- Table of Contents
-
- H3C S6300 Configuration Examples-6W100
- 01-Login Management Configuration Examples
- 02-RBAC Configuration Examples
- 03-Software Upgrade Configuration Examples
- 04-Software Patching Examples
- 05-ISSU Configuration Examples
- 06-Ethernet Link Aggregation Configuration Examples
- 07-Port Isolation Configuration Examples
- 08-Spanning Tree Configuration Examples
- 09-VLAN Configuration Examples
- 10-VLAN Tagging Configuration Examples
- 11-DHCP Snooping Configuration Examples
- 12-Cross-Subnet Dynamic IP Address Allocation Configuration Examples
- 13-IGMP Snooping Configuration Examples
- 14-MLD Snooping Configuration Examples
- 15-IPv6 Multicast VLAN Configuration Examples
- 16-ACL Configuration Examples
- 17-Control Plane-Based QoS Policy Configuration Examples
- 18-Traffic Policing Configuration Examples
- 19-GTS and Rate Limiting Configuration Examples
- 20-Priority and Queue Scheduling Configuration Examples
- 21-Traffic Filtering Configuration Examples
- 22-AAA Configuration Examples
- 23-Port Security Configuration Examples
- 24-Portal Configuration Examples
- 25-SSH Configuration Examples
- 26-IP Source Guard Configuration Examples
- 27-Ethernet OAM Configuration Examples
- 28-CFD Configuration Examples
- 29-DLDP Configuration Examples
- 30-FCoE Configuration Examples
- 31-NTP Configuration Examples
- 32-PTP Configuration Examples
- 33-SNMP Configuration Examples
- 34-NQA Configuration Examples
- 35-Mirroring Configuration Examples
- 36-sFlow Configuration Examples
- 37-OpenFlow Configuration Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Login Management Configuration Examples | 188.88 KB |
|
|
|
H3C S6300 Switch Series |
|
Login Management Configuration Examples |
|
|
Copyright © 2020 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Contents
Example: Configuring console login
Configuration restrictions and guidelines
Example: Configuring Telnet login
Example: Configuring login user command authorization and accounting
Configuration restrictions and guidelines
Configuring the HWTACACS server
Verify the command authorization feature:
Introduction
This document provides login configuration examples. It also provides examples for implementing user access control by using command authorization and command accounting.
Prerequisites
The configuration examples in this document were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
This document assumes that you have basic knowledge of login management.
Example: Configuring console login
Network requirements
Configure console login so users must pass local authentication to log in to the device through the console port.
Requirements analysis
The port properties for the terminal emulation program must match the console port's settings.
By default, a local user is assigned the default user role network-operator and is not assigned any service type. To enable a local user to log in through the console port and manage the device, you must assign the terminal service type and network-admin user role to the user.
Software version used
This configuration example was created and verified on S6300-CMW710-R2310.
Configuration restrictions and guidelines
When you configure console login, follow these restrictions and guidelines:
· Identify the console port carefully to make sure you are connecting to the correct port.
· If the PC is running Windows XP or Windows Server 2003, you must first add the HyperTerminal program. If the PC is running Windows Server 2008, Windows 7, Windows Vista, or another operating system, you must first obtain and install a third-party terminal control program. For information about how to use the program to log in to the device, see the program's user guide or online help.
Configuration procedures
1. Connect the DB-9 female connector of the console cable to the serial port of the PC.
2. Connect the RJ-45 connector of the console cable to the console port of the device.
|
|
IMPORTANT: Serial ports on a PC do not support hot swapping. If the device has been powered on, always connect the console cable to the PC before connecting it to the device, and always disconnect the console cable from the device before disconnecting it from the PC. |
Figure 1 Connecting a configuration terminal to the console port
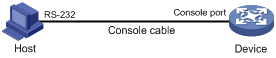
3. If the PC is off, turn on the PC.
4. On the PC, launch the terminal emulation program and create a connection that uses the serial port connected to the device. Set the port properties to match the console port settings on the device.
