- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Text | 3.39 MB |
Feature and software version compatibility
Specifying the label type advertised by the egress
Enabling sending of MPLS TTL-expired messages
Enabling SNMP notifications for MPLS
Displaying and maintaining MPLS
Feature and software version compatibility
Static LSP configuration example
Configuration restrictions and guidelines
Label distribution and control
Feature and software version compatibility
Configuring LDP session parameters
Configuring LDP MD5 authentication
Configuring an LSP generation policy
Configuring the LDP label distribution control mode
Configuring a label advertisement policy·
Configuring a label acceptance policy
Configuring LDP loop detection
Configuring LDP-IGP synchronization
Configuring LDP-OSPF synchronization
Configuring LDP-ISIS synchronization
Enabling SNMP notifications for LDP
Displaying and maintaining LDP
Label acceptance control configuration example
Label advertisement control configuration example
Automatic bandwidth adjustment
Feature and software version compatibility
MPLS TE configuration task list
Configuring a tunnel interface
Configuring an MPLS TE tunnel to use a static CRLSP
Configuring an MPLS TE tunnel to use a dynamic CRLSP
Configuring MPLS TE attributes for a link
Advertising link TE attributes by using IGP TE extension
Configuring MPLS TE tunnel constraints
Establishing an MPLS TE tunnel by using RSVP-TE
Controlling CRLSP path selection
Controlling MPLS TE tunnel setup
Configuring traffic forwarding
Configuring static routing to direct traffic to an MPLS TE tunnel
Configuring automatic route advertisement to direct traffic to an MPLS TE tunnel
Configuring a bidirectional MPLS TE tunnel
Configuring a bypass tunnel on the PLR
Configuring node fault detection
Configuring the optimal bypass tunnel selection interval
Displaying and maintaining MPLS TE·
MPLS TE configuration examples
Establishing an MPLS TE tunnel over a static CRLSP
Establishing an MPLS TE tunnel with RSVP-TE
Establishing an inter-AS MPLS TE tunnel with RSVP-TE
Bidirectional MPLS TE tunnel configuration example
CRLSP backup configuration example
Manual bypass tunnel for FRR configuration example
Auto FRR configuration example
IETF DS-TE configuration example
Feature and software version compatibility
Static CRLSP configuration example
Feature and software version compatibility
Configuring RSVP Srefresh and reliable RSVP message delivery
Configuring RSVP hello extension
Configuring RSVP authentication
Specifying a DSCP value for outgoing RSVP packets
Displaying and maintaining RSVP
Establishing an MPLS TE tunnel with RSVP-TE
Feature and software version compatibility
Tunnel policy configuration examples
Preferred tunnel configuration example
Exclusive tunnel configuration example
Tunnel selection order configuration example
Preferred tunnel and tunnel selection order configuration example
MPLS L3VPN route advertisement
Feature and software version compatibility
MPLS L3VPN configuration task list
Configuring routing between a PE and a CE
Configuring routing between PEs
Configuring BGP VPNv4 route control
Configuring a loopback interface
Redistributing the loopback interface route
Specifying the VPN label processing mode on the egress PE
Configuring BGP AS number substitution·
Enabling SNMP notifications for MPLS L3VPN
Enabling logging for BGP route flapping
Displaying and maintaining MPLS L3VPN
MPLS L3VPN configuration examples
Configuring a hub-spoke network
Configuring MPLS L3VPN inter-AS option A
Configuring MPLS L3VPN inter-AS option B
Configuring MPLS L3VPN inter-AS option C
Configuring MPLS L3VPN carrier's carrier
Configuring BGP AS number substitution·
Configuring MPLS L3VPN FRR through VPNv4 route backup for a VPNv4 route
Configuring MPLS L3VPN FRR through VPNv4 route backup for an IPv4 route
Configuring MPLS L3VPN FRR through IPv4 route backup for a VPNv4 route
Associating a VPN instance with an interface
Configuring route related attributes for a VPN instance
Configuring routing between an MCE and a VPN site
Configuring routing between an MCE and a PE
Displaying and maintaining MCE
Configuring the MCE that uses OSPF to advertise VPN routes to the PE
Configuring the MCE that uses EBGP to advertise VPN routes to the PE
Configuring basic MPLS
Multiprotocol Label Switching (MPLS) provides connection-oriented label switching over connectionless IP backbone networks. It integrates both the flexibility of IP routing and the simplicity of Layer 2 switching.
Unless otherwise specified, the term "interface" in this chapter refers to a Layer 3 interface. It can be a VLAN interface or a Layer 3 Ethernet interface. Layer 3 Ethernet interfaces refer to the Ethernet interfaces that operate in Layer 3 mode. For information about switching the Ethernet interface operating mode, see Layer 2—LAN Switching Configuration Guide.
Overview
MPLS has the following advantages:
· High speed and efficiency—MPLS uses short- and fixed-length labels to forward packets, avoiding complicated routing table lookups.
· Multiprotocol support—MPLS resides between the link layer and the network layer. It can work over various link layer protocols (for example, PPP, ATM, frame relay, and Ethernet) to provide connection-oriented services for various network layer protocols (for example, IPv4 and IPX).
· Good scalability—The connection-oriented switching and multilayer label stack features enable MPLS to deliver various extended services, such as VPN, traffic engineering, and QoS.
Basic concepts
FEC
MPLS groups packets with the same characteristics (such as packets with the same destination or service class) into a forwarding equivalence class (FEC). Packets of the same FEC are handled in the same way on an MPLS network.
Label
A label uniquely identifies an FEC and has local significance.
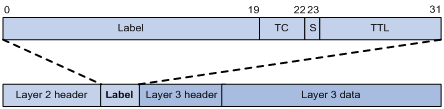
A label is encapsulated between the Layer 2 header and Layer 3 header of a packet. It is four bytes long and consists of the following fields:
· Label—20-bit label value.
· TC—3-bit traffic class, used for QoS. It is also called Exp.
· S—1-bit bottom of stack flag. A label stack can have multiple labels. The label nearest to the Layer 2 header is called the top label, and the label nearest to the Layer 3 header is called the bottom label. The S field is set to 1 if the label is the bottom label and set to 0 if not.
· TTL—8-bit time to live field used for routing loop prevention.
LSR
A router that performs MPLS forwarding is a label switching router (LSR).
LSP
A label switched path (LSP) is the path along which packets of an FEC travel through an MPLS network.
An LSP is a unidirectional packet forwarding path. Two neighboring LSRs are called the upstream LSR and downstream LSR along the direction of an LSP. As shown in Figure 2, LSR B is the downstream LSR of LSR A, and LSR A is the upstream LSR of LSR B.
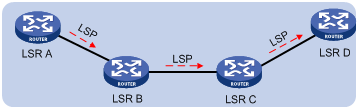
LFIB
The Label Forwarding Information Base (LFIB) on an MPLS network functions like the Forwarding Information Base (FIB) on an IP network. When an LSR receives a labeled packet, it searches the LFIB to obtain information for forwarding the packet, such as the label operation type, the outgoing label value, and the next hop.
Control plane and forwarding plane
An MPLS node consists of a control plane and a forwarding plane.
· Control plane—Assigns labels, distributes FEC-label mappings to neighbor LSRs, creates the LFIB, and establishes and removes LSPs.
· Forwarding plane—Forwards packets according to the LFIB.
MPLS network architecture
Figure 3 MPLS network architecture
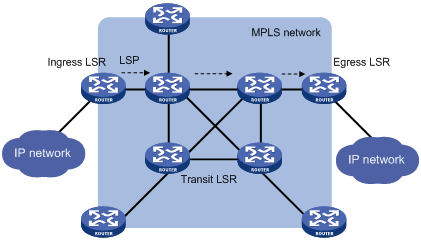
An MPLS network has the following types of LSRs:
· Ingress LSR—Ingress LSR of packets. It labels packets entering into the MPLS network.
· Transit LSR—Intermediate LSRs in the MPLS network. The transit LSRs on an LSP forward packets to the egress LSR according to labels.
· Egress LSR—Egress LSR of packets. It removes labels from packets and forwards the packets to their destination networks.
LSP establishment
LSPs include static and dynamic LSPs.
· Static LSP—To establish a static LSP, you must configure an LFIB entry on each LSR along the LSP. Establishing static LSPs consumes fewer resources than establishing dynamic LSPs, but static LSPs cannot automatically adapt to network topology changes. Therefore, static LSPs are suitable for small-scale networks with simple, stable topologies.
· Dynamic LSP—Established by a label distribution protocol (also called an MPLS signaling protocol). A label distribution protocol classifies FECs, distributes FEC-label mappings, and establishes and maintains LSPs. Label distribution protocols include protocols designed specifically for label distribution, such as the Label Distribution Protocol (LDP), and protocols extended to support label distribution, such as MP-BGP and RSVP-TE.
In this document, the term "label distribution protocols" refers to all protocols for label distribution. The term "LDP" refers to the RFC 5036 LDP.
A dynamic LSP is established in the following steps:
1. A downstream LSR classifies FECs according to destination addresses.
2. The downstream LSR assigns a label for each FEC, and distributes the FEC-label binding to its upstream LSR.
3. The upstream LSR establishes an LFIB entry for the FEC according to the binding information.
After all LSRs along the LSP establish an LFIB entry for the FEC, a dynamic LSP is established for the packets of this FEC.
Figure 4 Dynamic LSP establishment
MPLS forwarding

As shown in Figure 5, a packet is forwarded over the MPLS network in the following steps:
1. Router B (the ingress LSR) receives a packet with no label. Then, it performs the following operations:
a. Identifies the FIB entry that matches the destination address of the packet.
b. Adds the outgoing label (40, in this example) to the packet.
c. Forwards the labeled packet out of the interface VLAN-interface 20 to the next hop LSR Router C.
2. When receiving the labeled packet, Router C processes the packet as follows:
a. Identifies the LFIB entry that has an incoming label of 40.
b. Uses the outgoing label 50 of the entry to replace label 40 in the packet.
c. Forwards the labeled packet out of the outgoing interface VLAN-interface 30 to the next hop LSR Router D.
3. When receiving the labeled packet, Router D (the egress) processes the packet as follows:
a. Identifies the LFIB entry that has an incoming label of 50.
b. Removes the label from the packet.
c. Forwards the packet out of the outgoing interface VLAN-interface 40 to the next hop LSR Router E.
If the LFIB entry records no outgoing interface or next hop information, Router D performs the following operations:
a. Identifies the FIB entry by the IP header.
b. Forwards the packet according to the FIB entry.
PHP
An egress node must perform two forwarding table lookups to forward a packet:
· Two LFIB lookups (if the packet has more than one label).
· One LFIB lookup and one FIB lookup (if the packet has only one label).
The penultimate hop popping (PHP) feature can pop the label at the penultimate node, so the egress node only performs one table lookup.
A PHP-capable egress node sends the penultimate node an implicit null label of 3. This label never appears in the label stack of packets. If an incoming packet matches an LFIB entry comprising the implicit null label, the penultimate node pops the top label of the packet and forwards the packet to the egress LSR. The egress LSR directly forwards the packet.
Sometimes, the egress node must use the TC field in the label to perform QoS. To keep the TC information, you can configure the egress node to send the penultimate node an explicit null label of 0. If an incoming packet matches an LFIB entry comprising the explicit null label, the penultimate hop replaces the value of the top label with value 0, and forwards the packet to the egress node. The egress node gets the TC information, pops the label of the packet, and forwards the packet.
Protocols and standards
· RFC 3031, Multiprotocol Label Switching Architecture
· RFC 3032, MPLS Label Stack Encoding
· RFC 5462, Multiprotocol Label Switching (MPLS) Label Stack Entry: "EXP" Field Renamed to "Traffic Class" Field
Feature and software version compatibility
The basic MPLS feature is available in Release 1138P01 and later versions.
MPLS configuration task list
|
Tasks at a glance |
|
(Required.) Enabling MPLS |
|
(Optional.) Configuring MPLS MTU |
|
(Optional.) Specifying the label type advertised by the egress |
|
(Optional.) Configuring TTL propagation |
|
(Optional.) Enabling sending of MPLS TTL-expired messages |
|
(Optional.) Enabling SNMP notifications for MPLS |
Enabling MPLS
Before you enable MPLS, perform the following tasks:
· Configure link layer protocols to ensure connectivity at the link layer.
· Configure IP addresses for interfaces to ensure IP connectivity between neighboring nodes.
· Configure static routes or an IGP protocol to ensure IP connectivity among LSRs.
To enable MPLS:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure an LSR ID for the local node. |
mpls lsr-id lsr-id |
By default, no LSR ID is configured. An LSR ID must be unique in an MPLS network and in IP address format. As a best practice, use the IP address of a loopback interface as an LSR ID. |
|
3. Enter the view of the interface that needs to perform MPLS forwarding. |
interface interface-type interface-number |
N/A |
|
4. Enable MPLS for the interface. |
mpls enable |
By default, MPLS is disabled on an interface. |
Configuring MPLS MTU
MPLS inserts the label stack between the link layer header and network layer header of each packet. To make sure the size of MPLS labeled packets is smaller than the MTU of an interface, configure an MPLS MTU on the interface.
MPLS compares each MPLS packet against the interface MPLS MTU. When the packet exceeds the MPLS MTU:
· If fragmentation is allowed, MPLS does the following:
a. Removes the label stack from the packet.
b. Fragments the IP packet. The length of a fragment is the MPLS MTU minus the length of the label stack.
c. Adds the label stack to each fragment, and forwards the fragments.
· If fragmentation is not allowed, the LSR drops the packet.
To configure an MPLS MTU for an interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure an MPLS MTU for the interface. |
mpls mtu value |
By default, no MPLS MTU is configured on an interface. |
The following applies when an interface handles MPLS packets:
· If the MPLS MTU of an interface is greater than the MTU of the interface, data forwarding might fail on the interface.
· If you do not configure the MPLS MTU of an interface, fragmentation of MPLS packets is based on the MTU of the interface without considering MPLS labels. An MPLS fragment might be larger than the interface MTU and be dropped.
Specifying the label type advertised by the egress
In an MPLS network, an egress can advertise the following types of labels:
· Implicit null label with a value of 3.
· Explicit null label with a value of 0.
· Non-null label. The value range for a non-null label is 16 to 1048575.
For LSPs established by a label distribution protocol, the label advertised by the egress determines how the penultimate hop processes a labeled packet.
· If the egress advertises an implicit null label, the penultimate hop directly pops the top label of a matching packet.
· If the egress advertises an explicit null label, the penultimate hop swaps the top label value of a matching packet with the explicit null label.
· If the egress advertises a non-null label (normal label), the penultimate hop swaps the top label of a matching packet with the specific label assigned by the egress.
Configuration guidelines
As a best practice, configure the egress to advertise an implicit null label to the penultimate hop if the penultimate hop supports PHP. If you want to simplify packet forwarding on the egress but keep labels to determine QoS policies, configure the egress to advertise an explicit null label to the penultimate hop. Use non-null labels only in particular scenarios. For example, when OAM is configured on the egress, the egress can get the OAM function entity status only through non-null labels.
As a penultimate hop, the device accepts the implicit null label, explicit null label, or normal label advertised by the egress device.
For LDP LSPs, the mpls label advertise command triggers LDP to delete the LSPs established before the command is executed and re-establishes new LSPs.
For BGP LSPs, the mpls label advertise command takes effect only for the BGP LSPs established after the command is executed. To apply the new setting to BGP LSPs established before the command is executed, delete the routes corresponding to the BGP LSPs, and then redistribute the routes.
Configuration procedure
To specify the type of label that the egress node will advertise to the penultimate hop:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify the label type advertised by the egress to the penultimate hop. |
mpls label advertise { explicit-null | implicit-null | non-null } |
By default, an egress advertises an implicit null label to the penultimate hop. |
Configuring TTL propagation
When TTL propagation is enabled, the ingress node copies the TTL value of an IP packet to the TTL field of the label. Each LSR on the LSP decreases the label TTL value by 1. The LSR that pops the label copies the remaining label TTL value back to the IP TTL of the packet, so the IP TTL value can reflect how many hops the packet has traversed in the MPLS network. The IP tracert facility can show the real path along which the packet has traveled.
Figure 6 TTL propagation
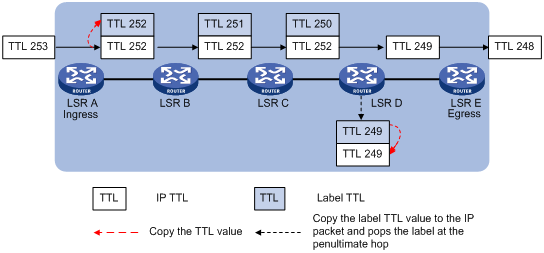
When TTL propagation is disabled, the ingress node sets the label TTL to 255. Each LSR on the LSP decreases the label TTL value by 1. The LSR that pops the label does not change the IP TTL value when popping the label. Therefore, the MPLS backbone nodes are invisible to user networks, and the IP tracert facility cannot show the real path in the MPLS network.
Figure 7 Without TTL propagation

Follow these guidelines when you configure TTL propagation:
· As a best practice, set the same TTL processing mode on all LSRs of an LSP.
· To enable TTL propagation for a VPN, you must enable it on all PE devices in the VPN, so that you can get the same traceroute result (hop count) from those PEs.
· After TTL propagation is disabled, the device cannot cannot perform correct DSCP-to-EXP mapping for IP packets entering the MPLS network.
· After TTL propagation is enabled or disabled, execute the reset mpls ldp command to make the configuration take effect. For more information about the reset mpls ldp command, see MPLS Command Reference.
To enable TTL propagation:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable TTL propagation. |
mpls ttl propagate { public | vpn } |
By default, TTL propagation is enabled only for public-network packets. This command affects only the propagation between IP TTL and label TTL. Within an MPLS network, TTL is always copied between the labels of an MPLS packet. |
Enabling sending of MPLS TTL-expired messages
This feature enables an LSR to generate an ICMP TTL-expired message upon receiving an MPLS packet with a TTL of 1. If the MPLS packet has only one label, the LSR sends the ICMP TTL-expired message back to the source through IP routing. If the MPLS packet has multiple labels, the LSR sends it along the LSP to the egress, which then sends the message back to the source.
To enable sending of MPLS TTL-expired messages:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable sending of MPLS TTL-expired messages. |
mpls ttl expiration enable |
By default, this feature is enabled. |
Enabling SNMP notifications for MPLS
This feature enables MPLS to generate SNMP notifications. The generated SNMP notifications are sent to the SNMP module.
For more information about SNMP notifications, see Network Management and Monitoring Configuration Guide.
To enable SNMP notifications for MPLS:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable SNMP notifications for MPLS. |
snmp-agent trap enable mpls |
By default, SNMP notifications for MPLS are enabled. |
Displaying and maintaining MPLS
Execute display commands in any view.
|
Task |
Command |
|
Display MPLS interface information. |
display mpls interface [ interface-type interface-number ] |
|
Display usage information about MPLS labels. |
display mpls label { label-value1 [ to label-value2 ] | all } |
|
Display LSP information. |
display mpls lsp [ egress | in-label label-value | ingress | outgoing-interface interface-type interface-number | protocol { bgp | ldp | local | rsvp-te | static | static-cr } | transit ] [ vpn-instance vpn-instance-name ] [ ipv4-dest mask-length ] [ verbose ] |
|
Display MPLS Nexthop Information Base (NIB) information. |
display mpls nib [ nib-id ] |
|
Display usage information about NIDs. |
display mpls nid [ nid-value1 [ to nid-value2 ] ] |
|
Display LSP statistics. |
display mpls lsp statistics |
|
Display MPLS summary information. |
display mpls summary |
|
Display ILM entries (in standalone mode). |
display mpls forwarding ilm [ label ] [ slot slot-number ] |
|
Display ILM entries (in IRF mode). |
display mpls forwarding ilm [ label ] [ chassis chassis-number slot slot-number ] |
|
Display NHLFE entries (in standalone mode). |
display mpls forwarding nhlfe [ nid ] [ slot slot-number ] |
|
Display NHLFE entries (in IRF mode). |
display mpls forwarding nhlfe [ nid ] [ chassis chassis-number slot slot-number ] |
Configuring a static LSP
Overview
A static label switched path (LSP) is established by manually specifying the incoming label and outgoing label on each node (ingress, transit, or egress node) of the forwarding path.
Static LSPs consume fewer resources, but they cannot automatically adapt to network topology changes. Therefore, static LSPs are suitable for small and stable networks with simple topologies.
Follow these guidelines to establish a static LSP:
· The ingress node performs the following operations:
a. Determines an FEC for a packet according to the destination address.
b. Adds the label for that FEC into the packet.
c. Forwards the packet to the next hop or out of the outgoing interface.
Therefore, on the ingress node, you must specify the outgoing label for the destination address (the FEC) and the next hop or the outgoing interface.
· A transit node swaps the label carried in a received packet with a specific label, and forwards the packet to the next hop or out of the outgoing interface. Therefore, on each transit node, you must specify the incoming label, the outgoing label, and the next hop or the outgoing interface.
· If the penultimate hop popping function is not configured, an egress node pops the incoming label of a packet, and performs label forwarding according to the inner label or IP forwarding. Therefore, on the egress node, you only need to specify the incoming label.
· The outgoing label specified on an LSR must be the same as the incoming label specified on the directly connected downstream LSR.
Feature and software version compatibility
The static LSP feature is available in Release 1138P01 and later versions.
Configuration prerequisites
Before you configure a static LSP, perform the following tasks:
· Identify the ingress node, transit nodes, and egress node of the LSP.
· Enable MPLS on all interfaces that participate in MPLS forwarding. For more information, see "Configuring basic MPLS."
· Make sure the ingress node has a route to the destination address of the LSP. This is not required on transit and egress nodes.
Configuration procedure
To configure a static LSP:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the ingress node of the static LSP. |
static-lsp ingress lsp-name destination dest-addr { mask | mask-length } { nexthop next-hop-addr | outgoing-interface interface-type interface-number } out-label out-label |
If you specify a next hop for the static LSP, make sure the ingress node has an active route to the specified next hop address. |
|
3. Configure the transit node of the static LSP. |
static-lsp transit lsp-name in-label in-label { nexthop next-hop-addr | outgoing-interface interface-type interface-number } out-label out-label |
If you specify a next hop for the static LSP, make sure the transit node has an active route to the specified next hop address. |
|
4. Configure the egress node of the static LSP. |
static-lsp egress lsp-name in-label in-label |
You do not need to configure this command if the outgoing label configured on the penultimate hop of the static LSP is 0 or 3. |
Displaying static LSPs
Execute display commands in any view.
|
Task |
Command |
|
Display static LSP information. |
display mpls static-lsp [ lsp-name lsp-name ] |
Static LSP configuration example
Network requirements
Switch A, Switch B, and Switch C all support MPLS.
Establish static LSPs between Switch A and Switch C, so that subnets 11.1.1.0/24 and 21.1.1.0/24 can access each other over MPLS.

Configuration restrictions and guidelines
· For an LSP, the outgoing label specified on an LSR must be identical with the incoming label specified on the downstream LSR.
· LSPs are unidirectional. You must configure an LSP for each direction of the data forwarding path.
· A route to the destination address of the LSP must be available on the ingress node and the egress node, but it is not needed on transit nodes. Therefore, you do not need to configure a routing protocol to ensure IP connectivity among all switches.
Configuration procedure
1. Create VLANs and configure IP addresses for all interfaces, including the loopback interfaces, as shown in Figure 8. (Details not shown.)
2. Configure a static route to the destination address of each LSP:
# On Switch A, configure a static route to network 21.1.1.0/24.
<SwitchA> system-view
[SwitchA] ip route-static 21.1.1.0 24 10.1.1.2
# On Switch C, configure a static route to network 11.1.1.0/24.
<SwitchC> system-view
[SwitchC] ip route-static 11.1.1.0 255.255.255.0 20.1.1.1
3. Configure basic MPLS on the switches:
# Configure Switch A.
[SwitchA] mpls lsr-id 1.1.1.9
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] mpls enable
[SwitchA-Vlan-interface2] quit
# Configure Switch B.
[SwitchB] mpls lsr-id 2.2.2.9
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] quit
[SwitchB] interface vlan-interface 3
[SwitchB-Vlan-interface3] mpls enable
[SwitchB-Vlan-interface3] quit
# Configure Switch C.
[SwitchC] mpls lsr-id 3.3.3.9
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] mpls enable
[SwitchC-Vlan-interface3] quit
4. Configure a static LSP from Switch A to Switch C:
# Configure the LSP ingress node, Switch A.
[SwitchA] static-lsp ingress AtoC destination 21.1.1.0 24 nexthop 10.1.1.2 out-label 30
# Configure the LSP transit node, Switch B.
[SwitchB] static-lsp transit AtoC in-label 30 nexthop 20.1.1.2 out-label 50
# Configure the LSP egress node, Switch C.
[SwitchC] static-lsp egress AtoC in-label 50
5. Configure a static LSP from Switch C to Switch A:
# Configure the LSP ingress node, Switch C.
[SwitchC] static-lsp ingress CtoA destination 11.1.1.0 24 nexthop 20.1.1.1 out-label 40
# Configure the LSP transit node, Switch B.
[SwitchB] static-lsp transit CtoA in-label 40 nexthop 10.1.1.1 out-label 70
# Configure the LSP egress node, Switch A.
[SwitchA] static-lsp egress CtoA in-label 70
Verifying the configuration
# Display static LSP information on switches. This example uses Switch A.
[SwitchA] display mpls static-lsp
Total: 2
Name FEC In/Out Label Nexthop/Out Interface State
AtoC 21.1.1.0/24 NULL/30 10.1.1.2 Up
CtoA -/- 70/NULL - Up
# Test the connectivity of the LSP from Switch A to Switch C.
[SwitchA] ping mpls -a 11.1.1.1 ipv4 21.1.1.0 24
MPLS Ping FEC: 21.1.1.0/24 : 100 data bytes
100 bytes from 20.1.1.2: Sequence=1 time=4 ms
100 bytes from 20.1.1.2: Sequence=2 time=1 ms
100 bytes from 20.1.1.2: Sequence=3 time=1 ms
100 bytes from 20.1.1.2: Sequence=4 time=1 ms
100 bytes from 20.1.1.2: Sequence=5 time=1 ms
--- FEC: 21.1.1.0/24 ping statistics ---
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max = 1/1/4 ms
# Test the connectivity of the LSP from Switch C to Switch A.
[SwitchC] ping mpls -a 21.1.1.1 ipv4 11.1.1.0 24
MPLS Ping FEC: 11.1.1.0/24 : 100 data bytes
100 bytes from 10.1.1.1: Sequence=1 time=5 ms
100 bytes from 10.1.1.1: Sequence=2 time=1 ms
100 bytes from 10.1.1.1: Sequence=3 time=1 ms
100 bytes from 10.1.1.1: Sequence=4 time=1 ms
100 bytes from 10.1.1.1: Sequence=5 time=1 ms
--- FEC: 11.1.1.0/24 ping statistics ---
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max = 1/1/5 ms
Configuring LDP
Overview
The Label Distribution Protocol (LDP) dynamically distributes FEC-label mapping information between LSRs to establish LSPs.
Terminology
LDP session
Two LSRs establish a TCP-based LDP session to exchange FEC-label mappings.
LDP peer
Two LSRs that use LDP to exchange FEC-label mappings are LSR peers.
Label spaces and LDP identifiers
Label spaces include the following types:
· Per-interface label space—Each interface uses a single, independent label space. Different interfaces can use the same label values.
· Per-platform label space—Each LSR uses a single label space. The device only supports the per-platform label space.
A six-byte LDP Identifier (LDP ID) identifies a label space on an LSR. It is in the format of <LSR ID>:<label space number>, where:
· The LSR ID takes four bytes to identity the LSR.
· The label space number takes two bytes to identify a label space within the LSR.
A label space number of 0 indicates that the label space is a per-platform label space. A label space number other than 0 indicates a per-interface label space.
FECs and FEC-label mappings
MPLS groups packets with the same characteristics (such as the same destination or service class) into a class, called an "FEC." The packets of the same FEC are handled in the same way on an MPLS network.
LDP can classify FECs by destination IP address.
An LSR assigns a label for a FEC and advertises the FEC-label mapping, or FEC-label binding, to its peers in a Label Mapping message.
LDP messages
LDP mainly uses the following types of messages:
· Discovery messages—Declare and maintain the presence of LSRs, such as Hello messages.
· Session messages—Establish, maintain, and terminate sessions between LDP peers, such as Initialization messages used for parameter negotiation and Keepalive messages used to maintain sessions.
· Advertisement messages—Create, alter, and remove FEC-label mappings, such as Label Mapping messages used to advertise FEC-label mappings.
· Notification messages—Provide advisory information and notify errors, such as Notification messages.
LDP uses UDP to transport discovery messages for efficiency, and uses TCP to transport session, advertisement, and notification messages for reliability.
LDP operation
LDP operates in the following phases:
Discovering and maintaining LDP peers
The device supports only the Basic Discovery mechanism in the current software release. Using Basic Discovery, an LSR enabled with LDP sends Link Hello messages to multicast address 224.0.0.2 that identifies all routers on the subnet. All directly-connected LSRs can discover the LSR and establish a hello adjacency.
LDP peers send Hello messages at the hello interval to maintain a hello adjacency. If LDP receives no Hello message from a hello adjacency before the hello hold timer expires, it removes the hello adjacency.
Establishing and maintaining LDP sessions
LDP establishes a session with a peer in the following steps:
1. Establishes a TCP connection with the neighbor.
2. Negotiates session parameters such as LDP version, label distribution method, and Keepalive timer, and establishes an LDP session with the neighbor if the negotiation succeeds.
After a session is established, LDP sends LDP PDUs (an LDP PDU carries one or more LDP messages) to maintain the session. If no information is exchanged between the LDP peers within the Keepalive interval, LDP sends Keepalive messages at the Keepalive interval to maintain the session. If LDP receives no LDP PDU from a neighbor before the keepalive hold timer expires, or the last hello adjacency with the neighbor is removed, LDP terminates the session.
LDP can also send a Shutdown message to a neighbor to terminate the LDP session.
Establishing LSPs
LDP classifies FECs according to destination IP addresses in IP routing entries, creates FEC-label mappings, and advertises the mappings to LDP peers through LDP sessions. After an LDP peer receives a FEC-label mapping, it uses the received label and the label locally assigned to that FEC to create an LFIB entry for that FEC. When all LSRs (from the Ingress to the Egress) establish an LFIB entry for the FEC, an LSP is established exclusively for the FEC.
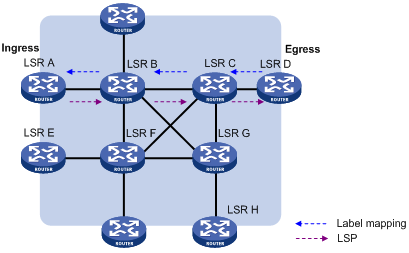
Figure 9 Dynamically establishing an LSP
Label distribution and control
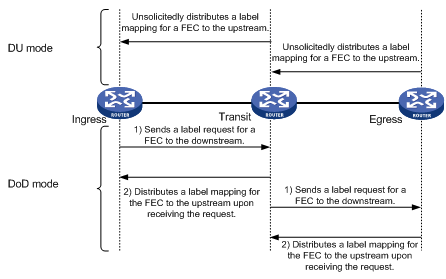
Label advertisement modes
Figure 10 Label advertisement modes
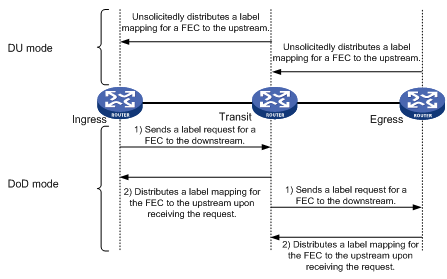
LDP advertises label-FEC mappings in one of the following ways:
· Downstream Unsolicited (DU) mode—Distributes FEC-label mappings to the upstream LSR, without waiting for label requests. The device supports only the DU mode.
· Downstream on Demand (DoD) mode—Sends a label request for a FEC to the downstream LSR. After receiving the label request, the downstream LSR distributes the FEC-label mapping for that FEC to the upstream LSR.
|
|
NOTE: A pair of upstream and downstream LSRs must use the same label advertisement mode. Otherwise, the LSP cannot be established. |
Label distribution control
LDP controls label distribution in one of the following ways:
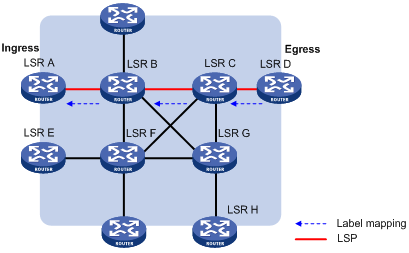
· Independent label distribution—Distributes a FEC-label mapping to an upstream LSR at any time. An LSR might distribute a mapping for a FEC to its upstream LSR before it receives a label mapping for that FEC from its downstream LSR. As shown in Figure 11, in DU mode, each LSR distributes a label mapping for a FEC to its upstream LSR whenever it is ready to label-switch the FEC, without waiting for a label mapping for the FEC from its downstream LSR. In DoD mode, an LSR distributes a label mapping for a FEC to its upstream LSR after it receives a label request for the FEC, without waiting for a label mapping for the FEC from its downstream LSR.
Figure 11 Independent label distribution control mode
· Ordered label distribution—Distributes a label mapping for a FEC to its upstream LSR only after it receives a label mapping for that FEC from its downstream LSR unless the local node is the egress node of the FEC. As shown in Figure 10, in DU mode, an LSR distributes a label mapping for a FEC to its upstream LSR only if it receives a label mapping for the FEC from its downstream LSR. In DoD mode, when an LSR (Transit) receives a label request for a FEC from its upstream LSR (Ingress), it continues to send a label request for the FEC to its downstream LSR (Egress). After the transit LSR receives a label mapping for the FEC from the egress LSR, it distributes a label mapping for the FEC to the ingress.
Label retention mode
The label retention mode specifies whether an LSR maintains a label mapping for a FEC learned from a neighbor that is not its next hop.
· Liberal label retention—Retains a received label mapping for a FEC regardless of whether the advertising LSR is the next hop of the FEC. This mechanism allows for quicker adaptation to topology changes, but it wastes system resources because LDP has to keep useless labels. The device only supports liberal label retention.
· Conservative label retention—Retains a received label mapping for a FEC only when the advertising LSR is the next hop of the FEC. This mechanism saves label resources, but it cannot quickly adapt to topology changes.
LDP GR
LDP GR overview
LDP Graceful Restart enables an LSR to retain MPLS forwarding entries during an LDP restart, ensuring continuous MPLS forwarding.

As shown in Figure 12, GR defines the following roles:
· GR restarter—An LSR that performs GR. It must be GR-capable.
· GR helper—A neighbor LSR that helps the GR restarter to complete GR.
The device can act as a GR restarter or a GR helper.
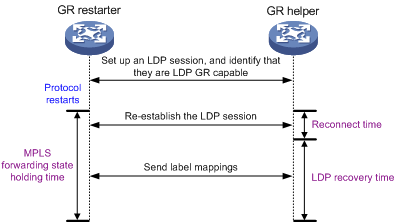
As shown in Figure 13, LDP GR works in the following steps:
1. LSRs establish an LDP session. The L flag of the Fault Tolerance TLV in their Initialization messages is set to 1 to indicate that they support LDP GR.
2. When LDP restarts, the GR restarter starts the MPLS Forwarding State Holding timer, and marks the MPLS forwarding entries as stale. When the GR helper detects that the LDP session with the GR restarter goes down, it marks the FEC-label mappings learned from the session as stale and starts the Reconnect timer received from the GR restarter.
3. After LDP completes restart, the GR restarter re-establishes an LDP session with the GR helper. If the LDP session is not set up before the Reconnect timer expires, the GR helper deletes the stale FEC-label mappings and the corresponding MPLS forwarding entries. If the LDP session is successfully set up before the Reconnect timer expires, the GR restarter sends the remaining time of the MPLS Forwarding State Holding timer as the LDP Recovery time to the GR helper.
4. After the LDP session is re-established, the GR helper starts the LDP Recovery timer.
5. The GR restarter and the GR helper exchange label mappings and update their MPLS forwarding tables.
The GR restarter compares each received label mapping against stale MPLS forwarding entries. If a match is found, the restarter deletes the stale mark for the matching entry. Otherwise, it adds a new entry for the label mapping.
The GR helper compares each received label mapping against stale FEC-label mappings. If a match is found, the helper deletes the stale mark for the matching mapping. Otherwise, it adds the received FEC-label mapping and a new MPLS forwarding entry for the mapping.
6. When the MPLS Forwarding State Holding timer expires, the GR restarter deletes all stale MPLS forwarding entries.
7. When the LDP Recovery timer expires, the GR helper deletes all stale FEC-label mappings.
LDP NSR
LDP nonstop routing (NSR) backs up protocol states and data (including LDP session and LSP information) from the active process to the standby process. When the LDP active process fails, the standby process becomes active and takes over processing seamlessly. The LDP peers are not notified of the LDP interruption. The LDP session stays in Operational state, and the forwarding is not interrupted.
The LDP active process fails when one of the following events occurs:
· The active process restarts.
· The MPU where the active process resides fails.
· The MPU where the active process resides performs an ISSU.
Choose either LDP NSR or LDP GR to ensure continuous traffic forwarding.
· Device requirements
? To use LDP NSR, the device must have two or more MPUs, and the active and standby processes for LDP reside on different MPUs.
? To use LDP GR, the device can have only one MPU on the device.
· LDP peer requirements
? With LDP NSR, LDP peers of the local device are not notified of any switchover event on the local device. The local device does not require help from a peer to restore the MPLS forwarding information.
? With LDP GR, the LDP peer must be able to identify the GR capability flag (in the Initialization message) of the GR restarter. The LDP peer acts as a GR helper to help the GR restarter to restore MPLS forwarding information.
LDP-IGP synchronization
Basic operating mechanism
LDP establishes LSPs based on the IGP optimal route. If LDP is not synchronized with IGP, MPLS traffic forwarding might be interrupted.
LDP is not synchronized with IGP when one of the following occurs:
· A link is up, and IGP advertises and uses this link. However, LDP LSPs on this link have not been established.
· An LDP session on a link is down, and LDP LSPs on the link have been removed. However, IGP still uses this link.
· The Ordered label distribution control mode is used. IGP used the link before the local device received the label mappings from the downstream LSR to establish LDP LSPs.
After LDP-IGP synchronization is enabled, IGP advertises the actual cost of a link only when LDP convergence on the link is completed. Before LDP convergence is completed, IGP advertises the maximum cost of the link. In this way, the link is visible on the IGP topology, but IGP does not select this link as the optimal route when other links are available. Therefore, the device can avoid discarding MPLS packets when there is not an LDP LSP established on the optimal route.
LDP convergence on a link is completed when all the followings occur:
· The local device establishes an LDP session to at least one peer, and the LDP session is already in Operational state.
· The local device has distributed the label mappings to at least one peer.
Notification delay for LDP convergence completion
By default, LDP immediately sends a notification to IGP that LDP convergence has completed. However, immediate notifications might cause MPLS traffic forwarding interruptions in one of the following scenarios:
· LDP peers use the Ordered label distribution control mode. The device has not received a label mapping from downstream at the time LDP notifies IGP that LDP convergence has completed.
· A large number of label mappings are distributed from downstream. Label advertisement is not completed when LDP notifies IGP that LDP convergence has completed.
To avoid traffic forwarding interruptions in these scenarios, configure the notification delay. When LDP convergence on a link is completed, LDP waits before notifying IGP.
Notification delay for LDP restart or active/standby switchover
When an LDP restart or an active/standby switchover occurs, LDP takes time to converge, and LDP notifies IGP of the LDP-IGP synchronization status as follows:
· If a notification delay is not configured, LDP immediately notifies IGP of the current synchronization states during convergence, and then updates the states after LDP convergence. This could impact IGP processing.
· If a notification delay is configured, LDP notifies IGP of the LDP-IGP synchronization states in bulk when one of the following events occurs:
? LDP recovers to the state before the restart or switchover.
? The maximum delay timer expires.
LDP FRR
A link or router failure on a path can cause packet loss until LDP completes LSP establishment on the new path. LDP FRR enables fast rerouting to minimize the failover time. LDP FRR bases on IP FRR and is enabled automatically after IP FRR is enabled.
You can use one of the following methods to enable IP FRR:
· Configure an IGP to automatically calculate a backup next hop.
· Configure an IGP to specify a backup next hop by using a routing policy.
Figure 14 Network diagram for LDP FRR
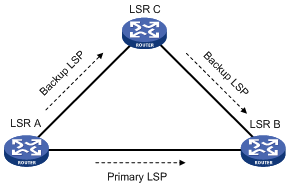
As shown in Figure 14, configure IP FRR on LSR A. The IGP automatically calculates a backup next hop or it specifies a backup next hop through a routing policy. LDP creates a primary LSP and a backup LSP according to the primary route and the backup route calculated by IGP. When the primary LSP operates correctly, it forwards the MPLS packets. When the primary LSP fails, LDP directs packets to the backup LSP.
When packets are forwarded through the backup LSP, IGP calculates the optimal path based on the new network topology. When IGP route convergence occurs, LDP establishes a new LSP according to the optimal path. If a new LSP is not established after IGP route convergence, traffic forwarding might be interrupted. As a best practice, enable LDP IGP synchronization to work with LDP FRR to reduce the traffic interruption time.
Protocols
RFC 5036, LDP Specification
Feature and software version compatibility
The LDP feature is available in Release 1138P01 and later versions.
LDP configuration task list
|
Tasks at a glance |
|
Enable LDP: 1. (Required.) Enabling LDP globally 2. (Required.) Enabling LDP on an interface |
|
(Optional.) Configuring Hello parameters |
|
(Optional.) Configuring LDP session parameters |
|
(Optional.) Configuring LDP backoff |
|
(Optional.) Configuring LDP MD5 authentication |
|
(Optional.) Configuring an LSP generation policy |
|
(Optional.) Configuring the LDP label distribution control mode |
|
(Optional.) Configuring a label advertisement policy |
|
(Optional.) Configuring a label acceptance policy |
|
(Optional.) Configuring LDP loop detection |
|
(Optional.) Configuring LDP GR |
|
(Optional.) Configuring LDP NSR |
|
(Optional.) Configuring LDP-IGP synchronization |
|
(Optional.) Configuring LDP FRR |
|
(Optional.) Resetting LDP sessions |
|
(Optional.) Enabling SNMP notifications for LDP |
Enabling LDP
To enable LDP, you must first enable LDP globally. Then, enable LDP on relevant interfaces or configure IGP to automatically enable LDP on those interfaces.
Enabling LDP globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable LDP for the local node or for a VPN. |
·
Enable LDP for the local node and enter LDP view: · Enable LDP for a VPN and enter LDP-VPN instance view: a. mpls ldp b. vpn-instance vpn-instance-name |
By default, LDP is disabled. |
|
3. Configure an LDP LSR ID. |
lsr-id lsr-id |
By default, the LDP LSR ID is the same as the MPLS LSR ID. |
Enabling LDP on an interface
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
If the interface is bound to a VPN instance, you must enable LDP for the VPN instance by using the vpn-instance command in LDP view. |
|
3. Enable LDP on the interface. |
mpls ldp enable |
By default, LDP is disabled on an interface. |
Configuring Hello parameters
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter the view of the interface where you want to establish an LDP session. |
interface interface-type interface-number |
N/A |
|
3. Configure the Link Hello hold time. |
mpls ldp timer hello-hold timeout |
By default, the Link Hello hold time is 15 seconds. |
|
4. Configure the Link Hello interval. |
mpls ldp timer hello-interval interval |
By default, the Link Hello interval is 5 seconds. |
Configuring LDP session parameters
This task configures the following LDP session parameters:
· Keepalive hold time and Keepalive interval.
· LDP transport address—IP address for establishing TCP connections.
When you configure LDP session parameters, follow these guidelines:
· The configured LDP transport address must be the IP address of an up interface on the device. Otherwise, no LDP session can be established.
· Make sure the LDP transport addresses of the local and peer LSRs can reach each other. Otherwise, no TCP connection can be established.
To configure LDP session parameters:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the Keepalive hold time. |
mpls ldp timer keepalive-hold timeout |
By default, the Keepalive hold time is 45 seconds. |
|
4. Configure the Keepalive interval. |
mpls ldp timer keepalive-interval interval |
By default, the Keepalive interval is 15 seconds. |
|
5. Configure the LDP transport address. |
mpls ldp transport-address { ip-address | interface } |
By default, the LDP transport address is the LSR ID of the local device if the interface where you want to establish an LDP session belongs to the public network. If the interface belongs to a VPN, the LDP transport address is the primary IP address of the interface. If the interface where you want to establish an LDP session is bound to a VPN instance, the interface with the IP address specified with this command must be bound to the same VPN instance. |
Configuring LDP backoff
If LDP session parameters (for example, the label advertisement mode) are incompatible, two LDP peers cannot establish a session, and they will keep negotiating with each other.
The LDP backoff mechanism can mitigate this problem by using an initial delay timer and a maximum delay timer. After LDP fails to establish a session with a peer LSR for the first time, LDP does not start an attempt until the initial delay timer expires. If the session setup fails again, LDP waits for two times the initial delay before the next attempt, and so forth until the maximum delay time is reached. After that, the maximum delay time will always take effect.
To configure LDP backoff:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDP view or enter LDP-VPN instance view. |
·
Enter LDP view: · Enter LDP-VPN instance view: a. mpls ldp b. vpn-instance vpn-instance-name |
N/A |
|
3. Configure the initial delay time and maximum delay time. |
backoff initial initial-time maximum maximum-time |
By default, the initial delay time is 15 seconds and the maximum delay time is 120 seconds. |
Configuring LDP MD5 authentication
To improve security for LDP sessions, you can configure MD5 authentication for the underlying TCP connections to check the integrity of LDP messages.
To configure LDP MD5 authentication:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDP view or enter LDP-VPN instance view. |
·
Enter LDP view: · Enter LDP-VPN instance view: a. mpls ldp b. vpn-instance vpn-instance-name |
N/A |
|
3. Enable LDP MD5 authentication. |
md5-authentication peer-lsr-id { cipher | plain } password |
By default, LDP MD5 authentication is disabled. |
Configuring an LSP generation policy
An LSP generation policy controls the number of LSPs generated by LDP in one of the following ways:
· Use all routes to establish LSPs.
· Use the routes permitted by an IP prefix list to establish LSPs. For information about IP prefix list configuration, see Layer 3—IP Routing Configuration Guide.
· Use only host routes with a 32-bit mask to establish LSPs.
To configure an LSP generation policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDP view or enter LDP-VPN instance view. |
·
Enter LDP view: · Enter LDP-VPN instance view: a. mpls ldp b. vpn-instance vpn-instance-name |
N/A |
|
3. Configure an LSP generation policy. |
lsp-trigger { all | prefix-list prefix-list-name } |
By default, LDP uses only host routes with a 32-bit mask to establish LSPs. |
Configuring the LDP label distribution control mode
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDP view or enter LDP-VPN instance view. |
·
Enter LDP view: · Enter LDP-VPN instance view: a. mpls ldp b. vpn-instance vpn-instance-name |
N/A |
|
3. Configure the label distribution control mode. |
label-distribution { independent | ordered } |
By default, the Ordered label distribution mode is used. To apply the new setting to LDP sessions established before the command is configured, you must reset the LDP sessions. |
Configuring a label advertisement policy
A label advertisement policy uses IP prefix lists to control the FEC-label mappings advertised to peers.
As shown in Figure 15, LSR A advertises label mappings for FECs permitted by IP prefix list B to LSR B and advertises label mappings for FECs permitted by IP prefix list C to LSR C.
Figure 15 Label advertisement control diagram
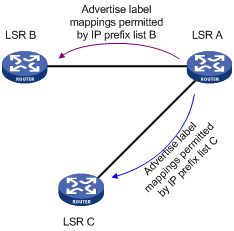
A label advertisement policy on an LSR and a label acceptance policy on its upstream LSR can achieve the same purpose. As a best practice, use label advertisement policies to reduce network load if downstream LSRs support label advertisement control.
Before you configure an LDP label advertisement policy, create an IP prefix list. For information about IP prefix list configuration, see Layer 3—IP Routing Configuration Guide.
To configure a label advertisement policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDP view or enter LDP-VPN instance view. |
·
Enter LDP view: · Enter LDP-VPN instance view: a. mpls ldp b. vpn-instance vpn-instance-name |
N/A |
|
3. Configure a label advertisement policy. |
advertise-label prefix-list prefix-list-name [ peer peer-prefix-list-name ] |
By default, LDP advertises all label mappings permitted by the LSP generation policy to all peers. |
Configuring a label acceptance policy
A label acceptance policy uses an IP prefix list to control the label mappings received from a peer.
As shown in Figure 16, LSR A uses an IP prefix list to filter label mappings from LSR B, and it does not filter label mappings from LSR C.
Figure 16 Label acceptance control diagram
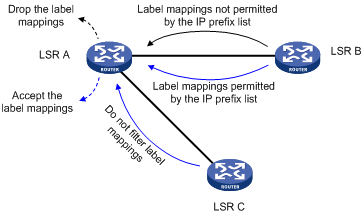
A label advertisement policy on an LSR and a label acceptance policy on its upstream LSR can achieve the same purpose. As a best practice, use the label advertisement policy to reduce network load.
You must create an IP prefix list before you configure a label acceptance policy. For information about IP prefix list configuration, see Layer 3—IP Routing Configuration Guide.
To configure a label acceptance policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDP view or enter LDP-VPN instance view. |
·
Enter LDP view: · Enter LDP-VPN instance view: a. mpls ldp b. vpn-instance vpn-instance-name |
N/A |
|
3. Configure a label acceptance policy. |
accept-label peer peer-lsr-id prefix-list prefix-list-name |
By default, LDP accepts all label mappings. |
Configuring LDP loop detection
LDP detects and terminates LSP loops in the following ways:
· Maximum hop count—LDP adds a hop count in a label request or label mapping message. The hop count value increments by 1 on each LSR. When the maximum hop count is reached, LDP considers that a loop has occurred and terminates the establishment of the LSP.
· Path vector—LDP adds LSR ID information in a label request or label mapping message. Each LSR checks whether its LSR ID is contained in the message. If it is not, the LSR adds its own LSR ID into the message. If it is, the LSR considers that a loop has occurred and terminates LSP establishment. In addition, when the number of LSR IDs in the message reaches the path vector limit, LDP also considers that a loop has occurred and terminates LSP establishment.
To configure LDP loop detection:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDP view or enter LDP-VPN instance view. |
·
Enter LDP view: · Enter LDP-VPN instance view: a. mpls ldp b. vpn-instance vpn-instance-name |
N/A |
|
3. Enable loop detection. |
loop-detect |
By default, loop detection is disabled. After loop detection is enabled, the device uses both the maximum hop count and the path vector methods to detect loops. |
|
4. Specify the maximum hop count. |
maxhops hop-number |
By default, the maximum hop count is 32. |
|
5. Specify the path vector limit. |
pv-limit pv-number |
By default, the path vector limit is 32. |
|
|
NOTE: The LDP loop detection feature is applicable only in networks comprised of devices that do not support TTL mechanism, such as ATM switches. Do not use LDP loop detection on other networks because it only results in extra LDP overhead. |
Configuring LDP GR
Before you configure LDP GR, enable LDP on the GR restarter and GR helpers.
To configure LDP GR:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDP view. |
mpls ldp |
N/A |
|
3. Enable LDP GR. |
graceful-restart |
By default, LDP GR is disabled. |
|
4. Configure the Reconnect timer for LDP GR. |
graceful-restart timer reconnect reconnect-time |
By default, the Reconnect time is 120 seconds. |
|
5. Configure the MPLS Forwarding State Holding timer for LDP GR. |
graceful-restart timer forwarding-hold hold-time |
By default, the MPLS Forwarding State Holding time is 180 seconds. |
Configuring LDP NSR
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDP view. |
mpls ldp |
N/A |
|
3. Enable LDP NSR. |
non-stop-routing |
By default, LDP NSR is disabled. |
Configuring LDP-IGP synchronization
After you enable LDP-IGP synchronization for an OSPF process, OSPF area, or an IS-IS process, LDP-IGP synchronization is enabled on the OSPF process interfaces or the IS-IS process interfaces.
You can execute the mpls ldp igp sync disable command to disable LDP-IGP synchronization on interfaces where LDP-IGP synchronization is not required.
Configuring LDP-OSPF synchronization
LDP-IGP synchronization is not supported for an OSPF process and its OSPF areas if the OSPF process belongs to a VPN instance.
To configure LDP-OSPF synchronization for an OSPF process:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter OSPF view. |
ospf [ process-id | router-id router-id ] * |
N/A |
|
3. Enable LDP-OSPF synchronization. |
mpls ldp sync |
By default, LDP-OSPF synchronization is disabled. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enter interface view. |
interface interface-type interface-number |
N/A |
|
6. (Optional.) Disable LDP-IGP synchronization on the interface. |
mpls ldp igp sync disable |
By default, LDP-IGP synchronization is not disabled on an interface. |
|
7. Return to system view. |
quit |
N/A |
|
8. Enter LDP view. |
mpls ldp |
N/A |
|
9. (Optional.) Set the delay for LDP to notify IGP of the LDP convergence. |
igp sync delay time |
By default, LDP immediately notifies IGP of the LDP convergence completion. |
|
10. (Optional.) Set the maximum delay for LDP to notify IGP of the LDP-IGP synchronization status after an LDP restart or active/standby switchover. |
igp sync delay on-restart time |
By default, the maximum notification delay is 90 seconds. |
To configure LDP-OSPF synchronization for an OSPF area:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter OSPF view. |
ospf [ process-id | router-id router-id ] * |
N/A |
|
3. Enter area view. |
area area-id |
N/A |
|
4. Enable LDP-OSPF synchronization. |
mpls ldp sync |
By default, LDP-OSPF synchronization is disabled. |
|
5. Return to system view. |
quit |
N/A |
|
6. Enter interface view. |
interface interface-type interface-number |
N/A |
|
7. (Optional.) Disable LDP-IGP synchronization on the interface. |
mpls ldp igp sync disable |
By default, LDP-IGP synchronization is not disabled on an interface. |
|
8. Return to system view. |
quit |
N/A |
|
9. Enter LDP view. |
mpls ldp |
N/A |
|
10. (Optional.) Set the delay for LDP to notify IGP of the LDP convergence. |
igp sync delay time |
By default, LDP immediately notifies IGP of the LDP convergence completion. |
|
11. (Optional.) Set the maximum delay for LDP to notify IGP of the LDP-IGP synchronization status after an LDP restart or active/standby switchover. |
igp sync delay on-restart time |
By default, the maximum notification delay is 90 seconds. |
Configuring LDP-ISIS synchronization
LDP-IGP synchronization is not supported for an IS-IS process that belongs to a VPN instance.
To configure LDP-ISIS synchronization for an IS-IS process:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IS-IS view. |
isis [ process-id ] |
N/A |
|
3. Enable LDP-ISIS synchronization. |
mpls ldp sync [ level-1 | level-2 ] |
By default, LDP-ISIS synchronization is disabled. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enter interface view. |
interface interface-type interface-number |
N/A |
|
6. (Optional.) Disable LDP-IGP synchronization on the interface. |
mpls ldp igp sync disable |
By default, LDP-IGP synchronization is not disabled on an interface. |
|
7. Return to system view. |
quit |
N/A |
|
8. Enter LDP view. |
mpls ldp |
N/A |
|
9. (Optional.) Set the delay for LDP to notify IGP of the LDP convergence completion. |
igp sync delay time |
By default, LDP immediately notifies IGP of the LDP convergence completion. |
|
10. (Optional.) Set the maximum delay for LDP to notify IGP of the LDP-IGP synchronization status after an LDP restart or an active/standby switchover occurs. |
igp sync delay on-restart time |
By default, the maximum notification delay is 90 seconds. |
Configuring LDP FRR
LDP FRR is based on IP FRR, and is enabled automatically after IP FRR is enabled. For information about configuring IP FRR, see Layer 3—IP Routing Configuration Guide.
Resetting LDP sessions
Changes to LDP session parameters take effect only on new LDP sessions. To apply the changes to an existing LDP session, you must reset all LDP sessions by executing the reset mpls ldp command.
Execute the reset mpls ldp command in user view.
|
Task |
Command |
Remarks |
|
Reset LDP sessions. |
reset mpls ldp [ vpn-instance vpn-instance-name ] [ peer peer-id ] |
If you specify the peer keyword, this command resets the LDP session to the specified peer without validating the session parameter changes. |
Enabling SNMP notifications for LDP
This feature enables generating SNMP notifications for LDP upon LDP session changes, as defined in RFC 3815. The generated SNMP notifications are sent to the SNMP module.
To enable SNMP notifications for LDP:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable SNMP notifications for LDP. |
snmp-agent trap enable ldp |
By default, SNMP notifications for LDP are enabled. |
For more information about SNMP notifications, see Network Management and Monitoring Configuration Guide.
Displaying and maintaining LDP
Execute display commands in any view.
|
Task |
Command |
|
Display LDP discovery information (in standalone mode). |
display mpls ldp discovery [ vpn-instance vpn-instance-name ] [ interface interface-type interface-number | peer peer-lsr-id ] [ verbose ] [ standby slot slot-number ] |
|
Display LDP discovery information (in IRF mode). |
display mpls ldp discovery [ vpn-instance vpn-instance-name ] [ interface interface-type interface-number | peer peer-lsr-id ] [ verbose ] [ standby chassis chassis-number slot slot-number ] |
|
Display LDP FEC-label mapping information (in standalone mode). |
display mpls ldp fec [ vpn-instance vpn-instance-name ] [ destination-address mask-length | summary ] [ standby slot slot-number ] |
|
Display LDP FEC-label mapping information (in IRF mode). |
display mpls ldp fec [ vpn-instance vpn-instance-name ] [ destination-address mask-length | summary ] [ standby chassis chassis-number slot slot-number ] |
|
Display LDP interface information. |
display mpls ldp interface [ interface-type interface-number ] |
|
Display LDP-IGP synchronization information. |
display mpls ldp igp sync [ interface interface-type interface-number ] |
|
Display LDP LSP information. |
display mpls ldp lsp [ vpn-instance vpn-instance-name ] [ destination-address mask-length ] |
|
Display LDP running parameters. |
display mpls ldp parameter [ vpn-instance vpn-instance-name ] |
|
Display LDP peer and session information (in standalone mode). |
display mpls ldp peer [ vpn-instance vpn-instance-name ] [ peer-lsr-id ] [ verbose ] [ standby slot slot-number ] |
|
Display LDP peer and session information (in IRF mode). |
display mpls ldp peer [ vpn-instance vpn-instance-name ] [ peer-lsr-id ] [ verbose ] [ standby chassis chassis-number slot slot-number ] |
|
Display LDP summary information (in standalone mode). |
display mpls ldp summary [ all | vpn-instance vpn-instance-name ] [ standby slot slot-number ] |
|
Display LDP summary information (in IRF mode). |
display mpls ldp summary [ all | vpn-instance vpn-instance-name ] [ standby chassis chassis-number slot slot-number ] |
LDP configuration examples
LDP LSP configuration example
Network requirements
Switch A, Switch B, and Switch C all support MPLS.
Configure LDP to establish LSPs between Switch A and Switch C, so subnets 11.1.1.0/24 and 21.1.1.0/24 can reach each other over MPLS.
Configure LDP to establish LSPs only for destinations 1.1.1.9/32, 2.2.2.9/32, 3.3.3.9/32, 11.1.1.0/24, and 21.1.1.0/24 on Switch A, Switch B, and Switch C.

Requirements analysis
· To ensure that the LSRs establish LSPs automatically, enable LDP on each LSR.
· To establish LDP LSPs, configure a routing protocol to ensure IP connectivity between the LSRs. This example uses OSPF.
· To control the number of LSPs, configure an LSP generation policy on each LSR.
Configuration procedure
1. Configure IP addresses and masks for interfaces, including the loopback interfaces, as shown in Figure 17. (Details not shown.)
2. Configure OSPF on each switch to ensure IP connectivity between them:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] ospf
[SwitchA-ospf-1] area 0
[SwitchA-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0
[SwitchA-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[SwitchA-ospf-1-area-0.0.0.0] network 11.1.1.0 0.0.0.255
[SwitchA-ospf-1-area-0.0.0.0] quit
[SwitchA-ospf-1] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] ospf
[SwitchB-ospf-1] area 0
[SwitchB-ospf-1-area-0.0.0.0] network 2.2.2.9 0.0.0.0
[SwitchB-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[SwitchB-ospf-1-area-0.0.0.0] network 20.1.1.0 0.0.0.255
[SwitchB-ospf-1-area-0.0.0.0] quit
[SwitchB-ospf-1] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] ospf
[SwitchC-ospf-1] area 0
[SwitchC-ospf-1-area-0.0.0.0] network 3.3.3.9 0.0.0.0
[SwitchC-ospf-1-area-0.0.0.0] network 20.1.1.0 0.0.0.255
[SwitchC-ospf-1-area-0.0.0.0] network 21.1.1.0 0.0.0.255
[SwitchC-ospf-1-area-0.0.0.0] quit
[SwitchC-ospf-1] quit
# Display routing tables on the switches, for example, on Switch A, to verify that the switches have learned the routes to each other.
[SwitchA] display ip routing-table
Destinations : 21 Routes : 21
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
1.1.1.9/32 Direct 0 0 127.0.0.1 InLoop0
2.2.2.9/32 OSPF 10 1 10.1.1.2 Vlan2
3.3.3.9/32 OSPF 10 2 10.1.1.2 Vlan2
10.1.1.0/24 Direct 0 0 10.1.1.1 Vlan2
10.1.1.0/32 Direct 0 0 10.1.1.1 Vlan2
10.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.255/32 Direct 0 0 10.1.1.1 Vlan2
11.1.1.0/24 Direct 0 0 11.1.1.1 Vlan4
11.1.1.0/32 Direct 0 0 11.1.1.1 Vlan4
11.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
11.1.1.255/32 Direct 0 0 11.1.1.1 Vlan4
20.1.1.0/24 OSPF 10 2 10.1.1.2 Vlan2
21.1.1.0/24 OSPF 10 3 10.1.1.2 Vlan2
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
3. Enable MPLS and LDP:
# Configure Switch A.
[SwitchA] mpls lsr-id 1.1.1.9
[SwitchA] mpls ldp
[SwitchA-ldp] quit
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] mpls enable
[SwitchA-Vlan-interface2] mpls ldp enable
[SwitchA-Vlan-interface2] quit
# Configure Switch B.
[SwitchB] mpls lsr-id 2.2.2.9
[SwitchB] mpls ldp
[SwitchB-ldp] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls ldp enable
[SwitchB-Vlan-interface2] quit
[SwitchB] interface vlan-interface 3
[SwitchB-Vlan-interface3] mpls enable
[SwitchB-Vlan-interface3] mpls ldp enable
[SwitchB-Vlan-interface3] quit
# Configure Switch C.
[SwitchC] mpls lsr-id 3.3.3.9
[SwitchC] mpls ldp
[SwitchC-ldp] quit
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] mpls enable
[SwitchC-Vlan-interface3] mpls ldp enable
[SwitchC-Vlan-interface3] quit
4. Configure LSP generation policies:
# On Switch A, create IP prefix list switcha, and configure LDP to use only the routes permitted by the prefix list to establish LSPs.
[SwitchA] ip prefix-list switcha index 10 permit 1.1.1.9 32
[SwitchA] ip prefix-list switcha index 20 permit 2.2.2.9 32
[SwitchA] ip prefix-list switcha index 30 permit 3.3.3.9 32
[SwitchA] ip prefix-list switcha index 40 permit 11.1.1.0 24
[SwitchA] ip prefix-list switcha index 50 permit 21.1.1.0 24
[SwitchA] mpls ldp
[SwitchA-ldp] lsp-trigger prefix-list switcha
[SwitchA-ldp] quit
# On Switch B, create IP prefix list switchb, and configure LDP to use only the routes permitted by the prefix list to establish LSPs.
[SwitchB] ip prefix-list switchb index 10 permit 1.1.1.9 32
[SwitchB] ip prefix-list switchb index 20 permit 2.2.2.9 32
[SwitchB] ip prefix-list switchb index 30 permit 3.3.3.9 32
[SwitchB] ip prefix-list switchb index 40 permit 11.1.1.0 24
[SwitchB] ip prefix-list switchb index 50 permit 21.1.1.0 24
[SwitchB] mpls ldp
[SwitchB-ldp] lsp-trigger prefix-list switchb
[SwitchB-ldp] quit
# On Switch C, create IP prefix list switchc, and configure LDP to use only the routes permitted by the prefix list to establish LSPs.
[SwitchC] ip prefix-list switchc index 10 permit 1.1.1.9 32
[SwitchC] ip prefix-list switchc index 20 permit 2.2.2.9 32
[SwitchC] ip prefix-list switchc index 30 permit 3.3.3.9 32
[SwitchC] ip prefix-list switchc index 40 permit 11.1.1.0 24
[SwitchC] ip prefix-list switchc index 50 permit 21.1.1.0 24
[SwitchC] mpls ldp
[SwitchC-ldp] lsp-trigger prefix-list switchc
[SwitchC-ldp] quit
Verifying the configuration
# Display LDP LSP information on switches, for example, on Switch A.
[SwitchA] display mpls ldp lsp
Status Flags: * - stale, L - liberal, B - backup
Statistics:
FECs: 5 Ingress LSPs: 3 Transit LSPs: 3 Egress LSPs: 2
FEC In/Out Label Nexthop OutInterface
1.1.1.9/32 3/-
-/1279(L)
2.2.2.9/32 -/3 10.1.1.2 Vlan-int2
1279/3 10.1.1.2 Vlan-int2
3.3.3.9/32 -/1278 10.1.1.2 Vlan-int2
1278/1278 10.1.1.2 Vlan-int2
11.1.1.0/24 1277/-
-/1277(L)
21.1.1.0/24 -/1276 10.1.1.2 Vlan-int2
1276/1276 10.1.1.2 Vlan-int2
# Test the connectivity of the LDP LSP from Switch A to Switch C.
[SwitchA] ping mpls -a 11.1.1.1 ipv4 21.1.1.0 24
MPLS Ping FEC: 21.1.1.0/24 : 100 data bytes
100 bytes from 20.1.1.2: Sequence=1 time=1 ms
100 bytes from 20.1.1.2: Sequence=2 time=1 ms
100 bytes from 20.1.1.2: Sequence=3 time=8 ms
100 bytes from 20.1.1.2: Sequence=4 time=2 ms
100 bytes from 20.1.1.2: Sequence=5 time=1 ms
--- FEC: 21.1.1.0/24 ping statistics ---
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max = 1/2/8 ms
# Test the connectivity of the LDP LSP from Switch C to Switch A.
[SwitchC] ping mpls -a 21.1.1.1 ipv4 11.1.1.0 24
MPLS Ping FEC: 11.1.1.0/24 : 100 data bytes
100 bytes from 10.1.1.1: Sequence=1 time=1 ms
100 bytes from 10.1.1.1: Sequence=2 time=1 ms
100 bytes from 10.1.1.1: Sequence=3 time=1 ms
100 bytes from 10.1.1.1: Sequence=4 time=1 ms
100 bytes from 10.1.1.1: Sequence=5 time=1 ms
--- FEC: 11.1.1.0/24 ping statistics ---
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max = 1/1/1 ms
Label acceptance control configuration example
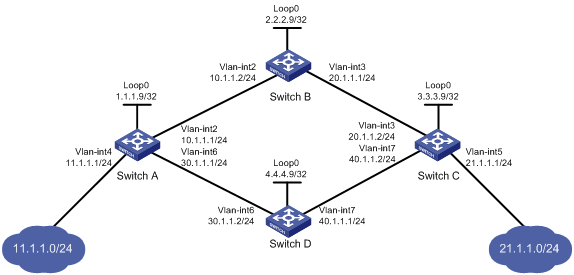
Network requirements
Two links, Switch A—Switch B—Switch C and Switch A—Switch D—Switch C, exist between subnets 11.1.1.0/24 and 21.1.1.0/24.
Configure LDP to establish LSPs only for routes to subnets 11.1.1.0/24 and 21.1.1.0/24.
Configure LDP to establish LSPs only on the link Switch A—Switch B—Switch C to forward traffic between subnets 11.1.1.0/24 and 21.1.1.0/24.
Requirements analysis
· To ensure that the LSRs establish LSPs automatically, enable LDP on each LSR.
· To establish LDP LSPs, configure a routing protocol to ensure IP connectivity between the LSRs. This example uses OSPF.
· To ensure that LDP establishes LSPs only for the routes 11.1.1.0/24 and 21.1.1.0/24, configure LSP generation policies on each LSR.
· To ensure that LDP establishes LSPs only over the link Switch A—Switch B—Switch C, configure label acceptance policies as follows:
? Switch A accepts only the label mapping for FEC 21.1.1.0/24 received from Switch B. Switch A denies the label mapping for FEC 21.1.1.0/24 received from Switch D.
? Switch C accepts only the label mapping for FEC 11.1.1.0/24 received from Switch B. Switch C denies the label mapping for FEC 11.1.1.0/24 received from Switch D.
Configuration procedure
1. Configure IP addresses and masks for interfaces, including the loopback interfaces, as shown in Figure 18. (Details not shown.)
2. Configure OSPF on each switch to ensure IP connectivity between them. (Details not shown.)
3. Enable MPLS and LDP:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] mpls lsr-id 1.1.1.9
[SwitchA] mpls ldp
[SwitchA-ldp] quit
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] mpls enable
[SwitchA-Vlan-interface2] mpls ldp enable
[SwitchA-Vlan-interface2] quit
[SwitchA] interface vlan-interface 6
[SwitchA-Vlan-interface6] mpls enable
[SwitchA-Vlan-interface6] mpls ldp enable
[SwitchA-Vlan-interface6] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] mpls lsr-id 2.2.2.9
[SwitchB] mpls ldp
[SwitchB-ldp] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls ldp enable
[SwitchB-Vlan-interface2] quit
[SwitchB] interface vlan-interface 3
[SwitchB-Vlan-interface3] mpls enable
[SwitchB-Vlan-interface3] mpls ldp enable
[SwitchB-Vlan-interface3] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] mpls lsr-id 3.3.3.9
[SwitchC] mpls ldp
[SwitchC-ldp] quit
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] mpls enable
[SwitchC-Vlan-interface3] mpls ldp enable
[SwitchC-Vlan-interface3] quit
[SwitchC] interface vlan-interface 7
[SwitchC-Vlan-interface7] mpls enable
[SwitchC-Vlan-interface7] mpls ldp enable
[SwitchC-Vlan-interface7] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] mpls lsr-id 4.4.4.9
[SwitchD] mpls ldp
[SwitchD-ldp] quit
[SwitchD] interface vlan-interface 6
[SwitchD-Vlan-interface6] mpls enable
[SwitchD-Vlan-interface6] mpls ldp enable
[SwitchD-Vlan-interface6] quit
[SwitchD] interface vlan-interface 7
[SwitchD-Vlan-interface7] mpls enable
[SwitchD-Vlan-interface7] mpls ldp enable
[SwitchD-Vlan-interface7] quit
4. Configure LSP generation policies:
# On Switch A, create IP prefix list switcha, and configure LDP to use only the routes permitted by the prefix list to establish LSPs.
[SwitchA] ip prefix-list switcha index 10 permit 11.1.1.0 24
[SwitchA] ip prefix-list switcha index 20 permit 21.1.1.0 24
[SwitchA] mpls ldp
[SwitchA-ldp] lsp-trigger prefix-list switcha
[SwitchA-ldp] quit
# On Switch B, create IP prefix list switchb, and configure LDP to use only the routes permitted by the prefix list to establish LSPs.
[SwitchB] ip prefix-list switchb index 10 permit 11.1.1.0 24
[SwitchB] ip prefix-list switchb index 20 permit 21.1.1.0 24
[SwitchB] mpls ldp
[SwitchB-ldp] lsp-trigger prefix-list switchb
[SwitchB-ldp] quit
# On Switch C, create IP prefix list switchc, and configure LDP to use only the routes permitted by the prefix list to establish LSPs.
[SwitchC] ip prefix-list switchc index 10 permit 11.1.1.0 24
[SwitchC] ip prefix-list switchc index 20 permit 21.1.1.0 24
[SwitchC] mpls ldp
[SwitchC-ldp] lsp-trigger prefix-list switchc
[SwitchC-ldp] quit
# On Switch D, create IP prefix list switchd, and configure LDP to use only the routes permitted by the prefix list to establish LSPs.
[SwitchD] ip prefix-list switchd index 10 permit 11.1.1.0 24
[SwitchD] ip prefix-list switchd index 20 permit 21.1.1.0 24
[SwitchD] mpls ldp
[SwitchD-ldp] lsp-trigger prefix-list switchd
[SwitchD-ldp] quit
5. Configure label acceptance policies:
# On Switch A, create an IP prefix list prefix-from-b that permits subnet 21.1.1.0/24. Switch A uses this list to filter FEC-label mappings received from Switch B.
[SwitchA] ip prefix-list prefix-from-b index 10 permit 21.1.1.0 24
# On Switch A, create an IP prefix list prefix-from-d that denies subnet 21.1.1.0/24. Switch A uses this list to filter FEC-label mappings received from Switch D.
[SwitchA] ip prefix-list prefix-from-d index 10 deny 21.1.1.0 24
# On Switch A, configure label acceptance policies to filter FEC-label mappings received from Switch B and Switch D.
[SwitchA] mpls ldp
[SwitchA-ldp] accept-label peer 2.2.2.9 prefix-list prefix-from-b
[SwitchA-ldp] accept-label peer 4.4.4.9 prefix-list prefix-from-d
[SwitchA-ldp] quit
# On Switch C, create an IP prefix list prefix-from-b that permits subnet 11.1.1.0/24. Switch C uses this list to filter FEC-label mappings received from Switch B.
[SwitchC] ip prefix-list prefix-from-b index 10 permit 11.1.1.0 24
# On Switch C, create an IP prefix list prefix-from-d that denies subnet 11.1.1.0/24. Switch A uses this list to filter FEC-label mappings received from Switch D.
[SwitchC] ip prefix-list prefix-from-d index 10 deny 11.1.1.0 24
# On Switch C, configure label acceptance policies to filter FEC-label mappings received from Switch B and Switch D.
[SwitchC] mpls ldp
[SwitchC-ldp] accept-label peer 2.2.2.9 prefix-list prefix-from-b
[SwitchC-ldp] accept-label peer 4.4.4.9 prefix-list prefix-from-d
[SwitchC-ldp] quit
Verifying the configuration
# Display LDP LSP information on switches, for example, on Switch A.
[SwitchA] display mpls ldp lsp
Status Flags: * - stale, L - liberal, B - backup
Statistics:
FECs: 2 Ingress LSPs: 1 Transit LSPs: 1 Egress LSPs: 1
FEC In/Out Label Nexthop OutInterface
11.1.1.0/24 1277/-
-/1148(L)
21.1.1.0/24 -/1149(L)
-/1276 10.1.1.2 Vlan-int2
1276/1276 10.1.1.2 Vlan-int2
The output shows that the next hop of the LSP for FEC 21.1.1.0/24 is Switch B (10.1.1.2). The LSP has been established over the link Switch A—Switch B—Switch C, not over the link Switch A—Switch D—Switch C.
# Test the connectivity of the LDP LSP from Switch A to Switch C.
[SwitchA] ping mpls -a 11.1.1.1 ipv4 21.1.1.0 24
MPLS Ping FEC: 21.1.1.0/24 : 100 data bytes
100 bytes from 20.1.1.2: Sequence=1 time=1 ms
100 bytes from 20.1.1.2: Sequence=2 time=1 ms
100 bytes from 20.1.1.2: Sequence=3 time=8 ms
100 bytes from 20.1.1.2: Sequence=4 time=2 ms
100 bytes from 20.1.1.2: Sequence=5 time=1 ms
--- FEC: 21.1.1.0/24 ping statistics ---
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max = 1/2/8 ms
# Test the connectivity of the LDP LSP from Switch C to Switch A.
[SwitchC] ping mpls -a 21.1.1.1 ipv4 11.1.1.0 24
MPLS Ping FEC: 11.1.1.0/24 : 100 data bytes
100 bytes from 10.1.1.1: Sequence=1 time=1 ms
100 bytes from 10.1.1.1: Sequence=2 time=1 ms
100 bytes from 10.1.1.1: Sequence=3 time=1 ms
100 bytes from 10.1.1.1: Sequence=4 time=1 ms
100 bytes from 10.1.1.1: Sequence=5 time=1 ms
--- FEC: 11.1.1.0/24 ping statistics ---
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max = 1/1/1 ms
Label advertisement control configuration example
Network requirements
Two links, Switch A—Switch B—Switch C and Switch A—Switch D—Switch C, exist between subnets 11.1.1.0/24 and 21.1.1.0/24.
Configure LDP to establish LSPs only for routes to subnets 11.1.1.0/24 and 21.1.1.0/24.
Configure LDP to establish LSPs only on the link Switch A—Switch B—Switch C to forward traffic between subnets 11.1.1.0/24 and 21.1.1.0/24.

