- Table of Contents
- Related Documents
-
01-Text
Download Book (536.86 KB)Contents
Assignment of traffic to VXLANs
Traffic from the local site to a remote site
Traffic from a remote site to the local site
Centralized EVPN gateway deployment
Distributed EVPN gateway deployment
Configuration restrictions and guidelines
Setting the forwarding mode for VXLANs
Configuration restrictions and guidelines
Configuring BGP to advertise EVPN routes
Mapping an Ethernet service instance to a VSI
Configuring a centralized EVPN gateway
Configuration restrictions and guidelines
Configuring a distributed EVPN gateway
Configuration restrictions and guidelines
Configuring an L3 VXLAN ID for a VSI interface
Configuring IP prefix route advertisement
Managing remote MAC address entries and remote ARP learning
Disabling remote MAC address learning and remote ARP learning
Disabling MAC address advertisement
Disabling learning of MAC addresses from ARP information
Enabling BGP EVPN route advertisement to the local site
Confining floods to the local site
Enabling ARP flood suppression
Displaying and maintaining EVPN
Centralized EVPN gateway configuration example
EVPN overview
Ethernet Virtual Private Network (EVPN) is a Layer 2 VPN technology that provides both Layer 2 and Layer 3 connectivity between distant network sites across an IP network. EVPN uses MP-BGP in the control plane and VXLAN in the data plane. EVPN is typically used in data centers for multitenant services.
EVPN provides the following benefits:
· Configuration automation—MP-BGP automates VTEP discovery, VXLAN tunnel establishment, and VXLAN tunnel assignment to ease deployment.
· Separation of the control plane and the data plane—EVPN uses MP-BGP to advertise host reachability information in the control plane and uses VXLAN to forward traffic in the data plane.
· Integrated routing and bridging (IRB)—MP-BGP advertises both Layer 2 and Layer 3 host reachability information to provide optimal forwarding paths and minimize flooding.
EVPN network model
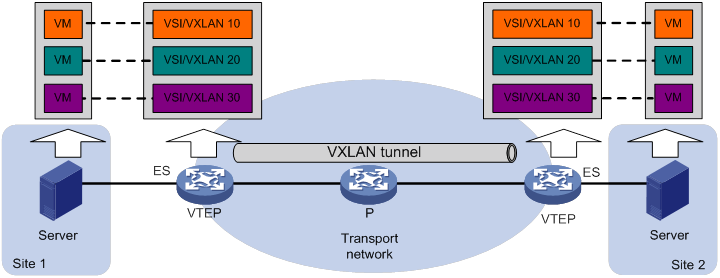
As shown in Figure 1, EVPN uses the VXLAN technology for traffic forwarding in the data plane. The transport edge devices assign VMs to different VXLANs, and then forward traffic between sites for VMs by using VXLAN tunnels. The transport edge devices are VXLAN tunnel endpoints (VTEPs). They can be servers that host VMs or independent network devices.
A VTEP uses ESs, VSIs, and VXLAN tunnels to provide VXLAN services:
· Ethernet segment (ES)—An ES is a link that connects a site to a VTEP. Each ES is uniquely identified by an Ethernet segment identifier (ESI). A site can be connected to a VTEP through only one ES. The ES uses ESI 0.
· VSI—A virtual switch instance is a virtual Layer 2 switched domain. Each VSI provides switching services only for one VXLAN. VSIs learn MAC addresses and forward frames independently of one another. VMs in different sites have Layer 2 connectivity if they are in the same VXLAN. A VXLAN is identified by a 24-bit VXLAN ID which is also called the virtual network identifier (VNI). A VXLAN corresponds to an EVPN instance.
· VXLAN tunnel—Logical point-to-point tunnels between VTEPs over the transport network. Each VXLAN tunnel can trunk multiple VXLANs.
All VXLAN processing is performed on VTEPs. The ingress VTEP encapsulates VXLAN traffic in the VXLAN, outer UDP, and outer IP headers, and forwards the traffic through VXLAN tunnels. The egress VTEP removes the VXLAN encapsulation and forwards the traffic to the destination. Transport network devices (for example, the P device in Figure 1) forward VXLAN traffic only based on the outer IP header of VXLAN packets.
Layered transport network
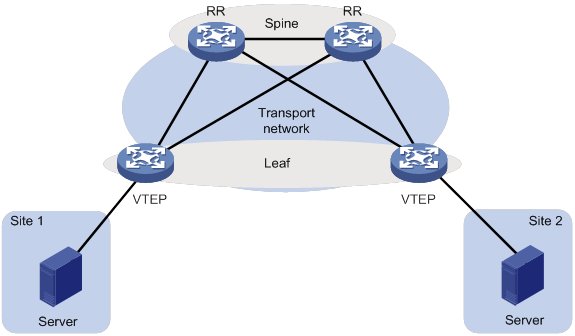
As shown in Figure 2, typically the EVPN transport network uses a layered structure. On the transport network, leaf nodes act as VTEPs to provide VXLAN services, and spine nodes perform forwarding for VXLAN traffic based on the outer IP header. If all VTEPs and transport network devices of an EVPN network belong to the same AS, the spine nodes can act as route reflectors (RRs) to reflect routes between the VTEPs. In this scenario, the spine nodes advertise and receive BGP EVPN routes, but do not perform VXLAN encapsulation and de-encapsulation.
Figure 2 Layered transport network
MP-BGP extension for EVPN
To support EVPN, MP-BGP introduces the EVPN subsequent address family under the L2VPN address family and the following network layer reachability information (BGP EVPN routes):
· Ethernet auto-discovery route—Advertises ES information in multihomed sites.
· MAC/IP advertisement route—Advertises MAC reachability information and host route information (host ARP information).
· Inclusive multicast Ethernet tag (IMET) route—Advertises VTEP and VXLAN mappings for automating VTEP discovery, VXLAN tunnel establishment, and VXLAN tunnel assignment.
· Ethernet segment route—Advertises ES and VTEP mappings.
· IP prefix advertisement route—Advertises BGP IPv4 unicast routes as IP prefixes.
Generation of Ethernet auto-discovery routes and Ethernet segment routes is not supported in the current software version.
MP-BGP uses the route distinguisher (RD) field to differentiate BGP EVPN routes of different VXLANs and uses route targets to control the advertisement and acceptance of BGP EVPN routes. MP-BGP supports the following types of route targets:
· Export targets—A VTEP sets the export targets for BGP EVPN routes learned from the local site before advertising them to remote VTEPs.
· Import targets—A VTEP checks the export targets of BGP EVPN routes received from remote VTEPs. The VTEP imports the BGP EVPN routes only when their export targets match the local import targets.
Configuration automation
VTEPs use BGP EVPN routes to discover VTEP neighbors, establish VXLAN tunnels, and assign the tunnels to VXLANs.
· IMET route—VTEPs advertise the VXLAN IDs they have through IMET routes. If two VTEPs have the same VXLAN ID, they automatically establish a VXLAN tunnel and assign the tunnel to the VXLAN.
· MAC/IP advertisement route and IP prefix advertisement route—In the EVPN gateway deployment, VTEPs advertise MAC/IP advertisement routes or IP prefix advertisement routes which carry export targets. When a VTEP receives a route, it compares the export targets of the route with the local import targets. If the route targets match, the VTEP establishes a VXLAN tunnel with the remote VTEP and associates the tunnel with the L3 VXLAN ID of the corresponding VPN instance. For more information about the L3 VXLAN ID, see "Distributed EVPN gateway deployment."
Assignment of traffic to VXLANs
Traffic from the local site to a remote site
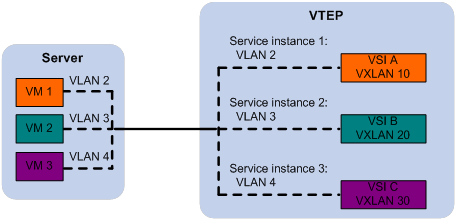
The VTEP uses an Ethernet service instance to match a list of VLANs on a site-facing interface. The VTEP assigns customer traffic to a VXLAN by mapping the Ethernet service instance to a VSI. An Ethernet service instance is identical to an attachment circuit (AC) in L2VPN.
As shown in Figure 3, Ethernet service instance 1 matches VLAN 2 and is mapped to VSI A (VXLAN 10). When a frame from VLAN 2 arrives, the VTEP assigns the frame to VXLAN 10, and looks up VSI A's MAC address table for the outgoing interface.
Figure 3 Identifying traffic from the local site
Traffic from a remote site to the local site
When a VXLAN packet arrives at a VXLAN tunnel interface, the VTEP uses the VXLAN ID in the packet to identify its VXLAN.
Layer 2 forwarding
MAC learning
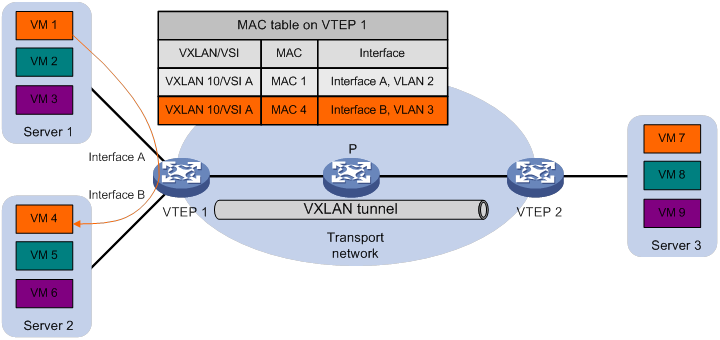
The VTEP performs Layer 2 forwarding based on a VSI's MAC address table. The VTEP learns MAC addresses by using the following methods:
· Local MAC learning—The VTEP automatically learns the source MAC addresses of frames sent from the local site. The outgoing interfaces of local MAC address entries are site-facing interfaces on which the MAC addresses are learned.
· Remote MAC learning—The VTEP uses MP-BGP to advertise local MAC reachability information to remote sites and learn MAC reachability information from remote sites. The outgoing interfaces of MAC address entries advertised from a remote site are VXLAN tunnel interfaces.
Unicast
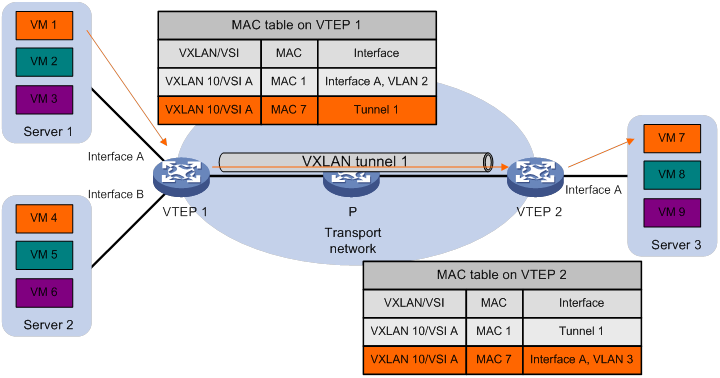
As shown in Figure 4, the VTEP performs typical Layer 2 forwarding for known unicast traffic within the local site.
As shown in Figure 5, the following process applies to a known unicast frame between sites:
1. The source VTEP encapsulates the Ethernet frame in the VXLAN/UDP/IP header.
In the outer IP header, the source IP address is the source VTEP's VXLAN tunnel source IP address. The destination IP address is the VXLAN tunnel destination IP address.
2. The source VTEP forwards the encapsulated packet out of the outgoing VXLAN tunnel interface found in the VSI's MAC address table.
3. The intermediate transport devices (P devices) forward the packet to the destination VTEP by using the outer IP header.
4. The destination VTEP removes the headers on top of the inner Ethernet frame. It then performs MAC address table lookup in the VXLAN's VSI to forward the frame out of the matching outgoing interface.