In this example, the console port uses the following default settings:
¡ Bits per second—9600 bps.
¡ Flow control—None.
¡ Parity—None.
¡ Stop bits—1.
¡ Data bits—8.
5. Power on the device and press Enter as prompted.
The user view prompt appears. To get help, enter ?.
******************************************************************************
* Copyright (c) 2004-2014 Hewlett-Packard Development Company,L.P. *
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
Line aux0 is available.
Press ENTER to get started.
<Sysname>%Jun 23 09:52:58:243 2014 Sysname SHELL/5/SHELL_LOGIN:TTY logged in from aux0.
<Sysname>
6. Configure AUX line 0:
# Enter AUX line view.
<Sysname> system-view
[Sysname] line aux 0
# Enable scheme authentication to use AAA to authenticate the console login user.
[Sysname-line-aux0] authentication-mode scheme
[Sysname-line-aux0] quit
# Create local user admin.
[Sysname] local-user admin class manage
New local user added.
# Set the password to 123 (plain text) for the local user.
[Sysname-luser-manage-admin] password simple 123
# Assign the terminal service type and the network-admin user role to the user. Reclaim the default user role.
[Sysname-luser-manage-admin] service-type terminal
[Sysname-luser-manage-admin] authorization-attribute user-role network-admin
[Sysname-luser-manage-admin] undo authorization-attribute user-role network-operator
[Sysname-luser-manage-admin] quit
Verifying the configuration
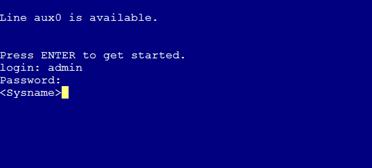
1. Log in to the device through the console port again and press Enter as prompted.
The prompt for username login: appears.
2. Enter the username admin.
The prompt for password Password: appears.
3. Enter the password 123.
The user view prompt <Sysname> appears, as shown in Figure 2.
Figure 2 Console login interface
Configuration files
#
line aux 0
authentication-mode scheme
user-role network-admin
#
local-user admin class manage
password hash $h$6$R1DZqFZrkA93GMAf$th9k1FcsjqRRy1A2reQXQkfmnTBSr/7//80W5gKuyeHYxNor/FVNl4tbBQLhaGeY5XFrVr1+WopPcC+dfaumgg==
service-type terminal
authorization-attribute user-role network-admin
#
Example: Configuring Telnet login
Network requirements
As shown in Figure 3, users need to log in to the device remotely to manage the device.
· Configure Telnet login to enable users to Telnet to the device.
· Configure Telnet user authentication so a Telnet user must provide the correct username and password at login.
· Configure access control so only Telnet users at 192.168.0.46/24 and 192.168.0.52/24 can Telnet to the device.
· Configure two local users.
¡ One local user can manage the device.
¡ One local user can use only the read commands of features.
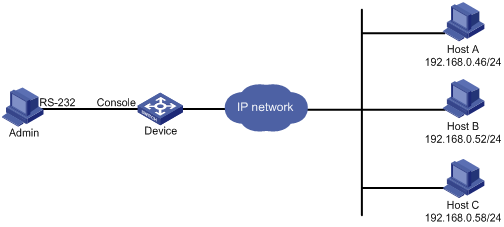
Requirements analysis
Telnet service is disabled by default. To enable Telnet login, you must enable Telnet service.
To control Telnet login, configure an ACL to permit access only from the specified IP addresses.
By default, a local user is assigned the default user role network-operator. To restrict a local user to read commands, you must create a user role that can access only read commands.
Software version used
This configuration example was created and verified on S6300-CMW710-R2310.