Requirements analysis
· To ensure that the LSRs establish LSPs automatically, enable LDP on each LSR.
· To establish LDP LSPs, configure a routing protocol to ensure IP connectivity between the LSRs. This example uses OSPF.
· To ensure that LDP establishes LSPs only for the routes 11.1.1.0/24 and 21.1.1.0/24, configure LSP generation policies on each LSR.
· To ensure that LDP establishes LSPs only over the link Switch A—Switch B—Switch C, configure label advertisement policies as follows:
? Switch A advertises only the label mapping for FEC 11.1.1.0/24 to Switch B.
? Switch C advertises only the label mapping for FEC 21.1.1.0/24 to Switch B.
? Switch D does not advertise label mapping for FEC 21.1.1.0/24 to Switch A. Switch D does not advertise label mapping for FEC 11.1.1.0/24 to Switch C.
Configuration procedure
1. Configure IP addresses and masks for interfaces, including the loopback interfaces, as shown in Figure 19. (Details not shown.)
2. Configure OSPF on each switch to ensure IP connectivity between them. (Details not shown.)
3. Enable MPLS and LDP:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] mpls lsr-id 1.1.1.9
[SwitchA] mpls ldp
[SwitchA-ldp] quit
[SwitchA] interface vlan-interface 2
[SwitchA-Vlan-interface2] mpls enable
[SwitchA-Vlan-interface2] mpls ldp enable
[SwitchA-Vlan-interface2] quit
[SwitchA] interface vlan-interface 6
[SwitchA-Vlan-interface6] mpls enable
[SwitchA-Vlan-interface6] mpls ldp enable
[SwitchA-Vlan-interface6] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] mpls lsr-id 2.2.2.9
[SwitchB] mpls ldp
[SwitchB-ldp] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls ldp enable
[SwitchB-Vlan-interface2] quit
[SwitchB] interface vlan-interface 3
[SwitchB-Vlan-interface3] mpls enable
[SwitchB-Vlan-interface3] mpls ldp enable
[SwitchB-Vlan-interface3] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] mpls lsr-id 3.3.3.9
[SwitchC] mpls ldp
[SwitchC-ldp] quit
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] mpls enable
[SwitchC-Vlan-interface3] mpls ldp enable
[SwitchC-Vlan-interface3] quit
[SwitchC] interface vlan-interface 7
[SwitchC-Vlan-interface7] mpls enable
[SwitchC-Vlan-interface7] mpls ldp enable
[SwitchC-Vlan-interface7] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] mpls lsr-id 4.4.4.9
[SwitchD] mpls ldp
[SwitchD-ldp] quit
[SwitchD] interface vlan-interface 6
[SwitchD-Vlan-interface6] mpls enable
[SwitchD-Vlan-interface6] mpls ldp enable
[SwitchD-Vlan-interface6] quit
[SwitchD] interface vlan-interface 7
[SwitchD-Vlan-interface7] mpls enable
[SwitchD-Vlan-interface7] mpls ldp enable
[SwitchD-Vlan-interface7] quit
4. Configure LSP generation policies:
# On Switch A, create IP prefix list switcha, and configure LDP to use only the routes permitted by the prefix list to establish LSPs.
[SwitchA] ip prefix-list switcha index 10 permit 11.1.1.0 24
[SwitchA] ip prefix-list switcha index 20 permit 21.1.1.0 24
[SwitchA] mpls ldp
[SwitchA-ldp] lsp-trigger prefix-list switcha
[SwitchA-ldp] quit
# On Switch B, create IP prefix list switchb, and configure LDP to use only the routes permitted by the prefix list to establish LSPs.
[SwitchB] ip prefix-list switchb index 10 permit 11.1.1.0 24
[SwitchB] ip prefix-list switchb index 20 permit 21.1.1.0 24
[SwitchB] mpls ldp
[SwitchB-ldp] lsp-trigger prefix-list switchb
[SwitchB-ldp] quit
# On Switch C, create IP prefix list switchc, and configure LDP to use only the routes permitted by the prefix list to establish LSPs.
[SwitchC] ip prefix-list switchc index 10 permit 11.1.1.0 24
[SwitchC] ip prefix-list switchc index 20 permit 21.1.1.0 24
[SwitchC] mpls ldp
[SwitchC-ldp] lsp-trigger prefix-list switchc
[SwitchC-ldp] quit
# On Switch D, create IP prefix list switchd, and configure LDP to use only the routes permitted by the prefix list to establish LSPs.
[SwitchD] ip prefix-list switchd index 10 permit 11.1.1.0 24
[SwitchD] ip prefix-list switchd index 20 permit 21.1.1.0 24
[SwitchD] mpls ldp
[SwitchD-ldp] lsp-trigger prefix-list switchd
[SwitchD-ldp] quit
5. Configure label advertisement policies:
# On Switch A, create an IP prefix list prefix-to-b that permits subnet 11.1.1.0/24. Switch A uses this list to filter FEC-label mappings advertised to Switch B.
[SwitchA] ip prefix-list prefix-to-b index 10 permit 11.1.1.0 24
# On Switch A, create an IP prefix list peer-b that permits 2.2.2.9/32. Switch A uses this list to filter peers.
[SwitchA] ip prefix-list peer-b index 10 permit 2.2.2.9 32
# On Switch A, configure a label advertisement policy to advertise only the label mapping for FEC 11.1.1.0/24 to Switch B.
[SwitchA] mpls ldp
[SwitchA-ldp] advertise-label prefix-list prefix-to-b peer peer-b
[SwitchA-ldp] quit
# On Switch C, create an IP prefix list prefix-to-b that permits subnet 21.1.1.0/24. Switch C uses this list to filter FEC-label mappings advertised to Switch B.
[SwitchC] ip prefix-list prefix-to-b index 10 permit 21.1.1.0 24
# On Switch C, create an IP prefix list peer-b that permits 2.2.2.9/32. Switch C uses this list to filter peers.
[SwitchC] ip prefix-list peer-b index 10 permit 2.2.2.9 32
# On Switch C, configure a label advertisement policy to advertise only the label mapping for FEC 21.1.1.0/24 to Switch B.
[SwitchC] mpls ldp
[SwitchC-ldp] advertise-label prefix-list prefix-to-b peer peer-b
[SwitchC-ldp] quit
# On Switch D, create an IP prefix list prefix-to-a that denies subnet 21.1.1.0/24. Switch D uses this list to filter FEC-label mappings to be advertised to Switch A.
[SwitchD] ip prefix-list prefix-to-a index 10 deny 21.1.1.0 24
[SwitchD] ip prefix-list prefix-to-a index 20 permit 0.0.0.0 0 less-equal 32
# On Switch D, create an IP prefix list peer-a that permits 1.1.1.9/32. Switch D uses this list to filter peers.
[SwitchD] ip prefix-list peer-a index 10 permit 1.1.1.9 32
# On Switch D, create an IP prefix list prefix-to-c that denies subnet 11.1.1.0/24. Switch D uses this list to filter FEC-label mappings to be advertised to Switch C.
[SwitchD] ip prefix-list prefix-to-c index 10 deny 11.1.1.0 24
[SwitchD] ip prefix-list prefix-to-c index 20 permit 0.0.0.0 0 less-equal 32
# On Switch D, create an IP prefix list peer-c that permits subnet 3.3.3.9/32. Switch D uses this list to filter peers.
[SwitchD] ip prefix-list peer-c index 10 permit 3.3.3.9 32
# On Switch D, configure a label advertisement policy, so Switch D does not advertise label mappings for FEC 21.1.1.0/24 to Switch A, and does not advertise label mappings for FEC 11.1.1.0/24 to Switch C.
[SwitchD] mpls ldp
[SwitchD-ldp] advertise-label prefix-list prefix-to-a peer peer-a
[SwitchD-ldp] advertise-label prefix-list prefix-to-c peer peer-c
[SwitchD-ldp] quit
Verifying the configuration
# Display LDP LSP information on each switch.
[SwitchA] display mpls ldp lsp
Status Flags: * - stale, L - liberal, B - backup
Statistics:
FECs: 2 Ingress LSPs: 1 Transit LSPs: 1 Egress LSPs: 1
FEC In/Out Label Nexthop OutInterface
11.1.1.0/24 1277/-
-/1151(L)
-/1277(L)
21.1.1.0/24 -/1276 10.1.1.2 Vlan-int2
1276/1276 10.1.1.2 Vlan-int2
[SwitchB] display mpls ldp lsp
Status Flags: * - stale, L - liberal, B - backup
Statistics:
FECs: 2 Ingress LSPs: 2 Transit LSPs: 2 Egress LSPs: 0
FEC In/Out Label Nexthop OutInterface
11.1.1.0/24 -/1277 10.1.1.1 Vlan-int2
1277/1277 10.1.1.1 Vlan-int2
21.1.1.0/24 -/1149 20.1.1.2 Vlan-int3
1276/1149 20.1.1.2 Vlan-int3
[SwitchC] display mpls ldp lsp
Status Flags: * - stale, L - liberal, B - backup
Statistics:
FECs: 2 Ingress LSPs: 1 Transit LSPs: 1 Egress LSPs: 1
FEC In/Out Label Nexthop OutInterface
11.1.1.0/24 -/1277 20.1.1.1 Vlan-int3
1148/1277 20.1.1.1 Vlan-int3
21.1.1.0/24 1149/-
-/1276(L)
-/1150(L)
[SwitchD] display mpls ldp lsp
Status Flags: * - stale, L - liberal, B - backup
Statistics:
FECs: 2 Ingress LSPs: 0 Transit LSPs: 0 Egress LSPs: 2
FEC In/Out Label Nexthop OutInterface
11.1.1.0/24 1151/-
-/1277(L)
21.1.1.0/24 1150/-
The output shows that Switch A and Switch C has received FEC-label mappings only from Switch B. Switch B has received FEC-label mappings from both Switch A and Switch C. Switch D does not receive FEC-label mappings from Switch A or Switch C. LDP has established an LSP only over the link Switch A—Switch B—Switch C.
# Test the connectivity of the LDP LSP from Switch A to Switch C.
[SwitchA] ping mpls -a 11.1.1.1 ipv4 21.1.1.0 24
MPLS Ping FEC: 21.1.1.0/24 : 100 data bytes
100 bytes from 20.1.1.2: Sequence=1 time=1 ms
100 bytes from 20.1.1.2: Sequence=2 time=1 ms
100 bytes from 20.1.1.2: Sequence=3 time=8 ms
100 bytes from 20.1.1.2: Sequence=4 time=2 ms
100 bytes from 20.1.1.2: Sequence=5 time=1 ms
--- FEC: 21.1.1.0/24 ping statistics ---
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max = 1/2/8 ms
# Test the connectivity of the LDP LSP from Switch C to Switch A.
[SwitchC] ping mpls -a 21.1.1.1 ipv4 11.1.1.0 24
MPLS Ping FEC: 11.1.1.0/24 : 100 data bytes
100 bytes from 10.1.1.1: Sequence=1 time=1 ms
100 bytes from 10.1.1.1: Sequence=2 time=1 ms
100 bytes from 10.1.1.1: Sequence=3 time=1 ms
100 bytes from 10.1.1.1: Sequence=4 time=1 ms
100 bytes from 10.1.1.1: Sequence=5 time=1 ms
--- FEC: 11.1.1.0/24 ping statistics ---
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max = 1/1/1 ms
LDP FRR configuration example
Network requirements
Switch S, Switch A, and Switch D reside in the same OSPF domain. Configure OSPF FRR so LDP can establish a primary LSP and a backup LSP on the Switch S—Switch D and the Switch S—Switch A—Switch D links, respectively.
When the primary LSP operates correctly, traffic between subnets 11.1.1.0/24 and 21.1.1.0/24 is forwarded through the LSP.
When the primary LSP fails, traffic between the two subnets can be immediately switched to the backup LSP.
Requirements analysis
· To ensure that the LSRs establish LSPs automatically, enable LDP on each LSR.
· To establish LDP LSPs, configure a routing protocol to ensure IP connectivity between the LSRs. This example uses OSPF.
· To ensure that LDP establishes LSPs only for the routes 11.1.1.0/24 and 21.1.1.0/24, configure LSP generation policies on each LSR.
· To allow LDP to establish backup LSRs, configure OSPF FRR on Switch S and Switch D.
Configuration procedure
1. Configure IP addresses and masks for interfaces, including the loopback interfaces, as shown in Figure 20. (Details not shown.)
2. Configure OSPF on each switch to ensure IP connectivity between them. (Details not shown.)
3. Configure OSPF FRR by using one of the following methods:
? (Method 1.) Enable OSPF FRR to calculate a backup next hop by using the LFA algorithm:
# Configure Switch S.
<SwitchS> system-view
[SwitchS] bfd echo-source-ip 10.10.10.10
[SwitchS] ospf 1
[SwitchS-ospf-1] fast-reroute lfa
[SwitchS-ospf-1] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] bfd echo-source-ip 11.11.11.11
[SwitchD] ospf 1
[SwitchD-ospf-1] fast-reroute lfa
[SwitchD-ospf-1] quit
? (Method 2.) Enable OSPF FRR to specify a backup next hop by using a routing policy:
# Configure Switch S.
<SwitchS> system-view
[SwitchS] bfd echo-source-ip 10.10.10.10
[SwitchS] ip prefix-list abc index 10 permit 21.1.1.0 24
[SwitchS] route-policy frr permit node 10
[SwitchS-route-policy] if-match ip address prefix-list abc
[SwitchS-route-policy] apply fast-reroute backup-interface vlan-interface 12 backup-nexthop 12.12.12.2
[SwitchS-route-policy] quit
[SwitchS] ospf 1
[SwitchS-ospf-1] fast-reroute route-policy frr
[SwitchS-ospf-1] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] bfd echo-source-ip 10.10.10.10
[SwitchD] ip prefix-list abc index 10 permit 11.1.1.0 24
[SwitchD] route-policy frr permit node 10
[SwitchD-route-policy] if-match ip address prefix-list abc
[SwitchD-route-policy] apply fast-reroute backup-interface vlan-interface 24 backup-nexthop 24.24.24.2
[SwitchD-route-policy] quit
[SwitchD] ospf 1
[SwitchD-ospf-1] fast-reroute route-policy frr
[SwitchD-ospf-1] quit
4. Enable MPLS and LDP:
# Configure Switch S.
[SwitchS] mpls lsr-id 1.1.1.1
[SwitchS] mpls ldp
[SwitchS-mpls-ldp] quit
[SwitchS] interface vlan-interface 12
[SwitchS-Vlan-interface12] mpls enable
[SwitchS-Vlan-interface12] mpls ldp enable
[SwitchS-Vlan-interface12] quit
[SwitchS] interface vlan-interface 13
[SwitchS-Vlan-interface13] mpls enable
[SwitchS-Vlan-interface13] mpls ldp enable
[SwitchS-Vlan-interface13] quit
# Configure Switch D.
[SwitchD] mpls lsr-id 3.3.3.3
[SwitchD] mpls ldp
[SwitchD-mpls-ldp] quit
[SwitchD] interface vlan-interface 13
[SwitchD-Vlan-interface13] mpls enable
[SwitchD-Vlan-interface13] mpls ldp enable
[SwitchD-Vlan-interface13] quit
[SwitchD] interface vlan-interface 24
[SwitchD-Vlan-interface24] mpls enable
[SwitchD-Vlan-interface24] mpls ldp enable
[SwitchD-Vlan-interface24] quit
# Configure Switch A.
[SwitchA] mpls lsr-id 2.2.2.2
[SwitchA] mpls ldp
[SwitchA-mpls-ldp] quit
[SwitchA] interface vlan-interface 12
[SwitchA-Vlan-interface12] mpls enable
[SwitchA-Vlan-interface12] mpls ldp enable
[SwitchA-Vlan-interface12] quit
[SwitchA] interface vlan-interface 24
[SwitchA-Vlan-interface24] mpls enable
[SwitchA-Vlan-interface24] mpls ldp enable
[SwitchA-Vlan-interface24] quit
5. Configure LSP generation policies so LDP using all static routes and IGP routes to establish LSPs:
# Configure Switch S.
[SwitchS] mpls ldp
[SwitchS-ldp] lsp-trigger all
[SwitchS-ldp] quit
# Configure Switch D.
[SwitchD] mpls ldp
[SwitchD-ldp] lsp-trigger all
[SwitchD-ldp] quit
# Configure Switch A.
[SwitchA] mpls ldp
[SwitchA-ldp] lsp-trigger all
[SwitchA-ldp] quit
Verifying the configuration
# Verify that primary and backup LSPs have been established on Switch S.
[SwitchS] display mpls ldp lsp 21.1.1.0 24
Status Flags: * - stale, L - liberal, B - backup
Statistics:
FECs: 1 Ingress LSPs: 2 Transit LSPs: 2 Egress LSPs: 0
FEC In/Out Label Nexthop OutInterface
21.1.1.0/24 -/3 13.13.13.2 Vlan-int13
2174/3 13.13.13.2 Vlan-int13
-/3(B) 12.12.12.2 Vlan-int12
2174/3(B) 12.12.12.2 Vlan-int12
Configuring MPLS TE
Overview
TE and MPLS TE
Network congestion can degrade the network backbone performance. It might occur when network resources are inadequate or when load distribution is unbalanced. Traffic engineering (TE) is intended to avoid the latter situation where partial congestion might occur because of improper resource allocation.
TE can make the best use of network resources and avoid uneven load distribution by the following:
· Real-time monitoring of traffic and traffic load on network elements.
· Dynamic tuning of traffic management attributes, routing parameters, and resources constraints.
MPLS TE combines the MPLS technology and traffic engineering. It reserves resources by establishing LSP tunnels along the specified paths, allowing traffic to bypass congested nodes to achieve appropriate load distribution.
With MPLS TE, a service provider can deploy traffic engineering on the existing MPLS backbone to provide various services and optimize network resources management.
MPLS TE basic concepts
· CRLSP—Constraint-based Routed Label Switched Path. To establish a CRLSP, you must configure routing, and specify constrains, such as the bandwidth and explicit paths.
· MPLS TE tunnel—A virtual point-to-point connection from the ingress node to the egress node. Typically, an MPLS TE tunnel consists of one CRLSP. To deploy CRLSP backup or transmit traffic over multiple paths, you need to establish multiple CRLSPs for one class of traffic. In this case, an MPLS TE tunnel consists of a set of CRLSPs. An MPLS TE tunnel is identified by an MPLS TE tunnel interface on the ingress node. When the outgoing interface of a traffic flow is an MPLS TE tunnel interface, the traffic flow is forwarded through the CRLSP of the MPLS TE tunnel.
Static CRLSP establishment
A static CRLSP is established by manually specifying the incoming label, outgoing label, and other constraints on each hop along the path that the traffic travels. Static CRLSPs feature simple configuration, but they cannot automatically adapt to network changes.
For more information about static CRLSPs, see "Configuring a static CRLSP."
Dynamic CRLSP establishment
Dynamic CRLSPs are dynamically established as follows:
1. An IGP advertises TE attributes for links.
2. MPLS TE uses the CSPF algorithm to calculate the shortest path to the tunnel destination. The path must meet constraints such as bandwidth and explicit routing.
3. A label distribution protocol (such as RSVP-TE) advertises labels to establish CRLSPs and reserve bandwidth resources on each node along the calculated path.
Dynamic CRLSPs adapt to network changes and support CRLSP backup and fast reroute, but they require complicated configurations.
Advertising TE attributes
MPLS TE uses extended link state IGPs, such as OSPF and IS-IS, to advertise TE attributes for links.
TE attributes include the maximum bandwidth, maximum reservable bandwidth, non-reserved bandwidth for each priority, and the link attribute. The IGP floods TE attributes on the network. Each node collects the TE attributes of all links on all routers within the local area or at the same level to build up a TE database (TEDB).
Calculating paths
Based on the TEDB, MPLS TE uses the Constraint-based Shortest Path First (CSPF) algorithm, an improved SPF algorithm, to calculate the shortest, TE constraints-compliant path to the tunnel destination.
CSPF first prunes TE constraints-incompliant links from the TEDB. Then it performs SPF calculation to identify the shortest path (a set of LSR addresses) to an egress. CSPF calculation is usually performed on the ingress node of an MPLS TE tunnel.
TE constraints include the bandwidth, affinity, setup and holding priorities, and explicit path. They are configured on the ingress node of an MPLS TE tunnel.
· Bandwidth
Bandwidth constraints specify the class of service and the required bandwidth for the traffic to be forwarded along the MPLS TE tunnel. A link complies with the bandwidth constraints when the reservable bandwidth for the class type is greater than or equal to the bandwidth required by the class type.
· Affinity
Affinity determines which links a tunnel can use. The affinity attribute and its mask, and the link attribute are all 32-bit long. A link is available for a tunnel if the link attribute meets the following requirements:
? The link attribute bits corresponding to the affinity attribute's 1 bits whose mask bits are 1 must have at least one bit set to 1.
? The link attribute bits corresponding to the affinity attribute's 0 bits whose mask bits are 1 must have no bit set to 1.
The link attribute bits corresponding to the 0 bits in the affinity mask are not checked.
For example, if the affinity attribute is 0xFFFFFFF0 and its mask is 0x0000FFFF, a link is available for the tunnel when its link attribute bits meet the following requirements: the highest 16 bits each can be 0 or 1 (no requirements), the 17th through 28th bits must have at least one bit whose value is 1, and the lowest four bits must be 0.
· Setup priority and holding priority
If MPLS TE cannot find a qualified path for an MPLS TE tunnel, it can remove an existing MPLS TE tunnel and preempt its bandwidth to set up the new MPLS TE tunnel.
MPLS TE uses the setup priority and holding priority to make preemption decisions. For a new MPLS TE tunnel to preempt an existing MPLS TE tunnel, the setup priority of the new tunnel must be higher than the holding priority of the existing tunnel. Both setup and holding priorities are in the range of 0 to 7. A smaller value indicates a higher priority.
To avoid flapping caused by improper preemptions, the setup priority of a tunnel must not be higher than its holding priority, namely, the setup priority value must be equal to or greater than the holding priority value.
· Explicit path
Explicit path specifies the nodes to pass and the nodes to not pass for a tunnel.
Explicit paths include the following types:
? Strict explicit path—Among the nodes that the path must traverse, a node and its previous hop must be connected directly.
? Loose explicit path—Among the nodes that the path must traverse, a node and its previous hop can be connected indirectly.
Strict explicit path precisely specifies the path that an MPLS TE tunnel must traverse. Loose explicit path vaguely specifies the path that an MPLS TE tunnel must traverse. Strict explicit path and loose explicit path can be used together to specify that some nodes are directly connected and some nodes have other nodes in between.
Setting up a CRLSP through RSVP-TE
After calculating a path by using CSPF, MPLS TE uses a label distribution protocol to set up the CRLSP and reserves resources on each node of the path.
The device supports the label distribution protocol of RSVP-TE for MPLS TE. Resource Reservation Protocol (RSVP) reserves resources on each node along a path. Extended RSVP can support MPLS label distribution and allow resource reservation information to be transmitted with label bindings. This extended RSVP is called RSVP-TE.
For more information about RSVP, see "Configuring RSVP."
Traffic forwarding
After an MPLS TE tunnel is established, traffic is not forwarded on the tunnel automatically. You must direct the traffic to the tunnel by using one of the following methods.
Static routing
You can direct traffic to an MPLS TE tunnel by creating a static route that reaches the destination through the tunnel interface. This is the easiest way to implement MPLS TE tunnel forwarding. When the traffic to multiple networks is to be forwarded through the MPLS TE tunnel, you must configure multiple static routes, which are complicated to configure and difficult to maintain.
For more information about static routing, see Layer 3—IP Routing Configuration Guide.
Automatic route advertisement
You can also configure automatic route advertisement to forward traffic through an MPLS TE tunnel. Automatic route advertisement distributes the MPLS TE tunnel to the IGP (OSPF or IS-IS), so the MPLS TE tunnel can participate in IGP routing calculation. Automatic route advertisement is easy to configure and maintain.
Automatic route advertisement can be implemented by using the following methods:
· IGP shortcut—Also known as AutoRoute Announce. It considers the MPLS TE tunnel as a link that directly connects the tunnel ingress node and the egress node. Only the ingress node uses the MPLS TE tunnel during IGP route calculation.
· Forwarding adjacency—Considers the MPLS TE tunnel as a link that directly connects the tunnel ingress node and the egress node and advertises the link to the network through an IGP, so every node in the network uses the MPLS TE tunnel during IGP route calculation.
Figure 21 IGP shortcut and forwarding adjacency diagram

As shown in Figure 21, an MPLS TE tunnel is present from Router D to Router C. IGP shortcut enables only the ingress node Router D to use the MPLS TE tunnel in the IGP route calculation. Router A cannot use this tunnel to reach Router C. With forwarding adjacency enabled, Router A can learn this MPLS TE tunnel and transfer traffic to Router C by forwarding the traffic to Router D.
Make-before-break
Make-before-break is a mechanism to change an MPLS TE tunnel with minimum data loss and without using extra bandwidth.
In cases of tunnel reoptimization and automatic bandwidth adjustment, traffic forwarding is interrupted if the existing CRLSP is removed before a new CRLSP is established. The make-before-break mechanism makes sure that the existing CRLSP is removed after the new CRLSP is established and the traffic is switched to the new CRLSP. However, this wastes bandwidth resources if some links on the old and new CRLSPs are the same. It is because you need to reserve bandwidth on these links for the old and new CRLSPs separately. The make-before-break mechanism uses the SE resource reservation style to address this problem.
The resource reservation style refers to the style in which RSVP-TE reserves bandwidth resources during CRLSP establishment. The resource reservation style used by an MPLS TE tunnel is determined by the ingress node, and is advertised to other nodes through RSVP.
The device supports the following resource reservation styles:
· FF—Fixed-filter, where resources are reserved for individual senders and cannot be shared among senders on the same session.
· SE—Shared-explicit, where resources are reserved for senders on the same session and shared among them. SE is mainly used for make-before-break.
Figure 22 Diagram for make-before-break

As shown in Figure 22, a CRLSP with 30 M reserved bandwidth has been set up from Router A to Router D through the path Router A—Router B—Router C—Router D.
To increase the reserved bandwidth to 40 M, a new CRLSP must be set up through the path Router A—Router E—Router C—Router D. To achieve this purpose, RSVP-TE needs to reserve 30 M bandwidth for the old CRLSP and 40 M bandwidth for the new CRLSP on the link Router C—Router D, but the link bandwidth is not enough.
Using the make-before-break mechanism, the new CRLSP can share the bandwidth reserved for the old CRLSP. After the new CRLSP is set up, traffic is switched to the new CRLSP without service interruption, and then the old CRLSP is removed.
Route pinning
Route pinning enables CRLSPs to always use the original optimal path even if a new optimal route has been learned.
On a network where route changes frequently occur, you can use route pinning to avoid re-establishing CRLSPs upon route changes.
Tunnel reoptimization
Tunnel reoptimization allows you to manually or dynamically trigger the ingress node to recalculate a path. If the ingress node recalculates a better path, it creates a new CRLSP, switches traffic from the old CRLSP to the new, and then deletes the old CRLSP.
MPLS TE uses the tunnel reoptimization function to implement dynamic CRLSP optimization. For example, when MPLS TE sets up a tunnel, if a link on the optimal path does not have enough reservable bandwidth, MPLS TE sets up the tunnel on another path. When the link has enough bandwidth, the tunnel optimization function can switch the MPLS TE tunnel to the optimal path.
Automatic bandwidth adjustment
Because users cannot estimate accurately how much traffic they need to transmit through a service provider network, the service provider should be able to do the following:
· Create MPLS TE tunnels with the bandwidth initially requested by the users.
· Automatically tune the bandwidth resources when user traffic increases.
MPLS TE uses the automatic bandwidth adjustment function to meet this requirement. After the automatic bandwidth adjustment is enabled, the device periodically samples the output rate of the tunnel and computes the average output rate within the sampling interval. When the auto bandwidth adjustment frequency timer expires, MPLS TE resizes the tunnel bandwidth to the maximum average output rate sampled during the adjustment time to set up a new CRLSP. If the new CRLSP is set up successfully, MPLS TE switches traffic to the new CRLSP and clears the old CRLSP.
You can use a command to limit the maximum and minimum bandwidth. If the tunnel bandwidth calculated by auto bandwidth adjustment is greater than the maximum bandwidth, MPLS TE uses the maximum bandwidth to set up the new CRLSP. If it is smaller than the minimum bandwidth, MPLS TE uses the minimum bandwidth to set up the new CRLSP.
CRLSP backup
CRLSP backup uses a CRLSP to back up a primary CRLSP. When the ingress detects that the primary CRLSP fails, it switches traffic to the backup CRLSP. When the primary CRLSP recovers, the ingress switches traffic back.
CRLSP backup has the following modes:
· Hot standby—A backup CRLSP is created immediately after a primary CRLSP is created.
· Ordinary—A backup CRLSP is created after the primary CR-LSP fails.
FRR
Fast reroute (FRR) protects CRLSPs from link and node failures. FRR can implement 50-millisecond CRLSP failover.
After FRR is enabled for an MPLS TE tunnel, once a link or node fails on the primary CRLSP, FRR reroutes the traffic to a bypass tunnel, and the ingress node attempts to set up a new CRLSP. After the new CRLSP is set up, traffic is forwarded on the new CRLSP.
CRLSP backup provides end-to-end path protection for a CRLSP without time limitation. FRR provides quick but temporary protection for a link or node on a CRLSP.
Basic concepts
· Primary CRLSP—Protected CRLSP.
· Bypass tunnel—An MPLS TE tunnel used to protect a link or node of the primary CRLSP.
· Point of local repair—A PLR is the ingress node of the bypass tunnel. It must be located on the primary CRLSP but must not be the egress node of the primary CRLSP.
· Merge point—An MP is the egress node of the bypass tunnel. It must be located on the primary CRLSP but must not be the ingress node of the primary CRLSP.
Protection modes
FRR provides the following protection modes:
· Link protection—The PLR and the MP are connected through a direct link and the primary CRLSP traverses this link. When the link fails, traffic is switched to the bypass tunnel. As shown in Figure 23, the primary CRLSP is Router A—Router B—Router C—Router D, and the bypass tunnel is Router B—Router F—Router C. This mode is also called next-hop (NHOP) protection.
· Node protection—The PLR and the MP are connected through a device and the primary CRLSP traverses this device. When the device fails, traffic is switched to the bypass tunnel. As shown in Figure 24, the primary CRLSP is Router A—Router B—Router C—Router D—Router E, and the bypass tunnel is Router B—Router F—Router D. Router C is the protected device. This mode is also called next-next-hop (NNHOP) protection.
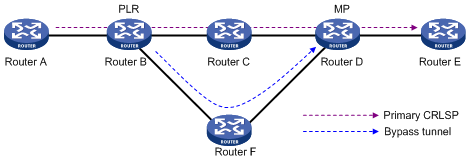
DiffServ-aware TE
DiffServ is a model that provides differentiated QoS guarantees based on class of service. MPLS TE is a traffic engineering solution that focuses on optimizing network resources allocation.
DiffServ-aware TE (DS-TE) combines DiffServ and TE to optimize network resources allocation on a per-service class basis. DS-TE defines different bandwidth constraints for class types. It maps each traffic class type to the CRLSP that is constraint-compliant for the class type.
The device supports these DS-TE modes:
· Prestandard mode—H3C proprietary DS-TE.
· IETF mode—Complies with RFC 4124, RFC 4125, and RFC 4127.
Basic concepts
· CT—Class Type. DS-TE allocates link bandwidth, implements constraint-based routing, and performs admission control on a per class type basis. A given traffic flow belongs to the same CT on all links.
· BC—Bandwidth Constraint. BC restricts the bandwidth for one or more CTs.
· Bandwidth constraint model—Algorithm for implementing bandwidth constraints on different CTs. A BC model comprises two factors, the maximum number of BCs (MaxBC) and the mappings between BCs and CTs. DS-TE supports two BC models, Russian Dolls Model (RDM) and Maximum Allocation Model (MAM).
· TE class—Defines a CT and a priority. The setup priority or holding priority of an MPLS TE tunnel for a CT must be the same as the priority of the TE class.
The prestandard and IETF modes of DS-TE have the following differences:
· The prestandard mode supports two CTs (CT 0 and CT 1), eight priorities, and up to 16 TE classes. The IETF mode supports four CTs (CT 0 through CT 3), eight priorities, and up to eight TE classes.
· The prestandard mode does not allow you to configure TE classes. The IETF mode allows for TE class configuration.
· The prestandard mode supports only RDM. The IETF mode supports both RDM and MAM.
· A device operating in prestandard mode cannot communicate with devices from some vendors. A device operating in IETF mode can communicate with devices from other vendors.
How DS-TE operates
A device takes the following steps to establish an MPLS TE tunnel for a CT:
1. Determines the CT.
A device classifies traffic according to your configuration:
? When configuring a dynamic MPLS TE tunnel, you can use the mpls te bandwidth command on the tunnel interface to specify a CT for the traffic to be forwarded by the tunnel.
? When configuring a static MPLS TE tunnel, you can use the bandwidth keyword to specify a CT for the traffic to be forwarded along the tunnel.
2. Checks whether bandwidth is enough for the CT.
You can use the mpls te max-reservable-bandwidth command on an interface to configure the bandwidth constraints of the interface. The device determines whether the bandwidth is enough to establish an MPLS TE tunnel for the CT.
The relation between BCs and CTs varies with different BC models:
In RDM model, a BC constrains the total bandwidth of multiple CTs, as shown in Figure 25:
· BC 2 is for CT 2. The total bandwidth for CT 2 cannot exceed BC 2.
· BC 1 is for CT 2 and CT 1. The total bandwidth for CT 2 and CT 1 cannot exceed BC 1.
· BC 0 is for CT 2, CT 1, and CT 0. The total bandwidth for CT 2, CT 1, and CT 0 cannot exceed BC 0. In this model, BC 0 equals the maximum reservable bandwidth of the link.
In cooperation with priority preemption, the RDM model can also implement bandwidth isolation between CTs. RDM is suitable for networks where traffic is unstable and traffic bursts might occur.
Figure 25 RDM bandwidth constraints model
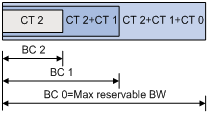
In MAM model, a BC constrains the bandwidth for only one CT. This ensures bandwidth isolation among CTs no matter whether preemption is used or not. Compared with RDM, MAM is easier to configure. MAM is suitable for networks where traffic of each CT is stable and no traffic bursts occur. Figure 26 shows an example:
· BC 0 is for CT 0. The bandwidth occupied by the traffic of CT 0 cannot exceed BC 0.
· BC 1 is for CT 1. The bandwidth occupied by the traffic of CT 1 cannot exceed BC 1.
· BC 2 is for CT 2. The bandwidth occupied by the traffic of CT 2 cannot exceed BC 2.
· The total bandwidth occupied by CT 0, CT 1, and CT 2 cannot exceed the maximum reservable bandwidth.
Figure 26 MAM bandwidth constraints model
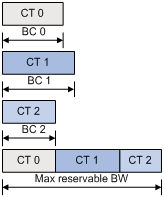
3. Checks whether the CT and the LSP setup/holding priority match an existing TE class.
An MPLS TE tunnel can be established for the CT only when the following conditions are met:
? Every node along the tunnel has a TE class that matches the CT and the LSP setup priority.
? Every node along the tunnel has a TE class that matches the CT and the LSP holding priority.
Bidirectional MPLS TE tunnel
MPLS Transport Profile (MPLS-TP) uses bidirectional MPLS TE tunnels to implement 1:1 and 1+1 protection switching and support in-band detection tools and signaling protocols such as OAM and PSC.
A bidirectional MPLS TE tunnel includes a pair of CRLSPs in opposite directions. It can be established in the following modes:
· Co-routed mode—Uses the extended RSVP-TE protocol to establish a bidirectional MPLS TE tunnel. RSVP-TE uses a Path message to advertise the labels assigned by the upstream LSR to the downstream LSR and a Resv message to advertise the labels assigned by the downstream LSR to the upstream LSR. During the delivery of the path message, a CRLSP in one direction is established. During the delivery of the Resv message, a CRLSP in the other direction is established. The CRLSPs of a bidirectional MPLS TE tunnel established in co-routed mode use the same path.
· Associated mode—In this mode, you establish a bidirectional MPLS TE tunnel by binding two unidirectional CRLSPs in opposite directions. The two CRLSPs can be established in different modes and use different paths. For example, one CRLSP is established statically and the other CRLSP is established dynamically by RSVP-TE.
For more information about establishing MPLS TE tunnel through RSVP-TE, the Path message, and the Resv message, see "Configuring RSVP."
Protocols and standards
· RFC 2702, Requirements for Traffic Engineering Over MPLS
· RFC 3564, Requirements for Support of Differentiated Service-aware MPLS Traffic Engineering
· RFC 4124, Protocol Extensions for Support of Diffserv-aware MPLS Traffic Engineering
· RFC 4125, Maximum Allocation Bandwidth Constraints Model for Diffserv-aware MPLS Traffic Engineering
· RFC 4127, Russian Dolls Bandwidth Constraints Model for Diffserv-aware MPLS Traffic Engineering
· ITU-T Recommendation Y.1720, Protection switching for MPLS networks
Feature and software version compatibility
The MPLS TE feature is available in Release 1138P01 and later versions.
MPLS TE configuration task list
To configure an MPLS TE tunnel to use a static CRLSP, complete the following tasks:
1. Enable MPLS TE on each node and interface that the MPLS TE tunnel traverses.
2. Create a tunnel interface on the ingress node of the MPLS TE tunnel, and specify the tunnel destination address (the address of the egress node).
3. Create a static CRLSP on each node that the MPLS TE tunnel traverses.
For information about creating a static CRLSP, see "Configuring a static CRLSP."
4. On the ingress node of the MPLS TE tunnel, configure the tunnel interface to reference the created static CRLSP.
5. On the ingress node of the MPLS TE tunnel, configure static routing or automatic route advertisement to direct traffic to the MPLS TE tunnel.
To configure an MPLS TE tunnel to use a CRLSP dynamically established by RSVP-TE, complete the following tasks:
1. Enable MPLS TE and RSVP on each node and interface that the MPLS TE tunnel traverses.
For information about enabling RSVP, see "Configuring RSVP."
2. Create a tunnel interface on the ingress node of the MPLS TE tunnel, specify the tunnel destination address (the address of the egress node), and configure the MPLS TE tunnel constraints (such as the tunnel bandwidth constraints and affinity) on the tunnel interface.
3. Configure the link TE attributes (such as the maximum link bandwidth and link attribute) on each interface that the MPLS TE tunnel traverses.
4. Configure an IGP on each node that the MPLS TE tunnel traverses, and configure the IGP to support MPLS TE, so that the nodes advertise the link TE attributes through the IGP.
5. On the ingress node of the MPLS TE tunnel, configure RSVP-TE to establish a CRLSP based on the tunnel constraints and link TE attributes.
6. On the ingress node of the MPLS TE tunnel, configure static routing or automatic route advertisement to direct traffic to the MPLS TE tunnel.
You can also configure other MPLS TE functions such as the DS-TE, automatic bandwidth adjustment, and FRR as needed.
To configure MPLS TE, perform the following tasks:
|
Tasks at a glance |
|
(Required.) Enabling MPLS TE |
|
(Required.) Configuring a tunnel interface |
|
(Optional.) Configuring DS-TE |
|
(Required.) Perform at least one of the following tasks to configure an MPLS TE tunnel: |
|
(Required.) Configuring traffic forwarding: · Configuring static routing to direct traffic to an MPLS TE tunnel · Configuring automatic route advertisement to direct traffic to an MPLS TE tunnel |
|
(Optional.) Configuring a bidirectional MPLS TE tunnel |
|
(Optional.) Configuring CRLSP backup Only MPLS TE tunnels established by RSVP-TE support this configuration. |
|
(Optional.) Configuring MPLS TE FRR Only MPLS TE tunnels established by RSVP-TE support this configuration. |
Enabling MPLS TE
Enable MPLS TE on each node and interface that the MPLS TE tunnel traverses.
Before you enable MPLS TE, complete the following tasks:
· Configure static routing or IGP to make sure all LSRs can reach each other.
· Enable MPLS. For information about enabling MPLS, see "Configuring basic MPLS."
To enable MPLS TE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable MPLS TE and enter MPLS TE view. |
mpls te |
By default, MPLS TE is disabled. |
|
3. Return to system view. |
quit |
N/A |
|
4. Enter interface view. |
interface interface-type interface-number |
N/A |
|
5. Enable MPLS TE for the interface. |
mpls te enable |
By default, MPLS TE is disabled on an interface. |
Configuring a tunnel interface
To configure an MPLS TE tunnel, you must create an MPLS TE tunnel interface and enter tunnel interface view. All MPLS TE tunnel attributes are configured in tunnel interface view.
Perform this task on the ingress node of the MPLS TE tunnel.
To configure a tunnel interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an MPLS TE tunnel interface and enter tunnel interface view. |
interface tunnel tunnel-number mode mpls-te |
By default, no tunnel interface is created. |
|
3. Configure an IP address for the tunnel interface. |
ip address ip-address { mask-length | mask } |
By default, a tunnel interface does not have an IP address. |
|
4. Specify the tunnel destination address. |
destination ip-address |
By default, no tunnel destination address is specified. |
Configuring DS-TE
DS-TE is configurable on any node that an MPLS TE tunnel traverses.
To configure DS-TE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE view. |
mpls te |
N/A |
|
3. (Optional.) Configure the DS-TE mode as IETF. |
ds-te mode ietf |
By default, the DS-TE mode is prestandard. |
|
4. (Optional.) Configure the BC model of IETF DS-TE as MAM. |
ds-te bc-model mam |
By default, the BC model of IETF DS-TE is RDM. |
|
5. Configure a TE class. |
ds-te te-class te-class-index class-type class-type-number priority pri-number |
The default TE classes for IETF mode are shown in Table 1. In prestandard mode, you cannot configure TE classes. |
Table 1 Default TE classes in IETF mode
|
TE Class |
CT |
Priority |
|
0 |
0 |
7 |
|
1 |
1 |
7 |
|
2 |
2 |
7 |
|
3 |
3 |
7 |
|
4 |
0 |
0 |
|
5 |
1 |
0 |
|
6 |
2 |
0 |
|
7 |
3 |
0 |
Configuring an MPLS TE tunnel to use a static CRLSP
To configure an MPLS TE tunnel to use a static CRLSP, perform the following tasks:
· Establish the static CRLSP.
· Specify the MPLS TE tunnel establishment mode as static.
· Configure the MPLS TE tunnel to reference the static CRLSP.
Other configurations, such as tunnel constraints and IGP extension, are not needed.
To configure an MPLS TE tunnel to use a static CRLSP:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a static CRLSP. |
See "Configuring a static CRLSP." |
N/A |
|
3. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
Execute this command on the ingress node. |
|
4. Specify the MPLS TE tunnel establishment mode as static. |
mpls te signaling static |
By default, MPLS TE uses RSVP-TE to establish a tunnel. |
|
5. Apply the static CRLSP to the tunnel interface. |
mpls te static-cr-lsp lsp-name |
By default, a tunnel does not reference any static CRLSP. |
Configuring an MPLS TE tunnel to use a dynamic CRLSP
To configure an MPLS TE tunnel to use a CRLSP dynamically established by RSVP-TE, complete the following tasks:
· Configure MPLS TE attributes for the links.
· Configure IGP TE extension to advertise link TE attributes, so as to generate a TEDB on each node.
· Configure tunnel constraints.
· Establish the CRLSP by using the signaling protocol RSVP-TE.
You must configure the IGP TE extension to form a TEDB. Otherwise, the path is created based on IGP routing rather than computed by CSPF.
Configuration task list
To establish an MPLS TE tunnel by using a dynamic CRLSP:
|
Tasks at a glance |
|
(Required.) Configuring MPLS TE attributes for a link |
|
(Required.) Advertising link TE attributes by using IGP TE extension |
|
(Required.) Configuring MPLS TE tunnel constraints |
|
(Required.) Establishing an MPLS TE tunnel by using RSVP-TE |
|
(Optional.) Controlling CRLSP path selection |
|
(Optional.) Controlling MPLS TE tunnel setup |
Configuring MPLS TE attributes for a link
MPLS TE attributes for a link include the maximum link bandwidth, the maximum reservable bandwidth, and the link attribute.
Perform this task on each interface that the MPLS TE tunnel traverses.
To configure the link TE attributes:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the maximum link bandwidth for MPLS TE traffic. |
mpls te max-link-bandwidth bandwidth-value |
By default, the maximum link bandwidth for MPLS TE traffic is 0. |
|
4. Configure the maximum reservable bandwidth. |
·
Configure the maximum reservable bandwidth of
the link (BC 0) and BC 1 in RDM model of the prestandard DS-TE: ·
Configure the maximum reservable bandwidth of
the link and the BCs in MAM model of the IETF DS-TE: ·
Configure the maximum
reservable bandwidth of the link and the BCs in RDM
model of the IETF DS-TE: |
Use one command according to the DS-TE mode and BC model configured in "Configuring DS-TE." By default, the maximum reservable bandwidth of a link is 0 kbps and each BC is 0 kbps. In RDM model, BC 0 is the maximum reservable bandwidth of a link. |
|
5. Configure the link attribute. |
mpls te link-attribute attribute-value |
By default, the link attribute value is 0x00000000. |
Advertising link TE attributes by using IGP TE extension
Both OSPF and IS-IS are extended to advertise link TE attributes. The extensions are called OSPF TE and IS-IS TE. If both OSPF TE and IS-IS TE are available, OSPF TE takes precedence.
Configuring OSPF TE
OSPF TE uses Type-10 opaque LSAs to carry the TE attributes for a link. Before you configure OSPF TE, you must enable opaque LSA advertisement and reception by using the opaque-capability enable command. For more information about opaque LSA advertisement and reception, see Layer 3—IP Routing Configuration Guide.
MPLS TE cannot reserve resources and distribute labels for an OSPF virtual link, and cannot establish a CRLSP through an OSPF virtual link. Therefore, make sure no virtual link exists in an OSPF area before you configure MPLS TE.
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter OSPF view. |
ospf [ process-id ] |
N/A |
|
3. Enable opaque LSA advertisement and reception. |
opaque-capability enable |
By default, opaque LSA advertisement and reception are enabled. For more information about this command, see Layer 3—IP Routing Command Reference. |
|
4. Enter area view. |
area area-id |
N/A |
|
5. Enable MPLS TE for the OSPF area. |
mpls te enable |
By default, an OSPF area does not support MPLS TE. |
Configuring IS-IS TE
IS-IS TE uses a sub-TLV of the extended IS reachability TLV (type 22) to carry TE attributes. Because the extended IS reachability TLV carries wide metrics, specify a wide metric-compatible metric style for the IS-IS process before enabling IS-IS TE. Available metric styles for IS-IS TE include wide, compatible, or wide-compatible. For more information about IS-IS, see Layer 3—IP Routing Configuration Guide.
To make sure IS-IS LSPs can be flooded on the network, specify an MTU that is equal to or greater than 512 bytes on each IS-IS enabled interface, because of the following:
· The length of the extended IS reachability TLV might reach the maximum of 255 bytes.
· The LSP header takes 27 bytes and the TLV header takes two bytes.
· The LSP might also carry the authentication information.
To configure IS-IS TE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an IS-IS process and enter IS-IS view. |
isis [ process-id ] |
By default, no IS-IS process exists. |
|
3. Specify a metric style. |
cost-style { wide | wide-compatible | compatible [ relax-spf-limit ] } |
By default, only narrow metric style packets can be received and sent. For more information about this command, see Layer 3—IP Routing Command Reference. |
|
4. Enable MPLS TE for the IS-IS process. |
mpls te enable [ Level-1 | Level-2 ] |
By default, an IS-IS process does not support MPLS TE. |
|
5. Specify the types of the sub-TLVs for carrying DS-TE parameters. |
te-subtlv { bw-constraint value | unreserved-bw-sub-pool value } * |
By default, the bw-constraint parameter is carried in sub-TLV 252, and the unreserved-bw-sub-pool parameter is carried in sub-TLV 251. |
Configuring MPLS TE tunnel constraints
Perform this task on the ingress node of the MPLS TE tunnel.
Configuring bandwidth constraints for an MPLS TE tunnel
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Configure bandwidth required for the tunnel, and specify a CT for the tunnel's traffic. |
mpls te bandwidth [ ct0 | ct1 | ct2 | ct3 ] bandwidth |
By default, no bandwidth is assigned, and the class type is CT 0. |
Configuring the affinity attribute for an MPLS TE tunnel
The associations between the link attribute and the affinity attribute might vary by vendor. To ensure the successful establishment of a tunnel between two devices from different vendors, correctly configure their respective link attribute and affinity attribute.
To configure the affinity attribute for an MPLS TE tunnel:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Configure an affinity for the MPLS TE tunnel. |
mpls te affinity-attribute attribute-value [ mask mask-value ] |
By default, the affinity is 0x00000000, and the mask is 0x00000000. The default affinity matches all link attributes. |
Configuring a setup priority and a holding priority for an MPLS TE tunnel
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Configure a setup priority and a holding priority for the MPLS TE tunnel. |
mpls te priority setup-priority [ hold-priority ] |
By default, the setup priority and the holding priority are both 7 for an MPLS TE tunnel. |
Configuring an explicit path for an MPLS TE tunnel
An explicit path is a set of nodes. The relationship between any two neighboring nodes on an explicit path can be either strict or loose.
· Strict—The two nodes must be directly connected.
· Loose—The two nodes can have devices in between.
When establishing an MPLS TE tunnel between areas or ASs, you must do the following:
· Use a loose explicit path.
· Specify the ABR or ASBR as the next hop of the path.
· Make sure the tunnel's ingress node and the ABR or ASBR can reach each other.
To configure an explicit path for a MPLS TE tunnel:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an explicit path and enter its view. |
explicit-path path-name |
By default, no explicit path exists on the device. |
|
3. Enable the explicit path. |
undo disable |
By default, an explicit path is enabled. |
|
4. Add or modify a node in the explicit path. |
nexthop [ index index-number ] ip-address [ exclude | include [ loose | strict ] ] |
By default, an explicit path does not include any node. You can specify the include keyword to have the CRLSP traverse the specified node or the exclude keyword to have the CRLSP bypass the specified node. |
|
5. Return to system view. |
quit |
N/A |
|
6. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
7. Configure the MPLS TE tunnel interface to use the explicit path, and specify a preference value for the explicit path. |
mpls te path preference value explicit-path path-name [ no-cspf ] |
By default, MPLS TE uses the calculated path to establish a CRLSP. |
Establishing an MPLS TE tunnel by using RSVP-TE
Before you configure this task, you must use the rsvp command and the rsvp enable command to enable RSVP on all nodes and interfaces that the MPLS TE tunnel traverses.
Perform this task on the ingress node of the MPLS TE tunnel.
To configure RSVP-TE to establish an MPLS TE tunnel:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Configure MPLS TE to use RSVP-TE to establish the tunnel. |
mpls te signaling rsvp-te |
By default, MPLS TE uses RSVP-TE to establish a tunnel. |
|
4. Specify an explicit path for the MPLS TE tunnel, and specify the path preference value. |
mpls te path preference value { dynamic | explicit-path path-name } [ no-cspf ] |
By default, MPLS TE uses the calculated path to establish a CRLSP. |
Controlling CRLSP path selection
Before performing the configuration tasks in this section, be aware of each configuration objective and its impact on your device.
MPLS TE uses CSPF to calculate a path according to the TEDB and constraints and sets up the CRLSP through RSVP-TE. MPLS TE provides measures that affect the CSPF calculation. You can use these measures to tune the path selection for CRLSP.
Configuring the metric type for path selection
Each MPLS TE link has two metrics: IGP metric and TE metric. By planning the two metrics, you can select different tunnels for different classes of traffic. For example, use the IGP metric to represent a link delay (a smaller IGP metric value indicates a lower link delay), and use the TE metric to represent a link bandwidth value (a smaller TE metric value indicates a bigger link bandwidth value).
You can establish two MPLS TE tunnels: Tunnel 1 for voice traffic and Tunnel 2 for video traffic. Configure Tunnel 1 to use IGP metrics for path selection, and configure Tunnel 2 to use TE metrics for path selection. As a result, the video service (with larger traffic) travels through the path that has larger bandwidth, and the voice traffic travels through the path that has lower delay.
To configure the metric type for tunnel path selection:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE view. |
mpls te |
N/A |
|
3. Specify the metric type to use when no metric type is explicitly configured for a tunnel. |
path-metric-type { igp | te } |
By default, a tunnel uses the TE metric for path selection. Execute this command on the ingress node of an MPLS TE tunnel. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
6. Specify the metric type for path selection. |
mpls te path-metric-type { igp | te } |
By default, no link metric type is specified and the one specified in MPLS TE view is used. Execute this command on the ingress node of an MPLS TE tunnel. |
|
7. Return to system view. |
quit |
N/A |
|
8. Enter interface view. |
interface interface-type interface-number |
N/A |
|
9. Assign a TE metric to the link. |
mpls te metric value |
By default, the link uses its IGP metric as the TE metric. This command is available on every interface that the MPLS TE tunnel traverses. |
Configuring route pinning
When route pinning is enabled, MPLS TE tunnel reoptimization and automatic bandwidth adjustment are not available.
Perform this task on the ingress node of an MPLS TE tunnel.
To configure route pinning:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Enable route pinning. |
mpls te route-pinning |
By default, route pinning is disabled. |
Configuring tunnel reoptimization
Tunnel reoptimization allows you to manually or dynamically trigger the ingress node to recalculate a path. If the ingress node recalculates a better path, it creates a new CRLSP, switches the traffic from the old CRLSP to the new CRLSP, and then deletes the old CRLSP.
Perform this task on the ingress node of an MPLS TE tunnel.
To configure tunnel reoptimization:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Enable tunnel reoptimization. |
mpls te reoptimization [ frequency seconds ] |
By default, tunnel reoptimization is disabled. |
|
4. Return to user view. |
return |
N/A |
|
5. (Optional.) Immediately reoptimize all MPLS TE tunnels that are enabled with the tunnel reoptimization function. |
mpls te reoptimization |
N/A |
Configuring TE flooding thresholds and interval
When the bandwidth of an MPLS TE link changes, IGP floods the new bandwidth information, so the ingress node can use CSPF to recalculate the path.
To prevent such recalculations from consuming too many resources, you can configure IGP to flood only significant bandwidth changes by setting the following flooding thresholds:
· Up threshold—When the percentage of the reservable-bandwidth increase to the maximum reservable bandwidth reaches the threshold, IGP floods the TE information.
· Down threshold—When the percentage of the reservable-bandwidth decrease to the maximum reservable bandwidth reaches the threshold, IGP floods the TE information.
You can also configure the flooding interval at which bandwidth changes that cannot trigger immediate flooding are flooded.
This task can be performed on all nodes that the MPLS TE tunnel traverses.
To configure TE flooding thresholds and the flooding interval:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the up/down threshold. |
mpls te bandwidth change thresholds { down | up } percent |
By default, the up/down threshold is 10% of the link reservable bandwidth. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enter MPLS TE view. |
mpls te |
N/A |
|
6. Configure the flooding interval. |
link-management periodic-flooding timer interval |
By default, the flooding interval is 180 seconds. |
Controlling MPLS TE tunnel setup
Before performing the configuration tasks in this section, be aware of each configuration objective and its impact on your device.
Perform the tasks in this section on the ingress node of the MPLS TE tunnel.
Enabling route and label recording
Perform this task to record the nodes that an MPLS TE tunnel traverses and the label assigned by each node. The recorded information helps you know about the path used by the MPLS TE tunnel and the label distribution information, and when the tunnel fails, it helps you locate the fault.
To enable route and label recording:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Record routes or record both routes and labels. |
·
To record routes: ·
To record both routes and labels: |
By default, both route recording and label recording are disabled. |
Enabling loop detection
Enabling loop detection also enables the route recording function, regardless of whether you have configured the mpls te record-route command. Loop detection enables each node of the tunnel to detect whether a loop has occurred according to the recorded route information.
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Enable loop detection. |
mpls te loop-detection |
By default, loop detection is disabled. |
Configuring tunnel setup retry
If the ingress node fails to establish an MPLS TE tunnel, it waits for the retry interval, and then tries to set up the tunnel again. It repeats this process until the tunnel is established or until the number of attempts reaches the maximum. If the tunnel cannot be established when the number of attempts reaches the maximum, the ingress waits for a longer period and then repeats the previous process.
To configure tunnel setup retry:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Configure maximum number of tunnel setup attempts. |
mpls te retry times |
By default, the maximum number of attempts is 3. |
|
4. Configure the retry interval. |
mpls te timer retry seconds |
By default, the retry interval is 2 seconds. |
Configuring automatic bandwidth adjustment
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE view. |
mpls te |
N/A |
|
3. Enable automatic bandwidth adjustment globally, and configure the output rate sampling interval. |
auto-bandwidth enable [ sample-interval seconds ] |
By default, the global auto bandwidth adjustment is disabled. The sampling interval configured in MPLS TE view applies to all MPLS TE tunnels. The output rates of all MPLS TE tunnels are recorded every sampling interval to calculate the actual average bandwidth of each MPLS TE tunnel in one sampling interval. |
|
4. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
5. Enable automatic bandwidth adjustment or output rate sampling for the MPLS TE tunnel. |
·
To enable automatic
bandwidth adjustment: ·
To enable output rate
sampling: |
Use either command. By default, automatic bandwidth adjustment and output rate sampling are disabled for an MPLS TE tunnel. |
|
6. Return to user view. |
return |
N/A |
|
7. (Optional.) Reset the automatic bandwidth adjustment. |
reset mpls te auto-bandwidth-adjustment timers |
After this command is executed, the system clears the output rate sampling information and the remaining time to the next bandwidth adjustment to start a new output rate sampling and bandwidth adjustment. |
Configuring RSVP resource reservation style
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Configure the resources reservation style for the tunnel. |
mpls te resv-style { ff | se } |
By default, the resource reservation style is SE. In current MPLS TE applications, tunnels are established usually by using the make-before-break mechanism. As a best practice, use the SE style. |
Configuring traffic forwarding
Perform the tasks in this section on the ingress node of the MPLS TE tunnel.
Configuring static routing to direct traffic to an MPLS TE tunnel
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a static route to direct traffic to an MPLS TE tunnel. |
For information about static routing commands, see Layer 3—IP Routing Command Reference. |
By default, no static route exists on the device. The interface specified in this command must be an MPLS TE tunnel interface in load sharing mode. |
Configuring automatic route advertisement to direct traffic to an MPLS TE tunnel
You can use either IGP shortcut or forwarding adjacency to implement automatic route advertisement. When you use IGP shortcut, you can specify a metric for the TE tunnel. If you assign an absolute metric, the metric is directly used as the MPLS TE tunnel's metric. If you assign a relative metric, the MPLS TE tunnel's metric is the assigned metric plus the IGP link metric.
Before configuring automatic route advertisement, perform the following tasks:
· Enable OSPF or IS-IS on the tunnel interface to advertise the tunnel interface address to OSPF or IS-IS.
· Enable MPLS TE for an OSPF area or an IS-IS process by executing the mpls te enable command in OSPF area view or IS-IS view.
Follow these restrictions and guidelines when you configure automatic route advertisement:
· The destination address of the MPLS TE tunnel can be the LSR ID of the egress node or the primary IP address of an interface on the egress node. As a best practice, configure the destination address of the MPLS TE tunnel as the LSR ID of the egress node.
· If you configure the tunnel destination address as the primary IP address of an interface on the egress node, you must enable MPLS TE, and configure OSPF or IS-IS on that interface. This makes sure the primary IP address of the interface can be advertised to its peer.
· The route to the tunnel interface address and the route to the tunnel destination must be in the same OSPF area or at the same IS-IS level.
Configuring IGP shortcut
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Enable IGP shortcut. |
mpls te igp shortcut [ isis | ospf ] |
By default, IGP shortcut is disabled. If no IGP is specified, both OSPF and IS-IS will include the MPLS TE tunnel in route calculation. |
|
4. Assign a metric to the MPLS TE tunnel. |
mpls te igp metric { absolute value | relative value } |
By default, the metric of an MPLS TE tunnel equals its IGP metric. |
Configuring forwarding adjacency
To use forwarding adjacency, you must establish two MPLS TE tunnels in opposite directions between two nodes, and configure forwarding adjacency on both the nodes.
To configure forwarding adjacency:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Enable forwarding adjacency. |
mpls te igp advertise [ hold-time value ] |
By default, forwarding adjacency is disabled. |
Configuring a bidirectional MPLS TE tunnel
Before you create a bidirectional MPLS TE tunnel, complete the following tasks:
· Disable the PHP feature on both ends of the tunnel.
· To set up a bidirectional MPLS TE tunnel in co-routed mode, you must specify the signaling protocol as RSVP-TE, and use the mpls te resv-style command to configure the resources reservation style as FF for the tunnel.
· To set up a bidirectional MPLS TE tunnel in associated mode and use RSVP-TE to set up one CRLSP of the tunnel, you must use the mpls te resv-style command to configure the resources reservation style as FF for the CR-LSP.
To create a bidirectional MPLS TE tunnel, create an MPLS TE tunnel interface on both ends of the tunnel and enable the bidirectional tunnel function on the tunnel interfaces:
· For a co-routed bidirectional tunnel, configure one end of the tunnel as the active end and the other end as the passive end, and specify the reverse CR-LSP at the passive end.
· For an associated bidirectional tunnel, specify a reverse CR-LSP at both ends of the tunnel.
To configure the active end of a co-routed bidirectional MPLS TE tunnel:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Configure a co-routed bidirectional MPLS TE tunnel and specify the local end as the active end of the tunnel. |
mpls te bidirectional co-routed active |
By default, no bidirectional tunnel is configured, and tunnels established on the tunnel interface are unidirectional MPLS TE tunnels. |
To configure the passive end of a co-routed bidirectional MPLS TE tunnel:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Configure a co-routed bidirectional MPLS TE tunnel and specify the local end as the passive end of the tunnel. |
mpls te bidirectional co-routed passive reverse-lsp lsr-id ingress-lsr-id tunnel-id tunnel-id |
By default, no bidirectional tunnel is configured, and tunnels established on the tunnel interface are unidirectional MPLS TE tunnels. |
To configure an associated bidirectional MPLS TE tunnel:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Configure an associated bidirectional MPLS TE tunnel. |
mpls te bidirectional associated reverse-lsp { lsp-name lsp-name | lsr-id ingress-lsr-id tunnel-id tunnel-id } } |
By default, no bidirectional tunnel is configured, and tunnels established on the tunnel interface are unidirectional MPLS TE tunnels. |
Configuring CRLSP backup
CRLSP backup provides end-to-end CRLSP protection. Only MPLS TE tunnels established through RSVP-TE support CRLSP backup.
Perform this task on the ingress node of an MPLS TE tunnel.
To configure CRLSP backup:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE tunnel interface view. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Enable CRLSP backup and specify the backup mode. |
mpls te backup { hot-standby | ordinary } |
By default, tunnel backup is disabled. |
|
4. Specify a path for the primary CRLSP and set the preference of the path. |
mpls te path preference value { dynamic | explicit-path path-name } [ no-cspf ] |
By default, MPLS TE uses the dynamically calculated path to set up the primary CRLSP. |
|
5. Specify a path for the backup CRLSP and set the preference of the path. |
mpls te backup-path preference value { dynamic | explicit-path path-name } [ no-cspf ] |
By default, MPLS TE uses the dynamically calculated path to set up the backup CRLSP. |
Configuring MPLS TE FRR
MPLS TE FRR provides temporary link or node protection on a CRLSP. When you configure FRR, note the following restrictions and guidelines:
· Do not configure both FRR and RSVP authentication on the same interface.
· Only MPLS TE tunnels established through RSVP-TE support FRR.
Enabling FRR
Perform this task on the ingress node of a primary CRLSP.
To enable FRR:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter tunnel interface view of the primary CRLSP. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Enable FRR. |
mpls te fast-reroute [ bandwidth ] |
By default, FRR is disabled. If you specify the bandwidth keyword, the primary CRLSP must have bandwidth protection. |
Configuring a bypass tunnel on the PLR
Overview
To configure FRR, you must configure bypass tunnels for primary CRLSPs on the PLR.
To configure bypass tunnels on the PLR, you can use the following methods:
· Manually configuring a bypass tunnel on the PLR—Create an MPLS TE tunnel on the PLR, and configure the tunnel as a bypass tunnel for a primary CRLSP. You need to specify the bandwidth and CT that the bypass tunnel can protect, and bind the bypass tunnel to the egress interface of the primary CRLSP.
You can configure up to three bypass tunnels for a primary CRLSP.
· Configuring the PLR to set up bypass tunnels automatically—Configure the automatic bypass tunnel setup function (also referred to as the auto FRR function) on the PLR. The PLR automatically sets up two bypass tunnels for each of its primary CRLSPs: one in link protection mode and the other in node protection mode. Automatically created bypass tunnels can be used to protect any type of CT, but they cannot provide bandwidth protection.
A primary tunnel can have both manually configured and automatically created bypass tunnels. The PLR will select one bypass tunnel to protect the primary CRLSP. The selected bypass tunnel is bound to the primary CRLSP.
Manually created bypass tunnels take precedence over automatically created bypass tunnels. An automatically created bypass tunnel in node protection mode takes precedence over an automatically created bypass tunnel in link protection mode. Among manually created bypass tunnels, the PLR selects the bypass tunnel for protecting the primary CRLSP by following these rules:
1. Selects a bypass tunnel according to the principles, as shown in Table 2.
2. Prefers the bypass tunnel in node protection mode over the one in link protection mode.
3. Prefers the bypass tunnel with a smaller ID over the one with a bigger tunnel ID.
Table 2 FRR protection principles
|
Bandwidth required by primary CRLSP |
Primary CRLSP requires bandwidth protection or not |
Bypass tunnel providing bandwidth protection |
Bypass tunnel providing no bandwidth protection |
|
0 |
Yes |
The primary CRLSP cannot be bound to the bypass tunnel. |
The primary CRLSP can be bound to the bypass tunnel if CT 0 or no CT is specified for the bypass tunnel. After binding, the RRO message does not carry the bandwidth protection flag. The bypass tunnel does not provide bandwidth protection for the primary CRLSP, and performs best-effort forwarding for traffic of the primary CRLSP. |
|
No |
|||
|
None-zero |
Yes |
The primary CRLSP can be bound to the bypass tunnel when all the following conditions are met: · The bandwidth that the bypass tunnel can protect is no less than the bandwidth required by the primary CRLSP. · There is not a CT specified for the bypass tunnel, or the specified CT is the same as that specified for the primary CRLSP. After binding, the RRO message carries the bandwidth protection flag, and the bypass tunnel provides bandwidth protection for the primary CRLSP. The primary CRLSP prefers bypass tunnels that provide bandwidth protection over those providing no bandwidth protection. |
The primary CRLSP can be bound to the bypass tunnel when one of the following conditions is met: · No CT is specified for the bypass tunnel. · The specified CT is the same as that specified for the primary CRLSP. After binding, the RRO message does not carry the bandwidth protection flag. This bypass tunnel is selected only when no bypass tunnel that provides bandwidth protection can be bound to the primary CRLSP. |
|
Non-zero |
No |
The primary CRLSP can be bound to the bypass tunnel when all the following conditions are met: · The bandwidth that the bypass tunnel can protect is no less than the bandwidth required by the primary CRLSP. · No CT that the bypass tunnel can protect is specified, or the specified CT is the same as that of the traffic on the primary CRLSP. After binding, the RRO message carries the bandwidth protection flag. This bypass tunnel is selected only when no bypass tunnel that does not provide bandwidth protection can be bound to the primary CRLSP. |
The primary CRLSP can be bound to the bypass tunnel when one of the following conditions is met: · No CT is specified for the bypass tunnel. · The specified CT is the same as that of the traffic on the primary CRLSP. After binding, the RRO message does not carry the bandwidth protection flag. The primary CRLSP prefers bypass tunnels that does not provide bandwidth protection over those providing bandwidth protection. |
Configuration restrictions and guidelines
When you configure a bypass tunnel on the PLR, follow these restrictions and guidelines:
· Use bypass tunnels to protect only critical interfaces or links when bandwidth is insufficient. Bypass tunnels are pre-established and require extra bandwidth.
· Make sure the bandwidth assigned to the bypass tunnel is no less than the total bandwidth needed by all primary CRLSPs to be protected by the bypass tunnel. Otherwise, some primary CRLSPs might not be protected by the bypass tunnel.
· A bypass tunnel typically does not forward data when the primary CRLSP operates correctly. For a bypass tunnel to also forward data during tunnel protection, you must assign adequate bandwidth to the bypass tunnel.
· A bypass tunnel cannot be used for services such as VPN.
· You cannot configure FRR for a bypass tunnel. A bypass tunnel cannot act as a primary CRLSP.
· Make sure the protected node or interface is not on the bypass tunnel.
· After you associate a primary CRLSP that does not require bandwidth protection with a bypass tunnel that provides bandwidth protection, the primary CRLSP occupies the bandwidth that the bypass tunnel protects. The bandwidth is protected on a first-come-first-served basis. The primary CRLSP that needs bandwidth protection cannot preempt the one that does not need bandwidth protection.
· After an FRR, the primary CRLSP will be down if you modify the bandwidth that the bypass tunnel can protect and your modification results in one of the following:
? The CT type changes.
? The bypass tunnel cannot protect adequate bandwidth as configured.
? FRR protection type (whether or not to provide bandwidth protection for the primary CRLSP) changes.
Manually configuring a bypass tunnel
The bypass tunnel setup method is the same as a normal MPLS TE tunnel. This section describes only FRR-related configurations.
To configure a bypass tunnel on the PLR:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter tunnel interface view of the bypass tunnel. |
interface tunnel tunnel-number [ mode mpls-te ] |
N/A |
|
3. Specify the destination address of the bypass tunnel. |
destination ip-address |
The bypass tunnel destination address is the LSR ID of the MP. |
|
4. Configure the bandwidth and the CT to be protected by the bypass tunnel. |
mpls te backup bandwidth [ ct0 | ct1 | ct2 | ct3 ] { bandwidth | un-limited } |
By default, the bandwidth and the CT to be protected by the bypass tunnel are not specified. |
|
5. Return to system view. |
quit |
N/A |
|
6. Enter interface view of the egress interface of a primary CRLSP. |
interface interface-type interface-number |
N/A |
|
7. Specify a bypass tunnel for the protected interface (the current interface). |
mpls te fast-reroute bypass-tunnel tunnel tunnel-number |
By default, no bypass tunnel is specified for an interface. |
Automatically setting up bypass tunnels
With auto FRR, if the PLR is the penultimate node of a primary CRLSP, the PLR does not create a node-protection bypass tunnel for the primary CRLSP.
To configure auto FRR on the PLR:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE view. |
mpls te |
N/A |
|
3. Enable the auto FRR function globally. |
auto-tunnel backup |
By default, the auto FRR function is disabled globally. |
|
4. Specify an interface number range for the automatically created bypass tunnels. |
tunnel-number min min-number max max-number |
By default, no interface number range is specified, and the PLR cannot set up a bypass tunnel automatically. |
|
5. (Optional.) Configure the PLR to create only link-protection bypass tunnels. |
nhop-only |
By default, the PLR automatically creates both a link-protection and a node-protection bypass tunnel for each of its primary CRLSPs. Execution of this command deletes all existing node-protection bypass tunnels automatically created for MPLS TE auto FRR. |
|
6. (Optional.) Configure a removal timer for unused bypass tunnels. |
timers removal unused seconds |
By default, a bypass tunnel is removed after it is unused for 3600 seconds. |
|
7. (Optional.) Return to system view. |
quit |
N/A |
|
8. (Optional.) Enter interface view. |
interface interface-type interface-number |
N/A |
|
9. (Optional.) Disable the auto FRR function on the interface. |
mpls te auto-tunnel backup disable |
By default, the auto FRR function is enabled on all RSVP-enabled interfaces after it is enabled globally. Execution of this command deletes all existing bypass tunnels automatically created on the interface for MPLS TE auto FRR. |
Configuring node fault detection
Perform this task to configure the RSVP hello mechanism or BFD on the PLR and the protected node to detect the node faults caused by signaling protocol faults. FRR does not need to use the RSVP hello mechanism or BFD to detect the node faults caused by the link faults between the PLR and the protected node.
You do not need to perform this task for FRR link protection.
To configure node fault detection:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view of the connecting interface between the PLR and the protected node. |
interface interface-type interface-number |
N/A |
|
3. Configure node fault detection. |
·
(Method 1) Enable RSVP hello extension
on the interface: ·
(Method 2) Enable BFD on the interface: |
By default, RSVP hello extension is disabled, and BFD is not configured. For more information about the rsvp hello enable command and the rsvp bfd enable command, see "Configuring RSVP." |
Configuring the optimal bypass tunnel selection interval
If you have specified multiple bypass tunnels for a primary CRLSP, MPLS TE selects an optimal bypass tunnel to protect the primary CRLSP. Sometimes, a bypass tunnel might become better than the current optimal bypass tunnel because, for example, the reservable bandwidth changes. Therefore, MPLS TE needs to poll the bypass tunnels periodically to update the optimal bypass tunnel.
Perform this task on the PLR to configure the interval for selecting an optimal bypass tunnel:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MPLS TE view. |
mpls te |
N/A |
|
3. Configure the interval for selecting an optimal bypass tunnel. |
fast-reroute timer interval |
By default, the interval is 300 seconds. |
Displaying and maintaining MPLS TE
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display information about explicit paths. |
display explicit-path [ path-name ] |
|
Display link and node information in an IS-IS TEDB. |
display isis mpls te advertisement [ [ level-1 | level-2 ] | [ originate-system system-id | local ] | verbose ] * [ process-id ] |
|
Display sub-TLV information for IS-IS TE. |
display isis mpls te configured-sub-tlvs [ process-id ] |
|
Display network information in an IS-IS TEDB. |
display isis mpls te network [ [ level-1 | level-2 ] | local | lsp-id lsp-id ]* [ process-id ] |
|
Display IS-IS tunnel interface information. |
display isis mpls te tunnel [ level-1 | level-2 ] [ process-id ] |
|
Display DS-TE information. |
display mpls te ds-te |
|
Display bandwidth information on MPLS TE-enabled interfaces. |
display mpls te link-management bandwidth-allocation [ interface interface-type interface-number ] |
|
Display MPLS TEDB information. |
display mpls te tedb { { isis { level-1 | level-2 } | ospf area area-id } | link ip-address | network | node [ local | mpls-lsr-id ] | summary } |
|
Display information about MPLS TE tunnel interfaces. |
display mpls te tunnel-interface [ tunnel number ] |
|
Display link and node information in an OSPF TEDB. |
display ospf [ process-id ] [ area area-id ] mpls te advertisement [ originate-router advertising-router-id | self-originate ] |
|
Display network information in an OSPF TEDB. |
display ospf [ process-id ] [ area area-id ] mpls te network [ originate-router advertising-router-id | self-originate ] |
|
Display OSPF tunnel interface information. |
display ospf [ process-id ] [ area area-id ] mpls te tunnel |
|
Reset the automatic bandwidth adjustment function. |
reset mpls te auto-bandwidth-adjustment timers |
MPLS TE configuration examples
Establishing an MPLS TE tunnel over a static CRLSP
Network requirements
Switch A, Switch B, and Switch C run IS-IS.
Establish an MPLS TE tunnel over a static CRLSP from Switch A to Switch C.
The MPLS TE tunnel requires a bandwidth of 2000 kbps. The maximum bandwidth of the link that the tunnel traverses is 10000 kbps. The maximum reservable bandwidth of the link is 5000 kbps.
Figure 27 Network diagram
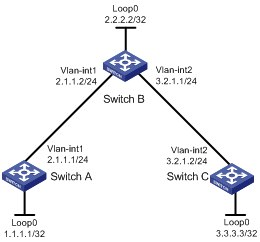
Configuration procedure
1. Configure IP addresses and masks for interfaces. (Details not shown.)
2. Configure IS-IS to advertise interface addresses, including the loopback interface address:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] isis 1
[SwitchA-isis-1] network-entity 00.0005.0000.0000.0001.00
[SwitchA-isis-1] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] isis enable 1
[SwitchA-Vlan-interface1] quit
[SwitchA] interface loopback 0
[SwitchA-LoopBack0] isis enable 1
[SwitchA-LoopBack0] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] isis 1
[SwitchB-isis-1] network-entity 00.0005.0000.0000.0002.00
[SwitchB-isis-1] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] isis enable 1
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] isis enable 1
[SwitchB-Vlan-interface2] quit
[SwitchB] interface loopback 0
[SwitchB-LoopBack0] isis enable 1
[SwitchB-LoopBack0] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] isis 1
[SwitchC-isis-1] network-entity 00.0005.0000.0000.0003.00
[SwitchC-isis-1] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] isis enable 1
[SwitchC-Vlan-interface2] quit
[SwitchC] interface loopback 0
[SwitchC-LoopBack0] isis enable 1
[SwitchC-LoopBack0] quit
# Execute the display ip routing-table command on each switch to verify that the switches have learned the routes to one another, including the routes to the loopback interfaces. (Details not shown.)
3. Configure an LSR ID, and enable MPLS and MPLS TE:
# Configure Switch A.
[SwitchA] mpls lsr-id 1.1.1.1
[SwitchA] mpls te
[SwitchA-te] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls enable
[SwitchA-Vlan-interface1] mpls te enable
[SwitchA-Vlan-interface1] quit
# Configure Switch B.
[SwitchB] mpls lsr-id 2.2.2.2
[SwitchB] mpls te
[SwitchB-te] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls enable
[SwitchB-Vlan-interface1] mpls te enable
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls te enable
[SwitchB-Vlan-interface2] quit
# Configure Switch C.
[SwitchC] mpls lsr-id 3.3.3.3
[SwitchC] mpls te
[SwitchC-te] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] mpls enable
[SwitchC-Vlan-interface2] mpls te enable
[SwitchC-Vlan-interface2] quit
4. Configure MPLS TE attributes of links:
# Configure the maximum link bandwidth and maximum reservable bandwidth on Switch A.
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls te max-link-bandwidth 10000
[SwitchA-Vlan-interface1] mpls te max-reservable-bandwidth 5000
[SwitchA-Vlan-interface1] quit
# Configure the maximum link bandwidth and maximum reservable bandwidth on Switch B.
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls te max-link-bandwidth 10000
[SwitchB-Vlan-interface1] mpls te max-reservable-bandwidth 5000
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls te max-link-bandwidth 10000
[SwitchB-Vlan-interface2] mpls te max-reservable-bandwidth 5000
[SwitchB-Vlan-interface2] quit
# Configure the maximum link bandwidth and maximum reservable bandwidth on Switch C.
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] mpls te max-link-bandwidth 10000
[SwitchC-Vlan-interface2] mpls te max-reservable-bandwidth 5000
[SwitchC-Vlan-interface2] quit
5. Configure an MPLS TE tunnel on Switch A:
# Configure MPLS TE tunnel interface Tunnel 0.
[SwitchA] interface tunnel 0 mode mpls-te
[SwitchA-Tunnel0] ip address 6.1.1.1 255.255.255.0
# Specify the tunnel destination address as the LSR ID of Switch C.
[SwitchA-Tunnel0] destination 3.3.3.3
# Configure MPLS TE to use a static CRLSP to establish the tunnel.
[SwitchA-Tunnel0] mpls te signaling static
[SwitchA-Tunnel0] quit
6. Create a static CRLSP:
# Configure Switch A as the ingress node of the static CRLSP, and specify the next hop address as 2.1.1.2, outgoing label as 20, and bandwidth for the tunnel as 2000 kbps.
[SwitchA] static-cr-lsp ingress static-cr-lsp-1 nexthop 2.1.1.2 out-label 20 bandwidth 2000
# On Switch A, configure tunnel 0 to reference the static CRLSP static-cr-lsp-1.
[SwitchA] interface Tunnel0
[SwitchA-Tunnel0] mpls te static-cr-lsp static-cr-lsp-1
[SwitchA-Tunnel0] quit
# Configure Switch B as the transit node of the static CRLSP, and specify the incoming label as 20, next hop address as 3.2.1.2, outgoing label as 30, and bandwidth for the tunnel as 2000 kbps.
[SwitchB] static-cr-lsp transit static-cr-lsp-1 in-label 20 nexthop 3.2.1.2 out-label 30 bandwidth 2000
# Configure Switch C as the egress node of the static CRLSP, and specify the incoming label as 30.
[SwitchC] static-cr-lsp egress static-cr-lsp-1 in-label 30
7. Configure a static route on Switch A to direct traffic destined for subnet 3.2.1.0/24 to MPLS TE tunnel 0.
[SwitchA] ip route-static 3.2.1.2 24 tunnel 0 preference 1
Verifying the configuration
# Execute the display interface tunnel command on Switch A. The output shows that the tunnel interface is up.
[SwitchA] display interface tunnel
Tunnel0
Current state: UP
Line protocol state: UP
Description: Tunnel0 Interface
Bandwidth: 64kbps
Maximum Transmit Unit: 1496
Internet Address is 6.1.1.1/24 Primary
Tunnel source unknown, destination 3.3.3.3
Tunnel TTL 255
Tunnel protocol/transport CR_LSP
Output queue - Urgent queuing: Size/Length/Discards 0/100/0
Output queue - Protocol queuing: Size/Length/Discards 0/500/0
Output queue - FIFO queuing: Size/Length/Discards 0/75/0
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# Execute the display mpls te tunnel-interface command on Switch A to display detailed information about the MPLS TE tunnel.
[SwitchA] display mpls te tunnel-interface
Tunnel Name : Tunnel 0
Tunnel State : Up (Main CRLSP up)
Tunnel Attributes :
LSP ID : 1 Tunnel ID : 0
Admin State : Normal
Ingress LSR ID : 1.1.1.1 Egress LSR ID : 3.3.3.3
Signaling : Static Static CRLSP Name : static-cr-lsp-1
Resv Style : -
Tunnel mode : -
Reverse-LSP name : -
Reverse-LSP LSR ID : - Reverse-LSP Tunnel ID: -
Class Type : - Tunnel Bandwidth : -
Reserved Bandwidth : -
Setup Priority : 0 Holding Priority : 0
Affinity Attr/Mask : -/-
Explicit Path : -
Backup Explicit Path : -
Metric Type : TE
Record Route : - Record Label : -
FRR Flag : - Bandwidth Protection : -
Backup Bandwidth Flag: - Backup Bandwidth Type: -
Backup Bandwidth : -
Bypass Tunnel : - Auto Created : -
Route Pinning : -
Retry Limit : 3 Retry Interval : 2 sec
Reoptimization : - Reoptimization Freq : -
Backup Type : - Backup LSP ID : -
Auto Bandwidth : - Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
# Execute the display mpls lsp command or the display mpls static-cr-lsp command on each switch to display static CRLSP information.
[SwitchA] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
1.1.1.1/0/1 StaticCR -/20 Vlan1
2.1.1.2 Local -/- Vlan1
[SwitchB] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
- StaticCR 20/30 Vlan2
3.2.1.2 Local -/- Vlan2
[SwitchC] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
- StaticCR 30/- -
[SwitchA] display mpls static-cr-lsp
Name LSR Type In/Out Label Out Interface State
static-cr-lsp-1 Ingress Null/20 Vlan1 Up
[SwitchB] display mpls static-cr-lsp
Name LSR Type In/Out Label Out Interface State
static-cr-lsp-1 Transit 20/30 Vlan2 Up
[SwitchC] display mpls static-cr-lsp
Name LSR Type In/Out Label Out Interface State
static-cr-lsp1 Egress 30/Null - Up
# Execute the display ip routing-table command on Switch A. The output shows a static route entry with interface Tunnel 0 as the output interface. (Details not shown.)
Establishing an MPLS TE tunnel with RSVP-TE
Network requirements
Switch A, Switch B, Switch C, and Switch D run IS-IS and all of them are Level-2 switches.
Use RSVP-TE to create an MPLS TE tunnel from Switch A to Switch D. The MPLS TE tunnel requires a bandwidth of 2000 kbps.
The maximum bandwidth of the link that the tunnel traverses is 10000 kbps and the maximum reservable bandwidth of the link is 5000 kbps.
Figure 28 Network diagram
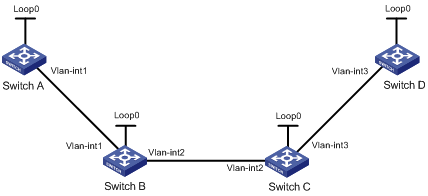
Table 3 Interface and IP address assignment
|
Interface |
IP address |
Device |
Interface |
IP address |
|
|
Switch A |
Loop0 |
1.1.1.9/32 |
Switch D |
Loop0 |
4.4.4.9/32 |
|
|
Vlan-int1 |
10.1.1.1/24 |
|
Vlan-int3 |
30.1.1.2/24 |
|
Switch B |
Loop0 |
2.2.2.9/32 |
Switch C |
Loop0 |
3.3.3.9/32 |
|
|
Vlan-int1 |
10.1.1.2/24 |
|
Vlan-int3 |
30.1.1.1/24 |
|
|
Vlan-int2 |
20.1.1.1/24 |
|
Vlan-int2 |
20.1.1.2/24 |
Configuration procedure
1. Configure IP addresses and masks for interfaces. (Details not shown.)
2. Configure IS-IS to advertise interface addresses, including the loopback interface address:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] isis 1
[SwitchA-isis-1] network-entity 00.0005.0000.0000.0001.00
[SwitchA-isis-1] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] isis enable 1
[SwitchA-Vlan-interface1] isis circuit-level level-2
[SwitchA-Vlan-interface1] quit
[SwitchA] interface loopback 0
[SwitchA-LoopBack0] isis enable 1
[SwitchA-LoopBack0] isis circuit-level level-2
[SwitchA-LoopBack0] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] isis 1
[SwitchB-isis-1] network-entity 00.0005.0000.0000.0002.00
[SwitchB-isis-1] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] isis enable 1
[SwitchB-Vlan-interface1] isis circuit-level level-2
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] isis enable 1
[SwitchB-Vlan-interface2] isis circuit-level level-2
[SwitchB-Vlan-interface2] quit
[SwitchB] interface loopback 0
[SwitchB-LoopBack0] isis enable 1
[SwitchB-LoopBack0] isis circuit-level level-2
[SwitchB-LoopBack0] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] isis 1
[SwitchC-isis-1] network-entity 00.0005.0000.0000.0003.00
[SwitchC-isis-1] quit
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] isis enable 1
[SwitchC-Vlan-interface3] isis circuit-level level-2
[SwitchC-Vlan-interface3] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] isis enable 1
[SwitchC-Vlan-interface2] isis circuit-level level-2
[SwitchC-Vlan-interface2] quit
[SwitchC] interface loopback 0
[SwitchC-LoopBack0] isis enable 1
[SwitchC-LoopBack0] isis circuit-level level-2
[SwitchC-LoopBack0] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] isis 1
[SwitchD-isis-1] network-entity 00.0005.0000.0000.0004.00
[SwitchD-isis-1] quit
[SwitchD] interface vlan-interface 3
[SwitchD-Vlan-interface3] isis enable 1
[SwitchD-Vlan-interface3] isis circuit-level level-2
[SwitchD-Vlan-interface3] quit
[SwitchD] interface loopback 0
[SwitchD-LoopBack0] isis enable 1
[SwitchD-LoopBack0] isis circuit-level level-2
[SwitchD-LoopBack0] quit
# Execute the display ip routing-table command on each switch to verify that the switches have learned the routes to one another, including the routes to the loopback interfaces. (Details not shown.)
3. Configure an LSR ID, and enable MPLS, MPLS TE, and RSVP-TE:
# Configure Switch A.
[SwitchA] mpls lsr-id 1.1.1.9
[SwitchA] mpls te
[SwitchA-te] quit
[SwitchA] rsvp
[SwitchA-rsvp] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls enable
[SwitchA-Vlan-interface1] mpls te enable
[SwitchA-Vlan-interface1] rsvp enable
[SwitchA-Vlan-interface1] quit
# Configure Switch B.
[SwitchB] mpls lsr-id 2.2.2.9
[SwitchB] mpls te
[SwitchB-te] quit
[SwitchB] rsvp
[SwitchB-rsvp] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls enable
[SwitchB-Vlan-interface1] mpls te enable
[SwitchB-Vlan-interface1] rsvp enable
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls te enable
[SwitchB-Vlan-interface2] rsvp enable
[SwitchB-Vlan-interface2] quit
# Configure Switch C.
[SwitchC] mpls lsr-id 3.3.3.9
[SwitchC] mpls te
[SwitchC-te] quit
[SwitchC] rsvp
[SwitchC-rsvp] quit
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] mpls enable
[SwitchC-Vlan-interface3] mpls te enable
[SwitchC-Vlan-interface3] rsvp enable
[SwitchC-Vlan-interface3] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] mpls enable
[SwitchC-Vlan-interface2] mpls te enable
[SwitchC-Vlan-interface2] rsvp enable
[SwitchC-Vlan-interface2] quit
# Configure Switch D.
[SwitchD] mpls lsr-id 4.4.4.9
[SwitchD] mpls te
[SwitchD-te] quit
[SwitchD] rsvp
[SwitchD-rsvp] quit
[SwitchD] interface vlan-interface 3
[SwitchD-Vlan-interface3] mpls enable
[SwitchD-Vlan-interface3] mpls te enable
[SwitchD-Vlan-interface3] rsvp enable
[SwitchD-Vlan-interface3] quit
4. Configure IS-IS TE:
# Configure Switch A.
[SwitchA] isis 1
[SwitchA-isis-1] cost-style wide
[SwitchA-isis-1] mpls te enable level-2
[SwitchA-isis-1] quit
# Configure Switch B.
[SwitchB] isis 1
[SwitchB-isis-1] cost-style wide
[SwitchB-isis-1] mpls te enable level-2
[SwitchB-isis-1] quit
# Configure Switch C.
[SwitchC] isis 1
[SwitchC-isis-1] cost-style wide
[SwitchC-isis-1] mpls te enable level-2
[SwitchC-isis-1] quit
# Configure Switch D.
[SwitchD] isis 1
[SwitchD-isis-1] cost-style wide
[SwitchD-isis-1] mpls te enable level-2
[SwitchD-isis-1] quit
5. Configure MPLS TE attributes of links:
# Configure the maximum link bandwidth and maximum reservable bandwidth on Switch A.
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls te max-link-bandwidth 10000
[SwitchA-Vlan-interface1] mpls te max-reservable-bandwidth 5000
[SwitchA-Vlan-interface1] quit
# Configure the maximum link bandwidth and maximum reservable bandwidth on Switch B.
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls te max-link-bandwidth 10000
[SwitchB-Vlan-interface1] mpls te max-reservable-bandwidth 5000
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls te max-link-bandwidth 10000
[SwitchB-Vlan-interface2] mpls te max-reservable-bandwidth 5000
[SwitchB-Vlan-interface2] quit
# Configure the maximum link bandwidth and maximum reservable bandwidth on Switch C.
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] mpls te max-link-bandwidth 10000
[SwitchC-Vlan-interface3] mpls te max-reservable-bandwidth 5000
[SwitchC-Vlan-interface3] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] mpls te max-link-bandwidth 10000
[SwitchC-Vlan-interface2] mpls te max-reservable-bandwidth 5000
[SwitchC-Vlan-interface2] quit
# Configure the maximum link bandwidth and maximum reservable bandwidth on Switch D.
[SwitchD] interface vlan-interface 3
[SwitchD-Vlan-interface3] mpls te max-link-bandwidth 10000
[SwitchD-Vlan-interface3] mpls te max-reservable-bandwidth 5000
[SwitchD-Vlan-interface3] quit
6. Configure an MPLS TE tunnel on Switch A:
# Configure MPLS TE tunnel interface Tunnel 1.
[SwitchA] interface tunnel 1 mode mpls-te
[SwitchA-Tunnel1] ip address 7.1.1.1 255.255.255.0
# Specify the tunnel destination address as the LSR ID of Switch D.
[SwitchA-Tunnel1] destination 4.4.4.9
# Configure MPLS TE to use RSVP-TE to establish the tunnel.
[SwitchA-Tunnel1] mpls te signaling rsvp-te
# Assign 2000 kbps bandwidth to the tunnel.
[SwitchA-Tunnel1] mpls te bandwidth 2000
[SwitchA-Tunnel1] quit
7. Configure a static route on Switch A to direct the traffic destined for subnet 30.1.1.0/24 to MPLS TE tunnel 1.
[SwitchA] ip route-static 30.1.1.2 24 tunnel 1 preference 1
Verifying the configuration
# Execute the display interface tunnel command on Switch A. The output shows that the tunnel interface is up.
[SwitchA] display interface tunnel
Tunnel1 current state: UP
Line protocol current state: UP
Description: Tunnel1 Interface
The Maximum Transmit Unit is 64000
Internet Address is 7.1.1.1/24 Primary
Tunnel source unknown, destination 4.4.4.9
Tunnel bandwidth 64 (kbps)
Tunnel TTL 255
Tunnel protocol/transport CR_LSP
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 6 bytes/sec, 48 bits/sec, 0 packets/sec
0 packets input, 0 bytes, 0 drops
177 packets output, 11428 bytes, 0 drops
# Execute the display mpls te tunnel-interface command on Switch A to display detailed information about the MPLS TE tunnel.
[SwitchA] display mpls te tunnel-interface
Tunnel Name : Tunnel 1
Tunnel State : Up (Main CRLSP up, Shared-resource CRLSP down)
Tunnel Attributes :
LSP ID : 23331 Tunnel ID : 1
Admin State : Normal
Ingress LSR ID : 1.1.1.9 Egress LSR ID : 4.4.4.9
Signaling : RSVP-TE Static CRLSP Name : -
Resv Style : SE
Tunnel mode : -
Reverse-LSP name : -
Reverse-LSP LSR ID : - Reverse-LSP Tunnel ID: -
Class Type : CT0 Tunnel Bandwidth : 2000 kbps
Reserved Bandwidth : 2000 kbps
Setup Priority : 7 Holding Priority : 7
Affinity Attr/Mask : 0/0
Explicit Path : -
Backup Explicit Path : -
Metric Type : TE
Record Route : Disabled Record Label : Disabled
FRR Flag : Disabled Bandwidth Protection : Disabled
Backup Bandwidth Flag: Disabled Backup Bandwidth Type: -
Backup Bandwidth : -
Bypass Tunnel : No Auto Created : No
Route Pinning : Disabled
Retry Limit : 10 Retry Interval : 2 sec
Reoptimization : Disabled Reoptimization Freq : -
Backup Type : None Backup LSP ID : -
Auto Bandwidth : Disabled Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
# Execute the display ip routing-table command on Switch A. The output shows a static route entry with interface Tunnel 1 as the output interface. (Details not shown.)
Establishing an inter-AS MPLS TE tunnel with RSVP-TE
Network requirements
Switch A and Switch B are in AS 100. Switch C and Switch D are in AS 200. AS 100 and AS 200 use OSPF as the IGP.
Establish an EBGP connection between ASBRs Switch B and Switch C. Redistribute BGP routes into OSPF and OSPF routes into BGP, so that a route is available between AS 100 and AS 200.
Establish an MPLS TE tunnel from Switch A to Switch D. The tunnel requires a bandwidth of 2000 kbps. The maximum bandwidth of the link that the tunnel traverses is 10000 kbps and the maximum reservable bandwidth of the link is 5000 kbps.
Figure 29 Network diagram
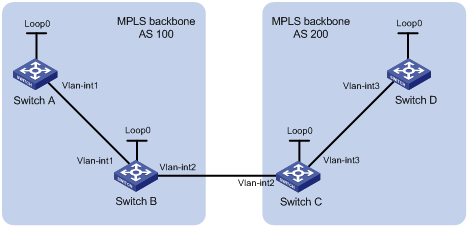
Table 4 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Switch A |
Loop0 |
1.1.1.9/32 |
Switch D |
Loop0 |
4.4.4.9/32 |
|
|
Vlan-int1 |
10.1.1.1/24 |
|
Vlan-int3 |
30.1.1.2/24 |
|
Switch B |
Loop0 |
2.2.2.9/32 |
Switch C |
Loop0 |
3.3.3.9/32 |
|
|
Vlan-int1 |
10.1.1.2/24 |
|
Vlan-int3 |
30.1.1.1/24 |
|
|
Vlan-int2 |
20.1.1.1/24 |
|
Vlan-int2 |
20.1.1.2/24 |
Configuration procedure
1. Configure IP addresses and masks for interfaces. (Details not shown.)
2. Configure OSPF to advertise routes within the ASs, and redistribute the direct and BGP routes into OSPF on Switch B and Switch C:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] ospf
[SwitchA-ospf-1] area 0
[SwitchA-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[SwitchA-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0
[SwitchA-ospf-1-area-0.0.0.0] quit
[SwitchA-ospf-1] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] ospf
[SwitchB-ospf-1] import-route direct
[SwitchB-ospf-1] import-route bgp
[SwitchB-ospf-1] area 0
[SwitchB-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[SwitchB-ospf-1-area-0.0.0.0] network 2.2.2.9 0.0.0.0
[SwitchB-ospf-1-area-0.0.0.0] quit
[SwitchB-ospf-1] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] ospf
[SwitchC-ospf-1] import-route direct
[SwitchC-ospf-1] import-route bgp
[SwitchC-ospf-1] area 0
[SwitchC-ospf-1-area-0.0.0.0] network 30.1.1.0 0.0.0.255
[SwitchC-ospf-1-area-0.0.0.0] network 3.3.3.9 0.0.0.0
[SwitchC-ospf-1-area-0.0.0.0] quit
[SwitchC-ospf-1] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] ospf
[SwitchD-ospf-1] area 0
[SwitchD-ospf-1-area-0.0.0.0] network 30.1.1.0 0.0.0.255
[SwitchD-ospf-1-area-0.0.0.0] network 4.4.4.9 0.0.0.0
[SwitchD-ospf-1-area-0.0.0.0] quit
[SwitchD-ospf-1] quit
# Execute the display ip routing-table command on each switch to verify that the switches have learned the routes to one another, including the routes to the loopback interfaces. Take Switch A as an example:
[SwitchA] display ip routing-table
Destinations : 6 Routes : 6
Destination/Mask Proto Pre Cost NextHop Interface
1.1.1.9/32 Direct 0 0 127.0.0.1 InLoop0
2.2.2.9/32 OSPF 10 1 10.1.1.2 Vlan1
10.1.1.0/24 Direct 0 0 10.1.1.1 Vlan1
10.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
3. Configure BGP on Switch B and Switch C to make sure the ASs can communicate with each other:
# Configure Switch B.
[SwitchB] bgp 100
[SwitchB-bgp] peer 20.1.1.2 as-number 200
[SwitchB-bgp] address-family ipv4 unicast
[SwitchB-bgp-ipv4] peer 20.1.1.2 enable
[SwitchB-bgp-ipv4] import-route ospf
[SwitchB-bgp-ipv4] import-route direct
[SwitchB-bgp-ipv4] quit
[SwitchB-bgp] quit
# Configure Switch C.
[SwitchC] bgp 200
[SwitchC-bgp] peer 20.1.1.1 as-number 100
[SwitchC-bgp] address-family ipv4 unicast
[SwitchC-bgp-ipv4] peer 20.1.1.1 enable
[SwitchC-bgp-ipv4] import-route ospf
[SwitchC-bgp-ipv4] import-route direct
[SwitchC-bgp-ipv4] quit
[SwitchC-bgp] quit
# Execute the display ip routing-table command on each switch to verify that the switches have learned AS-external routes. Take Switch A as an example:
[SwitchA] display ip routing-table
Destinations : 10 Routes : 10
Destination/Mask Proto Pre Cost NextHop Interface
1.1.1.9/32 Direct 0 0 127.0.0.1 InLoop0
2.2.2.9/32 OSPF 10 1 10.1.1.2 Vlan1
3.3.3.9/32 O_ASE 150 1 10.1.1.2 Vlan1
4.4.4.9/32 O_ASE 150 1 10.1.1.2 Vlan1
10.1.1.0/24 Direct 0 0 10.1.1.1 Vlan1
10.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
20.1.1.0/24 O_ASE 150 1 10.1.1.2 Vlan1
30.1.1.0/24 O_ASE 150 1 10.1.1.2 Vlan1
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
4. Configure an LSR ID, and enable MPLS, MPLS TE, and RSVP-TE:
# Configure Switch A.
[SwitchA] mpls lsr-id 1.1.1.9
[SwitchA] mpls te
[SwitchA-te] quit
[SwitchA] rsvp
[SwitchA-rsvp] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls enable
[SwitchA-Vlan-interface1] mpls te enable
[SwitchA-Vlan-interface1] rsvp enable
[SwitchA-Vlan-interface1] quit
# Configure Switch B.
[SwitchB] mpls lsr-id 2.2.2.9
[SwitchB] mpls te
[SwitchB-te] quit
[SwitchB] rsvp
[SwitchB-rsvp] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls enable
[SwitchB-Vlan-interface1] mpls te enable
[SwitchB-Vlan-interface1] rsvp enable
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls te enable
[SwitchB-Vlan-interface2] rsvp enable
[SwitchB-Vlan-interface2] quit
# Configure Switch C.
[SwitchC] mpls lsr-id 3.3.3.9
[SwitchC] mpls te
[SwitchC-te] quit
[SwitchC] rsvp
[SwitchC-rsvp] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] mpls enable
[SwitchC-Vlan-interface2] mpls te enable
[SwitchC-Vlan-interface2] rsvp enable
[SwitchC-Vlan-interface2] quit
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] mpls enable
[SwitchC-Vlan-interface3] mpls te enable
[SwitchC-Vlan-interface3] rsvp enable
[SwitchC-Vlan-interface3] quit
# Configure Switch D.
[SwitchD] mpls lsr-id 4.4.4.9
[SwitchD] mpls te
[SwitchD-te] quit
[SwitchD] rsvp
[SwitchD-rsvp] quit
[SwitchD] interface vlan-interface 3
[SwitchD-Vlan-interface3] mpls enable
[SwitchD-Vlan-interface3] mpls te enable
[SwitchD-Vlan-interface3] rsvp enable
[SwitchD-Vlan-interface3] quit
5. Configure OSPF TE:
# Configure Switch A.
[SwitchA] ospf
[SwitchA-ospf-1] opaque-capability enable
[SwitchA-ospf-1] area 0
[SwitchA-ospf-1-area-0.0.0.0] mpls te enable
[SwitchA-ospf-1-area-0.0.0.0] quit
[SwitchA-ospf-1] quit
# Configure Switch B.
[SwitchB] ospf
[SwitchB-ospf-1] opaque-capability enable
[SwitchB-ospf-1] area 0
[SwitchB-ospf-1-area-0.0.0.0] mpls te enable
[SwitchB-ospf-1-area-0.0.0.0] quit
[SwitchB-ospf-1] quit
# Configure Switch C.
[SwitchC] ospf
[SwitchC-ospf-1] opaque-capability enable
[SwitchC-ospf-1] area 0
[SwitchC-ospf-1-area-0.0.0.0] mpls te enable
[SwitchC-ospf-1-area-0.0.0.0] quit
[SwitchC-ospf-1] quit
# Configure Switch D.
[SwitchD] ospf
[SwitchD-ospf-1] opaque-capability enable
[SwitchD-ospf-1] area 0
[SwitchD-ospf-1-area-0.0.0.0] mpls te enable
[SwitchD-ospf-1-area-0.0.0.0] quit
[SwitchD-ospf-1] quit
6. Configure an explicit route on Switch A. Specify Switch B and Switch D as loose nodes, and Switch C as a strict node.
[SwitchA] explicit-path atod
[SwitchA-explicit-path-atod] nexthop 10.1.1.2 include loose
[SwitchA-explicit-path-atod] nexthop 20.1.1.2 include strict
[SwitchA-explicit-path-atod] nexthop 30.1.1.2 include loose
[SwitchA-explicit-path-atod] quit
7. Configure MPLS TE attributes of links:
# Configure the maximum link bandwidth and maximum reservable bandwidth on Switch A.
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls te max-link-bandwidth 10000
[SwitchA-Vlan-interface1] mpls te max-reservable-bandwidth 5000
[SwitchA-Vlan-interface1] quit
# Configure the maximum link bandwidth and maximum reservable bandwidth on Switch B.
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls te max-link-bandwidth 10000
[SwitchB-Vlan-interface1] mpls te max-reservable-bandwidth 5000
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls te max-link-bandwidth 10000
[SwitchB-Vlan-interface2] mpls te max-reservable-bandwidth 5000
[SwitchB-Vlan-interface2] quit
# Configure the maximum link bandwidth and maximum reservable bandwidth on Switch C.
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] mpls te max-link-bandwidth 10000
[SwitchC-Vlan-interface2] mpls te max-reservable-bandwidth 5000
[SwitchC-Vlan-interface2] quit
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] mpls te max-link-bandwidth 10000
[SwitchC-Vlan-interface3] mpls te max-reservable-bandwidth 5000
[SwitchC-Vlan-interface3] quit
# Configure the maximum link bandwidth and maximum reservable bandwidth on Switch D.
[SwitchD] interface vlan-interface 3
[SwitchD-Vlan-interface3] mpls te max-link-bandwidth 10000
[SwitchD-Vlan-interface3] mpls te max-reservable-bandwidth 5000
[SwitchD-Vlan-interface3] quit
8. Configure an MPLS TE tunnel on Switch A:
# Configure the MPLS TE tunnel interface Tunnel 1.
[SwitchA] interface tunnel 1 mode mpls-te
[SwitchA-Tunnel1] ip address 7.1.1.1 255.255.255.0
# Specify the tunnel destination address as the LSR ID of Switch D.
[SwitchA-Tunnel1] destination 4.4.4.9
# Configure MPLS TE to use RSVP-TE to establish the tunnel.
[SwitchA-Tunnel1] mpls te signaling rsvp-te
# Assign 2000 kbps bandwidth to the tunnel.
[SwitchA-Tunnel1] mpls te bandwidth 2000
# Specify the explicit path atod for the tunnel.
[SwitchA-Tunnel1] mpls te path preference 5 explicit-path atod
[SwitchA-Tunnel1] quit
9. Configure a static route on Switch A to direct the traffic destined for subnet 30.1.1.0/24 to MPLS TE tunnel 1.
[SwitchA] ip route-static 30.1.1.2 24 tunnel 1 preference 1
Verifying the configuration
# Execute the display interface tunnel command on Switch A. The output shows that the tunnel interface is up.
[SwitchA] display interface tunnel 1
Tunnel1 current state: UP
Line protocol current state: UP
Description: Tunnel1 Interface
The Maximum Transmit Unit is 64000
Internet Address is 7.1.1.1/24 Primary
Tunnel source unknown, destination 4.4.4.9
Tunnel bandwidth 64 (kbps)
Tunnel TTL 255
Tunnel protocol/transport CR_LSP
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
0 packets input, 0 bytes, 0 drops
3077 packets output, 197028 bytes, 0 drops
# Execute the display mpls te tunnel-interface command on Switch A to display detailed information about the MPLS TE tunnel.
[SwitchA] display mpls te tunnel-interface
Tunnel Name : Tunnel 1
Tunnel State : Up (Main CRLSP up, Shared-resource CRLSP down)
Tunnel Attributes :
LSP ID : 23549 Tunnel ID : 1
Admin State : Normal
Ingress LSR ID : 1.1.1.9 Egress LSR ID : 4.4.4.9
Signaling : RSVP-TE Static CRLSP Name : -
Resv Style : SE
Tunnel mode : -
Reverse-LSP name : -
Reverse-LSP LSR ID : - Reverse-LSP Tunnel ID: -
Class Type : CT0 Tunnel Bandwidth : 2000 kbps
Reserved Bandwidth : 2000 kbps
Setup Priority : 7 Holding Priority : 7
Affinity Attr/Mask : 0/0
Explicit Path : atod
Backup Explicit Path : -
Metric Type : TE
Record Route : Disabled Record Label : Disabled
FRR Flag : Disabled Bandwidth Protection : Disabled
Backup Bandwidth Flag: Disabled Backup Bandwidth Type: -
Backup Bandwidth : -
Bypass Tunnel : No Auto Created : No
Route Pinning : Disabled
Retry Limit : 10 Retry Interval : 2 sec
Reoptimization : Disabled Reoptimization Freq : -
Backup Type : None Backup LSP ID : -
Auto Bandwidth : Disabled Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
# Execute the display ip routing-table command on Switch A. The output shows a static route entry with interface Tunnel1 as the output interface.
[SwitchA] display ip routing-table
Destinations : 14 Routes : 14
Destination/Mask Proto Pre Cost NextHop Interface
1.1.1.9/32 Direct 0 0 127.0.0.1 InLoop0
2.2.2.9/32 OSPF 10 1 10.1.1.2 Vlan1
3.3.3.9/32 O_ASE 150 1 10.1.1.2 Vlan1
4.4.4.9/32 O_ASE 150 1 10.1.1.2 Vlan1
7.1.1.0/24 Direct 0 0 7.1.1.1 Tun1
7.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.0/24 Direct 0 0 10.1.1.1 Vlan1
10.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
20.1.1.0/24 O_ASE 150 1 10.1.1.2 Vlan1
30.1.1.0/24 Static 1 0 7.1.1.1 Tun1
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
Bidirectional MPLS TE tunnel configuration example
Network requirements
Switch A, Switch B, Switch C, and Switch D all run IS-IS and they are all level-2 switches.
Use RSVP-TE to establish a bidirectional MPLS TE tunnel between Switch A and Switch D.
Figure 30 Network diagram

