Configuring the target Layer 3 device
Setting the parameters for ARP entry synchronization
Display and maintenance commands for
MAC address learning through a Layer 3 device configuration examples
Example: Configuring MAC address learning through a Layer 3 device
Configuring MAC address learning through a Layer 3 device
About MAC address learning through a Layer 3 device
This feature enables the device to learn the MAC address of a terminal (a PC for example) when a Layer 3 device exists between the device and the terminal through SNMP for network traffic control.
Working mechanism
Figure 1 MAC address learning through a Layer device workflow
As shown in Figure 1, MAC address learning through a Layer 3 device proceeds as follows:
1. The gateway learns the IP-MAC binding of the terminal, and then generates an ARP entry.
2. The device sends SNMP requests to the gateway at the specified intervals to request the ARP entry.
3. The gateway sends a response that contains the ARP entry to the device.
4. Upon receiving the response, the device saves the ARP entry in the memory. Then it can learn the MAC address of the terminal.
Entry aging
ARP entries learned through a Layer 3 device will be automatically deleted when the aging timer expires, or can be cleared using the reset snmp-server arp-sync table command.
Restrictions and guidelines: MAC address learning through a Layer 3 device configuration
· ARP entries learned using this feature can be used only for policy packet filtering and cannot be used for packet forwarding.
· Only MAC addresses mapped from IPv4 addresses can be learned.
· Make sure no NAT devices exist between the device and the Layer 3 device.
· This feature is not applicable to a VRF network.
MAC address learning through a Layer 3 device configuration tasks at a glance
To configure MAC address learning through a Layer 3 device, perform the following tasks:
1. Enabling ARP entry synchronization through SNMP
2. Configuring the target Layer 3 device
3. (Optional.) Setting the parameters for ARP entry synchronization
Prerequistes
Make sure SNMP agent has been enabled and a community name has been configured on the Layer 3 device. For information about SNMP, see SNMP configuration in Network Management and Monitoring.
Enabling ARP entry synchronization through SNMP
About this task
With this feature enabled, the device acts as an NMS to learn all ARP entries on a Layer 3 device (agent) to obtain the MAC address of the Layer 3 device.
Procedure
1. Enter system view.
system-view
2. Enable ARP entry synchronization through SNMP.
snmp-server arp-sync enable
By default, ARP entry synchronization through SNMP is disabled.
Configuring the target Layer 3 device
1. Enter system view.
system-view
2. Configure the target Layer 3 device for ARP entry synchronization through SNMP.
SNMP v2c:
snmp-server arp-sync target-host address ip-address community { simple | cipher } community-name v2c
SNMP v3:
snmp-server arp-sync target-host address ip-address usm-user v3 user-name [ { simple | cipher } authentication-mode { md5 | sha } auth-password [ privacy-mode des pri-password ] ]
By default, no target Layer 3 device is configured for ARP entry synchronization through SNMP.
Setting the parameters for ARP entry synchronization
About this task
With this feature configured, the device sends SNMP requests for ARP entry synchronization to the target Layer 3 device at the specified intervals. If the device does not receive an SNMP response before the timeout expires within the specified interval, the device re-sends SNMP requests.
Procedure
1. Enter system view.
system-view
2. Set the parameters for ARP entry synchronization.
snmp-server arp-sync { interval interval | timeout time } *
By default, the interval for sending SNMP requests is 5 seconds and the timeout for SNMP responses is 3 seconds.
Display and maintenance commands for
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display the ARP entries synchronized through SNMP. |
display snmp-server arp-sync table |
|
Clear the ARP entries synchronized through SNMP. |
reset snmp-server arp-sync table |
MAC address learning through a Layer 3 device configuration examples
Example: Configuring MAC address learning through a Layer 3 device
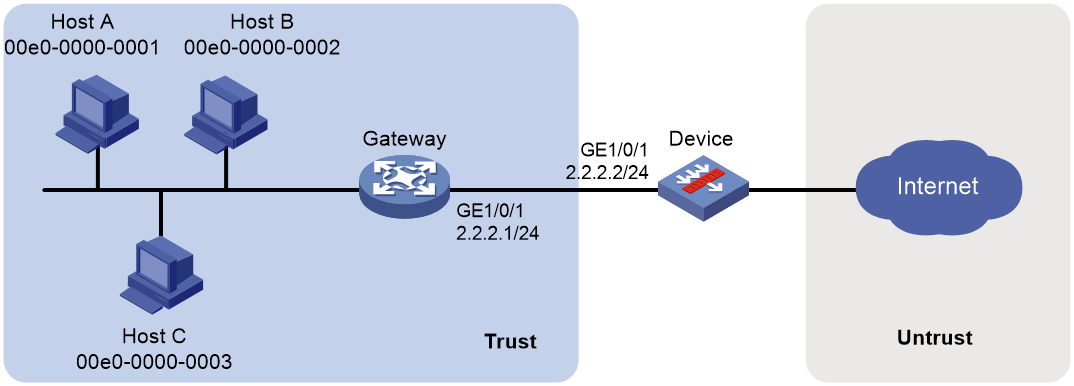
Network configuration
Hosts in an internal network are connected to the device through a Layer 3 gateway and the device is connected to the Internet. Configure MAC address learning through a Layer 3 device to ensure that the device can learn the MAC addresses of the hosts through the gateway to implement access control of the hosts.