Flood
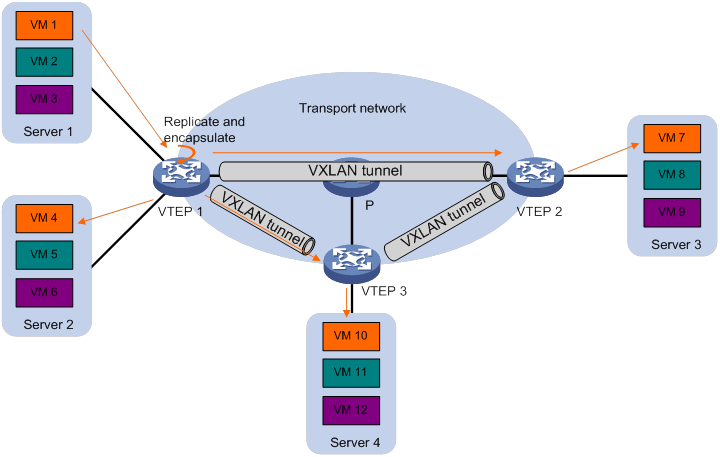
As shown in Figure 6, a VTEP floods a broadcast, multicast, or unknown unicast frame to all site-facing interfaces and VXLAN tunnels in the VXLAN, except for the incoming interface. The source VTEP replicates the flood frame, and then sends one replica to the destination IP address of each VXLAN tunnel in the VXLAN. Each destination VTEP floods the inner Ethernet frame to all the site-facing interfaces in the VXLAN. To avoid loops, the destination VTEPs do not flood the frame to VXLAN tunnels.
Figure 6 Forwarding of flood traffic
Layer 3 forwarding
EVPN uses EVPN gateways to provide Layer 3 forwarding services for hosts in VXLANs. EVPN provides the following EVPN gateway placement designs:
· Centralized EVPN gateway deployment—Use one VTEP to provide Layer 3 forwarding for VXLANs. Typically, the gateway-collocated VTEP connects to other VTEPs and the external network. To use this design, make sure the gateway has sufficient bandwidth and processing capability.
· Distributed EVPN gateway deployment—Deploy one EVPN gateway on each VTEP to provide Layer 3 forwarding for VXLANs at their respective sites. This design distributes the Layer 3 traffic load across VTEPs. However, its configuration is more complex than the centralized EVPN gateway design.
In either design, the gateways use virtual Layer 3 VSI interfaces as gateway interfaces for VXLANs.
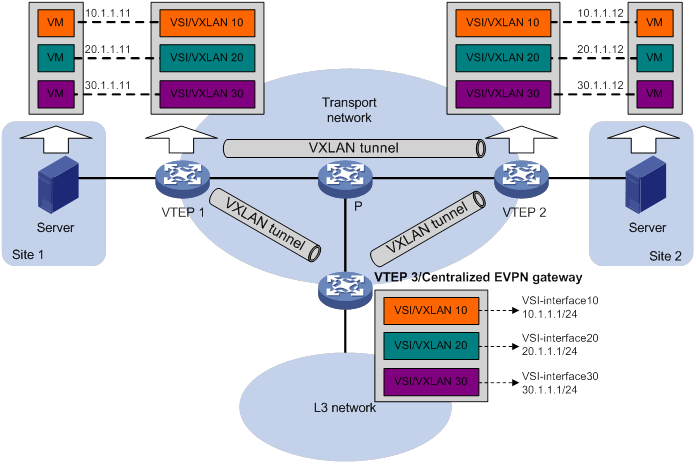
Centralized EVPN gateway deployment
As shown in Figure 7, a VTEP acts as a gateway for VMs in the VXLANs. The VTEP both terminates the VXLANs and performs Layer 3 forwarding for the VMs. The network uses the following process to forward Layer 3 traffic from a VM to the destination:
1. The VM sends an ARP request to obtain the MAC address of the VSI interface that acts as the gateway, and then sends the Layer 3 traffic to the centralized EVPN gateway.
2. The local VTEP looks up the matching VSI's MAC address table and forwards the traffic to the centralized EVPN gateway through a VXLAN tunnel.
3. The centralized EVPN gateway removes the VXLAN encapsulation and forwards the traffic at Layer 3.
4. The centralized EVPN gateway forwards the replies sent by the destination node to the VM based on the ARP entry for the VM.
Figure 7 Example of centralized EVPN gateway deployment
Distributed EVPN gateway deployment
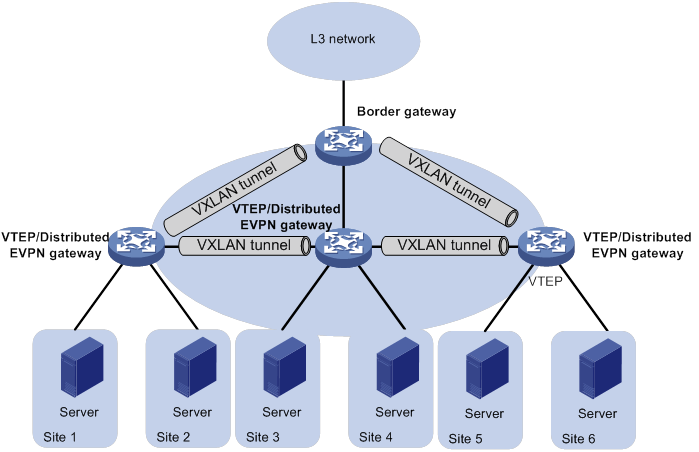
As shown in Figure 8, each site's VTEP acts as a gateway to perform Layer 3 forwarding for the VXLANs of the local site. A VTEP acts as a border gateway to the Layer 3 network for the VXLANs.
Figure 8 Distributed EVPN gateway placement design
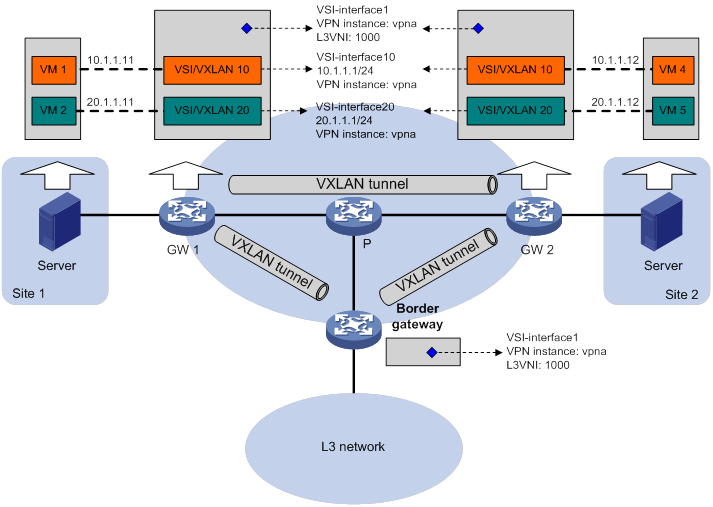
A distributed EVPN gateway uses symmetric IRB for Layer 3 forwarding, which means both the ingress and egress gateways perform Layer 2 and Layer 3 lookups. Symmetric IRB introduces the following concepts:
· L3 VXLAN ID—Also called L3 VNI. An L3 VXLAN ID uniquely identifies a tenant VPN instance. Distributed EVPN gateways use L3 VXLAN IDs to differentiate tenant traffic received from VXLAN tunnel interfaces.
· Router MAC address—Each distributed EVPN gateway has a unique router MAC address used for inter-gateway forwarding. The MAC addresses in the inner Ethernet header of VXLAN packets are router MAC addresses of distributed EVPN gateways.
As shown in Figure 9, each distributed EVPN gateway has the following types of VSI interfaces:
· VSI interface as a gateway interface of a VXLAN—The VSI interface acts as the gateway interface for VMs in a VXLAN. The VSI interface is associated with a VSI and a VPN instance. On different distributed EVPN gateways, the VSI interface of a VXLAN use the same IP address to provide services.
· VSI interface associated with an L3 VXLAN ID—The VSI interface is associated with a VPN instance and assigned an L3 VXLAN ID. VSI interfaces associated with the same VPN instance share an L3 VXLAN ID.
A border gateway only has VSI interfaces that are associated with an L3 VXLAN ID.
Figure 9 Example of distributed EVPN gateway deployment
Layer 3 forwarding entry learning
A distributed EVPN gateway forwards Layer 3 traffic based on FIB entries generated from BGP EVPN routes and ARP information.
A VTEP advertises an external route imported in the EVPN address family through MP-BGP. A remote VTEP adds the route to the FIB table of a VPN instance based on the L3 VXLAN ID carried in the route. In the FIB entry, the outgoing interface is a VXLAN tunnel interface, and the next hop is the peer VTEP address in the NEXT_HOP attribute of the route.
A VTEP has the following types of ARP information:
· Local ARP information—ARP information of VMs in the local site. The VTEP snoops GARP packets, RARP packets, and ARP requests for the gateway MAC address to learn the ARP information of the senders and generates ARP entries and FIB entries. In an ARP or FIB entry, the outgoing interface is the site-facing interface where the packet is received, and the VPN instance is the instance associated with the corresponding VSI interface.
· Remote ARP information—ARP information of VMs in remote sites. Each VTEP uses MP-BGP to advertise its local ARP information with L3 VXLAN IDs in routes to remote sites. A VTEP generates only FIB entries for the remote ARP information. A FIB entry contains the following information:
? Outgoing interface: VSI interface associated with the L3 VXLAN ID.
? Next hop: Peer VTEP address in the NEXT_HOP attribute of the route.
? VPN instance: VPN instance associated with the L3 VXLAN ID.
The VTEP then creates an ARP entry for the next hop in the FIB entry.
Traffic forwarding
A distributed EVPN gateway can work in one of the following mode:
· Switching and routing mode—Forwards Layer 2 traffic based on the MAC address table and forwards Layer 3 traffic based on the FIB table. In this mode, you need to enable ARP flood suppression on the distributed EVPN gateway to reduce flooding.
· Routing mode— Forwards both Layer 2 and Layer 3 traffic based on the FIB table. In this mode, you need to enable local proxy ARP on the distributed EVPN gateway.
For more information about MAC address table-based Layer 2 forwarding, see "Unicast."
Figure 10 shows the intra-site Layer 3 forwarding process.
1. The source VM sends an ARP request to obtain the MAC address of the destination VM.
2. The gateway replies to the source VM with the MAC address of the VSI interface associated with the source VM's VSI.
3. The source VM sends a Layer 3 packet to the gateway.
4. The gateway looks up the FIB table of the VPN instance associated with the source VM's VSI and finds the matching outgoing site-facing interface.
5. The gateway processes the Ethernet header of the Layer 3 packet as follows:
? Replaces the destination MAC address with the destination VM's MAC address.
? Replaces the source MAC address with the VSI interface's MAC address.
6. The gateway forwards the Layer 3 packet to the destination VM.
Figure 10 Intra-site Layer 3 forwarding
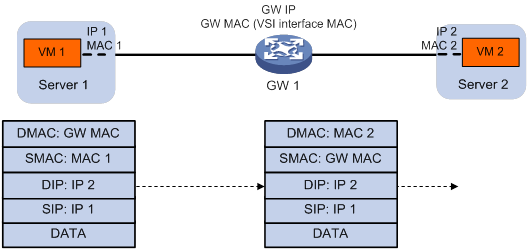
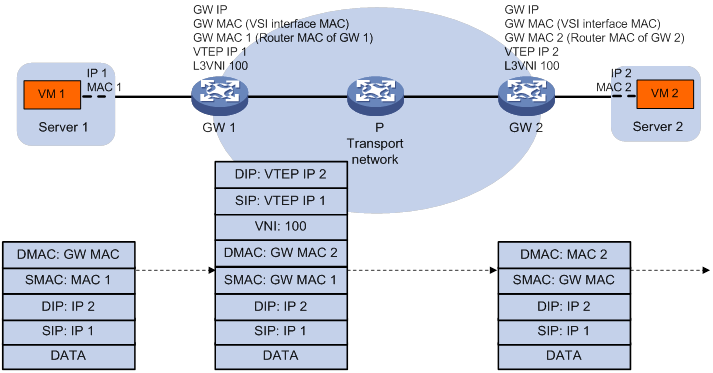
Figure 11 shows the inter-site Layer 3 forwarding process.
1. The source VM sends an ARP request to obtain the MAC address of the destination VM.
2. The gateway replies to the source VM with the MAC address of the VSI interface associated with the source VM's VSI.
3. The source VM sends a Layer 3 packet to the gateway.
4. The gateway looks up the FIB table of the VPN instance associated with the source VM's VSI and finds the matching outgoing VSI interface.
5. The gateway processes the Ethernet header of the Layer 3 packet as follows:
? Replaces the destination MAC address with the destination gateway's router MAC address.
? Replaces the source MAC address with its own router MAC address.
6. The gateway adds VXLAN encapsulation to the Layer 3 packet and forwards the packet to the destination gateway. The encapsulated VXLAN ID is the L3 VXLAN ID of the corresponding VPN instance.