Table 5 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Switch A |
Loop0 |
1.1.1.9/32 |
Switch D |
Loop0 |
4.4.4.9/32 |
|
|
Vlan-int1 |
10.1.1.1/24 |
|
Vlan-int3 |
30.1.1.2/24 |
|
Switch B |
Loop0 |
2.2.2.9/32 |
Switch C |
Loop0 |
3.3.3.9/32 |
|
|
Vlan-int1 |
10.1.1.2/24 |
|
Vlan-int3 |
30.1.1.1/24 |
|
|
Vlan-int2 |
20.1.1.1/24 |
|
Vlan-int2 |
20.1.1.2/24 |
Configuration procedure
1. Configure IP addresses and masks for interfaces. (Details not shown.)
2. Configure IS-IS to advertise interface addresses, including the loopback interface address.
For more information, see "Establishing an MPLS TE tunnel with RSVP-TE."
3. Configure an LSR ID, and enable MPLS, MPLS TE, and RSVP-TE on each switch. Configure Switch A and Switch D to assign a non-null label to the penultimate hop:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] mpls lsr-id 1.1.1.9
[SwitchA] mpls label advertise non-null
[SwitchA] mpls te
[SwitchA-te] quit
[SwitchA] rsvp
[SwitchA-rsvp] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls enable
[SwitchA-Vlan-interface1] mpls te enable
[SwitchA-Vlan-interface1] rsvp enable
[SwitchA-Vlan-interface1] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] mpls lsr-id 2.2.2.9
[SwitchB] mpls te
[SwitchB-te] quit
[SwitchB] rsvp
[SwitchB-rsvp] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls enable
[SwitchB-Vlan-interface1] mpls te enable
[SwitchB-Vlan-interface1] rsvp enable
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls te enable
[SwitchB-Vlan-interface2] rsvp enable
[SwitchB-Vlan-interface1] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] mpls lsr-id 3.3.3.9
[SwitchC] mpls te
[SwitchC-te] quit
[SwitchC] rsvp
[SwitchC-rsvp] quit
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] mpls enable
[SwitchC-Vlan-interface3] mpls te enable
[SwitchC-Vlan-interface3] rsvp enable
[SwitchC-Vlan-interface3] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] mpls enable
[SwitchC-Vlan-interface2] mpls te enable
[SwitchC-Vlan-interface2] rsvp enable
[SwitchC-Vlan-interface2] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] mpls lsr-id 4.4.4.9
[SwitchD] mpls label advertise non-null
[SwitchD] mpls te
[SwitchD-te] quit
[SwitchD] rsvp
[SwitchD-rsvp] quit
[SwitchD] interface vlan-interface 3
[SwitchD-Vlan-interface3] mpls enable
[SwitchD-Vlan-interface3] mpls te enable
[SwitchD-Vlan-interface3] rsvp enable
[SwitchD-Vlan-interface3] quit
4. Configure IS-IS TE:
# Configure Switch A.
[SwitchA] isis 1
[SwitchA-isis-1] cost-style wide
[SwitchA-isis-1] mpls te enable level-2
[SwitchA-isis-1] quit
# Configure Switch B.
[SwitchB] isis 1
[SwitchB-isis-1] cost-style wide
[SwitchB-isis-1] mpls te enable level-2
[SwitchB-isis-1] quit
# Configure Switch C.
[SwitchC] isis 1
[SwitchC-isis-1] cost-style wide
[SwitchC-isis-1] mpls te enable level-2
[SwitchC-isis-1] quit
# Configure Switch D.
[SwitchD] isis 1
[SwitchD-isis-1] cost-style wide
[SwitchD-isis-1] mpls te enable level-2
[SwitchD-isis-1] quit
5. Configure a co-routed bidirectional MPLS TE tunnel:
# Configure Switch A as the active end of the co-routed bidirectional tunnel.
[SwitchA] interface tunnel 1 mode mpls-te
[SwitchA-Tunnel1] ip address 7.1.1.1 255.255.255.0
[SwitchA-Tunnel1] destination 4.4.4.9
[SwitchA-Tunnel1] mpls te signaling rsvp-te
[SwitchA-Tunnel1] mpls te resv-style ff
[SwitchA-Tunnel1] mpls te bidirectional co-routed active
[SwitchA-Tunnel1] quit
# Configure Switch D as the passive end of the co-routed bidirectional tunnel.
[SwitchD] interface tunnel 4 mode mpls-te
[SwitchD-Tunnel4] ip address 8.1.1.1 255.255.255.0
[SwitchD-Tunnel4] destination 1.1.1.9
[SwitchD-Tunnel4] mpls te signaling rsvp-te
[SwitchD-Tunnel4] mpls te resv-style ff
[SwitchD-Tunnel4] mpls te bidirectional co-routed passive reverse-lsp lsr-id 1.1.1.9 tunnel-id 1
[SwitchD-Tunnel4] quit
Verifying the configuration
# Execute the display interface tunnel command on Switch A. The output shows that the tunnel interface is up.
[SwitchA] display interface tunnel
Tunnel1 current state: UP
Line protocol current state: UP
Description: Tunnel1 Interface
The Maximum Transmit Unit is 64000
Internet Address is 7.1.1.1/24 Primary
Tunnel source unknown, destination 4.4.4.9
Tunnel bandwidth 64 (kbps)
Tunnel protocol/transport CR_LSP
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
0 packets input, 0 bytes, 0 drops
0 packets output, 0 bytes, 0 drops
# Execute the display mpls te tunnel-interface command on Switch A to display detailed information about the MPLS TE tunnel.
[SwitchA] display mpls te tunnel-interface
Tunnel Name : Tunnel 1
Tunnel State : Up (Main CRLSP up, Reverse CRLSP up)
Tunnel Attributes :
LSP ID : 30478 Tunnel ID : 1
Admin State : Normal
Ingress LSR ID : 1.1.1.9 Egress LSR ID : 4.4.4.9
Signaling : RSVP-TE Static CRLSP Name : -
Resv Style : FF
Tunnel mode : Co-routed, active
Reverse-LSP name : -
Reverse-LSP LSR ID : - Reverse-LSP Tunnel ID: -
Class Type : CT0 Tunnel Bandwidth : 0 kbps
Reserved Bandwidth : 0 kbps
Setup Priority : 7 Holding Priority : 7
Affinity Attr/Mask : 0/0
Explicit Path : -
Backup Explicit Path : -
Metric Type : TE
Record Route : Disabled Record Label : Disabled
FRR Flag : Disabled Bandwidth Protection : Disabled
Backup Bandwidth Flag: Disabled Backup Bandwidth Type: -
Backup Bandwidth : -
Bypass Tunnel : No Auto Created : No
Route Pinning : Disabled
Retry Limit : 10 Retry Interval : 2 sec
Reoptimization : Disabled Reoptimization Freq : -
Backup Type : None Backup LSP ID : -
Auto Bandwidth : Disabled Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
# Execute the display mpls lsp verbose command on Switch A to display detailed information about the bidirectional MPLS TE tunnel.
[SwitchA] display mpls lsp verbose
Destination : 4.4.4.9
FEC : 1.1.1.9/1/30478
Protocol : RSVP
LSR Type : Ingress
Service : -
NHLFE ID : 1027
State : Active
Out-Label : 1149
Nexthop : 10.1.1.2
Out-Interface: Vlan1
Destination : 4.4.4.9
FEC : 1.1.1.9/1/30478
Protocol : RSVP
LSR Type : Egress
Service : -
In-Label : 1151
State : Active
Nexthop : 127.0.0.1
Out-Interface: -
Destination : 10.1.1.2
FEC : 10.1.1.2
Protocol : Local
LSR Type : Ingress
Service : -
NHLFE ID : 1026
State : Active
Nexthop : 10.1.1.2
Out-Interface: Vlan1
# Execute the display interface tunnel command on Switch D. The output shows that the tunnel interface is up.
[SwitchD] display interface tunnel
Tunnel4 current state: UP
Line protocol current state: UP
Description: Tunnel8 Interface
The Maximum Transmit Unit is 64000
Internet Address is 8.1.1.1/24 Primary
Tunnel source unknown, destination 1.1.1.9
Tunnel bandwidth 64 (kbps)
Tunnel TTL 255
Tunnel protocol/transport CR_LSP
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
0 packets input, 0 bytes, 0 drops
0 packets output, 0 bytes, 0 drops
# Execute the display mpls te tunnel-interface command on Switch D to display detailed information about the MPLS TE tunnel.
[SwitchD] display mpls te tunnel-interface
[SwitchD] display mpls te tunnel-interface
Tunnel Name : Tunnel 4
Tunnel State : Up (Main CRLSP up, Reverse CRLSP up)
Tunnel Attributes :
LSP ID : - Tunnel ID : 8
Admin State : Normal
Ingress LSR ID : - Egress LSR ID : -
Signaling : RSVP-TE Static CRLSP Name : -
Resv Style : FF
Tunnel mode : Co-routed, passive
Reverse-LSP name : -
Reverse-LSP LSR ID : 1.1.1.9 Reverse-LSP Tunnel ID: 1
Class Type : - Tunnel Bandwidth : -
Reserved Bandwidth : -
Setup Priority : - Holding Priority : -
Affinity Attr/Mask : -/-
Explicit Path : -
Backup Explicit Path : -
Metric Type : -
Record Route : - Record Label : -
FRR Flag : - Bandwidth Protection : -
Backup Bandwidth Flag: - Backup Bandwidth Type: -
Backup Bandwidth : -
Bypass Tunnel : - Auto Created : No
Route Pinning : -
Retry Limit : - Retry Interval : -
Reoptimization : - Reoptimization Freq : -
Backup Type : - Backup LSP ID : -
Auto Bandwidth : - Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
# Execute the display mpls lsp verbose command on Switch D to display detailed information about the bidirectional MPLS TE tunnel.
[SwitchD] display mpls lsp verbose
Destination : 4.4.4.9
FEC : 1.1.1.9/1/30478
Protocol : RSVP
LSR Type : Egress
Service : -
In-Label : 3
State : Active
Nexthop : 127.0.0.1
Out-Interface: -
Destination : 4.4.4.9
FEC : 1.1.1.9/1/30478
Protocol : RSVP
LSR Type : Ingress
Service : -
NHLFE ID : 1025
State : Active
Out-Label : 1150
Nexthop : 30.1.1.1
Out-Interface: Vlan1
Destination : 30.1.1.1
FEC : 30.1.1.1
Protocol : Local
LSR Type : Ingress
Service : -
NHLFE ID : 1024
State : Active
Nexthop : 30.1.1.1
Out-Interface: Vlan1
CRLSP backup configuration example
Network requirements
Switch A, Switch B, Switch C, and Switch D run IS-IS.
Use RSVP-TE to establish an MPLS TE tunnel from Switch A to Switch C. Enable CRLSP hot backup for the tunnel to simultaneously establish a primary CRLSP and a backup CRLSP. When the primary CRLSP fails, traffic is switched to the backup CRLSP.
Figure 31 Network diagram
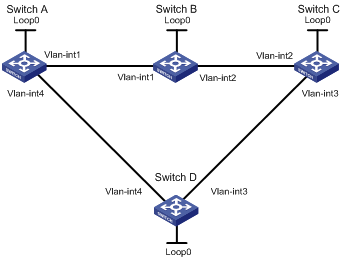
Table 6 Interface and IP address assignment
|
Interface |
IP address |
Device |
Interface |
IP address |
|
|
Switch A |
Loop0 |
1.1.1.9/32 |
Switch D |
Loop0 |
4.4.4.9/32 |
|
|
Vlan-int1 |
10.1.1.1/24 |
|
Vlan-int4 |
30.1.1.2/24 |
|
|
Vlan-int4 |
30.1.1.1/24 |
|
Vlan-int3 |
40.1.1.1/24 |
|
Switch B |
Loop0 |
2.2.2.9/32 |
Switch C |
Loop0 |
3.3.3.9/32 |
|
|
Vlan-int1 |
10.1.1.2/24 |
|
Vlan-int2 |
20.1.1.2/24 |
|
|
Vlan-int2 |
20.1.1.1/24 |
|
Vlan-int3 |
40.1.1.2/24 |
Configuration procedure
1. Configure IP addresses and masks for interfaces. (Details not shown.)
2. Configure IS-IS to advertise interface addresses, including the loopback interface address. (Details not shown.)
3. Configure an LSR ID, and enable MPLS, MPLS TE, and RSVP-TE:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] mpls lsr-id 1.1.1.9
[SwitchA] mpls te
[SwitchA-te] quit
[SwitchA] rsvp
[SwitchA-rsvp] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls enable
[SwitchA-Vlan-interface1] mpls te enable
[SwitchA-Vlan-interface1] rsvp enable
[SwitchA-Vlan-interface1] quit
[SwitchA] interface vlan-interface 4
[SwitchA-Vlan-interface4] mpls enable
[SwitchA-Vlan-interface4] mpls te enable
[SwitchA-Vlan-interface4] rsvp enable
[SwitchA-Vlan-interface4] quit
# Configure Switch B, Switch C, and Switch D in the same way that Switch A is configured. (Details not shown.)
4. Configure an MPLS TE tunnel on Switch A:
# Configure the MPLS TE tunnel interface Tunnel 3.
[SwitchA] interface tunnel 3 mode mpls-te
[SwitchA-Tunnel3] ip address 9.1.1.1 24
# Specify the tunnel destination address as the LSR ID of Switch C.
[SwitchA-Tunnel3] destination 3.3.3.9
# Configure MPLS TE to use RSVP-TE to establish the tunnel.
[SwitchA-Tunnel3] mpls te signaling rsvp-te
# Enable CRLSP hot backup for the tunnel.
[SwitchA-Tunnel3] mpls te backup hot-standby
[SwitchA-Tunnel3] quit
5. Configure a static route on Switch A to direct the traffic destined for subnet 20.1.1.0/24 to MPLS TE tunnel 3.
[SwitchA] ip route-static 20.1.1.2 24 tunnel 3 preference 1
Verifying the configuration
# Execute the display interface tunnel command on Switch A. The output shows that the tunnel interface Tunnel 3 is up.
[SwitchA] display interface tunnel
Tunnel3 current state: UP
Line protocol current state: UP
Description: Tunnel3 Interface
The Maximum Transmit Unit is 64000
Internet Address is 9.1.1.1/24 Primary
Tunnel source unknown, destination 3.3.3.9
Tunnel bandwidth 64 (kbps)
Tunnel TTL 255
Tunnel protocol/transport CR_LSP
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 1802 bytes/sec, 14416 bits/sec, 0 packets/sec
0 packets input, 0 bytes, 0 drops
351 packets output, 3105652 bytes, 0 drops
# Execute the display mpls lsp command on Switch A. The output shows that two CRLSPs exist on the switch, one with the output interface VLAN-interface 1 and the other with the output interface VLAN-interface 4.
[SwitchA] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
1.1.1.9/3/30106 RSVP -/1137 Vlan1
1.1.1.9/3/30107 RSVP -/1150 Vlan4
10.1.1.2 Local -/- Vlan1
30.1.1.2 Local -/- Vlan4
# Execute the display rsvp lsp verbose command on Switch A to display the paths used by the two CRLSPs.
[SwitchA] display rsvp lsp verbose
Tunnel name: SwitchA_t3
Destination: 3.3.3.9 Source: 1.1.1.9
Tunnel ID: 3 LSP ID: 30106
LSR type: Ingress Direction: Unidirectional
Setup priority: 7 Holding priority: 7
In-Label: - Out-Label: 1137
In-Interface: - Out-Interface: Vlan1
Nexthop: 10.1.1.2 Exclude-any: 0
Include-Any: 0 Include-all: 0
Mean rate (CIR): 0 kbps Mean burst size (CBS): 1000.00 bytes
Path MTU: 1500 Class type: CT0
RRO number: 6
10.1.1.1/32 Flag: 0x00 (No FRR)
10.1.1.2/32 Flag: 0x00 (No FRR)
2.2.2.9/32 Flag: 0x20 (No FRR/Node-ID)
20.1.1.1/32 Flag: 0x00 (No FRR)
20.1.1.2/32 Flag: 0x00 (No FRR)
3.3.3.9/32 Flag: 0x20 (No FRR/Node-ID)
Fast Reroute protection: None
Tunnel name: Tunnel3
Destination: 3.3.3.9 Source: 1.1.1.9
Tunnel ID: 3 LSP ID: 30107
LSR type: Ingress Direction: Unidirectional
Setup priority: 7 Holding priority: 7
In-Label: - Out-Label: 1150
In-Interface: - Out-Interface: Vlan4
Nexthop: 30.1.1.2 Exclude-any: 0
Include-Any: 0 Include-all: 0
Mean rate (CIR): 0 kbps Mean burst size (CBS): 1000.00 bytes
Path MTU: 1500 Class type: CT0
RRO number: 6
30.1.1.1/32 Flag: 0x00 (No FRR)
30.1.1.2/32 Flag: 0x00 (No FRR)
4.4.4.9/32 Flag: 0x20 (No FRR/Node-ID)
40.1.1.1/32 Flag: 0x00 (No FRR)
40.1.1.2/32 Flag: 0x00 (No FRR)
3.3.3.9/32 Flag: 0x20 (No FRR/Node-ID)
Fast Reroute protection: None
# Tracert the tunnel destination 3.3.3.9. The output shows that the used CRLSP is the one that traverses Switch B.
[SwitchA] tracert –a 1.1.1.9 3.3.3.9
traceroute to 3.3.3.9 (3.3.3.9) from 1.1.1.9, 30 hops at most, 40 bytes each pac
ket, press CTRL_C to break
1 10.1.1.2 (10.1.1.2) 1.000 ms 1.000 ms 1.000 ms
2 * * *
# Shut down interface VLAN-interface 2 on Switch B, and then tracert the tunnel destination. The output shows that packets are forwarded on the CRLSP that traverses Switch D.
[SwitchA] tracert –a 1.1.1.9 3.3.3.9
traceroute to 3.3.3.9 (3.3.3.9) from 9.1.1.1, 30 hops at most, 40 bytes each pac
ket, press CTRL_C to break
1 30.1.1.2 (30.1.1.2) 3.000 ms 7.000 ms 3.000 ms
2 * * *
# Execute the display mpls lsp command on Switch A. The output shows that only one CRLSP exists on the switch.
[SwitchA] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
1.1.1.9/3/48984 RSVP -/1150 Vlan4
30.1.1.2 Local -/- Vlan4
# Execute the display ip routing-table command on Switch A. The output shows a static route entry with interface Tunnel 3 as the output interface. (Details not shown.)
Manual bypass tunnel for FRR configuration example
Network requirements
On the primary CRLSP Switch A—Switch B—Switch C—Switch D, use FRR to protect the link Switch B—Switch C.
Use RSVP-TE to establish the primary CRLSP and bypass tunnel of the MPLS TE tunnel based on the constraints of the explicit paths. The bypass tunnel uses path Switch B—Switch E—Switch C. Switch B is the PLR and Switch C is the MP.
Configure BFD for RSVP-TE between Switch B and Switch C. When the link between Switch B and Switch C fails, BFD can detect the failure quickly and notify RSVP-TE of the failure, so RSVP-TE can switch traffic to the bypass tunnel.
Figure 32 Network diagram

Table 7 Interface and IP address assignment
|
Interface |
IP address |
Device |
Interface |
IP address |
|
|
Switch A |
Loop0 |
1.1.1.1/32 |
Switch E |
Loop0 |
5.5.5.5/32 |
|
|
Vlan-int1 |
2.1.1.1/24 |
|
Vlan-int4 |
3.2.1.2/24 |
|
Switch B |
Loop0 |
2.2.2.2/32 |
|
Vlan-int5 |
3.3.1.1/24 |
|
|
Vlan-int1 |
2.1.1.2/24 |
Switch C |
Loop0 |
3.3.3.3/32 |
|
|
Vlan-int2 |
3.1.1.1/24 |
|
Vlan-int3 |
4.1.1.1/24 |
|
|
Vlan-int4 |
3.2.1.1/24 |
|
Vlan-int2 |
3.1.1.2/24 |
|
Switch D |
Loop0 |
4.4.4.4/32 |
|
Vlan-int5 |
3.3.1.2/24 |
|
|
Vlan-int3 |
4.1.1.2/24 |
|
|
|
Configuration procedure
1. Configure IP addresses and masks for interfaces. (Details not shown.)
2. Configure IS-IS to advertise interface addresses, including the loopback interface address. (Details not shown.)
3. Configure an LSR ID, and enable MPLS, MPLS TE, and RSVP-TE on each switch. Enable BFD for RSVP-TE on Switch B and Switch C:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] mpls lsr-id 1.1.1.1
[SwitchA] mpls te
[SwitchA-te] quit
[SwitchA] rsvp
[SwitchA-rsvp] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls enable
[SwitchA-Vlan-interface1] mpls te enable
[SwitchA-Vlan-interface1] rsvp enable
[SwitchA-Vlan-interface1] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] mpls lsr-id 2.2.2.2
[SwitchB] mpls te
[SwitchB-te] quit
[SwitchB] rsvp
[SwitchB-rsvp] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls enable
[SwitchB-Vlan-interface1] mpls te enable
[SwitchB-Vlan-interface1] rsvp enable
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls te enable
[SwitchB-Vlan-interface2] rsvp enable
[SwitchB-Vlan-interface2] rsvp bfd enable
[SwitchB-Vlan-interface2] quit
[SwitchB] interface vlan-interface 4
[SwitchB-Vlan-interface4] mpls enable
[SwitchB-Vlan-interface4] mpls te enable
[SwitchB-Vlan-interface4] rsvp enable
[SwitchB-Vlan-interface4] quit
# Configure Switch C in the same way that Switch B is configured. Configure Switch D and Switch E in the same way that Switch A is configured. (Details not shown.)
4. Configure an MPLS TE tunnel on Switch A, the ingress node of the primary CRLSP:
# Configure an explicit path for the primary CRLSP.
[SwitchA] explicit-path pri-path
[SwitchA-explicit-path-pri-path] nexthop 2.1.1.2
[SwitchA-explicit-path-pri-path] nexthop 3.1.1.2
[SwitchA-explicit-path-pri-path] nexthop 4.1.1.2
[SwitchA-explicit-path-pri-path] nexthop 4.4.4.4
[SwitchA-explicit-path-pri-path] quit
# Create MPLS TE tunnel interface Tunnel4 for the primary CRLSP.
[SwitchA] interface tunnel 4 mode mpls-te
[SwitchA-Tunnel4] ip address 10.1.1.1 255.255.255.0
# Specify the tunnel destination address as the LSR ID of Switch D.
[SwitchA-Tunnel4] destination 4.4.4.4
# Specify the tunnel signaling protocol as RSVP-TE.
[SwitchA-Tunnel4] mpls te signaling rsvp-te
# Specify the explicit path to be used as pri-path.
[SwitchA-Tunnel4] mpls te path preference 1 explicit-path pri-path
# Enable FRR for the MPLS TE tunnel.
[SwitchA-Tunnel4] mpls te fast-reroute
[SwitchA-Tunnel4] quit
# Execute the display interface tunnel command on Switch A. The output shows that the tunnel interface Tunnel4 is up.
[SwitchA] display interface tunnel
Tunnel4 current state: UP
Line protocol current state: UP
Description: Tunnel3 Interface
The Maximum Transmit Unit is 64000
Internet Address is 9.1.1.1/24 Primary
Tunnel source unknown, destination 3.3.3.9
Tunnel bandwidth 64 (kbps)
Tunnel TTL 255
Tunnel protocol/transport CR_LSP
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 1911 bytes/sec, 15288 bits/sec, 0 packets/sec
0 packets input, 0 bytes, 0 drops
1526 packets output, 22356852 bytes, 0 drops
# Execute the display mpls te tunnel-interface command on Switch A to display detailed information about the MPLS TE tunnel.
[SwitchA] display mpls te tunnel-interface
Tunnel Name : Tunnel 4
Tunnel State : Up (Main CRLSP up, Shared-resource CRLSP down)
Tunnel Attributes :
LSP ID : 48960 Tunnel ID : 4
Admin State : Normal
Ingress LSR ID : 1.1.1.1 Egress LSR ID : 3.3.3.3
Signaling : RSVP-TE Static CRLSP Name : -
Resv Style : SE
Tunnel mode : -
Reverse-LSP name : -
Reverse-LSP LSR ID : - Reverse-LSP Tunnel ID: -
Class Type : CT0 Tunnel Bandwidth : 0 kbps
Reserved Bandwidth : 0 kbps
Setup Priority : 7 Holding Priority : 7
Affinity Attr/Mask : 0/0
Explicit Path : pri-path
Backup Explicit Path : -
Metric Type : TE
Record Route : Enabled Record Label : Enabled
FRR Flag : Enabled Bandwidth Protection : Disabled
Backup Bandwidth Flag: Disabled Backup Bandwidth Type: -
Backup Bandwidth : -
Bypass Tunnel : No Auto Created : No
Route Pinning : Disabled
Retry Limit : 10 Retry Interval : 2 sec
Reoptimization : Disabled Reoptimization Freq : -
Backup Type : None Backup LSP ID : -
Auto Bandwidth : Disabled Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
5. Configure a bypass tunnel on Switch B (the PLR):
# Configure an explicit path for the bypass tunnel.
[SwitchB] explicit-path by-path
[SwitchB-explicit-path-by-path] nexthop 3.2.1.2
[SwitchB-explicit-path-by-path] nexthop 3.3.1.2
[SwitchB-explicit-path-by-path] nexthop 3.3.3.3
[SwitchB-explicit-path-by-path] quit
# Create MPLS TE tunnel interface Tunnel 5 for the bypass tunnel.
[SwitchB] interface tunnel 5 mode mpls-te
[SwitchB-Tunnel5] ip address 11.1.1.1 255.255.255.0
# Specify the tunnel destination address as LSR ID of Switch C.
[SwitchB-Tunnel5] destination 3.3.3.3
# Specify the tunnel signaling protocol as RSVP-TE.
[SwitchB-Tunnel5] mpls te signaling rsvp-te
# Specify the explicit path to be used as by-path.
[SwitchB-Tunnel5] mpls te path preference 1 explicit-path by-path
# Configure the bandwidth that the bypass tunnel can protect.
[SwitchB-Tunnel5] mpls te backup bandwidth un-limited
[SwitchB-Tunnel5] quit
# Bind the bypass tunnel to the protected interface.
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls te fast-reroute bypass-tunnel tunnel 5
[SwitchB-Vlan-interface2] quit
# Execute the display interface tunnel command on Switch B to verify that the tunnel interface Tunnel 5 is up. (Details not shown.)
6. Configure a static route on Switch A to direct the traffic destined for subnet 4.1.1.0/24 to MPLS TE tunnel 4.
[SwitchA] ip route-static 4.1.1.2 24 tunnel 4 preference 1
Verifying the configuration
# Execute the display mpls lsp command on each switch. The output shows the LSP entries. Switch B and Switch C each have two CRLSPs. The bypass tunnel backs up the primary CRLSP.
[SwitchA] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
1.1.1.1/4/61400 RSVP -/1245 Vlan1
2.1.1.2 Local -/- Vlan1
[SwitchB] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
1.1.1.1/4/614000 RSVP 1245/3 Vlan2
Backup 1245/3 Tun5
2.2.2.2/5/30914 RSVP -/1150 Vlan2
3.2.1.2 Local -/- Vlan4
3.1.1.2 Local -/- Vlan2
[SwitchE] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
2.2.2.2/5/30914 RSVP 1150/3 Vlan5
3.3.1.2 Local -/- Vlan5
# Shut down the protected interface VLAN-interface 2 on the PLR (Switch B).
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] shutdown
[SwitchB-Vlan-interface2] quit
# Execute the display interface tunnel 4 command on Switch A to display information about the primary CRLSP. The output shows that the tunnel interface is still up. (Details not shown.)
# Execute the display mpls te tunnel-interface command on Switch A to display detailed information about the tunnel interface.
[SwitchA] display mpls te tunnel-interface
Tunnel Name : Tunnel 4
Tunnel State : Up (Main CRLSP up, Shared-resource CRLSP being set up)
Tunnel Attributes :
LSP ID : 18753 Tunnel ID : 4
Admin State : Normal
Ingress LSR ID : 1.1.1.1 Egress LSR ID : 3.3.3.3
Signaling : RSVP-TE Static CRLSP Name : -
Resv Style : SE
Tunnel mode : -
Reverse-LSP name : -
Reverse-LSP LSR ID : - Reverse-LSP Tunnel ID: -
Class Type : CT0 Tunnel Bandwidth : 0 kbps
Reserved Bandwidth : 0 kbps
Setup Priority : 7 Holding Priority : 7
Affinity Attr/Mask : 0/0
Explicit Path : pri-path
Backup Explicit Path : -
Metric Type : TE
Record Route : Enabled Record Label : Enabled
FRR Flag : Enabled Bandwidth Protection : Disabled
Backup Bandwidth Flag: Disabled Backup Bandwidth Type: -
Backup Bandwidth : -
Bypass Tunnel : No Auto Created : No
Route Pinning : Disabled
Retry Limit : 10 Retry Interval : 2 sec
Reoptimization : Disabled Reoptimization Freq : -
Backup Type : None Backup LSP ID : -
Auto Bandwidth : Disabled Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
|
|
NOTE: If you execute the display mpls te tunnel-interface command immediately after an FRR, you can see two CRLSPs in up state. This is because FRR uses the make-before-break mechanism to set up a new LSP, and the old LSP is deleted after the new one has been established for a while. |
# Execute the display mpls lsp command on Switch B. The output shows that the bypass tunnel is in use.
[SwitchB] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
1.1.1.1/4/61400 RSVP 1136/3 Tun5
2.2.2.2/5/30914 RSVP -/1149 Vlan4
3.2.1.2 Local -/- Vlan4
# On the PLR, configure the interval for selecting an optimal bypass tunnel as 5 seconds.
[SwitchB] mpls te
[SwitchB-te] fast-reroute timer 5
[SwitchB-te] quit
# On the PLR, bring up the protected interface VLAN-interface 2.
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] undo shutdown
# On Switch A, execute the display interface tunnel 4 command to display information about the primary CRLSP. The output shows that the tunnel interface is in up state. (Details not shown.)
# Wait for about 5 seconds, execute the display mpls lsp verbose command on Switch B. The output shows that Tunnel 5 is bound to interface VLAN-interface 2 but not in use. (Details not shown.)
# Execute the display ip routing-table command on Switch A. The output shows a static route entry with interface Tunnel4 as the output interface. (Details not shown.)
Auto FRR configuration example
Network requirements
Use RSVP-TE to set up a primary CRLSP that explicitly uses path Switch A—Switch B—Switch C—Switch D.
Configure auto FRR on Switch B to automatically set up bypass tunnels for the primary CRLSP.
Configure BFD for RSVP-TE between Switch B and Switch C. When the link between Switch B and Switch C fails, BFD can detect the failure quickly and notify RSVP-TE of the failure, so RSVP-TE can switch traffic to the bypass tunnel.
Figure 33 Network diagram
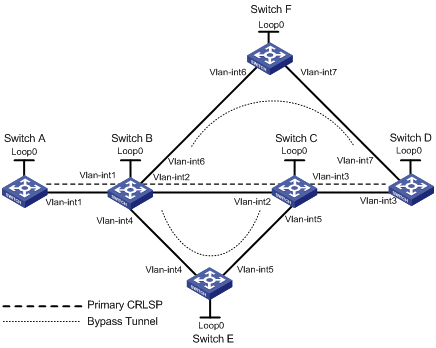
Table 8 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Switch A |
Loop0 |
1.1.1.1/32 |
Switch E |
Loop0 |
5.5.5.5/32 |
|
|
Vlan-int1 |
2.1.1.1/24 |
|
Vlan-int4 |
3.2.1.2/24 |
|
Switch B |
Loop0 |
2.2.2.2/32 |
|
Vlan-int5 |
3.4.1.1/24 |
|
|
Vlan-int1 |
2.1.1.2/24 |
Switch C |
Loop0 |
3.3.3.3/32 |
|
|
Vlan-int2 |
3.1.1.1/24 |
|
Vlan-int3 |
4.1.1.1/24 |
|
|
Vlan-int4 |
3.2.1.1/24 |
|
Vlan-int2 |
3.1.1.2/24 |
|
|
Vlan-int6 |
3.3.1.1/24 |
|
Vlan-int5 |
3.4.1.2/24 |
|
Switch D |
Loop0 |
4.4.4.4/32 |
Switch F |
Loop0 |
6.6.6.6/32 |
|
|
Vlan-int3 |
4.1.1.2/24 |
|
Vlan-int6 |
3.3.1.2/24 |
|
|
Vlan-int7 |
4.2.1.2/24 |
|
Vlan-int7 |
4.2.1.1/24 |
Configuration procedure
1. Configure IP addresses and masks for interfaces. (Details not shown.)
2. Configure IS-IS to advertise interface addresses, including the loopback interface address. (Details not shown.)
3. Configure an LSR ID, and enable MPLS, MPLS TE, and RSVP-TE on each switch. Enable BFD for RSVP-TE on Switch B and Switch C:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] mpls lsr-id 1.1.1.1
[SwitchA] mpls te
[SwitchA-te] quit
[SwitchA] rsvp
[SwitchA-rsvp] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls enable
[SwitchA-Vlan-interface1] mpls te enable
[SwitchA-Vlan-interface1] rsvp enable
[SwitchA-Vlan-interface1] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] mpls lsr-id 2.2.2.2
[SwitchB] mpls te
[SwitchB-te] quit
[SwitchB] rsvp
[SwitchB-rsvp] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls enable
[SwitchB-Vlan-interface1] mpls te enable
[SwitchB-Vlan-interface1] rsvp enable
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls te enable
[SwitchB-Vlan-interface2] rsvp enable
[SwitchB-Vlan-interface2] rsvp bfd enable
[SwitchB-Vlan-interface2] quit
[SwitchB] interface vlan-interface 4
[SwitchB-Vlan-interface4] mpls enable
[SwitchB-Vlan-interface4] mpls te enable
[SwitchB-Vlan-interface4] rsvp enable
[SwitchB-Vlan-interface4] quit
[SwitchB] interface vlan-interface 6
[SwitchB-Vlan-interface6] mpls enable
[SwitchB-Vlan-interface6] mpls te enable
[SwitchB-Vlan-interface6] rsvp enable
[SwitchB-Vlan-interface6] quit
# Configure Switch C in the same way that Switch B is configured. Configure Switch D, Switch E, and Switch F in the same way that Switch A is configured. (Details not shown.)
4. Configure an MPLS TE tunnel on Switch A, the ingress node of the primary CRLSP:
# Configure an explicit path named pri-path for the primary CRLSP.
[SwitchA] explicit-path pri-path
[SwitchA-explicit-path-pri-path] nexthop 2.1.1.2
[SwitchA-explicit-path-pri-path] nexthop 3.1.1.2
[SwitchA-explicit-path-pri-path] nexthop 4.1.1.2
[SwitchA-explicit-path-pri-path] nexthop 4.4.4.4
[SwitchA-explicit-path-pri-path] quit
# Configure an MPLS TE tunnel.
[SwitchA] interface tunnel 1 mode mpls-te
[SwitchA-Tunnel1] ip address 10.1.1.1 255.255.255.0
# Specify the tunnel destination address as the LSR ID of Switch D.
[SwitchA-Tunnel1] destination 4.4.4.4
# Specify the tunnel signaling protocol as RSVP-TE.
[SwitchA-Tunnel1] mpls te signaling rsvp-te
# Specify the explicit path as pri-path.
[SwitchA-Tunnel1] mpls te path preference 1 explicit-path pri-path
# Enable FRR for the MPLS TE tunnel.
[SwitchA-Tunnel1] mpls te fast-reroute
[SwitchA-Tunnel1] quit
# Execute the display interface tunnel command on Switch A. The output shows that the MPLS TE interface Tunnel1 is up.
[SwitchA] display interface tunnel
Tunnel1 current state: UP
Line protocol current state: UP
Description: Tunnel1 Interface
The Maximum Transmit Unit is 64000
Internet Address is 10.1.1.1/24 Primary
Tunnel source unknown, destination 4.4.4.4
Tunnel bandwidth 64 (kbps)
Tunnel TTL 255
Tunnel protocol/transport CR_LSP
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 1911 bytes/sec, 15288 bits/sec, 0 packets/sec
0 packets input, 0 bytes, 0 drops
1526 packets output, 22356852 bytes, 0 drops
# Execute the display mpls te tunnel-interface command on Switch A to display detailed information about the MPLS TE tunnel interface.
[SwitchA] display mpls te tunnel-interface
Tunnel Name : Tunnel 1
Tunnel State : Up (Main CRLSP up, Shared-resource CRLSP down)
Tunnel Attributes :
LSP ID : 16802 Tunnel ID : 1
Admin State : Normal
Ingress LSR ID : 2.2.2.2 Egress LSR ID : 4.4.4.4
Signaling : RSVP-TE Static CRLSP Name : -
Resv Style : SE
Tunnel mode : -
Reverse-LSP name : -
Reverse-LSP LSR ID : - Reverse-LSP Tunnel ID: -
Class Type : CT0 Tunnel Bandwidth : 0 kbps
Reserved Bandwidth : 0 kbps
Setup Priority : 7 Holding Priority : 7
Affinity Attr/Mask : 0/0
Explicit Path : exp1
Backup Explicit Path : -
Metric Type : TE
Record Route : Enabled Record Label : Enabled
FRR Flag : Enabled Bandwidth Protection : Disabled
Backup Bandwidth Flag: Disabled Backup Bandwidth Type: -
Backup Bandwidth : -
Bypass Tunnel : No Auto Created : No
Route Pinning : Disabled
Retry Limit : 3 Retry Interval : 2 sec
Reoptimization : Disabled Reoptimization Freq : -
Backup Type : None Backup LSP ID : -
Auto Bandwidth : Disabled Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
5. Configure auto FRR on Switch B (the PLR):
# Enable the automatic bypass tunnel setup function globally.
[SwitchB] mpls te
[SwitchB-te] auto-tunnel backup
# Specify interface numbers 50 to 100 for the automatically created bypass tunnels.
[SwitchB-te-auto-bk] tunnel-number min 50 max 100
[SwitchB-te-auto-bk] quit
Verifying the configuration
# Execute the display interface tunnel brief on Switch B. The output shows that two tunnels have been created automatically.
[SwitchB] display interface tunnel brief
Brief information on interface(s) under route mode:
Link: ADM - administratively down; Stby - standby
Protocol: (s) - spoofing
Interface Link Protocol Main IP Description
Tun50 UP UP --
Tun51 UP UP --
# Execute the display mpls te tunnel-interface command on Switch B to display information about Tunnel 50 and Tunnel 51. The output shows that Tunnel 50 and Tunnel 51 are automatically created bypass tunnels. Tunnel 50 is a node-protection bypass tunnel (egress LSR ID is 4.4.4.4, the LSR ID of Switch D). Tunnel 51 is a link-protection bypass tunnel (egress LSR ID is 3.3.3.3, the LSR ID of Switch C).
[SwitchB] display mpls te tunnel-interface tunnel 50
Tunnel Name : Tunnel 50
Tunnel State : Up (Main CRLSP up, Shared-resource CRLSP down)
Tunnel Attributes :
LSP ID : 16802 Tunnel ID : 50
Admin State : Normal
Ingress LSR ID : 2.2.2.2 Egress LSR ID : 4.4.4.4
Signaling : RSVP-TE Static CRLSP Name : -
Resv Style : SE
Tunnel mode : -
Reverse-LSP name : -
Reverse-LSP LSR ID : - Reverse-LSP Tunnel ID: -
Class Type : CT0 Tunnel Bandwidth : 0 kbps
Reserved Bandwidth : 0 kbps
Setup Priority : 7 Holding Priority : 7
Affinity Attr/Mask : 0/0
Explicit Path : -
Backup Explicit Path : -
Metric Type : TE
Record Route : Enabled Record Label : Disabled
FRR Flag : Disabled Bandwidth Protection : Disabled
Backup Bandwidth Flag: Disabled Backup Bandwidth Type: -
Backup Bandwidth : -
Bypass Tunnel : Yes Auto Created : Yes
Route Pinning : Disabled
Retry Limit : 3 Retry Interval : 2 sec
Reoptimization : Disabled Reoptimization Freq : -
Backup Type : None Backup LSP ID : -
Auto Bandwidth : Disabled Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
[SwitchB] display mpls te tunnel-interface tunnel 51
Tunnel Name : Tunnel 51
Tunnel State : Up (Main CRLSP up, Shared-resource CRLSP down)
Tunnel Attributes :
LSP ID : 16802 Tunnel ID : 51
Admin State : Normal
Ingress LSR ID : 2.2.2.2 Egress LSR ID : 3.3.3.3
Signaling : RSVP-TE Static CRLSP Name : -
Resv Style : SE
Tunnel mode : -
Reverse-LSP name : -
Reverse-LSP LSR ID : - Reverse-LSP Tunnel ID: -
Class Type : CT0 Tunnel Bandwidth : 0 kbps
Reserved Bandwidth : 0 kbps
Setup Priority : 7 Holding Priority : 7
Affinity Attr/Mask : 0/0
Explicit Path : -
Backup Explicit Path : -
Metric Type : TE
Record Route : Enabled Record Label : Disabled
FRR Flag : Disabled Bandwidth Protection : Disabled
Backup Bandwidth Flag: Disabled Backup Bandwidth Type: -
Backup Bandwidth : -
Bypass Tunnel : Yes Auto Created : Yes
Route Pinning : Disabled
Retry Limit : 3 Retry Interval : 2 sec
Reoptimization : Disabled Reoptimization Freq : -
Backup Type : None Backup LSP ID : -
Auto Bandwidth : Disabled Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
# Execute the display mpls lsp command on Switch B. The output shows that the current bypass tunnel that protects the primary CRLSP is Tunnel 50.
[SwitchB] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
2.2.2.2/51/16802 RSVP -/3 Vlan4
2.2.2.2/1/16802 RSVP -/1151 Vlan2
Backup -/3 Tun50
2.2.2.2/50/16802 RSVP -/3 Vlan6
3.2.1.2 Local -/- Vlan6
3.3.1.2 Local -/- Vlan6
# Execute the display rsvp lsp verbose command on Switch A to display detailed information about MPLS TE tunnel 1, the tunnel for the primary CRLSP. The output shows that Tunnel1 is protected by the bypass tunnel Tunnel 50, and the protected node is 3.1.1.1.
[SwitchA] display rsvp lsp tunnel-id 1 verbose
Tunnel name: Tunnel1
Destination: 4.4.4.4 Source: 1.1.1.1
Tunnel ID: 1 LSP ID: 16802
LSR type: Ingress Direction: Unidirectional
Setup priority: 7 Holding priority: 7
In-Label: - Out-Label: 1150
In-Interface: - Out-Interface: Vlan1
Nexthop: 2.1.1.2 Exclude-any: 0
Include-Any: 0 Include-all: 0
Average bitrate: 0 kbps Maximum burst: 1000.00 bytes
Path MTU: 1500 Class type: CT0
RRO number: 12
2.1.1.1/32 Flag: 0x00 (No FRR)
2.1.1.2/32 Flag: 0x00 (No FRR)
1150 Flag: 0x01 (Global label)
2.2.2.2/32 Flag: 0x20 (No FRR/Node-ID)
3.1.1.1/32 Flag: 0x09 (FRR Avail/Node-Prot)
3.1.1.2/32 Flag: 0x00 (No FRR)
1151 Flag: 0x01 (Global label)
3.3.3.3/32 Flag: 0x20 (No FRR/Node-ID)
4.1.1.1/32 Flag: 0x00 (No FRR)
4.1.1.2/32 Flag: 0x00 (No FRR)
3 Flag: 0x01 (Global label)
4.4.4.4/32 Flag: 0x20 (No FRR/Node-ID)
Fast Reroute protection: Ready
FRR inner label: 3 Bypass tunnel: Tunnel50
IETF DS-TE configuration example
Network requirements
Switch A, Switch B, Switch C, and Switch D run IS-IS and all of them are Level-2 switches.
Use RSVP-TE to create a TE tunnel from Switch A to Switch D. Traffic of the tunnel belongs to CT 2, and the tunnel needs a bandwidth of 4000 kbps.
The maximum bandwidth of the link that the tunnel traverses is 10000 kbps and the maximum reservable bandwidth of the link is 10000 kbps. BC 1, BC 2, and BC 3 are 8000 kbps, 5000 kbps, and 2000 kbps.
Figure 34 Network diagram