Configuration procedures
# Log in to the device through the console port. (Details not shown.)
# Enable Telnet service.
<Sysname> system-view
[Sysname] telnet server enable
# Enable scheme authentication to use AAA to authenticate the Telnet login user.
[Sysname] line vty 0 63
[Sysname-line-vty0-63] authentication-mode scheme
[Sysname-line-vty0-63] quit
# Create local user userA. Set the password to 123 (plain text).
[Sysname] local-user userA class manage
New local user added.
[Sysname-luser-manage-userA] password simple 123
# Assign the Telnet service type and the network-admin user role to the user. Reclaim the default user role.
[Sysname-luser-manage-userA] authorization-attribute user-role network-admin
[Sysname-luser-manage-userA] service-type telnet
[Sysname-luser-manage-userA] undo authorization-attribute user-role network-operator
[Sysname-luser-manage-userA] quit
# Create user role roleB. Add rule 1 to permit the user role to access read commands of all features.
[Sysname] role name roleB
[Sysname-role-roleB] rule 1 permit read feature
[Sysname-role-roleB] quit
# Create local user userB. Set the password to 123 (plain text).
[Sysname] local-user userB class manage
New local user added.
[Sysname-luser-manage-userB] password simple 123
# Assign the Telnet service type and the roleB user role to the user. Reclaim the default user role.
[Sysname-luser-manage-userB] authorization-attribute user-role roleB
[Sysname-luser-manage-userB] service-type telnet
[Sysname-luser-manage-userB] undo authorization-attribute user-role network-operator
[Sysname-luser-manage-userB] quit
# Create ACL 2000 and add rules to permit only access from 192.168.0.46 and 192.168.0.52.
[Sysname] acl number 2000
[Sysname-acl-basic-2000] rule 1 permit source 192.168.0.46 0
[Sysname-acl-basic-2000] rule 2 permit source 192.168.0.52 0
[Sysname-acl-basic-2000] rule 3 deny source any
[Sysname-acl-basic-2000] quit
# Apply the ACL to filter Telnet logins.
[Sysname] telnet server acl 2000
Verifying the configuration
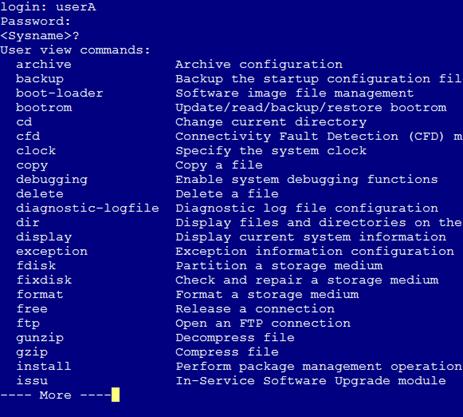
1. Telnet to the device from Host A as userA. (Details not shown.)
2. Display the commands available in user view, as shown in Figure 4.
The commands for device configuration and management are included in the list.
Figure 4 Commands available for userA
3. Telnet to the device from Host B as userB. (Details not shown.)
4. Display the commands available in user view, as shown in Figure 5.
Only read commands are displayed.
Figure 5 Commands available for userB
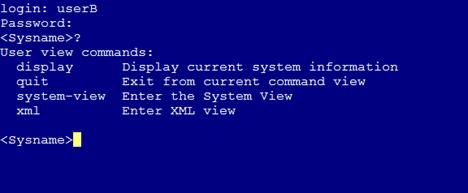
5. Telnet to the device from Host C. (Details not shown.)
Your access request is rejected.