7. The destination gateway identifies the VPN instance of the packet based on the L3 VXLAN ID and removes the VXLAN encapsulation. Then the gateway forwards the packet based on the matching ARP entry.
Figure 11 Inter-site Layer 3 forwarding
ARP flood suppression
ARP flood suppression reduces ARP request broadcasts by enabling the VTEP to reply to ARP requests on behalf of VMs.
As shown in Figure 12, this feature snoops ARP requests, ARP responses, and BGP EVPN routes to populate the ARP flood suppression table with local and remote MAC addresses. If an ARP request has a matching entry, the VTEP replies to the request on behalf of the VM. If no match is found, the VTEP floods the request to both local and remote sites.
Figure 12 ARP flood suppression
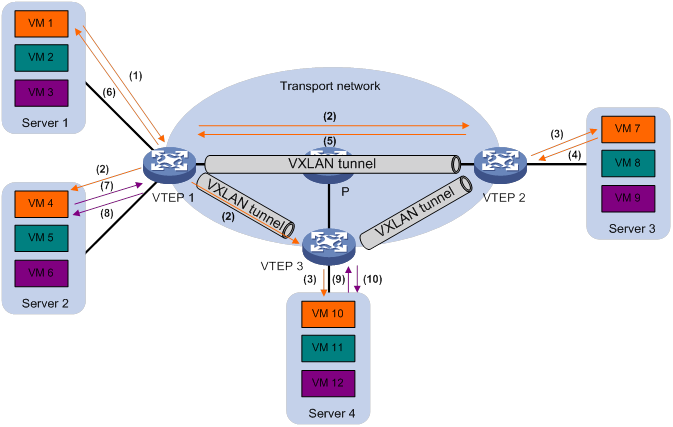
ARP flood suppression uses the following workflow:
1. VM 1 sends an ARP request to obtain the MAC address of VM 7.
2. VTEP 1 creates a suppression entry for VM 1, and floods the ARP request in the VXLAN.
3. VTEP 2 and VTEP 3 de-encapsulate the ARP request. The VTEPs create a suppression entry for VM 1, and broadcast the request in the local site.
4. VM 7 sends an ARP reply.
5. VTEP 2 creates a suppression entry for VM 7 and forwards the ARP reply to VTEP 1.
6. VTEP 1 de-encapsulates the ARP reply, creates a suppression entry for VM 7, and forwards the ARP reply to VM 1.
7. VM 4 sends an ARP request to obtain the MAC address of VM 1 or VM 7.
8. VTEP 1 creates a suppression entry for VM 4 and replies to the ARP request.
9. VM 10 sends an ARP request to obtain the MAC address of VM 1.
10. VTEP 3 creates a suppression entry for VM 10 and replies to the ARP request.
MAC mobility
MAC mobility refers to that a VM or host moves from one ES to another. The source VTEP is unaware of the MAC move event. To notify other VTEPs of the change, the destination VTEP advertises a MAC/IP advertisement route for the MAC address. The source VTEP withdraws the old route for the MAC address after receiving the new route. The MAC/IP advertisement route has a sequence number that increases when the MAC address moves. The sequence number identifies the most recent move if the MAC address moves multiple times.
Configuring EVPN
Configuration restrictions and guidelines
Before you can configure EVPN, you must perform the following tasks:
1. Set the system operating mode to standard or advanced by using the system-working-mode command in system view.
2. Save the configuration.
3. Reboot the device.
For more information about setting the system operating mode, see device management in Fundamentals Configuration Guide.
Make sure the following VXLAN tunnels are not associated with the same VXLAN when they have the same tunnel destination IP address:
· A VXLAN tunnel automatically created by EVPN.
· A manually created VXLAN tunnel.
For more information about manual VXLAN tunnel setup, see VXLAN Configuration Guide.
EVPN configuration task list
|
Tasks at a glance |
Remarks |
|
(Required.) Setting the forwarding mode for VXLANs |
N/A |
|
(Required) Creating a VXLAN on a VSI |
N/A |
|
(Required) Configuring an EVPN instance |
N/A |
|
(Required) Configuring BGP to advertise EVPN routes |
N/A |
|
Perform this task to assign customer traffic to VXLANs. |
|
|
(Optional.) Configuring an EVPN gateway: |
Perform this task to provide Layer 3 connectivity for VXLANs. |
|
(Optional.) Managing remote MAC address entries and remote ARP learning |
N/A |
|
(Optional.) Enabling BGP EVPN route advertisement to the local site |
Perform this task to advertise private BGP EVPN routes to the local site. |
|
(Optional.) Confining floods to the local site |
Perform this task to reduce flooding to the transport network. |
|
(Optional.) Enabling ARP flood suppression |
Perform this task to reduce ARP request broadcasts. |
Setting the forwarding mode for VXLANs
Enable Layer 3 forwarding mode if you want to use the device as an EVPN gateway. Enable Layer 2 or Layer 3 forwarding mode if you want to use the device as a VTEP.
Configuration restrictions and guidelines
When you set the VXLAN forwarding mode, follow these restrictions and guidelines:
· If you enable Layer 3 forwarding for VXLANs, the tagging status of VXLAN packets is not determined by the link type of the outgoing interface. You must set the tagging mode of VXLAN packets.
? Set the tagging mode to untagged if the following requirements are met:
- The link type of the outgoing interface is access, trunk, or hybrid.
- VXLAN packets are transmitted to the next hop through the PVID of the outgoing interface.
? Set the tagging mode to tagged if the following requirements are met:
- The link type of the outgoing interface is trunk or hybrid.
- VXLAN packets are transmitted to the next hop through a VLAN other than the PVID of the outgoing interface.
· You must delete all VSIs, VSI interfaces, and VXLAN tunnel interfaces before you can change the forwarding mode.
· You must delete all VXLAN tunnel interfaces before you can change the tagging mode of VXLAN packets.
Configuration procedure
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable Layer 2 or Layer 3 forwarding for VXLANs. |
·
Enable Layer 2 forwarding: ·
Enable Layer 3 forwarding: |
By default, Layer 3 forwarding is enabled for VXLANs. If you do not set the tagging mode, the untagged mode is used. For more information about this command, see VXLAN Command Reference. |
Creating a VXLAN on a VSI
For more information about the VXLAN commands in this task, see VXLAN Command Reference.
To create a VXLAN on a VSI:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable L2VPN. |
l2vpn enable |
By default, L2VPN is disabled. |
|
3. Create a VSI and enter VSI view. |
vsi vsi-name |
By default, no VSIs exist. |
|
4. (Optional.) Configure a VSI description. |
description text |
By default, a VSI does not have a description. |
|
5. Enable the VSI. |
undo shutdown |
By default, a VSI is enabled. |
|
6. Create a VXLAN and enter VXLAN view. |
vxlan vxlan-id |
By default, no VXLANs exist. You can create only one VXLAN on a VSI. The VXLAN ID must be unique for each VSI. |
Configuring an EVPN instance
You do not need to associate a VPN instance with a VXLAN that requires only Layer 2 connectivity. The BGP EVPN routes advertised by the device carry the RD and route targets configured for the EVPN instance associated with the VXLAN.
To configure an EVPN instance:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VSI view. |
vsi vsi-name |
N/A |
|
3. Create an EVPN instance and enter EVPN instance view. |
evpn encapsulation vxlan |
By default, no EVPN instance exists. |
|
4. Configure an RD for the EVPN instance. |
route-distinguisher { route-distinguisher | auto } |
By default, no RD is configured for an EVPN instance. |
|
5. Configure route targets for the EVPN instance. |
vpn-target { vpn-target&<1-8> | auto } [ both | export-extcommunity | import-extcommunity ] |
By default, an EVPN instance does not have route targets. Make sure the following requirements are met: · The import targets of the EVPN instance do not match the export targets of the VPN instance associated with the VXLAN. · The export targets of the EVPN instance do not match the import targets of the VPN instance associated with the VXLAN. For more information about VPN instance configuration, see "Configuring an L3 VXLAN ID for a VSI interface." |
Configuring BGP to advertise EVPN routes
For more information about the following BGP commands, see Layer 3—IP Routing Command Reference:
· peer allow-as-loop
· peer as-number
· peer enable
· peer reflect-client
· reflect between-clients
· reflector cluster-id
· refresh bgp
· reset bgp
To configure BGP to advertise EVPN routes:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a global router ID. |
router id router-id |
By default, no global router ID is configured. |
|
3. Enable a BGP instance and enter BGP instance view. |
bgp as-number [ instance instance-name ] [ multi-session-thread ] |
By default, BGP is disabled and no BGP instances exist. |
|
4. Specify remote VTEPs as BGP peers. |
peer { group-name | ipv4-address [ mask-length ] } as-number as-number |
By default, no BGP peers are specified. |
|
5. Create the BGP EVPN address family and enter BGP EVPN address family view. |
address-family l2vpn evpn |
By default, the BGP EVPN address family does not exist. |
|
6. Enable BGP to exchange BGP EVPN routes with a peer or peer group. |
peer { group-name | ipv4-address [ mask-length ] } enable |
By default, BGP does not exchange BGP EVPN routes with peers. |
|
7. (Optional.) Permit the local AS number to appear in routes from a peer or peer group and set the number of appearances. |
peer { group-name | ipv4-address [ mask-length ] } allow-as-loop [ number ] |
By default, the local AS number is not allowed in routes from peers. |
|
8. (Optional.) Enable route target filtering for BGP EVPN routes. |
policy vpn-target |
By default, route target filtering is enabled for BGP EVPN routes. |
|
9. (Optional.) Configure the device as an RR and specify a peer or peer group as its client. |
peer { group-name | ipv4-address [ mask-length ] } reflect-client |
By default, no RR or client is configured. |
|
10. (Optional.) Enable EVPN route reflection between clients. |
reflect between-clients |
By default, EVPN route reflection between clients is enabled. |
|
11. (Optional.) Configure the cluster ID of the RR. |
reflector cluster-id { cluster-id | ipv4-address } |
By default, an RR uses its own router ID as the cluster ID. |
|
12. (Optional.) Create a reflection policy for the RR to filter reflected BGP EVPN routes. |
rr-filter ext-comm-list-number |
By default, an RR does not filter reflected BGP EVPN routes. |
|
13. (Optional.) Configure the device to not change the next hop of routes advertised to an EBGP peer or peer group. |
peer { group-name | ipv4-address [ mask-length ] } next-hop-invariable |
By default, the device uses its address as the next hop of routes advertised to EBGP peers. |
|
14. (Optional.) Return to user view. |
return |
N/A |
|
15. (Optional.) Soft-reset BGP sessions of the BGP EVPN address family. |
refresh bgp [ instance instance-name ] { ipv4-address [ mask-length ] | all | external | group group-name | internal } { export | import } l2vpn evpn |
N/A |
|
16. (Optional.) Reset BGP sessions of the BGP EVPN address family. |
reset bgp [ instance instance-name ] { as-number | ipv4-address [ mask-length ] | all | external | group group-name | internal } l2vpn evpn |
N/A |
Mapping an Ethernet service instance to a VSI
An Ethernet service instance matches a list of VLANs on a site-facing interface by using a frame match criterion. The frame match criterion specifies the characteristics of traffic from the VLANs, such as tagging status and VLAN IDs. The VTEP assigns traffic from the VLANs to a VXLAN by mapping the Ethernet service instance to a VSI. The VSI performs Layer 2 forwarding for the VLANs based on its MAC address table.
For more information about the VXLAN commands in this task, see VXLAN Command Reference.
To map an Ethernet service instance to a VSI:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
· interface interface-type interface-number · interface bridge-aggregation interface-number |
N/A |
|
3. Create an Ethernet service instance and enter Ethernet service instance view. |
service-instance instance-id |
By default, no Ethernet service instances exist. |
|
4. Configure a frame match criterion. |
·
Match frames that do not match any other
service instance on the interface: ·
Match any 802.1Q untagged frames: ·
Match frames tagged with the specified outer
802.1Q VLAN IDs: ·
Match frames tagged with the specified outer
and inner 802.1Q VLAN IDs: |
By default, an Ethernet service instance does not contain a frame match criterion. You can specify multiple SVLAN IDs or CVLAN IDs only in Ethernet access mode. |
|
5. Map the Ethernet service instance to a VSI. |
xconnect vsi vsi-name [ access-mode { ethernet | vlan } ] [ track track-entry-number&<1-3> ] |
By default, an Ethernet service instance is not mapped to any VSI. |
Configuring a centralized EVPN gateway
Configuration restrictions and guidelines
If the device is a centralized EVPN gateway, you must enable ARP flood suppression on VTEPs. Typically remote ARP learning is disabled in an EVPN network. When ARP requests for the gateway MAC address are sent to the centralized EVPN gateway through VXLAN tunnels, the gateway does not respond to the requests. If ARP flood suppression is disabled on VTEPs, VMs cannot obtain the MAC address of the gateway.