Table 9 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Switch A |
Loop0 |
1.1.1.9/32 |
Switch D |
Loop0 |
4.4.4.9/32 |
|
|
Vlan-int1 |
10.1.1.1/24 |
|
Vlan-int3 |
30.1.1.2/24 |
|
Switch B |
Loop0 |
2.2.2.9/32 |
Switch C |
Loop0 |
3.3.3.9/32 |
|
|
Vlan-int1 |
10.1.1.2/24 |
|
Vlan-int3 |
30.1.1.1/24 |
|
|
Vlan-int2 |
20.1.1.1/24 |
|
Vlan-int2 |
20.1.1.2/24 |
Configuration procedure
1. Configure IP addresses and masks for interfaces. (Details not shown.)
2. Configure IS-IS to advertise interface addresses, including the loopback interface address:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] isis 1
[SwitchA-isis-1] network-entity 00.0005.0000.0000.0001.00
[SwitchA-isis-1] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] isis enable 1
[SwitchA-Vlan-interface1] isis circuit-level level-2
[SwitchA-Vlan-interface1] quit
[SwitchA] interface loopback 0
[SwitchA-LoopBack0] isis enable 1
[SwitchA-LoopBack0] isis circuit-level level-2
[SwitchA-LoopBack0] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] isis 1
[SwitchB-isis-1] network-entity 00.0005.0000.0000.0002.00
[SwitchB-isis-1] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] isis enable 1
[SwitchB-Vlan-interface1] isis circuit-level level-2
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] isis enable 1
[SwitchB-Vlan-interface2] isis circuit-level level-2
[SwitchB-Vlan-interface2] quit
[SwitchB] interface loopback 0
[SwitchB-LoopBack0] isis enable 1
[SwitchB-LoopBack0] isis circuit-level level-2
[SwitchB-LoopBack0] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] isis 1
[SwitchC-isis-1] network-entity 00.0005.0000.0000.0003.00
[SwitchC-isis-1] quit
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] isis enable 1
[SwitchC-Vlan-interface3] isis circuit-level level-2
[SwitchC-Vlan-interface3] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] isis enable 1
[SwitchC-Vlan-interface2] isis circuit-level level-2
[SwitchC-Vlan-interface2] quit
[SwitchC] interface loopback 0
[SwitchC-LoopBack0] isis enable 1
[SwitchC-LoopBack0] isis circuit-level level-2
[SwitchC-LoopBack0] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] isis 1
[SwitchD-isis-1] network-entity 00.0005.0000.0000.0004.00
[SwitchD-isis-1] quit
[SwitchD] interface vlan-interface 3
[SwitchD-Vlan-interface3] isis enable 1
[SwitchD-Vlan-interface3] isis circuit-level level-2
[SwitchD-Vlan-interface3] quit
[SwitchD] interface loopback 0
[SwitchD-LoopBack0] isis enable 1
[SwitchD-LoopBack0] isis circuit-level level-2
[SwitchD-LoopBack0] quit
# Execute the display ip routing-table command on each switch to verify that the switches have learned the routes to one another, including the routes to the loopback interfaces. Take Switch A as an example:
[SwitchA] display ip routing-table
Destinations : 10 Routes : 10
Destination/Mask Proto Pre Cost NextHop Interface
1.1.1.9/32 Direct 0 0 127.0.0.1 InLoop0
2.2.2.9/32 ISIS 15 10 10.1.1.2 Vlan1
3.3.3.9/32 ISIS 15 20 10.1.1.2 Vlan1
4.4.4.9/32 ISIS 15 30 10.1.1.2 Vlan1
10.1.1.0/24 Direct 0 0 10.1.1.1 Vlan1
10.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
20.1.1.0/24 ISIS 15 20 10.1.1.2 Vlan1
30.1.1.0/24 ISIS 15 30 10.1.1.2 Vlan1
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
3. Configure an LSR ID, enable MPLS, MPLS TE, and RSVP-TE, and configure the DS-TE mode as IETF:
# Configure Switch A.
[SwitchA] mpls lsr-id 1.1.1.9
[SwitchA] mpls te
[SwitchA-te] ds-te mode ietf
[SwitchA-te] quit
[SwitchA] rsvp
[SwitchA-rsvp] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls enable
[SwitchA-Vlan-interface1] mpls te enable
[SwitchA-Vlan-interface1] rsvp enable
[SwitchA-Vlan-interface1] quit
# Configure Switch B.
[SwitchB] mpls lsr-id 2.2.2.9
[SwitchB] mpls te
[SwitchB-te] ds-te mode ietf
[SwitchB-te] quit
[SwitchB] rsvp
[SwitchB-rsvp] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls enable
[SwitchB-Vlan-interface1] mpls te enable
[SwitchB-Vlan-interface1] rsvp enable
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls te enable
[SwitchB-Vlan-interface2] rsvp enable
[SwitchB-Vlan-interface2] quit
# Configure Switch C.
[SwitchC] mpls lsr-id 3.3.3.9
[SwitchC] mpls te
[SwitchC-te] ds-te mode ietf
[SwitchC-te] quit
[SwitchC] rsvp
[SwitchC-rsvp] quit
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] mpls enable
[SwitchC-Vlan-interface3] mpls te enable
[SwitchC-Vlan-interface3] rsvp enable
[SwitchC-Vlan-interface3] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] mpls enable
[SwitchC-Vlan-interface2] mpls te enable
[SwitchC-Vlan-interface2] rsvp enable
[SwitchC-Vlan-interface2] quit
# Configure Switch D.
[SwitchD] mpls lsr-id 4.4.4.9
[SwitchD] mpls te
[SwitchD-te] ds-te mode ietf
[SwitchD-te] quit
[SwitchD] rsvp
[SwitchD-rsvp] quit
[SwitchD] interface vlan-interface 3
[SwitchD-Vlan-interface3] mpls enable
[SwitchD-Vlan-interface3] mpls te enable
[SwitchD-Vlan-interface3] rsvp enable
[SwitchD-Vlan-interface3] quit
4. Configure IS-IS TE:
# Configure Switch A.
[SwitchA] isis 1
[SwitchA-isis-1] cost-style wide
[SwitchA-isis-1] mpls te enable level-2
[SwitchA-isis-1] quit
# Configure Switch B.
[SwitchB] isis 1
[SwitchB-isis-1] cost-style wide
[SwitchB-isis-1] mpls te enable level-2
[SwitchB-isis-1] quit
# Configure Switch C.
[SwitchC] isis 1
[SwitchC-isis-1] cost-style wide
[SwitchC-isis-1] mpls te enable level-2
[SwitchC-isis-1] quit
# Configure Switch D.
[SwitchD] isis 1
[SwitchD-isis-1] cost-style wide
[SwitchD-isis-1] mpls te enable level-2
[SwitchD-isis-1] quit
5. Configure MPLS TE attributes of links:
# Configure the maximum bandwidth, maximum reservable bandwidth, and bandwidth constraints on Switch A.
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls te max-link-bandwidth 10000
[SwitchA-Vlan-interface1] mpls te max-reservable-bandwidth rdm 10000 bc1 8000 bc2 5000 bc3 2000
[SwitchA-Vlan-interface1] quit
# Configure the maximum bandwidth, maximum reservable bandwidth, and bandwidth constraints on Switch B.
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls te max-link-bandwidth 10000
[SwitchB-Vlan-interface1] mpls te max-reservable-bandwidth rdm 10000 bc1 8000 bc2 5000 bc3 2000
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls te max-link-bandwidth 10000
[SwitchB-Vlan-interface2] mpls te max-reservable-bandwidth rdm 10000 bc1 8000 bc2 5000 bc3 2000
[SwitchB-Vlan-interface2] quit
# Configure the maximum bandwidth, maximum reservable bandwidth, and bandwidth constraints on Switch C.
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] mpls te max-link-bandwidth 10000
[SwitchC-Vlan-interface3] mpls te max-reservable-bandwidth rdm 10000 bc1 8000 bc2 5000 bc3 2000
[SwitchC-Vlan-interface3] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] mpls te max-link-bandwidth 10000
[SwitchC-Vlan-interface2] mpls te max-reservable-bandwidth rdm 10000 bc1 8000 bc2 5000 bc3 2000
[SwitchC-Vlan-interface2] quit
# Configure the maximum bandwidth, maximum reservable bandwidth, and bandwidth constraints on Switch D.
[SwitchD] interface vlan-interface 3
[SwitchD-Vlan-interface3] mpls te max-link-bandwidth 10000
[SwitchD-Vlan-interface3] mpls te max-reservable-bandwidth rdm 10000 bc1 8000 bc2 5000 bc3 2000
[SwitchD-Vlan-interface3] quit
6. Configure an MPLS TE tunnel on Switch A:
# Create the MPLS TE tunnel interface Tunnel 1.
[SwitchA] interface Tunnel 1 mode mpls-te
[SwitchA-Tunnel1] ip address 7.1.1.1 255.255.255.0
# Specify the tunnel destination address as the LSR ID of Switch D.
[SwitchA-Tunnel1] destination 4.4.4.9
# Configure MPLS TE to use RSVP-TE to establish the tunnel.
[SwitchA-Tunnel1] mpls te signaling rsvp-te
# Assign 4000 kbps bandwidth to CT 2 for the tunnel.
[SwitchA-Tunnel1] mpls te bandwidth ct2 4000
# Set the tunnel setup priority and holding priority both to 0.
[SwitchA-Tunnel1] mpls te priority 0
[SwitchA-Tunnel1] quit
7. Configure a static route on Switch A to direct the traffic destined for subnet 30.1.1.0/24 to MPLS TE tunnel 1.
[SwitchA] ip route-static 30.1.1.2 24 tunnel 1 preference 1
Verifying the configuration
# Execute the display interface tunnel command on Switch A. The output shows that the tunnel interface is up.
[SwitchA] display interface tunnel
Tunnel1 current state: UP
Line protocol current state: UP
Description: Tunnel1 Interface
The Maximum Transmit Unit is 64000
Internet Address is 7.1.1.1/24 Primary
Tunnel source unknown, destination 4.4.4.9
Tunnel bandwidth 64 (kbps)
Tunnel TTL 255
Tunnel protocol/transport CR_LSP
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
0 packets input, 0 bytes 0 drop 0 packets output, 0 bytes 0 drop
# Execute the display mpls te tunnel-interface command on Switch A to display detailed information about the MPLS TE tunnel.
[SwitchA] display mpls te tunnel-interface
Tunnel Name : Tunnel 1
Tunnel State : Up (Main CRLSP up, Shared-resource CRLSP down)
Tunnel Attributes :
LSP ID : 36882 Tunnel ID : 1
Admin State : Normal
Ingress LSR ID : 1.1.1.9 Egress LSR ID : 4.4.4.9
Signaling : RSVP-TE Static CRLSP Name : -
Resv Style : SE
Tunnel mode : -
Reverse-LSP name : -
Reverse-LSP LSR ID : - Reverse-LSP Tunnel ID: -
Class Type : CT2 Tunnel Bandwidth : 4000 kbps
Reserved Bandwidth : 4000 kbps
Setup Priority : 0 Holding Priority : 0
Affinity Attr/Mask : 0/0
Explicit Path : -
Backup Explicit Path : -
Metric Type : TE
Record Route : Disabled Record Label : Disabled
FRR Flag : Disabled Bandwidth Protection : Disabled
Backup Bandwidth Flag: Disabled Backup Bandwidth Type: -
Backup Bandwidth : -
Bypass Tunnel : No Auto Created : No
Route Pinning : Disabled
Retry Limit : 10 Retry Interval : 2 sec
Reoptimization : Disabled Reoptimization Freq : -
Backup Type : None Backup LSP ID : -
Auto Bandwidth : Disabled Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
# Execute the display mpls te link-management bandwidth-allocation command on Switch A to display bandwidth information on interface VLAN-interface 1.
[SwitchA] display mpls te link-management bandwidth-allocation interface vlan-interface 1
Interface: Vlan-interface1
Max Link Bandwidth : 10000 kbps
Max Reservable Bandwidth of Prestandard RDM : 0 kbps
Max Reservable Bandwidth of IETF RDM : 10000 kbps
Max Reservable Bandwidth of IETF MAM : 0 kbps
Allocated Bandwidth-Item Count : 1
Allocated Bandwidth : 0 kbps
Physical Link Status : Up
BC Prestandard RDM(kbps) IETF RDM(kbps) IETF MAM(kbps)
0 0 10000 0
1 0 8000 0
2 - 5000 0
3 - 2000 0
TE Class Class Type Priority BW Reserved(kbps) BW Available(kbps)
0 0 0 0 0
1 0 1 0 0
2 0 2 0 0
3 0 3 0 0
4 0 4 0 0
5 0 5 0 0
6 0 6 0 0
7 0 7 0 0
8 1 0 0 0
9 1 1 0 0
10 1 2 0 0
11 1 3 0 0
12 1 4 0 0
13 1 5 0 0
14 1 6 0 0
15 1 7 0 0
# Execute the display ip routing-table command on Switch A. The output shows a static route entry with interface Tunnel 1 as the output interface. (Details not shown.)
Troubleshooting MPLS TE
No TE LSA generated
Symptom
OSPF TE is configured but no TE LSAs can be generated to describe MPLS TE attributes.
Analysis
For TE LSAs to be generated, at least one OSPF neighbor must reach FULL state.
Solution
1. To resolve the problem:
a. Use the display current-configuration command to verify that MPLS TE is configured on involved interfaces.
b. Use the debugging ospf mpls-te command to verify that OSPF can receive the TE LINK establishment message.
c. Use the display ospf peer command to verify that OSPF neighbors are established correctly.
2. If the problem persists, contact H3C Support.
Configuring a static CRLSP
Overview
A static Constraint-based Routed Label Switched Path (CRLSP) is established by manually specifying CRLSP setup information on the ingress, transit, and egress nodes of the forwarding path. The CRLSP setup information includes incoming label, outgoing label, and required bandwidth. If the device does not have enough bandwidth resources required by a CRLSP, the CRLSP cannot be established.
Static CRLSPs consume fewer resources, but they cannot automatically adapt to network topology changes. Therefore, static CRLSPs are suitable for small and stable networks with simple topologies.
Follow these guidelines to establish a static CRLSP:
· Configure the ingress node as follows:
? Specify the outgoing label for the CRLSP, the next hop or the outgoing interface to the next hop, and the required bandwidth.
? Create an MPLS TE tunnel interface.
? Reference the static CRLSP for the tunnel interface.
The tunnel interface adds the outgoing label of the static CRLSP to each packet, and forwards the packet to the next hop or out of the outgoing interface.
· A transit node swaps the label carried in a received packet with a specific label. It forwards the packet to the next hop or out of the outgoing interface. You must specify the incoming label, the outgoing label, the next hop or the outgoing interface, and the required bandwidth on each transit node.
· If it is not configured with the penultimate hop popping function, an egress node pops the incoming label of a packet. It performs label forwarding according to the inner label or IP forwarding. You are only required to specify the incoming label on the egress node.
· The outgoing label specified on an LSR must be the same as the incoming label specified on the directly connected downstream LSR.
Feature and software version compatibility
The static CRLSP feature is available in Release 1138P01 and later versions.
Configuration procedure
Static CRLSPs are special static LSPs. They use the same label space as static LSPs. On a device, a static CRLSP and a static LSP cannot use the same incoming label.
A static CRLSP can be used to forward MPLS TE traffic only after you create an MPLS TE tunnel interface on the ingress node and reference the static CRLSP for the tunnel interface. For more information about MPLS TE, see "Configuring MPLS TE."
Before you configure a static CRLSP, perform the following tasks:
· Identify the ingress node, transit nodes, and egress node of the CRLSP.
· Enable MPLS on all interfaces that participate in MPLS forwarding. For more information, see "Configuring basic MPLS."
· Enable MPLS TE for each node and interface that the CRLSP traverses. For more information, see "Configuring MPLS TE."
To configure a static CRLSP:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a static CRLSP. |
·
Configure the ingress node: ·
Configure a transit node: ·
Configure the egress node: |
Use one command according to the position of a device on the network. By default, no static CRLSP exists. Do not configure the next hop address as a local public IP address when configuring the static CRLSP on the ingress node or a transit node. You do not need to execute the static-cr-lsp egress command on the egress node if the outgoing label configured on the penultimate hop of the static CRLSP is 0 or 3. |
Displaying static CRLSPs
Execute display commands in any view.
|
Task |
Command |
|
Display static CRLSP information. |
display mpls static-cr-lsp [ lsp-name lsp-name ] [ verbose ] |
Static CRLSP configuration example
Network requirements
Switch A, Switch B, and Switch C run IS-IS.
Establish an MPLS TE tunnel over a static CRLSP from Switch A to Switch C.
Figure 35 Network diagram
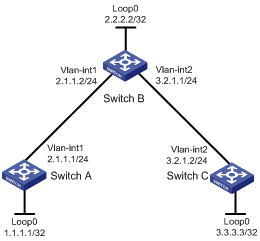
Configuration procedure
1. Configure IP addresses and masks for interfaces. (Details not shown.)
2. Configure IS-IS to advertise interface addresses, including the loopback interface address:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] isis 1
[SwitchA-isis-1] network-entity 00.0005.0000.0000.0001.00
[SwitchA-isis-1] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] isis enable 1
[SwitchA-Vlan-interface1] quit
[SwitchA] interface loopback 0
[SwitchA-LoopBack0] isis enable 1
[SwitchA-LoopBack0] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] isis 1
[SwitchB-isis-1] network-entity 00.0005.0000.0000.0002.00
[SwitchB-isis-1] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] isis enable 1
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] isis enable 1
[SwitchB-Vlan-interface2] quit
[SwitchB] interface loopback 0
[SwitchB-LoopBack0] isis enable 1
[SwitchB-LoopBack0] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] isis 1
[SwitchC-isis-1] network-entity 00.0005.0000.0000.0003.00
[SwitchC-isis-1] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] isis enable 1
[SwitchC-Vlan-interface2] quit
[SwitchC] interface loopback 0
[SwitchC-LoopBack0] isis enable 1
[SwitchC-LoopBack0] quit
# Execute the display ip routing-table command on each switch to verify that the switches have learned the routes to one another, including the routes to the Loopback interfaces. (Details not shown.)
3. Configure an LSR ID, and enable MPLS and MPLS TE:
# Configure Switch A.
[SwitchA] mpls lsr-id 1.1.1.1
[SwitchA] mpls te
[SwitchA-te] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls enable
[SwitchA-Vlan-interface1] mpls te enable
[SwitchA-Vlan-interface1] quit
# Configure Switch B.
[SwitchB] mpls lsr-id 2.2.2.2
[SwitchB] mpls te
[SwitchB-te] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls enable
[SwitchB-Vlan-interface1] mpls te enable
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls te enable
[SwitchB-Vlan-interface2] quit
# Configure Switch C.
[SwitchC] mpls lsr-id 3.3.3.3
[SwitchC] mpls te
[SwitchC-te] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] mpls enable
[SwitchC-Vlan-interface2] mpls te enable
[SwitchC-Vlan-interface2] quit
4. Configure an MPLS TE tunnel on Switch A:
# Configure MPLS TE tunnel interface Tunnel 0.
[SwitchA] interface tunnel 0 mode mpls-te
[SwitchA-Tunnel0] ip address 6.1.1.1 255.255.255.0
# Specify the tunnel destination address as the LSR ID of Switch C.
[SwitchA-Tunnel0] destination 3.3.3.3
# Configure MPLS TE to use a static CRLSP to establish the tunnel.
[SwitchA-Tunnel0] mpls te signaling static
[SwitchA-Tunnel0] quit
5. Create a static CRLSP:
# Configure Switch A as the ingress node of the static CRLSP, and specify the next hop address as 2.1.1.2 and outgoing label as 20.
[SwitchA] static-cr-lsp ingress static-cr-lsp-1 nexthop 2.1.1.2 out-label 20
# On Switch A, configure tunnel 0 to reference the static CRLSP static-cr-lsp-1.
[SwitchA] interface Tunnel0
[SwitchA-Tunnel0] mpls te static-cr-lsp static-cr-lsp-1
[SwitchA-Tunnel0] quit
# Configure Switch B as the transit node of the static CRLSP, and specify the incoming label as 20, the next hop address as 3.2.1.2, and outgoing label as 30.
[SwitchB] static-cr-lsp transit static-cr-lsp-1 in-label 20 nexthop 3.2.1.2 out-label 30
# Configure Switch C as the egress node of the static CRLSP, and specify the incoming label as 30.
[SwitchC] static-cr-lsp egress static-cr-lsp-1 in-label 30
6. Configure a static route on Switch A to direct traffic destined for subnet 3.2.1.0/24 to MPLS TE tunnel 0.
[SwitchA] ip route-static 3.2.1.2 24 tunnel 0 preference 1
Verifying the configuration
# Execute the display interface tunnel command on Switch A. The output shows that the tunnel interface is up.
[SwitchA] display interface tunnel
Tunnel0
Current state: UP
Line protocol state: UP
Description: Tunnel0 Interface
Bandwidth: 64kbps
Maximum Transmit Unit: 64000
Internet Address is 6.1.1.1/24 Primary
Tunnel source unknown, destination 3.3.3.3
Tunnel TTL 255
Tunnel protocol/transport CR_LSP
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# Execute the display mpls te tunnel-interface command on Switch A to display detailed information about the MPLS TE tunnel.
[SwitchA] display mpls te tunnel-interface
Tunnel Name : Tunnel 0
Tunnel State : Up (Main CRLSP up)
Tunnel Attributes :
LSP ID : 1 Tunnel ID : 0
Admin State : Normal
Ingress LSR ID : 1.1.1.1 Egress LSR ID : 3.3.3.3
Signaling : Static Static CRLSP Name : static-cr-lsp-1
Resv Style : -
Tunnel mode : -
Reverse-LSP name : -
Reverse-LSP LSR ID : - Reverse-LSP Tunnel ID: -
Class Type : - Tunnel Bandwidth : -
Reserved Bandwidth : -
Setup Priority : 0 Holding Priority : 0
Affinity Attr/Mask : -/-
Explicit Path : -
Backup Explicit Path : -
Metric Type : TE
Record Route : - Record Label : -
FRR Flag : - Backup Bandwidth Flag: -
Backup Bandwidth Type: - Backup Bandwidth : -
Route Pinning : -
Retry Limit : 10 Retry Interval : 2 sec
Reoptimization : - Reoptimization Freq : -
Backup Type : - Backup LSP ID : -
Auto Bandwidth : - Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
# Execute the display mpls lsp command or the display mpls static-cr-lsp command on each switch to display the static CRLSP information.
[SwitchA] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
1.1.1.1/0/1 StaticCR -/20 Vlan1
2.1.1.2 Local -/- Vlan1
[SwitchB] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
- StaticCR 20/30 Vlan2
3.2.1.2 Local -/- Vlan2
[SwitchC] display mpls lsp
FEC Proto In/Out Label Interface/Out NHLFE
- StaticCR 30/- -
[SwitchA] display mpls static-cr-lsp
Name LSR Type In/Out Label Out Interface State
static-cr-lsp-1 Ingress Null/20 Vlan1 Up
[SwitchB] display mpls static-cr-lsp
Name LSR Type In/Out Label Out Interface State
static-cr-lsp-1 Transit 20/30 Vlan2 Up
[SwitchC] display mpls static-cr-lsp
Name LSR Type In/Out Label Out Interface State
static-cr-lsp1 Egress 30/Null - Up
# Execute the display ip routing-table command on Switch A. The output shows a static route entry with interface Tunnel 0 as the egress interface. (Details not shown.)
Configuring RSVP
Overview
The Resource Reservation Protocol (RSVP) is a signaling protocol that reserves resources on a network. Extended RSVP supports MPLS label distribution and allows resource reservation information to be transmitted with label bindings. This extended RSVP is called RSVP-TE. RSVP-TE is a label distribution protocol for MPLS TE. It distributes MPLS labels and reserves resources on the nodes of a specific path to establish a CRLSP.
RSVP messages
RSVP uses the following types of messages:
· Path messages—Sent by the sender downstream along the data transmission path to save path state information on each node along the path.
· Resv messages—Sent by the receiver upstream towards the sender to request resource reservation and to create and maintain reservation state on each node along the reverse of the data transmission path.
· PathTear messages—Sent downstream by the sender or a transit node to remove the path state and related reservation state on each node along the path.
· ResvTear messages—Sent upstream by the receiver or a transit node to remove the reservation state on each node along the path.
· PathErr messages—Sent upstream by the receiver or a transit node to report Path message processing errors to the sender. They do not affect the state of the nodes along the path.
· ResvErr messages—Sent downstream by the sender or a transit node to notify the downstream nodes that an error has occurred during Resv message processing or that a reservation error has occurred because of preemption.
· ResvConf messages—Sent to the receiver to confirm Resv messages.
· Hello messages—Sent between any two directly connected RSVP neighbors to set up and maintain the neighbor relationship. Hello messages are sent only when the RSVP hello extension has been enabled.
RSVP-TE extends RSVP by adding new objects to Path and Resv messages. In addition to label bindings, these objects also carry routing constraints to support CRLSP and FRR.
New objects added to the Path message include:
· LABEL_REQUEST—Requests the downstream node to allocate a label.
· EXPLICIT_ROUTE—Carries the path information calculated by the ingress node, making sure the CRLSP is set up along that path.
· RECORD_ROUTE—Records the path that the CRLSP actually traverses and the label allocated by each node on the path.
· SESSION_ATTRIBUTE—Carries the MPLS TE tunnel attributes, such as the setup priority, holding priority, and affinity.
New objects added to the Resv message include:
· LABEL—Advertises the label allocated by the downstream node to the upstream node.
· RECORD_ROUTE—Records the path that the CRLSP actually traverses and the label allocated by each node on the path.
CRLSP setup procedure
Figure 36 Setting up a CRLSP
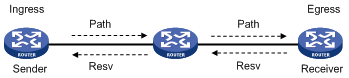
As shown in Figure 36, a CRLSP is set up using the following steps:
1. The ingress LSR generates a Path message that carries LABEL_REQUEST, and then forwards the message along the path calculated by CSPF hop-by-hop towards the egress LSR.
2. After receiving the Path message, the egress LSR generates a Resv message carrying the reservation information and the LABEL object. It forwards the Resv message to the ingress LSR along the reverse direction of the path that the Path message traveled.
The Resv message advertises labels, reserves resources, and creates a reserve state on each LSR it passes, so QoS can be guaranteed for services transmitted on the CRLSP.
3. When the ingress LSR receives the Resv message, the CRLSP is established.
RSVP refresh mechanism
Refresh messages
RSVP maintains resource reservation states on a node by periodically sending messages.
The resource reservation states include path states and reservation states. A path state is saved in a path state block (PSB), and a reservation state is saved in a reservation state block (RSB). A PSB is created by a Path message and saves the LABEL_REQUEST object. A RSB is created by a Resv message and saves the LABEL object.
The path states and reservation states are refreshed periodically by Path and Resv messages. A state is removed if no refresh messages for the state are received in a certain interval, and the CRLSP established based on this state is also removed.
The Path and Resv messages for refreshing the resource reservation states are collectively referred to as refresh messages. Refresh messages can also be used to recover from lost RSVP messages.
When multiple RSVP sessions exist on a network, a short refresh interval can cause network degradation, but a long refresh interval cannot meet the requirements of delay sensitive applications. To find an appropriate balance, you can use the summary refresh (Srefresh) and the reliable RSVP message delivery functions.
Srefresh
Srefresh is implemented by adding a Message_ID object to a Path or Resv message to uniquely identify the message. To refresh Path and Resv states, RSVP does not need to send standard Path and Resv messages. Instead, it sends an Srefresh message carrying a set of Message_ID objects that identify the Path and Resv states to be refreshed. The Srefresh function reduces the number of refresh messages on the network and speeds up refresh message processing.
Reliable RSVP message delivery
An RSVP sender cannot know or retransmit lost RSVP messages. The reliable RSVP message delivery mechanism is designed to ensure reliable transmission.
This mechanism requires the peer device to acknowledge each RSVP message received from the local device. If no acknowledgment is received, the local device retransmits the message.
To implement reliable RSVP message delivery, a node sends an RSVP message that includes a Message_ID object in which the ACK_Desired flag is set. The receiver needs to confirm the delivery by sending back a message that includes the Message_ID_ACK object. If the sender does not receive a Message_ID_ACK within the retransmission interval (Rf), it performs the following tasks:
· Retransmits the message when Rf expires.
· Sets the next transmission interval to (1 + delta) × Rf.
The sender repeats this process until it receives the Message_ID_ACK before the retransmission time expires or it has transmitted the message three times.
RSVP authentication
RSVP authentication ensures integrity of RSVP messages, and prevents false resource reservation requests from occupying network resources.
With RSVP authentication, the sender uses the MD5 algorithm and the authentication key to calculate a message digest for an RSVP message, and inserts the message digest to the RSVP message. When the receiver receives the message, it performs the same calculation and compares the result with the message digest. If they match, the receiver accepts the message. Otherwise, it drops the message.
By carrying a sequence number in a message, RSVP authentication can also prevent packet replay attacks. The device records the sequence number of a received RSVP message, and determines whether the subsequent messages are valid according to the recorded sequence number. If the sequence number of a subsequent message is within the valid range, the device accepts the message. Otherwise, it drops the message.
RSVP GR
RSVP GR defines the following roles:
· GR restarter—Router that gracefully restarts due to a manually configured command or a fault. It must be GR-capable.
· GR helper—Neighbor of the GR restarter. A GR helper maintains the neighbor relationship with the GR restarter and helps the GR restarter restore its LFIB information. A GR helper must be GR-capable.
The device can act only as a RSVP GR helper.
The RSVP GR function depends on the extended hello capability of RSVP. A GR-capable device advertises its GR capability and relevant time parameters to its neighbors in RSVP hello packets. If a device and all its neighbors have the RSVP GR capability and have exchanged GR parameters, each of them can function as the GR helper of another device.
A GR helper considers that a GR restarter is rebooting when it does not receive hellos or receives erroneous hellos from the restarter in three consecutive hello intervals. When a GR restarter is rebooting, the GR helpers perform the following tasks:
· Retain soft state information about the GR restarter.
· Continue sending hello packets periodically to the GR restarter until the restart timer expires.
If a GR helper receives a hello message from the GR restarter before the restart timer expires, the recovery timer is started and signaling packet exchange is triggered to restore the original soft state. Otherwise, all RSVP soft state information and forwarding entries relevant to the neighbor are removed. When the recovery timer expires, soft state information and forwarding entries that are not restored are removed.
Protocols and standards
· RFC 2205, Resource ReSerVation Protocol
· RFC 3209, RSVP-TE: Extensions to RSVP for LSP Tunnels
· RFC 2961, RSVP Refresh Overhead Reduction Extensions
Feature and software version compatibility
The RSVP feature is available in Release 1138P01 and later versions.
RSVP configuration task list
|
Tasks at a glance |
|
(Required.) Enabling RSVP |
|
(Optional.) Perform the following tasks on each node of an MPLS TE tunnel according to your network requirements: · Configuring RSVP Srefresh and reliable RSVP message delivery · Configuring RSVP hello extension · Configuring RSVP authentication |
Enabling RSVP
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable global RSVP and enter RSVP view. |
rsvp |
By default, global RSVP is disabled. |
|
3. Return to system view. |
quit |
N/A |
|
4. Enter interface view. |
interface interface-type interface-number |
N/A |
|
5. Enable RSVP for the interface. |
rsvp enable |
By default, RSVP is disabled on an interface. |
Configuring RSVP refresh
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RSVP view. |
rsvp |
N/A |
|
3. Configure the refresh interval for Path and Resv messages. |
refresh interval interval |
By default, the refresh interval is 30 seconds for both path and Resv messages. |
|
4. Configure the PSB and RSB timeout multiplier. |
keep-multiplier number |
By default, the PSB and RSB timeout multiplier is 3. |
Configuring RSVP Srefresh and reliable RSVP message delivery
To configure Srefresh and reliable RSVP message delivery:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable Srefresh and reliable RSVP message delivery. |
rsvp reduction srefresh [ reliability ] |
By default, Srefresh and reliable RSVP message delivery are disabled. |
|
4. Configure the retransmission increment value for reliable RSVP message delivery. |
rsvp reduction retransmit increment increment-value |
By default, the RSVP message retransmission increment is 1. This command takes effect after reliable RSVP message delivery is enabled by using the rsvp reduction srefresh reliability command. |
|
5. Configure the retransmission interval for reliable RSVP message delivery. |
rsvp reduction retransmit interval retrans-timer-value |
By default, the RSVP message retransmission interval is 500 milliseconds. This command takes effect after reliable RSVP message delivery is enabled by using the rsvp reduction srefresh reliability command. |
Configuring RSVP hello extension
When RSVP hello extension is enabled on an interface, the device receives and sends hello messages through the interface to detect the neighbor's status.
If the device receives a hello request from the neighbor, the device replies with a hello ACK message. If the device receives no hello request from the neighbor within the interval specified by the hello interval command, the device sends hello requests to the neighbor.
When the number of consecutive lost hellos or erroneous hellos from the neighbor reaches the maximum (specified by the hello lost command), the device determines the neighbor is in fault. If GR is configured, the device serves as a GR helper to help the neighbor to restart. If FRR is configured, the device performs an FRR. For more information about FRR, see "Configuring MPLS TE."
To configure RSVP hello extension:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RSVP view. |
rsvp |
N/A |
|
3. Configure the maximum number of consecutive lost or erroneous hellos. |
hello lost times |
By default, the maximum number is 4. |
|
4. Configure the interval for sending hello requests. |
hello interval interval |
By default, hello requests are sent every 5 seconds. |
|
5. Return to system view. |
quit |
N/A |
|
6. Enter interface view. |
interface interface-type interface-number |
N/A |
|
7. Enable RSVP hello extension. |
rsvp hello enable |
By default, RSVP hello extension is disabled. |
Configuring RSVP authentication
RSVP adopts hop-by-hop authentication to prevent fake resource reservation requests from occupying network resources. The interfaces at the two ends of a link must use the same authentication key.
RSVP authentication can be configured in the following views:
· RSVP view—Configuration applies to all RSVP security associations.
· RSVP neighbor view—Configuration applies only to RSVP security associations with the specified RSVP neighbor.
· Interface view—Configuration applies only to RSVP security associations established on the current interface.
To configure RSVP authentication in RSVP neighbor view:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RSVP view. |
rsvp |
N/A |
|
3. Create an RSVP authentication neighbor and enter RSVP neighbor view. |
peer ip-address |
By default, the device does not have any RSVP authentication neighbors. |
|
4. Enable RSVP authentication for the RSVP neighbor and specify the authentication key. |
authentication key { cipher | plain } auth-key |
By default, RSVP authentication is disabled. |
|
5. Enable challenge-response handshake for the RSVP neighbor. |
By default, the challenge-response handshake function is disabled. |
|
|
6. Configure the idle timeout for the RSVP security associations with the RSVP neighbor. |
authentication lifetime life-time |
By default, the idle timeout is 1800 seconds (30 minutes). |
|
7. Specify the maximum number of out-of-sequence RSVP authentication messages that can be received from the RSVP neighbor. |
authentication window-size number |
By default, only one RSVP authenticated message can be received out of sequence. |
To configure RSVP authentication in interface view:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable RSVP authentication on the interface and configure the authentication key. |
rsvp authentication key { cipher | plain } auth-key |
By default, RSVP authentication is disabled. Do not enable both RSVP authentication and FRR on the same interface. |
|
4. Enable challenge-response handshake on the interface. |
rsvp authentication challenge |
By default, the challenge-response handshake function is disabled. |
|
5. Configure the idle timeout for RSVP security associations on the interface. |
rsvp authentication lifetime life-time |
By default, the idle timeout is 1800 seconds (30 minutes). |
|
6. Specify the maximum number of out-of-sequence RSVP authentication messages that can be received on the interface. |
rsvp authentication window-size number |
By default, only one RSVP authenticated message can be received out of sequence. |
To configure RSVP authentication in RSVP view:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RSVP view. |
rsvp |
N/A |
|
3. Enable RSVP authentication globally and configure the authentication key. |
authentication key { cipher | plain } auth-key |
By default, RSVP authentication is disabled. |
|
4. Enable challenge-response handshake globally. |
authentication challenge |
By default, the challenge-response handshake function is disabled. |
|
5. Configure the global idle timeout for RSVP security associations. |
authentication lifetime life-time |
By default, the idle timeout is 1800 seconds (30 minutes). |
|
6. Specify the global RSVP authentication window size—the maximum number of RSVP authenticated messages that can be received out of sequence. |
authentication window-size number |
By default, only one RSVP authenticated message can be received out of sequence. |
Specifying a DSCP value for outgoing RSVP packets
The DSCP value of an IP packet specifies the priority level of the packet and affects the transmission priority of the packet.
To specify a DSCP value for outgoing RSVP packets:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RSVP view. |
rsvp |
N/A |
|
3. Specify a DSCP value for outgoing RSVP packets. |
dscp dscp-value |
By default, the DSCP value is 48. |
Configuring RSVP GR
RSVP GR depends on the RSVP hello extension function. When configuring RSVP GR, you must enable RSVP hello extension.
Perform this task on GR-capable devices.
To configure RSVP GR:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RSVP view. |
rsvp |
N/A |
|
3. Enable GR for RSVP. |
graceful-restart enable |
By default, RSVP GR is disabled. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enter interface view. |
interface interface-type interface-number |
N/A |
|
6. Enable RSVP hello extension. |
rsvp hello enable |
By default, RSVP hello extension is disabled. |
Enabling BFD for RSVP
If a link fails, MPLS TE tunnels over the link fail to forward packets. MPLS TE cannot quickly detect a link failure. To address this issue, you can enable BFD for RSVP so MPLS TE can quickly switch data from the primary path to the backup path upon a link failure.
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
You must enable RSVP on the interface. |
|
3. Enable BFD for the RSVP neighbor on the interface. |
rsvp bfd enable |
By default, RSVP BFD is disabled. |
Displaying and maintaining RSVP
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display RSVP information. |
display rsvp [ interface [ interface-type interface-number ] ] |
|
Display information about the security associations established with RSVP neighbors. |
display rsvp authentication [ from ip-address ] [ to ip-address ] [ verbose ] |
|
Display information about CRLSPs established through RSVP. |
display rsvp lsp [ destination ip-address ] [ source ip-address ] [ tunnel-id tunnel-id ] [ lsp-id lsp-id ] [ verbose ] |
|
Display information about RSVP neighbors. |
display rsvp peer [ interface interface-type interface-number ] [ ip ip-address ] [ verbose ] |
|
Display information about RSVP resource reservation requests sent to upstream devices. |
display rsvp request [ destination ip-address ] [ source ip-address ] [ tunnel-id tunnel-id ] [ prev-hop ip-address ] [ verbose ] |
|
Display information about RSVP resource reservation states. |
display rsvp reservation [ destination ip-address ] [ source ip-address ] [ tunnel-id tunnel-id ] [ nexthop ip-address ] [ verbose ] |
|
Display information about RSVP path states. |
display rsvp sender [ destination ip-address ] [ source ip-address ] [ tunnel-id tunnel-id ] [ lsp-id lsp-id ] [ verbose ] |
|
Display RSVP statistics. |
display rsvp statistics [ interface [ interface-type interface-number ] ] |
|
Clear RSVP security associations. |
reset rsvp authentication [ from ip-address to ip-address ] |
|
Clear RSVP statistics. |
reset rsvp statistics [ interface [ interface-type interface-number ] |
RSVP configuration examples
Establishing an MPLS TE tunnel with RSVP-TE
Network requirements
Switch A, Switch B, Switch C, and Switch D run IS-IS.
Use RSVP-TE to create an MPLS TE tunnel from Switch A to Switch D.
Figure 37 Network diagram

Table 10 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Switch A |
Loop0 |
1.1.1.9/32 |
Switch D |
Loop0 |
4.4.4.9/32 |
|
|
Vlan-int1 |
10.1.1.1/24 |
|
Vlan-int3 |
30.1.1.2/24 |
|
Switch B |
Loop0 |
2.2.2.9/32 |
Switch C |
Loop0 |
3.3.3.9/32 |
|
|
Vlan-int1 |
10.1.1.2/24 |
|
Vlan-int3 |
30.1.1.1/24 |
|
|
Vlan-int2 |
20.1.1.1/24 |
|
Vlan-int2 |
20.1.1.2/24 |
Configuration procedure
1. Configure IP addresses and masks for interfaces. (Details not shown.)
2. Configure IS-IS to advertise interface addresses, including the loopback interface address:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] isis 1
[SwitchA-isis-1] network-entity 00.0005.0000.0000.0001.00
[SwitchA-isis-1] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] isis enable 1
[SwitchA-Vlan-interface1] quit
[SwitchA] interface loopback 0
[SwitchA-LoopBack0] isis enable 1
[SwitchA-LoopBack0] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] isis 1
[SwitchB-isis-1] network-entity 00.0005.0000.0000.0002.00
[SwitchB-isis-1] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] isis enable 1
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] isis enable 1
[SwitchB-Vlan-interface2] quit
[SwitchB] interface loopback 0
[SwitchB-LoopBack0] isis enable 1
[SwitchB-LoopBack0] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] isis 1
[SwitchC-isis-1] network-entity 00.0005.0000.0000.0003.00
[SwitchC-isis-1] quit
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] isis enable 1
[SwitchC-Vlan-interface3] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] isis enable 1
[SwitchC-Vlan-interface2] quit
[SwitchC] interface loopback 0
[SwitchC-LoopBack0] isis enable 1
[SwitchC-LoopBack0] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] isis 1
[SwitchD-isis-1] network-entity 00.0005.0000.0000.0004.00
[SwitchD-isis-1] quit
[SwitchD] interface vlan-interface 3
[SwitchD-Vlan-interface3] isis enable 1
[SwitchD-Vlan-interface3] quit
[SwitchD] interface loopback 0
[SwitchD-LoopBack0] isis enable 1
[SwitchD-LoopBack0] quit
# Execute the display ip routing-table command on each switch to verify that the switches have learned the routes to one another, including the host to the loopback interfaces. (Details not shown.)
3. Configure an LSR ID, and enable MPLS, MPLS TE, and RSVP:
# Configure Switch A.
[SwitchA] mpls lsr-id 1.1.1.9
[SwitchA] mpls te
[SwitchA-te] quit
[SwitchA] rsvp
[SwitchA-rsvp] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls enable
[SwitchA-Vlan-interface1] mpls te enable
[SwitchA-Vlan-interface1] rsvp enable
[SwitchA-Vlan-interface1] quit
# Configure Switch B.
[SwitchB] mpls lsr-id 2.2.2.9
[SwitchB] mpls te
[SwitchB-te] quit
[SwitchB] rsvp
[SwitchB-rsvp] quit
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls enable
[SwitchB-Vlan-interface1] mpls te enable
[SwitchB-Vlan-interface1] rsvp enable
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls te enable
[SwitchB-Vlan-interface2] rsvp enable
[SwitchB-Vlan-interface2] quit
# Configure Switch C.
[SwitchC] mpls lsr-id 3.3.3.9
[SwitchC] mpls te
[SwitchC-te] quit
[SwitchC] rsvp
[SwitchC-rsvp] quit
[SwitchC] interface vlan-interface 3
[SwitchC-Vlan-interface3] mpls enable
[SwitchC-Vlan-interface3] mpls te enable
[SwitchC-Vlan-interface3] rsvp enable
[SwitchC-Vlan-interface3] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] mpls enable
[SwitchC-Vlan-interface2] mpls te enable
[SwitchC-Vlan-interface2] rsvp enable
[SwitchC-Vlan-interface2] quit
# Configure Switch D.
[SwitchD] mpls lsr-id 4.4.4.9
[SwitchD] mpls te
[SwitchD-te] quit
[SwitchD] rsvp
[SwitchD-rsvp] quit
[SwitchD] interface vlan-interface 3
[SwitchD-Vlan-interface3] mpls enable
[SwitchD-Vlan-interface3] mpls te enable
[SwitchD-Vlan-interface3] rsvp enable
[SwitchD-Vlan-interface3] quit
4. Configure an MPLS TE tunnel on Switch A:
# Configure MPLS TE tunnel interface Tunnel 1.
[SwitchA] interface tunnel 1 mode mpls-te
[SwitchA-Tunnel1] ip address 7.1.1.1 255.255.255.0
# Specify the tunnel destination address as the LSR ID of Switch D.
[SwitchA-Tunnel1] destination 4.4.4.9
# Configure MPLS TE to use RSVP-TE to establish the tunnel.
[SwitchA-Tunnel1] mpls te signaling rsvp-te
[SwitchA-Tunnel1] quit
5. Configure a static route on Switch A to direct the traffic destined for subnet 30.1.1.0/24 to the MPLS TE tunnel 1 for forwarding.
[SwitchA] ip route-static 30.1.1.2 24 tunnel 1 preference 1
Verifying the configuration
# Execute the display interface tunnel command on Switch A. The output shows that the tunnel interface is up.
[SwitchA] display interface tunnel
Tunnel1
Current state: UP
Line protocol state: UP
Description: Tunnel1 Interface
Bandwidth: 64kbps
Maximum Transmit Unit: 1496
Internet Address is 7.1.1.1/24 Primary
Tunnel source unknown, destination 4.4.4.9
Tunnel TTL 255
Tunnel protocol/transport CR_LSP
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 6 bytes/sec, 48 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 177 packets, 11428 bytes, 0 drops
# Execute the display mpls te tunnel-interface command on Switch A. The output shows detailed information about the MPLS TE tunnel.
[SwitchA] display mpls te tunnel-interface
Tunnel Name : Tunnel 1
Tunnel State : Up (Main CRLSP up, Shared-resource CRLSP down)
Tunnel Attributes :
LSP ID : 23331 Tunnel ID : 1
Admin State : Normal
Ingress LSR ID : 1.1.1.9 Egress LSR ID : 4.4.4.9
Signaling : RSVP-TE Static CRLSP Name : -
Resv Style : SE
Tunnel mode : -
Reverse-LSP name : -
Reverse-LSP LSR ID : - Reverse-LSP Tunnel ID: -
Class Type : CT0 Tunnel Bandwidth : 0 kbps
Reserved Bandwidth : 0 kbps
Setup Priority : 7 Holding Priority : 7
Affinity Attr/Mask : 0/0
Explicit Path : -
Backup Explicit Path : -
Metric Type : TE
Record Route : Disabled Record Label : Disabled
FRR Flag : Disabled Backup Bandwidth Flag: Disabled
Backup Bandwidth Type: - Backup Bandwidth : -
Route Pinning : Disabled
Retry Limit : 10 Retry Interval : 2 sec
Reoptimization : Disabled Reoptimization Freq : -
Backup Type : None Backup LSP ID : -
Auto Bandwidth : Disabled Auto Bandwidth Freq : -
Min Bandwidth : - Max Bandwidth : -
Collected Bandwidth : -
# Execute the display ip routing-table command on Switch A to verify that a static route entry with interface Tunnel 1 as the output interface exists. (Details not shown.)
RSVP GR configuration example
Network requirements
Switch A, Switch B, and Switch C run IS-IS.
Use RSVP-TE to establish a TE tunnel from Switch A to Switch C.
Configure RSVP GR on the switches to ensure continuous forwarding when a switch reboots.
Figure 38 Network diagram
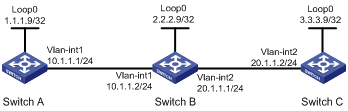
Configuration procedure
1. Configure IP addresses and masks for interfaces. (Details not shown.)
2. Configure IS-IS to advertise interface addresses, including the loopback interface address. (Details not shown.)
3. Configure an LSR ID, enable MPLS, MPLS TE, RSVP, and RSVP hello extension:
# Configure Switch A.
<SwitchA> system-view
[SwitchA] mpls lsr-id 1.1.1.9
[SwitchA] mpls te
[SwitchA-te] quit
[SwitchA] rsvp
[SwitchA-rsvp] quit
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] mpls enable
[SwitchA-Vlan-interface1] mpls te enable
[SwitchA-Vlan-interface1] rsvp enable
[SwitchA-Vlan-interface1] rsvp hello enable
[SwitchA-Vlan-interface1] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] mpls lsr-id 2.2.2.9
[SwitchB] mpls te
[SwitchB-te] quit
[SwitchB] rsvp
[SwitchB-rsvp] quit
[SwitchB-mpls] interface vlan-interface 1
[SwitchB-Vlan-interface1] mpls enable
[SwitchB-Vlan-interface1] mpls te enable
[SwitchB-Vlan-interface1] rsvp enable
[SwitchB-Vlan-interface1] rsvp hello enable
[SwitchB-Vlan-interface1] quit
[SwitchB] interface vlan-interface 2
[SwitchB-Vlan-interface2] mpls enable
[SwitchB-Vlan-interface2] mpls te enable
[SwitchB-Vlan-interface2] rsvp enable
[SwitchB-Vlan-interface2] rsvp hello enable
[SwitchB-Vlan-interface2] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] mpls lsr-id 3.3.3.9
[SwitchC] mpls te
[SwitchC-te] quit
[SwitchC] rsvp
[SwitchC-rsvp] quit
[SwitchC] interface vlan-interface 2
[SwitchC-Vlan-interface2] mpls enable
[SwitchC-Vlan-interface2] mpls te enable
[SwitchC-Vlan-interface2] rsvp enable
[SwitchC-Vlan-interface2] rsvp hello enable
[SwitchC-Vlan-interface2] quit
4. Configure an MPLS TE tunnel. (Details not shown.)
5. Configure RSVP GR:
# Configure Switch A.
[SwitchA] rsvp
[SwitchA-rsvp] graceful-restart enable
# Configure Switch B.
[SwitchB] rsvp
[SwitchB-rsvp] graceful-restart enable
# Configure Switch C.
[SwitchC] rsvp
[SwitchC-rsvp] graceful-restart enable
Verifying the configuration
# After a tunnel is established from Switch A and Switch C, execute the following command on Switch A:
<SwitchA> display rsvp peer verbose
Peer: 10.1.1.2 Interface: Vlan1
Hello state: Up Hello type: Active
PSB count: 0 RSB count: 1
Src instance: 0x1f08 Dst instance: 0x22
Refresh reduction: Disabled Graceful Restart state: Ready
Peer GR restart time: 120000 ms Peer GR recovery time: 0 ms
Configuring tunnel policies
Overview
Tunnel policies enable a PE to forward traffic for each MPLS VPN over a preferred tunnel or over multiple tunnels. The tunnels supported by MPLS VPN include MPLS LSPs and MPLS TE tunnels.
For more information about MPLS TE, see "Configuring MPLS TE." For more information about MPLS VPNs, see "Configuring MPLS L3VPN."
Feature and software version compatibility
The tunnel policy feature is available in Release 1138P01 and later versions.
Configuring a tunnel policy
Configuration guidelines
· To select a preferred tunnel, create a tunnel policy and specify the preferred tunnel with the preferred-path command. The destination address of the preferred tunnel identifies a peer PE so the PE will forward traffic destined for that peer PE over the preferred tunnel.
? If you specify multiple preferred tunnels that have the same destination address in a tunnel policy, only the first configured tunnel takes effect.
? If the first tunnel is not available, the second tunnel is used, and so forth. No load balancing will be performed on these tunnels.
This method explicitly specifies an MPLS TE tunnel for an MPLS VPN, facilitating traffic planning. As a best practice, use this method.
· To select multiple tunnels for load sharing, create a tunnel policy and specify the tunnel selection order and the number of tunnels by using the select-seq load-balance-number command. A tunnel type closer to the select-seq keyword has a higher priority. For example, the select-seq lsp cr-lsp load-balance-number 3 command gives LSP higher priority. If no LSP is available or the number of LSPs is less than 3, VPN uses CRLSP tunnels. The tunnels selected by this method are not fixed, complicating traffic planning. As a best practice, do not use this method.
If you configure both methods for a tunnel policy, the tunnel policy selects tunnels in the following steps:
1. If the destination address of a preferred tunnel identifies a peer PE, the tunnel policy uses the preferred tunnel to forward traffic destined for the peer PE without using any other tunnels.
2. If not, the tunnel policy selects tunnels as configured by the select-seq load-balance-number command.
Figure 39 MPLS VPN tunnel selection diagram
As shown in Figure 39, PE 1 and PE 2 have multiple tunnels in between and they are connected to multiple MPLS VPNs. You can control the paths for VPN traffic by using one of the following methods:
· Configure multiple tunnel policies, and specify a preferred tunnel for each policy by using the preferred-path command. Apply these policies to different MPLS VPNs to forward the traffic of each VPN over a specific tunnel.
· Configure one tunnel policy, and use the select-seq load-balance-number command to specify the tunnel selection order and the number of tunnels for load balancing. Apply the tunnel policy to MPLS VPNs to forward the traffic of every VPN over multiple tunnels.
The second method distributes traffic of a single VPN to multiple tunnels. The transmission delays on different tunnels can vary by a large amount. Therefore, the destination device or the upper layer application might take a great time to sequence the packets. As a best practice, do not use the second method.
Configuration procedure
To configure a tunnel policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a tunnel policy, and enter tunnel policy view. |
tunnel-policy tunnel-policy-name |
By default, no tunnel policy is configured. |
|
3. Configure tunnel selection methods. |
·
(Method 1) Specify a
preferred tunnel: ·
(Method 2) Configure the tunnel selection
order and the number of tunnels for load balancing: |
Configure one or both methods. By default, no preferred tunnel is specified. By default, only one tunnel is selected in LSP–CRLSP order. |
|
|
NOTE: For a VPN to exclusively use a tunnel, you can specify the tunnel as the preferred tunnel in a tunnel policy, and apply the policy only to that VPN. |
Displaying tunnel information
Execute display commands in any view.
|
Task |
Command |
|
Display tunnel information. |
display mpls tunnel { all | statistics | [ vpn-instance vpn-instance-name ] destination tunnel-ipv4-dest } |
Tunnel policy configuration examples
Preferred tunnel configuration example
Network requirements
PE 1 has multiple tunnels to reach PE 2: one MPLS TE tunnel on the interface Tunnel 1, and one LDP LSP tunnel.
Two MPLS VPN instances, vpna and vpnb, exist on PE 1. Configure PE 1 to use the MPLS TE tunnel to forward traffic for both VPNs.
Configuration procedure
1. Create a tunnel policy named preferredte1, and configure tunnel 1 as the preferred tunnel.
<PE1> system-view
[PE1] tunnel-policy preferredte1
[PE1-tunnel-policy-preferredte1] preferred-path tunnel 1
[PE1-tunnel-policy-preferredte1] quit
2. Configure MPLS VPN instances and apply the tunnel policy to the VPN instances:
# Create MPLS VPN instance vpna, and apply tunnel policy preferredte1 to it.
[PE1] ip vpn-instance vpna
[PE1-vpn-instance-vpna] route-distinguisher 100:1
[PE1-vpn-instance-vpna] vpn-target 100:1
[PE1-vpn-instance-vpna] tnl-policy preferredte1
[PE1-vpn-instance-vpna] quit
# Create MPLS VPN instance vpnb, and apply tunnel policy preferredte1 to it.
[PE1] ip vpn-instance vpnb
[PE1-vpn-instance-vpnb] route-distinguisher 100:2
[PE1-vpn-instance-vpnb] vpn-target 100:2
[PE1-vpn-instance-vpnb] tnl-policy preferredte1
Exclusive tunnel configuration example
Network requirements
PE 1 has multiple tunnels to reach PE 2: one MPLS TE tunnel on the interface Tunnel 1, and one LDP LSP tunnel.
One MPLS VPN vpna exists on PE 1. The VPN exclusively uses the MPLS TE tunnel.
Configuration procedure
1. Create tunnel policy preferredte1, and configure tunnel 1 as the preferred tunnel.
<PE1> system-view
[PE1] tunnel-policy preferredte1
[PE1-tunnel-policy-preferredte1] preferred-path tunnel 1
[PE1-tunnel-policy-preferredte1] quit
2. Create MPLS VPN instance vpna, and apply tunnel policy preferredte1 to it.
[PE1] ip vpn-instance vpna
[PE1-vpn-instance-vpna] route-distinguisher 100:1
[PE1-vpn-instance-vpna] vpn-target 100:1
[PE1-vpn-instance-vpna] tnl-policy preferredte1
[PE1-vpn-instance-vpna] quit
Tunnel selection order configuration example
Network requirements
PE 1 has multiple tunnels to reach PE 2: one MPLS TE tunnel on the interface Tunnel 1, and one LDP LSP tunnel.
Only one MPLS VPN, vpna, exists on PE 1. Select only one tunnel in LDP LSP-MPLS TE order for this VPN.
Configuration procedure
# Create tunnel policy seq-lsp-te.
<PE1> system-view
[PE1] tunnel-policy seq-lsp-te
# Specify the tunnel selection order, and set the number of tunnels for load balancing to 1—no load balancing.
[PE1-tunnel-policy-seq-lsp-te] select-seq lsp cr-lsp load-balance-number 1
[PE1-tunnel-policy-seq-lsp-te] quit
# Create MPLS VPN instance vpna, and apply tunnel policy seq-lsp-te to it.
[PE1] ip vpn-instance vpna
[PE1-vpn-instance-vpna] route-distinguisher 100:1
[PE1-vpn-instance-vpna] vpn-target 100:1
[PE1-vpn-instance-vpna] tnl-policy seq-lsp-te
Preferred tunnel and tunnel selection order configuration example
Network requirements
PE 1 has multiple tunnels to reach PE 2: two MPLS TE tunnels on the interface Tunnel 1 and Tunnel 3, and one LDP LSP tunnel.
PE 1 has multiple MPLS VPN instances: vpna, vpnb, vpnc, vpnd, and vpne. Table 11 shows the tunnel policy that PE 1 uses for each VPN instance.
Table 11 Tunnel policies used for VPN instances
|
VPN instance |
Tunnel policy |
|
vpna, vpnb |
Use MPLS TE tunnel Tunnel1 as the preferred tunnel. |
|
vpnc, vpnd |
Use MPLS TE tunnel Tunnel3 as the preferred tunnel. |
|
vpne |
Uses one tunnel selected in LDP LSP-MPLS TE order. |
Configuration procedure
1. Configure tunnel policies on PE 1:
# Create tunnel policy preferredte1, and configure tunnel 1 as the preferred tunnel.
<PE1> system-view
[PE1] tunnel-policy preferredte1
[PE1-tunnel-policy-preferredte1] preferred-path tunnel 1
[PE1-tunnel-policy-preferredte1] quit
# Create tunnel policy preferredte2, and configure tunnel 3 as the preferred tunnel.
[PE1] tunnel-policy preferredte2
[PE1-tunnel-policy-preferredte2] preferred-path tunnel 3
[PE1-tunnel-policy-preferredte2] quit
# Create tunnel policy select-lsp.
[PE1] tunnel-policy select-lsp
# Configure the policy to select only one tunnel in LDP LSP-MPLS TE order.
[PE1-tunnel-policy-select-lsp] select-seq lsp cr-lsp load-balance-number 1
[PE1-tunnel-policy-select-lsp] quit
2. Configure MPLS VPN instances and apply tunnel policies to the VPN instances:
# Create MPLS VPN instances vpna and vpnb, and apply tunnel policy preferredte1 to them.
[PE1] ip vpn-instance vpna
[PE1-vpn-instance-vpna] route-distinguisher 100:1
[PE1-vpn-instance-vpna] vpn-target 100:1
[PE1-vpn-instance-vpna] tnl-policy preferredte1
[PE1-vpn-instance-vpna] quit
[PE1] ip vpn-instance vpnb
[PE1-vpn-instance-vpnb] route-distinguisher 100:2
[PE1-vpn-instance-vpnb] vpn-target 100:2
[PE1-vpn-instance-vpnb] tnl-policy preferredte1
[PE1-vpn-instance-vpnb] quit
# Create MPLS VPN instances vpnc and vpnd, and apply tunnel policy preferredte2 to them.
[PE1] ip vpn-instance vpnc
[PE1-vpn-instance-vpnc] route-distinguisher 100:3
[PE1-vpn-instance-vpnc] vpn-target 100:3
[PE1-vpn-instance-vpnc] tnl-policy preferredte2
[PE1-vpn-instance-vpnc] quit
[PE1] ip vpn-instance vpnd
[PE1-vpn-instance-vpnd] route-distinguisher 100:4
[PE1-vpn-instance-vpnd] vpn-target 100:4
[PE1-vpn-instance-vpnd] tnl-policy preferredte2
[PE1-vpn-instance-vpnd] quit
# Create MPLS VPN instance vpne, and apply tunnel policy select-lsp to it.
[PE1] ip vpn-instance vpne
[PE1-vpn-instance-vpne] route-distinguisher 100:5
[PE1-vpn-instance-vpne] vpn-target 100:5
[PE1-vpn-instance-vpne] tnl-policy select-lsp
Configuring MPLS L3VPN
This chapter describes MPLS L3VPN configuration.
Overview
MPLS L3VPN is a L3VPN technology used to interconnect geographically dispersed VPN sites. MPLS L3VPN uses BGP to advertise VPN routes and uses MPLS to forward VPN packets over a service provider backbone.
MPLS L3VPN provides flexible networking modes, excellent scalability, and convenient support for MPLS TE.
Basic MPLS L3VPN architecture
Figure 40 Basic MPLS L3VPN architecture

A basic MPLS L3VPN architecture has the following types of devices:
· Customer edge device—A CE device resides on a customer network and has one or more interfaces directly connected to a service provider network. It does not support VPN or MPLS.
· Provider edge device—A PE device resides at the edge of a service provider network and connects to one or more CEs. All MPLS VPN services are processed on PEs.
· Provider device—A P device is a core device on a service provider network. It is not directly connected to any CE. A P device has only basic MPLS forwarding capability and does not handle VPN routing information.
MPLS L3VPN concepts
Site
A site has the following features:
· A site is a group of IP systems with IP connectivity that does not rely on any service provider network.
· The classification of a site depends on the topology relationship of the devices, rather than the geographical positions. However, the devices at a site are, in most cases, adjacent to each other geographically.
· The devices at a site can belong to multiple VPNs, which means that a site can belong to multiple VPNs.
· A site is connected to a provider network through one or more CEs. A site can contain multiple CEs, but a CE can belong to only one site.
Sites connected to the same provider network can be classified into different sets by policies. Only the sites in the same set can access each other through the provider network. Such a set is called a VPN.
VPN instance
VPN instances, also called virtual routing and forwarding (VRF) instances, implement route isolation, data independence, and data security for VPNs.
A VPN instance has the following components:
· A separate Label Forwarding Information Base (LFIB).
· An IP routing table.
· Interfaces bound to the VPN instance.
· VPN instance administration information, including route distinguishers (RDs), route targets (RTs), and route filtering policies.
To associate a site with a VPN instance, bind the VPN instance to the PE's interface connected to the site. A site can be associated with only one VPN instance, and different sites can associate with the same VPN instance. A VPN instance contains the VPN membership and routing rules of associated sites.
VPN-IPv4 address
Each VPN independently manages its address space. The address spaces of VPNs might overlap. For example, if both VPN 1 and VPN 2 use the addresses on subnet 10.110.10.0/24, address space overlapping occurs.
BGP cannot process overlapping VPN address spaces. For example, if both VPN 1 and VPN 2 use the subnet 10.110.10.0/24 and each advertise a route destined for the subnet, BGP selects only one of them. This results in the loss of the other route.
Multiprotocol BGP (MP-BGP) can solve this problem by advertising VPN-IPv4 addresses (also called VPNv4 addresses).
Figure 41 VPN-IPv4 address structure
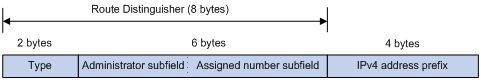
As shown in Figure 41, a VPN-IPv4 address consists of 12 bytes. The first eight bytes represent the RD, followed by a four-byte IPv4 prefix. The RD and the IPv4 prefix form a unique VPN-IPv4 prefix.
An RD can be in one of the following formats:
· When the Type field is 0, the Administrator subfield occupies two bytes, the Assigned number subfield occupies four bytes, and the RD format is 16-bit AS number:32-bit user-defined number. For example, 100:1.
· When the Type field is 1, the Administrator subfield occupies four bytes, the Assigned number subfield occupies two bytes, and the RD format is 32-bit IPv4 address:16-bit user-defined number. For example, 172.1.1.1:1.
· When the Type field is 2, the Administrator subfield occupies four bytes, the Assigned number subfield occupies two bytes, and the RD format is 32-bit AS number:16-bit user-defined number, where the minimum value of the AS number is 65536. For example, 65536:1.
To guarantee global uniqueness for a VPN-IPv4 address, do not set the Administrator subfield to any private AS number or private IP address.
Route target attribute
MPLS L3VPN uses route target community attributes to control the advertisement of VPN routing information. A VPN instance on a PE supports the following types of route target attributes:
· Export target attribute—A PE sets the export target attribute for VPN-IPv4 routes learned from directly connected sites before advertising them to other PEs.
· Import target attribute—A PE checks the export target attribute of VPN-IPv4 routes received from other PEs. If the export target attribute matches the import target attribute of a VPN instance, the PE adds the routes to the routing table of the VPN instance.
Route target attributes define which sites can receive VPN-IPv4 routes, and from which sites a PE can receive routes.
Like RDs, route target attributes can be one of the following formats:
· 16-bit AS number:32-bit user-defined number. For example, 100:1.
· 32-bit IPv4 address:16-bit user-defined number. For example, 172.1.1.1:1.
· 32-bit AS number:16-bit user-defined number, where the minimum value of the AS number is 65536. For example, 65536:1.
MP-BGP
MP-BGP supports multiple address families, including IPv4 multicast and VPN-IPv4 address families.
In MPLS L3VPN, MP-BGP advertises VPN-IPv4 routes for VPN sites between PEs.
MPLS L3VPN route advertisement
In a basic MPLS L3VPN, CEs and PEs are responsible for advertising VPN routing information. P routers maintain only the routes within the backbone. A PE maintains only routing information for directly connected VPNs, rather than for all VPNs.
VPN routing information is advertised from the local CE to the remote CE by using the following process:
1. From the local CE to the ingress PE:
The CE advertises standard IPv4 routing information to the ingress PE over a static route, RIP route, OSPF route, IS-IS route, EBGP route, or IBGP route.
2. From the ingress PE to the egress PE:
The ingress PE performs the following operations:
a. Adds RD and route target attributes to these standard IPv4 routes to create VPN-IPv4 routes.
b. Saves them to the routing table of the VPN instance created for the CE.
c. Advertises the VPN-IPv4 routes to the egress PE through MP-BGP.
3. From the egress PE to the remote CE:
After receiving the VPN-IPv4 routes, the egress PE performs the following operations:
a. Compares the routes' export target attributes with the local import target attributes.
b. Adds the routes to the routing table of the VPN instance if the export and local import target attributes match each other.
c. Restores the VPN-IPv4 routes to the original IPv4 routes.
d. Advertises those routes to the connected CE over a static route, RIP route, OSPF route, IS-IS route, EBGP route, or IBGP route.
MPLS L3VPN packet forwarding
In a basic MPLS L3VPN (within a single AS), a PE adds the following information into VPN packets:
· Outer tag—Identifies the public tunnel from the local PE to the remote PE. The public tunnel can be an LSP, an MPLS TE tunnel. Based on the outer tag, a VPN packet can be forwarded along the public tunnel to the remote PE. For a GRE public tunnel, the outer tag is the GRE encapsulation. For an LSP or MPLS TE tunnel, the outer tag is an MPLS label.
· Inner label—Identifies the remote VPN site. The remote PE uses the inner label to forward packets to the target VPN site. MP-BGP advertises inner labels for VPN routes among PEs.
Figure 42 VPN packet forwarding
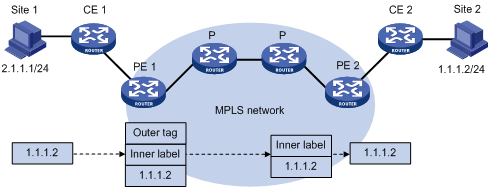
As shown in Figure 42, a VPN packet is forwarded from Site 1 to Site 2 by using the following process:
1. Site 1 sends an IP packet with the destination address 1.1.1.2. CE 1 transmits the packet to PE 1.
2. PE 1 performs the following operations:
a. Finds the matching VPN route based on the inbound interface and destination address of the packet.
b. Labels the packet with both the inner label and the outer tag.
c. Forwards the packet to the public tunnel.
3. P devices forward the packet to PE 2 by the outer tag.
? If the outer tag is an MPLS label, the label is removed from the packet at the penultimate hop.
? If the outer tag is GRE encapsulation, PE 2 removes the GRE encapsulation.
4. PE 2 performs the following operations:
a. Uses the inner label to find the matching VPN instance to which the destination address of the packet belongs.
b. Looks up the routing table of the VPN instance for the output interface.
c. Removes the inner label and forwards the packet out of the interface to CE 2.
5. CE 2 transmits the packet to the destination through IP forwarding.
When two sites of a VPN are connected to the same PE, the PE directly forwards packets between the two sites through the VPN routing table without adding any tag or label.
For more information about GRE, see Layer 3—IP Services Configuration Guide.
MPLS L3VPN networking schemes
In MPLS L3VPNs, route target attributes are used to control the advertisement and reception of VPN routes between sites. They work independently and can be configured with multiple values to support flexible VPN access control and implement multiple types of VPN networking schemes.
Basic VPN networking scheme
In the simplest case, all users in a VPN form a closed user group. They can forward traffic to each other but cannot communicate with any user outside the VPN.
For the basic VPN networking scheme, you must assign a route target to each VPN for identifying the export target attribute and import target attribute of the VPN. Moreover, this route target cannot be used by any other VPNs.
Figure 43 Network diagram for basic VPN networking scheme
As shown in Figure 43, the route target for VPN 1 is 100:1, while that for VPN 2 is 200:1. The two VPN 1 sites can communicate with each other, and the two VPN 2 sites can communicate with each other. However, the VPN 1 sites cannot communicate with the VPN 2 sites.
Hub and spoke networking scheme
The hub and spoke networking scheme is suitable for a VPN where all users must communicate with each other through an access control device.
In a hub and spoke network as shown in Figure 44, configure route targets as follows:
· On spoke PEs (PEs connected to spoke sites), set the export target to Spoke and the import target to Hub.
· On the hub PE (PE connected to the hub site), use two interfaces that each belong to a different VPN instance to connect the hub CE. One VPN instance receives routes from spoke PEs and has the import target set to Spoke. The other VPN instance advertises routes to spoke PEs and has the export target set to Hub.
These route targets rules produce the following results:
· The hub PE can receive all VPN-IPv4 routes from spoke PEs.
· All spoke PEs can receive VPN-IPv4 routes advertised by the hub PE.
· The hub PE advertises the routes learned from a spoke PE to the other spoke PEs so the spoke sites can communicate with each other through the hub site.
· The import target attribute of a spoke PE is different from the export target attribute of any other spoke PE. Therefore, any two spoke PEs cannot directly advertise VPN-IPv4 routes to each other or directly access each other.
Figure 44 Network diagram for hub and spoke network
A route in Site 1 is advertised to Site 2 by using the following process:
1. Spoke-CE 1 advertises a route in Site 1 to Spoke-PE 1.
2. Spoke-PE 1 changes the route to a VPN-IPv4 route and advertises the VPN-IPv4 route to Hub-PE through MP-BGP.
3. Hub-PE adds the VPN-IPv4 route into the routing table of VPN 1-in, changes it to the original IPv4 route, and advertises the IPv4 route to Hub-CE.
4. Hub-CE advertises the IPv4 route back to Hub-PE.
5. Hub-PE adds the IPv4 route to the routing table of VPN 1-out, changes it to a VPN-IPv4 route, and advertises the VPN-IPv4 route to Spoke-PE 2 through MP-BGP.
6. Spoke-PE 2 changes the VPN-IPv4 route to the original IPv4 route, and advertises the IPv4 route to Site 2.
After spoke sites exchange routes through the hub site, they can communicate with each other through the hub site.
Extranet networking scheme
The extranet networking scheme allows specific resources in a VPN to be accessed by users not in the VPN.
In this networking scheme, if a VPN instance needs to access a shared site, the export target attribute and the import target attribute of the VPN instance must be contained in the import target attribute and the export target attribute of the VPN instance of the shared site, respectively.
Figure 45 Network diagram for extranet networking scheme
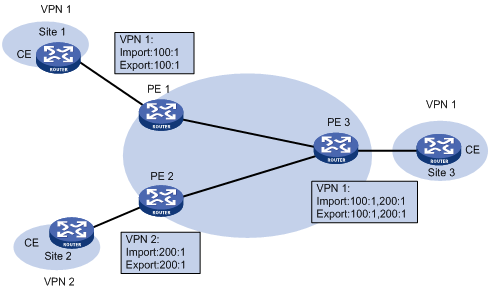
As shown in Figure 45, route targets configured on PEs produce the following results:
· PE 3 can receive VPN-IPv4 routes from PE 1 and PE 2.
· PE 1 and PE 2 can receive VPN-IPv4 routes advertised by PE 3.
· Site 1 and Site 3 of VPN 1 can communicate with each other, and Site 2 of VPN 2 and Site 3 of VPN 1 can communicate with each other.
· PE 3 advertises neither the VPN-IPv4 routes received from PE 1 to PE 2 nor the VPN-IPv4 routes received from PE 2 to PE 1 (routes learned from an IBGP neighbor are not advertised to any other IBGP neighbor). Therefore, Site 1 of VPN 1 and Site 2 of VPN 2 cannot communicate with each other.
Inter-AS VPN
In an inter-AS VPN networking scenario, multiple sites of a VPN are connected to multiple ISPs in different ASs, or to multiple ASs of an ISP.
The following inter-AS VPN solutions are available:
· VRF-to-VRF connections between ASBRs—This solution is also called inter-AS option A.
· EBGP redistribution of labeled VPN-IPv4 routes between ASBRs—ASBRs advertise VPN-IPv4 routes to each other through MP-EBGP. This solution is also called inter-AS option B.
· Multihop EBGP redistribution of labeled VPN-IPv4 routes between PE routers—PEs advertise VPN-IPv4 routes to each other through MP-EBGP. This solution is also called inter-AS option C.
Inter-AS option A
In this solution, PEs of two ASs are directly connected, and each PE is also the ASBR of its AS. Each PE treats the other as a CE and advertises unlabeled IPv4 unicast routes through EBGP. The PEs associate a VPN instance with at least one interface.
Figure 46 Network diagram for inter-AS option A
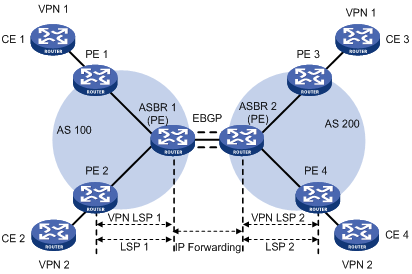
As shown in Figure 46, VPN 1 routes are advertised from CE 1 to CE 3 by using the following process:
1. PE 1 advertises the VPN routes learned from CE 1 to ASBR 1 through MP-IBGP.
2. ASBR 1 performs the following operations:
a. Adds the routes to the routing table of the VPN instance whose import target attribute matches the export target attribute of the routes.
b. Advertises the routes as IPv4 unicast routes to its CE (ASBR 2) through EBGP.
3. ASBR 2 adds the IPv4 unicast routes to the routing table of the VPN instance bound to the receiving interface, and advertises the routes to PE 3 through MP-IBGP.
4. PE 3 advertises the received routes to CE 3.
Packets forwarded within an AS are VPN packets that carry two labels. Packets forwarded between ASBRs are common IP packets.
Inter-AS option A is easy to carry out because no special configuration is required on the PEs acting as the ASBRs.
However, it has limited scalability because the PEs acting as the ASBRs must manage all the VPN routes and create VPN instances on a per-VPN basis. This leads to excessive VPN-IPv4 routes on the PEs. Associateing a separate interface with each VPN also requires additional system resources.
Inter-AS option B
In this solution, two ASBRs use MP-EBGP to exchange VPN-IPv4 routes that they obtain from the PEs in their respective ASs.
Figure 47 Network diagram for inter-AS option B

As shown in Figure 47, VPN 1 routes are advertised from CE 1 to CE 3 by using the following process:
1. PE 1 advertises the VPN routes learned from CE 1 to ASBR 1 through MP-IBGP.
Assume that the inner label assigned by PE 1 to the routes is L1.
2. ASBR 1 advertises the VPN-IPv4 routes to ASBR 2 through MP-IBGP.
Before advertising the routes, ASBR 1 modifies the next hop as its own address, assigns a new inner label (L2) to the routes, and associates L1 with L2.
3. ASBR 2 advertises the VPN-IPv4 routes to PE 3 through MP-IBGP.
Before advertising the routes, ASBR 2 modifies the next hop as its own address, assigns a new inner label (L3) to the routes, and associates L2 with L3.
4. PE 3 advertises the received routes to CE 3.
A packet is forwarded from CE 3 to CE 1 by using the following process:
1. PE 3 encapsulates the received packet with two labels, and forwards the encapsulated packet to ASBR 2.
The two labels are the inner label for the VPN (L3) and the outer tag for the public tunnel from PE 3 to ASBR 2.
2. ASBR 2 removes the outer tag, replaces L3 with L2, and forwards the packet to ASBR 1.
Packets between ASBR 1 and ASBR 2 carry only one inner label.
3. ASBR 1 replaces L2 with L1, adds the outer tag of the public tunnel from ASBR 1 to PE 1, and forwards the packet to PE 1.
4. PE 1 removes the outer tag and inner label and forwards the packet to CE 1.
In this solution, ASBRs must receive all inter-AS VPN routes. Therefore, ASBRs cannot filter incoming VPN-IPv4 routes by route targets.
Inter-AS option B has better scalability than option A. However, it requires that ASBRs maintain and advertise VPN routes.
Inter-AS option C
The inter-AS option A and option B solutions require that the ASBRs maintain and advertise VPN-IPv4 routes. When every AS needs to exchange a great amount of VPN routes, the ASBRs might become bottlenecks, which hinders network extension. Inter-AS option C has better scalability because it makes PEs directly exchange VPN-IPv4 routes.
In this solution, PEs exchange VPN-IPv4 routes over a multihop MP-EBGP session. Each PE must have a route to the peer PE and a label for the route so that the inter-AS public tunnel between the PEs can be set up. Inter-AS option C sets up a public tunnel by using the following methods:
· A label distribution protocol within the AS, for example, LDP.
· Labeled IPv4 unicast route advertisement by ASBRs through BGP.
Labeled IPv4 unicast route advertisement refers to the process of assigning MPLS labels to IPv4 unicast routes and advertising the IPv4 unicast routes and their labels.
Figure 48 Network diagram for inter-AS option C
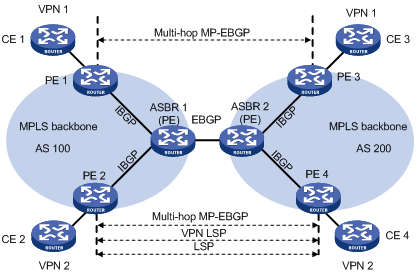
As shown in Figure 48, VPN 1 routes are advertised from CE 1 to CE 3 by using the following process:
1. PE 1 advertises the VPN routes learned from CE 1 as VPN-IPv4 routes to PE 3 through multihop MP-EBGP.
Assume that the inner label assigned by PE 1 for the routes is Lx.
2. PE 3 advertises the received routes to CE 3.
Setting up an inter-AS public tunnel is difficult in this solution. A public tunnel, for example, the one from PE 3 to PE 1, is set up by using the following process:
1. Within AS 100, the public tunnel from ASBR 1 to PE 1 is set up by using a label distribution protocol, for example, LDP.
Assume that the outgoing label for the public tunnel on ASBR 1 is L1.
2. ASBR 1 advertises labeled IPv4 unicast routes to ASBR 2 through EBGP to set up the public tunnel from ASBR 2 to ASBR 1.
ASBR 1 assigns a label (L2) to the route destined for PE 1, and advertises the route and its label (L2) to ASBR 2. The next hop for the route is ASBR 1. The incoming label for the public tunnel on ASBR 1 is L2.
3. ASBR 2 advertises labeled IPv4 unicast routes to PE 3 through IBGP to set up the public tunnel from PE 3 directly to ASBR 2.
ASBR 2 assigns a label (L3) to the route destined for PE 1, and advertises the route and its label (L3) to PE 3. The next hop for the route is ASBR 2. The incoming label for the public tunnel on ASBR 2 is L3, and the outgoing label is L2.
4. MPLS packets cannot be forwarded directly from PE 3 to ASBR 2. Therefore, another public tunnel from PE 3 to ASBR 2 is required to be set up hop by hop through a label distribution protocol, for example, LDP.
Assume that the outgoing label for the public tunnel on PE 3 is Lv.
After route advertisement and public tunnel setup, a packet is forwarded from CE 3 to CE 1 by using the following process:
1. PE 3 performs the following routing table lookups for the packet:
a. Finds a matching route with next hop PE 1 and inner label Lx, and encapsulates the packet with label Lx.
b. Finds the route to PE 1 with next hop ASBR 2 and label L3, and encapsulates the packet with label L3 as the outer label.
c. Finds the route to ASBR 2 with outgoing label Lv, and encapsulates the packet with label Lv as the outmost label.
2. AS 200 transmits the packet to ASBR 2 by the outmost label.
3. ASBR 2 removes the outmost label, replaces L3 with L2, and forwards the packet to ASBR 1.
4. ASBR 1 replaces L2 with L1, and forwards the packet.
5. AS 100 transmits the packet to PE 1 by the outer label.
6. PE 1 removes the outer label, and forwards the packet to CE 1 according to the inner label Lx.
As shown in Figure 49, to improve scalability, you can specify an RR in each AS to exchange VPN-IPv4 routes with PEs in the same AS. The RR in each AS maintains all VPN-IPv4 routes. The RRs in two ASs establish a multihop MP-EBGP session to advertise VPN-IPv4 routes.
Figure 49 Network diagram for inter-AS option C using RRs

Carrier's carrier
If a customer of the MPLS L3VPN service provider is also a service provider:
· The MPLS L3VPN service provider is called the provider carrier or the Level 1 carrier.
· The customer is called the customer carrier or the Level 2 carrier.
This networking model is referred to as carrier's carrier.
The PEs of the Level 2 carrier directly exchange customer networks over a BGP session. The Level 1 carrier only learns the backbone networks of the Level 2 carrier, without learning customer networks.
For packets between customer networks to travel through the Level 1 carrier, the PE of the Level 1 carrier and the CE of the Level 2 carrier must assign labels to the backbone networks of the Level 2 carrier. The CE of the Level 2 carrier is a PE within the Level 2 carrier network.
Follow these guidelines to assign labels:
· If the PE and the CE are in a same AS, you must configure IGP and LDP between them. If they are in different ASs, you must configure MP-EBGP to assign labels to IPv4 unicast routes exchanged between them.
· You must enable MPLS on the CE of the Level 2 carrier regardless of whether the PE and CE are in the same AS.
A Level 2 carrier can be an ordinary ISP or an MPLS L3VPN service provider.
As shown in Figure 50, when the customer carrier is an ordinary ISP, its PEs and CEs run IGP to communicate with each other. The PEs do not need to run MPLS. PE 3 and PE 4 exchange customer network routes (IPv4 unicast routes) through an IBGP session.
Figure 50 Scenario where the Level 2 carrier is an ISP
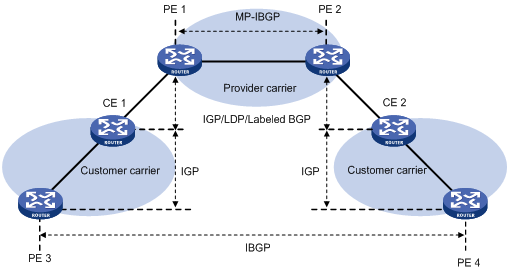
As shown in Figure 51, when the customer carrier is an MPLS L3VPN service provider, its PEs and CEs must run IGP and LDP to communicate with each other. PE 3 and PE 4 exchange customer network routes (VPN-IPv4 routes) through an MP-IBGP session.
Figure 51 Scenario where the Level 2 carrier is an MPLS L3VPN service provider

|
|
NOTE: As a best practice, establish equal cost LSPs between the Level 1 carrier and the Level 2 carrier if equal cost routes exist between them. |
Nested VPN
The nested VPN technology exchanges VPNv4 routes between PEs and CEs of the ISP MPLS L3VPN and allows a customer to manage its own internal VPNs. Figure 52 shows a nested VPN network. On the service provider's MPLS VPN network, there is a customer VPN named VPN A. The customer VPN contains two sub-VPNs, VPN A-1 and VPN A-2.
The service provider PEs consider the customer's network as a common VPN user and do not join any sub-VPNs. The service provider CE devices (CE 1 and CE 2) exchange VPNv4 routes including sub-VPN routing information with the service provider PEs, which implements the propagation of the sub-VPN routing information throughout the customer network.
The nested VPN technology supports both symmetric networking and asymmetric networking. Sites of the same VPN can have the same number or different numbers of internal VPNs. Nested VPN also supports multiple-level nesting of internal VPNs.
Figure 52 Network diagram for nested VPN
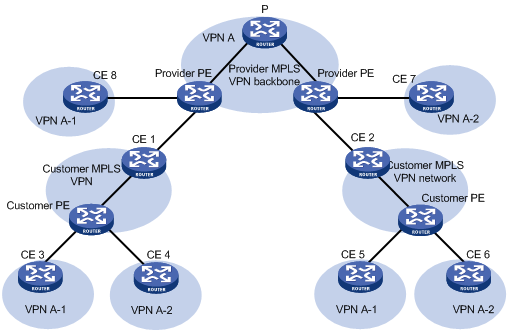
Propagation of routing information
In a nested VPN network, routing information is propagated by using the following process:
1. After receiving VPN routes from customer CEs, a customer PE advertises VPN-IPv4 routes to the provider CE through MP-BGP.
2. The provider CE advertises the VPN-IPv4 routes to the provider PE through MP-BGP.
3. After receiving a VPN-IPv4 route, the provider PE keeps the customer's internal VPN information, and appends the customer's MPLS VPN attributes on the service provider network. It replaces the RD of the VPN-IPv4 route with the RD of the customer's MPLS VPN on the service provider network. It also adds the export route-target (ERT) attribute of the customer's MPLS VPN on the service provider network to the extended community attribute list of the route. The internal VPN information for the customer is maintained on the provider PE.
4. The provider PE advertises VPN-IPv4 routes carrying the comprehensive VPN information to the other PEs of the service provider.
5. After another provider PE receives the VPN-IPv4 routes, it matches the VPN-IPv4 routes to the import targets of its local VPNs. Each local VPN accepts routes of its own and advertises them to provider CEs. If a provider CE (such as CE 7 and CE 8 in Figure 52) is connected to a provider PE through an IPv4 connection, the PE advertises IPv4 routes to the CE. If it is a VPN-IPv4 connection (a customer MPLS VPN network), the PE advertises VPN-IPv4 routes to the CE.
6. After receiving VPN-IPv4 routes from the provider CE, a customer PE matches those routes to local import targets. Each customer VPN accepts only its own routes and advertises them to connected customer CEs (such as CE 3, CE 4, CE 5, and CE 6 in Figure 52).
HoVPN
Hierarchy of VPN (HoVPN), also called Hierarchy of PE (HoPE), prevents PEs from being bottlenecks and is applicable to large-scale VPN deployment.
HoVPN divides PEs into underlayer PEs (UPEs) or user-end PEs, and superstratum PEs (SPEs) or service provider-end PEs. UPEs and SPEs have different functions and comprise a hierarchical PE. The HoPE and common PEs can coexist in an MPLS network.
Figure 53 Basic architecture of HoVPN
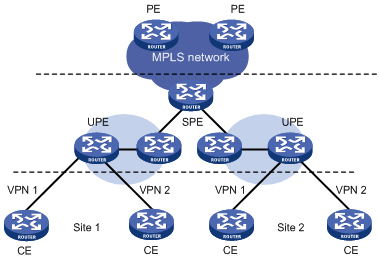
As shown in Figure 53, UPEs and SPEs play the following different roles:
· A UPE is directly connected to CEs. It provides user access. It maintains the routes of directly connected VPN sites. It does not maintain the routes of the remote sites in the VPN, or it only maintains their summary routes. A UPE assigns inner labels to the routes of its directly connected sites, and advertises the labels along with VPN routes to the SPE through MP-BGP. A UPE features high access capability, small routing table capacity, and low forwarding performance.
· An SPE is connected to UPEs and is in the internal network. It manages and advertises VPN routes. It maintains all the routes of the VPNs connected through UPEs, including the routes of both the local and remote sites. An SPE advertises routes along with labels to UPEs, including the default routes of VPN instances or summary routes and the routes permitted by the routing policy. By using routing policies, you can control which sites in a VPN can communicate with each other. An SPE features large routing table capacity, high forwarding performance, and fewer interface resources.
Either MP-IBGP or MP-EBGP can run between SPE and UPE. When MP-IBGP runs between SPE and UPEs, the SPE acts as the RR of multiple UPEs to reflect routes between UPEs.
HoVPN supports HoPE recursion:
· An HoPE can act as a UPE to form a new HoPE with an SPE.
· An HoPE can act as an SPE to form a new HoPE with multiple UPEs.
HoVPN supports multilevel recursion. In HoPE recursion, the concepts of SPE and UPE are relative. A PE might be the SPE of its underlayer PEs and a UPE of its SPE at the same time.
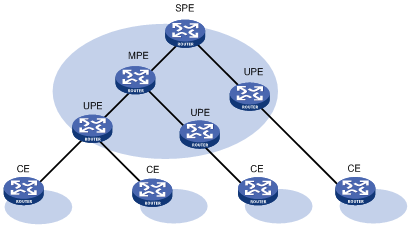
Figure 54 shows a three-level HoPE. The PE in the middle is called the middle-level PE (MPE). MP-BGP runs between SPE and MPE, and between MPE and UPE.
MP-BGP advertises the following routes:
· All the VPN routes of UPEs to the SPEs.
· The default routes of the VPN instance of the SPEs or the VPN routes permitted by the routing policies to the UPEs.
The SPE maintains the VPN routes of all sites in the HoVPN. Each UPE maintains only VPN routes of its directly connected sites. An MPE has fewer routes than the SPE but has more routes than a UPE.
OSPF VPN extension
This section describes the OSPF VPN extension. For more information about OSPF, see Layer 3—IP Routing Configuration Guide.
OSPF for VPNs on a PE
If OSPF runs between a CE and a PE to exchange VPN routes, the PE must support multiple OSPF instances to create independent routing tables for VPN instances. Each OSPF process is bound to a VPN instance. Routes learned by an OSPF process are added into the routing table of the bound VPN instance.
OSPF area configuration between a PE and a CE
The OSPF area between a PE and a CE can be either a non-backbone area or a backbone area.
In the OSPF VPN extension application, the MPLS VPN backbone is considered the backbone area (area 0). The area 0 of each VPN site must be connected to the MPLS VPN backbone (physically connected or logically connected through a virtual link) because OSPF requires that the backbone area be contiguous.
BGP/OSPF interaction
If OSPF runs between PEs and CEs, each PE redistributes BGP routes to OSPF and advertises the routes to CEs through OSPF. OSPF considers the routes redistributed from BGP as external routes but the OSPF routes actually might belong to the same OSPF domain. This problem can be resolved by configuring the same domain ID for sites in an OSPF domain.
Figure 55 Network diagram for BGP/OSPF interaction