Configuration files
#
telnet server enable
telnet server acl 2000
#
acl number 2000
rule 1 permit source 192.168.0.52 0
rule 2 permit source 192.168.0.46 0
rule 3 deny
#
line vty 0 63
authentication-mode scheme
user-role network-operator
#
local-user userA class manage
password hash $h$6$I2Sg4Llj1qVUWQZ3$JA6KkU3zfVVRg48MM92X6cVpdiqR2JF887PKi3GQMwn
XXXcsWBuz7GIeJZeeNFMmMBaV7DPkKblnb0sGT2axvg==
service-type telnet
authorization-attribute user-role network-admin
local-user userB class manage
password hash $h$6$q+c3OcSxrPpDpsDf$BWkgfOyxBLyR5zyYgF/+VvN/1ofy81zoHDlFf80OjDl
a6/EiSJbSBl33PeazilSkWSYcttkg5v5bGecB7oYwAw==
service-type telnet
authorization-attribute user-role roleB
#
role name roleB
rule 1 permit read feature
#
Example: Configuring login user command authorization and accounting
Network requirements
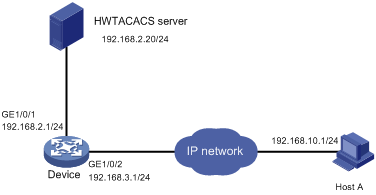
As shown in Figure 6, Host A needs to log in to the device to manage the device.
For device security purposes, configure the device to perform the following tasks:
· Allow Host A to Telnet in after authentication.
· Use the HWTACACS server to control the commands that the user can execute.
· Send commands executed by users to the HWTACACS server to monitor and control user operations on the device.
Requirements analysis
To implement command authorization and accounting, you must perform the following tasks:
· Enable scheme authentication and configure an HWTACACS scheme on the device.
· Configure an account on the HWTACACS server for the Telnet user and assign commands for the user to use.
Software version used
This configuration example was created and verified on S6300-CMW710-R2310.
Configuration restrictions and guidelines
The command authorization function takes effect immediately after you execute the command authorization command. Before executing this command, you must complete the following tasks:
· Configure a user account on the HWTACACS server and specify the commands for the user to use.
· Configure the required HWTACACS scheme on the device.
Configuration procedures
Configuring the HWTACACS server
In this example, the HWTACACS server runs on IMC PLAT 7.0 (E0202) and IMC TAM 7.0 (E0202).
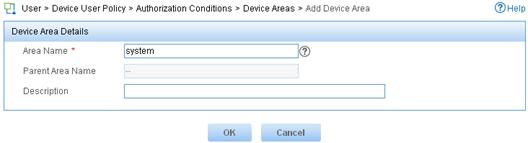
1. Add a device area:
a. Log in to IMC.
b. Click the User tab.
c. From the navigation tree, select Device User Policy > Authorization Conditions > Device Areas.
d. Click Add.
e. Set the area name to system and click OK.
Figure 7 Adding a device area
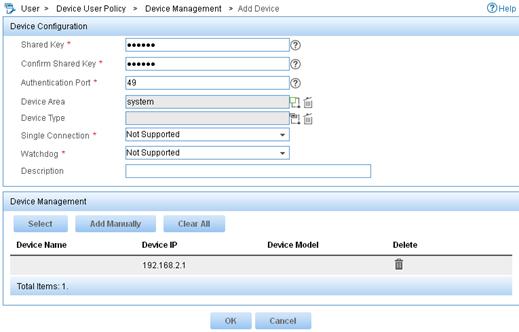
2. Add a device:
a. From the navigation tree, select Device User Policy > Device Management.
b. Click Add.
c. Enter expert for both Shared Key and Confirm Shared Key.
d. Set the authentication port to 49.
e. Select the device area system.
f. Select Not Supported for Single Connection to disable the device from establishing multiple sessions over a single TCP connection.
g. Select Not Supported for Watchdog to disable the device from sending watchdog packets while the user is online.
h. In the Device Management area, click Add Manually.
i. Enter the IP address 192.168.2.1 and click OK.
j. Click OK.
Figure 8 Adding a device
3. Add a shell profile:
a. From the navigation tree, select Device User Policy > Authorization Command > Shell Profiles.
b. Click Add.
c. Enter the profile name Shell Profile1.
d. Select the privilege Level 1.
e. Click OK.