Configuration prerequisites
Before you configure a centralized EVPN gateway, you must enable Layer 3 forwarding for VXLANs.
Configuration procedure
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a VSI interface and enter VSI interface view. |
interface vsi-interface vsi-interface-id |
By default, no VSI interfaces exist. For more information about this command, see VXLAN Command Reference. |
|
3. Assign an IPv4 address to the VSI interface. |
ip address ip-address { mask | mask-length } [ sub ] |
By default, no IPv4 address is assigned to a VSI interface. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enter VSI view. |
vsi vsi-name |
N/A |
|
6. Specify the VSI interface as the gateway interface for the VSI. |
gateway vsi-interface vsi-interface-id |
By default, no gateway interface is specified for a VSI. For more information about this command, see VXLAN Command Reference. |
Configuring a distributed EVPN gateway
Configuration restrictions and guidelines
For a VXLAN to access to the external network, specify the VXLAN's VSI interface on the border gateway as the next hop on distributed EVPN gateways by using one of the following methods:
· Configure a static route.
· Configure a routing policy, and apply the policy by using the apply default-next-hop or apply next-hop command. For more information about configuring routing policies, see routing policy configuration in Layer 3—IP Routing Configuration Guide.
If both ARP flood suppression and local proxy ARP are enabled on a distributed EVPN gateway, only local proxy ARP takes effect. As a best practice, do not use these features together on distributed EVPN gateways.
Configuration prerequisites
Before you configure a distributed EVPN gateway, you must enable Layer 3 forwarding for VXLANs.
Configuring a VSI interface
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a VSI interface and enter VSI interface view. |
interface vsi-interface vsi-interface-id |
By default, no VSI interfaces exist. For more information about this command, see VXLAN Command Reference. |
|
3. Assign an IPv4 address to the VSI interface. |
ip address ip-address { mask | mask-length } [ sub ] |
By default, no IPv4 address is assigned to a VSI interface. You can assign multiple IP addresses to a VSI interface for VSIs to share one gateway interface. |
|
4. Specify the VSI interface as a distributed gateway. |
distributed-gateway local |
By default, a VSI interface is not a distributed gateway. For more information about this command, see VXLAN Command Reference. |
|
5. (Optional.) Enable local proxy ARP. |
local-proxy-arp enable [ ip-range startIP to endIP ] |
By default, local proxy ARP is disabled. For more information about the commands, see Layer 3—IP Services Command Reference. |
|
6. Return to system view. |
quit |
N/A |
|
7. Enter VSI view. |
vsi vsi-name |
N/A |
|
8. Specify the VSI interface as the gateway interface for the VSI. |
gateway vsi-interface vsi-interface-id |
By default, no gateway interface is specified for a VSI. For more information about this command, see VXLAN Command Reference. |
|
9. Assign a subnet to the VSI. |
gateway subnet ipv4-address wildcard-mask |
By default, no subnet exists on a VSI. You must configure this command on VSIs that share a gateway interface. This command enables the VSI interface to identify the VSI of a packet. For VSIs that share a gateway interface, the subnets must be unique. For more information about this command, see VXLAN Command Reference. |
Configuring an L3 VXLAN ID for a VSI interface
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a VPN instance and enter VPN instance view. |
ip vpn-instance vpn-instance-name |
By default, no VPN instances exist. |
|
3. Configure an RD for the VPN instance. |
route-distinguisher route-distinguisher |
By default, no RD is configured for a VPN instance. |
|
4. (Optional.) Configure route targets for the VPN instance. |
vpn-target { vpn-target&<1-8> [ both | export-extcommunity | import-extcommunity ] | auto } |
By default, a VPN instance does not have route targets. |
|
5. (Optional.) Apply an export routing policy to the VPN instance. |
export route-policy route-policy |
By default, no export routing policy is applied to a VPN instance. |
|
6. Enter EVPN view. |
address-family evpn |
N/A |
|
7. Configure route targets for EVPN on the VPN instance. |
vpn-target vpn-target&<1-8> [ both | export-extcommunity | import-extcommunity ] |
By default, EVPN does not have route targets on a VPN instance. Make sure the following requirements are met: · The import targets of EVPN do not match the export targets of the VPN instance. · The export targets of EVPN do not match the import targets of the VPN instance. |
|
8. (Optional.) Apply an export routing policy to EVPN on the VPN instance. |
export route-policy route-policy |
By default, no export routing policy is applied to EVPN on a VPN instance. |
|
9. Return to VPN instance view. |
quit |
N/A |
|
10. Return to system view. |
quit |
N/A |
|
11. Create a VSI interface and enter VSI interface view. |
interface vsi-interface vsi-interface-id |
By default, no VSI interfaces exist. |
|
12. Associate the VSI interface with the VPN instance. |
ip binding vpn-instance vpn-instance-name |
By default, a VSI interface is not associated with a VPN instance. The interface is on the public network. |
|
13. Configure an L3 VXLAN ID for the VSI interface. |
l3-vni vxlan-id |
By default, no L3 VXLAN ID is configured for a VSI interface. A VPN instance can have only one L3 VXLAN ID. If multiple L3 VXLAN IDs are configured for a VPN instance, the VPN instance uses the lowest one. To view the L3 VXLAN ID of a VPN instance, use the display evpn routing-table command. |
Configuring IP prefix route advertisement
If IGP routes are imported to the BGP-VPN IPv4 unicast address family and the corresponding VPN instance has a L3 VXLAN ID, the device advertises the imported routes as IP prefix advertisement routes. These routes carry the RD and route targets configured in VPN instance view or IPv4 VPN view of the VPN instance. If the route targets of the routes match the import targets configured in VPN instance view or IPv4 VPN view of a VPN instance on a remote VTEP, the VTEP accepts the routes and adds the routes to the routing table of the matching VPN instance.
This feature is supported only by distributed EVPN gateway deployment.
For more information about the BGP commands in this task, see Layer 3—IP Routing Command Reference.
To configure IP prefix route advertisement:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable a BGP instance and enter BGP instance view. |
bgp as-number [ instance instance-name ] [ multi-session-thread ] |
By default, BGP is disabled and no BGP instances exist. |
|
3. Enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
N/A |
|
4. Enter BGP-VPN IPv4 unicast address family view. |
address-family ipv4 [ unicast ] |
N/A |
|
5. Enable BGP to redistribute routes from an IGP protocol. |
import-route protocol [ { process-id | all-processes } [ allow-direct | med med-value | route-policy route-policy-name ] * ] |
By default, BGP does not redistribute IGP routes. |
|
6. (Optional.) Enable default route redistribution into the BGP routing table. |
default-route imported |
By default, default route redistribution into the BGP routing table is disabled. |
Managing remote MAC address entries and remote ARP learning
Disabling remote MAC address learning and remote ARP learning
By default, the device learns MAC information and ARP information of remote VMs from packets received on VXLAN tunnel interfaces. The automatically learned remote MAC and ARP information might conflict with the remote MAC and ARP information advertised through BGP. As a best practice to avoid the conflicts, disable remote MAC address learning and remote ARP learning on the device.
For more information about the VXLAN commands in this task, see VXLAN Command Reference.
To disable remote MAC address learning and remote ARP learning:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Disable remote MAC address learning. |
vxlan tunnel mac-learning disable |
By default, remote MAC address learning is enabled. |
|
3. Disable remote ARP learning. |
vxlan tunnel arp-learning disable |
By default, remote ARP learning is enabled. |
Disabling MAC address advertisement
The MAC information and ARP information advertised by the VTEP overlap. To avoid duplication, disable MAC address advertisement and withdraw the MAC addresses advertised to remote VTEPs.
To disable MAC address advertisement:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VSI view. |
vsi vsi-name |
N/A |
|
3. Enter EVPN instance view. |
evpn encapsulation vxlan |
N/A |
|
4. Disable MAC address advertisement and withdraw advertised MAC addresses. |
mac-advertising disable |
By default, MAC address advertisement is enabled. |
Disabling learning of MAC addresses from ARP information
The MAC information and ARP information advertised by a remote VTEP overlap. To avoid duplication, disable the learning of MAC addresses from ARP information. EVPN will learn remote MAC addresses only from the MAC information advertised from remote sites.
To disable learning of MAC addresses from ARP information:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VSI view. |
vsi vsi-name |
N/A |
|
3. Enter EVPN instance view. |
evpn encapsulation vxlan |
N/A |
|
4. Disable the EVPN instance from learning MAC addresses from ARP information. |
arp mac-learning disable |
By default, an EVPN instance learns MAC addresses from ARP information. |
Enabling BGP EVPN route advertisement to the local site
This feature enables the device to advertise private BGP EVPN routes to the local site after the device adds the routes to the routing table of a VPN instance.
To enable BGP EVPN route advertisement to the local site:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP instance view. |
bgp as-number [ instance instance-name ] [ multi-session-thread ] |
N/A |
|
3. Enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
N/A |
|
4. Enter BGP-VPN IPv4 unicast address family view. |
address-family ipv4 [ unicast ] |
N/A |
|
5. Enable BGP EVPN route advertisement to the local site. |
advertise l2vpn evpn |
By default, BGP EVPN route advertisement to the local site is enabled. |
Confining floods to the local site
By default, the VTEP floods broadcast, unknown unicast, and unknown multicast frames received from the local site to the following interfaces in the frame's VXLAN:
· All site-facing interfaces except for the incoming interface.
· All VXLAN tunnel interfaces.
To confine a kind of flood traffic to the site-facing interfaces, disable flooding for that kind of flood traffic on the VSI bound to the VXLAN. The VSI will not flood the corresponding frames to VXLAN tunnel interfaces.
For more information about the VXLAN commands in this task, see VXLAN Command Reference.
To confine floods to site-facing interfaces for a VXLAN:
|
Step |
Command |
Remarks |
|
|
1. Enter system view. |
system-view |
N/A |
|
|
2. Enter VSI view. |
vsi vsi-name |
N/A |
|
|
3. Disable flooding for the VSI. |
flooding disable { all | { broadcast | unknown-multicast | unknown-unicast } * } |
By default, flooding is enabled for a VSI. The unknown-multicast or unknown-unicast keyword cannot be used alone. You must specify both of them. |
|
|
4. (Optional.) Enable selective flood for a MAC address. |
selective-flooding mac-address mac-address |
By default, selective flood is disabled. Use this feature to exclude a remote unicast or multicast MAC address from the flood suppression done by using the flooding disable command. The VTEP will flood the frames destined for the specified MAC address to remote sites when floods are confined to the local site. |
|
Enabling ARP flood suppression
Use ARP flood suppression to reduce ARP request broadcasts.
The aging timer is fixed at 25 minutes for ARP flood suppression entries. If the flooding disable command is configured, set the MAC aging timer to a higher value than the aging timer for ARP flood suppression entries on all VTEPs. This setting prevents the traffic blackhole that occurs when a MAC address entry ages out before its ARP flood suppression entry ages out. To set the MAC aging timer, use the mac-address timer command.
When remote ARP learning is disabled for VXLANs, the device does not use ARP flood suppression entries to respond to ARP requests received on VXLAN tunnels. To disable remote ARP learning for VXLANs, use the vxlan tunnel arp-learning disable command.