As shown in Figure 55, CE 11, CE 21, and CE 22 belong to the same VPN and the same OSPF domain.
Before a domain ID is configured, VPN 1 routes are advertised from CE 11 to CE 21 and CE 22 by using the following process:
1. PE 1 redistributes OSPF routes from CE 11 into BGP, and advertises the VPN routes to PE 2 through BGP.
2. PE 2 redistributes the BGP routes to OSPF, and advertises them to CE 21 and CE 22 in AS External LSAs (Type 5) or NSSA External LSAs (Type 7).
After a domain ID is configured, VPN 1 routes are advertised from CE 11 to CE 21 and CE 22 by using the following process:
1. PE 1 redistributes OSPF routes into BGP, adds the domain ID to the redistributed BGP VPNv4 routes as a BGP extended community attribute, and advertises the routes to PE 2.
2. PE 2 compares the domain ID in the received routes with the locally configured domain ID. If they are the same and the received routes are intra-area or inter-area routes, OSPF advertises these routes in Network Summary LSAs (Type 3). Otherwise, OSPF advertises these routes in AS External LSAs (Type 5) or NSSA External LSAs (Type 7).
Routing loop avoidance
Figure 56 Network diagram for routing loop avoidance
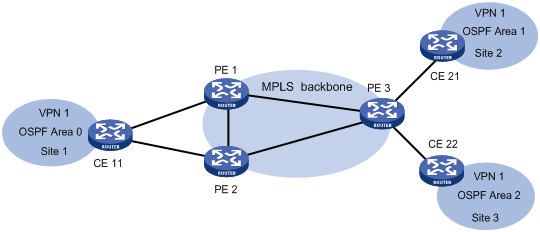
As shown in Figure 56, Site 1 is connected to two PEs. When a PE advertises VPN routes learned from MP-BGP to Site 1 through OSPF, the routes might be received by the other PE. This results in a routing loop.
OSPF VPN extension uses the following tags to avoid routing loops:
· DN bit (for Type 3 LSAs)—When a PE redistributes BGP routes into OSPF and creates Type 3 LSAs, it sets the DN bit for the LSAs. When receiving the Type 3 LSAs advertised by CE 11, the other PE ignores the LSAs whose DN bit is set to avoid routing loops.
· Route tag (for Type 5 or 7 LSAs)—The two PEs use the same route tag. When a PE redistributes BGP routes into OSPF and creates Type 5 or 7 LSAs, it adds the route tag to the LSAs. When receiving the Type 5 or 7 LSAs advertised by CE 11, the other PE compares the route tag in the LSAs against the local route tag. If they are the same, the PE ignores the LSAs to avoid routing loops.
OSPF sham link
As shown in Figure 57, two routes exist between site 1 and site 2 of VPN 1:
· A route connected through PEs—Inter-area route or external route.
? Inter-area route—The route is an inter-area route if the two PEs have the same domain ID configured for the OSPF process of VPN 1.
? External route—The route is an external route if the two PEs have no or different domain IDs configured for the OSPF process of VPN 1.
· A route directly connected through CEs—Intra-area route, which is called a backdoor link.
The inter-area route priority is lower than the intra-area route priority. To use the inter-area route, you can establish a sham link between the two PEs to change the inter-area route to an intra-area route. VPN traffic are forwarded over the sham link through metric adjustment.
Figure 57 Network diagram for sham link
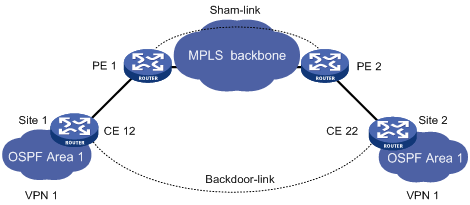
A sham link is considered a virtual point-to-point link within a VPN and is advertised in a Type 1 LSA. It is identified by the source IP address and destination IP address that are the local PE address and the remote PE address in the VPN address space. Typically, the source and destination addresses are loopback interface addresses with a 32-bit mask.
To add a route to the destination IP address of a sham link to a VPN instance, the remote PE must advertise the source IP address of the sham link as a VPN-IPv4 address through MP-BGP. To avoid routing loops, a PE does not advertise the sham link's destination address.
BGP AS number substitution
BGP detects routing loops by examining AS numbers. If EBGP runs between PE and CE, you must assign different AS numbers to geographically different sites to ensure correct transmission of routing information.
The BGP AS number substitution function allows physically dispersed CEs to use the same AS number. The function is a BGP outbound policy and affects routes to be advertised.
With the BGP AS number substitution function, when a PE advertises a route to a CE, if an AS number identical to that of the CE exists in the AS_PATH of the route, the PE replaces it with its own AS number.
After you enable the BGP AS number substitution function, the PE performs BGP AS number substitution for all routes and re-advertises them to connected CEs in the peer group.
Figure 58 Application of BGP AS number substitution
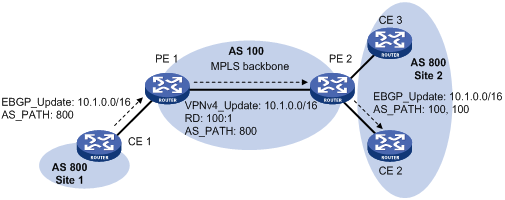
As shown in Figure 58, both Site and Site 2 use the AS number 800. AS number substitution is enabled on PE 2 for CE 2. Before advertising updates received from CE 1 to CE 2, PE 2 substitutes its own AS number 100 for the AS number 800. In this way, CE 2 can correctly receive the routing information from CE 1.
However, the AS number substitution function also introduces a routing loop in Site 2 because route updates originated from CE 3 can be advertised back to Site 2 through PE 2 and CE 2. To remove the routing loop, you can configure a routing policy on PE 2 to add the SoO attribute to route updates received from CE 2 and CE 3 so that PE 2 does not advertise route updates from CE 3 to CE 2.
|
|
NOTE: The device does not support adding the SoO attribute to routes. |
MPLS L3VPN FRR
MPLS L3VPN Fast Reroute (FRR) is applicable to a dual-homed scenario, as shown in Figure 59. By using BFD to detect the primary link, FRR enables a PE router to use the backup link when the primary link fails. The PE router then selects a new optimal route, and uses the new optimal route to forward traffic.
MPLS L3VPN FRR supports the following types of backup:
· VPNv4 route backup for a VPNv4 route.
· VPNv4 route backup for an IPv4 route.
· IPv4 route backup for a VPNv4 route.
VPNv4 route backup for a VPNv4 route
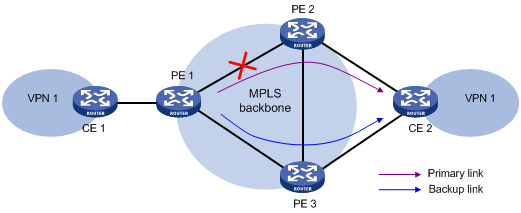
As show in Figure 59, configure FRR on the ingress node PE 1, and specify the backup next hop for VPN 1 as PE 3. When PE 1 receives a VPNv4 route to CE 2 from both PE 2 and PE 3, it uses the route from PE 2 as the primary link, and the route from PE 3 as the backup link.
Configure BFD for LSPs or MPLS TE tunnels on PE 1 to detect the connectivity of the public tunnel from PE 1 to PE 2. When the tunnel PE 1—PE 2 operates correctly, traffic from CE 1 to CE 2 goes through the path CE 1—PE 1—PE 2—CE 2. When the tunnel fails, the traffic goes through the path CE 1—PE 1—PE 3—CE 2.
In this scenario, PE 1 is responsible for primary link detection and traffic switchover.
For more information about BFD for LSPs or MPLS TE tunnels, see "Configuring MPLS OAM."
VPNv4 route backup for an IPv4 route
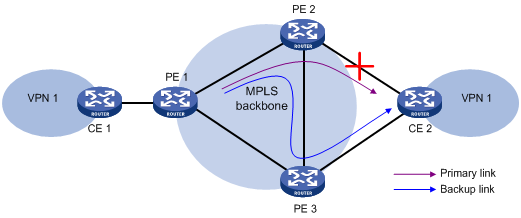
As shown in Figure 60, configure FRR on the egress node PE 2, and specify the backup next hop for VPN 1 as PE 3. When PE 2 receives an IPv4 route from CE 2 and a VPNv4 route from PE 3 (both routes are destined for VPN 1 connected to CE 2), PE 2 uses the IPv4 route as the primary link, and the VPNv4 route as the backup link.
PE 2 uses echo-mode BFD to detect the connectivity of the link from PE 2 to CE 2. When the link operates correctly, traffic from CE 1 to CE 2 goes through the path CE 1—PE 1—PE 2—CE 2. When the link fails, PE 2 switches traffic to the link PE 2—PE 3—CE 2, and traffic from CE 1 to CE 2 goes through the path CE 1—PE 1—PE 2—PE 3—CE 2. This avoids traffic interruption before route convergence completes (switching to the link CE 1—PE 1—PE 3—CE 2).
In this scenario, PE 2 is responsible for primary link detection and traffic switchover.
IPv4 route backup for a VPNv4 route

As shown in Figure 61, configure FRR on the egress node PE 2, and specify the backup next hop for VPN 1 as CE 2. When PE 2 receives an IPv4 route from CE 2 and a VPNv4 route from PE 3 (both routes are destined for VPN 1 connected to CE 2), PE 2 uses the VPNv4 route as the primary link, and the IPv4 route as the backup link.
Configure BFD for LSPs or MPLS TE tunnels on PE 2 to detect the connectivity of the public tunnel from PE 2 to PE 3. When the tunnel operates correctly, traffic from CE 1 to CE 2 goes through the path CE 1—PE 1—PE 2—PE 3—CE 2. When the tunnel fails, the traffic goes through the path CE 1—PE 1—PE 2—CE 2.
In this scenario, PE 2 is responsible for primary link detection and traffic switchover.
Protocols and standards
· RFC 3107, Carrying Label Information in BGP-4
· RFC 4360, BGP Extended Communities Attribute
· RFC 4364, BGP/MPLS IP Virtual Private Networks (VPNs)
· RFC 4577, OSPF as the Provider/Customer Edge Protocol for BGP/MPLS IP Virtual Private Networks (VPNs)
Feature and software version compatibility
The MPLS L3VPN feature is available in Release 1138P01 and later versions.
MPLS L3VPN configuration task list
|
Tasks at a glance |
|
(Required.) Configuring basic MPLS L3VPN |
|
(Optional.) Configuring inter-AS VPN |
|
(Optional.) Configuring nested VPN |
|
(Optional.) Configuring HoVPN |
|
(Optional.) Configuring an OSPF sham link |
|
(Optional.) Specifying the VPN label processing mode on the egress PE |
|
(Optional.) Configuring BGP AS number substitution |
|
(Optional.) Configuring MPLS L3VPN FRR |
|
(Optional.) Enabling SNMP notifications for MPLS L3VPN |
|
(Optional.) Enabling logging for BGP route flapping |
Configuring basic MPLS L3VPN
|
Tasks at a glance |
|
|
1. (Required.) Creating a VPN instance 2. (Required.) Associating a VPN instance with an interface 3. (Optional.) Configuring route related attributes for a VPN instance |
|
|
(Required.) Configuring routing between a PE and a CE |
|
|
(Required.) Configuring routing between PEs |
|
|
(Optional.) Configuring BGP VPNv4 route control |
Configuration prerequisites
Before you configure basic MPLS L3VPN, perform the following tasks:
· Configure an IGP for the MPLS backbone (on the PEs and Ps) to achieve IP connectivity.
· Configure basic MPLS for the MPLS backbone.
· Configure MPLS LDP for the MPLS backbone so that LDP LSPs can be established.
Configuring VPN instances
VPN instances isolate VPN routes from public network routes and routes among VPNs. This feature allows VPN instances to be used in network scenarios besides MPLS L3VPNs.
All VPN instance configurations are performed on PEs.
Creating a VPN instance
A VPN instance is a collection of the VPN membership and routing rules of its associated site. A VPN instance might correspond to more than one VPN.
Before you create VPN instances, you must reserve local VLAN interface resources by executing the reserve-vlan-interface command. The device uses the reserved resources to create VPN instances. For more information about local VLAN interface resource reservation, see Layer 2—LAN Switching Configuration Guide.
To create and configure a VPN instance:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a VPN instance and enter VPN instance view. |
ip vpn-instance vpn-instance-name |
By default, no VPN instance is created. |
|
3. Configure an RD for the VPN instance. |
route-distinguisher route-distinguisher |
By default, no RD is specified for a VPN instance. |
|
4. (Optional.) Configure a description for the VPN instance. |
description text |
By default, no description is configured for a VPN instance. |
|
5. (Optional.) Configure a VPN ID for the VPN instance. |
vpn-id vpn-id |
By default, no VPN ID is configured for a VPN instance. |
Associating a VPN instance with an interface
After creating and configuring a VPN instance, associate the VPN instance with the interface connected to the CE.
To associate a VPN instance with an interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Associate a VPN instance with the interface. |
ip binding vpn-instance vpn-instance-name |
By default, no VPN instance is associated with an interface. The ip binding vpn-instance command deletes the IP address of the current interface. You must re-configure an IP address for the interface after configuring the command. |
Configuring route related attributes for a VPN instance
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VPN instance view or IPv4 VPN view |
·
Enter VPN instance view: · Enter IPv4 VPN view: a. ip vpn-instance vpn-instance-name b. address-family ipv4 |
IPv4 VPN prefers the configurations in IPv4 VPN view over the configurations in VPN instance view. |
|
3. Configure route targets. |
vpn-target vpn-target&<1-8> [ both | export-extcommunity | import-extcommunity ] |
By default, no route targets are configured. |
|
4. Set the maximum number of active routes allowed. |
routing-table limit number { warn-threshold | simply-alert } |
By default, the number of active routes allowed for a VPN instance is not limited. Setting the maximum number of active routes for a VPN instance can prevent the PE from learning too many routes. |
|
5. Apply an import routing policy. |
import route-policy route-policy |
By default, all routes matching the import target attribute are accepted. The specified routing policy must have been created. For information about routing policies, see Layer 3—IP Routing Configuration Guide. |
|
6. Apply an export routing policy. |
export route-policy route-policy |
By default, routes to be advertised are not filtered. The specified routing policy must have been created. For information about routing policies, see Layer 3—IP Routing Configuration Guide. |
|
7. Apply a tunnel policy to the VPN instance. |
tnl-policy tunnel-policy-name |
By default, only one tunnel is selected (no load balancing) in this order: LSP tunnel, GRE tunnel, and CRLSP tunnel. The specified tunnel policy must have been created. For information about tunnel policies, see "Configuring tunnel policies." |
Configuring routing between a PE and a CE
You can configure static routing, RIP, OSPF, IS-IS, EBGP, or IBGP between a PE and a CE.
Configuring static routing between a PE and a CE
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a static route for a VPN instance. |
ip route-static vpn-instance s-vpn-instance-name dest-address { mask-length | mask } { interface-type interface-number [ next-hop-address ] |next-hop-address [ public ] [ track track-entry-number ] | vpn-instance d-vpn-instance-name next-hop-address [ track track-entry-number ] } [ permanent ] [ preference preference-value ] [ tag tag-value ] [ description description-text ] |
By default, no static route is configured for a VPN instance. Perform this configuration on the PE. On the CE, configure a common static route. For more information about static routing, see Layer 3—IP Routing Configuration Guide. |
Configuring RIP between a PE and a CE
A RIP process belongs to the public network or a single VPN instance. If you create a RIP process without binding it to a VPN instance, the process belongs to the public network.
To configure RIP between a PE and a CE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a RIP process for a VPN instance and enter RIP view. |
rip [ process-id ] vpn-instance vpn-instance-name |
Perform this configuration on the PE. On the CE, create a common RIP process. |
|
3. Enable RIP on the interface attached to the specified network. |
network network-address |
By default, RIP is disabled on an interface. |
Configuring OSPF between a PE and a CE
An OSPF process that is bound to a VPN instance does not use the public network router ID configured in system view. Therefore, you must specify a router ID when starting a process or configure an IP address for at least one interface of the VPN instance.
An OSPF process belongs to the public network or a single VPN instance. If you create an OSPF process without binding it to a VPN instance, the process belongs to the public network.
To configure OSPF between a PE and a CE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an OSPF process for a VPN instance and enter the OSPF view. |
ospf [ process-id | router-id router-id | vpn-instance vpn-instance-name ] * |
Perform this configuration on the PE. On the CE, create a common OSPF process. |
|
3. (Optional.) Configure an OSPF domain ID. |
domain-id domain-id [ secondary ] |
The default domain ID is 0. Perform this configuration on the PE. The domain ID is carried in the routes of the OSPF process. When redistributing routes from the OSPF process, BGP adds the domain ID as an extended community attribute into BGP routes. An OSPF process can be configured with only one domain ID. Domain IDs of different OSPF processes can be the same. All OSPF processes of a VPN must be configured with the same domain ID. |
|
4. Configure the type codes of OSPF extended community attributes. |
ext-community-type { domain-id type-code1 | router-id type-code2 | route-type type-code3 } |
The defaults are as follows: · 0x0005 for Domain ID. · 0x0107 for Router ID. · 0x0306 for Route Type. Perform this configuration on the PE. |
|
5. Create an OSPF area and enter area view. |
area area-id |
By default, no OSPF area is created. |
|
6. Enable OSPF on the interface attached to the specified network in the area. |
network ip-address wildcard-mask |
By default, an interface neither belongs to any area nor runs OSPF. |
Configuring IS-IS between a PE and a CE
An IS-IS process belongs to the public network or a single VPN instance. If you create an IS-IS process without binding it to a VPN instance, the process belongs to the public network.
To configure IS-IS between a PE and a CE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an IS-IS process for a VPN instance and enter IS-IS view. |
isis [ process-id ] vpn-instance vpn-instance-name |
Perform this configuration on the PE. On the CE, configure common IS-IS. |
|
3. Configure a network entity title for the IS-IS process. |
network-entity net |
By default, no NET is configured. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enter interface view. |
interface interface-type interface-number |
N/A |
|
6. Enable the IS-IS process on the interface. |
isis enable [ process-id ] |
By default, no IS-IS process is enabled on the interface. |
Configuring EBGP between a PE and a CE
1. Configure the PE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable BGP and enter BGP view. |
bgp as-number |
N/A |
|
3. Enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
Configuration commands in BGP-VPN instance view are the same as those in BGP view. For details, see Layer 3—IP Routing Configuration Guide. |
|
4. Configure the CE as the VPN EBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
By default, no BGP peer is configured. For more information about BGP peers and peer groups, see Layer 3—IP Routing Configuration Guide. |
|
5. Create the BGP-VPN IPv4 unicast family and enter its view. |
address-family ipv4 [ unicast ] |
By default, the BGP-VPN IPv4 unicast family is not created. |
|
6. Enable IPv4 unicast route exchange with the specified peer or peer group. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange IPv4 unicast routes with any peer. |
|
7. Redistribute the routes of the local CE. |
import-route protocol [ { process-id | all-processes } [ med med-value | route-policy route-policy-name ] * ] |
A PE must redistribute the routes of the local CE into its VPN routing table so it can advertise them to the peer PE. |
|
8. (Optional.) Allow the local AS number to appear in the AS_PATH attribute of a received route, and set the maximum number of repetitions. |
peer { group-name | ip-address [ mask-length ] } allow-as-loop [ number ] |
By default, BGP discards incoming route updates that contain the local AS number. BGP detects routing loops by examining AS numbers. In a hub-spoke network where EBGP is running between a PE and a CE, the routing information the PE advertises to a CE carries the AS number of the PE. Therefore, the route updates that the PE receives from the CE also include the AS number of the PE. This causes the PE to be unable to receive the route updates. In this case, you must configure this command to allow routing loops. |
2. Configure the CE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Configure the PE as a BGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
By default, no BGP peer is created. |
|
4. Create the BGP IPv4 unicast family and enter its view. |
address-family ipv4 [ unicast ] |
By default, the BGP IPv4 unicast family is not created. |
|
5. Enable IPv4 unicast route exchange with the specified peer or peer group. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange IPv4 unicast routes with any peer. |
|
6. (Optional.) Configure route redistribution. |
import-route protocol [ { process-id | all-processes } [ allow-direct | med med-value | route-policy route-policy-name ] * ] |
A CE must redistribute its routes to the PE so the PE can advertise them to the peer CE. |
Configuring IBGP between a PE and a CE
Use IBGP between PE and CE only in a basic MPLS L3VPN network. In networks such as Hub&Spoke, Extranet, inter-AS VPN, carrier's carrier, nested VPN, and HoVPN, you cannot use IBGP between PE and CE.
1. Configure the PE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
Configuration commands in BGP-VPN instance view are the same as those in BGP view. For details, see Layer 3—IP Routing Configuration Guide. |
|
4. Configure the CE as the VPN IBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
By default, no BGP peer is created. |
|
5. Create the BGP-VPN IPv4 unicast family and enter its view. |
address-family ipv4 [ unicast ] |
By default, the BGP-VPN IPv4 unicast family is not created. |
|
6. Enable IPv4 unicast route exchange with the specified peer. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange IPv4 unicast routes with any peer. |
|
7. Configure the CE as a client of the RR. |
peer { group-name | ip-address [ mask-length ] } reflect-client |
By default, no RR or RR client is configured, and the PE does not advertise routes learned from the IBGP peer CE to other IBGP peers, including VPNv4 IBGP peers. The PE advertises routes learned from the CE to other IBGP peers only when you configure the IBGP peer CE as a client of the RR. Configuring an RR does not change the next hop of a route. To change the next hop of a route, configure an inbound policy on the receiving side. |
|
8. (Optional.) Enable route reflection between clients. |
reflect between-clients |
Route reflection between clients is enabled by default. |
|
9. (Optional.) Configure the cluster ID for the RR. |
reflector cluster-id { cluster-id | ip-address } |
By default, the RR uses its own router ID as the cluster ID. If multiple RRs exist in a cluster, use this command to configure the same cluster ID for all RRs in the cluster to avoid routing loops. |
2. Configure the CE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Configure the PE as an IBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
By default, no BGP peer is created. |
|
4. Create the BGP IPv4 unicast family and enter its view. |
address-family ipv4 [ unicast ] |
By default, the BGP IPv4 unicast family is not created. |
|
5. Enable IPv4 unicast route exchange with the specified peer or peer group. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange IPv4 unicast routes with any peer. |
|
6. (Optional.) Configure route redistribution. |
import-route protocol [ { process-id | all-processes } [ allow-direct | med med-value | route-policy route-policy-name ] * ] |
A CE must redistribute its routes to the PE so the PE can advertise them to the peer CE. |
Configuring routing between PEs
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Configure the remote PE as a BGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
By default, no BGP peer is created. |
|
4. Specify the source interface for route updates. |
peer { group-name | ip-address [ mask-length ] } connect-interface interface-type interface-number |
By default, BGP uses the egress interface of the optimal route destined for the peer as the source interface. |
|
5. Create the BGP VPNv4 address family and enter its view. |
address-family vpnv4 |
By default, the BGP VPNv4 address family is not created. |
|
6. Enable BGP VPNv4 route exchange with the specified peer. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange BGP VPNv4 routes with any peer. |
Configuring BGP VPNv4 route control
BGP VPNv4 route control is configured similarly with BGP route control, except that it is configured in BGP VPNv4 address family view. For detailed information about BGP route control, see Layer 3—IP Routing Configuration Guide.
To configure BGP VPNv4 route control:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Enter BGP VPNv4 address family view. |
address-family vpnv4 |
N/A |
|
4. (Optional.) Configure filtering of advertised routes. |
filter-policy { acl-number | prefix-list prefix-list-name } export [ protocol process-id ] |
By default, BGP does not filter advertised routes. |
|
5. (Optional.) Configure filtering of received routes. |
filter-policy { acl-number | prefix-list prefix-list-name } import |
By default, BGP does not filter received routes. |
|
6. (Optional.) Advertise community attributes to a peer or peer group. |
peer { group-name | ip-address [ mask-length ] } advertise-community |
By default, no community attributes are advertised to any peer or peer group. |
|
7. Allow the local AS number to appear in the AS_PATH attribute of routes received from the peer, and set the maximum number of repetitions. |
peer { group-name | ip-address [ mask-length ] } allow-as-loop [ number ] |
By default, BGP discards route updates that contain the local AS number. |
|
8. (Optional.) Filter routes received from or advertised to a peer or peer group based on an AS_PATH list. |
peer { group-name | ip-address [ mask-length ] } as-path-acl aspath-filter-number { import | export } |
By default, no AS filtering list is applied to a peer or peer group. |
|
9. (Optional.) Advertise a default VPN route to a peer or peer group. |
peer { group-name | ip-address [ mask-length ] } default-route-advertise vpn-instance vpn-instance-name |
By default, no default VPN route is advertised to a peer or peer group. |
|
10. (Optional.) Apply an ACL to filter routes received from or advertised to a peer or peer group. |
peer { group-name | ip-address [ mask-length ] } filter-policy acl-number { export | import } |
By default, no ACL-based filtering is configured. |
|
11. Save all route updates from a peer or peer group. |
peer { group-name | ip-address [ mask-length ] } keep-all-routes |
By default, BGP does not save route updates from any peer. |
|
12. Specify the router as the next hop of routes sent to a peer or peer group. |
peer { group-name | ip-address [ mask-length ] } next-hop-local |
By default, the router sets itself as the next hop for routes sent to a peer or peer group. |
|
13. (Optional.) Configure BGP to not change the next hop of routes sent to an EBGP peer or peer group. |
peer { group-name | ip-address [ mask-length ] } next-hop-invariable |
By default, the router sets itself as the next hop for routes sent to an EBGP peer or peer group. In an inter-AS option C network where an RR is used to advertise VPNv4 routes, configure this command on the RR so the RR does not change the next hop of routes sent to EBGP peers and clients. |
|
14. (Optional.) Specify a preferred value for routes received from a peer or peer group. |
peer { group-name | ip-address [ mask-length ] } preferred-value value |
By default, the preferred value is 0. |
|
15. Apply a prefix list to filter routes received from or advertised to a peer or peer group. |
peer { group-name | ip-address [ mask-length ] } prefix-list prefix-list-name { export | import } |
By default, no prefix list based filtering is configured. |
|
16. (Optional.) Configure BGP updates advertised to an EBGP peer or peer group to carry only public AS numbers. |
peer { group-name | ip-address [ mask-length ] } public-as-only |
By default, BGP route updates advertised to an EBGP peer or peer group can carry both public and private AS numbers. |
|
17. Configure the router as a route reflector and specify a peer or peer group as its client. |
peer { group-name | ip-address [ mask-length ] } reflect-client |
By default, no RR is configured. |
|
18. Specify the maximum number of routes BGP can receive from a peer or peer group. |
peer { group-name | ip-address [ mask-length ] } route-limit prefix-number [ { alert-only | discard | reconnect reconnect-time } | percentage-value ] * |
By default, the number of routes that BGP can receive from a peer or peer group is not limited. |
|
19. Apply a routing policy to a peer or peer group. |
peer { group-name | ip-address [ mask-length ] } route-policy route-policy-name { export | import } |
By default, no routing policy is applied to a peer or peer group. |
|
20. Enable route target-based filtering of received VPNv4 routes. |
policy vpn-target |
By default, this feature is enabled. |
|
21. Enable route reflection between clients. |
reflect between-clients |
By default, route reflection between clients is enabled on the RR. |
|
22. Configure a cluster ID for the route reflector. |
reflector cluster-id { cluster-id | ip-address } |
By default, the RR uses its own router ID as the cluster ID. |
|
23. Configure filtering of reflected routes. |
rr-filter extended-community-number |
By default, the RR does not filter reflected routes. |
Configuring inter-AS VPN
If the MPLS backbone spans multiple ASs, you must configure inter-AS VPN.
Configuring inter-AS option A
Inter-AS option A applies to scenarios with a few VPNs.
To configure inter-AS option A, create VPN instances on PEs and ASBRs. The VPN instances on PEs are used to allow CEs to access the network. The VPN instances on ASBRs are used to access the peer ASBRs. An ASBR considers the peer ASBR as a CE.
The route targets configured on the PEs must match those configured on the ASBRs in the same AS to make sure VPN routes sent by the PEs (or ASBRs) can be received by the ASBRs (or PEs). Route targets configured on the PEs in different ASs do not have such requirements.
For more information, see "Configuring basic MPLS L3VPN."
Configuring inter-AS option B
To configure inter-AS option B, configure PEs and ASBRs.
· PE configuration:
Configure basic MPLS L3VPN, and specify the ASBR in the same AS as an MP-IBGP peer. The route targets for the VPN instances on the PEs in different ASs must match for the same VPN. For more information about PE configuration, see "Configuring basic MPLS L3VPN."
· ASBR configuration:
? Configure a routing protocol, and enable MPLS and LDP on the interface connecting to an internal router of the AS.
? Specify the PE in the same AS as an MP-IBGP peer, and the ASBR in a different AS as an MP-EBGP peer.
? Disable VPN target filtering for VPNv4 routes so the ASBR can maintain all VPNv4 routes and advertise the routes to the peer ASBR.
? Enable MPLS on the interface connected to the remote ASBRs. There is no need to configure a label distribution protocol, for example, MPLS LDP.
An ASBR always sets itself as the next hop of VPNv4 routes advertised to an MP-IBGP peer regardless of the peer next-hop-local command.
To configure inter-AS option B on an ASBR:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view of the interface connected to an internal router of the AS. |
interface interface-type interface-number |
N/A |
|
3. Enable MPLS on the interface. |
mpls enable |
By default, MPLS is disabled on the interface. |
|
4. Enable MPLS LDP on the interface. |
mpls ldp enable |
By default, MPLS LDP is disabled on the interface. |
|
5. Return to system view. |
quit |
N/A |
|
6. Enter interface view of the interface connecting to the remote ASBR. |
interface interface-type interface-number |
N/A |
|
7. Enable MPLS on the interface. |
mpls enable |
By default, MPLS is disabled on the interface. |
|
8. Return to system view. |
quit |
N/A |
|
9. Enter BGP view. |
bgp as-number |
N/A |
|
10. Create a BGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
By default, no BGP peer is configured. Configure PEs in the same AS as IBGP peers, and ASBRs in different ASs as EBGP peers. |
|
11. Enter BGP VPNv4 address family view. |
address-family vpnv4 |
N/A |
|
12. Enable BGP to exchange VPNv4 routes with the PE in the same AS and the ASBR in different ASs. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP cannot exchange VPNv4 routing information with a peer. |
|
13. Disable route target based filtering of VPNv4 routes. |
undo policy vpn-target |
By default, the PE filters received VPNv4 routes by route targets. The routes surviving the filtering are added to the routing table, and the others are discarded. |
Configuring inter-AS option C
To configure inter-AS option C, configure PEs and ASBRs.
· PE configuration:
? Configure basic MPLS L3VPN, and specify the PE in another AS as an MP-EBGP peer. The route targets for the VPN instances on the PEs in different ASs must match for the same VPN.
? Execute the peer ebgp-max-hop command to enable the local router to establish an EBGP session to an indirectly-connected peer because the PEs are not directly connected.
? Specify the ASBR in the same AS as an IBGP peer, and enable BGP to exchange labeled IPv4 unicast routes with the ASBR.
· ASBR configuration:
? Configure a routing protocol, and enable MPLS and LDP on the interface connecting to an internal router of the AS.
? Specify the PE in the same AS as an IBGP peer, and the ASBR in a different AS as an EBGP peer.
? Enable BGP to exchange labeled IPv4 unicast routes with the PE in the same AS and the ASBR in different AS.
? Enable MPLS on the interface connected to the remote ASBR. There is no need to configure a label distribution protocol, for example, MPLS LDP.
? Configure a routing policy to determine which IPv4 unicast routes are advertised to the IBGP or EBGP peer with MPLS labels.
In addition, configure BGP to advertise routes destined for a PE on PEs or ASBRs. For more information, see Layer 3—IP Routing Configuration Guide.
Configuring a PE
For basic MPLS L3VPN configurations on a PE, see "Configuring basic MPLS L3VPN." The following table describes inter-AS option C specific configurations.
To configure a PE for inter-AS option C:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Configure the ASBR in the same AS as an IBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
By default, no BGP peer is created. |
|
4. Configure the PE of another AS as an EBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
By default, no BGP peer is created. |
|
5. Create the BGP IPv4 unicast address family and enter its view. |
address-family ipv4 [ unicast ] |
By default, the BGP IPv4 unicast address family is not created. |
|
6. Enable BGP to exchange IPv4 unicast routes with the ASBR in the same AS. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange IPv4 unicast routes with any peer. |
|
7. Enable BGP to exchange labeled IPv4 routes with the ASBR in the same AS. |
peer { group-name | ip-address [ mask-length ] } label-route-capability |
By default, BGP cannot exchange labeled routes with any IPv4 peer or peer group. |
|
8. Return to BGP view. |
quit |
N/A |
|
9. Enter BGP VPNv4 address family view. |
address-family vpnv4 |
N/A |
|
10. Enable BGP to exchange VPNv4 routes with the PE in different ASs. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP cannot exchange VPNv4 routes with any peer. |
|
11. (Optional.) Configure the PE to not change the next hop of routes advertised to the EBGP peer. |
peer { group-name | ip-address [ mask-length ] } next-hop-invariable |
Configure this command on the RR so the RR does not change the next hop of advertised VPNv4 routes. |
Configuring an ASBR
To set up an inter-AS public tunnel for the inter-AS option C solution, an ASBR must assign an MPLS label to the route destined for a PE, and advertise the label along with the route. Typically, the routes advertised by an ASBR through BGP include the PE address as well as other routes. You can configure a routing policy to filter routes. Routes surviving the filtering are assigned labels, and all others are advertised as common IPv4 routes.
To configure a routing policy, use the following commands:
· if-match mpls-label—Matches routes carrying MPLS labels.
· apply mpls-label—Sets MPLS labels for IPv4 routes to be advertised to a peer. You can use this command together with if-match clauses. For example, when used together with the if-match mpls-label command, the apply mpls-label sets new MPLS labels for routes with MPLS labels. The newly assigned labels are advertised along with the routes.
For more information about routing policy configuration, see Layer 3—IP Routing Configuration Guide.
To configure an ASBR-PE for inter-AS option C:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. (Optional.) Create a routing policy, and enter routing policy view. |
route-policy route-policy-name { deny | permit } node node-number |
By default, no routing policy is created. |
|
3. (Optional.) Match IPv4 routes carrying labels. |
if-match mpls-label |
By default, no MPLS label match criterion is configured. |
|
4. (Optional.) Set labels for IPv4 routes. |
apply mpls-label |
By default, no MPLS label is set for IPv4 routes. |
|
5. Return to system view. |
quit |
N/A |
|
6. Enter interface view of the interface connected to an internal router of the AS. |
interface interface-type interface-number |
N/A |
|
7. Enable MPLS on the interface. |
mpls enable |
By default, MPLS is disabled on the interface. |
|
8. Enable MPLS LDP on the interface. |
mpls ldp enable |
By default, MPLS LDP is disabled on the interface. |
|
9. Return to system view. |
quit |
N/A |
|
10. Enter interface view of the interface connected to the remote ASBR. |
interface interface-type interface-number |
N/A |
|
11. Enable MPLS on the interface. |
mpls enable |
By default, MPLS is disabled on the interface. |
|
12. Return to system view. |
quit |
N/A |
|
13. Enter BGP view. |
bgp as-number |
N/A |
|
14. Configure the PE in the same AS as an IBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
By default, no BGP peer is created. |
|
15. Configure the ASBR in another AS as an EBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
By default, no BGP peer is created. |
|
16. Create the BGP IPv4 unicast address family and enter its view. |
address-family ipv4 [ unicast ] |
By default, the BGP IPv4 unicast address family is not created. |
|
17. Enable exchange of IPv4 unicast routes with the PE in the same AS and the ASBR in another AS. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange IPv4 unicast routes with any peer. |
|
18. Enable exchange of labeled IPv4 routes with the PE in the same AS and the ASBR in another AS. |
peer { group-name | ip-address [ mask-length ] } label-route-capability |
By default, BGP cannot advertise labeled routes to any IPv4 peer or peer group. |
|
19. Configure the ASBR-PE to set itself as the next hop of routes advertised to the PE in the local AS. |
peer { group-name | ip-address [ mask-length ] } next-hop-local |
By default, BGP does not use its address as the next hop of routes advertised to an IBGP peer or peer group. |
|
20. (Optional.) Apply a routing policy to routes incoming from or outgoing to a peer or peer group. |
peer { group-name | ip-address [ mask-length ] } route-policy route-policy-name { export | import } |
By default, no routing policy is applied. |
Configuring a routing policy on an ASBR-PE
A routing policy on an ASBR-PE performs the following operations:
· Assigns MPLS labels to routes received from the PEs in the local AS before advertising them to the peer ASBR-PE.
· Assigns new MPLS labels to labeled IPv4 routes advertised to PEs in the local AS.
Which IPv4 routes are assigned with MPLS labels depends on the routing policy. Only routes that meet the criteria are assigned with labels. All other routes are still common IPv4 routes.
To configure a routing policy for inter-AS option C on an ASBR-PE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a routing policy and enter routing policy view. |
route-policy route-policy-name { deny | permit } node node-number |
By default, no routing policy is created. |
|
3. Match IPv4 routes carrying labels. |
if-match mpls-label |
By default, no match criterion is configured. |
|
4. Set labels for IPv4 routes. |
apply mpls-label |
By default, no apply clause is configured. |
Configuring nested VPN
For a network with many VPNs, nested VPN is a good solution to implement layered management of VPNs and to conceal the deployment of internal VPNs.
To build a nested VPN network, perform the following configurations:
· Configurations between customer PE and customer CE—Configure VPN instances on the customer PE and configure route exchange between customer PE and customer CE.
· Configurations between customer PE and provider CE—Configure BGP VPNv4 route exchange between them. To make sure the provider CE can receive all BGP VPNv4 routes, configure the undo policy vpn-target command on the provider CE to not filter VPNv4 routes by RTs.
· Configurations between provider CE and provider PE—Configure VPN instances and enable nested VPN on the provider PE and configure BGP VPNv4 route exchange between the provider CE and provider PE.
· Configurations between provider PEs—Configure BGP VPNv4 route exchange between them.
Nested VPN allows a customer PE to directly exchange VPNv4 routes with a provider PE, without needing to deploy a provider CE. In this case, the customer PE also acts as the provider CE. Therefore, you must configure provider CE settings on it.
Configurations on the customer CE, customer PE, and provider CE are similar to basic MPLS L3VPN configurations. This task describes the configurations on the provider PE.
When you configure nested VPN, follow these guidelines:
· The address spaces of sub-VPNs of a VPN cannot overlap.
· Do not assign nested VPN peers addresses that public network peers use.
· Nested VPN does not support multihop EBGP. A provider PE and a provider CE must use the addresses of the directly connected interfaces to establish a neighbor relationship.
To configure nested VPN:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Enter BGP VPNv4 address family view. |
address-family vpnv4 |
N/A |
|
4. Enable nested VPN. |
nesting-vpn |
By default, nested VPN is disabled. |
|
5. Return to BGP view. |
quit |
N/A |
|
6. Enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
N/A |
|
7. Specify the peer CE or the peer group of the peer CE. |
peer { group-name | peer-address [ mask-length ] } as-number as-number |
By default, no peer is specified. |
|
8. Create the BGP-VPN VPNv4 address family and enter its view. |
address-family vpnv4 |
By default, the BGP-VPN VPNv4 address family is not created. |
|
9. (Optional.) Enable BGP VPNv4 route exchange with the peer CE or the peer group of the peer CE. |
peer { group-name | peer-address [ mask-length ] } enable |
By default, BGP does not exchange VPNv4 routes with any peer. |
Configuring HoVPN
In a HoVPN networking scenario, perform basic MPLS L3VPN settings on UPE and SPE. In addition, configure the following settings on the SPE:
· Specify the BGP peer or peer group as a UPE.
· Advertise the default route of the specified VPN instance or routes matching a routing policy to the UPE.
· Create a BGP-VPN instance so the learned VPNv4 routes can be added into the BGP routing table of the corresponding VPN instance by RTs.
Associating an interface with a VPN instance is not required on the SPE because no interface on the SPE is directly connected to the customer network.
As a best practice, do not configure the peer default-route-advertise vpn-instance and peer upe route-policy commands at the same time.
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Specify a BGP peer or peer group. |
peer { group-name | peer-address [ mask-length ] } as-number as-number |
By default, no BGP peer is specified. |
|
4. Enter BGP-VPN VPNv4 address family view. |
address-family vpnv4 |
N/A |
|
5. Enable BGP VPNv4 route exchange with the peer or peer group. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange VPNv4 routes with any peer. |
|
6. Specify the BGP peer or peer group as a UPE. |
peer { group-name | ip-address [ mask-length ] } upe |
By default, no peer is a UPE. |
|
7. Advertise routes to the UPE. |
·
Advertise a default VPN route to the UPE: ·
Advertise
routes permitted by a routing policy to the UPE: |
By default, no route is advertised to the UPE. Do not configure both commands. The peer default-route-advertise vpn-instance command advertises a default route using the local address as the next hop to the UPE, regardless of whether the default route is present in the local routing table. However, if the specified peer is not a UPE, the command does not advertise a default route. |
|
8. Return to BGP view. |
quit |
N/A |
|
9. Create a BGP-VPN instance, and enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
By default, no BGP-VPN instance is created. |
Configuring an OSPF sham link
When a backdoor link exists between the two sites of a VPN, you can create a sham link between PEs to forward VPN traffic through the sham link on the backbone rather than the backdoor link. A sham link is considered an OSPF intra-area route.
The source and destination addresses of the sham link must be loopback interface addresses with 32-bit masks. The loopback interfaces must be bound to VPN instances, and their addresses are advertised through BGP.
Before you configure an OSPF sham link, complete the following tasks:
· Configure basic MPLS L3VPN (OSPF is used between PE and CE).
· Configure OSPF in the LAN where customer CEs reside.
Configuring a loopback interface
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a loopback interface and enter loopback interface view. |
interface loopback interface-number |
By default, no loopback interface is created. |
|
3. Associate the loopback interface with a VPN instance. |
ip binding vpn-instance vpn-instance-name |
By default, the interface is associated with no VPN instance. |
|
4. Configure the address of the loopback interface. |
ip address ip-address { mask | mask-length } |
N/A |
Redistributing the loopback interface route
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
N/A |
|
4. Enter BGP-VPN IPv4 unicast address family view. |
address-family ipv4 [ unicast ] |
N/A |
|
5. Redistribute direct routes into BGP (including the loopback interface route). |
import-route direct |
By default, no direct routes are redistributed into BGP. |
Creating a sham link
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter OSPF view. |
ospf [ process-id | router-id router-id | vpn-instance vpn-instance-name ] * |
As a best practice, specify a router ID. |
|
3. Configure the external route tag for imported VPN routes. |
route-tag tag-value |
If BGP runs within an MPLS backbone, and the BGP AS number is not greater than 65535, the first two octets of the external route tag are 0xD000 and the last two octets are the local BGP AS number. If the AS number is greater than 65535, the external route tag is 0. |
|
4. Enter OSPF area view. |
area area-id |
N/A |
|
5. Configure a sham link. |
sham-link source-ip-address destination-ip-address [ cost cost | dead dead-interval | hello hello-interval | { { hmac-md5 | md5 } key-id { cipher cipher-string | plain plain-string } | simple { cipher cipher-string | plain plain-string } } | retransmit retrans-interval | trans-delay delay ] * |
By default, no sham link is configured. |
Specifying the VPN label processing mode on the egress PE
An egress PE can process VPN labels in either POPGO or POP mode:
· POPGO forwarding—Pops the label and forwards the packet out of the egress interface corresponding to the label.
· POP forwarding—Pops the label and forwards the packet through the FIB table.
To specify the VPN label processing mode on an egress PE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Specify the VPN label processing mode as POPGO forwarding. |
vpn popgo |
The default is POP forwarding. |
Configuring BGP AS number substitution
When CEs at different sites have the same AS number, configure the BGP AS number substitution function to avoid route loss. If the AS_PATH attribute of a route contains the AS number of the specified CE, the PE replaces the AS number with its own AS number before advertising the route to that CE.
To configure BGP AS number substitution:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
N/A |
|
4. Configure a BGP peer or peer group. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
N/A |
|
5. Enable the BGP AS number substitution function. |
peer { group-name | ip-address [ mask-length ] } substitute-as |
By default, BGP AS number substitution is disabled. For more information about this command, see Layer 3—IP Routing Command Reference. |
Configuring MPLS L3VPN FRR
There are two methods to configure MPLS L3VPN FRR:
· Method 1—Execute the pic command in BGP-VPN IPv4 unicast address family view. The device calculates a backup next hop for each BGP route in the VPN instance if there are two or more unequal-cost routes to reach the destination.
· Method 2—Execute the fast-reroute route-policy command in BGP-VPN IPv4 unicast address family view to reference a routing policy in which a backup next hop is specified by using the apply fast-reroute backup-nexthop command. The backup next hop calculated by the device must be the same as the specified backup next hop. Otherwise, the device does not generate a backup next hop for the primary route. You can also configure if-match clauses in the routing policy to identify the routes protected by FRR.
If both methods are configured, Method 2 takes precedence over Method 1.
To configure MPLS L3VPN FRR:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable MPLS BFD. |
mpls bfd enable |
The mpls bfd enable command applies to VPNv4 route backup for a VPNv4 route and IPv4 route backup for a VPNv4 route. For more information about this command, see MPLS Command Reference. |
|
3. Configure the source IP address for BFD echo packets. |
bfd echo-source-ip ip-address |
The bfd echo-source-ip command is required when echo-mode BFD is used to detect primary route connectivity in VPNv4 route backup for an IPv4 route. For more information about this command, see High Availability Command Reference. |
|
4. Use BFD to test the connectivity of an LSP or MPLS TE tunnel. |
·
Configure BFD to test the connectivity of the
LSP for the specified FEC: · Configure BFD to test the connectivity of the MPLS TE tunnel for the tunnel interface: a. interface tunnel number mode mpls-te b. mpls bfd [ discriminator local local-id remote remote-id ] [ template template-name ] c. quit |
By default, BFD is not configured to test the connectivity of the LSP or MPLS TE tunnel. This step is required for VPNv4 route backup for a VPNv4 route and IPv4 route backup for a VPNv4 route. Use either command depending on the public tunnel type. For more information about the commands in this step, see MPLS Command Reference. |
|
5. Create a routing policy and enter routing policy view. |
route-policy route-policy-name permit node node-number |
By default, no routing policy is created. This step is required to enable MPLS L3VPN FRR in Method 2. For more information about this command, see Layer 3—IP Routing Command Reference. |
|
6. Set the backup next hop for FRR. |
apply fast-reroute backup-nexthop ip-address |
By default, no backup next hop address is set for FRR. This step is required to enable MPLS L3VPN FRR in Method 2. For more information about this command, see Layer 3—IP Routing Command Reference. |
|
7. Return to system view. |
quit |
N/A |
|
8. Enter BGP view. |
bgp as-number |
N/A |
|
9. (Optional.) Use echo-mode BFD to detect the connectivity to the next hop of the primary route. |
primary-path-detect bfd echo |
By default, ARP is used to detect the connectivity to the next hop. Use this command if necessary in VPNv4 route backup for an IPv4 route. For more information about this command, see Layer 3—IP Routing Command Reference. |
|
10. Enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
N/A |
|
11. Enter BGP-VPN IPv4 unicast address family view. |
address-family ipv4 [ unicast ] |
N/A |
|
12. Enable MPLS L3VPN FRR. |
·
(Method 1) Enable MPLS L3VPN FRR for the address family: ·
(Method 2) Reference a routing policy
to specify a backup next hop for the address family: |
By default, MPLS L3VPN FRR is disabled. Method 1 might result in routing loops. Use it with caution. By default, no routing policy is referenced. The apply fast-reroute backup-nexthop command can take effect in the routing policy that is being used. Other apply commands do not take effect. For more information about the command, see Layer 3—IP Routing Command Reference. |
Enabling SNMP notifications for MPLS L3VPN
This feature enables MPLS L3VPN to generate SNMP notifications. The generated SNMP notifications are sent to the SNMP module.
For more information about SNMP notifications, see Network Management and Monitoring Configuration Guide.
To enable SNMP notifications for MPLS L3VPN:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable SNMP notifications for MPLS L3VPN. |
snmp-agent trap enable l3vpn |
By default, SNMP notifications for MPLS L3VPN are enabled. |
Enabling logging for BGP route flapping
This feature enables BGP to generate logs for BGP route flappings that trigger log generation. The generated logs are sent to the information center. For the logs to be output correctly, you must also configure information center on the device. For more information about the information center, see Network Management and Monitoring Configuration Guide.
To enable logging for BGP route flapping:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP VPNv4 address family view or BGP-VPN VPNv4 address family view. |
· Enter BGP VPNv4 address family view: a. bgp as-number b. address-family vpnv4 · Enter BGP-VPN VPNv4 address family view: c. bgp as-number d. ip vpn-instance vpn-instance-name e. address-family vpnv4 |
N/A |
|
3. Enable logging for BGP route flapping. |
log-route-flap monitor-time monitor-count [ log-count-limit | route-policy route-policy-name ] * |
By default, logging for BGP route flapping is disabled. |
Displaying and maintaining MPLS L3VPN
You can soft-reset or reset BGP sessions to apply new BGP configurations. A soft reset operation updates BGP routing information without tearing down BGP connections. A reset operation updates BGP routing information by tearing down, and then re-establishing BGP connections. Soft reset requires that BGP peers have route refresh capability.
Execute the following commands in user view to soft reset or reset BGP connections:
|
Task |
Command |
|
Soft reset BGP sessions for VPNv4 address family. |
refresh bgp { ip-address [ mask-length ] | all | external | group group-name | internal } { export | import } vpnv4 [ vpn-instance vpn-instance-name ] |
|
Reset BGP sessions for VPNv4 address family. |
reset bgp { as-number | ip-address [ mask-length ] | all | external | internal | group group-name } vpnv4 [ vpn-instance vpn-instance-name ] |
For more information about the refresh bgp vpnv4 and reset bgp vpnv4 commands, see Layer 3—IP Routing Command Reference.
Execute the following commands in any view to display MPLS L3VPN:
|
Task |
Command |
|
Display the routing table for a VPN instance (in standalone mode). |
display ip routing-table vpn-instance vpn-instance-name [ statistics | verbose ] [ standby slot slot-number ] |
|
Display the routing table for a VPN instance (in IRF mode). |
display ip routing-table vpn-instance vpn-instance-name [ statistics | verbose ] [ standby chassis chassis-number slot slot-number ] |
|
Display information about a specified or all VPN instances. |
display ip vpn-instance [ instance-name vpn-instance-name ] |
|
Display the FIB of a VPN instance. |
display fib vpn-instance vpn-instance-name |
|
Display FIB entries that match the specified destination IP address in the specified VPN instance. |
display fib vpn-instance vpn-instance-name ip-address [ mask | mask-length ] |
|
Display BGP VPNv4 peer group information. |
display bgp group vpnv4 [ vpn-instance vpn-instance-name ] [ group-name group-name ] |
|
Display BGP VPNv4 peer information (in standalone mode). |
display bgp peer vpnv4 [ vpn-instance vpn-instance-name ] [ ip-address mask-length | { ip-address | group-name group-name } log-info | [ [ ip-address ] verbose ] [ standby slot slot-number ] ] |
|
Display BGP VPNv4 peer information (in IRF mode). |
display bgp peer vpnv4 [ vpn-instance vpn-instance-name ] [ ip-address mask-length | { ip-address | group-name group-name } log-info | [ [ ip-address ] verbose ] [ standby chassis chassis-number slot slot-number ] ] |
|
Display BGP VPNv4 routes (in standalone mode). |
display bgp routing-table vpnv4 [ [ route-distinguisher route-distinguisher ] [ network-address [ { mask | mask-length } [ longest-match ] ] | network-address [ mask | mask-length ] advertise-info | as-path-acl as-path-acl-number | community-list { { basic-community-list-number | comm-list-name } [ whole-match ] | adv-community-list-number } ] | [ vpn-instance vpn-instance-name ] peer ip-address { advertised-routes | received-routes } [ network-address [ mask | mask-length ] | statistics ] | statistics ] [ standby slot slot-number ] |
|
Display BGP VPNv4 routes (in IRF mode). |
display bgp routing-table vpnv4 [ [ route-distinguisher route-distinguisher ] [ network-address [ { mask | mask-length } [ longest-match ] ] | network-address [ mask | mask-length ] advertise-info | as-path-acl as-path-acl-number | community-list { { basic-community-list-number | comm-list-name } [ whole-match ] | adv-community-list-number } ] | [ vpn-instance vpn-instance-name ] peer ip-address { advertised-routes | received-routes } [ network-address [ mask | mask-length ] | statistics ] | statistics ] [ standby chassis chassis-number slot slot-number ] |
|
Display incoming labels for BGP IPv4 unicast routes. |
display bgp routing-table ipv4 [ unicast ] [ vpn-instance vpn-instance-name ] inlabel |
|
Display outgoing labels for BGP IPv4 unicast routes (in standalone mode). |
display bgp routing-table ipv4 [ unicast ] [ vpn-instance vpn-instance-name ] outlabel [ standby slot slot-number ] |
|
Display outgoing labels for BGP IPv4 unicast routes (in IRF mode). |
display bgp routing-table ipv4 [ unicast ] [ vpn-instance vpn-instance-name ] outlabel [ standby chassis chassis-number slot slot-number ] |
|
Display incoming labels for BGP VPNv4 routes. |
display bgp routing-table vpnv4 inlabel |
|
Display outgoing labels for BGP VPNv4 routes (in standalone mode). |
display bgp routing-table vpnv4 outlabel [ standby slot slot-number ] |
|
Display outgoing labels for BGP VPNv4 routes (in IRF mode). |
display bgp routing-table vpnv4 outlabel [ standby chassis chassis-number slot slot-number ] |
|
Display BGP VPNv4 address family update group information. |
display bgp update-group vpnv4 [ vpn-instance vpn-instance-name ] [ ip-address ] |
|
Display OSPF sham link information (in standalone mode). |
display ospf [ process-id ] sham-link [ area area-id ] [ standby slot slot-number ] |
|
Display OSPF sham link information (in IRF mode). |
display ospf [ process-id ] sham-link [ area area-id ] [ standby chassis chassis-number slot slot-number ] |
For more information about the display ip routing-table, display bgp group vpnv4, display bgp peer vpnv4, and display bgp update-group vpnv4 commands, see Layer 3—IP Routing Command Reference.
MPLS L3VPN configuration examples
Configuring basic MPLS L3VPN
Network requirements
CE 1 and CE 3 belong to VPN 1. CE 2 and CE 4 belong to VPN 2.
VPN 1 uses route target attribute 111:1. VPN 2 uses route target attribute 222:2. Users of different VPNs cannot access each other.
EBGP is used to exchange VPN routing information between CE and PE.
PEs use OSPF to communicate with each other and use MP-IBGP to exchange VPN routing information.
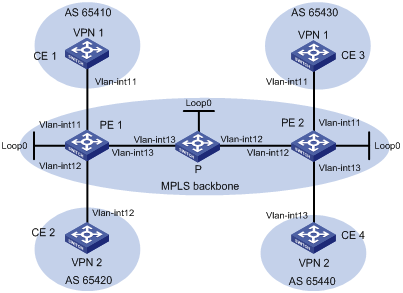
Table 12 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
Vlan-int11 |
10.1.1.1/24 |
P |
Loop0 |
2.2.2.9/32 |
|
PE 1 |
Loop0 |
1.1.1.9/32 |
|
Vlan-int12 |
172.2.1.1/24 |
|
|
Vlan-int11 |
10.1.1.2/24 |
|
Vlan-int13 |
172.1.1.2/24 |
|
|
Vlan-int13 |
172.1.1.1/24 |
PE 2 |
Loop0 |
3.3.3.9/32 |
|
|
Vlan-int12 |
10.2.1.2/24 |
|
Vlan-int12 |
172.2.1.2/24 |
|
CE 2 |
Vlan-int12 |
10.2.1.1/24 |
|
Vlan-int11 |
10.3.1.2/24 |
|
CE 3 |
Vlan-int11 |
10.3.1.1/24 |
|
Vlan-int13 |
10.4.1.2/24 |
|
CE 4 |
Vlan-int13 |
10.4.1.1/24 |
|
|
|
Configuration procedure
1. Configure an IGP on the MPLS backbone to ensure IP connectivity within the backbone:
# Configure PE 1.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 1.1.1.9 32
[PE1-LoopBack0] quit
[PE1] interface vlan-interface 13
[PE1-Vlan-interface13] ip address 172.1.1.1 24
[PE1-Vlan-interface13] quit
[PE1] ospf
[PE1-ospf-1] area 0
[PE1-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255
[PE1-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0
[PE1-ospf-1-area-0.0.0.0] quit
[PE1-ospf-1] quit
# Configure the P device.
<P> system-view
[P] interface loopback 0
[P-LoopBack0] ip address 2.2.2.9 32
[P-LoopBack0] quit
[P] interface vlan-interface 13
[P-Vlan-interface13] ip address 172.1.1.2 24
[P- Vlan-interface13] quit
[P] interface vlan-interface 12
[P-Vlan-interface12] ip address 172.2.1.1 24
[P-Vlan-interface12] quit
[P] ospf
[P-ospf-1] area 0
[P-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255
[P-ospf-1-area-0.0.0.0] network 172.2.1.0 0.0.0.255
[P-ospf-1-area-0.0.0.0] network 2.2.2.9 0.0.0.0
[P-ospf-1-area-0.0.0.0] quit
[P-ospf-1] quit
# Configure PE 2.
<PE2> system-view
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 3.3.3.9 32
[PE2-LoopBack0] quit
[PE2] interface vlan-interface 12
[PE2-Vlan-interface12] ip address 172.2.1.2 24
[PE2-Vlan-interface12] quit
[PE2] ospf
[PE2-ospf-1] area 0
[PE2-ospf-1-area-0.0.0.0] network 172.2.1.0 0.0.0.255
[PE2-ospf-1-area-0.0.0.0] network 3.3.3.9 0.0.0.0
[PE2-ospf-1-area-0.0.0.0] quit
[PE2-ospf-1] quit
# Execute the display ospf peer command to verify that OSPF adjacencies in Full state have been established between PE 1, P, and PE 2. Execute the display ip routing-table command to verify that the PEs have learned the routes to the loopback interfaces of each other. (Details not shown.)
2. Configure basic MPLS and MPLS LDP on the MPLS backbone to establish LDP LSPs:
# Configure PE 1.
[PE1] mpls lsr-id 1.1.1.9
[PE1] mpls ldp
[PE1-ldp] quit
[PE1] interface vlan-interface 13
[PE1-Vlan-interface13] mpls enable
[PE1-Vlan-interface13] mpls ldp enable
[PE1-Vlan-interface13] quit
# Configure the P device.
[P] mpls lsr-id 2.2.2.9
[P] mpls ldp
[P-ldp] quit
[P] interface vlan-interface 13
[P-Vlan-interface13] mpls enable
[P-Vlan-interface13] mpls ldp enable
[P-Vlan-interface13] quit
[P] interface vlan-interface 12
[P-Vlan-interface12] mpls enable
[P-Vlan-interface12] mpls ldp enable
[P-Vlan-interface12] quit
# Configure PE 2.
[PE2] mpls lsr-id 3.3.3.9
[PE2] mpls ldp
[PE2-ldp] quit
[PE2] interface vlan-interface 12
[PE2-Vlan-interface12] mpls enable
[PE2-Vlan-interface12] mpls ldp enable
[PE2-Vlan-interface12] quit
# Execute the display mpls ldp peer command to verify that LDP sessions in Operational state have been established between PE 1, P, and PE 2. Execute the display mpls ldp lsp command to verify that the LSPs have been established by LDP. (Details not shown.)
3. Configure VPN instances on PEs:
# Configure PE 1.
[PE1] reserve-vlan-interface 3000 to 3050
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 100:1
[PE1-vpn-instance-vpn1] vpn-target 111:1
[PE1-vpn-instance-vpn1] quit
[PE1] ip vpn-instance vpn2
[PE1-vpn-instance-vpn2] route-distinguisher 100:2
[PE1-vpn-instance-vpn2] vpn-target 222:2
[PE1-vpn-instance-vpn2] quit
[PE1] interface vlan-interface 11
[PE1-Vlan-interface11] ip binding vpn-instance vpn1
[PE1-Vlan-interface11] ip address 10.1.1.2 24
[PE1-Vlan-interface11] quit
[PE1] interface vlan-interface 12
[PE1-Vlan-interface12] ip binding vpn-instance vpn2
[PE1-Vlan-interface12] ip address 10.2.1.2 24
[PE1-Vlan-interface12] quit
# Configure PE 2.
[PE2] reserve-vlan-interface 3000 to 3050
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] route-distinguisher 200:1
[PE2-vpn-instance-vpn1] vpn-target 111:1
[PE2-vpn-instance-vpn1] quit
[PE2] ip vpn-instance vpn2
[PE2-vpn-instance-vpn2] route-distinguisher 200:2
[PE2-vpn-instance-vpn2] vpn-target 222:2
[PE2-vpn-instance-vpn2] quit
[PE2] interface vlan-interface 11
[PE2-Vlan-interface11] ip binding vpn-instance vpn1
[PE2-Vlan-interface11] ip address 10.3.1.2 24
[PE2-Vlan-interface11] quit
[PE2] interface vlan-interface 13
[PE2-Vlan-interface13] ip binding vpn-instance vpn2
[PE2-Vlan-interface13] ip address 10.4.1.2 24
[PE2-Vlan-interface13] quit
# Configure IP addresses for the CEs according to Figure 62. (Details not shown.)
# Execute the display ip vpn-instance command on the PEs to display the configuration of the VPN instance, for example, on PE 1.
[PE1] display ip vpn-instance
Total VPN-Instances configured : 2
VPN-Instance Name RD Create time
vpn1 100:1 2012/02/13 12:49:08
vpn2 100:2 2012/02/13 12:49:20
# Use the ping command on the PEs to verify that the PEs can ping their attached CEs, for example, on PE 1.
[PE1] ping -vpn-instance vpn1 10.1.1.1
Ping 10.1.1.1 (10.1.1.1): 56 data bytes, press CTRL_C to break
56 bytes from 10.1.1.1: icmp_seq=0 ttl=255 time=1.000 ms
56 bytes from 10.1.1.1: icmp_seq=1 ttl=255 time=2.000 ms
56 bytes from 10.1.1.1: icmp_seq=2 ttl=255 time=0.000 ms
56 bytes from 10.1.1.1: icmp_seq=3 ttl=255 time=1.000 ms
56 bytes from 10.1.1.1: icmp_seq=4 ttl=255 time=0.000 ms
--- Ping statistics for 10.1.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/0.800/2.000/0.748 ms
4. Establish EBGP peer relationships between PEs and CEs, and redistribute VPN routes into BGP:
# Configure CE 1.
<CE1> system-view
[CE1] bgp 65410
[CE1-bgp] peer 10.1.1.2 as-number 100
[CE1-bgp] address-family ipv4 unicast
[CE1-bgp-ipv4] peer 10.1.1.2 enable
[CE1-bgp-ipv4] import-route direct
[CE1-bgp-ipv4] quit
[CE1-bgp] quit
# Configure the other three CEs in the same way that CE 1 is configured. (Details not shown.)
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp] ip vpn-instance vpn1
[PE1-bgp-vpn1] peer 10.1.1.1 as-number 65410
[PE1-bgp-vpn1] address-family ipv4 unicast
[PE1-bgp-ipv4-vpn1] peer 10.1.1.1 enable
[PE1-bgp-ipv4-vpn1] import-route direct
[PE1-bgp-ipv4-vpn1] quit
[PE1-bgp-vpn1] quit
[PE1-bgp] ip vpn-instance vpn2
[PE1-bgp-vpn2] peer 10.2.1.1 as-number 65420
[PE1-bgp-vpn2] address-family ipv4 unicast
[PE1-bgp-ipv4-vpn1] peer 10.2.1.1 enable
[PE1-bgp-ipv4-vpn2] import-route direct
[PE1-bgp-ipv4-vpn2] quit
[PE1-bgp-vpn1] quit
[PE1-bgp] quit
# Configure PE 2 in the same way that PE 1 is configured. (Details not shown.)
# Execute the display bgp peer ipv4 vpn-instance command on the PEs to verify that a BGP peer relationship in Established state has been established between a PE and a CE. (Details not shown.)
5. Establish an MP-IBGP peer relationship between PEs:
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp] peer 3.3.3.9 as-number 100
[PE1-bgp] peer 3.3.3.9 connect-interface loopback 0
[PE1-bgp] address-family vpnv4
[PE1-bgp-vpnv4] peer 3.3.3.9 enable
[PE1-bgp-vpnv4] quit
[PE1-bgp] quit
# Configure PE 2.
[PE2] bgp 100
[PE2-bgp] peer 1.1.1.9 as-number 100
[PE2-bgp] peer 1.1.1.9 connect-interface loopback 0
[PE2-bgp] address-family vpnv4
[PE2-bgp-vpnv4] peer 1.1.1.9 enable
[PE2-bgp-vpnv4] quit
[PE2-bgp] quit
# Execute the display bgp peer vpnv4 command on the PEs to verify that a BGP peer relationship in Established state has been established between the PEs. (Details not shown.)
Verifying the configuration
# Execute the display ip routing-table vpn-instance command on the PEs.
[PE1] display ip routing-table vpn-instance vpn1
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.0/24 Direct 0 0 10.1.1.2 Vlan11
10.1.1.0/32 Direct 0 0 10.1.1.2 Vlan11
10.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.255/32 Direct 0 0 10.1.1.2 Vlan11
10.3.1.0/24 BGP 255 0 3.3.3.9 Vlan13
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
The output shows that PE 1 has a route to the remote CE. Output on PE 2 is similar.
# Verify that CEs of the same VPN can ping each other, whereas those of different VPNs cannot. For example, CE 1 can ping CE 3 (10.3.1.1) but cannot ping CE 4 (10.4.1.1). (Details not shown.)
Configuring a hub-spoke network
Network requirements
The Spoke-CEs cannot communicate directly. They can communicate only through Hub-CE.
Configure EBGP between the Spoke-CEs and Spoke-PEs and between Hub-CE and Hub-PE to exchange VPN routing information.
Configure OSPF between the Spoke-PEs and Hub-PE to implement communication between the PEs, and configure MP-IBGP between them to exchange VPN routing information.
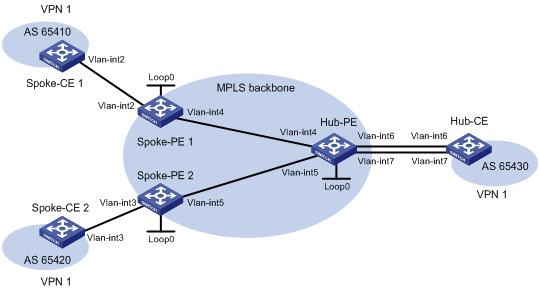
Table 13 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Spoke-CE 1 |
Vlan-int2 |
10.1.1.1/24 |
Hub-CE |
Vlan-int6 |
10.3.1.1/24 |
|
Spoke-PE 1 |
Loop0 |
1.1.1.9/32 |
|
Vlan-int7 |
10.4.1.1/24 |
|
|
Vlan-int2 |
10.1.1.2/24 |
Hub-PE |
Loop0 |
2.2.2.9/32 |
|
|
Vlan-int4 |
172.1.1.1/24 |
|
Vlan-int4 |
172.1.1.2/24 |
|
Spoke-CE 2 |
Vlan-int3 |
10.2.1.1/24 |
|
Vlan-int5 |
172.2.1.2/24 |
|
Spoke-PE 2 |
Loop0 |
3.3.3.9/32 |
|
Vlan-int6 |
10.3.1.2/24 |
|
|
Vlan-int3 |
10.2.1.2/24 |
|
Vlan-int7 |
10.4.1.2/24 |
|
|
Vlan-int5 |
172.2.1.1/24 |
|
|
|
Configuration procedure
1. Configure an IGP on the MPLS backbone to ensure IP connectivity within the backbone:
# Configure Spoke-PE 1.
<Spoke-PE1> system-view
[Spoke-PE1] interface loopback 0
[Spoke-PE1-LoopBack0] ip address 1.1.1.9 32
[Spoke-PE1-LoopBack0] quit
[Spoke-PE1] interface vlan-interface 4
[Spoke-PE1-Vlan-interface4] ip address 172.1.1.1 24
[Spoke-PE1-Vlan-interface4] quit
[Spoke-PE1] ospf
[Spoke-PE1-ospf-1] area 0
[Spoke-PE1-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255
[Spoke-PE1-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0
[Spoke-PE1-ospf-1-area-0.0.0.0] quit
[Spoke-PE1-ospf-1] quit
# Configure Spoke-PE 2.
<Spoke-PE2> system-view
[Spoke-PE2] interface loopback 0
[Spoke-PE2-LoopBack0] ip address 3.3.3.9 32
[Spoke-PE2-LoopBack0] quit
[Spoke-PE2] interface vlan-interface 5
[Spoke-PE2-Vlan-interface5] ip address 172.2.1.1 24
[Spoke-PE2-Vlan-interface5] quit
[Spoke-PE2] ospf
[Spoke-PE2-ospf-1] area 0
[Spoke-PE2-ospf-1-area-0.0.0.0] network 172.2.1.0 0.0.0.255
[Spoke-PE2-ospf-1-area-0.0.0.0] network 3.3.3.9 0.0.0.0
[Spoke-PE2-ospf-1-area-0.0.0.0] quit
[Spoke-PE2-ospf-1] quit
# Configure Hub-PE.
<Hub-PE> system-view
[Hub-PE] interface loopback 0
[Hub-PE-LoopBack0] ip address 2.2.2.9 32
[Hub-PE-LoopBack0] quit
[Hub-PE] interface vlan-interface 4
[Hub-PE-Vlan-interface4] ip address 172.1.1.2 24
[Hub-PE-Vlan-interface4] quit
[Hub-PE] interface vlan-interface 5
[Hub-PE-Vlan-interface5] ip address 172.2.1.2 24
[Hub-PE-Vlan-interface5] quit
[Hub-PE] ospf
[Hub-PE-ospf-1] area 0
[Hub-PE-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255
[Hub-PE-ospf-1-area-0.0.0.0] network 172.2.1.0 0.0.0.255
[Hub-PE-ospf-1-area-0.0.0.0] network 2.2.2.9 0.0.0.0
[Hub-PE-ospf-1-area-0.0.0.0] quit
[Hub-PE-ospf-1] quit
# Execute the display ospf peer command on the devices to verify that OSPF adjacencies in Full state have been established between Spoke-PE 1, Spoke-PE 2, and Hub-PE. Execute the display ip routing-table command on the devices to verify that the PEs have learned the routes to the loopback interfaces of each other. (Details not shown.)
2. Configure basic MPLS and MPLS LDP on the MPLS backbone to establish LDP LSPs:
# Configure Spoke-PE 1.
[Spoke-PE1] mpls lsr-id 1.1.1.9
[Spoke-PE1] mpls ldp
[Spoke-PE1-ldp] quit
[Spoke-PE1] interface vlan-interface 4
[Spoke-PE1-Vlan-interface4] mpls enable
[Spoke-PE1-Vlan-interface4] mpls ldp enable
[Spoke-PE1-Vlan-interface4] quit
# Configure Spoke-PE 2.
[Spoke-PE2] mpls lsr-id 3.3.3.9
[Spoke-PE2] mpls ldp
[Spoke-PE2-ldp] quit
[Spoke-PE2] interface vlan-interface 5
[Spoke-PE2-Vlan-interface5] mpls enable
[Spoke-PE2-Vlan-interface5] mpls ldp enable
[Spoke-PE2-Vlan-interface5] quit
# Configure Hub-PE.
[Hub-PE] mpls lsr-id 2.2.2.9
[Hub-PE] mpls ldp
[Hub-PE-ldp] quit
[Hub-PE] interface vlan-interface 4
[Hub-PE-Vlan-interface4] mpls enable
[Hub-PE-Vlan-interface4] mpls ldp enable
[Hub-PE-Vlan-interface4] quit
[Hub-PE] interface vlan-interface 5
[Hub-PE-Vlan-interface5] mpls enable
[Hub-PE-Vlan-interface5] mpls ldp enable
[Hub-PE-Vlan-interface5] quit
# Execute the display mpls ldp peer command on the devices to verify that LDP sessions in Operational state have been established between Spoke-PE 1, Spoke-PE 2, and Hub-PE. Execute the display mpls ldp lsp command on the devices to verify that the LSPs have been established by LDP. (Details not shown.)
3. Configure VPN instances on the Spoke-PEs and Hub-PE:
# Configure Spoke-PE 1.
[Spoke-PE1] reserve-vlan-interface 3000 to 3050
[Spoke-PE1] ip vpn-instance vpn1
[Spoke-PE1-vpn-instance-vpn1] route-distinguisher 100:1
[Spoke-PE1-vpn-instance-vpn1] vpn-target 111:1 import-extcommunity
[Spoke-PE1-vpn-instance-vpn1] vpn-target 222:2 export-extcommunity
[Spoke-PE1-vpn-instance-vpn1] quit
[Spoke-PE1] interface vlan-interface 2
[Spoke-PE1-Vlan-interface2] ip binding vpn-instance vpn1
[Spoke-PE1-Vlan-interface2] ip address 10.1.1.2 24
[Spoke-PE1-Vlan-interface2] quit
# Configure Spoke-PE 2.
[Spoke-PE2] reserve-vlan-interface 3000 to 3050
[Spoke-PE2] ip vpn-instance vpn1
[Spoke-PE2-vpn-instance-vpn1] route-distinguisher 100:2
[Spoke-PE2-vpn-instance-vpn1] vpn-target 111:1 import-extcommunity
[Spoke-PE2-vpn-instance-vpn1] vpn-target 222:2 export-extcommunity
[Spoke-PE2-vpn-instance-vpn1] quit
[Spoke-PE2] interface vlan-interface 3
[Spoke-PE2-Vlan-interface3] ip binding vpn-instance vpn1
[Spoke-PE2-Vlan-interface3] ip address 10.2.1.2 24
[Spoke-PE2-Vlan-interface3] quit
# Configure Hub-PE.
[Hub-PE] reserve-vlan-interface 3000 to 3050
[Hub-PE] ip vpn-instance vpn1-in
[Hub-PE-vpn-instance-vpn1-in] route-distinguisher 100:3
[Hub-PE-vpn-instance-vpn1-in] vpn-target 222:2 import-extcommunity
[Hub-PE-vpn-instance-vpn1-in] quit
[Hub-PE] ip vpn-instance vpn1-out
[Hub-PE-vpn-instance-vpn1-out] route-distinguisher 100:4
[Hub-PE-vpn-instance-vpn1-out] vpn-target 111:1 export-extcommunity
[Hub-PE-vpn-instance-vpn1-out] quit
[Hub-PE] interface vlan-interface 6
[Hub-PE-Vlan-interface6] ip binding vpn-instance vpn1-in
[Hub-PE-Vlan-interface6] ip address 10.3.1.2 24
[Hub-PE-Vlan-interface6] quit
[Hub-PE] interface vlan-interface 7
[Hub-PE-Vlan-interface7] ip binding vpn-instance vpn1-out
[Hub-PE-Vlan-interface7] ip address 10.4.1.2 24
[Hub-PE-Vlan-interface7] quit
# Configure IP addresses for the CEs according to Figure 63. (Details not shown.)
# Execute the display ip vpn-instance command on the PEs to display the configuration of the VPN instance, for example, on Spoke-PE 1.
[Spoke-PE1] display ip vpn-instance
Total VPN-Instances configured : 1
VPN-Instance Name RD Create time
vpn1 100:1 2009/04/08 10:55:07
# Use the ping command on the PEs to verify that the PEs can ping their attached CEs, for example, on Spoke-PE 1.
[Spoke-PE1] ping -vpn-instance vpn1 10.1.1.1
Ping 10.1.1.1 (10.1.1.1): 56 data bytes, press CTRL_C to break
56 bytes from 10.1.1.1: icmp_seq=0 ttl=128 time=1.913 ms
56 bytes from 10.1.1.1: icmp_seq=1 ttl=128 time=2.381 ms
56 bytes from 10.1.1.1: icmp_seq=2 ttl=128 time=1.707 ms
56 bytes from 10.1.1.1: icmp_seq=3 ttl=128 time=1.666 ms
56 bytes from 10.1.1.1: icmp_seq=4 ttl=128 time=2.710 ms
--- Ping statistics for 10.1.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 1.666/2.075/2.710/0.406 ms
4. Establish EBGP peer relationships between the PEs and CEs, and redistribute VPN routes into BGP:
# Configure Spoke-CE 1.
<Spoke-CE1> system-view
[Spoke-CE1] bgp 65410
[Spoke-CE1-bgp] peer 10.1.1.2 as-number 100
[Spoke-CE1-bgp] address-family ipv4
[Spoke-CE1-bgp-ipv4] peer 10.1.1.2 enable
[Spoke-CE1-bgp-ipv4] import-route direct
[Spoke-CE1-bgp-ipv4] quit
[Spoke-CE1-bgp] quit
# Configure Spoke-CE 2.
<Spoke-CE2> system-view
[Spoke-CE2] bgp 65420
[Spoke-CE2-bgp] peer 10.2.1.2 as-number 100
[Spoke-CE2-bgp] address-family ipv4
[Spoke-CE2-bgp-ipv4] peer 10.2.1.2 enable
[Spoke-CE2-bgp-ipv4] import-route direct
[Spoke-CE2-bgp-ipv4] quit
[Spoke-CE2-bgp] quit
# Configure Hub-CE.
<Hub-CE> system-view
[Hub-CE] bgp 65430
[Hub-CE-bgp] peer 10.3.1.2 as-number 100
[Hub-CE-bgp] peer 10.4.1.2 as-number 100
[Hub-CE-bgp] address-family ipv4
[Hub-CE-bgp-ipv4] peer 10.3.1.2 enable
[Hub-CE-bgp-ipv4] peer 10.4.1.2 enable
[Hub-CE-bgp-ipv4] import-route direct
[Hub-CE-bgp-ipv4] quit
[Hub-CE-bgp] quit
# Configure Spoke-PE 1.
[Spoke-PE1] bgp 100
[Spoke-PE1-bgp] ip vpn-instance vpn1
[Spoke-PE1-bgp-vpn1] peer 10.1.1.1 as-number 65410
[Spoke-PE1-bgp-vpn1] address-family ipv4
[Spoke-PE1-bgp-ipv4-vpn1] peer 10.1.1.1 enable
[Spoke-PE1-bgp-ipv4-vpn1] import-route direct
[Spoke-PE1-bgp-ipv4-vpn1] quit
[Spoke-PE1-bgp-vpn1] quit
[Spoke-PE1-bgp] quit
# Configure Spoke-PE 2.
[Spoke-PE2] bgp 100
[Spoke-PE2-bgp] ip vpn-instance vpn1
[Spoke-PE2-bgp-vpn1] peer 10.2.1.1 as-number 65420
[Spoke-PE2-bgp-vpn1] address-family ipv4
[Spoke-PE2-bgp-ipv4-vpn1] peer 10.2.1.1 enable
[Spoke-PE2-bgp-ipv4-vpn1] import-route direct
[Spoke-PE2-bgp-ipv4-vpn1] quit
[Spoke-PE2-bgp-vpn1] quit
[Spoke-PE2-bgp] quit
# Configure Hub-PE.
[Hub-PE] bgp 100
[Hub-PE-bgp] ip vpn-instance vpn1-in
[Hub-PE-bgp-vpn1-in] peer 10.3.1.1 as-number 65430
[Hub-PE-bgp-vpn1-in] address-family ipv4
[Hub-PE-bgp-ipv4-vpn1-in] peer 10.3.1.1 enable
[Hub-PE-bgp-ipv4-vpn1-in] import-route direct
[Hub-PE-bgp-ipv4-vpn1-in] quit
[Hub-PE-bgp-vpn1-in] quit
[Hub-PE-bgp] ip vpn-instance vpn1-out
[Hub-PE-bgp-vpn1-out] peer 10.4.1.1 as-number 65430
[Hub-PE-bgp-vpn1-out] address-family ipv4
[Hub-PE-bgp-ipv4-vpn1-out] peer 10.4.1.1 enable
[Hub-PE-bgp-ipv4-vpn1-out] peer 10.4.1.1 allow-as-loop 2
[Hub-PE-bgp-ipv4-vpn1-out] import-route direct
[Hub-PE-bgp-ipv4-vpn1-out] quit
[Hub-PE-bgp-vpn1-out] quit
[Hub-PE-bgp] quit
# Execute the display bgp peer ipv4 vpn-instance command on the PEs to verify that a BGP peer relationship in Established state has been established between a PE and a CE. (Details not shown.)
5. Establish an MP-IBGP peer relationship between the Spoke-PEs and Hub-PE:
# Configure Spoke-PE 1.
[Spoke-PE1] bgp 100
[Spoke-PE1-bgp] peer 2.2.2.9 as-number 100
[Spoke-PE1-bgp] peer 2.2.2.9 connect-interface loopback 0
[Spoke-PE1-bgp] address-family vpnv4
[Spoke-PE1-bgp-vpnv4] peer 2.2.2.9 enable
[Spoke-PE1-bgp-vpnv4] quit
[Spoke-PE1-bgp] quit
# Configure Spoke-PE 2.
[Spoke-PE2] bgp 100
[Spoke-PE2-bgp] peer 2.2.2.9 as-number 100
[Spoke-PE2-bgp] peer 2.2.2.9 connect-interface loopback 0
[Spoke-PE2-bgp] address-family vpnv4
[Spoke-PE2-bgp-vpnv4] peer 2.2.2.9 enable
[Spoke-PE2-bgp-vpnv4] quit
[Spoke-PE2-bgp] quit
# Configure Hub-PE.
[Hub-PE] bgp 100
[Hub-PE-bgp] peer 1.1.1.9 as-number 100
[Hub-PE-bgp] peer 1.1.1.9 connect-interface loopback 0
[Hub-PE-bgp] peer 3.3.3.9 as-number 100
[Hub-PE-bgp] peer 3.3.3.9 connect-interface loopback 0
[Hub-PE-bgp] address-family vpnv4
[Hub-PE-bgp-vpnv4] peer 1.1.1.9 enable
[Hub-PE-bgp-vpnv4] peer 3.3.3.9 enable
[Hub-PE-bgp-vpnv4] quit
[Hub-PE-bgp] quit
# Execute the display bgp peer vpnv4 command on the PEs to verify that a BGP peer relationship in Established state has been established between the PEs. (Details not shown.)
Verifying the configuration
# Execute the display ip routing-table vpn-instance command on the PEs to display the routes to the CEs. This example uses Spoke-PE 1 to verify that the next hop of the route from a Spoke-PE to its connected Spoke-CE is Hub-PE.
[Spoke-PE1] display ip routing-table vpn-instance vpn1
Destinations : 15 Routes : 15
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.0/24 Direct 0 0 10.1.1.2 Vlan2
10.1.1.0/32 Direct 0 0 10.1.1.2 Vlan2
10.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.255/32 Direct 0 0 10.1.1.2 Vlan2
10.2.1.0/24 BGP 255 0 2.2.2.9 Vlan4
10.3.1.0/24 BGP 255 0 2.2.2.9 Vlan4
10.4.1.0/24 BGP 255 0 2.2.2.9 Vlan4
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Verify that Spoke-CE 1 and Spoke-CE 2 can ping each other. The TTL value indicates that traffic from Spoke-CE 1 to Spoke-CE 2 passes six hops (255-250+1) and is forwarded through Hub-CE. This example uses Spoke-CE 1 to verify their connectivity.
[Spoke-CE1] ping 10.2.1.1
Ping 10.2.1.1 (10.2.1.1): 56 data bytes, press CTRL_C to break
56 bytes from 10.2.1.1: icmp_seq=0 ttl=250 time=1.000 ms
56 bytes from 10.2.1.1: icmp_seq=1 ttl=250 time=2.000 ms
56 bytes from 10.2.1.1: icmp_seq=2 ttl=250 time=0.000 ms
56 bytes from 10.2.1.1: icmp_seq=3 ttl=250 time=1.000 ms
56 bytes from 10.2.1.1: icmp_seq=4 ttl=250 time=0.000 ms
--- Ping statistics for 10.2.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/0.800/2.000/0.748 ms
Configuring MPLS L3VPN inter-AS option A
Network requirements
CE 1 and CE 2 belong to the same VPN. CE 1 accesses the network through PE 1 in AS 100, and CE 2 accesses the network through PE 2 in AS 200.
Configure MPLS L3VPN inter-AS option A, and use the VRF-to-VRF method to manage VPN routes.
Run OSPF on the MPLS backbone in each AS.
Figure 64 Network diagram