Figure 9 Adding a shell profile
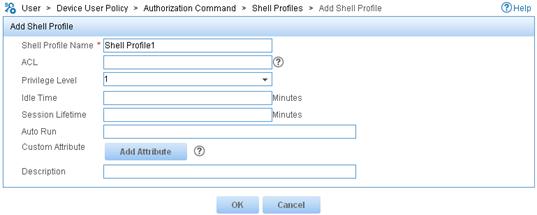
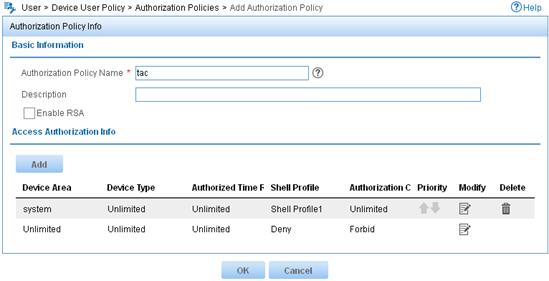
4. Add an authorization policy:
a. From the navigation tree, select Device User Policy > Authorization Policies.
b. Click Add.
c. Enter the policy name tac.
d. In the Access Authorization Info area, click Add to configure access authorization information.
e. Select Unlimited for Device Area, Device Type, and Authorized Time Range.
f. Select the shell profile Shell Profile1.
g. Select Unlimited for Authorization Command Set and click OK.
h. Click OK.
Figure 10 Configuring access authorization information
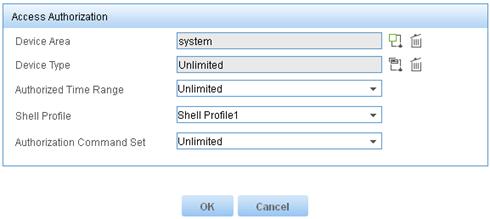
Figure 11 Adding an authorization policy
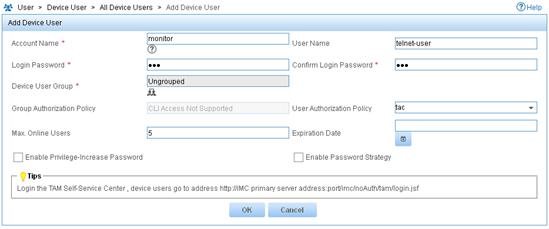
5. Add a device user:
a. From the navigation tree, select Device User > All Device Users.
b. Click Add.
c. Enter the account name monitor and username telnet-user.
d. Enter the login password 123 and confirm the password.
e. Select the user authorization policy tac.
f. Enter 5 for Max. Online Users to limit the number of online users that use the account.
g. Click OK.
Figure 12 Adding a device user
Configuring the device
# Assign IP addresses to relevant interfaces. Make sure the device and the HWTACACS server can reach each other, and the device and Host A can reach each other. (Details not shown.)
# Enable Telnet service.
<Sysname> system-view
[Sysname] telnet server enable
# Create HWTACACS scheme tac.
[Sysname] hwtacacs scheme tac
# Configure the scheme to use the HWTACACS server at 192.168.2.20:49 for authentication, authorization, and accounting.
[Sysname-hwtacacs-tac] primary authentication 192.168.2.20 49
[Sysname-hwtacacs-tac] primary authorization 192.168.2.20 49
[Sysname-hwtacacs-tac] primary accounting 192.168.2.20 49
# Set the shared keys to expert.
[Sysname-hwtacacs-tac] key authentication simple expert
[Sysname-hwtacacs-tac] key authorization simple expert
[Sysname-hwtacacs-tac] key accounting simple expert
# Remove domain names from usernames sent to the HWTACACS server.
[Sysname-hwtacacs-tac] user-name-format without-domain
[Sysname-hwtacacs-tac] quit
# Configure the system-predefined domain system.
[Sysname] domain system
# Use HWTACACS scheme tac for login user authentication, authorization, and accounting. Use local authentication, authorization, and accounting as the backup method.