To enable ARP flood suppression:
|
Step |
Command |
Remarks |
|
|
1. Enter system view. |
system-view |
N/A |
|
|
2. Enter VSI view. |
vsi vsi-name |
N/A |
|
|
3. Enable ARP flood suppression. |
arp suppression enable |
By default, ARP flood suppression is disabled. For more information about this command, see VXLAN Command Reference. |
|
Displaying and maintaining EVPN
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display BGP peer group information. |
display bgp [ instance instance-name ] group l2vpn evpn [ group-name group-name ] |
|
Display BGP EVPN routes. |
display bgp [ instance instance-name ] l2vpn evpn [ peer ipv4-address { advertised-routes | received-routes } [ statistics ] | route-distinguisher route-distinguisher [ route-type { auto-discovery | es | imet | ip-prefix | mac-ip } ] [ evpn-route route-length [ advertise-info ] ] | route-type { auto-discovery | es | imet | ip-prefix | mac-ip } | statistics ] |
|
Display BGP peer or peer group information. |
display bgp [ instance instance-name ] peer l2vpn evpn [ ipv4-address mask-length | { ipv4-address | group-name group-name } log-info | [ ipv4-address ] verbose ] |
|
Display information about BGP update groups. |
display bgp [ instance instance-name ] update-group l2vpn evpn [ ipv4-address ] |
|
Display information about peers that are automatically discovered through BGP. |
display evpn auto-discovery { imet [ peer ip-address] [ vsi vsi-name ] | macip-prefix [ nexthop next-hop ] [ count ] } |
|
Display EVPN MAC address entries. |
display evpn route mac [ local | remote ] [ vsi vsi-name ] [ count ] |
|
Display EVPN ARP entries. |
display evpn route arp [ local | remote ] [ vpn-instance vpn-instance-name ] [ count ] |
|
Display ARP flood suppression entries. |
display evpn route arp suppression [ local | remote ] [ vsi vsi-name ] [ count ] |
|
Display the routing table for a VPN instance. |
display evpn routing-table vpn-instance vpn-instance-name [ count ] |
|
|
NOTE: For more information about the display bgp group, display bgp peer, and display bgp update-group commands, see BGP commands in Layer 3—IP Routing Command Reference. |
EVPN configuration examples
Centralized EVPN gateway configuration example
Network requirements
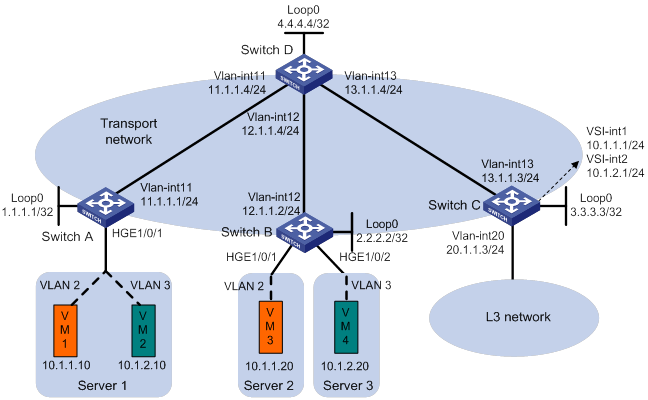
As shown in Figure 13:
· Configure VXLAN 10 and VXLAN 20 on Switch A, Switch B, and Switch C to provide connectivity for the VMs in the VXLANs across the network sites.
· Configure Switch C as a centralized EVPN gateway to provide gateway services and access to the connected Layer 3 network.
· Configure Switch D as an RR to reflect BGP EVPN routes between Switch A, Switch B, and Switch C.
Configuration procedure
1. On VM 1 and VM 3, specify 10.1.1.1 as the gateway address. On VM 2 and VM 4, specify 10.1.2.1 as the gateway address. (Details not shown.)
2. Configure IP addresses and unicast routing settings:
# Assign IP addresses to interfaces, as shown in Figure 13. (Details not shown.)
# Configure OSPF on all transport network switches (Switches A through D) for them to reach one another. (Details not shown.)
3. Configure Switch A:
# Enable L2VPN.
<SwitchA> system-view
[SwitchA] l2vpn enable
# Enable Layer 2 forwarding for VXLANs.
[SwitchA] undo vxlan ip-forwarding
# Disable remote MAC address learning.
[SwitchA] vxlan tunnel mac-learning disable
# Create an EVPN instance on VSI vpna, and configure the switch to automatically generate an RD and a route target for the EVPN instance.
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] arp suppression enable
[SwitchA-vsi-vpna] evpn encapsulation vxlan
[SwitchA-vsi-vpna-evpn-vxlan] route-distinguisher auto
[SwitchA-vsi-vpna-evpn-vxlan] vpn-target auto
[SwitchA-vsi-vpna-evpn-vxlan] quit
# Create VXLAN 10.
[SwitchA-vsi-vpna] vxlan 10
[SwitchA-vsi-vpna-vxlan-10] quit
[SwitchA-vsi-vpna] quit
# Create an EVPN instance on VSI vpnb, and configure the switch to automatically generate an RD and a route target for the EVPN instance.
[SwitchA] vsi vpnb
[SwitchA-vsi-vpnb] arp suppression enable
[SwitchA-vsi-vpnb] evpn encapsulation vxlan
[SwitchA-vsi-vpnb-evpn-vxlan] route-distinguisher auto
[SwitchA-vsi-vpnb-evpn-vxlan] vpn-target auto
[SwitchA-vsi-vpnb-evpn-vxlan] quit
# Create VXLAN 20.
[SwitchA-vsi-vpnb] vxlan 20
[SwitchA-vsi-vpnb-vxlan-20] quit
[SwitchA-vsi-vpnb] quit
# Configure BGP to advertise EVPN routes.
[SwitchA] bgp 200
[SwitchA-bgp-default] peer 4.4.4.4 as-number 200
[SwitchA-bgp-default] peer 4.4.4.4 connect-interface loopback 0
[SwitchA-bgp-default] address-family l2vpn evpn
[SwitchA-bgp-default-evpn] peer 4.4.4.4 enable
[SwitchA-bgp-default-evpn] quit
[SwitchA-bgp-default] quit
# On HundredGigE 1/0/1, create Ethernet service instance 1000 to match VLAN 2.
[SwitchA] interface hundredgige 1/0/1
[SwitchA-HundredGigE1/0/1] service-instance 1000
[SwitchA-HundredGigE1/0/1-srv1000] encapsulation s-vid 2
# Map Ethernet service instance 1000 to VSI vpna.
[SwitchA-HundredGigE1/0/1-srv1000] xconnect vsi vpna
[SwitchA-HundredGigE1/0/1-srv1000] quit
# On HundredGigE 1/0/1, create Ethernet service instance 2000 to match VLAN 3.
[SwitchA-HundredGigE1/0/1] service-instance 2000
[SwitchA-HundredGigE1/0/1-srv2000] encapsulation s-vid 3
# Map Ethernet service instance 2000 to VSI vpnb.
[SwitchA-HundredGigE1/0/1-srv2000] xconnect vsi vpnb
[SwitchA-HundredGigE1/0/1-srv2000] quit
[SwitchA-HundredGigE1/0/1] quit
4. Configure Switch B:
# Enable L2VPN.
<SwitchB> system-view
[SwitchB] l2vpn enable
# Enable Layer 2 forwarding for VXLANs.
[SwitchB] undo vxlan ip-forwarding
# Disable remote MAC address learning.
[SwitchB] vxlan tunnel mac-learning disable
# Create an EVPN instance on VSI vpna, and configure the switch to automatically generate an RD and a route target for the EVPN instance.
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] arp suppression enable
[SwitchB-vsi-vpna] evpn encapsulation vxlan
[SwitchB-vsi-vpna-evpn-vxlan] route-distinguisher auto
[SwitchB-vsi-vpna-evpn-vxlan] vpn-target auto
[SwitchB-vsi-vpna-evpn-vxlan] quit
# Create VXLAN 10.
[SwitchB-vsi-vpna] vxlan 10
[SwitchB-vsi-vpna-vxlan-10] quit
[SwitchB-vsi-vpna] quit
# Create an EVPN instance on VSI vpnb, and configure the switch to automatically generate an RD and a route target for the EVPN instance.
[SwitchB] vsi vpnb
[SwitchB-vsi-vpnb] arp suppression enable
[SwitchB-vsi-vpnb] evpn encapsulation vxlan
[SwitchB-vsi-vpnb-evpn-vxlan] route-distinguisher auto
[SwitchB-vsi-vpnb-evpn-vxlan] vpn-target auto
[SwitchB-vsi-vpnb-evpn-vxlan] quit
# Create VXLAN 20.
[SwitchB-vsi-vpnb] vxlan 20
[SwitchB-vsi-vpnb-vxlan-20] quit
[SwitchB-vsi-vpnb] quit
# Configure BGP to advertise EVPN routes.
[SwitchB] bgp 200
[SwitchB-bgp-default] peer 4.4.4.4 as-number 200
[SwitchB-bgp-default] peer 4.4.4.4 connect-interface loopback 0
[SwitchB-bgp-default] address-family l2vpn evpn
[SwitchB-bgp-default-evpn] peer 4.4.4.4 enable
[SwitchB-bgp-default-evpn] quit
[SwitchB-bgp-default] quit
# On HundredGigE 1/0/1, create Ethernet service instance 1000 to match VLAN 2.
[SwitchB] interface hundredgige 1/0/1
[SwitchB-HundredGigE1/0/1] service-instance 1000
[SwitchB-HundredGigE1/0/1-srv1000] encapsulation s-vid 2
# Map Ethernet service instance 1000 to VSI vpna.
[SwitchB-HundredGigE1/0/1-srv1000] xconnect vsi vpna
[SwitchB-HundredGigE1/0/1-srv1000] quit
[SwitchB-HundredGigE1/0/1] quit
# On HundredGigE 1/0/2, create Ethernet service instance 2000 to match VLAN 3.
[SwitchB] interface hundredgige 1/0/2
[SwitchB-HundredGigE1/0/2] service-instance 2000
[SwitchB-HundredGigE1/0/2-srv2000] encapsulation s-vid 3
# Map Ethernet service instance 2000 to VSI vpnb.
[SwitchB-HundredGigE1/0/2-srv2000] xconnect vsi vpnb
[SwitchB-HundredGigE1/0/2-srv2000] quit
[SwitchB-HundredGigE1/0/2] quit
5. Configure Switch C:
# Enable L2VPN.
<SwitchC> system-view
[SwitchC] l2vpn enable
# Disable remote MAC address learning.
[SwitchC] vxlan tunnel mac-learning disable
# Create an EVPN instance on VSI vpna, and configure the switch to automatically generate an RD and a route target for the EVPN instance.
[SwitchC] vsi vpna
[SwitchC-vsi-vpna] evpn encapsulation vxlan
[SwitchC-vsi-vpna-evpn-vxlan] route-distinguisher auto
[SwitchC-vsi-vpna-evpn-vxlan] vpn-target auto
[SwitchC-vsi-vpna-evpn-vxlan] quit
# Create VXLAN 10.
[SwitchC-vsi-vpna] vxlan 10
[SwitchC-vsi-vpna-vxlan-10] quit
[SwitchC-vsi-vpna] quit
# Create an EVPN instance on VSI vpnb, and configure the switch to automatically generate an RD and a route target for the EVPN instance.
[SwitchC] vsi vpnb
[SwitchC-vsi-vpnb] evpn encapsulation vxlan
[SwitchC-vsi-vpnb-evpn-vxlan] route-distinguisher auto
[SwitchC-vsi-vpnb-evpn-vxlan] vpn-target auto
[SwitchC-vsi-vpnb-evpn-vxlan] quit
# Create VXLAN 20.
[SwitchC-vsi-vpnb] vxlan 20
[SwitchC-vsi-vpnb-vxlan-20] quit
[SwitchC-vsi-vpnb] quit
# Configure BGP to advertise EVPN routes.
[SwitchC] bgp 200
[SwitchC-bgp-default] peer 4.4.4.4 as-number 200
[SwitchC-bgp-default] peer 4.4.4.4 connect-interface loopback 0
[SwitchC-bgp-default] address-family l2vpn evpn
[SwitchC-bgp-default-evpn] peer 4.4.4.4 enable
[SwitchC-bgp-default-evpn] quit
[SwitchC-bgp-default] quit
# Create VSI-interface 1 and assign the interface an IP address. The IP address will be used as the gateway address for VXLAN 10.
[SwitchC] interface vsi-interface 1
[SwitchC-Vsi-interface1] ip address 10.1.1.1 255.255.255.0
[SwitchC-Vsi-interface1] quit
# Specify VSI-interface 1 as the gateway interface for VSI vpna.
[SwitchC] vsi vpna
[SwitchC-vsi-vpna] gateway vsi-interface 1
[SwitchC-vsi-vpna] quit
# Create VSI-interface 2 and assign the interface an IP address. The IP address will be used as the gateway address for VXLAN 20.