Table 14 Interface and IP address assignment
|
Interface |
IP address |
Device |
Interface |
IP address |
|
|
CE 1 |
Vlan-int12 |
10.1.1.1/24 |
CE 2 |
Vlan-int12 |
10.2.1.1/24 |
|
PE 1 |
Loop0 |
1.1.1.9/32 |
PE 2 |
Loop0 |
4.4.4.9/32 |
|
|
Vlan-int12 |
10.1.1.2/24 |
|
Vlan-int12 |
10.2.1.2/24 |
|
|
Vlan-int11 |
172.1.1.2/24 |
|
Vlan-int11 |
162.1.1.2/24 |
|
ASBR-PE 1 |
Loop0 |
2.2.2.9/32 |
ASBR-PE 2 |
Loop0 |
3.3.3.9/32 |
|
|
Vlan-int11 |
172.1.1.1/24 |
|
Vlan-int11 |
162.1.1.1/24 |
|
|
Vlan-int12 |
192.1.1.1/24 |
|
Vlan-int12 |
192.1.1.2/24 |
Configuration procedure
1. Configure IGP on the MPLS backbone to implement the connectivity in the backbone:
This example uses OSPF. (Details not shown.)
# Execute the display ospf peer command to verify that each ASBR-PE has established an OSPF adjacency in Full state with the PE in the same AS, and that PEs and ASBR-PEs in the same AS have learned the routes to the loopback interfaces of each other. Verify that each ASBR-PE and the PE in the same AS can ping each other. (Details not shown.)
2. Configure basic MPLS and MPLS LDP on the MPLS backbone to establish LDP LSPs:
# Configure basic MPLS on PE 1, and enable MPLS LDP on the interface connected to ASBR-PE 1.
<PE1> system-view
[PE1] mpls lsr-id 1.1.1.9
[PE1] mpls ldp
[PE1-ldp] quit
[PE1] interface vlan-interface 11
[PE1-Vlan-interface11] mpls enable
[PE1-Vlan-interface11] mpls ldp enable
[PE1-Vlan-interface11] quit
# Configure basic MPLS on ASBR-PE 1, and enable MPLS LDP on the interface connected to PE 1.
<ASBR-PE1> system-view
[ASBR-PE1] mpls lsr-id 2.2.2.9
[ASBR-PE1] mpls ldp
[ASBR-PE1-ldp] quit
[ASBR-PE1] interface vlan-interface 11
[ASBR-PE1-Vlan-interface11] mpls enable
[ASBR-PE1-Vlan-interface11] mpls ldp enable
[ASBR-PE1-Vlan-interface11] quit
# Configure basic MPLS on ASBR-PE 2, and enable MPLS LDP on the interface connected to PE 2.
<ASBR-PE2> system-view
[ASBR-PE2] mpls lsr-id 3.3.3.9
[ASBR-PE2] mpls ldp
[ASBR-PE2-ldp] quit
[ASBR-PE2] interface vlan-interface 11
[ASBR-PE2-Vlan-interface11] mpls enable
[ASBR-PE2-Vlan-interface11] mpls ldp enable
[ASBR-PE2-Vlan-interface11] quit
# Configure basic MPLS on PE 2, and enable MPLS LDP on the interface connected to ASBR-PE 2.
<PE2> system-view
[PE2] mpls lsr-id 4.4.4.9
[PE2] mpls ldp
[PE2-ldp] quit
[PE2] interface vlan-interface 11
[PE2-Vlan-interface11] mpls enable
[PE2-Vlan-interface11] mpls ldp enable
[PE2-Vlan-interface11] quit
# Execute the display mpls ldp peer command on the devices to verify that the session status is Operational, and that each PE and the ASBR-PE in the same AS have established a neighbor relationship. (Details not shown.)
3. Configure VPN instances on PEs:
For the same VPN, the route targets for the VPN instance on the PE must match those for the VPN instance on the ASBR-PE in the same AS. This is not required for PEs in different ASs.
# Configure CE 1.
<CE1> system-view
[CE1] interface vlan-interface 12
[CE1-Vlan-interface12] ip address 10.1.1.1 24
[CE1-Vlan-interface12] quit
# Configure PE 1.
[PE1] reserve-vlan-interface 3000 to 3050
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 100:1
[PE1-vpn-instance-vpn1] vpn-target 100:1 both
[PE1-vpn-instance-vpn1] quit
[PE1] interface vlan-interface 12
[PE1-Vlan-interface12] ip binding vpn-instance vpn1
[PE1-Vlan-interface12] ip address 10.1.1.2 24
[PE1-Vlan-interface12] quit
# Configure CE 2.
<CE2> system-view
[CE2] interface vlan-interface 12
[CE2-Vlan-interface12] ip address 10.2.1.1 24
[CE2-Vlan-interface12] quit
# Configure PE 2.
[PE2] reserve-vlan-interface 3000 to 3050
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance] route-distinguisher 200:2
[PE2-vpn-instance] vpn-target 200:1 both
[PE2-vpn-instance] quit
[PE2] interface vlan-interface 12
[PE2-Vlan-interface12] ip binding vpn-instance vpn1
[PE2-Vlan-interface12] ip address 10.2.1.2 24
[PE2-Vlan-interface12] quit
# On ASBR-PE 1, create a VPN instance, and bind the instance to the interface connected to ASBR-PE 2. ASBR-PE 1 considers ASBR-PE 2 to be its CE.
[ASBR-PE1] reserve-vlan-interface 3000 to 3050
[ASBR-PE1] ip vpn-instance vpn1
[ASBR-PE1-vpn-instance-vpn1] route-distinguisher 100:1
[ASBR-PE1-vpn-instance-vpn1] vpn-target 100:1 both
[ASBR-PE1-vpn-instance-vpn1] quit
[ASBR-PE1] interface vlan-interface 12
[ASBR-PE1-Vlan-interface12] ip binding vpn-instance vpn1
[ASBR-PE1-Vlan-interface12] ip address 192.1.1.1 24
[ASBR-PE1-Vlan-interface12] quit
# On ASBR-PE 2, create a VPN instance, and bind the instance to the interface connected to ASBR-PE 1. ASBR-PE 2 considers ASBR-PE 1 to be its CE.
[ASBR-PE2] reserve-vlan-interface 3000 to 3050
[ASBR-PE2] ip vpn-instance vpn1
[ASBR-PE2-vpn-vpn-vpn1] route-distinguisher 200:1
[ASBR-PE2-vpn-vpn-vpn1] vpn-target 200:1 both
[ASBR-PE2-vpn-vpn-vpn1] quit
[ASBR-PE2] interface vlan-interface 12
[ASBR-PE2-Vlan-interface12] ip binding vpn-instance vpn1
[ASBR-PE2-Vlan-interface12] ip address 192.1.1.2 24
[ASBR-PE2-Vlan-interface12] quit
# Execute the display ip vpn-instance command to display VPN instance configurations. Verify that the PEs can ping the CEs, and the ASBR-PEs can ping each other. (Details not shown.)
4. Establish EBGP peer relationships between PEs and CEs, and redistribute VPN routes into BGP:
# Configure CE 1.
[CE1] bgp 65001
[CE1-bgp] peer 10.1.1.2 as-number 100
[CE1-bgp] address-family ipv4 unicast
[CE1-bgp-ipv4] peer 10.1.1.2 enable
[CE1-bgp-ipv4] import-route direct
[CE1-bgp-ipv4] quit
[CE1-bgp] quit
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp] ip vpn-instance vpn1
[PE1-bgp-vpn1] peer 10.1.1.1 as-number 65001
[PE1-bgp-vpn1] address-family ipv4 unicast
[PE1-bgp-ipv4-vpn1] peer 10.1.1.1 enable
[PE1-bgp-ipv4-vpn1] quit
[PE1-bgp-vpn1] quit
[PE1-bgp] quit
# Configure CE 2.
[CE2] bgp 65002
[CE2-bgp] peer 10.2.1.2 as-number 200
[CE2-bgp] address-family ipv4 unicast
[CE2-bgp-ipv4] peer 10.2.1.2 enable
[CE2-bgp-ipv4] import-route direct
[CE2-bgp-ipv4] quit
[CE2-bgp] quit
# Configure PE 2.
[PE2] bgp 200
[PE2-bgp] ip vpn-instance vpn1
[PE2-bgp-vpn1] peer 10.2.1.1 as-number 65002
[PE2-bgp-vpn1] address-family ipv4 unicast
[PE2-bgp-ipv4-vpn1] peer 10.2.1.1 enable
[PE2-bgp-ipv4-vpn1] quit
[PE2-bgp-vpn1] quit
[PE2-bgp] quit
5. Establish an MP-IBGP peer relationship between each PE and the ASBR-PE in the same AS, and an EBGP peer relationship between the ASBR-PEs:
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp] peer 2.2.2.9 as-number 100
[PE1-bgp] peer 2.2.2.9 connect-interface loopback 0
[PE1-bgp] address-family vpnv4
[PE1-bgp-vpnv4] peer 2.2.2.9 enable
[PE1-bgp-vpnv4] peer 2.2.2.9 next-hop-local
[PE1-bgp-vpnv4] quit
[PE1-bgp] quit
# Configure ASBR-PE 1.
[ASBR-PE1] bgp 100
[ASBR-PE1-bgp] ip vpn-instance vpn1
[ASBR-PE1-bgp-vpn1] peer 192.1.1.2 as-number 200
[ASBR-PE1-bgp-vpn1] address-family ipv4 unicast
[ASBR-PE1-bgp-ipv4-vpn1] peer 192.1.1.2 enable
[ASBR-PE1-bgp-ipv4-vpn1] quit
[ASBR-PE1-bgp-vpn1] quit
[ASBR-PE1-bgp] peer 1.1.1.9 as-number 100
[ASBR-PE1-bgp] peer 1.1.1.9 connect-interface loopback 0
[ASBR-PE1-bgp] address-family vpnv4
[ASBR-PE1-bgp-vpnv4] peer 1.1.1.9 enable
[ASBR-PE1-bgp-vpnv4] peer 1.1.1.9 next-hop-local
[ASBR-PE1-bgp-vpnv4] quit
[ASBR-PE1-bgp] quit
# Configure ASBR-PE 2.
[ASBR-PE2] bgp 200
[ASBR-PE2-bgp] ip vpn-instance vpn1
[ASBR-PE2-bgp-vpn1] peer 192.1.1.1 as-number 100
[ASBR-PE2-bgp-vpn1] address-family ipv4 unicast
[ASBR-PE2-bgp-ipv4-vpn1] peer 192.1.1.1 enable
[ASBR-PE2-bgp-ipv4-vpn1] quit
[ASBR-PE2-bgp-vpn1] quit
[ASBR-PE2-bgp] peer 4.4.4.9 as-number 200
[ASBR-PE2-bgp] peer 4.4.4.9 connect-interface loopback 0
[ASBR-PE2-bgp] address-family vpnv4
[ASBR-PE2-bgp-vpnv4] peer 4.4.4.9 enable
[ASBR-PE2-bgp-vpnv4] peer 4.4.4.9 next-hop-local
[ASBR-PE2-bgp-vpnv4] quit
[ASBR-PE2-bgp] quit
# Configure PE 2.
[PE2] bgp 200
[PE2-bgp] peer 3.3.3.9 as-number 200
[PE2-bgp] peer 3.3.3.9 connect-interface loopback 0
[PE2-bgp] address-family vpnv4
[PE2-bgp-vpnv4] peer 3.3.3.9 enable
[PE2-bgp-vpnv4] peer 3.3.3.9 next-hop-local
[PE2-bgp-vpnv4] quit
[PE2-bgp] quit
Verifying the configuration
# Verify that the CEs can learn the interface routes from each other and ping each other. (Details not shown.)
Configuring MPLS L3VPN inter-AS option B
Network requirements
Site 1 and Site 2 belong to the same VPN. CE 1 of Site 1 accesses the network through PE 1 in AS 100, and CE 2 of Site 2 accesses the network through PE 2 in AS 600. PEs in the same AS run IS-IS.
PE 1 and ASBR-PE 1 exchange VPNv4 routes through MP-IBGP. PE 2 and ASBR-PE 2 exchange VPNv4 routes through MP-IBGP. ASBR-PE 1 and ASBR-PE 2 exchange VPNv4 routes through MP-EBGP.
ASBRs do not perform route target filtering of received VPN-IPv4 routes.
Figure 65 Network diagram
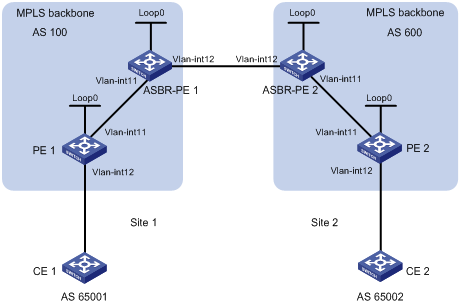
Table 15 Interface and IP address assignment
|
Interface |
IP address |
Device |
Interface |
IP address |
|
|
PE 1 |
Loop0 |
2.2.2.9/32 |
PE 2 |
Loop0 |
5.5.5.9/32 |
|
|
Vlan-int12 |
30.0.0.1/8 |
|
Vlan-int12 |
20.0.0.1/8 |
|
|
Vlan-int11 |
1.1.1.2/8 |
|
Vlan-int11 |
9.1.1.2/8 |
|
ASBR-PE 1 |
Loop0 |
3.3.3.9/32 |
ASBR-PE 2 |
Loop0 |
4.4.4.9/32 |
|
|
Vlan-int11 |
1.1.1.1/8 |
|
Vlan-int11 |
9.1.1.1/8 |
|
|
Vlan-int12 |
11.0.0.2/8 |
|
Vlan-int12 |
11.0.0.1/8 |
Configuration procedure
1. Configure PE 1:
# Configure IS-IS on PE 1.
<PE1> system-view
[PE1] isis 1
[PE1-isis-1] network-entity 10.111.111.111.111.00
[PE1-isis-1] quit
# Configure the LSR ID, and enable MPLS and LDP.
[PE1] mpls lsr-id 2.2.2.9
[PE1] mpls ldp
[PE1-ldp] quit
# Configure interface VLAN-interface 11, and enable IS-IS, MPLS, and LDP on the interface.
[PE1] interface vlan-interface 11
[PE1-Vlan-interface11] ip address 1.1.1.2 255.0.0.0
[PE1-Vlan-interface11] isis enable 1
[PE1-Vlan-interface11] mpls enable
[PE1-Vlan-interface11] mpls ldp enable
[PE1-Vlan-interface11] quit
# Configure interface Loopback 0, and enable IS-IS on it.
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 2.2.2.9 32
[PE1-LoopBack0] isis enable 1
[PE1-LoopBack0] quit
# Create VPN instance vpn1, and configure the RD and route target attributes.
[PE1] reserve-vlan-interface 3000 to 3050
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 11:11
[PE1-vpn-instance-vpn1] vpn-target 1:1 2:2 3:3 import-extcommunity
[PE1-vpn-instance-vpn1] vpn-target 3:3 export-extcommunity
[PE1-vpn-instance-vpn1] quit
# Bind the interface connected to CE 1 to the created VPN instance.
[PE1] interface vlan-interface 12
[PE1-Vlan-interface12] ip binding vpn-instance vpn1
[PE1-Vlan-interface12] ip address 30.0.0.1 8
[PE1-Vlan-interface12] quit
# Enable BGP on PE 1.
[PE1] bgp 100
# Configure IBGP peer 3.3.3.9 as a VPNv4 peer.
[PE1-bgp] peer 3.3.3.9 as-number 100
[PE1-bgp] peer 3.3.3.9 connect-interface loopback 0
[PE1-bgp] address-family vpnv4
[PE1-bgp-vpnv4] peer 3.3.3.9 enable
[PE1-bgp-vpnv4] quit
# Redistribute direct routes to the VPN routing table of vpn1.
[PE1-bgp] ip vpn-instance vpn1
[PE1-bgp-vpn1] address-family ipv4 unicast
[PE1-bgp-ipv4-vpn1] import-route direct
[PE1-bgp-ipv4-vpn1] quit
[PE1-bgp-vpn1] quit
[PE1-bgp] quit
2. Configure ASBR-PE 1:
# Enable IS-IS on ASBR-PE 1.
<ASBR-PE1> system-view
[ASBR-PE1] isis 1
[ASBR-PE1-isis-1] network-entity 10.222.222.222.222.00
[ASBR-PE1-isis-1] quit
# Configure the LSR ID, and enable MPLS and LDP.
[ASBR-PE1] mpls lsr-id 3.3.3.9
[ASBR-PE1] mpls ldp
[ASBR-PE1-ldp] quit
# Configure interface VLAN-interface 11, and enable IS-IS, MPLS, and LDP on the interface.
[ASBR-PE1] interface vlan-interface11
[ASBR-PE1-Vlan-interface11] ip address 1.1.1.1 255.0.0.0
[ASBR-PE1-Vlan-interface11] isis enable 1
[ASBR-PE1-Vlan-interface11] mpls enable
[ASBR-PE1-Vlan-interface11] mpls ldp enable
[ASBR-PE1-Vlan-interface11] quit
# Configure interface VLAN-interface 12, and enable MPLS on it.
[ASBR-PE1] interface vlan-interface 12
[ASBR-PE1-Vlan-interface12] ip address 11.0.0.2 255.0.0.0
[ASBR-PE1-Vlan-interface12] mpls enable
[ASBR-PE1-Vlan-interface12] quit
# Configure interface Loopback 0, and enable IS-IS on it.
[ASBR-PE1] interface loopback 0
[ASBR-PE1-LoopBack0] ip address 3.3.3.9 32
[ASBR-PE1-LoopBack0] isis enable 1
[ASBR-PE1-LoopBack0] quit
# Enable BGP on ASBR-PE 1.
[ASBR-PE1] bgp 100
[ASBR-PE1-bgp] peer 2.2.2.9 as-number 100
[ASBR-PE1-bgp] peer 2.2.2.9 connect-interface loopback 0
[ASBR-PE1-bgp] peer 11.0.0.1 as-number 600
[ASBR-PE1-bgp] peer 11.0.0.1 connect-interface vlan-interface 12
# Disable route target based filtering of received VPNv4 routes.
[ASBR-PE1-bgp] address-family vpnv4
[ASBR-PE1-bgp-vpnv4] undo policy vpn-target
# Configure both IBGP peer 2.2.2.0 and EBGP peer 11.0.0.1 as VPNv4 peers.
[ASBR-PE1-bgp-vpnv4] peer 11.0.0.1 enable
[ASBR-PE1-bgp-vpnv4] peer 2.2.2.9 enable
[ASBR-PE1-bgp-vpnv4] quit
3. Configure ASBR-PE 2:
# Enable IS-IS on ASBR-PE 2.
<ASBR-PE2> system-view
[ASBR-PE2] isis 1
[ASBR-PE2-isis-1] network-entity 10.222.222.222.222.00
[ASBR-PE2-isis-1] quit
# Configure the LSR ID, and enable MPLS and LDP.
[ASBR-PE2] mpls lsr-id 4.4.4.9
[ASBR-PE2] mpls ldp
[ASBR-PE2-ldp] quit
# Configure interface VLAN-interface 11, and enable IS-IS, MPLS, and LDP on the interface.
[ASBR-PE2] interface vlan-interface 11
[ASBR-PE2-Vlan-interface11] ip address 9.1.1.1 255.0.0.0
[ASBR-PE2-Vlan-interface11] isis enable 1
[ASBR-PE2-Vlan-interface11] mpls enable
[ASBR-PE2-Vlan-interface11] mpls ldp enable
[ASBR-PE2-Vlan-interface11] quit
# Configure interface VLAN-interface 12, and enable MPLS on it.
[ASBR-PE2] interface vlan-interface 12
[ASBR-PE2-Vlan-interface12] ip address 11.0.0.1 255.0.0.0
[ASBR-PE2-Vlan-interface12] mpls enable
[ASBR-PE2-Vlan-interface12] quit
# Configure interface Loopback 0, and enable IS-IS on it.
[ASBR-PE2] interface loopback 0
[ASBR-PE2-LoopBack0] ip address 4.4.4.9 32
[ASBR-PE2-LoopBack0] isis enable 1
[ASBR-PE2-LoopBack0] quit
# Enable BGP on ASBR-PE 2.
[ASBR-PE2] bgp 600
[ASBR-PE2-bgp] peer 11.0.0.2 as-number 100
[ASBR-PE2-bgp] peer 11.0.0.2 connect-interface vlan-interface 12
[ASBR-PE2-bgp] peer 5.5.5.9 as-number 600
[ASBR-PE2-bgp] peer 5.5.5.9 connect-interface loopback 0
# Disable route target based filtering of received VPNv4 routes.
[ASBR-PE2-bgp] address-family vpnv4
[ASBR-PE2-bgp-vpnv4] undo policy vpn-target
# Configure both IBGP peer 5.5.5.9 and EBGP peer 11.0.0.2 as VPNv4 peers.
[ASBR-PE2-bgp-vpnv4] peer 11.0.0.2 enable
[ASBR-PE2-bgp-vpnv4] peer 5.5.5.9 enable
[ASBR-PE2-bgp-vpnv4] quit
[ASBR-PE2-bgp] quit
4. Configure PE 2:
# Enable IS-IS on PE 2.
<PE2> system-view
[PE2] isis 1
[PE2-isis-1] network-entity 10.111.111.111.111.00
[PE2-isis-1] quit
# Configure the LSR ID, and enable MPLS and LDP.
[PE2] mpls lsr-id 5.5.5.9
[PE2] mpls ldp
[PE2-ldp] quit
# Configure interface VLAN-interface 11, and enable IS-IS, MPLS, and LDP on the interface.
[PE2] interface vlan-interface 11
[PE2-Vlan-interface11] ip address 9.1.1.2 255.0.0.0
[PE2-Vlan-interface11] isis enable 1
[PE2-Vlan-interface11] mpls enable
[PE2-Vlan-interface11] mpls ldp enable
[PE2-Vlan-interface11] quit
# Configure interface Loopback 0, and enable IS-IS on it.
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 5.5.5.9 32
[PE2-LoopBack0] isis enable 1
[PE2-LoopBack0] quit
# Create VPN instance vpn1, and configure the RD and route target attributes.
[PE2] reserve-vlan-interface 3000 to 3050
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] route-distinguisher 12:12
[PE2-vpn-instance-vpn1] vpn-target 1:1 2:2 3:3 import-extcommunity
[PE2-vpn-instance-vpn1] vpn-target 3:3 export-extcommunity
[PE2-vpn-instance-vpn1] quit
# Bind the interface connected with CE 2 to the created VPN instance.
[PE2] interface vlan-interface12
[PE2-Vlan-interface12] ip binding vpn-instance vpn1
[PE2-Vlan-interface12] ip address 20.0.0.1 8
[PE2-Vlan-interface12] quit
# Enable BGP on PE 2.
[PE2] bgp 600
# Configure IBGP peer 4.4.4.9 as a VPNv4 peer.
[PE2-bgp] peer 4.4.4.9 as-number 600
[PE2-bgp] peer 4.4.4.9 connect-interface loopback 0
[PE2-bgp] address-family vpnv4
[PE2-bgp-vpnv4] peer 4.4.4.9 enable
[PE2-bgp-vpnv4] quit
# Redistribute direct routes to the VPN routing table of vpn1.
[PE2-bgp] ip vpn-instance vpn1
[PE2-bgp-vpn1] address-family ipv4 unicast
[PE2-bgp-ipv4-vpn1] import-route direct
[PE2-bgp-ipv4-vpn1] quit
[PE2-bgp-vpn1] quit
[PE2-bgp] quit
Verifying the configuration
# Verify that PE 1 and PE 2 can ping each other.
[PE1] ping -a 30.0.0.1 -vpn-instance vpn1 20.0.0.1
Ping 20.0.0.1 (20.0.0.1) from 30.0.0.1: 56 data bytes, press CTRL_C to break
56 bytes from 20.0.0.1: icmp_seq=0 ttl=255 time=1.208 ms
56 bytes from 20.0.0.1: icmp_seq=1 ttl=255 time=0.867 ms
56 bytes from 20.0.0.1: icmp_seq=2 ttl=255 time=0.551 ms
56 bytes from 20.0.0.1: icmp_seq=3 ttl=255 time=0.566 ms
56 bytes from 20.0.0.1: icmp_seq=4 ttl=255 time=0.570 ms
--- Ping statistics for 20.0.0.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.551/0.752/1.208/0.257 ms
Configuring MPLS L3VPN inter-AS option C
Network requirements
Site 1 and Site 2 belong to the same VPN. Site 1 accesses the network through PE 1 in AS 100, and Site 2 accesses the network through PE 2 in AS 600. PEs in the same AS run IS-IS.
PE 1 and ASBR-PE 1 exchange labeled IPv4 routes through IBGP. PE 2 and ASBR-PE 2 exchange labeled IPv4 routes through IBGP. PE 1 and PE 2 exchange VPNv4 routes through MP-EBGP.
ASBR-PE 1 and ASBR-PE 2 use their respective routing policies and label routes received from each other.
ASBR-PE 1 and ASBR-PE 2 use EBGP to exchange labeled IPv4 routes.
Figure 66 Network diagram
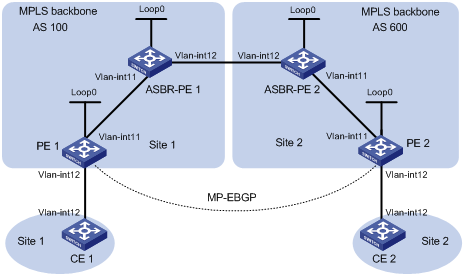
Table 16 Interface and IP address assignment
|
Interface |
IP address |
Device |
Interface |
IP address |
|
|
PE 1 |
Loop0 |
2.2.2.9/32 |
PE 2 |
Loop0 |
5.5.5.9/32 |
|
|
Vlan-int11 |
1.1.1.2/8 |
|
Vlan-int11 |
9.1.1.2/8 |
|
|
Vlan-int12 |
30.0.0.1/24 |
|
Vlan-int12 |
20.0.0.1/24 |
|
ASBR-PE 1 |
Loop0 |
3.3.3.9/32 |
ASBR-PE 2 |
Loop0 |
4.4.4.9/32 |
|
|
Vlan-int11 |
1.1.1.1/8 |
|
Vlan-int11 |
9.1.1.1/8 |
|
|
Vlan-int12 |
11.0.0.2/8 |
|
Vlan-int12 |
11.0.0.1/8 |
|
CE 1 |
Vlan-int12 |
30.0.0.2/24 |
CE 2 |
Vlan-int12 |
20.0.0.2/24 |
Configuration procedure
1. Configure CE 1:
# Configure an IP address for VLAN-interface 12.
<CE1> system-view
[CE1] interface vlan-interface 12
[CE1-Vlan-interface12] ip address 30.0.0.2 24
[CE1-Vlan-interface12] quit
# Configure 30.0.0.1 as an EBGP peer, and redistribute direct routes.
[CE1] bgp 65001
[CE1-bgp] peer 30.0.0.1 as-number 100
[CE1-bgp] address-family ipv4 unicast
[CE1-bgp-ipv4] peer 30.0.0.1 enable
[CE1-bgp-ipv4] import-route direct
[CE1-bgp-ipv4] quit
[CE1-bgp] quit
2. Configure PE 1:
# Configure IS-IS on PE 1.
<PE1> system-view
[PE1] isis 1
[PE1-isis-1] network-entity 10.111.111.111.111.00
[PE1-isis-1] quit
# Configure the LSR ID, and enable MPLS and LDP.
[PE1] mpls lsr-id 2.2.2.9
[PE1] mpls ldp
[PE1-ldp] quit
# Configure interface VLAN-interface 11, and enable IS-IS, MPLS, and LDP on the interface.
[PE1] interface vlan-interface 11
[PE1-Vlan-interface11] ip address 1.1.1.2 255.0.0.0
[PE1-Vlan-interface11] isis enable 1
[PE1-Vlan-interface11] mpls enable
[PE1-Vlan-interface11] mpls ldp enable
[PE1-Vlan-interface11] quit
# Configure interface Loopback 0, and enable IS-IS on it.
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 2.2.2.9 32
[PE1-LoopBack0] isis enable 1
[PE1-LoopBack0] quit
# Create VPN instance vpn1, and configure the RD and route target attributes.
[PE1] reserve-vlan-interface 3000 to 3050
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 11:11
[PE1-vpn-instance-vpn1] vpn-target 1:1 2:2 3:3 import-extcommunity
[PE1-vpn-instance-vpn1] vpn-target 3:3 export-extcommunity
[PE1-vpn-instance-vpn1] quit
# Associate interface VLAN-interface 12 with VPN instance vpn1, and specify an IP address for the interface.
[PE1] interface vlan-interface 12
[PE1-Vlan-interface12] ip binding vpn-instance vpn1
[PE1-Vlan-interface12] ip address 30.0.0.1 24
[PE1-Vlan-interface12] quit
# Enable BGP on PE 1.
[PE1] bgp 100
# Enable the capability to advertise labeled routes to IBGP peer 3.3.3.9 and to receive labeled routes from the peer.
[PE1-bgp] peer 3.3.3.9 as-number 100
[PE1-bgp] peer 3.3.3.9 connect-interface loopback 0
[PE1-bgp] address-family ipv4 unicast
[PE1-bgp-ipv4] peer 3.3.3.9 enable
[PE1-bgp-ipv4] peer 3.3.3.9 label-route-capability
[PE1-bgp-ipv4] quit
# Configure the maximum hop count from PE 1 to EBGP peer 5.5.5.9 as 10.
[PE1-bgp] peer 5.5.5.9 as-number 600
[PE1-bgp] peer 5.5.5.9 connect-interface loopback 0
[PE1-bgp] peer 5.5.5.9 ebgp-max-hop 10
# Configure peer 5.5.5.9 as a VPNv4 peer.
[PE1-bgp] address-family vpnv4
[PE1-bgp-vpnv4] peer 5.5.5.9 enable
[PE1-bgp-vpnv4] quit
# Configure 30.0.0.2 as an EBGP peer, and redistribute BGP routes to the routing table of vpn1.
[PE1-bgp] ip vpn-instance vpn1
[PE1-bgp-vpn1] peer 30.0.0.2 as-number 65001
[PE1-bgp-vpn1] address-family ipv4 unicast
[PE1-bgp-ipv4-vpn1] peer 30.0.0.2 enable
[PE1-bgp-ipv4-vpn1] quit
[PE1-bgp-vpn1] quit
[PE1-bgp] quit
3. Configure ASBR-PE 1:
# Enable IS-IS on ASBR-PE 1.
<ASBR-PE1> system-view
[ASBR-PE1] isis 1
[ASBR-PE1-isis-1] network-entity 10.222.222.222.222.00
[ASBR-PE1-isis-1] quit
# Configure the LSR ID, and enable MPLS and LDP.
[ASBR-PE1] mpls lsr-id 3.3.3.9
[ASBR-PE1] mpls ldp
[ASBR-PE1-ldp] quit
# Configure interface VLAN-interface 11, and enable IS-IS, MPLS, and LDP on the interface.
[ASBR-PE1] interface vlan-interface 11
[ASBR-PE1-Vlan-interface11] ip address 1.1.1.1 255.0.0.0
[ASBR-PE1-Vlan-interface11] isis enable 1
[ASBR-PE1-Vlan-interface11] mpls enable
[ASBR-PE1-Vlan-interface11] mpls ldp enable
[ASBR-PE1-Vlan-interface11] quit
# Configure interface VLAN-interface 12, and enable MPLS on it.
[ASBR-PE1] interface vlan-interface 12
[ASBR-PE1-Vlan-interface12] ip address 11.0.0.2 255.0.0.0
[ASBR-PE1-Vlan-interface12] mpls enable
[ASBR-PE1-Vlan-interface12] quit
# Configure interface Loopback 0, and enable IS-IS on it.
[ASBR-PE1] interface loopback 0
[ASBR-PE1-LoopBack0] ip address 3.3.3.9 32
[ASBR-PE1-LoopBack0] isis enable 1
[ASBR-PE1-LoopBack0] quit
# Create routing policies.
[ASBR-PE1] route-policy policy1 permit node 1
[ASBR-PE1-route-policy-policy1-1] apply mpls-label
[ASBR-PE1-route-policy-policy1-1] quit
[ASBR-PE1] route-policy policy2 permit node 1
[ASBR-PE1-route-policy-policy2-1] if-match mpls-label
[ASBR-PE1-route-policy-policy2-1] apply mpls-label
[ASBR-PE1-route-policy-policy2-1] quit
# Enable BGP on ASBR-PE 1, and apply the routing policy policy2 to routes advertised to IBGP peer 2.2.2.9.
[ASBR-PE1] bgp 100
[ASBR-PE1-bgp] peer 2.2.2.9 as-number 100
[ASBR-PE1-bgp] peer 2.2.2.9 connect-interface loopback 0
[ASBR-PE1-bgp] address-family ipv4 unicast
[ASBR-PE1-bgp-ipv4] peer 2.2.2.9 enable
[ASBR-PE1-bgp-ipv4] peer 2.2.2.9 route-policy policy2 export
# Enable the capability to advertise labeled routes to IBGP peer 2.2.2.9 and to receive labeled routes from the peer.
[ASBR-PE1-bgp-ipv4] peer 2.2.2.9 label-route-capability
# Redistribute routes from IS-IS process 1 to BGP.
[ASBR-PE1-bgp-ipv4] import-route isis 1
[ASBR-PE1-bgp-ipv4] quit
# Apply the routing policy policy1 to routes advertised to EBGP peer 11.0.0.1.
[ASBR-PE1-bgp] peer 11.0.0.1 as-number 600
[ASBR-PE1-bgp] address-family ipv4 unicast
[ASBR-PE1-bgp-ipv4] peer 11.0.0.1 enable
[ASBR-PE1-bgp-ipv4] peer 11.0.0.1 route-policy policy1 export
# Enable the capability to advertise labeled routes to EBGP peer 11.0.0.1 and to receive labeled routes from the peer.
[ASBR-PE1-bgp-ipv4] peer 11.0.0.1 label-route-capability
[ASBR-PE1-bgp-ipv4] quit
[ASBR-PE1-bgp] quit
4. Configure ASBR-PE 2:
# Enable IS-IS on ASBR-PE 2.
<ASBR-PE2> system-view
[ASBR-PE2] isis 1
[ASBR-PE2-isis-1] network-entity 10.222.222.222.222.00
[ASBR-PE2-isis-1] quit
# Configure the LSR ID, and enable MPLS and LDP.
[ASBR-PE2] mpls lsr-id 4.4.4.9
[ASBR-PE2] mpls ldp
[ASBR-PE2-ldp] quit
# Configure interface VLAN-interface 11, and enable IS-IS, MPLS, and LDP on the interface.
[ASBR-PE2] interface vlan-interface 11
[ASBR-PE2-Vlan-interface11] ip address 9.1.1.1 255.0.0.0
[ASBR-PE2-Vlan-interface11] isis enable 1
[ASBR-PE2-Vlan-interface11] mpls enable
[ASBR-PE2-Vlan-interface11] mpls ldp enable
[ASBR-PE2-Vlan-interface11] quit
# Configure interface Loopback 0, and enable IS-IS on it.
[ASBR-PE2] interface loopback 0
[ASBR-PE2-LoopBack0] ip address 4.4.4.9 32
[ASBR-PE2-LoopBack0] isis enable 1
[ASBR-PE2-LoopBack0] quit
# Configure interface VLAN-interface 12, and enable MPLS on it.
[ASBR-PE2] interface vlan-interface 12
[ASBR-PE2-Vlan-interface12] ip address 11.0.0.1 255.0.0.0
[ASBR-PE2-Vlan-interface12] mpls enable
[ASBR-PE2-Vlan-interface12] quit
# Create routing policies.
[ASBR-PE2] route-policy policy1 permit node 1
[ASBR-PE2-route-policy-policy1-1] apply mpls-label
[ASBR-PE2-route-policy-policy1-1] quit
[ASBR-PE2] route-policy policy2 permit node 1
[ASBR-PE2-route-policy-policy2-1] if-match mpls-label
[ASBR-PE2-route-policy-policy2-1] apply mpls-label
[ASBR-PE2-route-policy-policy2-1] quit
# Enable BGP on ASBR-PE 2, and enable the capability to advertise labeled routes to IBGP peer 5.5.5.9 and to receive labeled routes from the peer.
[ASBR-PE2] bgp 600
[ASBR-PE2-bgp] peer 5.5.5.9 as-number 600
[ASBR-PE2-bgp] peer 5.5.5.9 connect-interface loopback 0
[ASBR-PE2-bgp] address-family ipv4 unicast
[ASBR-PE2-bgp-ipv4] peer 5.5.5.9 enable
[ASBR-PE2-bgp-ipv4] peer 5.5.5.9 label-route-capability
# Apply the routing policy policy2 to routes advertised to IBGP peer 5.5.5.9.
[ASBR-PE2-bgp-ipv4] peer 5.5.5.9 route-policy policy2 export
# Redistribute routes from IS-IS process 1 into BGP.
[ASBR-PE2-bgp-ipv4] import-route isis 1
[ASBR-PE2-bgp-ipv4] quit
# Apply the routing policy policy1 to routes advertised to EBGP peer 11.0.0.2.
[ASBR-PE2-bgp] peer 11.0.0.2 as-number 100
[ASBR-PE2-bgp] address-family ipv4 unicast
[ASBR-PE2-bgp-ipv4] peer 11.0.0.2 enable
[ASBR-PE2-bgp-ipv4] peer 11.0.0.2 route-policy policy1 export
# Enable the capability to advertise labeled routes to EBGP peer 11.0.0.2 and to receive labeled routes from the peer.
[ASBR-PE2-bgp-ipv4] peer 11.0.0.2 label-route-capability
[ASBR-PE2-bgp-ipv4] quit
[ASBR-PE2-bgp] quit
5. Configure PE 2:
# Enable IS-IS on PE 2.
<PE2> system-view
[PE2] isis 1
[PE2-isis-1] network-entity 10.111.111.111.111.00
[PE2-isis-1] quit
# Configure the LSR ID, and enable MPLS and LDP.
[PE2] mpls lsr-id 5.5.5.9
[PE2] mpls ldp
[PE2-ldp] quit
# Configure interface VLAN-interface 11, and enable IS-IS, MPLS, and LDP on the interface.
[PE2] interface vlan-interface 11
[PE2-Vlan-interface11] ip address 9.1.1.2 255.0.0.0
[PE2-Vlan-interface11] isis enable 1
[PE2-Vlan-interface11] mpls enable
[PE2-Vlan-interface11] mpls ldp enable
[PE2-Vlan-interface11] quit
# Configure interface Loopback 0, and enable IS-IS on it.
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 5.5.5.9 32
[PE2-LoopBack0] isis enable 1
[PE2-LoopBack0] quit
# Create VPN instance vpn1, and configure the RD and route target attributes.
[PE2] reserve-vlan-interface 3000 to 3050
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] route-distinguisher 11:11
[PE2-vpn-instance-vpn1] vpn-target 1:1 2:2 3:3 import-extcommunity
[PE2-vpn-instance-vpn1] vpn-target 3:3 export-extcommunity
[PE2-vpn-instance-vpn1] quit
# Associate interface VLAN-interface 12 with VPN instance vpn1, and specify an IP address for the interface.
[PE2] interface vlan-interface 12
[PE2-Vlan-interface12] ip binding vpn-instance vpn1
[PE2-Vlan-interface12] ip address 20.0.0.1 24
[PE2-Vlan-interface12] quit
# Enable BGP on PE 2.
[PE2] bgp 600
# Enable the capability to advertise labeled routes to IBGP peer 4.4.4.9 and to receive labeled routes from the peer.
[PE2-bgp] peer 4.4.4.9 as-number 600
[PE2-bgp] peer 4.4.4.9 connect-interface loopback 0
[PE2-bgp] address-family ipv4 unicast
[PE2-bgp-ipv4] peer 4.4.4.9 enable
[PE2-bgp-ipv4] peer 4.4.4.9 label-route-capability
[PE2-bgp-ipv4] quit
# Configure the maximum hop count from PE 2 to EBGP peer 2.2.2.9 as 10.
[PE2-bgp] peer 2.2.2.9 as-number 100
[PE2-bgp] peer 2.2.2.9 connect-interface loopback 0
[PE2-bgp] peer 2.2.2.9 ebgp-max-hop 10
# Configure peer 2.2.2.9 as a VPNv4 peer.
[PE2-bgp] address-family vpnv4
[PE2-bgp-vpnv4] peer 2.2.2.9 enable
[PE2-bgp-vpnv4] quit
# Configure 20.0.0.2 as an EBGP peer, and redistribute BGP routes to the routing table of vpn1.
[PE2-bgp] ip vpn-instance vpn1
[PE2-bgp-vpn1] peer 20.0.0.2 as-number 65002
[PE2-bgp-vpn1] address-family ipv4 unicast
[PE2-bgp-ipv4-vpn1] peer 20.0.0.2 enable
[PE2-bgp-ipv4-vpn1] quit
[PE2-bgp-vpn1] quit
[PE2-bgp] quit
6. Configure CE 2:
# Configure an IP address for VLAN-interface 12.
<CE2> system-view
[CE2] interface vlan-interface 12
[CE2-Vlan-interface12] ip address 20.0.0.2 24
[CE2-Vlan-interface12] quit
# Configure 20.0.0.1 as an EBGP peer, and redistribute direct routes.
[CE2] bgp 65002
[CE2-bgp] peer 20.0.0.1 as-number 600
[CE2-bgp] address-family ipv4 unicast
[CE2-bgp-ipv4] peer 20.0.0.1 enable
[CE2-bgp-ipv4] import-route direct
[CE2-bgp-ipv4] quit
[CE2-bgp] quit
Verifying the configuration
# Execute the display ip routing table command on CE 1 and CE 2 to verify that CE 1 and CE 2 have a route to each other. Verify that CE 1 and CE 2 can ping each other. (Details not shown.)
Configuring MPLS L3VPN carrier's carrier
Network requirements
Configure carrier's carrier for the scenario shown in Figure 67. In this scenario:
· PE 1 and PE 2 are the provider carrier's PE switches. They provide VPN services for the customer carrier.
· CE 1 and CE 2 are the customer carrier's switches. They are connected to the provider carrier's backbone as CE switches.
· PE 3 and PE 4 are the customer carrier's PE switches. They provide MPLS L3VPN services for the end customers.
· CE 3 and CE 4 are customers of the customer carrier.
The key to carrier's carrier deployment is to configure exchange of two kinds of routes:
· Exchange of the customer carrier's internal routes on the provider carrier's backbone.
· Exchange of the end customers' VPN routes between PE 3 and PE 4, the PEs of the customer carrier. In this process, an MP-IBGP peer relationship must be established between PE 3 and PE 4.

Table 17 Interface and IP address assignment
|
Interface |
IP address |
Device |
Interface |
IP address |
|
|
CE 3 |
Vlan-int11 |
100.1.1.1/24 |
CE 4 |
Vlan-int11 |
120.1.1.1/24 |
|
PE 3 |
Loop0 |
1.1.1.9/32 |
PE 4 |
Loop0 |
6.6.6.9/32 |
|
|
Vlan-int11 |
100.1.1.2/24 |
|
Vlan-int11 |
120.1.1.2/24 |
|
|
Vlan-int12 |
10.1.1.1/24 |
|
Vlan-int12 |
20.1.1.2/24 |
|
CE 1 |
Loop0 |
2.2.2.9/32 |
CE 2 |
Loop0 |
5.5.5.9/32 |
|
|
Vlan-int12 |
10.1.1.2/24 |
|
Vlan-int11 |
21.1.1.2/24 |
|
|
Vlan-int11 |
11.1.1.1/24 |
|
Vlan-int12 |
20.1.1.1/24 |
|
PE 1 |
Loop0 |
3.3.3.9/32 |
PE 2 |
Loop0 |
4.4.4.9/32 |
|
|
Vlan-int11 |
11.1.1.2/24 |
|
Vlan-int12 |
30.1.1.2/24 |
|
|
Vlan-int12 |
30.1.1.1/24 |
|
Vlan-int11 |
21.1.1.1/24 |
Configuration procedure
1. Configure MPLS L3VPN on the provider carrier backbone. Enable IS-IS as the IGP, enable LDP between PE 1 and PE 2, and establish an MP-IBGP peer relationship between the PEs:
# Configure PE 1.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 3.3.3.9 32
[PE1-LoopBack0] quit
[PE1] mpls lsr-id 3.3.3.9
[PE1] mpls ldp
[PE1-ldp] quit
[PE1] isis 1
[PE1-isis-1] network-entity 10.0000.0000.0000.0004.00
[PE1-isis-1] quit
[PE1] interface loopback 0
[PE1-LoopBack0] isis enable 1
[PE1-LoopBack0] quit
[PE1] interface vlan-interface 12
[PE1-Vlan-interface12] ip address 30.1.1.1 24
[PE1-Vlan-interface12] isis enable 1
[PE1-Vlan-interface12] mpls enable
[PE1-Vlan-interface12] mpls ldp enable
[PE1-Vlan-interface12] mpls ldp transport-address interface
[PE1-Vlan-interface12] quit
[PE1] bgp 100
[PE1-bgp] peer 4.4.4.9 as-number 100
[PE1-bgp] peer 4.4.4.9 connect-interface loopback 0
[PE1-bgp] address-family vpnv4
[PE1-bgp-vpnv4] peer 4.4.4.9 enable
[PE1-bgp-vpnv4] quit
[PE1-bgp] quit
# Configure PE 2 in the same way that PE 1 is configured. (Details not shown.)
# On PE 1 or PE 2, execute the following commands:
? Execute the display mpls ldp peer command to verify that an LDP session in Operational state has been established between PE 1 and PE 2. (Details not shown.)
? Execute the display bgp peer vpnv4 command to verify that a BGP peer relationship in Established state has been established between PE 1 and PE 2. (Details not shown.)
? Execute the display isis peer command to verify that the IS-IS neighbor relationship has been established between PE 1 and PE 2. (Details not shown.)
2. Configure the customer carrier network. Enable IS-IS as the IGP, and enable LDP between PE 3 and CE 1, and between PE 4 and CE 2:
# Configure PE 3.
<PE3> system-view
[PE3] interface loopback 0
[PE3-LoopBack0] ip address 1.1.1.9 32
[PE3-LoopBack0] quit
[PE3] mpls lsr-id 1.1.1.9
[PE3] mpls ldp
[PE3-ldp] quit
[PE3] isis 2
[PE3-isis-2] network-entity 10.0000.0000.0000.0001.00
[PE3-isis-2] quit
[PE3] interface loopback 0
[PE3-LoopBack0] isis enable 2
[PE3-LoopBack0] quit
[PE3] interface vlan-interface 12
[PE3-Vlan-interface12] ip address 10.1.1.1 24
[PE3-Vlan-interface12] isis enable 2
[PE3-Vlan-interface12] mpls enable
[PE3-Vlan-interface12] mpls ldp enable
[PE3-Vlan-interface12] mpls ldp transport-address interface
[PE3-Vlan-interface12] quit
# Configure CE 1.
<CE1> system-view
[CE1] interface loopback 0
[CE1-LoopBack0] ip address 2.2.2.9 32
[CE1-LoopBack0] quit
[CE1] mpls lsr-id 2.2.2.9
[CE1] mpls ldp
[CE1-ldp] quit
[CE1] isis 2
[CE1-isis-2] network-entity 10.0000.0000.0000.0002.00
[CE1-isis-2] quit
[CE1] interface loopback 0
[CE1-LoopBack0] isis enable 2
[CE1-LoopBack0] quit
[CE1] interface vlan-interface 12
[CE1-Vlan-interface12] ip address 10.1.1.2 24
[CE1-Vlan-interface12] isis enable 2
[CE1-Vlan-interface12] mpls enable
[CE1-Vlan-interface12] mpls ldp enable
[CE1-Vlan-interface12] mpls ldp transport-address interface
[CE1-Vlan-interface12] quit
PE 3 and CE 1 can establish an LDP session and IS-IS neighbor relationship between them.
# Configure PE 4 and CE 2 in the same way that PE 3 and CE 1 are configured. (Details not shown.)
3. Perform configurations to allow CEs of the customer carrier to access PEs of the provider carrier, and redistribute IS-IS routes to BGP and BGP routes to IS-IS on the PEs:
# Configure PE 1.
[PE1] reserve-vlan-interface 3000 to 3050
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 200:1
[PE1-vpn-instance-vpn1] vpn-target 1:1
[PE1-vpn-instance-vpn1] quit
[PE1] mpls ldp
[PE1-ldp] vpn-instance vpn1
[PE1-ldp-vpn-instance-vpn1] quit
[PE1-ldp] quit
[PE1] isis 2 vpn-instance vpn1
[PE1-isis-2] network-entity 10.0000.0000.0000.0003.00
[PE1-isis-2] import-route bgp
[PE1-isis-2] quit
[PE1] interface vlan-interface 11
[PE1-Vlan-interface11] ip binding vpn-instance vpn1
[PE1-Vlan-interface11] ip address 11.1.1.2 24
[PE1-Vlan-interface11] isis enable 2
[PE1-Vlan-interface11] mpls enable
[PE1-Vlan-interface11] mpls ldp enable
[PE1-Vlan-interface11] mpls ldp transport-address interface
[PE1-Vlan-interface11] quit
[PE1] bgp 100
[PE1-bgp] ip vpn-instance vpn1
[PE1-bgp-vpn1] address-family ipv4 unicast
[PE1-bgp-ipv4-vpn1] import isis 2
[PE1-bgp-ipv4-vpn1] quit
[PE1-bgp-vpn1] quit
[PE1-bgp] quit
# Configure CE 1.
[CE1] interface vlan-interface 11
[CE1-Vlan-interface11] ip address 11.1.1.1 24
[CE1-Vlan-interface11] isis enable 2
[CE1-Vlan-interface11] mpls enable
[CE1-Vlan-interface11] mpls ldp enable
[CE1-Vlan-interface11] mpls ldp transport-address interface
[CE1-Vlan-interface11] quit
PE 1 and CE 1 can establish an LDP session and an IS-IS neighbor relationship between them.
# Configure PE 2 and CE 2 in the same way that PE 1 and CE 1 are configured. (Details not shown.)
4. Perform configuration to connect the CEs of the end customers to the PEs of the customer carrier:
# Configure CE 3.
<CE3> system-view
[CE3] interface vlan-interface 11
[CE3-Vlan-interface11] ip address 100.1.1.1 24
[CE3-Vlan-interface11] quit
[CE3] bgp 65410
[CE3-bgp] peer 100.1.1.2 as-number 100
[CE3-bgp] address-family ipv4 unicast
[CE3-bgp-ipv4] peer 100.1.1.2 enable
[CE3-bgp-ipv4] import-route direct
[CE3-bgp-ipv4] quit
[CE3-bgp] quit
# Configure PE 3.
[PE3] reserve-vlan-interface 3000 to 3050
[PE3] ip vpn-instance vpn1
[PE3-vpn-instance-vpn1] route-distinguisher 100:1
[PE3-vpn-instance-vpn1] vpn-target 1:1
[PE3-vpn-instance-vpn1] quit
[PE3] interface Vlan-interface11
[PE3-Vlan-interface11] ip binding vpn-instance vpn1
[PE3-Vlan-interface11] ip address 100.1.1.2 24
[PE3-Vlan-interface11] quit
[PE3] bgp 100
[PE3-bgp] ip vpn-instance vpn1
[PE3-bgp-vpn1] peer 100.1.1.1 as-number 65410
[PE3-bgp-vpn1] address-family ipv4 unicast
[PE3-bgp-ipv4-vpn1] peer 100.1.1.1 enable
[PE3-bgp-ipv4-vpn1] import-route direct
[PE3-bgp-ipv4-vpn1] quit
[PE3-bgp-vpn1] quit
[PE3-bgp] quit
# Configure PE 4 and CE 4 in the same way that PE 3 and CE 3 are configured. (Details not shown.)
5. Configure MP-IBGP peer relationship between the PEs of the customer carrier to exchange the end customers' VPN routes:
# Configure PE 3.
[PE3] bgp 100
[PE3-bgp] peer 6.6.6.9 as-number 100
[PE3-bgp] peer 6.6.6.9 connect-interface loopback 0
[PE3-bgp] address-family vpnv4
[PE3-bgp-vpnv4] peer 6.6.6.9 enable
[PE3-bgp-vpnv4] quit
[PE3-bgp] quit
# Configure PE 4 in the same way that PE 3 is configured. (Details not shown.)
Verifying the configuration
1. Display the public network routing table and VPN routing table on the provider carrier PEs, for example, on PE 1:
# Verify that the public network routing table contains only routes of the provider carrier network.
[PE1] display ip routing-table
Destinations : 14 Routes : 14
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
3.3.3.9/32 Direct 0 0 127.0.0.1 InLoop0
4.4.4.9/32 ISIS 15 10 30.1.1.2 Vlan12
30.1.1.0/24 Direct 0 0 30.1.1.1 Vlan12
30.1.1.0/32 Direct 0 0 30.1.1.1 Vlan12
30.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
30.1.1.255/32 Direct 0 0 30.1.1.1 Vlan12
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Verify that the VPN routing table contains the internal routes of the customer carrier network, but it does not contain the VPN routes that the customer carrier maintains on the PE.
[PE1] display ip routing-table vpn-instance vpn1
Destinations : 18 Routes : 18
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
1.1.1.9/32 ISIS 15 20 11.1.1.1 Vlan11
2.2.2.9/32 ISIS 15 10 11.1.1.1 Vlan11
5.5.5.9/32 BGP 255 10 4.4.4.9 Vlan12
6.6.6.9/32 BGP 255 20 4.4.4.9 Vlan12
10.1.1.0/24 ISIS 15 20 11.1.1.1 Vlan11
11.1.1.0/24 Direct 0 0 11.1.1.2 Vlan11
11.1.1.0/32 Direct 0 0 11.1.1.2 Vlan11
11.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
11.1.1.255/32 Direct 0 0 11.1.1.2 Vlan11
20.1.1.0/24 BGP 255 20 4.4.4.9 Vlan12
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
2. Display the routing table on the customer carrier CEs, for example, on CE 1:
# Verify that the routing table contains the internal routes of the customer carrier network, but it does not contain the VPN routes that the customer carrier maintains.
[CE1] display ip routing-table
Destinations : 21 Routes : 21
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
1.1.1.9/32 ISIS 15 10 10.1.1.1 Vlan12
2.2.2.9/32 Direct 0 0 127.0.0.1 InLoop0
5.5.5.9/32 ISIS 15 74 11.1.1.2 Vlan11
6.6.6.9/32 ISIS 15 74 11.1.1.2 Vlan11
10.1.1.0/24 Direct 0 0 10.1.1.2 Vlan12
10.1.1.0/32 Direct 0 0 10.1.1.2 Vlan12
10.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.255/32 Direct 0 0 10.1.1.2 Vlan12
11.1.1.0/24 Direct 0 0 11.1.1.1 Vlan11
11.1.1.0/32 Direct 0 0 11.1.1.1 Vlan11
11.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
11.1.1.255/32 Direct 0 0 11.1.1.1 Vlan11
20.1.1.0/24 ISIS 15 74 11.1.1.2 Vlan11
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
3. Display the public network routing table and VPN routing table on the customer carrier PEs, for example, on PE 3:
# Verify that the public network routing table contains the internal routes of the customer carrier network.
[PE3] display ip routing-table
Destinations : 18 Routes : 18
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
1.1.1.9/32 Direct 0 0 127.0.0.1 InLoop0
2.2.2.9/32 ISIS 15 10 10.1.1.2 Vlan12
5.5.5.9/32 ISIS 15 84 10.1.1.2 Vlan12
6.6.6.9/32 ISIS 15 84 10.1.1.2 Vlan12
10.1.1.0/24 Direct 0 0 10.1.1.1 Vlan12
10.1.1.0/32 Direct 0 0 10.1.1.1 Vlan12
10.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.255/32 Direct 0 0 10.1.1.1 Vlan12
11.1.1.0/24 ISIS 15 20 10.1.1.2 Vlan12
20.1.1.0/24 ISIS 15 84 10.1.1.2 Vlan12
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Verify that the VPN routing table contains the route to the remote VPN customer.
[PE3] display ip routing-table vpn-instance vpn1
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
100.1.1.0/24 Direct 0 0 100.1.1.2 Vlan11
100.1.1.0/32 Direct 0 0 100.1.1.2 Vlan11
100.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
100.1.1.255/32 Direct 0 0 100.1.1.2 Vlan11
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
120.1.1.0/24 BGP 255 0 6.6.6.9 Vlan12
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
4. Verify that PE 3 and PE 4 can ping each other. (Details not shown.)
5. Verify that CE 3 and CE 4 can ping each other. (Details not shown.)
Configuring nested VPN
Network requirements
The service provider provides nested VPN services for users, as shown in Figure 68.
· PE 1 and PE 2 are PE devices on the service provider backbone. Both of them support the nested VPN function.
· CE 1 and CE 2 are connected to the service provider backbone. Both of them support VPNv4 routes.
· PE 3 and PE 4 are PE devices of the customer VPN. Both of them support MPLS L3VPN.
· CE 3 through CE 6 are CE devices of the sub-VPNs for the customer VPN.
The key of nested VPN configuration is to understand the processing of routes of sub-VPNs on the service provider PEs:
· When receiving a VPNv4 route from a CE (CE 1 or CE 2 in this example), a service provider PE
a. Replaces the RD of the VPNv4 route with the RD of the MPLS VPN on the service provider network where the CE resides.
b. Adds the export target attribute of the MPLS VPN on the service provider network to the extended community attribute list.
c. Forwards the VPNv4 route.
· To implement exchange of sub-VPN routes between customer PEs and service provider PEs, MP-EBGP peers must be established between service provider PEs and customer CEs.