[Sysname-isp-system] authentication login hwtacacs-scheme tac local
[Sysname-isp-system] authorization login hwtacacs-scheme tac local
[Sysname-isp-system] accounting login hwtacacs-scheme tac local
# Use HWTACACS scheme tac for command authorization and accounting. Use local authorization as the backup command authorization method.
[Sysname-isp-system] authorization command hwtacacs-scheme tac local
[Sysname-isp-system] accounting command hwtacacs-scheme tac
[Sysname-isp-system] quit
# Create local user monitor. Set the password to 123 (plain text).
[Sysname] local-user monitor class manage
[Sysname-luser-manage-monitor] password simple 123
# Assign the Telnet service type and the level-1 user role to the user. Reclaim the default user role.
[Sysname-luser-manage-monitor] service-type telnet
[Sysname-luser-manage-monitor] authorization-attribute user-role level-1
[Sysname-luser-manage-monitor] undo authorization-attribute user-role network-operator
[Sysname-luser-manage-monitor] quit
# Enable scheme authentication to use AAA to authenticate the Telnet login user.
[Sysname] line vty 0 63
[Sysname-line-vty0-63] authentication-mode scheme
# Enable command authorization and command accounting.
[Sysname-line-vty0-63] command authorization
[Sysname-line-vty0-63] command accounting
[Sysname-line-vty0-63] quit
Verifying the configuration
Verify the command authorization feature:
# Telnet to the device and enter the username monitor and password 123.
C:\Documents and Settings\Administrator> telnet 192.168.1.1
******************************************************************************
* Copyright (c) 2004-2014 Hewlett-Packard Development Company,L.P. *
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
login:monitor
Password:
<Sysname>
# Enter ? to display commands available in user view and system view. Only commands permitted by the level-1 user role are displayed.
<Sysname> ?
User view commands:
display Display current system information
ping Ping function
quit Exit from current command view
ssh2 Establish a secure shell client connection
super Switch to a user role
system-view Enter the System View
telnet Establish a telnet connection
tracert Tracert function
xml Enter XML view
<Sysname> system-view
System View: return to User View with Ctrl+Z.
[Sysname] ?
System view commands:
display Display current system information
local-user Configure a local user
ping Ping function
quit Exit from current command view
return Exit to User View
tracert Tracert function
Configuration files
#
telnet server enable
#
hwtacacs scheme tac
primary authentication 192.168.2.20
primary authorization 192.168.2.20
primary accounting 192.168.2.20
key authentication cipher $c$3$Fl1Mn3wBsh+vH6otPvoz+AdE7VaNS3c0Pw==
key authorization cipher $c$3$2x6XI5xU7UGX6VqWFXNp2n3FG07uTNjiQw==
key accounting cipher $c$3$2oKsuCOAZX1+3ibvTPxnJ1YvJ1MHqv73Lw==
user-name-format without-domain
#
domain system
authentication login hwtacacs-scheme tac local
authorization login hwtacacs-scheme tac local
accounting login hwtacacs-scheme tac local
authorization command hwtacacs-scheme tac local
accounting command hwtacacs-scheme tac
#
local-user monitor class manage
password hash $h$6$5BqWnAJTpBbU5NbY$PbdgF+43eE5WMvj2iHPySfd5nGqj5AhDCDOXTiUMJvR
FFVsZaF8EW1tgpsQPRSq7SDKaGqwHTy9nsabAoGNaYg==
service-type telnet
authorization-attribute user-role level-1
#
line vty 0 63
authentication-mode scheme
user-role network-operator
idle-timeout 0 0
command authorization
command accounting
#
Related documentation
· H3C S6300 Switch Series Fundamentals Configuration Guide-Release 23xx
· H3C S6300 Switch Series Fundamentals Command Reference-Release 23xx