[SwitchC] interface vsi-interface 2
[SwitchC-Vsi-interface2] ip address 10.1.2.1 255.255.255.0
[SwitchC-Vsi-interface2] quit
# Specify VSI-interface 2 as the gateway interface for VSI vpnb.
[SwitchC] vsi vpnb
[SwitchC-vsi-vpnb] gateway vsi-interface 2
[SwitchC-vsi-vpnb] quit
6. Configure Switch D:
# Establish BGP connections with other transport network switches.
<SwitchD> system-view
[SwitchD] bgp 200
[SwitchD-bgp-default] group evpn
[SwitchD-bgp-default] peer 1.1.1.1 group evpn
[SwitchD-bgp-default] peer 2.2.2.2 group evpn
[SwitchD-bgp-default] peer 3.3.3.3 group evpn
[SwitchD-bgp-default] peer evpn as-number 200
[SwitchD-bgp-default] peer evpn connect-interface loopback 0
# Configure BGP to advertise EVPN routes, and disable route target filtering for BGP EVPN routes.
[SwitchD-bgp-default] address-family l2vpn evpn
[SwitchD-bgp-default-evpn] peer evpn enable
[SwitchD-bgp-default-evpn] undo policy vpn-target
# Configure Switch D as an RR.
[SwitchD-bgp-default-evpn] peer evpn reflect-client
[SwitchD-bgp-default-evpn] quit
[SwitchD-bgp-default] quit
Verifying the configuration
1. Verify the EVPN gateway settings on Switch C:
# Verify that Switch C has advertised MAC/IP advertisement routes and IMET routes for the gateways and received MAC/IP advertisement routes and IMET routes from Switch A and Switch B.
[SwitchC] display bgp l2vpn evpn
BGP local router ID is 3.3.3.3
Status codes: * - valid, > - best, d - dampened, h - history,
s - suppressed, S - stale, i - internal, e - external
Origin: i - IGP, e - EGP, ? - incomplete
Total number of routes from all PEs: 8
Route distinguisher: 1:10
Total number of routes: 4
Network NextHop MED LocPrf PrefVal Path/Ogn
* >i [2][0][48][0000-1234-0001][0][0.0.0.0]/104
1.1.1.1 0 100 0 i
* >i [2][0][48][0000-1234-0002][0][0.0.0.0]/104
1.1.1.1 0 100 0 i
* > [2][0][48][0003-0003-0003][32][10.1.1.1]/136
0.0.0.0 0 100 32768 i
* >i [3][10][32][1.1.1.1]/80
1.1.1.1 0 100 0 i
* > [3][10][32][3.3.3.3]/80
0.0.0.0 0 100 32768 i
Route distinguisher: 1:20
Total number of routes: 4
Network NextHop MED LocPrf PrefVal Path/Ogn
* >i [2][0][48][0000-1234-0003][0][0.0.0.0]/104
3.3.3.3 0 100 0 i
* >i [2][0][48][0000-1234-0004][0][0.0.0.0]/104
3.3.3.3 0 100 0 i
* > [2][0][48][0005-0005-0005][32][10.1.2.1]/136
0.0.0.0 0 100 32768 i
* > [3][20][32][3.3.3.3]/80
0.0.0.0 0 100 32768 i
* >i [3][20][32][2.2.2.2]/80
3.3.3.3 0 100 0 i
# Verify that the VXLAN tunnel interfaces are up on Switch C.
[SwitchC] display interface tunnel
Tunnel0
Current state: UP
Line protocol state: UP
Description: Tunnel0 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 3.3.3.3, destination 2.2.2.2
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 7 bytes/sec, 56 bits/sec, 0 packets/sec
Input: 10 packets, 980 bytes, 0 drops
Output: 85 packets, 6758 bytes, 0 drops
Tunnel1
Current state: UP
Line protocol state: UP
Description: Tunnel1 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 3.3.3.3, destination 1.1.1.1
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 1 bytes/sec, 8 bits/sec, 0 packets/sec
Last 300 seconds output rate: 9 bytes/sec, 72 bits/sec, 0 packets/sec
Input: 277 packets, 20306 bytes, 0 drops
Output: 1099 packets, 85962 bytes, 0 drops
# Verify that the VSI interfaces are up on Switch C.
[SwitchC] display interface vsi-interface
Vsi-interface1
Current state: UP
Line protocol state: UP
Description: Vsi-interface1 Interface
Bandwidth: 1000000 kbps
Maximum transmission unit: 1444
Internet address: 10.1.1.1/24 (primary)
IP packet frame type: Ethernet II, hardware address: 0003-0003-0003
IPv6 packet frame type: Ethernet II, hardware address: 0003-0003-0003
Physical: Unknown, baudrate: 1000000 kbps
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 64 packets, 6272 bytes, 0 drops
Vsi-interface2
Current state: UP
Line protocol state: UP
Description: Vsi-interface2 Interface
Bandwidth: 1000000 kbps
Maximum transmission unit: 1444
Internet address: 10.1.1.2/24 (primary)
IP packet frame type: Ethernet II, hardware address: 0005-0005-0005
IPv6 packet frame type: Ethernet II, hardware address: 0005-0005-0005
Physical: Unknown, baudrate: 1000000 kbps
Last clearing of counters: Never
Last 300 seconds input rate: 41 bytes/sec, 328 bits/sec, 0 packets/sec
Last 300 seconds output rate: 52 bytes/sec, 416 bits/sec, 0 packets/sec
Input: 2016 packets, 190272 bytes, 0 drops
Output: 2144 packets, 197568 bytes, 0 drops
# Verify that the VXLAN tunnels have been assigned to the VXLANs, and the VSI interfaces are the gateway interface of their respective VXLAN.
[SwitchC] display l2vpn vsi verbose
VSI Name: vpna
VSI Index : 0
VSI State : Up
MTU : 1500
Bandwidth : -
Broadcast Restrain : -
Multicast Restrain : -
Unknown Unicast Restrain: -
MAC Learning : Enabled
MAC Table Limit : -
MAC Learning rate : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
Gateway Interface : VSI-interface 1
VXLAN ID : 10
Tunnels:
Tunnel Name Link ID State Type Flood proxy
Tunnel1 0x5000001 UP Auto Disabled
VSI Name: vpnb
VSI Index : 1
VSI State : Up
MTU : 1500
Bandwidth : -
Broadcast Restrain : -
Multicast Restrain : -
Unknown Unicast Restrain: -
MAC Learning : Enabled
MAC Table Limit : -
MAC Learning rate : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
Gateway Interface : VSI-interface 2
VXLAN ID : 20
Tunnels:
Tunnel Name Link ID State Type Flood proxy
Tunnel0 0x5000000 UP Auto Disabled
# Verify that Switch C has created EVPN ARP entries for the VMs.
[SwitchC] display evpn route arp
Flags: D - Dynamic B - BGP G - Gateway L - Local Active
VPN instance:- Interface:Vsi-interface2
IP address MAC address Router MAC VSI Index Flags
10.1.2.1 0005-0005-0005 - 1 GL
10.1.2.10 0000-1234-0002 - 1 B
10.1.2.20 0000-1234-0004 - 1 B
VPN instance:- Interface:Vsi-interface1
IP address MAC address Router MAC VSI Index Flags
10.1.1.1 0003-0003-0003 - 0 GL
10.1.1.10 0000-1234-0001 - 0 B
10.1.1.20 0000-1234-0003 - 0 B
# Verify that Switch C has created FIB entries for the VMs.
[SwitchC] display fib 10.1.1.10
Destination count: 1 FIB entry count: 1
Flag:
U:Useable G:Gateway H:Host B:Blackhole D:Dynamic S:Static
R:Relay F:FRR
Destination/Mask Nexthop Flag OutInterface/Token Label
10.1.1.10/32 10.1.1.10 UH Vsi1 Null
2. Verify that VM 1, VM 2, VM 3, and VM 4 can communicate with one another.
Distributed EVPN gateway configuration example
Network requirements
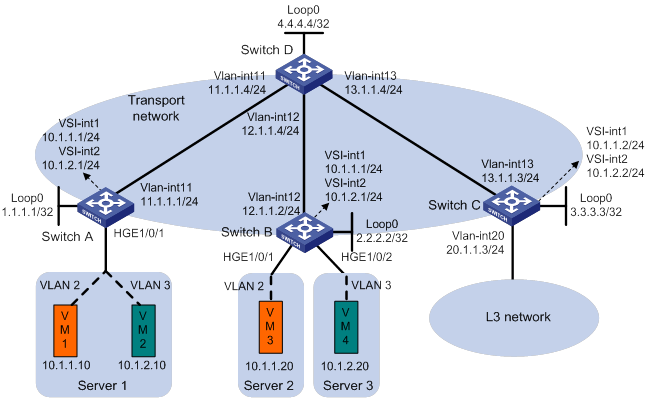
As shown in Figure 14:
· Configure VXLAN 10 and VXLAN 20 on Switch A and Switch B to provide connectivity for the VMs in the VXLANs across the network sites.
· Configure Switch A and Switch B as distributed EVPN gateways to provide gateway services. Configure Switch C as a border gateway to provide access to the connected Layer 3 network.
· Configure Switch D as an RR to reflect BGP EVPN routes between Switch A, Switch B, and Switch C.
Configuration procedure
1. On VM 1 and VM 3, specify 10.1.1.1 as the gateway address. On VM 2 and VM 4, specify 10.1.2.1 as the gateway address. (Details not shown.)
2. Configure IP addresses and unicast routing settings:
# Assign IP addresses to interfaces, as shown in Figure 14. (Details not shown.)
# Configure OSPF on all transport network switches (Switches A through D) for them to reach one another. (Details not shown.)
3. Configure Switch A:
# Enable L2VPN.
<SwitchA> system-view
[SwitchA] l2vpn enable
# Disable remote MAC address learning and remote ARP learning.
[SwitchA] vxlan tunnel mac-learning disable
[SwitchA] vxlan tunnel arp-learning disable
# Create an EVPN instance on VSI vpna, and configure the switch to automatically generate an RD and a route target for the EVPN instance.
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] evpn encapsulation vxlan
[SwitchA-vsi-vpna-evpn-vxlan] route-distinguisher auto
[SwitchA-vsi-vpna-evpn-vxlan] vpn-target auto
[SwitchA-vsi-vpna-evpn-vxlan] quit
# Create VXLAN 10.
[SwitchA-vsi-vpna] vxlan 10
[SwitchA-vsi-vpna-vxlan-10] quit
[SwitchA-vsi-vpna] quit
# Create an EVPN instance on VSI vpnb, and configure the switch to automatically generate an RD and a route target for the EVPN instance.