Table 18 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
Loop0 |
2.2.2.9/32 |
CE 2 |
Loop0 |
5.5.5.9/32 |
|
|
Vlan-int2 |
10.1.1.2/24 |
|
Vlan-int1 |
21.1.1.2/24 |
|
|
Vlan-int1 |
11.1.1.1/24 |
|
Vlan-int2 |
20.1.1.1/24 |
|
CE 3 |
Vlan-int1 |
100.1.1.1/24 |
CE 4 |
Vlan-int1 |
120.1.1.1/24 |
|
CE 5 |
Vlan-int3 |
110.1.1.1/24 |
CE 6 |
Vlan-int3 |
130.1.1.1/24 |
|
PE 1 |
Loop0 |
3.3.3.9/32 |
PE 2 |
Loop0 |
4.4.4.9/32 |
|
|
Vlan-int1 |
11.1.1.2/24 |
|
Vlan-int1 |
21.1.1.1/24 |
|
|
Vlan-int2 |
30.1.1.1/24 |
|
Vlan-int2 |
30.1.1.2/24 |
|
PE 3 |
Loop0 |
1.1.1.9/32 |
PE 4 |
Loop0 |
6.6.6.9/32 |
|
|
Vlan-int1 |
100.1.1.2/24 |
|
Vlan-int1 |
120.1.1.2/24 |
|
|
Vlan-int2 |
10.1.1.1/24 |
|
Vlan-int2 |
20.1.1.2/24 |
|
|
Vlan-int3 |
110.1.1.2/24 |
|
Vlan-int3 |
130.1.1.2/24 |
Configuration procedure
1. Configure MPLS L3VPN on the service provider backbone. Enable IS-IS, enable LDP, and establish an MP-IBGP peer relationship between PE 1 and PE 2:
# Configure PE 1.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 3.3.3.9 32
[PE1-LoopBack0] quit
[PE1] mpls lsr-id 3.3.3.9
[PE1] mpls ldp
[PE1-ldp] quit
[PE1] isis 1
[PE1-isis-1] network-entity 10.0000.0000.0000.0004.00
[PE1-isis-1] quit
[PE1] interface loopback 0
[PE1-LoopBack0] isis enable 1
[PE1-LoopBack0] quit
[PE1] interface vlan-interface 2
[PE1-Vlan-interface2] ip address 30.1.1.1 24
[PE1-Vlan-interface2] isis enable 1
[PE1-Vlan-interface2] mpls enable
[PE1-Vlan-interface2] mpls ldp enable
[PE1-Vlan-interface2] quit
[PE1] bgp 100
[PE1-bgp] peer 4.4.4.9 as-number 100
[PE1-bgp] peer 4.4.4.9 connect-interface loopback 0
[PE1-bgp] address-family vpnv4
[PE1-bgp-vpnv4] peer 4.4.4.9 enable
[PE1-bgp-vpnv4] quit
[PE1-bgp] quit
# Configure PE 2 in the same way that PE 1 is configured. (Details not shown.)
# On PE 1 or PE 2, execute the following commands:
? Execute the display mpls ldp peer command to verify that an LDP session in Operational state has been established between PE 1 and PE 2. (Details not shown.)
? Execute the display bgp peer vpnv4 command to verify that a BGP peer relationship in Established state has been established between PE 1 and PE 2. (Details not shown.)
? Execute the display isis peer command to verify that the IS-IS neighbor relationship has been established between PE 1 and PE 2. (Details not shown.)
2. Configure the customer VPN. Enable IS-IS, and enable LDP between PE 3 and CE 1, and between PE 4 and CE 2:
# Configure PE 3.
<PE3> system-view
[PE3] interface loopback 0
[PE3-LoopBack0] ip address 1.1.1.9 32
[PE3-LoopBack0] quit
[PE3] mpls lsr-id 1.1.1.9
[PE3] mpls ldp
[PE3-ldp] quit
[PE3] isis 2
[PE3-isis-2] network-entity 10.0000.0000.0000.0001.00
[PE3-isis-2] quit
[PE3] interface loopback 0
[PE3-LoopBack0] isis enable 2
[PE3-LoopBack0] quit
[PE3] interface vlan-interface 2
[PE3-Vlan-interface2] ip address 10.1.1.1 24
[PE3-Vlan-interface2] isis enable 2
[PE3-Vlan-interface2] mpls enable
[PE3-Vlan-interface2] mpls ldp enable
[PE3-Vlan-interface2] quit
# Configure CE 1.
<CE1> system-view
[CE1] interface loopback 0
[CE1-LoopBack0] ip address 2.2.2.9 32
[CE1-LoopBack0] quit
[CE1] mpls lsr-id 2.2.2.9
[CE1] mpls ldp
[CE1-ldp] quit
[CE1] isis 2
[CE1-isis-2] network-entity 10.0000.0000.0000.0002.00
[CE1-isis-2] quit
[CE1] interface loopback 0
[CE1-LoopBack0] isis enable 2
[CE1-LoopBack0] quit
[CE1] interface vlan-interface 2
[CE1-Vlan-interface2] ip address 10.1.1.2 24
[CE1-Vlan-interface2] isis enable 2
[CE1-Vlan-interface2] mpls enable
[CE1-Vlan-interface2] mpls ldp enable
[CE1-Vlan-interface2] quit
An LDP session and an IS-IS neighbor relationship can be established between PE 3 and CE 1.
# Configure PE 4 and CE 2 in the same way that PE 3 and CE 1 are configured. (Details not shown.)
3. Connect CE 1 and CE 2 to service provider PEs:
# Configure PE 1.
[PE1] reserve-vlan-interface 3000 to 3050
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 200:1
[PE1-vpn-instance-vpn1] vpn-target 1:1
[PE1-vpn-instance-vpn1] quit
[PE1] interface vlan-interface 1
[PE1-Vlan-interface1] ip binding vpn-instance vpn1
[PE1-Vlan-interface1] ip address 11.1.1.2 24
[PE1-Vlan-interface1] mpls enable
[PE1-Vlan-interface1] quit
[PE1] bgp 100
[PE1-bgp] ip vpn-instance vpn1
[PE1-bgp-vpn1] peer 11.1.1.1 as-number 200
[PE1-bgp-vpn1] address-family ipv4
[PE1-bgp-ipv4-vpn1] peer 11.1.1.1 enable
[PE1-bgp-ipv4-vpn1] quit
[PE1-bgp-vpn1] quit
[PE1-bgp] quit
# Configure CE 1.
[CE1] interface vlan-interface 1
[CE1-Vlan-interface1] ip address 11.1.1.1 24
[CE1-Vlan-interface1] mpls enable
[CE1-Vlan-interface1] quit
[CE1] bgp 200
[CE1-bgp] peer 11.1.1.2 as-number 100
[CE1-bgp-vpn1] address-family ipv4
[CE1-bgp-ipv4-vpn1] peer 11.1.1.2 enable
[CE1-bgp-ipv4-vpn1] quit
[CE1-bgp] quit
# Configure PE 2 and CE 2 in the same way that PE 1 and CE 1 are configured. (Details not shown.)
4. Connect sub-VPN CEs to the customer VPN PEs:
# Configure CE 3.
<CE3> system-view
[CE3] interface vlan-interface 1
[CE3-Vlan-interface1] ip address 100.1.1.1 24
[CE3-Vlan-interface1] quit
[CE3] bgp 65410
[CE3-bgp] peer 100.1.1.2 as-number 200
[CE3-bgp] address-family ipv4 unicast
[CE3-bgp-ipv4] peer 100.1.1.2 enable
[CE3-bgp-ipv4] import-route direct
[CE3-bgp-ipv4] quit
[CE3-bgp] quit
# Configure CE 5.
<CE5> system-view
[CE5] interface vlan-interface 3
[CE5-Vlan-interface3] ip address 110.1.1.1 24
[CE5-Vlan-interface3] quit
[CE5] bgp 65411
[CE5-bgp] peer 110.1.1.2 as-number 200
[CE5-bgp] address-family ipv4 unicast
[CE5-bgp-ipv4] peer 110.1.1.2 enable
[CE5-bgp-ipv4] import-route direct
[CE5-bgp-ipv4] quit
[CE5-bgp] quit
# Configure PE 3.
[PE3] reserve-vlan-interface 3000 to 3050
[PE3] ip vpn-instance SUB_VPN1
[PE3-vpn-instance-SUB_VPN1] route-distinguisher 100:1
[PE3-vpn-instance-SUB_VPN1] vpn-target 2:1
[PE3-vpn-instance-SUB_VPN1] quit
[PE3] interface vlan-interface 1
[PE3-Vlan-interface1] ip binding vpn-instance SUB_VPN1
[PE3-Vlan-interface1] ip address 100.1.1.2 24
[PE3-Vlan-interface1] quit
[PE3] ip vpn-instance SUB_VPN2
[PE3-vpn-instance-SUB_VPN2] route-distinguisher 101:1
[PE3-vpn-instance-SUB_VPN2] vpn-target 2:2
[PE3-vpn-instance-SUB_VPN2] quit
[PE3] interface vlan-interface 3
[PE3-Vlan-interface3] ip binding vpn-instance SUB_VPN2
[PE3-Vlan-interface3] ip address 110.1.1.2 24
[PE3-Vlan-interface3] quit
[PE3] bgp 200
[PE3-bgp] ip vpn-instance SUB_VPN1
[PE3-bgp-SUB_VPN1] peer 100.1.1.1 as-number 65410
[PE3-bgp-SUB_VPN1] address-family ipv4 unicast
[PE3-bgp-ipv4-SUB_VPN1] peer 100.1.1.1 enable
[PE3-bgp-ipv4-SUB_VPN1] import-route direct
[PE3-bgp-ipv4-SUB_VPN1] quit
[PE3-bgp-SUB_VPN1] quit
[PE3-bgp] ip vpn-instance SUB_VPN2
[PE3-bgp-SUB_VPN2] peer 100.1.1.1 as-number 65411
[PE3-bgp-SUB_VPN2] address-family ipv4 unicast
[PE3-bgp-ipv4-SUB_VPN2] peer 110.1.1.1 enable
[PE3-bgp-ipv4-SUB_VPN2] import-route direct
[PE3-bgp-ipv4-SUB_VPN2] quit
[PE3-bgp-SUB_VPN2] quit
[PE3-bgp] quit
# Configure PE 4, CE 4, and CE 6 in the same way that PE 3, CE 3, and CE 5 are configured. (Details not shown.)
5. Establish MP-EBGP peer relationships between service provider PEs and their CEs to exchange user VPNv4 routes:
# On PE 1, enable nested VPN and VPNv4 route exchange with CE 1.
[PE1] bgp 100
[PE1-bgp] address-family vpnv4
[PE1-bgp-vpnv4] nesting-vpn
[PE1-bgp-vpnv4] quit
[PE1-bgp] ip vpn-instance vpn1
[PE1-bgp-vpn1] address-family vpnv4
[PE1-bgp-vpnv4-vpn1] peer 11.1.1.1 enable
[PE1-bgp-vpnv4-vpn1] quit
[PE1-bgp-vpn1] quit
[PE1-bgp] quit
# Enable CE 1 to exchange VPNv4 routes with PE 1.
[CE1] bgp 200
[CE1-bgp] address-family vpnv4
[CE1-bgp-vpnv4] peer 11.1.1.2 enable
# Allow the local AS number to appear in the AS-PATH attribute of the routes received.
[CE1-bgp-vpnv4] peer 11.1.1.2 allow-as-loop 2
# Disable route target based filtering of received VPNv4 routes.
[CE1-bgp-vpnv4] undo policy vpn-target
[CE1-bgp-vpnv4] quit
[CE1-bgp] quit
# Configure PE 2 and CE 2 in the same way that PE 1 and CE 1 are configured. (Details not shown.)
6. Establish MP-IBGP peer relationships between sub-VPN PEs and CEs of the customer VPN to exchange VPNv4 routes of sub-VPNs:
# Configure PE 3.
[PE3] bgp 200
[PE3-bgp] peer 2.2.2.9 as-number 200
[PE3-bgp] peer 2.2.2.9 connect-interface loopback 0
[PE3-bgp] address-family vpnv4
[PE3-bgp-vpnv4] peer 2.2.2.9 enable
# Allow the local AS number to appear in the AS-PATH attribute of the routes received.
[PE3-bgp-vpnv4] peer 2.2.2.9 allow-as-loop 2
[PE3-bgp-vpnv4] quit
[PE3-bgp] quit
# Configure CE 1.
[CE1] bgp 200
[CE1-bgp] peer 1.1.1.9 as-number 200
[CE1-bgp] peer 1.1.1.9 connect-interface loopback 0
[CE1-bgp] address-family vpnv4
[CE1-bgp-vpnv4] peer 1.1.1.9 enable
[CE1-bgp-vpnv4] undo policy vpn-target
[CE1-bgp-vpnv4] quit
[CE1-bgp] quit
# Configure PE 4 and CE 2 in the same way that PE 3 and CE 1 are configured. (Details not shown.)
Verifying the configuration
1. Display the public routing table and VPN routing table on the provider PEs, for example, on PE 1:
# Verify that the public routing table contains only routes on the service provider network.
[PE1] display ip routing-table
Destinations : 14 Routes : 14
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
3.3.3.9/32 Direct 0 0 127.0.0.1 InLoop0
4.4.4.9/32 ISIS 15 10 30.1.1.2 Vlan2
30.1.1.0/24 Direct 0 0 30.1.1.1 Vlan2
30.1.1.0/32 Direct 0 0 30.1.1.1 Vlan2
30.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
30.1.1.255/32 Direct 0 0 30.1.1.1 Vlan2
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Verify that the VPN routing table contains sub-VPN routes.
[PE1] display ip routing-table vpn-instance vpn1
Destinations : 16 Routes : 16
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
11.1.1.0/24 Direct 0 0 11.1.1.2 Vlan1
11.1.1.0/32 Direct 0 0 11.1.1.2 Vlan1
11.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
11.1.1.255/32 Direct 0 0 11.1.1.1 Vlan1
100.1.1.0/24 BGP 255 0 11.1.1.1 NULL0
110.1.1.0/24 BGP 255 0 11.1.1.1 NULL0
120.1.1.0/24 BGP 255 0 4.4.4.9 NULL0
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
130.1.1.0/24 BGP 255 0 4.4.4.9 NULL0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
2. Display the VPNv4 routing table on the provider CEs, for example, on CE 1.
# Verify that the VPNv4 routing table on the customer VPN contains internal sub-VPN routes.
[CE1] display bgp routing-table vpnv4
BGP Local router ID is 2.2.2.9
Status codes: * - valid, > - best, d - damped, h - history,
s - suppressed, S - Stale, i - internal, e - external
Origin: i - IGP, e - EGP, ? - incomplete
Total number of routes from all PEs: 4
Route Distinguisher: 100:1
Total number of routes: 1
Network NextHop MED LocPrf PrefVal Path/Ogn
* > 100.1.1.0/24 1.1.1.9 0 100 0 200 65410?
Route Distinguisher: 101:1
Total number of routes: 1
Network NextHop MED LocPrf PrefVal Path/Ogn
* > 110.1.1.0/24 1.1.1.9 0 100 0 200 65411?
Route Distinguisher: 200:1
Total number of routes: 1
Network NextHop MED LocPrf PrefVal Path/Ogn
* > 120.1.1.0/24 11.1.1.2 0 100 200
65420?
Route Distinguisher: 201:1
Total number of routes: 1
Network NextHop MED LocPrf PrefVal Path/Ogn
* > 130.1.1.0/24 11.1.1.2 0 100 200
65421?
3. Display the VPN routing table on the customer PEs, for example, on PE 3:
# Verify that the VPN routing table contains routes sent by the provider PE to the sub-VPN.
[PE3] display ip routing-table vpn-instance SUB_VPN1
Destinations : 11 Routes : 11
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
100.1.1.0/24 Direct 0 0 100.1.1.2 Vlan1
100.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
120.1.1.0/24 BGP 255 0 2.2.2.9 Vlan2
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
4. Display the routing table on the CEs of sub-VPNs in the customer VPN, for example, on CE 3 and CE 5:
# Verify that the routing table contains the route to the remote sub-VPN on CE 3.
[CE3] display ip routing-table
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
100.1.1.0/24 Direct 0 0 100.1.1.1 Vlan1
100.1.1.0/32 Direct 0 0 100.1.1.1 Vlan1
100.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
100.1.1.255/32 Direct 0 0 100.1.1.1 Vlan1
120.1.1.0/24 BGP 255 0 100.1.1.2 Vlan1
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Verify that the routing table contains the route to the remote sub-VPN on CE 5.
[CE5] display ip routing-table
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
110.1.1.0/24 Direct 0 0 110.1.1.1 Vlan1
110.1.1.0/32 Direct 0 0 110.1.1.1 Vlan1
110.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
110.1.1.255/32 Direct 0 0 110.1.1.1 Vlan1
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
130.1.1.0/24 BGP 255 0 110.1.1.2 Vlan1
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
5. Verify that CE 3 and CE 4 can ping each other. (Details not shown.)
6. Verify that CE5 and CE 6 can ping each other. (Details not shown.)
7. Verify that CE 3 and CE 6 cannot ping each other. (Details not shown.)
Configuring HoVPN
Network requirements
There are two levels of networks, the backbone and the MPLS VPN networks, as shown in Figure 69.
· SPEs act as PEs to allow MPLS VPNs to access the backbone.
· UPEs act as PEs of the MPLS VPNs to allow end users to access the VPNs.
· Performance requirements for the UPEs are lower than those for the SPEs.
· SPEs advertise routes permitted by the routing policies to UPEs, permitting CE 1 and CE 3 in VPN 1 to communicate with each other, and forbidding CE 2 and CE 4 in VPN 2 from communicating with each other.
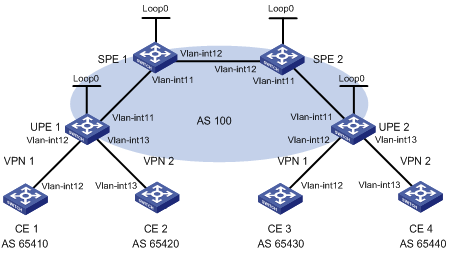
Table 19 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
Vlan-int12 |
10.2.1.1/24 |
CE 3 |
Vlan-int12 |
10.1.1.1/24 |
|
CE 2 |
Vlan-int13 |
10.4.1.1/24 |
CE 4 |
Vlan-int13 |
10.3.1.1/24 |
|
UPE 1 |
Loop0 |
1.1.1.9/32 |
UPE 2 |
Loop0 |
4.4.4.9/32 |
|
|
Vlan-int11 |
172.1.1.1/24 |
|
Vlan-int11 |
172.2.1.1/24 |
|
|
Vlan-int12 |
10.2.1.2/24 |
|
Vlan-int12 |
10.1.1.2/24 |
|
|
Vlan-int13 |
10.4.1.2/24 |
|
Vlan-int13 |
10.3.1.2/24 |
|
SPE 1 |
Loop0 |
2.2.2.9/32 |
SPE 2 |
Loop0 |
3.3.3.9/32 |
|
|
Vlan-int11 |
172.1.1.2/24 |
|
Vlan-int11 |
172.2.1.2/24 |
|
|
Vlan-int12 |
180.1.1.1/24 |
|
Vlan-int12 |
180.1.1.2/24 |
Configuration procedure
1. Configure UPE 1:
# Configure basic MPLS and MPLS LDP to establish LDP LSPs.
<UPE1> system-view
[UPE1] interface loopback 0
[UPE1-LoopBack0] ip address 1.1.1.9 32
[UPE1-LoopBack0] quit
[UPE1] mpls lsr-id 1.1.1.9
[UPE1] mpls ldp
[UPE1-ldp] quit
[UPE1] interface vlan-interface 11
[UPE1-Vlan-interface11] ip address 172.1.1.1 24
[UPE1-Vlan-interface11] mpls enable
[UPE1-Vlan-interface11] mpls ldp enable
[UPE1-Vlan-interface11] quit
# Configure the IGP protocol (OSPF, in this example).
[UPE1] ospf
[UPE1-ospf-1] area 0
[UPE1-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255
[UPE1-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0
[UPE1-ospf-1-area-0.0.0.0] quit
[UPE1-ospf-1] quit
# Configure VPN instances vpn1 and vpn2, allowing CE 1 and CE 2 to access UPE 1.
[UPE1] reserve-vlan-interface 3000 to 3050
[UPE1] ip vpn-instance vpn1
[UPE1-vpn-instance-vpn1] route-distinguisher 100:1
[UPE1-vpn-instance-vpn1] vpn-target 100:1 both
[UPE1-vpn-instance-vpn1] quit
[UPE1] ip vpn-instance vpn2
[UPE1-vpn-instance-vpn2] route-distinguisher 100:2
[UPE1-vpn-instance-vpn2] vpn-target 100:2 both
[UPE1-vpn-instance-vpn2] quit
[UPE1] interface vlan-interface 12
[UPE1-Vlan-interface12] ip binding vpn-instance vpn1
[UPE1-Vlan-interface12] ip address 10.2.1.2 24
[UPE1-Vlan-interface12] quit
[UPE1] interface vlan-interface 13
[UPE1-Vlan-interface13] ip binding vpn-instance vpn2
[UPE1-Vlan-interface13] ip address 10.4.1.2 24
[UPE1-Vlan-interface13] quit
# Establish an MP-IBGP peer relationship with SPE 1.
[UPE1] bgp 100
[UPE1-bgp] peer 2.2.2.9 as-number 100
[UPE1-bgp] peer 2.2.2.9 connect-interface loopback 0
[UPE1-bgp] address-family vpnv4
[UPE1-bgp-vpnv4] peer 2.2.2.9 enable
[UPE1-bgp-vpnv4] quit
# Establish an EBGP peer relationship with CE 1, and redistribute VPN routes into BGP.
[UPE1-bgp] ip vpn-instance vpn1
[UPE1-bgp-vpn1] peer 10.2.1.1 as-number 65410
[UPE1-bgp-vpn1] address-family ipv4 unicast
[UPE1-bgp-ipv4-vpn1] peer 10.2.1.1 enable
[UPE1-bgp-ipv4-vpn1] import-route direct
[UPE1-bgp-ipv4-vpn1] quit
[UPE1-bgp-vpn1] quit
# Establish an EBGP peer relationship with CE 2, and redistribute VPN routes into BGP.
[UPE1-bgp] ip vpn-instance vpn2
[UPE1-bgp-vpn2] peer 10.4.1.1 as-number 65420
[UPE1-bgp-vpn2] address-family ipv4 unicast
[UPE1-bgp-ipv4-vpn2] peer 10.4.1.1 enable
[UPE1-bgp-ipv4-vpn2] import-route direct
[UPE1-bgp-ipv4-vpn2] quit
[UPE1-bgp-vpn2] quit
[UPE1-bgp] quit
2. Configure CE 1.
<CE1> system-view
[CE1] interface vlan-interface 12
[CE1-Vlan-interface12] ip address 10.2.1.1 255.255.255.0
[CE1-Vlan-interface12] quit
[CE1] bgp 65410
[CE1-bgp] peer 10.2.1.2 as-number 100
[CE1-bgp] address-family ipv4 unicast
[CE1-bgp-ipv4] peer 10.2.1.2 enable
[CE1-bgp-ipv4] import-route direct
[CE1-bgp-ipv4] quit
[CE1-bgp] quit
3. Configure CE 2.
<CE2> system-view
[CE2] interface vlan-interface 13
[CE2-Vlan-interface13] ip address 10.4.1.1 255.255.255.0
[CE2-Vlan-interface13] quit
[CE2] bgp 65420
[CE2-bgp] peer 10.4.1.2 as-number 100
[CE2-bgp] address-family ipv4 unicast
[CE2-bgp-ipv4] peer 10.4.1.2 enable
[CE2-bgp-ipv4] import-route direct
[CE2-bgp-ipv4] quit
[CE2-bgp] quit
4. Configure UPE 2:
# Configure basic MPLS and MPLS LDP to establish LDP LSPs.
<UPE2> system-view
[UPE2] interface loopback 0
[UPE2-Loopback0] ip address 4.4.4.9 32
[UPE2-Loopback0] quit
[UPE2] mpls lsr-id 4.4.4.9
[UPE2] mpls ldp
[UPE2-ldp] quit
[UPE2] interface vlan-interface 11
[UPE2-Vlan-interface11] ip address 172.2.1.1 24
[UPE2-Vlan-interface11] mpls enable
[UPE2-Vlan-interface11] mpls ldp enable
[UPE2-Vlan-interface11] quit
# Configure the IGP protocol (OSPF, in this example).
[UPE2] ospf
[UPE2-ospf-1] area 0
[UPE2-ospf-1-area-0.0.0.0] network 172.2.1.0 0.0.0.255
[UPE2-ospf-1-area-0.0.0.0] network 4.4.4.9 0.0.0.0
[UPE2-ospf-1-area-0.0.0.0] quit
[UPE2-ospf-1] quit
# Configure VPN instances vpn1 and vpn2, allowing CE 3 and CE 4 to access UPE 2.
[UPE2] reserve-vlan-interface 3000 to 3050
[UPE2] ip vpn-instance vpn1
[UPE2-vpn-instance-vpn1] route-distinguisher 300:1
[UPE2-vpn-instance-vpn1] vpn-target 100:1 both
[UPE2-vpn-instance-vpn1] quit
[UPE2] ip vpn-instance vpn2
[UPE2-vpn-instance-vpn2] route-distinguisher 400:2
[UPE2-vpn-instance-vpn2] vpn-target 100:2 both
[UPE2-vpn-instance-vpn2] quit
[UPE2] interface vlan-interface 12
[UPE2-Vlan-interface12] ip binding vpn-instance vpn1
[UPE2-Vlan-interface12] ip address 10.1.1.2 24
[UPE2-Vlan-interface12] quit
[UPE2] interface vlan-interface 13
[UPE2-Vlan-interface13] ip binding vpn-instance vpn2
[UPE2-Vlan-interface13] ip address 10.3.1.2 24
[UPE2-Vlan-interface13] quit
# Establish an MP-IBGP peer relationship with SPE 2.
[UPE2] bgp 100
[UPE2-bgp] peer 3.3.3.9 as-number 100
[UPE2-bgp] peer 3.3.3.9 connect-interface loopback 0
[UPE2-bgp] address-family vpnv4
[UPE2-bgp-vpnv4] peer 3.3.3.9 enable
[UPE2-bgp-vpnv4] quit
# Establish an EBGP peer relationship with CE 3 and redistribute VPN routes.
[UPE2-bgp] ip vpn-instance vpn1
[UPE2-bgp-vpn1] peer 10.1.1.1 as-number 65430
[UPE2-bgp-vpn1] address-family ipv4 unicast
[UPE2-bgp-ipv4-vpn1] peer 10.1.1.1 enable
[UPE2-bgp-ipv4-vpn1] import-route direct
[UPE2-bgp-ipv4-vpn1] quit
[UPE2-bgp-vpn1] quit
# Establish an EBGP peer relationship with CE 4, and redistribute VPN routes into BGP.
[UPE2-bgp] ip vpn-instance vpn2
[UPE2-bgp-vpn2] peer 10.3.1.1 as-number 65440
[UPE2-bgp-vpn2] address-family ipv4 unicast
[UPE2-bgp-ipv4-vpn2] peer 10.3.1.1 enable
[UPE2-bgp-ipv4-vpn2] import-route direct
[UPE2-bgp-ipv4-vpn2] quit
[UPE2-bgp-vpn2] quit
[UPE2-bgp] quit
5. Configure CE 3.
<CE3> system-view
[CE3] interface vlan-interface 12
[CE3-Vlan-interface12] ip address 10.1.1.1 255.255.255.0
[CE3-Vlan-interface12] quit
[CE3] bgp 65430
[CE3-bgp] peer 10.1.1.2 as-number 100
[CE3-bgp] address-family ipv4 unicast
[CE3-bgp-ipv4] peer 10.1.1.2 enable
[CE3-bgp-ipv4] import-route direct
[CE3-bgp-ipv4] quit
[CE3-bgp] quit
6. Configure CE 4.
<CE4> system-view
[CE4] interface vlan-interface 13
[CE4-Vlan-interface13] ip address 10.3.1.1 255.255.255.0
[CE4-Vlan-interface13] quit
[CE4] bgp 65440
[CE4-bgp] peer 10.3.1.2 as-number 100
[CE4-bgp] address-family ipv4 unicast
[CE4-bgp-ipv4] peer 10.3.1.2 enable
[CE4-bgp-ipv4] import-route direct
[CE4-bgp-ipv4] quit
[CE4-bgp] quit
7. Configure SPE 1:
# Configure basic MPLS and MPLS LDP to establish LDP LSPs.
<SPE1> system-view
[SPE1] interface loopback 0
[SPE1-LoopBack0] ip address 2.2.2.9 32
[SPE1-LoopBack0] quit
[SPE1] mpls lsr-id 2.2.2.9
[SPE1] mpls ldp
[SPE1-ldp] quit
[SPE1] interface vlan-interface 11
[SPE1-Vlan-interface11] ip address 172.1.1.2 24
[SPE1-Vlan-interface11] mpls enable
[SPE1-Vlan-interface11] mpls ldp enable
[SPE1-Vlan-interface11] quit
[SPE1] interface vlan-interface 12
[SPE1-Vlan-interface12] ip address 180.1.1.1 24
[SPE1-Vlan-interface12] mpls enable
[SPE1-Vlan-interface12] mpls ldp enable
[SPE1-Vlan-interface12] quit
# Configure the IGP protocol (OSPF, in this example).
[SPE1] ospf
[SPE1-ospf-1] area 0
[SPE1-ospf-1-area-0.0.0.0] network 2.2.2.9 0.0.0.0
[SPE1-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255
[SPE1-ospf-1-area-0.0.0.0] network 180.1.1.0 0.0.0.255
[SPE1-ospf-1-area-0.0.0.0] quit
[SPE1-ospf-1] quit
# Configure VPN instances vpn1 and vpn2.
[SPE1] reserve-vlan-interface 3000 to 3050
[SPE1] ip vpn-instance vpn1
[SPE1-vpn-instance-vpn1] route-distinguisher 500:1
[SPE1-vpn-instance-vpn1] vpn-target 100:1 both
[SPE1-vpn-instance-vpn1] quit
[SPE1] ip vpn-instance vpn2
[SPE1-vpn-instance-vpn2] route-distinguisher 700:1
[SPE1-vpn-instance-vpn2] vpn-target 100:2 both
[SPE1-vpn-instance-vpn2] quit
# Establish MP-IBGP peer relationships with SPE 2 and UPE 1, and specify UPE 1 as a UPE.
[SPE1] bgp 100
[SPE1-bgp] peer 1.1.1.9 as-number 100
[SPE1-bgp] peer 1.1.1.9 connect-interface loopback 0
[SPE1-bgp] peer 3.3.3.9 as-number 100
[SPE1-bgp] peer 3.3.3.9 connect-interface loopback 0
[SPE1-bgp] address-family vpnv4
[SPE1-bgp-vpnv4] peer 3.3.3.9 enable
[SPE1-bgp-vpnv4] peer 1.1.1.9 enable
[SPE1-bgp-vpnv4] peer 1.1.1.9 upe
[SPE1-bgp-vpnv4] peer 1.1.1.9 next-hop-local
[SPE1-bgp-vpnv4] quit
# Create BGP-VPN instances for VPN instances vpn1 and vpn2, so the VPNv4 routes learned according to the RT attributes can be added into the BGP routing tables of the corresponding VPN instances.
[SPE1-bgp] ip vpn-instance vpn1
[SPE1-bgp-vpn1] quit
[SPE1-bgp] ip vpn-instance vpn2
[SPE1-bgp-vpn2] quit
[SPE1-bgp] quit
# Advertise to UPE 1 the routes permitted by a routing policy (the routes of CE 3).
[SPE1] ip prefix-list hope index 10 permit 10.1.1.1 24
[SPE1] route-policy hope permit node 0
[SPE1-route-policy-hope-0] if-match ip address prefix-list hope
[SPE1-route-policy-hope-0] quit
[SPE1] bgp 100
[SPE1-bgp] address-family vpnv4
[SPE1-bgp-vpnv4] peer 1.1.1.9 upe route-policy hope export
8. Configure SPE 2:
# Configure basic MPLS and MPLS LDP to establish LDP LSPs.
<SPE2> system-view
[SPE2] interface loopback 0
[SPE2-LoopBack0] ip address 3.3.3.9 32
[SPE2-LoopBack0] quit
[SPE2] mpls lsr-id 3.3.3.9
[SPE2] mpls ldp
[SPE2-ldp] quit
[SPE2] interface vlan-interface 12
[SPE2-Vlan-interface12] ip address 180.1.1.2 24
[SPE2-Vlan-interface12] mpls enable
[SPE2-Vlan-interface12] mpls ldp enable
[SPE2-Vlan-interface12] quit
[SPE2] interface vlan-interface 11
[SPE2-Vlan-interface11] ip address 172.2.1.2 24
[SPE2-Vlan-interface11] mpls enable
[SPE2-Vlan-interface11] mpls ldp enable
[SPE2-Vlan-interface11] quit
# Configure the IGP protocol (OSPF, in this example).
[SPE2] ospf
[SPE2-ospf-1] area 0
[SPE2-ospf-1-area-0.0.0.0] network 3.3.3.9 0.0.0.0
[SPE2-ospf-1-area-0.0.0.0] network 172.2.1.0 0.0.0.255
[SPE2-ospf-1-area-0.0.0.0] network 180.1.1.0 0.0.0.255
[SPE2-ospf-1-area-0.0.0.0] quit
[SPE2-ospf-1] quit
# Configure VPN instances vpn1 and vpn2.
[SPE2] reserve-vlan-interface 3000 to 3050
[SPE2] ip vpn-instance vpn1
[SPE2-vpn-instance-vpn1] route-distinguisher 600:1
[SPE2-vpn-instance-vpn1] vpn-target 100:1 both
[SPE2-vpn-instance-vpn1] quit
[SPE2] ip vpn-instance vpn2
[SPE2-vpn-instance-vpn2] route-distinguisher 800:1
[SPE2-vpn-instance-vpn2] vpn-target 100:2 both
[SPE2-vpn-instance-vpn2] quit
# Establish MP-IBGP peer relationships with SPE 1 and UPE 2, and specify UPE 2 as a UPE.
[SPE2] bgp 100
[SPE2-bgp] peer 4.4.4.9 as-number 100
[SPE2-bgp] peer 4.4.4.9 connect-interface loopback 0
[SPE2-bgp] peer 2.2.2.9 as-number 100
[SPE2-bgp] peer 2.2.2.9 connect-interface loopback 0
[SPE2-bgp] address-family vpnv4
[SPE2-bgp-vpnv4] peer 2.2.2.9 enable
[SPE2-bgp-vpnv4] peer 4.4.4.9 enable
[SPE2-bgp-vpnv4] peer 4.4.4.9 upe
[SPE2-bgp-vpnv4] peer 4.4.4.9 next-hop-local
[SPE2-bgp-vpnv4] quit
# Create BGP-VPN instances for VPN instances vpn1 and vpn2, so the VPNv4 routes learned according to the RT attributes can be added into the BGP routing tables of the corresponding VPN instances.
[SPE2-bgp] ip vpn-instance vpn1
[SPE2-bgp-vpn1] quit
[SPE2-bgp] ip vpn-instance vpn2
[SPE2-bgp-vpn2] quit
[SPE2-bgp] quit
# Advertise to UPE 2 the routes permitted by a routing policy (the routes of CE 1).
[SPE2] ip prefix-list hope index 10 permit 10.2.1.1 24
[SPE2] route-policy hope permit node 0
[SPE2-route-policy-hope-0] if-match ip address prefix-list hope
[SPE2-route-policy-hope-0] quit
[SPE2] bgp 100
[SPE2-bgp] address-family vpnv4
[SPE2-bgp-vpnv4] peer 4.4.4.9 upe route-policy hope export
Verifying the configuration
# Verify that CE 1 and CE3 can learn each other's interface routes and can ping each other. CE 2 and CE 4 cannot learn each other's interface routes and cannot ping each other. (Details not shown.)
Configuring an OSPF sham link
Network requirements
As shown in Figure 70, CE 1 and CE 2 belong to VPN 1. Configure an OSPF sham link between PE 1 and PE 2 so traffic between CE 1 and CE 2 is forwarded through the MPLS backbone, instead of the backdoor link.
Table 20 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
Vlan-int11 |
100.1.1.1/24 |
CE 2 |
Vlan-int11 |
120.1.1.1/24 |
|
|
Vlan-int13 |
20.1.1.1/24 |
|
Vlan-int12 |
30.1.1.2/24 |
|
PE 1 |
Loop0 |
1.1.1.9/32 |
PE 2 |
Loop0 |
2.2.2.9/32 |
|
|
Loop1 |
3.3.3.3/32 |
|
Loop1 |
5.5.5.5/32 |
|
|
Vlan-int11 |
100.1.1.2/24 |
|
Vlan-int11 |
120.1.1.2/24 |
|
|
Vlan-int12 |
10.1.1.1/24 |
|
Vlan-int12 |
10.1.1.2/24 |
|
Switch A |
Vlan-int11 |
20.1.1.2/24 |
|
|
|
|
|
Vlan-int12 |
30.1.1.1/24 |
|
|
|
Configuration procedure
1. Configure OSPF on the customer networks:
Configure conventional OSPF on CE 1, Switch A, and CE 2 to advertise addresses of the interfaces as shown in Figure 70. Execute the display ip routing-table command to verify that CE 1 and CE 2 have learned the route to each other. (Details not shown.)
2. Configure MPLS L3VPN on the backbone:
# Configure basic MPLS and MPLS LDP on PE 1 to establish LDP LSPs.
<PE1> system-view
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 1.1.1.9 32
[PE1-LoopBack0] quit
[PE1] mpls lsr-id 1.1.1.9
[PE1] mpls ldp
[PE1-ldp] quit
[PE1] interface vlan-interface 12
[PE1-Vlan-interface12] ip address 10.1.1.1 24
[PE1-Vlan-interface12] mpls enable
[PE1-Vlan-interface12] mpls ldp enable
[PE1-Vlan-interface12] quit
# Configure PE 1 to take PE 2 as an MP-IBGP peer.
[PE1] bgp 100
[PE1-bgp] peer 2.2.2.9 as-number 100
[PE1-bgp] peer 2.2.2.9 connect-interface loopback 0
[PE1-bgp] address-family vpnv4
[PE1-bgp-vpnv4] peer 2.2.2.9 enable
[PE1-bgp-vpnv4] quit
[PE1-bgp] quit
# Configure OSPF on PE 1.
[PE1]ospf 1
[PE1-ospf-1]area 0
[PE1-ospf-1-area-0.0.0.0]network 1.1.1.9 0.0.0.0
[PE1-ospf-1-area-0.0.0.0]network 10.1.1.0 0.0.0.255
[PE1-ospf-1-area-0.0.0.0]quit
[PE1-ospf-1]quit
# Configure basic MPLS and MPLS LDP on PE 2 to establish LDP LSPs.
<PE2> system-view
[PE2] interface loopback 0
[PE2-LoopBack0] ip address 2.2.2.9 32
[PE2-LoopBack0] quit
[PE2] mpls lsr-id 2.2.2.9
[PE2] mpls ldp
[PE2-ldp] quit
[PE2] interface vlan-interface 12
[PE2-Vlan-interface12] ip address 10.1.1.2 24
[PE2-Vlan-interface12] mpls enable
[PE2-Vlan-interface12] mpls ldp enable
[PE2-Vlan-interface12] quit
# Configure PE 2 to take PE 1 as an MP-IBGP peer.
[PE2] bgp 100
[PE2-bgp] peer 1.1.1.9 as-number 100
[PE2-bgp] peer 1.1.1.9 connect-interface loopback 0
[PE2-bgp] address-family vpnv4
[PE2-bgp-vpnv4] peer 1.1.1.9 enable
[PE2-bgp-vpnv4] quit
[PE2-bgp] quit
# Configure OSPF on PE 2.
[PE2]ospf 1
[PE2-ospf-1]area 0
[PE2-ospf-1-area-0.0.0.0]network 2.2.2.9 0.0.0.0
[PE2-ospf-1-area-0.0.0.0]network 10.1.1.0 0.0.0.255
[PE2-ospf-1-area-0.0.0.0]quit
[PE2-ospf-1]quit
3. Configure PEs to allow CE access:
# Configure PE 1.
[PE1] reserve-vlan-interface 3000 to 3050
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 100:1
[PE1-vpn-instance-vpn1] vpn-target 1:1
[PE1-vpn-instance-vpn1] quit
[PE1] interface vlan-interface 11
[PE1-Vlan-interface11] ip binding vpn-instance vpn1
[PE1-Vlan-interface11] ip address 100.1.1.2 24
[PE1-Vlan-interface11] quit
[PE1] ospf 100 vpn-instance vpn1
[PE1-ospf-100] domain-id 10
[PE1-ospf-100] area 1
[PE1-ospf-100-area-0.0.0.1] network 100.1.1.0 0.0.0.255
[PE1-ospf-100-area-0.0.0.1] quit
[PE1-ospf-100] quit
[PE2] bgp 100
[PE1-bgp] ip vpn-instance vpn1
[PE1-bgp-vpn1] address-family ipv4 unicast
[PE1-bgp-ipv4-vpn1] import-route ospf 100
[PE1-bgp-ipv4-vpn1] import-route direct
[PE1-bgp-ipv4-vpn1] quit
[PE1-bgp-vpn1] quit
[PE1-bgp] quit
# Configure PE 2.
[PE2] reserve-vlan-interface 3000 to 3050
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] route-distinguisher 100:2
[PE2-vpn-instance-vpn1] vpn-target 1:1
[PE2-vpn-instance-vpn1] quit
[PE2] interface vlan-interface 11
[PE2-Vlan-interface11] ip binding vpn-instance vpn1
[PE2-Vlan-interface11] ip address 120.1.1.2 24
[PE2-Vlan-interface11] quit
[PE2] ospf 100 vpn-instance vpn1
[PE2-ospf-100] domain-id 10
[PE2-ospf-100] area 1
[PE2-ospf-100-area-0.0.0.1] network 120.1.1.0 0.0.0.255
[PE2-ospf-100-area-0.0.0.1] quit
[PE2-ospf-100] quit
[PE2] bgp 100
[PE2-bgp] ip vpn-instance vpn1
[PE2-bgp-vpn1] address-family ipv4 unicast
[PE2-bgp-ipv4-vpn1] import-route ospf 100
[PE2-bgp-ipv4-vpn1] import-route direct
[PE2-bgp-ipv4-vpn1] quit
[PE2-bgp-vpn1] quit
[PE2-bgp] quit
# Execute the display ip routing-table vpn-instance command on the PEs to verify that the path to the peer CE is along the OSPF route across the customer networks, instead of the BGP route across the backbone. (Details not shown.)
4. Configure a sham link:
# Configure PE 1.
[PE1] interface loopback 1
[PE1-LoopBack1] ip binding vpn-instance vpn1
[PE1-LoopBack1] ip address 3.3.3.3 32
[PE1-LoopBack1] quit
[PE1] ospf 100
[PE1-ospf-100] area 1
[PE1-ospf-100-area-0.0.0.1] sham-link 3.3.3.3 5.5.5.5 cost 10
[PE1-ospf-100-area-0.0.0.1] quit
[PE1-ospf-100] quit
# Configure PE 2.
[PE2] interface loopback 1
[PE2-LoopBack1] ip binding vpn-instance vpn1
[PE2-LoopBack1] ip address 5.5.5.5 32
[PE2-LoopBack1] quit
[PE2] ospf 100
[PE2-ospf-100] area 1
[PE2-ospf-100-area-0.0.0.1] sham-link 5.5.5.5 3.3.3.3 cost 10
[PE2-ospf-100-area-0.0.0.1] quit
[PE2-ospf-100] quit
Verifying the configuration
# Execute the display ip routing-table vpn-instance command on the PEs to verify the following results: (Details not shown.)
· The path to the peer CE is now along the BGP route across the backbone.
· A route to the sham link destination address is present.
# Execute the display ip routing-table command on the CEs to verify that the next hop of the OSPF route to the peer CE is the VLAN interface 11 connected to the PE. The VPN traffic to the peer is forwarded over the backbone. (Details not shown.)
# Verify that a sham link has been established on PEs, for example, on PE 1.
[PE1] display ospf sham-link
OSPF Process 100 with Router ID 100.1.1.2
Sham link
Area Neighbor ID Source IP Destination IP State Cost
0.0.0.1 120.1.1.2 3.3.3.3 5.5.5.5 P-2-P 10
# Verify that the peer state is Full on PE 1.
[PE1] display ospf sham-link area 1
OSPF Process 100 with Router ID 100.1.1.2
Sham-Link: 3.3.3.3 --> 5.5.5.5
Neighbor ID: 120.1.1.2 State: Full
Area: 0.0.0.1
Cost: 10 State: P-2-P Type: Sham
Timers: Hello 10, Dead 40, Retransmit 5, Transmit Delay 1
Request list: 0 Retransmit list: 0
Configuring BGP AS number substitution
Network requirements
As shown in Figure 71, CE 1 and CE 2 belong to VPN 1 and are connected to PE 1 and PE 2, respectively. The two CEs have the same AS number, 600. Configure BGP AS number substitution on the PEs to enable the CEs to communicate with each other.
Table 21 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
Vlan-int11 |
10.1.1.1/24 |
P |
Loop0 |
2.2.2.9/32 |
|
|
Vlan-int12 |
100.1.1.1/24 |
|
Vlan-int11 |
30.1.1.1/24 |
|
PE 1 |
Loop0 |
1.1.1.9/32 |
|
Vlan-int12 |
20.1.1.2/24 |
|
|
Vlan-int11 |
10.1.1.2/24 |
PE 2 |
Loop0 |
3.3.3.9/32 |
|
|
Vlan-int12 |
20.1.1.1/24 |
|
Vlan-int11 |
30.1.1.2/24 |
|
CE 2 |
Vlan-int12 |
10.2.1.1/24 |
|
Vlan-int12 |
10.2.1.2/24 |
|
|
Vlan-int13 |
200.1.1.1/24 |
|
|
|
Configuration procedure
1. Configuring basic MPLS L3VPN:
? Configure OSPF on the MPLS backbone to allow the PEs and P device to learn the routes of the loopback interfaces from each other.
? Configure basic MPLS and MPLS LDP on the MPLS backbone to establish LDP LSPs.
? Establish MP-IBGP peer relationship between the PEs to advertise VPNv4 routes.
? Configure the VPN instance of VPN 1 on PE 2 to allow CE 2 to access the network.
? Configure the VPN instance of VPN 1 on PE 1 to allow CE 1 to access the network.
? Configure BGP between PE 1 and CE 1, and between PE 2 and CE 2 and redistribute routes of CEs into PEs.
For more information about basic MPLS L3VPN configurations, see "Configuring basic MPLS L3VPN."
# Execute the display ip routing-table command on CE 2. The output shows that CE 2 has learned the route to network 10.1.1.0/24, where the interface used by CE 1 to access PE 1 resides. However, it has not learned the route to the VPN (100.1.1.0/24) behind CE 1.
<CE2> display ip routing-table
Destinations : 17 Routes : 17
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.0/24 BGP 255 0 10.2.1.2 Vlan12
10.2.1.0/24 Direct 0 0 10.2.1.1 Vlan12
10.2.1.0/32 Direct 0 0 10.2.1.1 Vlan12
10.2.1.1/32 Direct 0 0 127.0.0.1 InLoop0
10.2.1.255/32 Direct 0 0 10.2.1.1 Vlan12
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
200.1.1.0/24 Direct 0 0 200.1.1.1 Vlan13
200.1.1.0/32 Direct 0 0 200.1.1.1 Vlan13
200.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
200.1.1.255/24 Direct 0 0 200.1.1.1 Vlan13
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Execute the display ip routing-table command on CE 1 to verify that CE 1 has not learned the route to the VPN behind CE 2. (Details not shown.)
# Execute the display ip routing-table vpn-instance command on the PEs. The output shows the route to the VPN behind the peer CE. This example uses PE 2.
<PE2> display ip routing-table vpn-instance vpn1
Destinations : 15 Routes : 15
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.0/24 BGP 255 0 1.1.1.9 Vlan11
10.2.1.0/24 Direct 0 0 10.2.1.2 Vlan12
10.2.1.0/32 Direct 0 0 10.2.1.2 Vlan12
10.2.1.2/32 Direct 0 0 127.0.0.1 InLoop0
10.2.1.255/32 Direct 0 0 10.2.1.2 Vlan12
100.1.1.0/24 BGP 255 0 1.1.1.9 Vlan11
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
200.1.1.0/24 BGP 255 0 10.2.1.1 Vlan12
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Enable BGP update packet debugging on PE 2. The output shows that PE 2 advertises the route to 100.1.1.1/32, and the AS_PATH is 100 600.
<PE2> terminal monitor
<PE2> terminal logging level 7
<PE2> debugging bgp update vpn-instance vpn1 10.2.1.1 ipv4
<PE2> refresh bgp all export ipv4 vpn-instance vpn1
*Jun 13 16:12:52:096 2012 PE2 BGP/7/DEBUG: -MDC=1;
BGP.vpn1: Send UPDATE to peer 10.2.1.1 for following destinations:
Origin : Incomplete
AS Path : 100 600
Next Hop : 10.2.1.2
100.1.1.0/24,
# Execute the display bgp routing-table ipv4 peer received-routes command on CE 2 to verify that CE 2 has not received the route to 100.1.1.0/24.
<CE2> display bgp routing-table ipv4 peer 10.2.1.2 received-routes
Total number of routes: 2
BGP local router ID is 200.1.1.1
Status codes: * - valid, > - best, d - dampened, h - history,
s - suppressed, S - stale, i - internal, e - external
Origin: i - IGP, e - EGP, ? - incomplete
Network NextHop MED LocPrf PrefVal Path/Ogn
* >e 10.1.1.0/24 10.2.1.2 0 100?
* e 10.2.1.0/24 10.2.1.2 0 0 100?
2. Configure BGP AS number substitution on PE 2.
<PE2> system-view
[PE2] bgp 100
[PE2-bgp] ip vpn-instance vpn1
[PE2-bgp-vpn1] peer 10.2.1.1 substitute-as
[PE2-bgp-vpn1] address-family ipv4 unicast
[PE2-bgp-ipv4-vpn1] peer 10.2.1.1 enable
[PE2-bgp-ipv4-vpn1] quit
[PE2-bgp-vpn1] quit
[PE2-bgp] quit
Verifying the configuration
# The output shows that among the routes advertised by PE 2 to CE 2, the AS_PATH of 100.1.1.0/24 has changed from 100 600 to 100 100.
*Jun 13 16:15:59:456 2012 PE2 BGP/7/DEBUG: -MDC=1;
BGP.vpn1: Send UPDATE to peer 10.2.1.1 for following destinations:
Origin : Incomplete
AS Path : 100 100
Next Hop : 10.2.1.2
100.1.1.0/24,
# Display again the routing information that CE 2 has received and the routing table.
<CE2> display bgp routing-table ipv4 peer 10.2.1.2 received-routes
Total number of routes: 3
BGP local router ID is 200.1.1.1
Status codes: * - valid, > - best, d - dampened, h - history,
s - suppressed, S - stale, i - internal, e - external
Origin: i - IGP, e - EGP, ? - incomplete
Network NextHop MED LocPrf PrefVal Path/Ogn
* >e 10.1.1.0/24 10.2.1.2 0 100?
* e 10.2.1.0/24 10.2.1.2 0 0 100?
* >e 100.1.1.0/24 10.2.1.2 0 100 100?
<CE2> display ip routing-table
Destinations : 18 Routes : 18
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.0/24 BGP 255 0 10.2.1.2 Vlan12
10.2.1.0/24 Direct 0 0 10.2.1.1 Vlan12
10.2.1.0/32 Direct 0 0 10.2.1.1 Vlan12
10.2.1.1/32 Direct 0 0 127.0.0.1 InLoop0
10.2.1.255/32 Direct 0 0 10.2.1.1 Vlan12
100.1.1.0/24 BGP 255 0 10.2.1.2 Vlan12
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
200.1.1.0/24 Direct 0 0 200.1.1.1 Vlan13
200.1.1.0/32 Direct 0 0 200.1.1.1 Vlan13
200.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
200.1.1.255/32 Direct 0 0 200.1.1.1 Vlan13
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Verify that the VLAN interfaces of CE 1 and CE 2 can ping each other. (Details not shown.)
Configuring MPLS L3VPN FRR through VPNv4 route backup for a VPNv4 route
Network requirements
CE 1 and CE 2 belong to VPN 1.
Configure EBGP between CEs and PEs to exchange VPN routes.
Configure OSPF to ensure connectivity between PEs, and configure MP-IBGP to exchange VPNv4 routing information between PEs.
Configure MPLS L3VPN FRR on PE 1 to achieve the following purposes:
· When the link PE 1—PE 2 operates correctly, traffic from CE 1 to CE 2 goes through the path CE 1—PE 1—PE 2—CE 2.
· When BFD detects that the LSP between PE 1 and PE 2 fails, traffic from CE 1 to CE 2 goes through the path CE 1—PE 1—PE 3—CE 2.
Figure 72 Network diagram
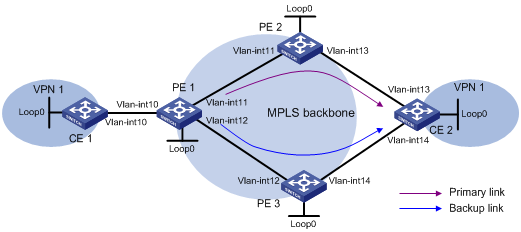
Table 22 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
Loop0 |
5.5.5.5/32 |
PE 1 |
Loop0 |
1.1.1.1/32 |
|
Vlan-int10 |
10.2.1.1/24 |
Vlan-int10 |
10.2.1.2/24 |
||
|
PE 2 |
Loop0 |
2.2.2.2/32 |
Vlan-int11 |
172.1.1.1/24 |
|
|
Vlan-int11 |
172.1.1.2/24 |
Vlan-int12 |
172.2.1.1/24 |
||
|
Vlan-int13 |
10.1.1.2/24 |
CE 2 |
Loop0 |
4.4.4.4/32 |
|
|
PE 3 |
Loop0 |
3.3.3.3/32 |
Vlan-int13 |
10.1.1.1/24 |
|
|
Vlan-int12 |
172.2.1.3/24 |
Vlan-int14 |
10.3.1.1/24 |
||
|
Vlan-int14 |
10.3.1.2/24 |
Configuration procedure
1. Configure IP addresses and masks for interfaces as shown in Table 22, and configure BGP and MPLS L3VPN. (Details not shown.)
For more information about configuring basic MPLS L3VPN, see "Configuring basic MPLS L3VPN."
2. Configure MPLS L3VPN FRR on PE 1:
# Configure BFD to test the connectivity of the LSP to 2.2.2.2/32.
<PE1> system-view
[PE1] mpls bfd enable
[PE1] mpls bfd 2.2.2.2 32
# Create routing policy frr, and specify the backup next hop as 3.3.3.3 for the route to 4.4.4.4/32.
[PE1] ip prefix-list abc index 10 permit 4.4.4.4 32
[PE1] route-policy frr permit node 10
[PE1-route-policy] if-match ip address prefix-list abc
[PE1-route-policy] apply fast-reroute backup-nexthop 3.3.3.3
[PE1-route-policy] quit
# Configure FRR for VPN instance vpn1 to reference routing policy frr.
[PE1] bgp 100
[PE1-bgp] ip vpn-instance vpn1
[PE1-bgp-vpn1] address-family ipv4 unicast
[PE1-bgp-ipv4-vpn1] fast-reroute route-policy frr
[PE1-bgp-ipv4-vpn1] quit
[PE1-bgp-vpn1] quit
# Specify the preferred value as 100 for BGP VPNv4 routes received from PE 2. This value is greater than the preferred value (0) for routes from PE 3, so PE 1 prefers the routes from PE 2.
[PE1-bgp] address-family vpnv4
[PE1-bgp-vpnv4] peer 2.2.2.2 preferred-value 100
[PE1-bgp-vpnv4] quit
[PE1-bgp] quit
3. Enable MPLS BFD on PE 2.
<PE2> system-view
[PE2] mpls bfd enable
Verifying the configuration
# Display detailed information about the route to 4.4.4.4/32 on PE 1. The output shows the backup next hop for the route.
[PE1] display ip routing-table vpn-instance vpn1 4.4.4.4 32 verbose
Summary Count : 1
Destination: 4.4.4.4/32
Protocol: BGP Process ID: 0
SubProtID: 0x1 Age: 00h00m03s
Cost: 0 Preference: 255
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x102 OrigAs: 300
NibID: 0x15000002 LastAs: 300
AttrID: 0x2 Neighbor: 2.2.2.2
Flags: 0x110060 OrigNextHop: 2.2.2.2
Label: 1146 RealNextHop: 172.1.1.2
BkLabel: 1275 BkNextHop: 172.2.1.3
Tunnel ID: Invalid Interface: Vlan-int11
BkTunnel ID: Invalid BkInterface: Vlan-int12
FtnIndex: 0x0
Configuring MPLS L3VPN FRR through VPNv4 route backup for an IPv4 route
Network requirements
CE 1 and CE 2 belong to VPN 1.
Configure EBGP between CEs and PEs to exchange VPN routes.
Configure OSPF to ensure connectivity between PEs, and configure MP-IBGP to exchange VPNv4 routing information between PEs.
Configure MPLS L3VPN FRR on PE 2 to achieve the following purposes:
· When the link PE 2—CE 2 operates correctly, traffic from CE 1 to CE 2 goes through the path CE 1—PE 1—PE 2—CE 2.
· When BFD detects that the link between PE 2 and CE 2 fails, traffic from CE 1 to CE 2 goes through the path CE 1—PE 1—PE 2—PE 3—CE 2.
Figure 73 Network diagram
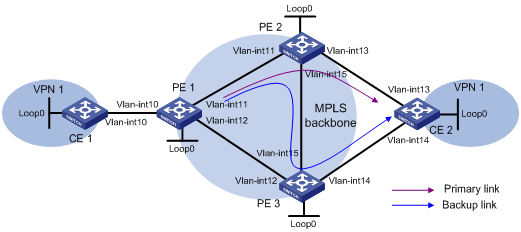
Table 23 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
Loop0 |
5.5.5.5/32 |
PE 2 |
Loop0 |
2.2.2.2/32 |
|
Vlan-int10 |
10.2.1.1/24 |
Vlan-int11 |
172.1.1.2/24 |
||
|
PE 1 |
Loop0 |
1.1.1.1/32 |
Vlan-int13 |
10.1.1.2/24 |
|
|
Vlan-int10 |
10.2.1.2/24 |
Vlan-int15 |
172.3.1.2/24 |
||
|
Vlan-int11 |
172.1.1.1/24 |
PE 3 |
Loop0 |
3.3.3.3/32 |
|
|
Vlan-int12 |
172.2.1.1/24 |
Vlan-int12 |
172.2.1.3/24 |
||
|
CE 2 |
Loop0 |
4.4.4.4/32 |
Vlan-int14 |
10.3.1.2/24 |
|
|
Vlan-int13 |
10.1.1.1/24 |
Vlan-int15 |
172.3.1.3/24 |
||
|
Vlan-int14 |
10.3.1.1/24 |
Configuration procedure
1. Configure IP addresses and masks for interfaces as shown in Table 23, and configure BGP and MPLS L3VPN. (Details not shown.)
For more information about configuring basic MPLS L3VPN, see "Configuring basic MPLS L3VPN."
2. Configure MPLS L3VPN FRR on PE 2:
# Configure the source IP address of BFD echo packets as 12.1.1.1.
<PE2> system-view
[PE2] bfd echo-source-ip 12.1.1.1
# Create routing policy frr, and specify the backup next hop as 3.3.3.3 for the route to 4.4.4.4/32.
[PE2] ip prefix-list abc index 10 permit 4.4.4.4 32
[PE2] route-policy frr permit node 10
[PE2-route-policy] if-match ip address prefix-list abc
[PE2-route-policy] apply fast-reroute backup-nexthop 3.3.3.3
[PE2-route-policy] quit
# Use echo-mode BFD to detect the primary route connectivity.
[PE2] bgp 100
[PE2-bgp] primary-path-detect bfd echo
# Configure FRR for VPN instance vpn1 to reference routing policy frr.
[PE2-bgp] ip vpn-instance vpn1
[PE2-bgp-vpn1] address-family ipv4 unicast
[PE2-bgp-ipv4-vpn1] fast-reroute route-policy frr
# Specify the preferred value as 200 for BGP routes received from CE 2. This value is greater than the preferred value (0) for routes from PE 3, so PE 2 prefers the routes from CE 2.
[PE2-bgp-ipv4-vpn1] peer 10.1.1.1 preferred-value 200
[PE2-bgp-vpn1] quit
[PE2-bgp] quit
Verifying the configuration
# Display detailed information about the route to 4.4.4.4/32 on PE 2. The output shows the backup next hop for the route.
[PE2] display ip routing-table vpn-instance vpn1 4.4.4.4 32 verbose
Summary Count : 1
Destination: 4.4.4.4/32
Protocol: BGP Process ID: 0
SubProtID: 0x2 Age: 01h54m24s
Cost: 0 Preference: 10
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: vpn1
TableID: 0x102 OrigAs: 300
NibID: 0x15000002 LastAs: 300
AttrID: 0x0 Neighbor: 10.1.1.1
Flags: 0x10060 OrigNextHop: 10.1.1.1
Label: NULL RealNextHop: 10.1.1.1
BkLabel: 1275 BkNextHop: 172.3.1.3
Tunnel ID: Invalid Interface: Vlan-int13
BkTunnel ID: 0x409 BkInterface: Vlan-int15
FtnIndex: 0x0
Configuring MPLS L3VPN FRR through IPv4 route backup for a VPNv4 route
Network requirements
CE 1 and CE 2 belong to VPN 1.
Configure EBGP between CEs and PEs to exchange VPN routes.
Configure OSPF to ensure connectivity between PEs, and configure MP-IBGP to exchange VPNv4 routing information between PEs.
Configure MPLS L3VPN FRR on PE 2 to achieve the following purposes:
· When the link PE 2—PE 3 operates correctly, traffic from CE 1 to CE 2 goes through the path CE 1—PE 1—PE 2—PE 3—CE 2.
· When BFD detects that the link between PE 2 and PE 3 fails, traffic from CE 1 to CE 2 goes through the path CE 1—PE 1—PE 2—CE 2.
Figure 74 Network diagram
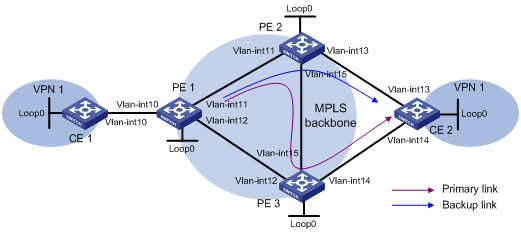
Table 24 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
Loop0 |
5.5.5.5/32 |
PE 2 |
Loop0 |
2.2.2.2/32 |
|
Vlan-int10 |
10.2.1.1/24 |
Vlan-int11 |
172.1.1.2/24 |
||
|
PE 1 |
Loop0 |
1.1.1.1/32 |
Vlan-int13 |
10.1.1.2/24 |
|
|
Vlan-int10 |
10.2.1.2/24 |
Vlan-int15 |
172.3.1.2/24 |
||
|
Vlan-int11 |
172.1.1.1/24 |
PE 3 |
Loop0 |
3.3.3.3/32 |
|
|
Vlan-int12 |
172.2.1.1/24 |
Vlan-int12 |
172.2.1.3/24 |
||
|
CE 2 |
Loop0 |
4.4.4.4/32 |
Vlan-int14 |
10.3.1.2/24 |
|
|
Vlan-int13 |
10.1.1.1/24 |
Vlan-int15 |
172.3.1.3/24 |
||
|
Vlan-int14 |
10.3.1.1/24 |
Configuration procedure
1. Configure IP addresses and masks for interfaces as shown in Table 24, and configure BGP and MPLS L3VPN. (Details not shown.)
For more information about configuring basic MPLS L3VPN, see "Configuring basic MPLS L3VPN."
2. Configure MPLS L3VPN FRR on PE 2:
# Configure BFD to test the connectivity of the LSP to 3.3.3.3/32.
<PE2> system-view
[PE2] mpls bfd enable
[PE2] mpls bfd 3.3.3.3 32
# Create routing policy frr, and specify the backup next hop as 10.1.1.1 for the route to 4.4.4.4/32.
[PE2] ip prefix-list abc index 10 permit 4.4.4.4 32
[PE2] route-policy frr permit node 10
[PE2-route-policy] if-match ip address prefix-list abc
[PE2-route-policy] apply fast-reroute backup-nexthop 10.1.1.1
[PE2-route-policy] quit
# Configure FRR for VPN instance vpn1 to reference routing policy frr.
[PE2] bgp 100
[PE2-bgp] ip vpn-instance vpn1
[PE2-bgp-vpn1] address-family ipv4 unicast
[PE2-bgp-ipv4-vpn1] fast-reroute route-policy frr
[PE2-bgp-ipv4-vpn1] quit
[PE2-bgp-vpn1] quit
# Specify the preferred value as 200 for BGP VPNv4 routes received from PE 3. This value is greater than the preferred value (0) for IPv4 unicast routes from CE 2, so PE 2 prefers the routes from PE 3.
[PE2-bgp] address-family vpnv4
[PE2-bgp-vpnv4] peer 3.3.3.3 preferred-value 200
[PE2-bgp-vpnv4] quit
[PE2-bgp] quit
3. Enable MPLS BFD on PE 3.
<PE3> system-view
[PE3] mpls bfd enable
Verifying the configuration
# Display detailed information about the route to 4.4.4.4/32 on PE 2. The output shows the backup next hop for the route.
[PE2] display ip routing-table vpn-instance vpn1 4.4.4.4 32 verbose
Summary Count : 1
Destination: 4.4.4.4/32
Protocol: BGP Process ID: 0
SubProtID: 0x1 Age: 00h00m04s
Cost: 0 Preference: 255
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x102 OrigAs: 300
NibID: 0x15000004 LastAs: 300
AttrID: 0x1 Neighbor: 3.3.3.3
Flags: 0x110060 OrigNextHop: 3.3.3.3
Label: 1275 RealNextHop: 172.3.1.3
BkLabel: NULL BkNextHop: 10.1.1.1
Tunnel ID: 0x409 Interface: Vlan-int15
BkTunnel ID: Invalid BkInterface: Vlan-int13
Configuring MCE
This chapter describes MCE configuration. For information about the related routing protocols, see Layer 3—IP Routing Configuration Guide.
MPLS L3VPN overview
MPLS L3VPN is a L3VPN technology used to interconnect geographically dispersed VPN sites. MPLS L3VPN uses BGP to advertise VPN routes and uses MPLS to forward VPN packets over a service provider backbone.
MPLS L3VPN provides flexible networking modes, excellent scalability, and convenient support for MPLS TE.
Basic MPLS L3VPN architecture
Figure 75 Basic MPLS L3VPN architecture
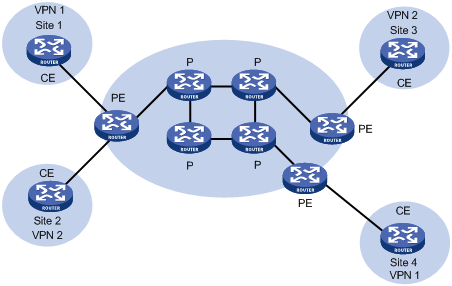
A basic MPLS L3VPN architecture has the following types of devices:
· Customer edge device—A CE device resides on a customer network and has one or more interfaces directly connected to a service provider network. It does not support VPN or MPLS.
· Provider edge device—A PE device resides at the edge of a service provider network and connects to one or more CEs. All MPLS VPN services are processed on PEs.
· Provider device—A P device is a core device on a service provider network. It is not directly connected to any CE. A P device has only basic MPLS forwarding capability and does not handle VPN routing information.
MPLS L3VPN concepts
Site
A site has the following features:
· A site is a group of IP systems with IP connectivity that does not rely on any service provider network.
· The classification of a site depends on the topology relationship of the devices, rather than the geographical positions, though the devices at a site are, in most cases, adjacent to each other geographically.
· The devices at a site can belong to multiple VPNs, which means that a site can belong to multiple VPNs.
· A site is connected to a provider network through one or more CEs. A site can contain multiple CEs, but a CE can belong to only one site.
Sites connected to the same provider network can be classified into different sets by policies. Only the sites in the same set can access each other through the provider network. Such a set is called a VPN.
VPN instance
VPN instances, also called virtual routing and forwarding (VRF) instances, implement route isolation, data independence, and data security for VPNs.
A VPN instance has the following components:
· A separate Label Forwarding Information Base (LFIB).
· An IP routing table.
· Interfaces bound to the VPN instance.
· VPN instance administration information, including route distinguishers (RDs), route targets (RTs), and route filtering policies.
To associate a site with a VPN instance, bind the VPN instance to the PE's interface connected to the site. A site can be associated with only one VPN instance, and different sites can associate with the same VPN instance. A VPN instance contains the VPN membership and routing rules of associated sites.
Address space overlapping
Each VPN independently manages its address space.
The address spaces of VPNs might overlap. For example, if both VPN 1 and VPN 2 use the addresses on subnet 10.110.10.0/24, address space overlapping occurs.
VPN-IPv4 address
BGP cannot process overlapping VPN address spaces. For example, if both VPN 1 and VPN 2 use the subnet 10.110.10.0/24 and each advertise a route destined for the subnet, BGP selects only one of them, resulting in the loss of the other route.
Multiprotocol BGP (MP-BGP) can solve this problem by advertising VPN-IPv4 prefixes.
Figure 76 VPN-IPv4 address structure

As shown in Figure 76, a VPN-IPv4 address consists of 12 bytes. The first eight bytes represent the RD, followed by a four-byte IPv4 prefix. The RD and the IPv4 prefix form a unique VPN-IPv4 prefix.
An RD can be in one of the following formats:
· When the Type field is 0, the Administrator subfield occupies two bytes, the Assigned number subfield occupies four bytes, and the RD format is 16-bit AS number:32-bit user-defined number. For example, 100:1.
· When the Type field is 1, the Administrator subfield occupies four bytes, the Assigned number subfield occupies two bytes, and the RD format is 32-bit IPv4 address:16-bit user-defined number. For example, 172.1.1.1:1.
· When the Type field is 2, the Administrator subfield occupies four bytes, the Assigned number subfield occupies two bytes, and the RD format is 32-bit AS number:16-bit user-defined number, where the minimum value of the AS number is 65536. For example, 65536:1.
To guarantee global uniqueness for an RD, do not set the Administrator subfield to any private AS number or private IP address.
Route target attribute
MPLS L3VPN uses route target community attributes to control the advertisement of VPN routing information. A VPN instance on a PE supports the following types of route target attributes:
· Export target attribute—A PE sets the export target attribute for VPN-IPv4 routes learned from directly connected sites before advertising them to other PEs.
· Import target attribute—A PE checks the export target attribute of VPN-IPv4 routes received from other PEs. If the export target attribute matches the import target attribute of a VPN instance, the PE adds the routes to the routing table of the VPN instance.
Route target attributes define which sites can receive VPN-IPv4 routes, and from which sites a PE can receive routes.
Like RDs, route target attributes can be one of the following formats:
· 16-bit AS number:32-bit user-defined number. For example, 100:1.
· 32-bit IPv4 address:16-bit user-defined number. For example, 172.1.1.1:1.
· 32-bit AS number:16-bit user-defined number, where the minimum value of the AS number is 65536. For example, 65536:1.
MCE overview
BGP/MPLS VPN transmits private network data through MPLS tunnels over the public network. However, the traditional MPLS L3VPN architecture requires that each VPN instance use an exclusive CE to connect to a PE, as shown in Figure 75.
A private network is typically divided into multiple VPNs to isolate services. To meet these requirements, you can configure a CE for each VPN, which increases device expense and maintenance costs. Or, you can configure multiple VPNs to use the same CE and the same routing table, which sacrifices data security.
You can use the Multi-VPN Instance CE (MCE) function in multi-VPN networks. MCE allows you to bind each VPN to a VLAN interface. The MCE creates and maintains a separate routing table for each VPN. This separates the forwarding paths of packets of different VPNs and, in conjunction with the PE, can correctly advertise the routes of each VPN to the peer PE, ensuring the normal transmission of VPN packets over the public network.
Figure 77 Network diagram for the MCE function
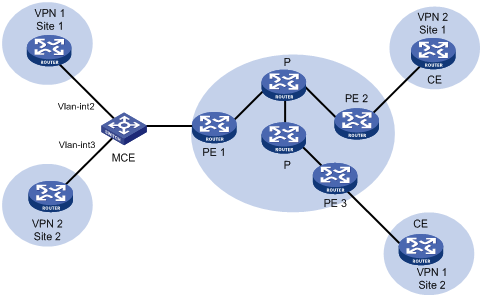
As shown in Figure 77, the MCE device creates a routing table for each VPN. VLAN interface 2 binds to VPN 1 and VLAN-interface 3 binds to VPN 2. When receiving a route, the MCE device determines the source of the routing information according to the number of the receiving interface, and then adds it to the corresponding routing table. The MCE connects to PE 1 through a trunk link that permits packets tagged with VLAN 2 or VLAN 3. PE 1 determines the VPN that a received packet belongs to according to the VLAN tag of the packet, and sends the packet through the corresponding tunnel.
You can configure static routes, RIP, OSPF, IS-IS, EBGP, or IBGP between an MCE and a VPN site and between an MCE and a PE.
|
|
NOTE: To implement dynamic IP assignment for DHCP clients in private networks, you can configure DHCP server or DHCP relay agent on the MCE. When the MCE functions as the DHCP server, the IP addresses assigned to different private networks cannot overlap. |
MCE configuration task list
|
Tasks at a glance |
|
|
1. (Required.) Creating a VPN instance 2. (Required.) Associating a VPN instance with an interface 3. (Optional.) Configuring route related attributes for a VPN instance |
|
|
Configuring routing on an MCE: · (Required.) Configuring routing between an MCE and a VPN site · (Required.) Configuring routing between an MCE and a PE |
Configuring VPN instances
VPN instances isolate VPN routes from public network routes and routes among VPNs. You must configure VPN instances for an MCE networking scheme.
Creating a VPN instance
A VPN instance is a collection of the VPN membership and routing rules of its associated site. A VPN instance might not correspond to one VPN.
To create and configure a VPN instance:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a VPN instance and enter VPN instance view. |
ip vpn-instance vpn-instance-name |
By default, no VPN instance is created. |
|
3. Configure an RD for the VPN instance. |
route-distinguisher route-distinguisher |
By default, no RD is specified for a VPN instance. |
|
4. (Optional.) Configure a description for the VPN instance. |
description text |
By default, no description is configured for a VPN instance. |
|
5. (Optional.) Configure a VPN ID for the VPN instance. |
vpn-id vpn-id |
By default, no VPN ID is configured for a VPN instance. |
Associating a VPN instance with an interface
After creating and configuring a VPN instance, associate the VPN instance with the MCE's interface connected to the site and the interface connected to the PE.
To associate a VPN instance with an interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Associate a VPN instance with the interface. |
ip binding vpn-instance vpn-instance-name |
By default, no VPN instance is associated with an interface. The ip binding vpn-instance command deletes the IP address of the current interface. You must re-configure an IP address for the interface after configuring the command. |
Configuring route related attributes for a VPN instance
VPN routes are controlled and advertised on a PE by using the following process:
1. When a VPN route learned from a site gets redistributed into BGP, BGP associates it with a route target extended community attribute list, which is typically the export target attribute of the VPN instance associated with the site.
2. The VPN instance determines which routes it can accept and redistribute according to the import-extcommunity in the route target.
3. The VPN instance determines how to change the route target attributes for routes to be advertised according to the export-extcommunity in the route target.
To configure route related attributes for a VPN instance:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VPN instance view or IPv4 VPN view. |
·
Enter VPN instance view: · Enter IPv4 VPN view: a. ip vpn-instance vpn-instance-name b. address-family ipv4 |
An IPv4 VPN prefers the configurations in IPv4 VPN view over the configurations in VPN instance view. |
|
3. Configure route targets. |
vpn-target vpn-target&<1-8> [ both | export-extcommunity | import-extcommunity ] |
By default, no route targets are configured. |
|
4. Set the maximum number of active routes allowed. |
routing-table limit number { warn-threshold | simply-alert } |
By default, the maximum number of active routes in the VPN instance is not limited. Setting the maximum number of active routes for a VPN instance can prevent the PE from learning too many routes. |
|
5. Apply an import routing policy. |
import route-policy route-policy |
By default, all routes matching the import target attribute are accepted. The specified routing policy must have been created. For information about routing policies, see Layer 3—IP Routing Configuration Guide. |
|
6. Apply an export routing policy. |
export route-policy route-policy |
By default, routes to be advertised are not filtered. The specified routing policy must have been created. For information about routing policies, see Layer 3—IP Routing Configuration Guide. |
Configuring routing on an MCE
MCE implements service isolation through route isolation. MCE routing configuration includes the following:
· MCE-VPN site routing configuration.
· MCE-PE routing configuration.
On the PE, disable routing loop detection to avoid route loss during route calculation, and disable route redistribution between routing protocols to save system resources.
Before you configure routing on an MCE, complete the following tasks:
· Configure VPN instances, and bind the VPN instances with the interfaces connected to the VPN sites and the PE.
· Configure the link layer and network layer protocols on related interfaces to ensure IP connectivity.
Configuring routing between an MCE and a VPN site
You can configure static routing, RIP, OSPF, IS-IS, EBGP, or IBGP between an MCE and a VPN site.
Configuring static routing between an MCE and a VPN site
An MCE can reach a VPN site through a static route. Static routing on a traditional CE is globally effective and does not support address overlapping among VPNs. An MCE supports binding a static route to a VPN instance, so that the static routes of different VPN instances can be isolated from each other.
To configure a static route to a VPN site:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a static route for a VPN instance. |
ip route-static vpn-instance s-vpn-instance-name dest-address { mask-length | mask } { interface-type interface-number [ next-hop-address ] | next-hop-address [ public ] [ track track-entry-number ] | vpn-instance d-vpn-instance-name next-hop-address [ track track-entry-number ] } [ permanent ] [ preference preference-value ] [ tag tag-value ] [ description description-text ] |
By default, no static route is configured. Perform this configuration on the MCE. On the VPN site, configure a common static route. |
|
3. (Optional.) Configure the default preference for static routes. |
ip route-static default-preference default-preference-value |
The default preference is 60. |
Configuring RIP between an MCE and a VPN site
A RIP process belongs to the public network or a single VPN instance. If you create a RIP process without binding it to a VPN instance, the process belongs to the public network. Binding RIP processes to VPN instances can isolate routes of different VPNs. For more information about RIP, see Layer 3—IP Routing Configuration Guide.
To configure RIP between an MCE and a VPN site:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a RIP process for a VPN instance and enter RIP view. |
rip [ process-id ] vpn-instance vpn-instance-name |
Perform this configuration on the MCE. On a VPN site, create a common RIP process. |
|
3. Enable RIP on the interface attached to the specified network. |
network network-address |
By default, RIP is disabled on an interface. |
|
4. Redistribute remote site routes advertised by the PE into RIP. |
import-route protocol [ process-id ] [ allow-ibgp ] [ cost cost | route-policy route-policy-name | tag tag ] * |
By default, no route is redistributed into RIP. |
|
5. (Optional.) Configure the default cost value for the redistributed routes. |
default cost value |
The default cost is 0. |
Configuring OSPF between an MCE and a VPN site
An OSPF process belongs to the public network or a single VPN instance. If you create an OSPF process without binding it to a VPN instance, the process belongs to the public network.
Binding OSPF processes to VPN instances can isolate routes of different VPNs. For more information about OSPF, see Layer 3—IP Routing Configuration Guide.
To configure OSPF between an MCE and a VPN site:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an OSPF process for a VPN instance and enter OSPF view. |
ospf [ process-id | router-id router-id | vpn-instance vpn-instance-name ] * |
Perform this configuration on the MCE. On a VPN site, create a common OSPF process. An OSPF process bound to a VPN instance does not use the public network router ID configured in system view. Therefore, configure a router ID for the OSPF process. An OSPF process can belong to only one VPN instance, but one VPN instance can use multiple OSPF processes to advertise VPN routes. |
|
3. (Optional.) Configure the OSPF domain ID. |
domain-id domain-id [ secondary ] |
The default domain ID is 0. Perform this configuration on the MCE. All OSPF processes of the same VPN instance must be configured with the same OSPF domain ID to ensure correct route advertisement. |
|
4. (Optional.) Configure the type codes of OSPF extended community attributes. |
ext-community-type { domain-id type-code1 | router-id type-code2 | route-type type-code3 } |
The defaults are as follows: · 0x0005 for Domain ID. · 0x0107 for Router ID. · 0x0306 for Route Type. |
|
5. (Optional.) Configure the external route tag for imported VPN routes. |
route-tag tag-value |
By default, no route tag is configured. In some networks, a VPN might be connected to multiple MCEs. When one MCE advertises the routes learned from BGP to the VPN, the other MCEs might learn the routes, resulting in routing loops. To avoid such routing loops, you can configure route tags for VPN instances on an MCE. As a best practice, configure the same route tag for the same VPN on the MCEs. |
|
6. Redistribute remote site routes advertised by the PE into OSPF. |
import-route protocol [ process-id | all-processes | allow-ibgp ] [ cost cost | route-policy route-policy-name | tag tag | type type ] * |
By default, no routes are redistributed into OSPF. |
|
7. (Optional.) Configure OSPF to redistribute the default route. |
default-route-advertise summary cost cost |
By default, OSPF does not redistribute the default route. This command redistributes the default route in a Type-3 LSA. The MCE advertises the default route to the site. |
|
8. Create an OSPF area and enter OSPF area view. |
area area-id |
By default, no OSPF area is created. |
|
9. Enable OSPF on the interface attached to the specified network in the area. |
network ip-address wildcard-mask |
By default, an interface neither belongs to any area nor runs OSPF. |
Configuring IS-IS between an MCE and a VPN site
An IS-IS process belongs to the public network or a single VPN instance. If you create an IS-IS process without binding it to a VPN instance, the process belongs to the public network.
Binding IS-IS processes to VPN instances can isolate routes of different VPNs. For more information about IS-IS, see Layer 3—IP Routing Configuration Guide.
To configure IS-IS between an MCE and a VPN site:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an IS-IS process for a VPN instance and enter IS-IS view. |
isis [ process-id ] vpn-instance vpn-instance-name |
Perform this configuration on the MCE. On a VPN site, configure a common IS-IS process. |
|
3. Configure a network entity title. |
network-entity net |
By default, no NET is configured. |
|
4. Redistribute remote site routes advertised by the PE into IS-IS. |
import-route protocol [ process-id | all-processes | allow-ibgp ] [ cost cost | cost-type { external | internal } | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] * |
By default, IS-IS does not redistribute routes from any other routing protocol. If you do not specify the route level in the command, the command redistributes routes to the level-2 routing table by default. |
|
5. Return to system view. |
quit |
N/A |
|
6. Enter interface view. |
interface interface-type interface-number |
N/A |
|
7. Enable the IS-IS process on the interface. |
isis enable [ process-id ] |
By default, no IS-IS process is enabled. |
Configuring EBGP between an MCE and a VPN site
To run EBGP between an MCE and a VPN site, you must configure a BGP peer for each VPN instance on the MCE, and redistribute the IGP routes of each VPN instance on the VPN site.
You can configure filtering policies to filter received routes and advertised routes.
1. Configure the MCE:
Routes redistributed from OSPF to BGP have their OSPF attributes removed. To enable BGP to distinguish routes redistributed from different OSPF domains, you must enable the redistributed routes to carry the OSPF domain ID by configuring the domain-id command in OSPF view. The domain ID is added to BGP VPN routes as an extended community attribute.
To configure the MCE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
N/A |
|
4. Configure an EBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
By default, no BGP peer is configured. |
|
5. Enter BGP-VPN IPv4 unicast address family view. |
address-family ipv4 [ unicast ] |
N/A |
|
6. Enable BGP to exchange IPv4 unicast routes with the peer. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange IPv4 unicast routes with any peer. |
|
7. Allow the local AS number to appear in the AS_PATH attribute of routes received from the peer, and set the maximum number of repetitions. |
peer { group-name | ip-address [ mask-length ] } allow-as-loop [ number ] |
By default, BGP discards incoming route updates that contain the local AS number. BGP detects routing loops by examining AS numbers. The routing information the MCE advertises to a site carries the local AS number. Therefore, the route updates that the MCE receives from the site also include the local AS number. This causes the MCE to be unable to receive the route updates. In this case, you must configure this command to allow routing loops. |
|
8. Redistribute remote site routes advertised by the PE into BGP. |
import-route protocol [ { process-id | all-processes } [ med med-value | route-policy route-policy-name ] * ] |
By default, no routes are redistributed into BGP. |
|
9. (Optional.) Configure filtering of advertised routes. |
filter-policy { acl-number | prefix-list prefix-list-name } export [ protocol process-id ] |
By default, BGP does not filter advertised routes. |
|
10. (Optional.) Configure filtering of received routes. |
filter-policy { acl-number | prefix-list prefix-list-name } import |
By default, BGP does not filter received routes. |
2. Configure a VPN site:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Configure the MCE as an EBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
N/A |
|
4. Enter BGP-VPN IPv4 unicast address family view. |
address-family ipv4 [ unicast ] |
N/A |
|
5. Enable BGP to exchange IPv4 unicast routes with the peer. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange IPv4 unicast routes with any peer. |
|
6. Redistribute the IGP routes of the VPN into BGP. |
import-route protocol [ { process-id | all-processes } [ med med-value | route-policy route-policy-name ] * ] |
By default, no routes are redistributed into BGP. A VPN site must advertise the VPN network addresses it can reach to the connected MCE. |
Configuring IBGP between MCE and VPN site
To run IBGP between an MCE and a VPN site, you must configure a BGP peer for each VPN instance on the MCE, and redistribute the IGP routes of each VPN instance on the VPN site.
1. Configure the MCE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
N/A |
|
4. Configure an IBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
N/A |
|
5. Enter BGP-VPN IPv4 unicast address family view. |
address-family ipv4 [ unicast ] |
N/A |
|
6. Enable BGP to exchange IPv4 unicast routes with the peer. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange IPv4 unicast routes with any peer. |
|
7. (Optional.) Configure the system to be the RR, and specify the peer as the client of the RR. |
peer { group-name | ip-address [ mask-length ] } reflect-client |
By default, no RR or RR client is configured. After you configure a VPN site as an IBGP peer, the MCE does not advertise the BGP routes learned from the VPN site to other IBGP peers, including VPNv4 peers. The MCE advertises routes learned from a VPN site only when you configure the VPN site as a client of the RR (the MCE). |
|
8. Redistribute remote site routes advertised by the PE into BGP. |
import-route protocol [ process-id | all-processes ] [ med med-value | route-policy route-policy-name ] * |
By default, no routes are redistributed into BGP. |
|
9. (Optional.) Configure filtering of advertised routes. |
filter-policy { acl-number | prefix-list prefix-list-name } export [ protocol process-id ] |
By default, BGP does not filter advertised routes. |
|
10. (Optional.) Configure filtering of received routes. |
filter-policy { acl-number | prefix-list prefix-list-name } import |
By default, BGP does not filter received routes. |
2. Configure a VPN site:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Configure the MCE as an IBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
N/A |
|
4. Enter BGP-VPN IPv4 unicast address family view. |
address-family ipv4 [ unicast ] |
N/A |
|
5. Enable BGP to exchange IPv4 unicast routes with the peer. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange IPv4 unicast routes with any peer. |
|
6. Redistribute the IGP routes of the VPN into BGP. |
import-route protocol [ { process-id | all-processes } [ med med-value | route-policy route-policy-name ] * ] |
By default, no routes are redistributed into BGP. A VPN site must advertise VPN network addresses to the connected MCE. |
Configuring routing between an MCE and a PE
MCE-PE routing configuration includes the following tasks:
· Binding the MCE-PE interfaces to VPN instances.
· Performing route configurations.
· Redistributing VPN routes into the routing protocol running between the MCE and the PE.
Perform the following configurations on the MCE. For more information about configuring the PE, see the documentation for the PE.
Configuring static routing between an MCE and a PE
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a static route for a VPN instance. |
ip route-static vpn-instance s-vpn-instance-name dest-address { mask-length | mask } { interface-type interface-number [ next-hop-address ] | next-hop-address [ public ] [ track track-entry-number ] | vpn-instance d-vpn-instance-name next-hop-address [ track track-entry-number ] } [ permanent ] [ preference preference-value ] [ tag tag-value ] [ description description-text ] |
By default, no static route is configured. |
|
3. (Optional.) Configure the default preference for static routes. |
ip route-static default-preference default-preference-value |
The default preference is 60. |
Configuring RIP between an MCE and a PE
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a RIP process for a VPN instance and enter RIP view. |
rip [ process-id ] vpn-instance vpn-instance-name |
N/A |
|
3. Enable RIP on the interface attached to the specified network. |
network network-address |
By default, RIP is disabled on an interface. |
|
4. Redistribute the VPN routes. |
import-route protocol [ process-id | all-processes | allow-ibgp ] [ cost cost | route-policy route-policy-name | tag tag ] * |
By default, no routes are redistributed into RIP. |
|
5. (Optional.) Configure the default cost for redistributed routes. |
default cost value |
The default cost is 0. |
Configuring OSPF between an MCE and a PE
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an OSPF process for a VPN instance and enter OSPF view. |
ospf [ process-id | router-id router-id | vpn-instance vpn-instance-name ] * |
N/A |
|
3. Disable routing loop detection. |
vpn-instance-capability simple |
By default, routing loop detection is enabled. You must disable routing loop detection for an OSPF VRF process on the MCE. Otherwise, the MCE does not receive OSPF routes from the PE. |
|
4. (Optional.) Configure the OSPF domain ID. |
domain-id domain-id [ secondary ] |
The default domain ID is 0. |
|
5. (Optional.) Configure the type codes of OSPF extended community attributes. |
ext-community-type { domain-id type-code1 | router-id type-code2 | route-type type-code3 } |
The defaults are as follows: · 0x0005 for Domain ID. · 0x0107 for Router ID. · 0x0306 for Route Type. |
|
6. (Optional.) Configure the external route tag for imported VPN routes. |
route-tag tag-value |
By default, no route tag is configured. In some networks, a VPN might be connected to multiple MCEs. When one MCE advertises the routes learned from BGP to the VPN, the other MCEs might learn the routes, resulting in routing loops. To avoid such routing loops, you can configure route tags for VPN instances on an MCE. As a best practice, configure the same route tag for the same VPN on the MCEs. |
|
7. Redistribute the VPN routes. |
import-route protocol [ process-id | all-processes | allow-ibgp ] [ cost cost | route-policy route-policy-name | tag tag | type type ] * |
By default, no routes are redistributed into OSPF. |
|
8. (Optional.) Configure OSPF to redistribute the default route. |
default-route-advertise summary cost cost |
By default, OSPF does not redistribute the default route. This command redistributes the default route in a Type-3 LSA. The MCE advertises the default route to the PE. |
|
9. (Optional.) Configure filtering of advertised routes. |
filter-policy { acl-number | prefix-list prefix-list-name } export [ protocol [ process-id ] ] |
By default, redistributed routes are not filtered. |
|
10. (Optional.) Configure the default parameters for redistributed routes (cost, route number, tag, and type). |
default { cost cost | tag tag | type type } * |
The default cost is 1, the default tag is 1, and default type of redistributed routes is Type-2. |
|
11. Create an OSPF area and enter OSPF area view. |
area area-id |
By default, no OSPF area is created. |
|
12. Enable OSPF on the interface attached to the specified network in the area. |
network ip-address wildcard-mask |
By default, an interface neither belongs to any area nor runs OSPF. |
Configuring IS-IS between an MCE and a PE
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an IS-IS process for a VPN instance and enter IS-IS view. |
isis [ process-id ] vpn-instance vpn-instance-name |
N/A |
|
3. Configure a network entity title. |
network-entity net |
By default, no NET is configured. |
|
4. Redistribute VPN routes. |
import-route protocol [ process-id | all-processes | allow-ibgp ] [ cost cost | cost-type { external | internal } | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] * |
By default, IS-IS does not redistribute routes from any other routing protocol. If you do not specify the route level in the command, the command redistributes routes to the level-2 routing table by default. |
|
5. (Optional.) Configure filtering of advertised routes. |
filter-policy { acl-number | prefix-list prefix-list-name | route-policy route-policy-name } export [ protocol [ process-id ] ] |
By default, IS-IS does not filter advertised routes. |
|
6. Return to system view. |
quit |
N/A |
|
7. Enter interface view. |
interface interface-type interface-number |
N/A |
|
8. Enable the IS-IS process on the interface. |
isis enable [ process-id ] |
By default, no IS-IS process is enabled. |
Configuring EBGP between an MCE and a PE
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
N/A |
|
4. Configure the PE as an EBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
N/A |
|
5. Enter BGP-VPN IPv4 unicast address family view. |
address-family ipv4 [ unicast ] |
N/A |
|
6. Enable BGP to exchange IPv4 unicast routes with the peer. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange IPv4 unicast routes with any peer. |
|
7. Redistribute the VPN routes of the VPN site. |
import-route protocol [ process-id | all-processes ] [ med med-value | route-policy route-policy-name ] * |
By default, no routes are redistributed into BGP. |
|
8. (Optional.) Configure filtering of advertised routes. |
filter-policy { acl-number | prefix-list prefix-list-name } export [ protocol process-id ] |
By default, BGP does not filter advertised routes. |
|
9. (Optional.) Configure filtering of received routes. |
filter-policy { acl-number | prefix-list prefix-list-name } import |
By default, BGP does not filter received routes. |
Configuring IBGP between an MCE and a PE
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter BGP view. |
bgp as-number |
N/A |
|
3. Enter BGP-VPN instance view. |
ip vpn-instance vpn-instance-name |
N/A |
|
4. Configure the PE as an IBGP peer. |
peer { group-name | ip-address [ mask-length ] } as-number as-number |
N/A |
|
5. Enter BGP-VPN IPv4 unicast address family view. |
address-family ipv4 [ unicast ] |
N/A |
|
6. Enable BGP to exchange IPv4 unicast routes with the peer. |
peer { group-name | ip-address [ mask-length ] } enable |
By default, BGP does not exchange IPv4 unicast routes with any peer. |
|
7. Redistribute the VPN routes of the VPN site. |
import-route protocol [ process-id | all-processes ] [ med med-value | route-policy route-policy-name ] * |
By default, no routes are redistributed into BGP. |
|
8. (Optional.) Configure filtering of advertised routes. |
filter-policy { acl-number | prefix-list prefix-list-name } export [ protocol process-id ] |
By default, BGP does not filter advertised routes. |
|
9. (Optional.) Configure filtering of received routes. |
filter-policy { acl-number | prefix-list prefix-list-name } import |
By default, BGP does not filter received routes. |
Displaying and maintaining MCE
Execute display commands in any view.
|
Task |
Command |
|
Display VPN instance information. |
display ip vpn-instance [ instance-name vpn-instance-name ] |
|
Display BGP peer group information for a VPN instance. |
display bgp group ipv4 [ unicast ] vpn-instance vpn-instance-name [ group-name group-name ] |
|
Display BGP peer information for a VPN instance (in standalone mode). |
display bgp peer ipv4 [ unicast ] vpn-instance vpn-instance-name [ ip-address mask-length | { ip-address | group-name group-name } log-info | [ [ ip-address ] verbose ] [ standby slot slot-number ] ] |
|
Display BGP peer information for a VPN instance (in IRF mode). |
display bgp peer ipv4 [ unicast ] vpn-instance vpn-instance-name [ ip-address mask-length | { ip-address | group-name group-name } log-info | [ [ ip-address ] verbose ] [ standby chassis chassis-number slot slot-number ] ] |
For other MCE displaying and maintaining commands, such as the commands for displaying VPN routing tables and maintaining VPN routing sessions, see Layer 3—IP Routing Command Reference.
For more information about the display bgp group ipv4 and display bgp peer ipv4 commands, see Layer 3—IP Routing Command Reference.
MCE configuration examples
Configuring the MCE that uses OSPF to advertise VPN routes to the PE
Network requirements
As shown in Figure 78, the MCE device is connected to VPN 1 through VLAN-interface 10 and is connected with VPN 2 through VLAN-interface 20. OSPF runs in VPN 2.
Configure the MCE device to separate routes from different VPNs and to advertise the VPN routes to PE 1 through OSPF.
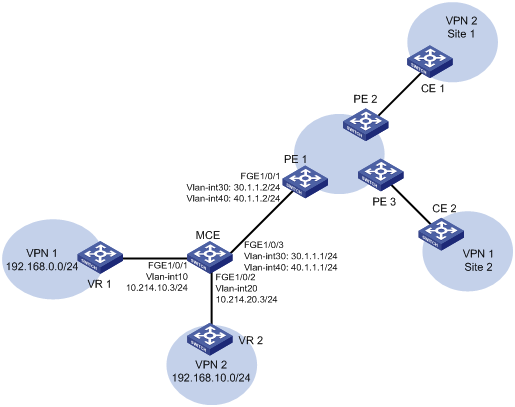
Configuration procedure
Assume that the system name of the MCE device is MCE, the system names of the edge devices of VPN 1 and VPN 2 are VR1 and VR2, respectively, and the system name of PE 1 is PE1.
1. Configure the VPN instances on the MCE and PE 1:
# On the MCE, configure VPN instances vpn1 and vpn2, and specify an RD and route targets for each VPN instance.
<MCE> system-view
[MCE] ip vpn-instance vpn1
[MCE-vpn-instance-vpn1] route-distinguisher 10:1
[MCE-vpn-instance-vpn1] vpn-target 10:1
[MCE-vpn-instance-vpn1] quit
[MCE] ip vpn-instance vpn2
[MCE-vpn-instance-vpn2] route-distinguisher 20:1
[MCE-vpn-instance-vpn2] vpn-target 20:1
[MCE-vpn-instance-vpn2] quit
# Create VLAN 10, add FortyGigE 1/0/1 to VLAN 10, and create VLAN-interface 10.
[MCE] vlan 10
[MCE-vlan10] port fortygige 1/0/1
[MCE-vlan10] quit
# Bind VLAN-interface 10 with VPN instance vpn1, and configure an IP address for VLAN-interface 10.
[MCE] interface vlan-interface 10
[MCE-Vlan-interface10] ip binding vpn-instance vpn1
[MCE-Vlan-interface10] ip address 10.214.10.3 24
[MCE-Vlan-interface10] quit
# Configure VLAN 20, add FortyGigE 1/0/2 to VLAN 20, bind VLAN-interface 20 with VPN instance vpn2, and specify an IP address for VLAN-interface 20.
[MCE] vlan 20
[MCE-vlan20] port fortygige 1/0/2
[MCE-vlan20] quit
[MCE] interface vlan-interface 20
[MCE-Vlan-interface20] ip binding vpn-instance vpn2
[MCE-Vlan-interface20] ip address 10.214.20.3 24
[MCE-Vlan-interface20] quit
# On PE 1, configure VPN instances vpn1 and vpn2, and specify an RD and route targets for each VPN instance.
<PE1> system-view
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 10:1
[PE1-vpn-instance-vpn1] vpn-target 10:1
[PE1-vpn-instance-vpn1] quit
[PE1] ip vpn-instance vpn2
[PE1-vpn-instance-vpn2] route-distinguisher 20:1
[PE1-vpn-instance-vpn2] vpn-target 20:1
[PE1-vpn-instance-vpn2] quit
2. Configure routing between the MCE and VPN sites:
The MCE is connected to VPN 1 directly, and no routing protocol is enabled in VPN 1. Therefore, you can configure static routes.
# On VR 1, assign IP address 10.214.10.2/24 to the interface connected to MCE and 192.168.0.1/24 to the interface connected to VPN 1. Add ports to VLANs correctly. (Details not shown.)
# On VR 1, configure a default route with the next hop being 10.214.10.3.
<VR1> system-view
[VR1] ip route-static 0.0.0.0 0.0.0.0 10.214.10.3
# On the MCE, configure a static route to 192.168.0.0/24, specify the next hop as 10.214.10.2, and bind the static route with VPN instance vpn1.
[MCE] ip route-static vpn-instance vpn1 192.168.0.0 24 10.214.10.2
# On the MCE, display the routing information maintained for VPN instance vpn1.
[MCE] display ip routing-table vpn-instance vpn1
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
10.214.10.0/24 Direct 0 0 10.214.10.3 Vlan10
10.214.10.0/32 Direct 0 0 10.214.10.3 Vlan10
10.214.10.3/32 Direct 0 0 127.0.0.1 InLoop0
10.214.10.255/32 Direct 0 0 10.214.10.3 Vlan10
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
192.168.0.0/24 Static 60 0 10.214.10.2 Vlan10
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
The output shows that the MCE has a static route for VPN instance vpn1.
# Run OSPF in VPN 2. Create OSPF process 20 and bind it with VPN instance vpn2 on the MCE, so that the MCE can learn the routes of VPN 2 and add them to the routing table of the VPN instance vpn2.
[MCE] ospf 2 vpn-instance vpn2
# Advertise subnet 10.214.20.0.
[MCE-ospf-2] area 0
[MCE-ospf-2-area-0.0.0.0] network 10.214.20.0 0.0.0.255
[MCE-ospf-2-area-0.0.0.0] quit
[MCE-ospf-2] quit
# On VR 2, assign IP address 10.214.20.2/24 to the interface connected to MCE and 192.168.10.1/24 to the interface connected to VPN 2. (Details not shown.)
# Configure OSPF process 2, and advertise subnets 192.168.10.0 and 10.214.20.0.
<VR2> system-view
[VR2] ospf 2
[VR2-ospf-2] area 0
[VR2-ospf-2-area-0.0.0.0] network 192.168.10.0 0.0.0.255
[VR2-ospf-2-area-0.0.0.0] network 10.214.20.0 0.0.0.255
[VR2-ospf-2-area-0.0.0.0] quit
[VR2-ospf-2] quit
# On the MCE, display the routing information maintained for VPN instance vpn2.
[MCE] display ip routing-table vpn-instance vpn2
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
10.214.20.0/24 Direct 0 0 10.214.20.3 Vlan20
10.214.20.0/32 Direct 0 0 10.214.20.3 Vlan20
10.214.20.3/32 Direct 0 0 127.0.0.1 InLoop0
10.214.20.255/32 Direct 0 0 10.214.20.3 Vlan20
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
192.168.10.0/24 OSPF 10 2 10.214.20.2 Vlan20
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
The output shows that the MCE has learned the private routes of VPN 2. The MCE maintains the routes of VPN 1 and those of VPN2 in two different routing tables. In this way, routes from different VPNs are separated.
3. Configure routing between the MCE and PE 1:
# The MCE uses FortyGigE 1/0/3 to connect to PE's port FortyGigE 1/0/1. Configure the two ports as trunk ports, and configure them to permit packets carrying VLAN tags 30 and 40 to pass.
[MCE] interface fortygige 1/0/3
[MCE-FortyGigE1/0/3] port link-type trunk
[MCE-FortyGigE1/0/3] port trunk permit vlan 30 40
[MCE-FortyGigE1/0/3] quit
# Configure FortyGigE 1/0/1 on the PE.
[PE1] interface fortygige 1/0/1
[PE1-FortyGigE1/0/1] port link-type trunk
[PE1-FortyGigE1/0/1] port trunk permit vlan 30 40
[PE1-FortyGigE1/0/1] quit
# On the MCE, create VLAN 30 and VLAN-interface 30, bind the VLAN interface with VPN instance vpn1, and configure an IP address for the VLAN interface.
[MCE] vlan 30
[MCE-vlan30] quit
[MCE] interface vlan-interface 30
[MCE-Vlan-interface30] ip binding vpn-instance vpn1
[MCE-Vlan-interface30] ip address 30.1.1.1 24
[MCE-Vlan-interface30] quit
# On the MCE, create VLAN 40 and VLAN-interface 40, bind the VLAN interface with VPN instance vpn2, and configure an IP address for the VLAN interface.
[MCE] vlan 40
[MCE-vlan40] quit
[MCE] interface vlan-interface 40
[MCE-Vlan-interface40] ip binding vpn-instance vpn2
[MCE-Vlan-interface40] ip address 40.1.1.1 24
[MCE-Vlan-interface40] quit
# On PE 1, create VLAN 30 and VLAN-interface 30, bind the VLAN interface with VPN instance vpn1, and configure an IP address for the VLAN interface.
[PE1] vlan 30
[PE1-vlan30] quit
[PE1] interface vlan-interface 30
[PE1-Vlan-interface30] ip binding vpn-instance vpn1
[PE1-Vlan-interface30] ip address 30.1.1.2 24
[PE1-Vlan-interface30] quit
# On PE 1, create VLAN 40 and VLAN-interface 40, bind the VLAN interface with VPN instance vpn2, and configure an IP address for the VLAN interface.
[PE1] vlan 40
[PE1-vlan40] quit
[PE1] interface vlan-interface 40
[PE1-Vlan-interface40] ip binding vpn-instance vpn2
[PE1-Vlan-interface40] ip address 40.1.1.2 24
[PE1-Vlan-interface40] quit
# Configure the IP address of the interface Loopback 0 as 101.101.10.1 for the MCE and as 100.100.10.1 for PE 1. Specify the loopback interface address as the router ID for the MCE and PE 1. (Details not shown.)
# Enable OSPF process 10 on the MCE, bind the process to VPN instance vpn1, disable OSPF routing loop detection, and set the domain ID to 10.
[MCE] ospf 10 router-id 101.101.10.1 vpn-instance vpn1
[MCE-ospf-10] vpn-instance-capability simple
[MCE-ospf-10] domain-id 10
# On the MCE, advertise subnet 30.1.1.0 in area 0, and redistribute the static route of VPN 1.
[MCE-ospf-10] area 0
[MCE-ospf-10-area-0.0.0.0] network 30.1.1.0 0.0.0.255
[MCE-ospf-10-area-0.0.0.0] quit
[MCE-ospf-10] import-route static
# On PE 1, enable OSPF process 10, bind the process with VPN instance vpn1, set the domain ID to 10, and advertise subnet 30.1.1.0 in area 0.
[PE1] ospf 10 router-id 100.100.10.1 vpn-instance vpn1
[PE1-ospf-10] domain-id 10
[PE1-ospf-10] area 0
[PE1-ospf-10-area-0.0.0.0] network 30.1.1.0 0.0.0.255
[PE1-ospf-10-area-0.0.0.0] quit
[PE1-ospf-10] quit
# Use similar procedures to configure OSPF process 20 between MCE and PE 1 and redistribute VPN 2's routing information. (Details not shown.)
Verifying the configuration
# On PE 1, display the routing information for VPN 1. The output shows that the static route of VPN 1 has been redistributed to the OSPF routing table of PE 1.
[PE1] display ip routing-table vpn-instance vpn1
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
30.1.1.0/24 Direct 0 0 30.1.1.2 Vlan30
30.1.1.0/32 Direct 0 0 30.1.1.2 Vlan30
30.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
30.1.1.255/32 Direct 0 0 30.1.1.2 Vlan30
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
192.168.0.0/24 OSPF 150 1 30.1.1.1 Vlan30
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# On PE 1, display the routing information for VPN 2. The output shows that the routes of OSPF process 2 in VPN 2 have been redistributed to the OSPF routing table of PE 1.
[PE1] display ip routing-table vpn-instance vpn2
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
40.1.1.0/24 Direct 0 0 40.1.1.2 Vlan40
40.1.1.0/32 Direct 0 0 40.1.1.2 Vlan40
40.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
40.1.1.255/32 Direct 0 0 40.1.1.2 Vlan40
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
192.168.10.0/24 OSPF 150 1 40.1.1.1 Vlan40
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
Now, the routing information for the two VPNs has been redistributed into the routing tables on PE 1.
Configuring the MCE that uses EBGP to advertise VPN routes to the PE
Network requirements
As shown in Figure 79, configure the MCE to advertise the routes of VPNs 1 and 2 to PE 1, so that the sites of each VPN can communicate with each other over the MPLS backbone.
Run OSPF in both VPN 1 and VPN 2. Run EBGP between the MCE and PE 1.