Figure 2 Network diagram
?
Procedure
1. Configure the gateway:
# Specify an IP address for each interface and configure routing features to ensure network reachability. (Details not shown.)
# Configure SNMPv2c, and create the read-only community with the plaintext form name public.
<Gateway> system-view
[Gateway] snmp-agent sys-info version v2c
[Gateway] snmp-agent community read simple public
2. Configure the device:
# Specify an IP addres for each interface, and configure routing features and security domains to ensure network reachability. (Details not shown.)
# Enable ARP entry synchronization through SNMP.
<Device> system-view
[Device] snmp-server arp-sync enable
# Configure the device to use the plaintext form community name public to synchronize ARP entries from the Layer 3 device with IP address 2.2.2.1.
[Device] snmp-server arp-sync target-host address 2.2.2.1 community simple public v2c
# Set the interval for sending SNMP requests to 10 seconds and the timeout for SNMP responses to 4 seconds.
[Device] snmp-server arp-sync interval 10 timeout 4
3. Create an IPv4 address object group and add the subnet that connects the device to the gateway to the object group.
# Create an IPv4 address object group named groupip.
[Device] object-group ip address groupip
# Configure an IPv4 address object with an IPv4 address of 2.2.2.0 and mask of 255.255.255.0.
[Device-obj-grp-ip-groupip] network subnet 2.2.2.0 255.255.255.0
[Device-obj-grp-ip-groupip] quit
4. Create a MAC object group and add the MAC addresses of the permitted hosts to the object group.
# Create a MAC object group named groupmac.
[Device] object-group mac-address groupmac
# Configure MAC address objects with MAC addresses 00e0-0000-0001 and 00e0-0000-0002, respectively.
[Device-obj-grp-mac-groupmac] mac 00e0-0000-0001
[Device-obj-grp-mac-groupmac] mac 00e0-0000-0002
[Device-obj-grp-mac-groupmac] quit
5. Configure a security policy to allow only device to access the gateway so that the device can learn the ARP entries on the gateway.
# Enter IPv4 security policy view.
[Device] security-policy ip
# Configure an IPv4 security policy rule with rule ID 0 and rule name rule1.
[Device-security-policy-ip] rule 0 name rule1
[Device-security-policy-ip-0-rule1] source-zone local
[Device-security-policy-ip-0-rule1] destination-zone trust
[Device-security-policy-ip-0-rule1] source-ip groupip
[Device-security-policy-ip-0-rule1] destination-ip groupip
[Device-security-policy-ip-0-rule1] action pass
[Device-security-policy-ip-0-rule1] quit
6. Configure a security policy to allow only Host A and Host B to access the external network.
# Configure an IPv4 security policy rule with rule ID 1 and rule name rule2.
[Device-security-policy-ip] rule 1 name rule2
[Device-security-policy-ip-1-rule2] source-zone trust
[Device-security-policy-ip-1-rule2] destination-zone untrust
[Device-security-policy-ip-1-rule2] source-mac groupmac
[Device-security-policy-ip-1-rule2] action pass
[Device-security-policy-ip-1-rule2] quit
# Activate rule matching acceleration.
[Device-security-policy-ip] accelerate enhanced enable
[Device-security-policy-ip] quit
Verifying the configuration
1. Verify that ARP entries have been synchronized to the device.
[Device] display snmp-server arp-sync table
IP Address?????? MAC Address??? ????Aging(M)
1.1.1.1????????? 00e0-0000-0001???? 1
1.1.1.2????????? 00e0-0000-0002???? 1
1.1.1.3????????? 00e0-0000-0003???? 1
Total:3
2. Verify that Host A and Host B can access the external network but Host C cannot.