[SwitchA] vsi vpnb
[SwitchA-vsi-vpnb] evpn encapsulation vxlan
[SwitchA-vsi-vpnb-evpn-vxlan] route-distinguisher auto
[SwitchA-vsi-vpnb-evpn-vxlan] vpn-target auto
[SwitchA-vsi-vpnb-evpn-vxlan] quit
# Create VXLAN 20.
[SwitchA-vsi-vpnb] vxlan 20
[SwitchA-vsi-vpnb-vxlan-20] quit
[SwitchA-vsi-vpnb] quit
# Configure BGP to advertise EVPN routes.
[SwitchA] bgp 200
[SwitchA-bgp-default] peer 4.4.4.4 as-number 200
[SwitchA-bgp-default] peer 4.4.4.4 connect-interface loopback 0
[SwitchA-bgp-default] address-family l2vpn evpn
[SwitchA-bgp-default-evpn] peer 4.4.4.4 enable
[SwitchA-bgp-default-evpn] quit
[SwitchA-bgp-default] quit
# On HundredGigE 1/0/1, create Ethernet service instance 1000 to match VLAN 2.
[SwitchA] interface hundredgige 1/0/1
[SwitchA-HundredGigE1/0/1] service-instance 1000
[SwitchA-HundredGigE1/0/1-srv1000] encapsulation s-vid 2
# Map Ethernet service instance 1000 to VSI vpna.
[SwitchA-HundredGigE1/0/1-srv1000] xconnect vsi vpna
[SwitchA-HundredGigE1/0/1-srv1000] quit
# On HundredGigE 1/0/1, create Ethernet service instance 2000 to match VLAN 3.
[SwitchA-HundredGigE1/0/1] service-instance 2000
[SwitchA-HundredGigE1/0/1-srv2000] encapsulation s-vid 3
# Map Ethernet service instance 2000 to VSI vpnb.
[SwitchA-HundredGigE1/0/1-srv2000] xconnect vsi vpnb
[SwitchA-HundredGigE1/0/1-srv2000] quit
[SwitchA-HundredGigE1/0/1] quit
# Configure RD and route target settings for VPN instance vpna.
[SwitchA] ip vpn-instance vpna
[SwitchA-vpn-instance-vpna] route-distinguisher 1:1
[SwitchA-vpn-instance-vpna] address-family ipv4
[SwitchA-vpn-ipv4-vpna] vpn-target 2:2
[SwitchA-vpn-ipv4-vpna] quit
[SwitchA-vpn-instance-vpna] address-family evpn
[SwitchA-vpn-evpn-vpna] vpn-target 1:1
[SwitchA-vpn-evpn-vpna] quit
[SwitchA-vpn-instance-vpna] quit
# Configure VSI-interface 1.
[SwitchA] interface vsi-interface 1
[SwitchA-Vsi-interface1] ip binding vpn-instance vpna
[SwitchA-Vsi-interface1] ip address 10.1.1.1 255.255.255.0
[SwitchA-Vsi-interface1] mac-address 1-1-1
[SwitchA-Vsi-interface1] distributed-gateway local
[SwitchA-Vsi-interface1] local-proxy-arp enable
[SwitchA-Vsi-interface1] quit
# Configure VSI-interface 2.
[SwitchA] interface vsi-interface 2
[SwitchA-Vsi-interface2] ip binding vpn-instance vpna
[SwitchA-Vsi-interface2] ip address 10.1.2.1 255.255.255.0
[SwitchA-Vsi-interface2] mac-address 2-2-2
[SwitchA-Vsi-interface2] distributed-gateway local
[SwitchA-Vsi-interface2] local-proxy-arp enable
[SwitchA-Vsi-interface2] quit
# Associate VSI-interface 3 with VPN instance vpna, and configure the L3 VXLAN ID as 1000 for the VPN instance.
[SwitchA] interface vsi-interface 3
[SwitchA-Vsi-interface3] ip binding vpn-instance vpna
[SwitchA-Vsi-interface3] l3-vni 1000
[SwitchA-Vsi-interface3] quit
# Specify VSI-interface 1 as the gateway interface for VSI vpna.
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] gateway vsi-interface 1
[SwitchA-vsi-vpna] quit
# Specify VSI-interface 2 as the gateway interface for VSI vpnb.
[SwitchA] vsi vpnb
[SwitchA-vsi-vpnb] gateway vsi-interface 2
[SwitchA-vsi-vpnb] quit
4. Configure Switch B:
# Enable L2VPN.
<SwitchB> system-view
[SwitchB] l2vpn enable
# Disable remote MAC address learning and remote ARP learning.
[SwitchB] vxlan tunnel mac-learning disable
[SwitchB] vxlan tunnel arp-learning disable
# Create an EVPN instance on VSI vpna, and configure the switch to automatically generate an RD and a route target for the EVPN instance.
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] evpn encapsulation vxlan
[SwitchB-vsi-vpna-evpn-vxlan] route-distinguisher auto
[SwitchB-vsi-vpna-evpn-vxlan] vpn-target auto
[SwitchB-vsi-vpna-evpn-vxlan] quit
# Create VXLAN 10.
[SwitchB-vsi-vpna] vxlan 10
[SwitchB-vsi-vpna-vxlan-10] quit
[SwitchB-vsi-vpna] quit
# Create an EVPN instance on VSI vpnb, and configure the switch to automatically generate an RD and a route target for the EVPN instance.
[SwitchB] vsi vpnb
[SwitchB-vsi-vpnb] evpn encapsulation vxlan
[SwitchB-vsi-vpnb-evpn-vxlan] route-distinguisher auto
[SwitchB-vsi-vpnb-evpn-vxlan] vpn-target auto
[SwitchB-vsi-vpnb-evpn-vxlan] quit
# Create VXLAN 20.
[SwitchB-vsi-vpnb] vxlan 20
[SwitchB-vsi-vpnb-vxlan-20] quit
[SwitchB-vsi-vpnb] quit
# Configure BGP to advertise EVPN routes.
[SwitchB] bgp 200
[SwitchB-bgp-default] peer 4.4.4.4 as-number 200
[SwitchB-bgp-default] peer 4.4.4.4 connect-interface loopback 0
[SwitchB-bgp-default] address-family l2vpn evpn
[SwitchB-bgp-default-evpn] peer 4.4.4.4 enable
[SwitchB-bgp-default-evpn] quit
[SwitchB-bgp-default] quit
# On HundredGigE 1/0/1, create Ethernet service instance 1000 to match VLAN 2.
[SwitchB] interface hundredgige 1/0/1
[SwitchB-HundredGigE1/0/1] service-instance 1000
[SwitchB-HundredGigE1/0/1-srv1000] encapsulation s-vid 2
# Map Ethernet service instance 1000 to VSI vpna.
[SwitchB-HundredGigE1/0/1-srv1000] xconnect vsi vpna
[SwitchB-HundredGigE1/0/1-srv1000] quit
[SwitchB-HundredGigE1/0/1] quit
# On HundredGigE 1/0/2, create Ethernet service instance 2000 to match VLAN 3.
[SwitchB] interface hundredgige 1/0/2
[SwitchB-HundredGigE1/0/2] service-instance 2000
[SwitchB-HundredGigE1/0/2-srv2000] encapsulation s-vid 3
# Map Ethernet service instance 2000 to VSI vpnb.
[SwitchB-HundredGigE1/0/2-srv2000] xconnect vsi vpnb
[SwitchB-HundredGigE1/0/2-srv2000] quit
[SwitchB-HundredGigE1/0/2] quit
# Configure RD and route target settings for VPN instance vpna.
[SwitchB] ip vpn-instance vpna
[SwitchB-vpn-instance-vpna] route-distinguisher 1:1
[SwitchB-vpn-instance-vpna] address-family ipv4
[SwitchB-vpn-ipv4-vpna] vpn-target 2:2
[SwitchB-vpn-ipv4-vpna] quit
[SwitchB-vpn-instance-vpna] address-family evpn
[SwitchB-vpn-evpn-vpna] vpn-target 1:1
[SwitchB-vpn-evpn-vpna] quit
[SwitchB-vpn-instance-vpna] quit
# Configure VSI-interface 1.
[SwitchB] interface vsi-interface 1
[SwitchB-Vsi-interface1] ip binding vpn-instance vpna
[SwitchB-Vsi-interface1] ip address 10.1.1.1 255.255.255.0
[SwitchB-Vsi-interface1] mac-address 1-1-1
[SwitchB-Vsi-interface1] distributed-gateway local
[SwitchB-Vsi-interface1] local-proxy-arp enable
[SwitchB-Vsi-interface1] quit
# Configure VSI-interface 2.
[SwitchB] interface vsi-interface 2
[SwitchB-Vsi-interface2] ip binding vpn-instance vpna
[SwitchB-Vsi-interface2] ip address 10.1.2.1 255.255.255.0
[SwitchB-Vsi-interface2] mac-address 2-2-2
[SwitchB-Vsi-interface2] distributed-gateway local
[SwitchB-Vsi-interface2] local-proxy-arp enable
[SwitchB-Vsi-interface2] quit
# Associate VSI-interface 3 with VPN instance vpna, and configure the L3 VXLAN ID as 1000 for the VPN instance.
[SwitchB] interface vsi-interface 3
[SwitchB-Vsi-interface3] ip binding vpn-instance vpna
[SwitchB-Vsi-interface3] l3-vni 1000
[SwitchB-Vsi-interface3] quit
# Specify VSI-interface 1 as the gateway interface for VSI vpna.
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] gateway vsi-interface 1
[SwitchB-vsi-vpna] quit
# Specify VSI-interface 2 as the gateway interface for VSI vpnb.
[SwitchB] vsi vpnb
[SwitchB-vsi-vpnb] gateway vsi-interface 2
[SwitchB-vsi-vpnb] quit
5. Configure Switch C:
# Enable L2VPN.
<SwitchC> system-view
[SwitchC] l2vpn enable
# Disable remote MAC address learning and remote ARP learning.
[SwitchC] vxlan tunnel mac-learning disable
[SwitchC] vxlan tunnel arp-learning disable
# Configure BGP to advertise EVPN routes.
[SwitchC] bgp 200
[SwitchC-bgp-default] peer 4.4.4.4 as-number 200
[SwitchC-bgp-default] peer 4.4.4.4 connect-interface loopback 0
[SwitchC-bgp-default] address-family l2vpn evpn
[SwitchC-bgp-default-evpn] peer 4.4.4.4 enable
[SwitchC-bgp-default-evpn] quit
[SwitchC-bgp-default] quit
# Configure RD and route target settings for VPN instance vpna.
[SwitchC] ip vpn-instance vpna
[SwitchC-vpn-instance-vpna] route-distinguisher 1:1
[SwitchC-vpn-instance-vpna] address-family ipv4
[SwitchC-vpn-ipv4-vpna] vpn-target 2:2
[SwitchC-vpn-ipv4-vpna] quit
[SwitchC-vpn-instance-vpna] address-family evpn
[SwitchC-vpn-evpn-vpna] vpn-target 1:1
[SwitchC-vpn-evpn-vpna] quit
[SwitchC-vpn-instance-vpna] quit
# Associate VSI-interface 3 with VPN instance vpna, and configure the L3 VXLAN ID as 1000 for the VPN instance.
[SwitchC] interface vsi-interface 3
[SwitchC-Vsi-interface3] ip binding vpn-instance vpna
[SwitchC-Vsi-interface3] l3-vni 1000
[SwitchC-Vsi-interface3] quit
# Configure a default route.
[SwitchC] ip route-static vpn-instance vpna 0.0.0.0 0 null0
# Import the default route to the BGP IPv4 unicast routing table of VPN instance vpna.
[SwitchC] bgp 200
[SwitchC-bgp-default] ip vpn-instance vpna
[SwitchC-bgp-default-vpna] address-family ipv4 unicast
[SwitchC-bgp-default-ipv4-vpna] default-route imported
[SwitchC-bgp-default-ipv4-vpna] import-route static
[SwitchC-bgp-default-ipv4-vpna] quit
[SwitchC-bgp-default-vpna] quit
[SwitchC-bgp-default] quit
6. Configure Switch D:
# Establish BGP connections with other transport network switches.
<SwitchD> system-view
[SwitchD] bgp 200
[SwitchD-bgp-default] group evpn
[SwitchD-bgp-default] peer 1.1.1.1 group evpn
[SwitchD-bgp-default] peer 2.2.2.2 group evpn
[SwitchD-bgp-default] peer 3.3.3.3 group evpn
[SwitchD-bgp-default] peer evpn as-number 200
[SwitchD-bgp-default] peer evpn connect-interface loopback 0
# Configure BGP to advertise EVPN routes, and disable route target filtering for BGP EVPN routes.
[SwitchD-bgp-default] address-family l2vpn evpn
[SwitchD-bgp-default-evpn] peer evpn enable
[SwitchD-bgp-default-evpn] undo policy vpn-target
# Configure Switch D as an RR.
[SwitchD-bgp-default-evpn] peer evpn reflect-client
[SwitchD-bgp-default-evpn] quit
[SwitchD-bgp-default] quit
Verifying the configuration
1. Verify the distributed EVPN gateway settings on Switch A:
# Verify that Switch A has advertised the IP prefix advertisement routes for the gateways and the MAC/IP advertisement routes and IMET routes for each VSI. Verify that Switch A has received the IP prefix advertisement routes for the gateways and the MAC/IP advertisement routes and IMET routes for each VSI from Switch B.