Configuration procedure
1. Create VPN instances on the MCE and PE 1, and bind the VPN instances with VLAN interfaces. For the configuration procedure, see "Configure the VPN instances on the MCE and PE 1:."
2. Configure routing between the MCE and VPN sites:
# Enable an OSPF process on the devices in the two VPNs, and advertise the subnets. (Details not shown.)
# Configure OSPF on the MCE, and bind OSPF process 10 with VPN instance vpn1 to learn the routes of VPN 1.
<MCE> system-view
[MCE] ospf 10 router-id 10.10.10.1 vpn-instance vpn1
[MCE-ospf-10] area 0
[MCE-ospf-10-area-0.0.0.0] network 10.214.10.0 0.0.0.255
[MCE-ospf-10-area-0.0.0.0] quit
[MCE-ospf-10] quit
# Display the routing table of VPN 1 on the MCE.
[MCE] display ip routing-table vpn-instance vpn1
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
10.214.10.0/24 Direct 0 0 10.214.10.3 Vlan10
10.214.10.0/32 Direct 0 0 10.214.10.3 Vlan10
10.214.10.3/32 Direct 0 0 127.0.0.1 InLoop0
10.214.10.255/32 Direct 0 0 10.214.10.3 Vlan10
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
192.168.0.0/24 OSPF 10 2 10.214.10.2 Vlan10
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
The output shows that the MCE has learned the private route of VPN 1 through OSPF process 10.
# On the MCE, bind OSPF process 20 with VPN instance vpn2 to learn the routes of VPN 2. The configuration procedure is similar to that for OSPF process 10.
The output shows that the MCE has learned the private route of VPN 2 through OSPF.
[MCE] display ip routing-table vpn-instance vpn2
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
10.214.20.0/24 Direct 0 0 10.214.20.3 Vlan20
10.214.20.0/32 Direct 0 0 10.214.20.3 Vlan20
10.214.20.3/32 Direct 0 0 127.0.0.1 InLoop0
10.214.20.255/32 Direct 0 0 10.214.20.3 Vlan20
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
192.168.10.0/24 OSPF 10 2 10.214.20.2 Vlan20
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
3. Configure routing between the MCE and PE 1:
# Configure the ports between the MCE and PE 1 as trunk ports. The configuration procedure is similar to that described in "Configure routing between the MCE and PE 1:." (Details not shown.)
# Enable BGP in AS 100 on the MCE, enter the BGP-VPN instance view of VPN instance vpn1, and specify the EBGP peer PE 1 in AS 200.
[MCE] bgp 100
[MCE-bgp] ip vpn-instance vpn1
[MCE-bgp-vpn1] peer 30.1.1.2 as-number 200
# Activate the EBGP VPNv4 peer PE 1, and redistribute routing information from OSPF process 10 to BGP.
[MCE-bgp-vpn1] address-family ipv4
[MCE-bgp-ipv4-vpn1] peer 30.1.1.2 enable
[MCE-bgp-ipv4-vpn1] import-route ospf 10
# On PE 1, enable BGP in AS 200, and specify the MCE as its EBGP peer.
[PE1] bgp 200
[PE1-bgp] ip vpn-instance vpn1
[PE1-bgp-vpn1] peer 30.1.1.1 as-number 100
[PE1-bgp-vpn1] address-family ipv4
[PE1-bgp-ipv4-vpn1] peer 30.1.1.1 enable
[PE1-bgp-ipv4-vpn1] quit
[PE1-bgp-vpn1] quit
[PE1-bgp] quit
# Use similar procedures to configure VPN 2 settings on MCE and PE 1. (Details not shown.)
Verifying the configuration
# Display the routing information for VPN 1 on PE 1.
[PE1] display ip routing-table vpn-instance vpn1
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
30.1.1.0/24 Direct 0 0 30.1.1.2 Vlan30
30.1.1.0/32 Direct 0 0 30.1.1.2 Vlan30
30.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
30.1.1.255/32 Direct 0 0 30.1.1.2 Vlan30
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
192.168.0.0/24 BGP 255 3 30.1.1.1 Vlan30
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Display the routing information for VPN 2 on PE 1.
[PE1] display ip routing-table vpn-instance vpn2
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
40.1.1.0/24 Direct 0 0 40.1.1.2 Vlan40
40.1.1.0/32 Direct 0 0 40.1.1.2 Vlan40
40.1.1.2/32 Direct 0 0 127.0.0.1 InLoop0
40.1.1.255/32 Direct 0 0 40.1.1.2 Vlan40
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
192.168.10.0/24 BGP 255 3 40.1.1.1 Vlan40
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
Now, the MCE has redistributed the OSPF routes of the two VPN instances into the EBGP routing tables of PE 1.
A
LDP label acceptance policy, 27
MPLS TE traffic forwarding automatic route advertisement (forwarding adjacency), 52
MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement/forwarding adjacency), 72
LDP advertisement messages, 15
LDP label advertisement control, 41
LDP label advertisement modes, 17
LDP label advertisement policy, 26
MCE EBGP VPN route advertisement, 286
MCE OSPF VPN route advertisement, 280
MPLS egress label type advertisement, 6
MPLS L3VPN basics, 174
MPLS L3VPN HoVPN configuration, 189
MPLS L3VPN route advertisement, 156
MPLS TE attribute advertisement, 51
MPLS TE CRLSP dynamic establishment, 50
MPLS TE link attribute (IGP TE extension), 63
MPLS TE link attribute (IS-IS TE), 64
MPLS TE link attribute (OSPF TE), 63
MPLS TE traffic forwarding automatic route advertisement (forwarding adjacency), 52
MPLS TE traffic forwarding automatic route advertisement (IGP shortcut), 52
MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement), 71
MPLS TE tunnel constraints, 64
MPLS TE CSPF path calculation, 51
MPLS L3VPN, 154, 265
MPLS network, 2
MPLS L3VPN OSPF area PE-CE configuration, 168
MPLS L3VPN BGP AS number substitution, 171, 192
MPLS L3VPN BGP AS number substitution configuration, 254
MPLS L3VPN inter-AS option A, 160
MPLS L3VPN inter-AS option A configuration, 209
MPLS L3VPN inter-AS option B, 161
MPLS L3VPN inter-AS option B configuration, 214
MPLS L3VPN inter-AS option C, 162
MPLS L3VPN inter-AS option C configuration, 219
MPLS L3VPN inter-AS VPN configuration, 183
MPLS L3VPN inter-AS VPN option A, 160, 184
MPLS L3VPN inter-AS VPN option B, 160, 184
MPLS L3VPN inter-AS VPN option C, 160, 185
MPLS L3VPN inter-AS VPN option C ASBR, 186
MPLS L3VPN inter-AS VPN option C ASBR, 186
MCE VPN instance+interface, 269
MPLS L3VPN VPN instance+interface, 175
MCE VPN instance route related attributes, 269
MPLS L3VPN BGP export target attribute, 156, 267
MPLS L3VPN BGP import target attribute, 156, 267
MPLS L3VPN VPN instance route related attributes, 176
MPLS TE attribute advertisement, 51
MPLS TE link attribute, 62
MPLS TE link attribute advertisement (IGP TE extension), 63
MPLS TE link attribute advertisement (IS-IS TE), 64
MPLS TE link attribute advertisement (OSPF TE), 63
MPLS TE tunnel constraints, 64
LDP MD5 configuration, 25
RSVP, 135
RSVP authentication configuration, 138
MPLS E FRR bypass tunnel on PLR (automatic setup), 77
MPLS TE auto FRR configuration, 113
MPLS TE automatic bandwidth adjustment, 54, 69
MPLS TE traffic forwarding automatic route advertisement (forwarding adjacency), 52
MPLS TE traffic forwarding automatic route advertisement (IGP shortcut), 52
MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement), 71
MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement/forwarding adjacency), 72
MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement/IGP shortcut), 71
MPLS L3VPN routing loop avoidance, 170
B
MPLS L3VPN FRR IPv4 route backup (VPNv4 route), 173
MPLS L3VPN FRR VPNv4 route backup (IPv4 route), 173
MPLS L3VPN FRR VPNv4 route backup (VPNv4 route), 172
MPLS TE CRLSP backup, 73, 103
MPLS TE CRLSP hot standby backup, 54
MPLS TE CRLSP ordinary backup, 54
MPLS TE automatic bandwidth adjustment, 69, 69
MPLS TE CRLSP dynamic establishment, 50
MPLS TE CRLSP static implementation, 50
MPLS TE DS-TE bandwidth constraint model, 56
MPLS TE link attribute, 62
MPLS TE tunnel automatic bandwidth adjustment, 54
MPLS TE tunnel constraints, 64
MPLS TE tunnel reoptimization, 54
static CRLSP configuration, 127, 128
MPLS L3VPN FRR, 172
RSVP enable, 140
MCE configuration, 265, 268, 280
MCE EBGP VPN route advertisement, 286
MPLS L3VPN basic configuration, 197
MPLS L3VPN BGP AS number substitution, 171, 192
MPLS L3VPN BGP AS number substitution configuration, 254
MPLS L3VPN BGP route flapping logging, 194
MPLS L3VPN BGP VPNv4 route control, 182
MPLS L3VPN BGP-OSPF interaction, 169
MPLS L3VPN carrier's carrier, 226
MPLS L3VPN configuration, 154, 174, 197
MPLS L3VPN FRR, 172
MPLS L3VPN FRR configuration (IPv4 route/VPNv4 route backup), 260
MPLS L3VPN FRR configuration (VPNv4 route/IPv4 route backup), 262
MPLS L3VPN FRR configuration (VPNv4 route/route backup), 258
MPLS L3VPN HoVPN configuration, 189, 243
MPLS L3VPN inter-AS option A configuration, 209
MPLS L3VPN inter-AS option B configuration, 214
MPLS L3VPN inter-AS option C configuration, 219
MPLS L3VPN MP-BGP, 156
MPLS L3VPN nested VPN configuration, 188, 234
MPLS L3VPN OSPF sham link, 170
MPLS L3VPN OSPF sham link configuration, 250
MPLS L3VPN route target attributes, 156, 267
MPLS TE tunnel configuration, 72, 97
MPLS TE tunnel implementation (associated mode), 58
MPLS TE tunnel implementation (co-routed mode), 58
MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement), 71
MPLS TE tunnel/tunnel bundle traffic direction (static routing), 71
MPLS TE FRR bypass tunnel, 55
C
MPLS TE CSPF path calculation, 51
MPLS L3VPN, 164, 226
MPLS L3VPN Level 1 carrier, 164
MPLS L3VPN Level 2 carrier, 164
MPLS L3VPN architecture, 154, 265
MPLS L3VPN HoVPN configuration, 189
MPLS L3VPN Layer 2 label packet forwarding, 157
MPLS L3VPN nested VPN, 166
MPLS L3VPN nested VPN configuration, 188
MPLS L3VPN OSPF area PE-CE configuration, 168
MPLS L3VPN OSPF sham link, 190
MPLS L3VPN OSPF sham link creation, 191
MPLS L3VPN PE-CE EBGP, 178
MPLS L3VPN PE-CE IBGP, 180
MPLS L3VPN PE-CE IS-IS, 178
MPLS L3VPN PE-CE OSPF, 177
MPLS L3VPN PE-CE RIP, 177
MPLS L3VPN PE-CE routing, 176
MPLS L3VPN PE-CE static routing, 177
MPLS FEC, 1
LDP feature and software version, 22
MPLS basics feature and software version, 5
MPLS L3VPN feature and software version, 174
MPLS TE feature and software version, 58
RSVP feature and software version, 136
static CRLSP feature and software version, 127
static LSP feature and software version, 11
tunnel policy feature and software version, 149
exclusive tunnel, 151
LDP, 15, 22, 33
LDP backoff, 25
LDP FRR, 32, 46
LDP GR, 29
LDP hello parameter, 24
LDP IS-IS synchronization, 31
LDP label acceptance control, 37
LDP label acceptance policy, 27
LDP label advertisement control, 41
LDP label advertisement policy, 26
LDP label distribution control mode, 26
LDP loop detection, 28
LDP LSP, 33
LDP LSP generation policy, 25
LDP MD5 authentication, 25
LDP NSR, 29
LDP-IGP synchronization, 30
LDP-OSPF synchronization, 30
MCE, 268, 280
MCE configuration, 265
MCE EBGP VPN route advertisement, 286
MCE OSPF VPN route advertisement, 280
MCE routing, 270
MCE VPN instance, 269
MCE VPN instance route related attribute, 269
MCE-PE EBGP, 279
MCE-PE IBGP, 279
MCE-PE IS-IS, 278
MCE-PE OSPF, 277
MCE-PE RIP, 277
MCE-PE routing, 276
MCE-PE static routing, 276
MCE-VPN site EBGP, 273
MCE-VPN site IBGP, 275
MCE-VPN site IS-IS, 273
MCE-VPN site OSPF, 272
MCE-VPN site RIP, 271
MCE-VPN site routing, 271
MCE-VPN site static routing, 271
MPLS basics, 1, 5
MPLS L3VPN, 154, 174, 197
MPLS L3VPN basics, 174, 197
MPLS L3VPN BGP AS number substitution, 192, 254
MPLS L3VPN BGP VPNv4 route control, 182
MPLS L3VPN carrier's carrier, 226
MPLS L3VPN FRR, 192
MPLS L3VPN FRR (IPv4 route/VPNv4 route backup), 260
MPLS L3VPN FRR (VPNv4 route/IPv4 route backup), 262
MPLS L3VPN FRR (VPNv4 route/route backup), 258
MPLS L3VPN HoVPN, 189, 243
MPLS L3VPN hub-spoke network, 202
MPLS L3VPN inter-AS option A, 209
MPLS L3VPN inter-AS option B, 214
MPLS L3VPN inter-AS option C, 219
MPLS L3VPN inter-AS VPN, 183
MPLS L3VPN inter-AS VPN option A, 184
MPLS L3VPN inter-AS VPN option B, 184
MPLS L3VPN inter-AS VPN option C, 185
MPLS L3VPN inter-AS VPN option C ASBR, 186
MPLS L3VPN inter-AS VPN option C PE, 185
MPLS L3VPN loopback interface, 190
MPLS L3VPN nested VPN, 188, 234
MPLS L3VPN OSPF sham link, 190, 250
MPLS L3VPN PE-CE EBGP, 178
MPLS L3VPN PE-CE IBGP, 180
MPLS L3VPN PE-CE IS-IS, 178
MPLS L3VPN PE-CE OSPF, 177
MPLS L3VPN PE-CE RIP, 177
MPLS L3VPN PE-CE routing, 176
MPLS L3VPN PE-CE static routing, 177
MPLS L3VPN PE-PE routing, 181
MPLS L3VPN VPN instance, 175
MPLS L3VPN VPN instance route related attribute, 176
MPLS TE, 50, 58, 79
MPLS TE auto FRR, 113
MPLS TE automatic bandwidth adjustment, 69
MPLS TE bidirectional tunnel, 72, 97
MPLS TE CRLSP backup, 73, 103
MPLS TE CRLSP path selection metric type, 66
MPLS TE CRLSP route pinning, 67
MPLS TE CRLSP tunnel reoptimization, 67
MPLS TE DS-TE, 60
MPLS TE FRR, 73
MPLS TE FRR bypass tunnel on PLR, 74
MPLS TE FRR manual bypass tunnel, 107
MPLS TE FRR node fault detection, 78
MPLS TE FRR optimal bypass tunnel selection interval, 78
MPLS TE IETF DS-TE, 119
MPLS TE link attribute, 62
MPLS TE link attribute advertisement (IS-IS TE), 64
MPLS TE link attribute advertisement (OSPF TE), 63
MPLS TE RSVP-TE RSVP resource reservation style, 70
MPLS TE traffic forwarding, 70
MPLS TE tunnel (dynamic CRLSP), 62
MPLS TE tunnel (static CRLSP), 61
MPLS TE tunnel affinity attribute, 64
MPLS TE tunnel constraints, 64
MPLS TE tunnel constraints (bandwidth), 64
MPLS TE tunnel interface, 60
MPLS TE tunnel loose explicit path, 65
MPLS TE tunnel strict explicit path, 65
MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement), 71
MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement/forwarding adjacency), 72
MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement/IGP shortcut), 71
MPLS TE tunnel/tunnel bundle traffic direction (static routing), 71
MPLS TTL propagation, 7
preferred tunnel, 151
preferred tunnel+selection order, 152
RSVP, 133, 136, 141
RSVP authentication (interface view), 138
RSVP authentication (RSVP neighbor view), 138
RSVP authentication (RSVP view), 138
RSVP GR, 140, 146
RSVP hello extension, 137
RSVP refresh, 136
RSVP reliable message delivery, 137
RSVP Srefresh, 137
static CRLSP, 127, 128
static LSP, 11, 12
tunnel policy, 149, 149, 151
tunnel selection order, 152
Routed Label Switched Path. See CRLSP
Shortest Path First. Use CSPF
Constraint-based Routed Label Switched Paths. Use CRLSP
MPLS, 2
LDP label distribution control mode, 26
MPLS TE CRLSP path selection, 66
MPLS TE tunnel setup, 68
MCE VPN instance, 269
MPLS L3VPN OSPF sham link, 191
MPLS L3VPN VPN instance, 175
MPLS TE auto FRR configuration, 113
MPLS TE bidirectional tunnel, 58, 72, 97
MPLS TE configuration, 50, 79
MPLS TE CRLSP backup, 54, 103
MPLS TE CRLSP path selection control, 66
MPLS TE CRLSP path selection metric type, 66
MPLS TE CRLSP route pinning, 67
MPLS TE CRLSP tunnel reoptimization, 67
MPLS TE dynamic implementation, 50
MPLS TE FRR, 55, 55, 73
MPLS TE FRR bypass tunnel on PLR, 74
MPLS TE FRR link protection, 55, 55
MPLS TE FRR manual bypass tunnel, 107
MPLS TE FRR node fault detection, 78
MPLS TE FRR node protection, 55
MPLS TE FRR optimal bypass tunnel selection interval, 78
MPLS TE IETF DS-TE configuration, 119
MPLS TE inter-AS tunnel establishment (RSVP-TE), 90
MPLS TE make-before-break, 53
MPLS TE route pinning, 54
MPLS TE static implementation, 50
MPLS TE tunnel automatic bandwidth adjustment, 54
MPLS TE tunnel configuration (dynamic CRLSP), 62
MPLS TE tunnel configuration (static CRLSP), 61
MPLS TE tunnel establishment (RSVP-TE), 84
MPLS TE tunnel establishment (static CRLSP), 79
MPLS TE tunnel reoptimization, 54
RSVP authentication, 135, 138
RSVP BFD enable, 140
RSVP configuration, 133, 136, 141
RSVP GR, 135
RSVP GR configuration, 140, 146
RSVP hello extension, 137
RSVP refresh, 136
RSVP refresh mechanism, 134
RSVP reliable message delivery, 137
RSVP Srefresh configuration, 137
RSVP-TE message types, 133
RSVP-TE object types, 133
RSVP-TE tunnel establishment, 141
static CRLSP configuration, 127, 128
static CRLSP display, 128
static feature and software version compatibility, 127
MPLS TE path calculation, 51
customer edge device. See CE
D
LDP loop detection, 28
MPLS TE FRR node fault detection, 78
MPLS TE loop detection, 69
customer edge device. See CE
LDP configuration, 33
MCE configuration, 265, 268, 280
MPLS L3VPN architecture, 154, 265
MPLS L3VPN basics, 174
MPLS L3VPN configuration, 154, 174, 197
MPLS L3VPN PE-CE EBGP, 178
MPLS L3VPN PE-CE IBGP, 180
MPLS L3VPN PE-CE IS-IS, 178
MPLS L3VPN PE-CE OSPF, 177
MPLS L3VPN PE-CE RIP, 177
MPLS L3VPN PE-CE routing, 176
MPLS L3VPN PE-CE static routing, 177
MPLS L3VPN PE-PE routing, 181
MPLS TE configuration, 79
MPLS TE tunnel interface, 60
provider device. See P device
provider edge device. See PE
RSVP configuration, 141
static CRLSP configuration, 127, 128
static LSP configuration, 12
DiffServ-aware TE. See DS-TE
LDP discovery message type, 15
LDP session parameters (Basic Discovery), 24
LDP session parameters (Extended Discovery), 24
LDP, 32
MCE, 280
MPLS, 9
MPLS L3VPN, 195
MPLS TE, 79
RSVP, 141
static CRLSP, 128
static LSP, 12
tunnel information, 151
LDP label distribution control mode, 26
RSVP packet DSCP value, 140
basic concepts, 56
how it works, 56
MPLS TE DS-TE, 56
MPLS TE DS-TE configuration, 60
MPLS TE IETF DS-TE configuration, 119
MPLS LSP establishment, 3
MPLS TE establishment, 50
MPLS TE tunnel configuration (dynamic CRLSP), 62
E
MCE-PE EBGP, 279
MCE-VPN site EBGP, 273
MPLS L3VPN hub-spoke network configuration, 202
MPLS L3VPN inter-AS VPN option B, 160, 161
MPLS L3VPN inter-AS VPN option C, 160, 162
MPLS L3VPN PE-CE EBGP, 178
MPLS egress label type advertisement, 6
MPLS egress LSR, 2
MPLS L3VPN egress PE VPN label processing mode, 191
LDP globally, 23
LDP on interface, 23
LDP SNMP notification, 32
MPLS, 5
MPLS L3VPN BGP route flapping logging, 194
MPLS L3VPN SNMP notification, 194
MPLS SNMP notifications, 9
MPLS TE, 59
MPLS TE FRR, 74
MPLS TE label recording, 69
MPLS TE loop detection, 69
MPLS TE route recording, 69
MPLS TTL-expired message send, 9
RSVP, 136
RSVP BFD, 140
MPLS LSP, 3
MPLS TE inter-AS tunnel (RSVP-TE), 90
MPLS TE tunnel (RSVP-TE), 84
MPLS TE tunnel (static CRLSP), 79
MPLS TE tunnel with RSVP-TE, 66
RSVP TE tunnel, 141
EXPLICIT_ROUTE object (RSVP-TE), 133
MCE VPN instance route related attributes, 269
MPLS L3VPN BGP export target attribute, 156, 267
MPLS L3VPN VPN instance route related attributes, 176
Extended Resource Reservation Protocol. See
MPLS L3VPN OSPF VPN extension, 168
RSVP hello extension, 137
MPLS L3VPN networking scheme, 159
F
LDP software version compatibility, 22
MPLS basics software version compatibility, 5
MPLS L3VPN software version compatibility, 174
MPLS TE software version compatibility, 58
RSVP software version compatibility, 136
static CRLSP software version compatibility, 127
static LSP software version compatibility, 11
tunnel policy software version compatibility, 149
LDP classification, 15
LDP configuration, 15, 22, 33
LDP label acceptance control, 37
LDP label advertisement control, 41
LDP label mapping, 15
LDP LSP configuration, 33
MPLS, 1
MPLS control plane, 2
MPLS label format, 1
MPLS L3VPN BGP route flapping logging, 194
MPLS FEC label, 1
exclusive tunnel configuration, 151
LDP GR, 18
LDP NSR, 20
MPLS FEC, 1
MPLS FEC label format, 1
MPLS forwarding plane, 2
MPLS L3VPN packet forwarding, 157
MPLS LFIB, 2
MPLS LSP, 2
MPLS LSP establishment, 3
MPLS LSR, 2
MPLS process, 4
MPLS TE bidirectional tunnel, 58
MPLS TE DS-TE, 56
MPLS TE make-before-break, 53
MPLS TE tunnel automatic bandwidth adjustment, 54
MPLS TE tunnel reoptimization, 54
MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement/forwarding adjacency), 72
preferred tunnel configuration, 151
preferred tunnel+selection order configuration, 152
tunnel policy configuration, 149, 151
tunnel selection order configuration, 152
LDP FRR, 21
LDP FRR configuration, 32, 46
MPLS L3VPN, 172
MPLS L3VPN FRR configuration, 192
MPLS L3VPN FRR configuration (IPv4 route/VPNv4 route backup), 260
MPLS L3VPN FRR configuration (VPNv4 route/IPv4 route backup), 262
MPLS L3VPN FRR configuration (VPNv4 route/route backup), 258
MPLS L3VPN FRR IPv4 route backup (VPNv4 route), 173
MPLS L3VPN FRR VPNv4 route backup (IPv4 route), 173
MPLS L3VPN FRR VPNv4 route backup (VPNv4 route), 172
MPLS TE, 55
MPLS TE auto FRR configuration, 113
MPLS TE FRR bypass CRLSP, 55
MPLS TE FRR bypass tunnel on PLR configuration restrictions, 76
MPLS TE FRR configuration, 73
MPLS TE FRR configuration on PLR, 74
MPLS TE FRR CRLSP link protection, 55, 55
MPLS TE FRR CRLSP node protection, 55
MPLS TE FRR enable, 74
MPLS TE FRR manual bypass tunnel, 107
MPLS TE FRR merge point (MP), 55
MPLS TE FRR node fault detection, 78
MPLS TE FRR optimal bypass tunnel selection interval, 78
MPLS TE FRR point of local repair (PLR), 55
MPLS TE FRR primary CRLSP, 55
G
LDP LSP generation policy, 25
LDP GR, 18
LDP GR configuration, 29
LDP GR helper, 18, 29
LDP GR restarter, 18, 29
RSVP configuration, 146
RSVP GR, 135
RSVP GR configuration, 140
RSVP GR helper, 135
RSVP GR restarter, 135
exclusive tunnel configuration, 151
preferred tunnel configuration, 151
preferred tunnel+selection order configuration, 152
tunnel policy configuration, 149, 151
tunnel selection order configuration, 152
H
RSVP GR, 135
RSVP GR configuration, 140
RSVP hello extension, 137
RSVP-TE hello message, 133
hop count (LDP loop detection), 28
hot standby CRLSP backup (MPLS TE), 54
configuration, 189
MPLS L3VPN configuration, 243
network model, 167
MPLS L3VPN networking configuration, 202
MPLS L3VPN networking scheme, 158
I
MCE-PE IBGP configuration, 279
MCE-VPN site IBGP, 275
MPLS L3VPN PE-CE IBGP, 180
MPLS TTL-expired message send, 9
LDP identifier, 15
MPLS TE DiffServ-aware TE mode, 56
MPLS TE IETF DS-TE configuration, 119
LDP-IGP synchronization, 20, 30
MPLS TE attribute advertisement, 51
MPLS TE link attribute advertisement (IGP TE extension), 63
MPLS TE link attribute advertisement (IS-IS TE), 64
MPLS TE link attribute advertisement (OSPF TE), 63
MPLS TE traffic forwarding automatic route advertisement (IGP shortcut), 52
MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement/IGP shortcut), 71
MCE VPN instance route related attributes, 269
MPLS L3VPN BGP import target attribute, 156, 267
MPLS L3VPN VPN instance route related attributes, 176
MPLS ingress LSR, 2
MCE VPN instance, 269
MCE VPN instance+interface association, 269
MCEVPN instance creation, 269
MPLS L3VPN VPN instance, 155, 175, 266
MPLS L3VPN VPN instance creation, 175
MPLS L3VPN VPN instance+interface association, 175
MPLS L3VPN BGP-OSPF interaction, 169
MPLS TE inter-AS tunnel establishment (RSVP-TE), 90
MPLS L3VPN configuration, 183
MPLS L3VPN option A, 160, 160, 184
MPLS L3VPN option A configuration, 209
MPLS L3VPN option B, 160, 161, 184
MPLS L3VPN option B configuration, 214
MPLS L3VPN option C, 160, 162, 185
MPLS L3VPN option C configuration, 219
MPLS TE FRR optimal bypass tunnel selection interval, 78
MPLS L3VPN loopback interface, 190
LDP backoff, 25
LDP configuration, 15, 22, 33
LDP FRR configuration, 32
LDP GR, 18
LDP GR configuration, 29
LDP IS-IS synchronization, 31
LDP label acceptance control, 37
LDP label acceptance policy, 27
LDP label advertisement control, 41
LDP label advertisement policy, 26
LDP label distribution control mode, 26
LDP loop detection, 28
LDP LSP configuration, 33
LDP LSP generation policy, 25
LDP MD5 authentication, 25
LDP NSR, 20
LDP NSR configuration, 29
LDP operation, 16
LDP session parameters, 24
LDP session reset, 32
LDP SNMP notification, 32
LDP-IGP synchronization, 20, 30
LDP-OSPF synchronization, 30
MPLS basics configuration, 1, 5
static LSP configuration, 11, 12
MCE-PE EBGP configuration, 279
MCE-PE IBGP configuration, 279
MPLS L3VPN FRR IPv4 route backup (VPNv4 route), 173
MPLS L3VPN FRR VPNv4 route backup (IPv4 route), 173
MPLS L3VPN inter-AS VPN option B, 160, 161
MPLS L3VPN inter-AS VPN option C, 160, 162
MPLS L3VPN VPN-IPv4 address, 155, 266
LDP IS-IS synchronization, 31
MCE-PE IS-IS, 278
MCE-VPN site IS-IS, 273
MPLS L3VPN PE-CE IS-IS configuration, 178
MPLS TE attribute advertisement, 51
MPLS TE link attribute advertisement (IS-IS TE), 64
MPLS L3VPN inter-AS VPN, 160
MPLS L3VPN inter-AS VPN option A, 160
MPLS L3VPN nested VPN, 166
K
LDP session parameter, 24
L
Label Forwarding Information Base. Use
LDP configuration, 15, 22
LDP distribution control, 17
LDP FEC label mapping, 15
LDP label acceptance control, 37
LDP label advertisement control, 41
LDP label advertisement modes, 17
LDP label advertisement policy, 26
LDP label distribution control mode, 26
LDP label spaces, 15
LDP retention mode, 18
MPLS egress label type advertisement, 6
MPLS FEC label format, 1
MPLS forwarding process, 4
MPLS L3VPN Layer 1 label packet forwarding, 157
MPLS L3VPN Layer 2 label packet forwarding, 157
MPLS L3VPN POP forwarding mode, 191
MPLS L3VPN POPGO forwarding mode, 191
MPLS LFIB, 2, 2
MPLS LSP, 2
MPLS LSR, 2
MPLS MTU set, 6
MPLS TE CRLSP dynamic establishment, 50
MPLS TE CRLSP RSVP-TE setup, 52
MPLS TE CRLSP static implementation, 50
MPLS TE label recording, 69
RSVP configuration, 133, 136, 141
RSVP GR configuration, 146
RSVP-TE LABEL object, 133
RSVP-TE LABEL_REQUEST object, 133
RSVP-TE tunnel establishment, 141
static CRLSP configuration, 127, 128
static LSP configuration, 11, 12
LDP label acceptance policy, 27
backoff configuration, 25
configuration, 15, 22, 33
display, 32
enable, 23
feature and software version compatibility, 22
FRR, 21
FRR configuration, 32, 46
GR, 18
GR configuration, 29
GR helper, 18
GR restarter, 18
hello parameters, 24
IGP synchronization, 20, 30
IS-IS synchronization, 31
label acceptance control, 37
label acceptance policy, 27
label advertisement control, 41
label advertisement policy, 26
label distribution control, 17
label distribution control mode, 26
label distribution+control, 17
label retention mode, 18
loop detection configuration, 28
LSP configuration, 33
LSP generation policy, 25
MD5 authentication, 25
message types, 15
nonstop routing (NSR), 20
nonstop routing (NSR) configuration, 29
operation, 16
OSPF synchronization, 30
protocols and standards, 22
session parameters configuration, 24
session reset, 32
SNMP notification enable, 32
terminology, 15
MPLS L3VPN Level 1 carrier, 164
MPLS L3VPN Level 2 carrier, 164
MPLS control plane, 2
MPLS forwarding plane, 2
MPLS forwarding process, 4
LDP FRR, 21
LDP FRR configuration, 32
LDP link hello parameters, 24
MPLS L3VPN OSPF sham link, 170, 190
MPLS L3VPN OSPF sham link configuration, 250
MPLS L3VPN OSPF sham link creation, 191
MPLS TE attribute advertisement, 51
MPLS TE FRR CRLSP link protection, 55
MPLS TE link attribute, 62
MPLS TE link attribute advertisement (IGP TE extension), 63
MPLS TE link attribute advertisement (IS-IS TE), 64
MPLS TE link attribute advertisement (OSPF TE), 63
MPLS L3VPN BGP route flapping logging, 194
LDP loop detection max hop count, 28
LDP loop detection path vector, 28
MPLS L3VPN routing loop avoidance, 170
MPLS TE loop detection, 69
MPLS L3VPN configuration, 190
MPLS TE configuration, 65
troubleshooting MPLS TE no TE LSA generated, 126
exclusive tunnel configuration, 151
LDP configuration, 15, 22, 33
LDP label acceptance control, 37
LDP label advertisement control, 41
LDP loop detection, 28
LDP LSP configuration, 33
LDP LSP generation policy, 25
MPLS control plane, 2
MPLS dynamic LSP establishment, 3
MPLS static LSP establishment, 3
MPLS TE auto FRR configuration, 113
MPLS TE bidirectional tunnel, 97
MPLS TE configuration, 50, 58, 79
MPLS TE CRLSP backup, 103
MPLS TE FRR manual bypass tunnel, 107
MPLS TE IETF DS-TE configuration, 119
MPLS TE inter-AS tunnel establishment (RSVP-TE), 90
MPLS TE tunnel establishment (RSVP-TE), 84
MPLS TE tunnel establishment (static CRLSP), 79
MPLS TTL propagation, 7
preferred tunnel configuration, 151
preferred tunnel+selection order configuration, 152
static feature and software version compatibility, 11
static LSP configuration, 11, 12
static LSP display, 12
tunnel policy configuration, 149, 151
tunnel selection order configuration, 152
LDP configuration, 15, 22, 33
LDP GR, 18
LDP label acceptance control, 37
LDP label advertisement control, 41
LDP LSP configuration, 33
MPLS control plane, 2
MPLS network architecture, 2
MPLS TTL propagation, 7
MPLS TTL-expired message send, 9
M
MCE, 280
MPLS, 9
MPLS L3VPN, 195
MPLS TE, 79
RSVP, 141
make-before-break (MPLS TE), 53
MPLS TE DS-TE bandwidth constraint model, 56
MPLS E FRR bypass tunnel on PLR (manual setup), 77
LDP configuration, 15, 22, 33
LDP FEC label mapping, 15
LDP GR, 18
LDP label acceptance control, 37
LDP label advertisement control, 41
LDP LSP configuration, 33
LDP message types, 15
LDP operation, 16
LDP terminology, 15
configuration, 265, 268, 280
display, 280
EBGP VPN route advertisement, 286
maintain, 280
MCE-PE EBGP, 279
MCE-PE IBGP configuration, 279
MCE-PE IS-IS, 278
MCE-PE OSPF, 277
MCE-PE RIP, 277
MCE-PE routing configuration, 276
MCE-PE static routing, 276
MCE-VPN site EBGP, 273
MCE-VPN site IBGP, 275
MCE-VPN site IS-IS, 273
MCE-VPN site OSPF, 272
MCE-VPN site RIP, 271
MCE-VPN site routing, 271
MCE-VPN site static routing, 271
OSPF VPN route advertisement, 280
routing configuration, 270
VPN instance configuration, 269
VPN instance creation, 269
VPN instance route related attributes, 269
VPN instance+interface association, 269
LDP authentication, 25
RSVP authentication, 135
LDP advertisement, 15
LDP discovery, 15
LDP notification, 15
LDP session, 15
MPLS TTL-expired message send, 9
RSVP authentication, 135
RSVP CRLSP setup, 134
RSVP refresh message, 134
RSVP reliable message delivery, 134
RSVP Srefresh mechanism, 134
RSVP-TE message types, 133
LDP label advertisement downstream on demand (DoD), 17
LDP label advertisement downstream unsolicited (DU), 17
LDP label distribution control, 26
LDP label retention conservative, 18
LDP label retention liberal, 18
MPLS L3VPN POP label forwarding, 191
MPLS L3VPN POPGO label forwarding, 191
MPLS TE bidirectional tunnel associated, 58
MPLS TE bidirectional tunnel co-routed, 58
MPLS TE FRR CRLSP link protection, 55
MPLS L3VPN hub-spoke network configuration, 202
basic concepts, 1
basics configuration, 1, 5
basics feature and software version compatibility, 5
control plane, 2
display, 9
egress label type advertisement, 6
enable, 5
exclusive tunnel configuration, 151
FEC, 1
FEC label format, 1
forwarding plane, 2
forwarding process, 4
LDP backoff, 25
LDP configuration, 15, 22, 33
LDP display, 32
LDP enable, 23
LDP FRR, 21
LDP FRR configuration, 32, 46
LDP GR, 18
LDP GR configuration, 29
LDP hello parameters, 24
LDP label acceptance control, 37
LDP label acceptance policy, 27
LDP label advertisement control, 41
LDP label advertisement policy, 26
LDP label distribution control mode, 26
LDP loop detection, 28
LDP LSP configuration, 33
LDP LSP generation policy, 25
LDP MD5 authentication, 25
LDP message types, 15
LDP NSR, 20
LDP NSR configuration, 29
LDP operation, 16
LDP protocols and standards, 22
LDP session parameters, 24
LDP session reset, 32
LDP SNMP notification, 32
LDP-IGP synchronization, 30
LFIB, 2
LSP, 2
LSP establishment, 3
LSR, 2
maintain, 9
MTU set, 6
network architecture, 2
PHP, 4
preferred tunnel configuration, 151
preferred tunnel+selection order configuration, 152
protocols and standards, 5
RSVP display, 141
RSVP maintain, 141
RSVP protocols and standards, 136
SNMP notifications enable, 9
static CRLSP configuration, 127, 128
static CRLSP display, 128
static LSP configuration, 11, 12
TTL propagation, 7
TTL-expired message send, 9
tunnel information display, 151
tunnel policy configuration, 149, 149, 151
tunnel selection order configuration, 152
architecture, 154, 265
basic configuration, 174, 197
BGP AS number substitution, 171, 192
BGP AS number substitution configuration, 254
BGP route flapping logging enable, 194
BGP route target attributes, 156, 267
BGP VPNv4 route control, 182
BGP-OSPF interaction, 169
carrier's carrier, 164, 226
concepts, 154, 265
configuration, 154, 174, 197
display, 195
egress PE VPN label processing mode, 191
feature and software version compatibility, 174
FRR, 172
FRR configuration, 192
FRR configuration (IPv4 route/VPNv4 route backup), 260
FRR configuration (VPNv4 route/IPv4 route backup), 262
FRR configuration (VPNv4 route/route backup), 258
FRR IPv4 route backup (VPNv4 route), 173
FRR VPNv4 route backup (IPv4 route), 173
FRR VPNv4 route backup (VPNv4 route), 172
HoVPN configuration, 189, 243
HoVPN network, 167
hub-spoke network configuration, 202
inter-AS option A configuration, 209
inter-AS option B configuration, 214
inter-AS option C configuration, 219
inter-AS VPN, 160
inter-AS VPN configuration, 183
inter-AS VPN option A, 184
inter-AS VPN option B, 184
inter-AS VPN option C, 185
inter-AS VPN option C ASBR, 186
inter-AS VPN option C PE, 185
loopback interface configuration, 190
maintain, 195
MCE configuration, 265, 268, 280
MCE display, 280
MCE EBGP VPN route advertisement, 286
MCE maintain, 280
MCE OSPF VPN route advertisement, 280
MCE routing configuration, 270
MCE-PE EBGP, 279
MCE-PE IBGP, 279
MCE-PE IS-IS, 278
MCE-PE OSPF, 277
MCE-PE RIP, 277
MCE-PE routing configuration, 276
MCE-PE static routing, 276
MCE-VPN site EBGP, 273
MCE-VPN site IBGP, 275
MCE-VPN site IS-IS, 273
MCE-VPN site OSPF, 272
MCE-VPN site RIP, 271
MCE-VPN site routing, 271
MCE-VPN site static routing, 271
MP-BGP, 156
nested VPN, 166
nested VPN configuration, 188, 234
nested VPN routing information propagation, 166
networking scheme, 158
networking scheme (basic), 158
networking scheme (extranet), 159
networking scheme (hub-spoke), 158
OSPF area PE-CE configuration, 168
OSPF sham link, 170
OSPF sham link configuration, 190, 250
OSPF sham link creation, 191
OSPF VPN extension, 168
OSPF VPN on PE, 168
packet forwarding, 157
PE-CE EBGP, 178
PE-CE IBGP, 180
PE-CE IS-IS, 178
PE-CE OSPF, 177
PE-CE RIP, 177
PE-CE routing, 176
PE-CE static routing, 177
PE-PE routing, 181
protocols and standards, 174
route advertisement, 156
routing loop avoidance, 170
site, 154, 265
SNMP notification enable, 194
VPN instance, 155, 266
VPN instance configuration, 175
VPN instance creation, 175
VPN instance route related attributes, 176
VPN instance+interface association, 175
VPN-IPv4 address, 155, 266
MCE configuration, 280
MCE EBGP VPN route advertisement, 286
MCE OSPF VPN route advertisement, 280
MPLS L3VPN basic configuration, 197
MPLS L3VPN BGP AS number substitution configuration, 254
MPLS L3VPN configuration, 154, 174, 197
MPLS L3VPN HoVPN configuration, 243
MPLS L3VPN inter-AS option A configuration, 209
MPLS L3VPN inter-AS option B configuration, 214
MPLS L3VPN inter-AS option C configuration, 219
MPLS L3VPN nested VPN configuration, 234
MPLS L3VPN OSPF sham link configuration, 250
attribute advertisement, 51
auto FRR configuration, 113
basic concepts, 50
bidirectional tunnel, 58, 97
bidirectional tunnel configuration, 72
class type, 56
configuration, 50, 58, 79
CRLSP backup, 54, 73, 103
CRLSP MPLS TE tunnel, 50
CRLSP path selection control, 66
CRLSP RSVP-TE setup, 52
CSPF path calculation, 51
display, 79
DS-TE, 56, 56
DS-TE configuration, 60
enable, 59
exclusive tunnel configuration, 151
feature and software version compatibility, 58
FRR, 55, 73
FRR bypass tunnel on PLR, 74
FRR CRLSP link protection, 55
FRR CRLSP node protection, 55
FRR manual bypass tunnel, 107
FRR node fault detection, 78
FRR optimal bypass tunnel selection interval, 78
IETF DS-TE configuration, 119
inter-AS tunnel establishment (RSVP-TE), 90
link attribute advertisement (IGP TE extension), 63
link attribute advertisement (IS-IS TE), 64
link attribute advertisement (OSPF TE), 63
link attribute configuration, 62
maintain, 79
make-before-break, 53
MCE configuration, 280
MCE EBGP VPN route advertisement, 286
MCE OSPF VPN route advertisement, 280
MPLS L3VPN basic configuration, 197
MPLS L3VPN BGP AS number substitution configuration, 254
MPLS L3VPN carrier's carrier, 226
MPLS L3VPN configuration, 154, 174, 197
MPLS L3VPN HoVPN configuration, 243
MPLS L3VPN inter-AS option A configuration, 209
MPLS L3VPN inter-AS option B configuration, 214
MPLS L3VPN inter-AS option C configuration, 219
MPLS L3VPN nested VPN configuration, 234
MPLS L3VPN OSPF sham link configuration, 250
preferred tunnel configuration, 151
preferred tunnel+selection order configuration, 152
protocols and standards, 58
route pinning, 54
RSVP authentication, 135, 138
RSVP BFD enable, 140
RSVP configuration, 133, 136, 141
RSVP CRLSP setup, 134
RSVP GR configuration, 140, 146
RSVP Graceful Restart (GR), 135
RSVP hello extension, 137
RSVP packet DSCP value, 140
RSVP refresh, 136
RSVP refresh mechanism, 134
RSVP reliable message delivery, 137
RSVP Srefresh configuration, 137
RSVP-TE message types, 133
RSVP-TE object types, 133
RSVP-TE tunnel establishment, 66, 141
traffic forwarding, 52
traffic forwarding automatic route advertisement, 52
traffic forwarding configuration, 70
traffic forwarding static routing, 52
troubleshoot, 126
troubleshoot no TE LSA generated, 126
tunnel automatic bandwidth adjustment, 54
tunnel configuration (dynamic CRLSP), 62
tunnel configuration (static CRLSP), 61
tunnel constraint configuration, 64
tunnel establishment (RSVP-TE), 84
tunnel establishment (static CRLSP), 79
tunnel interface configuration, 60
tunnel policy configuration, 149, 151
tunnel reoptimization, 54
tunnel selection order configuration, 152
tunnel setup, 68
tunnel traffic direction (static routing), 71
tunnel/tunnel bundle traffic direction (automatic route advertisement), 71
MPLS TE bidirectional tunnel, 58
MPLS MTU set, 6
Multiprotocol Label Switching. Use
N
configuration, 188, 234
MPLS L3VPN, 166
routing information propagation, 166
exclusive tunnel configuration, 151
LDP backoff, 25
LDP enable, 23
LDP FRR, 21
LDP FRR configuration, 32, 46
LDP GR, 18
LDP GR configuration, 29
LDP hello parameters, 24
LDP IS-IS synchronization, 31
LDP label acceptance control, 37
LDP label acceptance policy, 27
LDP label advertisement control, 41
LDP label advertisement policy, 26
LDP label distribution control mode, 26
LDP loop detection, 28
LDP LSP configuration, 33
LDP LSP generation policy, 25
LDP MD5 authentication, 25
LDP message types, 15
LDP NSR, 20
LDP NSR configuration, 29
LDP operation, 16
LDP session parameters, 24
LDP session reset, 32
LDP SNMP notification, 32
LDP terminology, 15
LDP-IGP synchronization, 20, 30
LDP-OSPF synchronization, 30
MCE EBGP VPN route advertisement, 286
MCE OSPF VPN route advertisement, 280
MCE routing configuration, 270
MCE VPN instance, 269
MCE VPN instance route related attributes, 269
MCE VPN instance+interface association, 269
MCE-PE EBGP, 279
MCE-PE IBGP configuration, 279
MCE-PE IS-IS, 278
MCE-PE OSPF, 277
MCE-PE RIP, 277
MCE-PE routing configuration, 276
MCE-PE static routing, 276
MCEVPN instance creation, 269
MCE-VPN site EBGP, 273
MCE-VPN site IBGP, 275
MCE-VPN site IS-IS, 273
MCE-VPN site OSPF, 272
MCE-VPN site RIP, 271
MCE-VPN site routing, 271
MCE-VPN site static routing, 271
MPLS control plane, 2
MPLS egress label type advertisement, 6
MPLS FEC, 1
MPLS FEC label format, 1
MPLS forwarding plane, 2
MPLS forwarding process, 4
MPLS L3VPN basic configuration, 197
MPLS L3VPN basics, 174
MPLS L3VPN BGP AS number substitution, 171, 192
MPLS L3VPN BGP AS number substitution configuration, 254
MPLS L3VPN BGP route flapping logging, 194
MPLS L3VPN BGP route target attributes, 156, 267
MPLS L3VPN BGP VPNv4 route control, 182
MPLS L3VPN BGP-OSPF interaction, 169
MPLS L3VPN carrier's carrier, 164, 226
MPLS L3VPN concepts, 154, 265
MPLS L3VPN egress PE VPN label processing mode, 191
MPLS L3VPN FRR, 172
MPLS L3VPN FRR configuration, 192
MPLS L3VPN FRR configuration (IPv4 route/VPNv4 route backup), 260
MPLS L3VPN FRR configuration (VPNv4 route/IPv4 route backup), 262
MPLS L3VPN FRR configuration (VPNv4 route/route backup), 258
MPLS L3VPN HoVPN configuration, 189, 243
MPLS L3VPN HoVPN network, 167
MPLS L3VPN hub-spoke network configuration, 202
MPLS L3VPN inter-AS option A configuration, 209
MPLS L3VPN inter-AS option B configuration, 214
MPLS L3VPN inter-AS option C configuration, 219
MPLS L3VPN inter-AS VPN, 160
MPLS L3VPN inter-AS VPN configuration, 183
MPLS L3VPN inter-AS VPN option A, 160, 184
MPLS L3VPN inter-AS VPN option B, 184
MPLS L3VPN inter-AS VPN option C, 185
MPLS L3VPN loopback interface, 190
MPLS L3VPN MP-BGP, 156
MPLS L3VPN nested VPN, 166
MPLS L3VPN nested VPN configuration, 188, 234
MPLS L3VPN nested VPN routing information propagation, 166
MPLS L3VPN networking scheme, 158
MPLS L3VPN networking scheme (basic), 158
MPLS L3VPN networking scheme (extranet), 159
MPLS L3VPN networking scheme (hub-spoke), 158
MPLS L3VPN OSPF area PE-CE configuration, 168
MPLS L3VPN OSPF sham link, 170, 190
MPLS L3VPN OSPF sham link configuration, 250
MPLS L3VPN OSPF sham link creation, 191
MPLS L3VPN OSPF VPN extension, 168
MPLS L3VPN OSPF VPN on PE, 168
MPLS L3VPN packet forwarding, 157
MPLS L3VPN PE-CE EBGP, 178
MPLS L3VPN PE-CE IBGP, 180
MPLS L3VPN PE-CE IS-IS, 178
MPLS L3VPN PE-CE OSPF, 177
MPLS L3VPN PE-CE RIP, 177
MPLS L3VPN PE-CE routing, 176
MPLS L3VPN PE-CE static routing, 177
MPLS L3VPN PE-PE routing, 181
MPLS L3VPN route advertisement, 156
MPLS L3VPN routing loop avoidance, 170
MPLS L3VPN site, 154, 265
MPLS L3VPN SNMP notification, 194
MPLS L3VPN VPN instance, 155, 175, 266
MPLS L3VPN VPN instance creation, 175
MPLS L3VPN VPN instance route related attributes, 176
MPLS L3VPN VPN instance+interface association, 175
MPLS L3VPN VPN-IPv4 address, 155, 266
MPLS LFIB, 2
MPLS LSP, 2
MPLS LSP establishment, 3
MPLS LSR, 2
MPLS MTU set, 6
MPLS PHP, 4
MPLS TE auto FRR configuration, 113
MPLS TE bidirectional tunnel, 58, 97
MPLS TE CRLSP backup, 54, 73, 103
MPLS TE CRLSP RSVP-TE setup, 52
MPLS TE CSPF path calculation, 51
MPLS TE DS-TE, 56, 60
MPLS TE FRR, 55, 73
MPLS TE FRR bypass tunnel on PLR, 74
MPLS TE FRR manual bypass tunnel, 107
MPLS TE FRR node fault detection, 78
MPLS TE FRR optimal bypass tunnel selection interval, 78
MPLS TE IETF DS-TE configuration, 119
MPLS TE inter-AS tunnel establishment (RSVP-TE), 90
MPLS TE make-before-break, 53
MPLS TE route pinning, 54
MPLS TE traffic forwarding, 52, 70
MPLS TE tunnel automatic bandwidth adjustment, 54
MPLS TE tunnel configuration (dynamic CRLSP), 62
MPLS TE tunnel configuration (static CRLSP), 61
MPLS TE tunnel establishment (RSVP-TE), 84
MPLS TE tunnel establishment (static CRLSP), 79
MPLS TE tunnel interface, 60
MPLS TE tunnel reoptimization, 54
MPLS TE tunnel setup, 68
MPLS TE tunnel with RSVP-TE, 66
MPLS TTL propagation, 7
MPLS TTL-expired message send, 9
preferred tunnel configuration, 151
preferred tunnel+selection order configuration, 152
RSVP authentication, 138
RSVP BFD enable, 140
RSVP GR configuration, 140, 146
RSVP hello extension, 137
RSVP packet DSCP value, 140
RSVP refresh, 136
RSVP reliable message delivery, 137
RSVP Srefresh configuration, 137
RSVP-TE tunnel establishment, 141
tunnel policy configuration, 149
tunnel selection order configuration, 152
LDP configuration, 15, 22, 33
MCE configuration, 265, 268, 280
MPLS architecture, 2
MPLS basic concepts, 1
MPLS basics configuration, 1, 5
MPLS L3VPN architecture, 154, 265
MPLS L3VPN configuration, 154, 174, 197
MPLS TE configuration, 50, 58, 79
RSVP configuration, 133, 136, 141
static CRLSP configuration, 127, 128
static LSP configuration, 11, 12
tunnel policy configuration, 149, 151
MPLS TE FRR node fault detection, 78
RSVP configuration, 133, 136, 141
RSVP GR configuration, 146
RSVP-TE tunnel establishment, 141
static CRLSP configuration, 127, 128
LDP NSR, 20
LDP NSR configuration, 29
LDP notification message, 15
LDP SNMP notification, 32
MPLS L3VPN SNMP notification, 194
MPLS SNMP notifications, 9
MPLS L3VPN BGP AS number substitution, 171, 192
MPLS L3VPN BGP AS number substitution configuration, 254
O
MPLS TE bidirectional tunnel, 58
RSVP-TE object types, 133
MPLS TE CRLSP tunnel reoptimization, 67
MPLS TE tunnel reoptimization, 54
ordinary CRLSP backup (MPLS TE), 54
LDP-OSPF synchronization, 30
MCE OSPF VPN route advertisement, 280
MCE-PE OSPF, 277
MCE-VPN site OSPF, 272
MPLS L3VPN BGP-OSPF interaction, 169
MPLS L3VPN hub-spoke network configuration, 202
MPLS L3VPN OSPF area PE-CE configuration, 168
MPLS L3VPN OSPF sham link, 170
MPLS L3VPN OSPF sham link configuration, 250
MPLS L3VPN OSPF sham link creation, 191
MPLS L3VPN OSPF VPN extension, 168
MPLS L3VPN OSPF VPN on PE, 168
MPLS L3VPN PE-CE OSPF, 177
MPLS L3VPN sham link configuration, 190
MPLS TE attribute advertisement, 51
MPLS TE link attribute advertisement (OSPF TE), 63
P
MPLS L3VPN architecture, 154, 265
LDP FRR, 21
LDP FRR configuration, 32
MPLS control plane, 2
MPLS egress label type advertisement, 6
MPLS FEC, 1
MPLS FEC label format, 1
MPLS forwarding plane, 2
MPLS forwarding process, 4
MPLS L3VPN packet forwarding, 157
MPLS MTU set, 6
MPLS TTL propagation, 7
RSVP packet DSCP value, 140
LDP keepalive, 24
LDP link hello, 24
LDP session, 24
LDP targeted hello, 24
LDP loop detection path vector, 28
MPLS TE CRLSP path selection, 66
MPLS TE CSPF calculation, 51
MPLS TE route pinning, 54
MPLS TE tunnel automatic bandwidth adjustment, 54
MPLS TE tunnel loose explicit path, 65
MPLS TE tunnel reoptimization, 54
MPLS TE tunnel strict explicit path, 65
RSVP-TE Path message, 133
RSVP-TE PathErr message, 133
RSVP-TE PathTear message, 133
MCE EBGP VPN route advertisement, 286
MCE OSPF VPN route advertisement, 280
MCE routing configuration, 270
MCE-PE EBGP, 279
MCE-PE IBGP configuration, 279
MCE-PE IS-IS, 278
MCE-PE OSPF, 277
MCE-PE RIP, 277
MCE-PE routing configuration, 276
MCE-PE static routing, 276
MPLS L3VPN architecture, 154, 265
MPLS L3VPN egress PE VPN label processing mode, 191
MPLS L3VPN HoVPN configuration, 189
MPLS L3VPN inter-AS VPN option C ASBR, 186
MPLS L3VPN inter-AS VPN option C PE, 185
MPLS L3VPN Layer 1 label packet forwarding, 157
MPLS L3VPN MP-BGP, 156
MPLS L3VPN nested VPN, 166
MPLS L3VPN nested VPN configuration, 188
MPLS L3VPN OSPF area PE-CE configuration, 168
MPLS L3VPN OSPF sham link, 190
MPLS L3VPN OSPF sham link creation, 191
MPLS L3VPN OSPF VPN on PE, 168
MPLS L3VPN PE-CE EBGP, 178
MPLS L3VPN PE-CE IBGP, 180
MPLS L3VPN PE-CE IS-IS, 178
MPLS L3VPN PE-CE OSPF, 177
MPLS L3VPN PE-CE RIP, 177
MPLS L3VPN PE-CE routing, 176
MPLS L3VPN PE-CE static routing, 177
MPLS L3VPN PE-PE routing, 181
LDP hello parameters, 24
LDP session parameters, 24
MPLS, 4
MPLS TE CRLSP route pinning, 67
MPLS TE route pinning, 54
MPLS TE FRR configuration on PLR, 74
MPLS TE FRR CRLSP link protection, 55
LDP label acceptance policy, 27
LDP label advertisement policy, 26
LDP LSP generation policy, 25
tunnel policy configuration, 149
POP label forwarding mode (MPLS L3VPN), 191
POPGO label forwarding mode (MPLS L3VPN), 191
preferred tunnel configuration, 151
preferred tunnel+selection order configuration, 152
prestandard mode DS-TE (MPLS TE), 56
primary CRLSP (MPLS TE FRR), 55
MPLS TE tunnel holding priority, 65
MPLS TE tunnel setup priority, 65
advertising MPLS TE link attribute (IGP TE extension), 63
associating MCE VPN instance+interface, 269
associating MPLS L3VPN VPN instance+interface, 175
configuring exclusive tunnel, 151
configuring LDP, 22
configuring LDP backoff, 25
configuring LDP FRR, 32, 46
configuring LDP GR, 29
configuring LDP hello parameter, 24
configuring LDP IS-IS synchronization, 31
configuring LDP label acceptance control, 37
configuring LDP label acceptance policy, 27
configuring LDP label advertisement control, 41
configuring LDP label advertisement policy, 26
configuring LDP label distribution control mode, 26
configuring LDP loop detection, 28
configuring LDP LSP, 33
configuring LDP LSP generation policy, 25
configuring LDP MD5 authentication, 25
configuring LDP NSR, 29
configuring LDP-IGP synchronization, 30
configuring LDP-OSPF synchronization, 30
configuring MCE, 268, 280
configuring MCE EBGP VPN route advertisement, 286
configuring MCE OSPF VPN route advertisement, 280
configuring MCE routing, 270
configuring MCE VPN instance, 269
configuring MCE VPN instance route related attribute, 269
configuring MCE-PE EBGP, 279
configuring MCE-PE IBGP, 279
configuring MCE-PE IS-IS, 278
configuring MCE-PE OSPF, 277
configuring MCE-PE RIP, 277
configuring MCE-PE routing, 276
configuring MCE-PE static routing, 276
configuring MCE-VPN site EBGP, 273
configuring MCE-VPN site IBGP, 275
configuring MCE-VPN site IS-IS, 273
configuring MCE-VPN site OSPF, 272
configuring MCE-VPN site RIP, 271
configuring MCE-VPN site routing, 271
configuring MCE-VPN site static routing, 271
configuring MPLS basics, 5
configuring MPLS L3VPN, 174
configuring MPLS L3VPN basics, 174, 197
configuring MPLS L3VPN BGP AS number substitution, 192, 254
configuring MPLS L3VPN BGP VPNv4 route control, 182
configuring MPLS L3VPN carrier's carrier, 226
configuring MPLS L3VPN FRR, 192
configuring MPLS L3VPN FRR (IPv4 route/VPNv4 route backup), 260
configuring MPLS L3VPN FRR (VPNv4 route/IPv4 route backup), 262
configuring MPLS L3VPN FRR (VPNv4 route/route backup), 258
configuring MPLS L3VPN HoVPN, 189, 243
configuring MPLS L3VPN hub-spoke network, 202
configuring MPLS L3VPN inter-AS option A, 209
configuring MPLS L3VPN inter-AS option B, 214
configuring MPLS L3VPN inter-AS option C, 219
configuring MPLS L3VPN inter-AS VPN configuration, 183
configuring MPLS L3VPN inter-AS VPN option A, 184
configuring MPLS L3VPN inter-AS VPN option B, 184
configuring MPLS L3VPN inter-AS VPN option C, 185
configuring MPLS L3VPN inter-AS VPN option C ASBR, 186
configuring MPLS L3VPN inter-AS VPN option C PE, 185
configuring MPLS L3VPN loopback interface, 190
configuring MPLS L3VPN nested VPN, 188, 234
configuring MPLS L3VPN OSPF sham link, 190, 250
configuring MPLS L3VPN PE-CE EBGP, 178
configuring MPLS L3VPN PE-CE IBGP, 180
configuring MPLS L3VPN PE-CE IS-IS, 178
configuring MPLS L3VPN PE-CE OSPF, 177
configuring MPLS L3VPN PE-CE RIP, 177
configuring MPLS L3VPN PE-CE routing, 176
configuring MPLS L3VPN PE-CE static routing, 177
configuring MPLS L3VPN PE-PE routing, 181
configuring MPLS L3VPN VPN instance, 175
configuring MPLS L3VPN VPN instance route related attribute, 176
configuring MPLS TE, 58
configuring MPLS TE auto FRR, 113
configuring MPLS TE automatic bandwidth adjustment, 69
configuring MPLS TE bidirectional tunnel, 72, 97
configuring MPLS TE CRLSP backup, 73, 103
configuring MPLS TE CRLSP path selection metric type, 66
configuring MPLS TE CRLSP route pinning, 67
configuring MPLS TE CRLSP tunnel reoptimization, 67
configuring MPLS TE DS-TE, 60
configuring MPLS TE FRR, 73
configuring MPLS TE FRR bypass tunnel on PLR, 74
configuring MPLS TE FRR manual bypass tunnel, 107
configuring MPLS TE FRR node fault detection, 78
configuring MPLS TE FRR optimal bypass tunnel selection interval, 78
configuring MPLS TE IETF DS-TE, 119
configuring MPLS TE link attribute, 62
configuring MPLS TE link attribute advertisement (IS-IS TE), 64
configuring MPLS TE link attribute advertisement (OSPF TE), 63
configuring MPLS TE RSVP-TE RSVP resource reservation style, 70
configuring MPLS TE traffic forwarding, 70
configuring MPLS TE tunnel (dynamic CRLSP), 62
configuring MPLS TE tunnel (static CRLSP), 61
configuring MPLS TE tunnel affinity attribute, 64
configuring MPLS TE tunnel constraints, 64
configuring MPLS TE tunnel constraints (bandwidth), 64
configuring MPLS TE tunnel interface, 60
configuring MPLS TE tunnel loose explicit path, 65
configuring MPLS TE tunnel strict explicit path, 65
configuring MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement), 71
configuring MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement/forwarding adjacency), 72
configuring MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement/IGP shortcut), 71
configuring MPLS TE tunnel/tunnel bundle traffic direction (static routing), 71
configuring MPLS TTL propagation, 7
configuring preferred tunnel, 151
configuring preferred tunnel+selection order, 152
configuring RSVP, 136
configuring RSVP authentication (interface view), 138
configuring RSVP authentication (RSVP neighbor view), 138
configuring RSVP authentication (RSVP view), 138
configuring RSVP GR, 140, 146
configuring RSVP hello extension, 137
configuring RSVP refresh, 136
configuring RSVP reliable message delivery, 137
configuring RSVP Srefresh, 137
configuring static CRLSP, 127, 128
configuring static LSP, 11, 12
configuring tunnel policy, 149
configuring tunnel selection order, 152
controlling MPLS TE CRLSP path selection, 66
controlling MPLS TE tunnel setup, 68
creating MCE VPN instance, 269
creating MPLS L3VPN OSPF sham link, 191
creating MPLS L3VPN VPN instance, 175
displaying LDP, 32
displaying MCE, 280
displaying MPLS, 9
displaying MPLS L3VPN, 195
displaying MPLS TE, 79
displaying RSVP, 141
displaying static CRLSP, 128
displaying static LSP, 12
displaying tunnel information, 151
enabling LDP globally, 23
enabling LDP on interface, 23
enabling LDP SNMP notification, 32
enabling MPLS, 5
enabling MPLS L3VPN BGP route flapping logging, 194
enabling MPLS L3VPN SNMP notification, 194
enabling MPLS SNMP notifications, 9
enabling MPLS TE, 59
enabling MPLS TE FRR, 74
enabling MPLS TE label recording, 69
enabling MPLS TE loop detection, 69
enabling MPLS TE route recording, 69
enabling MPLS TTL-expired message send, 9
enabling RSVP, 136
enabling RSVP BFD, 140
establishing MPLS TE inter-AS tunnel (RSVP-TE), 90
establishing MPLS TE tunnel (RSVP-TE), 84
establishing MPLS TE tunnel (static CRLSP), 79
establishing MPLS TE tunnel with RSVP-TE, 66
establishing RSVP-TE tunnel, 141
maintaining MCE, 280
maintaining MPLS, 9
maintaining MPLS L3VPN, 195
maintaining MPLS TE, 79
maintaining RSVP, 141
resetting LDP session, 32
setting MPLS MTU, 6
setting MPLS TE tunnel holding priority, 65
setting MPLS TE tunnel setup priority, 65
setting MPLS TE tunnel setup retry, 69
setting RSVP packet DSCP value, 140
setting up MPLS E FRR bypass tunnel on PLR (automatic), 77
setting up MPLS E FRR bypass tunnel on PLR (manual), 77
specifying MPLS egress label type advertisement, 6
specifying MPLS L3VPN egress PE VPN label processing mode, 191
troubleshooting MPLS TE no TE LSA generated, 126
MPLS L3VPN nested VPN routing information, 166
MPLS TTL, 7
LDP, 22
MPLS, 5
MPLS L3VPN, 174
MPLS TE, 58
RSVP, 136
MPLS TE bidirectional tunnel, 58
Q
MPLS TE CRLSP RSVP-TE setup, 52
MPLS TE DS-TE, 56
R
MPLS TE DS-TE bandwidth constraint model, 56
RECORD_ROUTE object (RSVP-TE), 133
MPLS L3VPN inter-AS VPN option B, 160, 161
MPLS L3VPN inter-AS VPN option C, 160, 162
RSVP refresh, 136
RSVP refresh mechanism, 134
RSVP Srefresh configuration, 137
RSVP Srefresh mechanism, 134
reliable message delivery (RSVP), 134, 137
MPLS TE tunnel reoptimization, 54
LDP session, 32
Resource Reservation Protocol. Use
MPLS TE FRR bypass tunnel on PLR, 76
ResvConf message (RSVP-TE), 133
ResvErr message (RSVP-TE), 133
ResvTear message (RSVP-TE), 133
MCE-PE RIP, 277
MCE-VPN site RIP, 271
MPLS L3VPN PE-CE RIP configuration, 177
MCE VPN instance route related attributes, 269
MPLS L3VPN BGP VPNv4 route control, 182
MPLS L3VPN route advertisement, 156
MPLS L3VPN VPN instance route related attributes, 176
LDP FRR configuration, 46
MCE configuration, 265, 280
MCE EBGP VPN route advertisement, 286
MCE OSPF VPN routes advertisement, 280
MCE routing configuration, 270
MCE-PE EBGP, 279
MCE-PE IBGP configuration, 279
MCE-PE IS-IS, 278
MCE-PE OSPF, 277
MCE-PE RIP, 277
MCE-PE routing configuration, 276
MCE-PE static routing, 276
MCE-VPN site EBGP, 273
MCE-VPN site IBGP, 275
MCE-VPN site IS-IS, 273
MCE-VPN site OSPF, 272
MCE-VPN site RIP, 271
MCE-VPN site routing, 271
MCE-VPN site static routing, 271
MPLS forwarding process, 4
MPLS L3VPN basic configuration, 197
MPLS L3VPN BGP AS number substitution, 171
MPLS L3VPN BGP AS number substitution configuration, 254
MPLS L3VPN BGP route target attributes, 156, 267
MPLS L3VPN BGP VPNv4 route control, 182
MPLS L3VPN carrier's carrier, 226
MPLS L3VPN configuration, 197
MPLS L3VPN egress PE VPN label processing mode, 191
MPLS L3VPN FRR, 172
MPLS L3VPN FRR configuration, 192
MPLS L3VPN FRR configuration (IPv4 route/VPNv4 route backup), 260
MPLS L3VPN FRR configuration (VPNv4 route/IPv4 route backup), 262
MPLS L3VPN FRR configuration (VPNv4 route/route backup), 258
MPLS L3VPN HoVPN configuration, 243
MPLS L3VPN hub-spoke network configuration, 202
MPLS L3VPN inter-AS option A configuration, 209
MPLS L3VPN inter-AS option B configuration, 214
MPLS L3VPN inter-AS option C configuration, 219
MPLS L3VPN MP-BGP, 156
MPLS L3VPN nested VPN configuration, 234
MPLS L3VPN nested VPN routing information propagation, 166
MPLS L3VPN OSPF sham link, 170
MPLS L3VPN OSPF sham link configuration, 250
MPLS L3VPN OSPF VPN extension, 168
MPLS L3VPN OSPF VPN on PE, 168
MPLS L3VPN PE-PE routing, 181
MPLS L3VPN route advertisement, 156
MPLS L3VPN routing loop avoidance, 170
MPLS L3VPN SNMP notification, 194
MPLS LFIB, 2
MPLS LSP, 2
MPLS LSP establishment, 3
MPLS LSR, 2
MPLS PHP, 4
MPLS TE auto FRR configuration, 113
MPLS TE bidirectional tunnel, 97
MPLS TE configuration, 50, 58
MPLS TE CRLSP backup, 103
MPLS TE FRR, 55
MPLS TE FRR manual bypass tunnel, 107
MPLS TE IETF DS-TE configuration, 119
MPLS TE inter-AS tunnel establishment (RSVP-TE), 90
MPLS TE make-before-break, 53
MPLS TE route pinning, 54
MPLS TE traffic forwarding, 52, 70
MPLS TE tunnel establishment (RSVP-TE), 84
MPLS TE tunnel establishment (static CRLSP), 79
MPLS TE tunnel/tunnel bundle traffic direction (automatic route advertisement), 71
MPLS TE tunnel/tunnel bundle traffic direction (static routing), 71
RSVP configuration, 133, 136, 141
RSVP GR configuration, 146
RSVP-TE EXPLICIT_ROUTE object, 133
RSVP-TE RECORD_ROUTE object, 133
RSVP-TE tunnel establishment, 141
authentication, 135
authentication configuration, 138
BFD enable, 140
configuration, 133, 136, 141
CRLSP setup, 134
display, 141
enable, 136
feature and software version compatibility, 136
GR configuration, 140, 146
Graceful Restart (GR), 135
hello extension configuration, 137
maintain, 141
packet DSCP value, 140
protocols and standards, 136
refresh configuration, 136
refresh mechanism, 134
reliable message delivery configuration, 137
Srefresh configuration, 137
tunnel establishment, 141
LABEL object, 133
message types, 133
MPLS TE auto FRR configuration, 113
MPLS TE bidirectional tunnel, 58, 72, 97
MPLS TE configuration, 50, 79
MPLS TE CRLSP backup, 73, 103
MPLS TE CRLSP dynamic establishment, 50
MPLS TE CRLSP path selection, 66
MPLS TE CRLSP setup, 52
MPLS TE FRR, 73
MPLS TE FRR bypass tunnel on PLR, 74
MPLS TE FRR manual bypass tunnel, 107
MPLS TE FRR node fault detection, 78
MPLS TE FRR optimal bypass tunnel selection interval, 78
MPLS TE IETF DS-TE configuration, 119
MPLS TE inter-AS tunnel establishment (RSVP-TE), 90
MPLS TE link attribute, 62
MPLS TE make-before-break FF, 53
MPLS TE make-before-break SE, 53
MPLS TE tunnel constraints, 64
MPLS TE tunnel establishment (RSVP-TE), 84
MPLS TE tunnel establishment (static CRLSP), 79
MPLS TE tunnel with RSVP-TE, 66
RSVP configuration, 136
tunnel establishment, 141
Russian Dolls Model. See
S
MPLS L3VPN networking, 158
MPLS L3VPN networking (basic), 158
MPLS L3VPN networking (extranet), 159
MPLS L3VPN networking (hub-spoke), 158
LDP MD5 authentication, 25
RSVP authentication, 138
preferred tunnel+selection order configuration, 152
tunnel selection order configuration, 152
MPLS TTL-expired message send, 9
LDP message type, 15
LDP session parameters, 24
LDP session reset, 32
RSVP-TE SESSION_ATTRIBUTE object, 133
LDP session reset, 32
MPLS MTU, 6
MPLS TE tunnel holding priority, 65
MPLS TE tunnel setup priority, 65
MPLS TE tunnel setup retry, 69
RSVP packet DSCP value, 140
MPLS E FRR bypass tunnel on PLR (automatic), 77
MPLS E FRR bypass tunnel on PLR (manual), 77
MPLS TE tunnel setup, 68
MPLS L3VPN OSPF sham link configuration, 190, 250
MPLS L3VPN OSPF sham link creation, 191
MPLS L3VPN, 154, 265
MPLS L3VPN notification, 194
MPLS SNMP notifications, 9
LDP feature compatibility, 22
MPLS basics feature compatibility, 5
MPLS L3VPN feature compatibility, 174
MPLS TE feature compatibility, 58
RSVP feature compatibility, 136
static CRLSP feature compatibility, 127
static LSP feature compatibility, 11
tunnel policy feature compatibility, 149
MPLS L3VPN HoVPN configuration, 189
MPLS egress label type advertisement, 6
MPLS L3VPN egress PE VPN label processing mode, 191
RSVP Srefresh configuration, 137
MCE-PE static routing, 276
MCE-VPN site static routing, 271
MPLS L3VPN PE-CE static routing, 177
MPLS LSP establishment, 3
MPLS TE traffic forwarding static routing, 52
MPLS TE tunnel/tunnel bundle traffic direction (static routing), 71
configuration, 127, 128
display, 128
MPLS TE establishment, 50
MPLS TE tunnel configuration, 61
MPLS TE tunnel establishment (static CRLSP), 79
configuration, 11, 12
display, 12
feature and software version compatibility, 11
MPLS TE configuration, 65
MPLS L3VPN BGP AS number substitution, 171, 192
MPLS L3VPN BGP AS number substitution configuration, 254
MPLS basics configuration, 1, 5
MPLS TE auto FRR configuration, 113
MPLS TE bidirectional tunnel, 97
MPLS TE configuration, 50, 58, 79
MPLS TE CRLSP backup, 103
MPLS TE FRR, 55
MPLS TE FRR manual bypass tunnel, 107
MPLS TE IETF DS-TE configuration, 119
MPLS TE inter-AS tunnel establishment (RSVP-TE), 90
MPLS TE tunnel establishment (RSVP-TE), 84
MPLS TE tunnel establishment (static CRLSP), 79
LDP IS-IS synchronization, 31
LDP-IGP synchronization, 20, 30
LDP-OSPF synchronization, 30
T
TE database. See
MPLS TE attribute advertisement, 51
MPLS TE CSPF calculation, 51
LDP backoff delay, 25
LDP link hello, 24
LDP targeted hello, 24
MPLS network architecture, 2
static LSP configuration, 11, 12
MPLS TE, 52
MPLS TE automatic route advertisement (forwarding adjacency), 52
MPLS TE automatic route advertisement (IGP shortcut), 52
MPLS TE CRLSP backup, 54
MPLS TE FRR, 55
MPLS TE make-before-break, 53
MPLS TE static routing, 52
MPLS TE traffic forwarding, 70
MPLS transit LSR, 2
LDP transport address, 24
LDP SNMP notification, 32
MPLS L3VPN SNMP notification, 194
MPLS SNMP notifications, 9
MPLS TE, 126
MPLS TE no TE LSA generated, 126
MPLS TTL propagation, 7
MPLS TTL-expired message send, 9
configuration, 149, 149, 151
feature and software version compatibility, 149
information display, 151
exclusive tunnel configuration, 151
MPLS TE auto FRR configuration, 113
MPLS TE bidirectional tunnel, 58, 72, 97
MPLS TE configuration, 50, 58, 79
MPLS TE CRLSP backup, 73, 103
MPLS TE DS-TE, 56, 60
MPLS TE FRR, 55, 73
MPLS TE FRR bypass tunnel on PLR, 74
MPLS TE FRR manual bypass tunnel, 107
MPLS TE FRR node fault detection, 78
MPLS TE FRR optimal bypass tunnel selection interval, 78
MPLS TE IETF DS-TE configuration, 119
MPLS TE inter-AS tunnel establishment (RSVP-TE), 90
MPLS TE make-before-break, 53
MPLS TE traffic forwarding, 52, 70
MPLS TE tunnel automatic bandwidth adjustment, 54
MPLS TE tunnel configuration (dynamic CRLSP), 62
MPLS TE tunnel configuration (static CRLSP), 61
MPLS TE tunnel establishment (RSVP-TE), 84
MPLS TE tunnel establishment (static CRLSP), 79
MPLS TE tunnel interface, 60
MPLS TE tunnel reoptimization, 54
MPLS TE tunnel setup, 68
MPLS TE tunnel with RSVP-TE, 66
preferred tunnel configuration, 151
preferred tunnel+selection order configuration, 152
RSVP-TE tunnel establishment, 141
tunnel policy configuration, 149, 149, 151
tunnel selection order configuration, 152
RSVP-TE EXPLICIT_ROUTE object, 133
RSVP-TE hello message, 133
RSVP-TE LABEL_REQUEST object, 133
RSVP-TE Path message, 133
RSVP-TE PathErr message, 133
RSVP-TE PathTear message, 133
RSVP-TE RECORD_ROUTE object, 133
RSVP-TE Resv message, 133
RSVP-TE ResvConf message, 133
RSVP-TE ResvErr message, 133
RSVP-TE ResvTear message, 133
RSVP-TE SESSION_ATTRIBUTE object, 133
U
MPLS L3VPN HoVPN configuration, 189
V
exclusive tunnel configuration, 151
MPLS L3VPN VPN-IPv4 address, 155, 266
preferred tunnel configuration, 151
preferred tunnel+selection order configuration, 152
tunnel policy configuration, 149, 151
tunnel selection order configuration, 152
MPLS L3VPN inter-AS VPN option A, 160, 160