[SwitchA] display bgp l2vpn evpn
BGP local router ID is 1.1.1.1
Status codes: * - valid, > - best, d - dampened, h - history,
s - suppressed, S - stale, i - internal, e - external
Origin: i - IGP, e - EGP, ? - incomplete
Total number of routes from all PEs: 14
Route distinguisher: 1:1
Total number of routes: 4
Network NextHop MED LocPrf PrefVal Path/Ogn
* > [5][0][24][10.1.1.0]/80
0.0.0.0 0 100 32768 i
* > [5][0][24][10.1.2.0]/80
0.0.0.0 0 100 32768 i
* >i [5][0][24][10.1.1.0]/80
2.2.2.2 0 100 0 i
* >i [5][0][24][10.1.2.0]/80
2.2.2.2 0 100 0 i
Route distinguisher: 1:10
Total number of routes: 5
Network NextHop MED LocPrf PrefVal Path/Ogn
* > [2][0][48][0000-1234-0001][0][0.0.0.0]/104
0.0.0.0 0 100 32768 i
* > [2][0][48][0000-1234-0001][32][10.1.1.10]/136
0.0.0.0 0 100 32768 i
* >i [2][0][48][0000-1234-0003][32][10.1.1.20]/136
2.2.2.2 0 100 0 i
* > [3][10][32][1.1.1.1]/80
0.0.0.0 0 100 32768 i
* >i [3][10][32][2.2.2.2]/80
2.2.2.2 0 100 32768 i
Route distinguisher: 1:20
Total number of routes: 5
Network NextHop MED LocPrf PrefVal Path/Ogn
* > [2][0][48][0000-1234-0002][0][0.0.0.0]/104
0.0.0.0 0 100 32768 i
* > [2][0][48][0000-1234-0002][32][10.1.2.10]/136
0.0.0.0 0 100 32768 i
* >i [2][0][48][0000-1234-0004][32][10.1.2.20]/136
2.2.2.2 0 100 0 i
* > [3][10][32][1.1.1.1]/80
0.0.0.0 0 100 32768 i
* >i [3][10][32][2.2.2.2]/80
2.2.2.2 0 100 32768 i
# Verify that the VXLAN tunnel interfaces are up on Switch A. (This example uses Tunnel 0.)
[SwitchA] display interface tunnel 0
Tunnel0
Current state: UP
Line protocol state: UP
Description: Tunnel0 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 1.1.1.1, destination 2.2.2.2
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 9 packets, 882 bytes, 0 drops
Output: 9 packets, 882 bytes, 0 drops
# Verify that the VSI interfaces are up on Switch A. (This example uses VSI-interface 1.)
[SwitchA] display interface vsi-interface 1
Vsi-interface1
Current state: UP
Line protocol state: UP
Description: Vsi-interface1 Interface
Bandwidth: 1000000 kbps
Maximum transmission unit: 1444
Internet address: 10.1.1.1/24 (primary)
IP packet frame type: Ethernet II, hardware address: 0001-0001-0001
IPv6 packet frame type: Ethernet II, hardware address: 0001-0001-0001
Physical: Unknown, baudrate: 1000000 kbps
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 192 packets, 18816 bytes, 0 drops
# Verify that the VXLAN tunnels have been assigned to the VXLANs, and the VSI interfaces are the gateway interface of their respective VXLAN.
[SwitchA] display l2vpn vsi verbose
VSI Name: Auto_L3VNI200_3
VSI Index : 1
VSI State : Down
MTU : 1500
Bandwidth : -
Broadcast Restrain : -
Multicast Restrain : -
Unknown Unicast Restrain: -
MAC Learning : Enabled
MAC Table Limit : -
MAC Learning rate : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
Gateway Interface : VSI-interface 3
VXLAN ID : 1000
VSI Name: vpna
VSI Index : 0
VSI State : Up
MTU : 1500
Bandwidth : -
Broadcast Restrain : -
Multicast Restrain : -
Unknown Unicast Restrain: -
MAC Learning : Enabled
MAC Table Limit : -
MAC Learning rate : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
Gateway Interface : VSI-interface 1
VXLAN ID : 10
ACs:
AC Link ID State
HGE1/0/1 srv1000 0 Up
VSI Name: vpnb
VSI Index : 0
VSI State : Up
MTU : 1500
Bandwidth : -
Broadcast Restrain : -
Multicast Restrain : -
Unknown Unicast Restrain: -
MAC Learning : Enabled
MAC Table Limit : -
MAC Learning rate : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
Gateway Interface : VSI-interface 2
VXLAN ID : 20
ACs:
AC Link ID State
HGE1/0/1 srv2000 0 Up
# Verify that Switch A has created ARP entries for the VMs.
[SwitchA] display arp
Type: S-Static D-Dynamic O-Openflow R-Rule M-Multiport I-Invalid
IP address MAC address VID Interface/Link ID Aging Type
10.1.1.10 0000-1234-0001 0 0x0 20 D
10.1.2.10 0000-1234-0002 0 0x0 19 D
2.2.2.2 a0ce-5e24-0100 1 Tunnel0 N/A R
# Verify that Switch A has created EVPN ARP entries for the local VMs.
[SwitchA] display evpn route arp
Flags: D - Dynamic B - BGP G - Gateway L - Local Active
VPN instance:vpna Interface:Vsi-interface1
IP address MAC address Router MAC VSI Index Flags
10.1.1.1 0003-0003-0003 a0ce-7e40-0400 0 GL
10.1.1.10 0000-1234-0001 a0ce-7e40-0400 0 DL
10.1.2.10 0000-1234-0002 a0ce-7e40-0400 0 DL
10.1.1.20 0000-1234-0003 a0ce-7e40-0400 0 B
10.1.2.20 0000-1234-0004 a0ce-7e40-0400 0 B
2. Verify that VM 1, VM 2, VM 3, and VM 4 can communicate with one another.
A
address
EVPN remote MAC address entry management, 21
advertisement
BGP EVPN route advertisement to local site, 22
EVPN MAC advertisement, 21
EVPN route advertisement, 15
IP prefix route advertisement, 20
ARP
EVPN ARP flood suppression, 11, 23
EVPN local flood confine, 23
assigning
EVPN traffic assignment, 3
B
BGP
EVPN route advertisement, 15
C
configuring
EVPN, 13, 24
EVPN gateway (centralized), 17, 24
EVPN gateway (distributed), 18, 33
EVPN instance, 15
EVPN route advertisement, 15
EVPN VSI interface, 18
IP prefix route advertisement, 20
L3 VXLAN ID, 19
confining
EVPN local flood, 23
creating
VXLAN on VSI, 14
D
disabling
EVPN MAC advertisement, 21
EVPN MAC learning from ARP information, 22
EVPN remote MAC+ARP learning, 21
displaying
EVPN, 24
E
enabling
BGP EVPN route advertisement to local site, 22
EVPN ARP flood suppression, 23
Ethernet
EVPN Ethernet service instance > VSI mapping, 17
EVPN MP-BGP extension, 2
EVPN network model, 1
EVPN overview, 1
EVPN transport network structure, 2
Ethernet Virtual Private Network. Use EVPN
ARP flood suppression, 11
ARP flood suppression enable, 23
centralized EVPN gateway restrictions, 17
centralized gateway, 6
configuration, 13
configuration automation, 3
configuration restrictions, 13
creation on VSI, 14
display, 24
distributed EVPN gateway restrictions, 18
distributed gateway, 7
Ethernet service instance > VSI mapping, 17
EVPN instance configuration, 15
EVPN route advertisement, 15
gateway configuration (centralized), 17, 24
gateway configuration (distributed), 18, 33
IP prefix route advertisement, 20
L3 VXLAN ID configuration, 19
Layer 2 traffic forwarding, 4
Layer 3 traffic forwarding, 6
local flood confine, 23
MAC address learning, 4
MAC mobility, 12
maintain, 24
MP-BGP extension, 2
network model, 1
overview, 1
remote MAC address entry management, 21
traffic assignment, 3
transport network structure, 2
VSI interface configuration, 18
VXLAN forwarding mode, 13
F
flooding
EVPN ARP flood suppression, 11, 23
EVPN local flood confine, 23
EVPN traffic forwarding flood process, 6
forwarding
EVPN centralized gateway, 6
EVPN distributed gateway, 7
EVPN Layer 2 traffic forwarding, 4
EVPN Layer 3 traffic forwarding, 6
VXLAN forwarding mode, 13
frame
EVPN local flood confine, 23, 23
G
gateway
EVPN centralized gateway, 6
EVPN distributed gateway, 7
EVPN gateway configuration (centralized), 17, 24
EVPN gateway configuration (distributed), 18, 33
L3 VXLAN ID configuration, 19
I
instance
EVPN instance configuration, 15
IP routing
EVPN ARP flood suppression, 11
EVPN gateway configuration (centralized), 17, 24
EVPN gateway configuration (distributed), 18, 33
EVPN VSI interface configuration, 18
L3 VXLAN ID configuration, 19
IPv4
EVPN network model, 1
EVPN overview, 1
EVPN transport network structure, 2
L
Layer 2
EVPN network model, 1
EVPN overview, 1
EVPN transport network structure, 2
Layer 3
EVPN centralized gateway, 6
EVPN distributed gateway, 7
EVPN gateway configuration (centralized), 17, 24
EVPN gateway configuration (distributed), 18, 33
EVPN VSI interface configuration, 18
L3 VXLAN ID configuration, 19
learning
EVPN MAC address learning, 4
EVPN MAC learning from ARP information, 22
EVPN remote ARP learning, 21
EVPN remote MAC+ARP learning, 21
M
MAC
EVPN MAC advertisement, 21, 21
EVPN MAC learning from ARP information, 22, 22
EVPN remote ARP learning, 21, 21
EVPN remote MAC learning, 21
MAC mobility, 12
MAC addressing
EVPN MAC address learning, 4
EVPN remote MAC address entry management, 21
MAC-in-UDP
EVPN ARP flood suppression, 11
EVPN local flood confine, 23
maintaining
EVPN, 24
managing
EVPN remote ARP learning, 21
EVPN remote MAC address entries, 21
mapping
EVPN Ethernet service instance > VSI, 17
mode
VXLAN forwarding, 13
multicast
EVPN traffic forwarding flood process, 6
N
network
EVPN ARP flood suppression, 11, 23
EVPN configuration, 13
EVPN Ethernet service instance > VSI mapping, 17
EVPN gateway configuration (centralized), 17, 24
EVPN gateway configuration (distributed), 18, 33
EVPN instance configuration, 15
EVPN local flood confine, 23
EVPN model, 1
EVPN MP-BGP extension, 2
EVPN remote MAC address entry management, 21
EVPN route advertisement, 15
EVPN transport network structure, 2
EVPN VSI interface configuration, 18
L3 VXLAN ID configuration, 19
v configuration, 24
VXLAN creation on VSI, 14
network management
EVPN overview, 1
NMM
EVPN configuration, 13, 24
P
procedure
configuring EVPN, 13
configuring EVPN gateway (centralized), 17, 24
configuring EVPN gateway (distributed), 18, 33
configuring EVPN instance, 15
configuring EVPN route advertisement, 15
configuring EVPN VSI interface, 18
configuring IP prefix route advertisement, 20
configuring L3 VXLAN ID, 19
confining EVPN local flood, 23
creating VXLAN on VSI, 14
disabling EVPN MAC advertisement, 21
disabling EVPN MAC learning from ARP information, 22
disabling EVPN remote MAC+ARP learning, 21
displaying EVPN, 24
enabling BGP EVPN route advertisement to local site, 22
enabling EVPN ARP flood suppression, 23
maintaining EVPN, 24
managing EVPN remote MAC address entries, 21
mapping EVPN Ethernet service instance > VSI, 17
setting VXLAN forwarding mode, 13
R
restrictions
centralized EVPN gateway configuration, 17
distributed EVPN gateway configuration, 18
EVPN configuration, 13
route
BGP EVPN route advertisement to local site, 22
IP prefix route advertisement, 20
routing
EVPN MP-BGP extension, 2
S
service instance
EVPN Ethernet service instance > VSI mapping, 17
setting
VXLAN forwarding mode, 13
suppressing
EVPN ARP flood suppression, 11, 23
T
traffic
EVPN centralized gateway, 6
EVPN configuration, 13, 24
EVPN distributed gateway, 7
EVPN Layer 2 traffic forwarding, 4
EVPN Layer 3 traffic forwarding, 6
EVPN MAC address learning, 4
EVPN traffic assignment, 3
VXLAN forwarding mode, 13
tunneling
EVPN configuration, 13, 24
EVPN network model, 1
U
unicast
EVPN traffic forwarding, 4
EVPN traffic forwarding flood process, 6
V
VSI
EVPN Ethernet service instance > VSI mapping, 17
EVPN network model, 1
EVPN VSI interface configuration, 18
VXLAN creation on VSI, 14
VSI interface
L3 VXLAN ID, 19
VTEP
EVPN gateway configuration (centralized), 17
EVPN gateway configuration (distributed), 18
L3 VXLAN ID configuration, 19
VXLAN IP gateway configuration (centralized), 24
VXLAN IP gateway configuration (distributed), 33

